AD40 AD8 Replay Plus Repartee Required Equipment n









- Slides: 20

AD-40, AD-8 Replay Plus Repartee

Required Equipment n n n A PC running DOS or Windows Debug. exe (included in DOS & Windows) A copy of the Avent. avd File Note: Debug is a Microsoft product and it is not included with OS2.

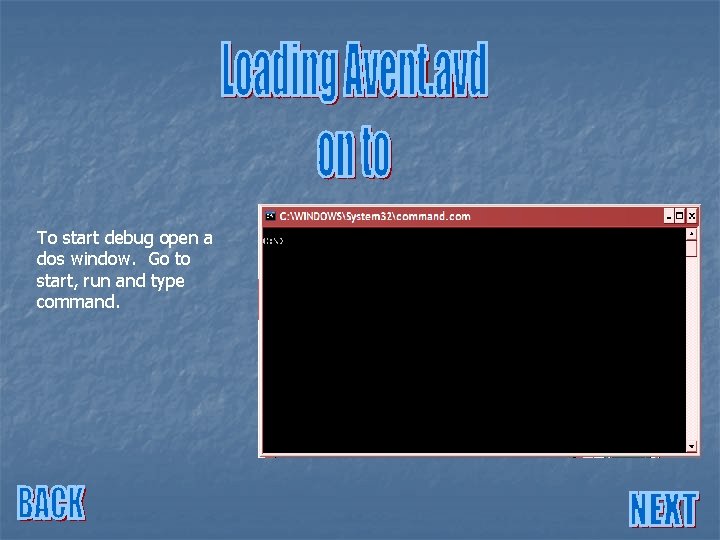
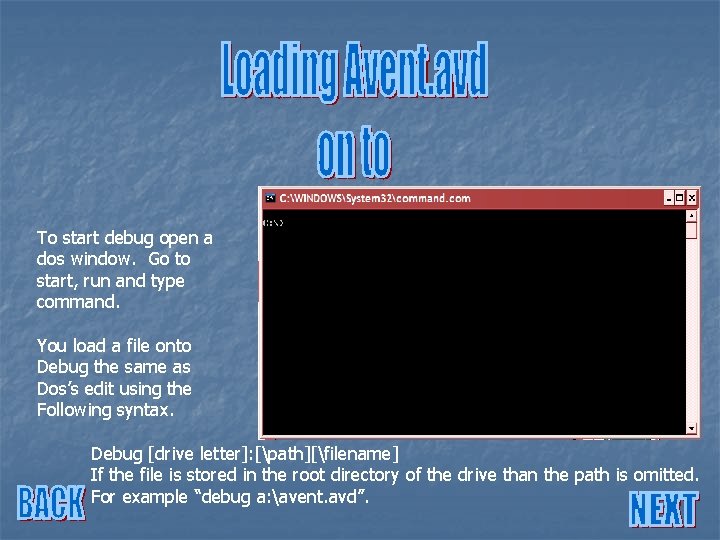
To start debug open a dos window. Go to start, run and type command.

To start debug open a dos window. Go to start, run and type command. You load a file onto Debug the same as Dos’s edit using the Following syntax. Debug [drive letter]: [path][filename] If the file is stored in the root directory of the drive than the path is omitted. For example “debug a: avent. avd”.

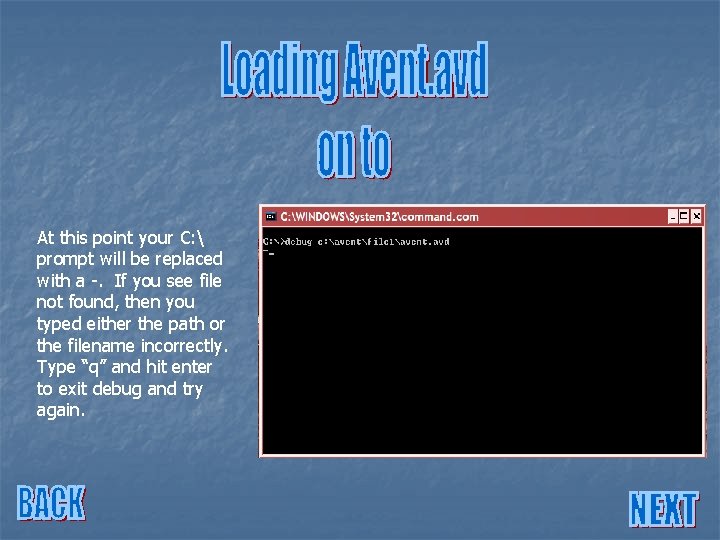
At this point your C: prompt will be replaced with a -. If you see file not found, then you typed either the path or the filename incorrectly. Type “q” and hit enter to exit debug and try again.

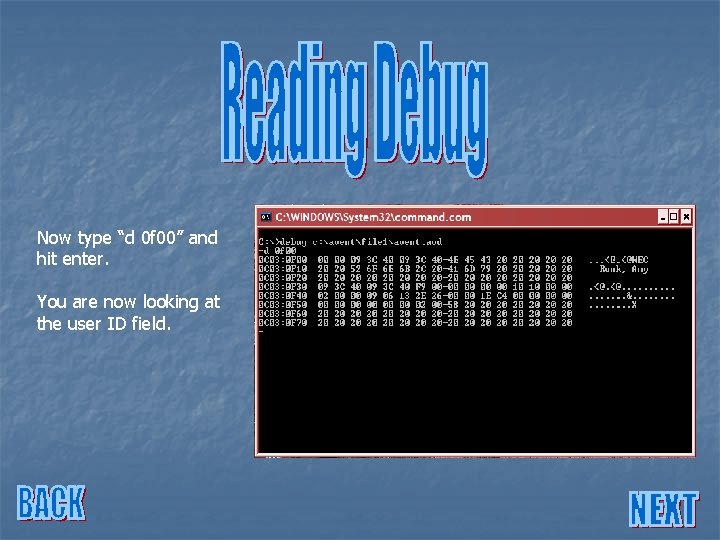
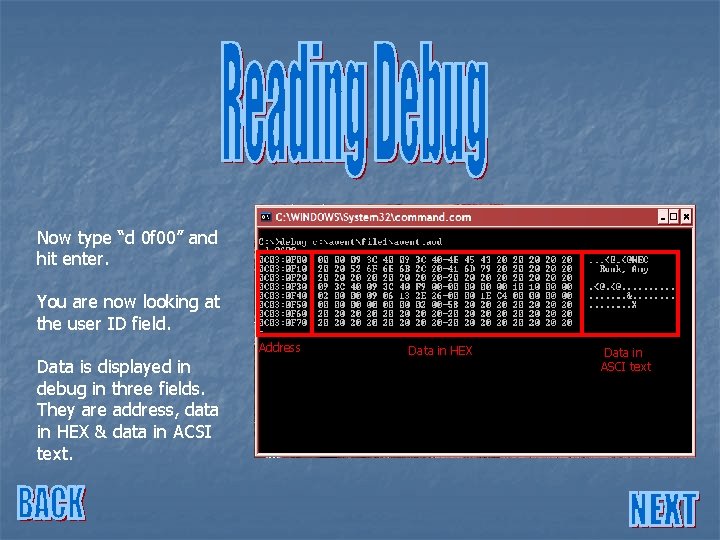
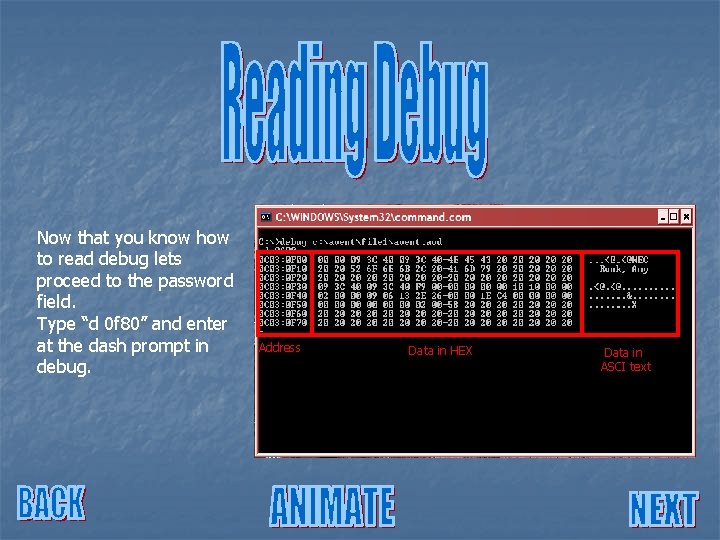
Now type “d 0 f 00” and hit enter. You are now looking at the user ID field.

Now type “d 0 f 00” and hit enter. You are now looking at the user ID field. Address Data is displayed in debug in three fields. They are address, data in HEX & data in ACSI text. Data in HEX Data in ASCI text

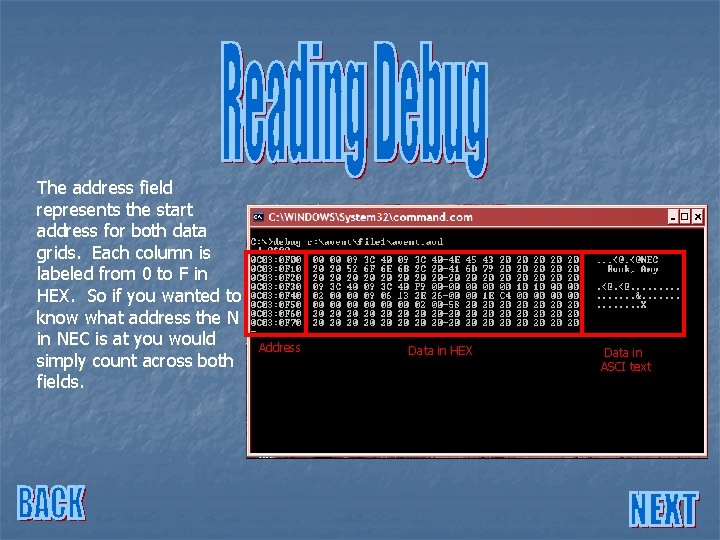
The address field represents the start address for both data grids. Each column is labeled from 0 to F in HEX. So if you wanted to know what address the N in NEC is at you would simply count across both fields. Address Data in HEX Data in ASCI text

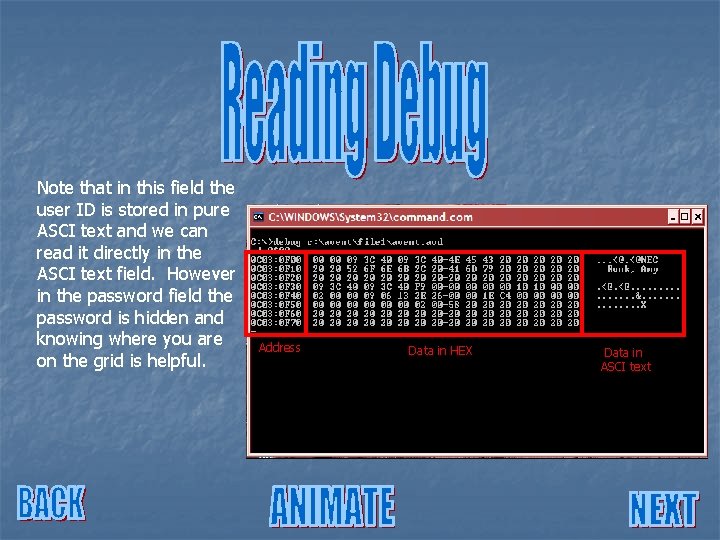
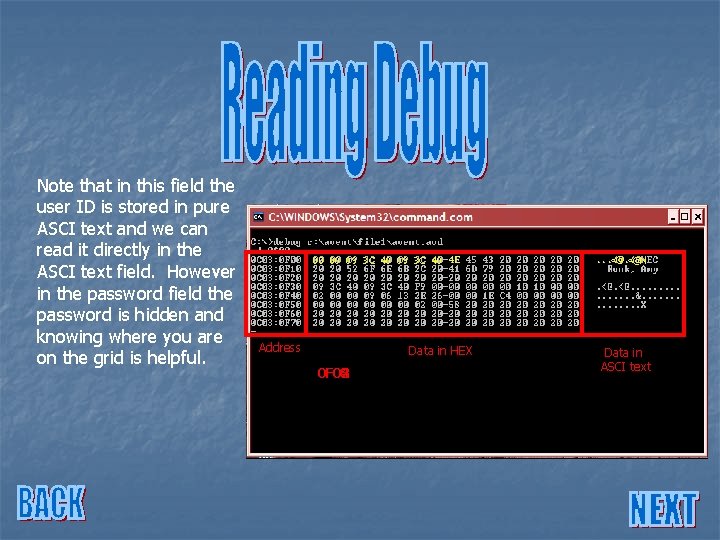
Note that in this field the user ID is stored in pure ASCI text and we can read it directly in the ASCI text field. However in the password field the password is hidden and knowing where you are on the grid is helpful. Address Data in HEX Data in ASCI text

Note that in this field the user ID is stored in pure ASCI text and we can read it directly in the ASCI text field. However in the password field the password is hidden and knowing where you are on the grid is helpful. 00 00 09 3 C 40 4 E Address Data in HEX 0 F 02 0 F 01 0 F 04 0 F 00 0 F 08 0 F 07 0 F 06 0 F 05 0 F 03 . . . <@N Data in ASCI text

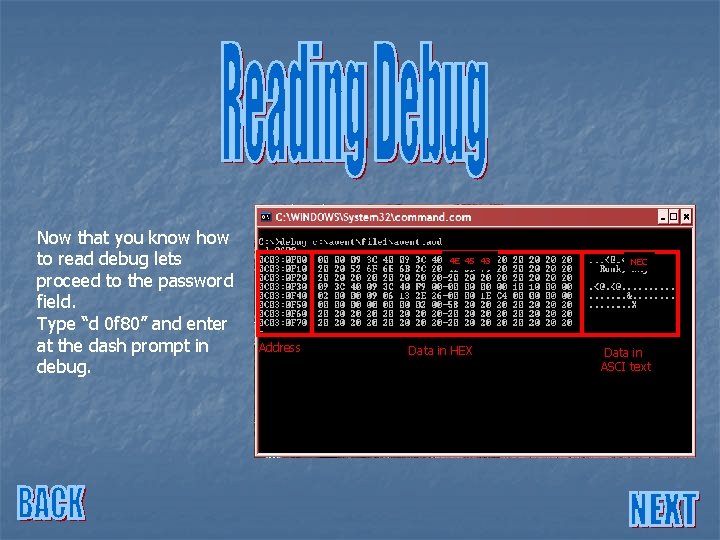
Now that you know how to read debug lets proceed to the password field. Type “d 0 f 80” and enter at the dash prompt in debug. Address Data in HEX Data in ASCI text

Now that you know how to read debug lets proceed to the password field. Type “d 0 f 80” and enter at the dash prompt in debug. 4 E 45 43 Address Data in HEX NEC Data in ASCI text

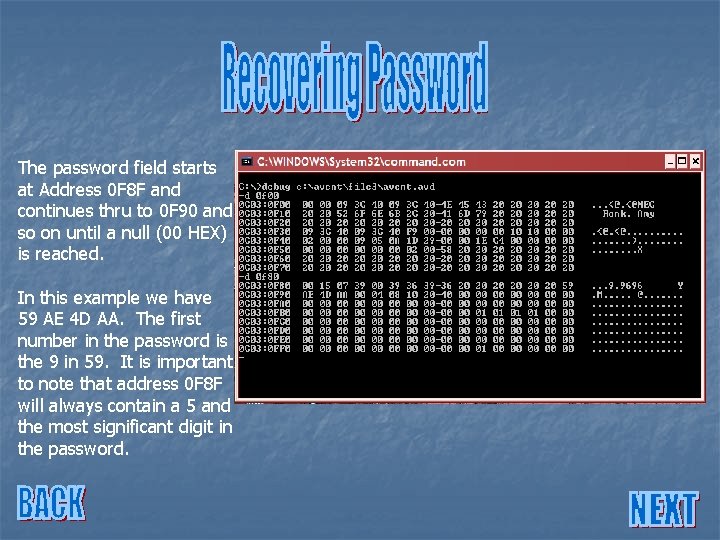
The password field starts at Address 0 F 8 F and continues thru to 0 F 90 and so on until a null (00 HEX) is reached. In this example we have 59 AE 4 D AA. The first number in the password is the 9 in 59. It is important to note that address 0 F 8 F will always contain a 5 and the most significant digit in the password.

The method that we will be using extract the password is called bit filtering or masking. Basically we will be removing some of the bits so we can read the password in binary

We start by converting the Hex values into binary starting with the 9 and working our way down to the end of the string. It is important to convert the numbers into one continuous string.

We start by converting the Hex values into binary starting with the 9 and working our way down to the end of the string. It is important to convert the numbers into one continuous string.

Next, the mask is applied using a 4 -3 -4 -3 pattern, meaning the first 4 bits equals the 1 st digit, the next 3 bits are masked, the next 4 bits equals the 2 nd digit, and so on.

Next, the mask is applied using a 4 -3 -4 -3 pattern, meaning the first 4 bits equals the 1 st digit, the next 3 bits are masked, the next 4 bits equals the 2 nd digit, and so on.

When using this method it is important to work carefully because the more digits that are in the password field the longer the string of binary digits you will be working with.

This presentation comes with this example file and 2 others. They are in zip format. When extracted you will be left with 3 directories, file 1 this example, file 2 another 4 digit example and, file 3 a 5 digit example. In each directory is a text file with the answer. A future supplement will be added to cover 8 -10 digit examples. Hit Escape to exit Written By Joseph O’Neill