Active Directory Windows Server 2008 R 2 Updates













- Slides: 23

Active Directory Windows Server 2008 R 2 Updates 1

Session Objectives And Takeaways Describe Active Directory features in Windows Server 2008 R 2 Discuss the importance of these features to our customers Demonstrate how some of these features will benefit our customers 2

Agenda What’s new in Active Directory for Windows Server 2008 R 2? Power. Shell Cmdlets Active Directory Administrative center Best Practice Analyzer Recycle Bin for AD Managed Service accounts Offline Domain Join Authentication Assurance Health Model and Management Packs 3 Active Directory Tour demonstration Conclusion

Powershell for AD Command line scripting for administrative, configuration and diagnostic tasks Past limitations 30+ command line tools for administering AD are not consistent in their usage Difficult to compose these tools to achieve complex tasks Feature takeaway 4 85+ AD cmdlets for comprehensive AD DS and AD LDS administration and configuration Communicates using Web Service protocols Can be used to manage Windows Server 2008 and 2003 domain controllers, using future AD Web Service download

Powershell Advantages Consistent vocabulary and syntax Predictable discovery Flexible output formatting Cmdlets can be easily composed (pipe) to build complex operations End-to-End manageability with Exchange, Group Policy, etc 5

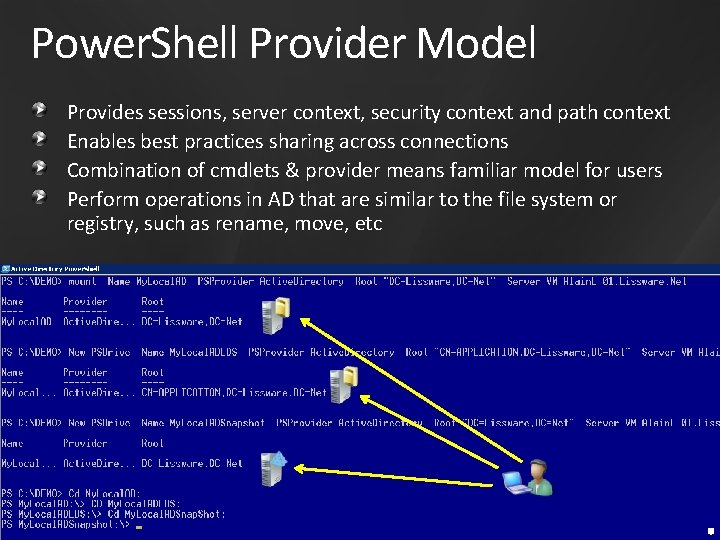
Power. Shell Provider Model Provides sessions, server context, security context and path context Enables best practices sharing across connections Combination of cmdlets & provider means familiar model for users Perform operations in AD that are similar to the file system or registry, such as rename, move, etc 6

Get-Command. Type Cmdlet *-AD* Add-ADComputer. Service. Account Add-ADDomain. Controller. Password. Replication. Policy Add-ADFine. Grained. Password. Policy. Subject Add-ADGroup. Member Add-ADPrincipal. Group. Membership Clear-ADAccount. Expiration Disable-ADAccount Disable-ADOptional. Feature Enable-ADAccount Enable-ADOptional. Feature Get-ADAccount. Authorization. Group Get-ADAccount. Resultant. Password. Replication. Policy Get-ADComputer. Service. Account Get-ADDefault. Domain. Password. Policy Get-ADDomain. Controller. Password. Replication. Policy. Usage Get-ADFine. Grained. Password. Policy. Subject Get-ADForest Get-ADGroup. Member Get-ADObject Get-ADOptional. Feature Get-ADOrganizational. Unit Get-ADPrincipal. Group. Membership Get-ADRoot. DSE 7 Get-ADService. Account Get-ADUser. Resultant. Password. Policy Install-ADService. Account Move-ADDirectory. Server. Operation. Master. Role Move-ADObject New-ADComputer New-ADFine. Grained. Password. Policy New-ADGroup New-ADObject New-ADOrganizational. Unit New-ADService. Account New-ADUser Remove-ADComputer. Service. Account Remove-ADDomain. Controller. Password. Replication. Policy Remove-ADFine. Grained. Password. Policy. Subject Remove-ADGroup. Member Remove-ADObject Remove-ADOrganizational. Unit Remove-ADPrincipal. Group. Membership Remove-ADService. Account Remove-ADUser Rename-ADObject Reset-ADService. Account. Password Restore-ADObject Search-ADAccount Set-ADAccount. Control Set-ADAccount. Expiration Set-ADAccount. Password Set-ADComputer Set-ADDefault. Domain. Password. Policy Set-ADDomain. Mode Set-ADFine. Grained. Password. Policy Set-ADForest. Mode Set-ADGroup Set-ADObject Set-ADOrganizational. Unit Set-ADService. Account Set-ADUser Uninstall-ADService. Account Unlock-ADAccount

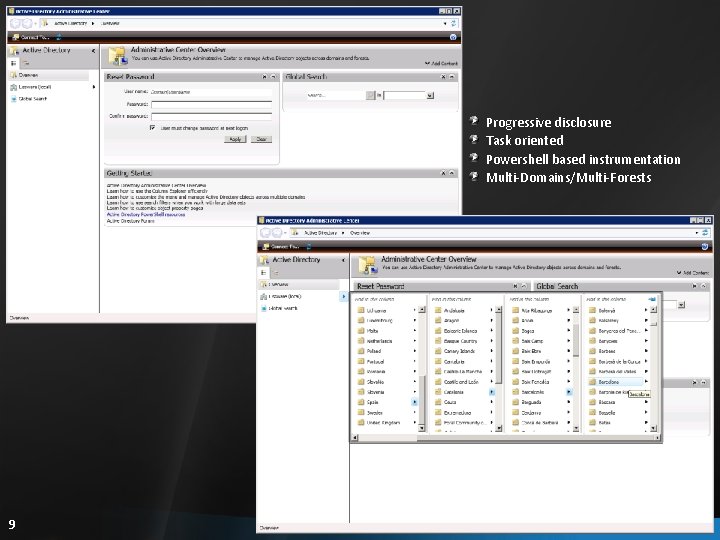
Administrative Center for AD Increase the productivity of IT Pros by providing a scalable, task -oriented UX for managing Active Directory Past limitations Non task-oriented UI causes customer pain Example: resetting user passwords Representation in MMC not scalable for large datasets Feature takeaway Tasks executed through Power. Shell Cmdlets Task oriented administration model, with support for larger datasets Consistency between CLI and UI management capabilities Navigation experience designed to support multi-domain, multi-forest environments 8

Progressive disclosure Task oriented Powershell based instrumentation Multi-Domains/Multi-Forests 9

Best Practice Analyzer Identify deviations from best practices to help our customers better manage their Active Directory deployments Past limitations No easy and automated validation of AD configuration against best practices Feature takeaway Analyzes AD settings that cause most unexpected behavior in customer environments Leverages Power. Shell cmdlets to gather run-time data Makes recommendations in the context of the deployment Available through Server Manager BPA runtime tool 10

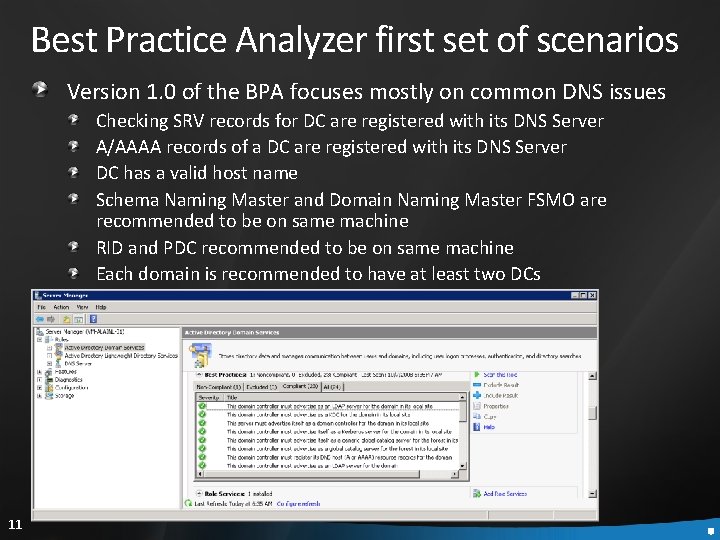
Best Practice Analyzer first set of scenarios Version 1. 0 of the BPA focuses mostly on common DNS issues Checking SRV records for DC are registered with its DNS Server A/AAAA records of a DC are registered with its DNS Server DC has a valid host name Schema Naming Master and Domain Naming Master FSMO are recommended to be on same machine RID and PDC recommended to be on same machine Each domain is recommended to have at least two DCs 11

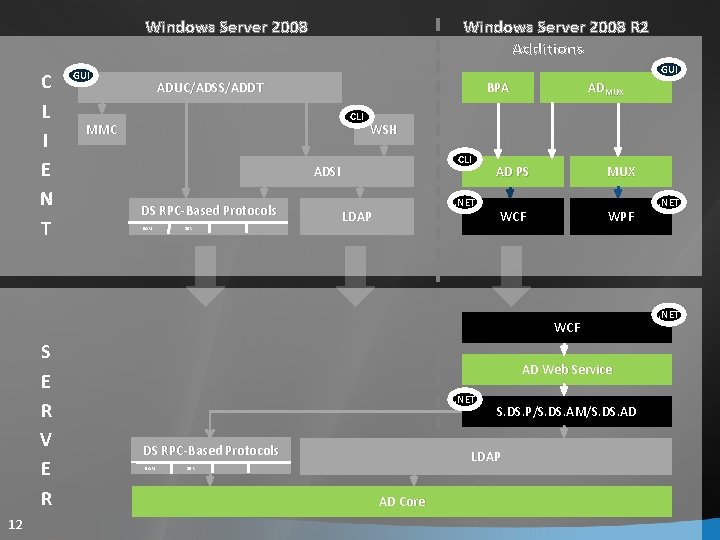
Windows Server 2008 C L I E N T Windows Server 2008 R 2 Additions GUI ADUC/ADSS/ADDT BPA CLI MMC WSH CLI ADSI DS RPC-Based Protocols SAM DSR … ADMUX . NET LDAP AD PS MUX WCF WPF … WCF S E R V E R 12 AD Web Service. NET DS RPC-Based Protocols SAM DSR … . NET S. DS. P/S. DS. AM/S. DS. AD LDAP … AD Core . NET

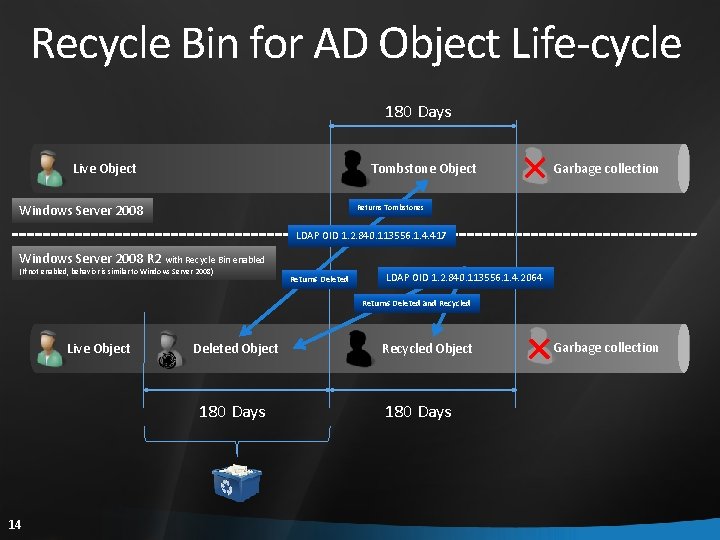
Recycle Bin for AD Customer can undo an accidental deletion in Active Directory Past limitations Accidental object deletion causes business downtime – deleted users cannot logon or access corporate resources Accidental deletions are the number #1 cause of AD DisasterRecovery scenarios Feature takeaway Recycle bin for AD DS and AD LDS objects Feature enabled with a new forest functional level Requires all DCs in the forest to be Windows Server 2008 R 2 DCs For AD LDS, all replicas must be running in a new ‘application mode’

Recycle Bin for AD Object Life-cycle 180 Days Live Object Tombstone Object Windows Server 2008 Garbage collection Returns Tombstones LDAP OID 1. 2. 840. 113556. 1. 4. 417 Windows Server 2008 R 2 with Recycle Bin enabled (If not enabled, behavior is similar to Windows Server 2008) Returns Deleted LDAP OID 1. 2. 840. 113556. 1. 4. 2064 Returns Deleted and Recycled Live Object Deleted Object 180 Days 14 Recycled Object 180 Days Garbage collection

Managed Service Accounts Simple management of service accounts Past limitations Management of individual accounts for services is cumbersome Periodic maintenance often causes outages Example: resetting service account password Feature takeaway A manageable solution that addresses isolation needs for services Better SPN management in Win 7 Domain Functional Mode Lower TCO from reduced service outages (for manual password resets and related issues) One Managed Service Account per Service per box No human intervention for password management!

Offline Domain Join Enable easier provisioning of machines in the data center Past limitations Reboot needed after domain join Inability to prepare the machine to be domain joined while offline Feature takeaway Ability to pre-provision machine accounts in the domain to prepare OS images for mass deployment Machines are domain joined on initial boot Reduces steps and time needed to deploy in the data center

Authentication Assurance Applications can control resource access based on authentication strength and method Past limitations Customers cannot use authentication type or authentication strength to protect corporate data Example: control access to resources based on claims such as use of smartcard for logon or the certificate used 2048 bit encryption Feature takeaway Administrators can map various properties, including authentication type and authentication strength to an identity Based on information during authentication, these identities are added to Kerberos tickets for use by applications Feature is enabled with a new domain functional level All domain controllers in the domain need to be Window Server 2008 R 2 DCs

Health Model Enable IT administrators to better diagnose and resolve Active Directory issues Past limitations Diagnostic information is incomplete and inconsistent Feature takeaway Continued investment towards completing the health model A single authoritative source for information used in Management Packs, Best Practice Analyzer and online documentation 18

Management Pack Provide proactive monitoring of availability and performance of Active Directory Past limitations Current management pack lacks support for Windows Server 2008 and MOM 2007 Feature takeaway Support for Windows Server 2008 domain controllers Multiple replication latency groups Ability to monitor multiple forests from a single management group Management pack for MOM 2007

The journey to Windows Server 2008 R 2 Upgrading to Windows 7 client while keeping existing servers, you can use: Off-line domain join Once AD Web-service is available for existing servers, if you upgrade to Windows 7 client, you can use: AD Powershell and ADAC with all your servers Upgrading to Windows 7 client while installing one or more Windows Server 2008 R 2 (one per domain), you can use: Managed service account If you change the domain functional level to Windows Server 2008 R 2, you can use: Authentication Assurance Managed service account with an enhanced SPN management experience If you change the Forest functional level to Windows Server 2008 R 2, you can use: AD Recycle-bin

Related Content Tuesday, November 4 th Identity Lifecycle Manager 2 (Part 1): Empowering users with self-service identity management solutions 10: 45 -12: 00 pm Windows Server 2008 R 2 Active Directory: What's Coming Up? 1: 30 -2: 45 pm Chalk & Talk: Windows Server Active Directory (IDA 03 -IS) 3: 15 -4: 30 pm Windows Vista PKI Enhancement in Windows 7 and Windows Server 2008 R 2 3: 15 -4: 30 pm Going Virtual with the Intelligent Application Gateway and a Sneak Peak at the Future! 3: 15 -4: 30 pm Forefront Security for Exchange Server: Advanced Spam and Anti. Malware Scanning Today and Tomorrow 5: 00 -6: 15 pm Active Directory Rights Management Services (AD RMS) - End to End 5: 00 -6: 15 pm Wednesday, November 5 th Microsoft Forefront Security for Share. Point: The Next Generation of Collaboration Security 9: 00 -10: 15 am Ask The Experts 12: 15 -12: 45 pm Identity Lifecycle Manager 2 (Part 2): Expressing and enforcing business policy 1: 30 -2: 45 pm Introduction to Microsoft Forefront Codename Stirling 1: 30 -2: 45 pm Connecting Active Directory to Microsoft Cloud Services 3: 45 -5: 00 pm Hybrid Messaging Security for Exchange Server 3: 45 -5: 00 pm Using Active Directory Domain Services for Linux Servers 5: 30 -6: 45 pm Visit the Identity & Security booths for a detailed guide to activities at Tech. Ed EMEA

Related Content Thursday, November 6 th Windows Server 2008 Active Directory Best Practices (IDA 08) 8: 30 -9: 45 pm Notes from the Field: Deploying Microsoft Identity Lifecycle Manager 2007 Certificate Management 10: 15 -11: 30 am Ask The Experts 12: 15 -12: 45 pm Successful deployment tips for Security and Strong Authentication 1: 00 -2: 15 pm Using Network Access Protection (NAP) in combination with FCS 1: 00 -2: 15 pm Identity Lifecycle Manager 2 (Part 3): Extensibility and provisioning with ILM 2 2: 40 -3: 55 pm Universal sign-in utilizing AD, Card. Space and federation technologies: How to sign in any user, in any kind of application, in any scenario, using 'Zermatt' and claims-based identity 4: 20 -5: 35 pm Windows Server 2008 R 2 Active Directory: What’s Coming Up? (IDA 309–REPEAT) 6: 00 -7: 15 pm Friday, November 7 th Active Directory Information Security - Where is the boundary? 9: 00 -10: 15 am A Technical Preview and Deep Dive of Next Generation ISA Server 9: 00 -10: 15 am A DS Geek's Notes from the Field - Active Directory Uncovered 10: 45 -12: 00 pm Infrastructure services for SOA security and federation: 'Geneva' Security Token Services 3: 15 -4: 30 pm Visit the Identity & Security booths for a detailed guide to activities at Tech. Ed EMEA 22

© 2008 Microsoft Corporation. All rights reserved. Microsoft, Windows Vista and other product names are or may be registered trademarks and/or trademarks in the U. S. and/or other countries. The information herein is for informational purposes only and represents the current view of Microsoft Corporation as of the date of this presentation. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information provided after the date of this presentation. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION. 23