Active Directory Domain Services AD DS Outline Windows









- Slides: 23

Active Directory Domain Services (AD DS)

Outline • Windows security mechanisms • Policy • Active Directory • Benefits • Architectural Concepts • Group Policy 2

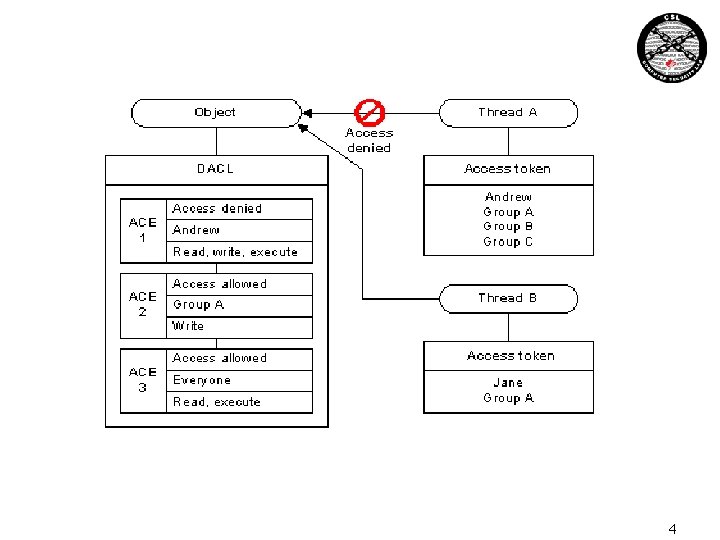
Securable Objects • A securable object is an object that can have a security descriptor. • A discretionary access control list (DACL) identifies the trustees that are allowed or denied access to a securable object. • A system access control list (SACL) enables administrators to log attempts to access a secured object. 3

4

MANY Security Relevant Registry Keys • HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrent. VersionRun • For each program you want to start automatically create a new string value using a descriptive name, and set the value of the string to the program executable. • HKEY_LOCAL_MACHINESoftwareMicrosoftWindows Current. VersionRun. Services • These keys are for background services such as remote registry service and are run only once per boot • HKLMSoftwareMicrosoftWindows NTCurrent. Version • The Current. Version subkey stores configuration data for programs designed to run on the most current version of Windows 2000 installed on the computer. 5

Directory Service Benefits • • • Centralization Scalability Standardization Extensibility Security Abstraction of Physical Network 6

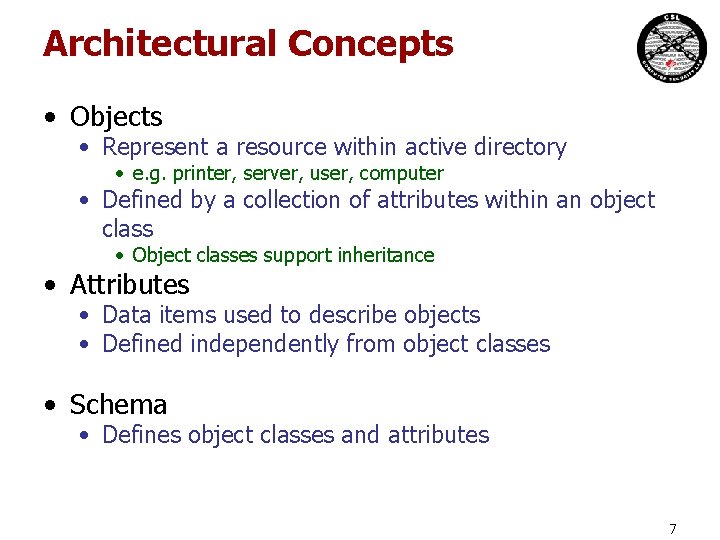
Architectural Concepts • Objects • Represent a resource within active directory • e. g. printer, server, user, computer • Defined by a collection of attributes within an object class • Object classes support inheritance • Attributes • Data items used to describe objects • Defined independently from object classes • Schema • Defines object classes and attributes 7

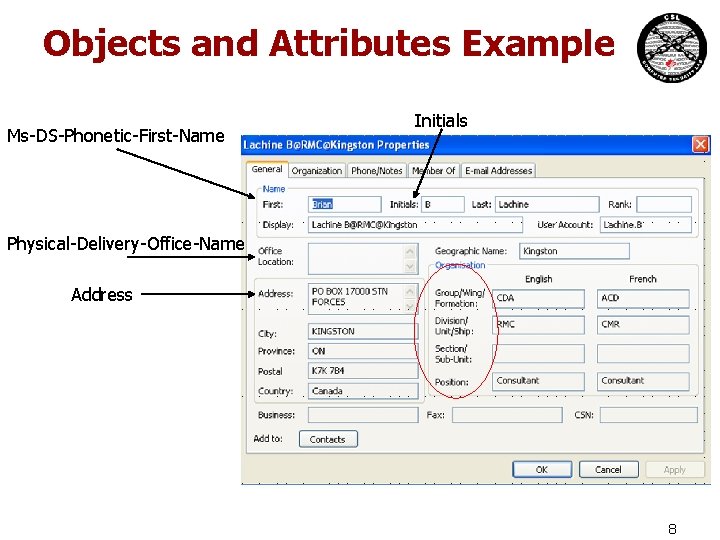
Objects and Attributes Example Ms-DS-Phonetic-First-Name Initials Physical-Delivery-Office-Name Address 8

Domains and DNS • DNS is fundamental to the operation of active directory domain services • Location of resources such as computers, servers, domain controllers • Shared naming conventions • Normally different internal and external DNS namespaces • Some organizations further integrate DNS directly into active directory • DNS zones stored in Active Directory • DNS multi-master replication model • Based on Active Directory replication • Referred to as Active Directory-Integrated DNS Zones 9

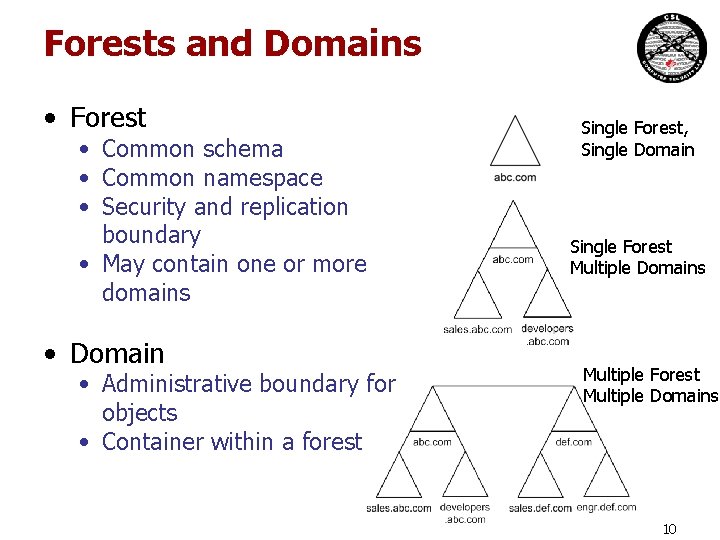
Forests and Domains • Forest • Common schema • Common namespace • Security and replication boundary • May contain one or more domains • Domain • Administrative boundary for objects • Container within a forest Single Forest, Single Domain Single Forest Multiple Domains Multiple Forest Multiple Domains 10

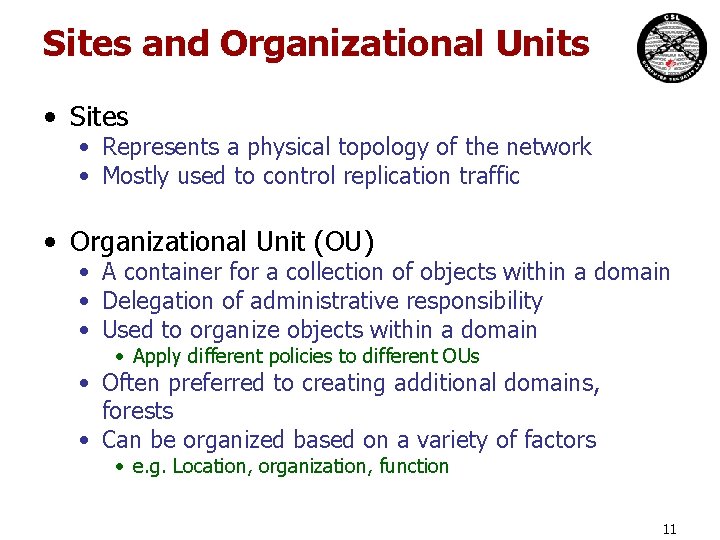
Sites and Organizational Units • Sites • Represents a physical topology of the network • Mostly used to control replication traffic • Organizational Unit (OU) • A container for a collection of objects within a domain • Delegation of administrative responsibility • Used to organize objects within a domain • Apply different policies to different OUs • Often preferred to creating additional domains, forests • Can be organized based on a variety of factors • e. g. Location, organization, function 11

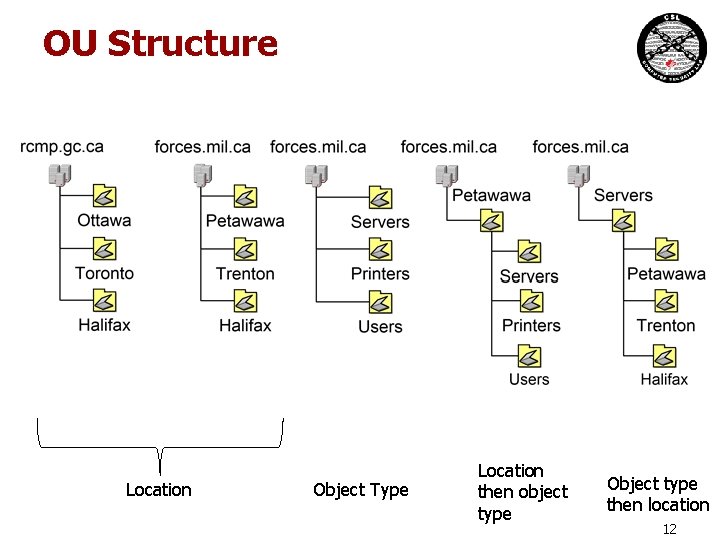
OU Structure Location Object Type Location then object type Object type then location 12

Group Policy • Group Policy • Enables configuration of objects within an Active Directory domain • Thousands of settings may be configured • e. g. security, look and feel, performance, application specific • Configurable locally • Local Group Policy (gpedit. msc) • Configurable within Active Directory • Active Directory-Based Group Policy (gpmc. msc) • Group Policy Objects have two halves or nodes • User • Computer • Local vs Active Directory based Group Policy 13

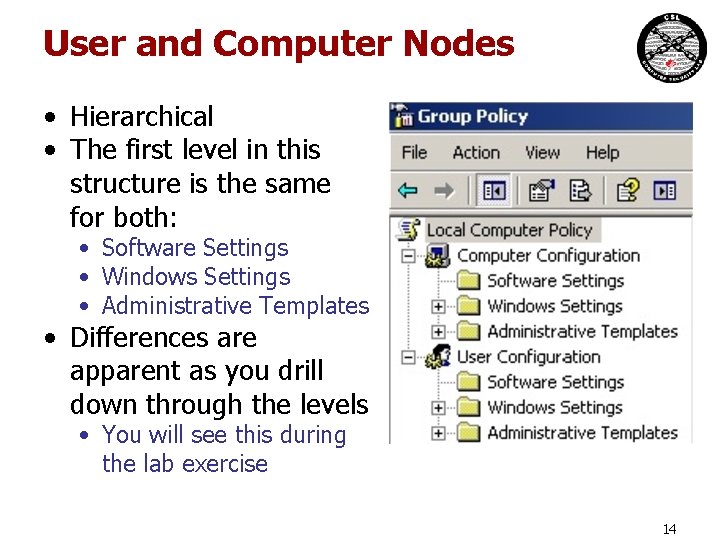
User and Computer Nodes • Hierarchical • The first level in this structure is the same for both: • Software Settings • Windows Settings • Administrative Templates • Differences are apparent as you drill down through the levels • You will see this during the lab exercise 14

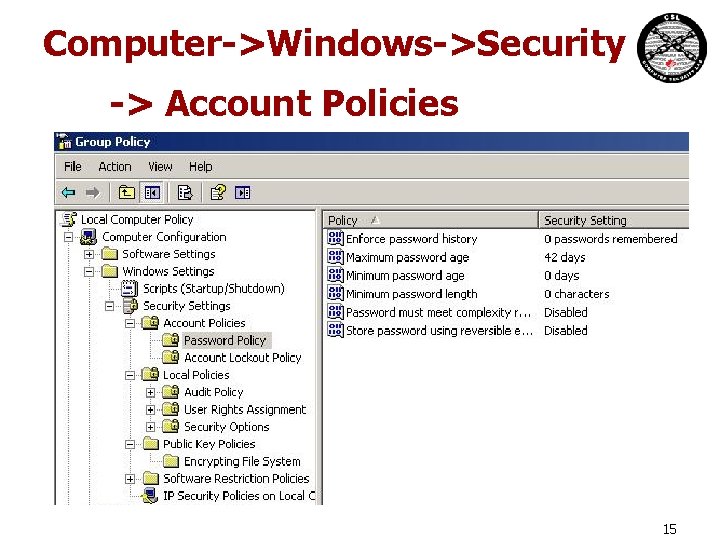
Computer->Windows->Security -> Account Policies 15

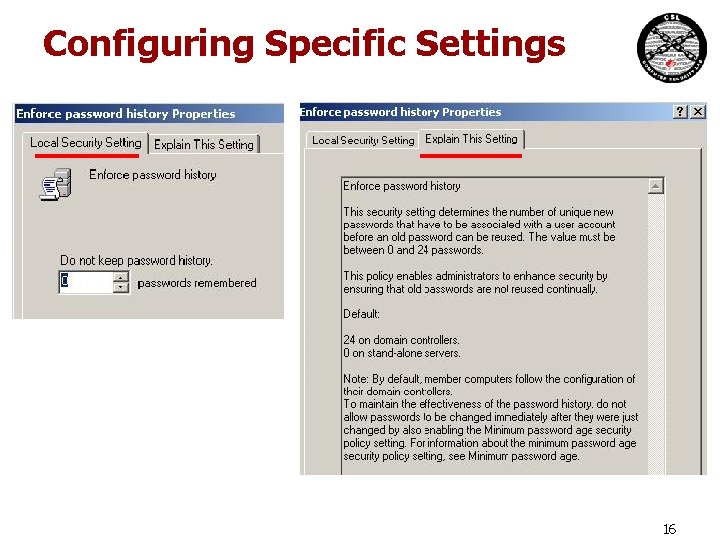
Configuring Specific Settings 16

Configuration Options • Will normally see enable, disable and/or not configured options for each setting • Enabled • Depending on the specific setting, may have unique values, such as • groups • numerical value • Disabled • Not Configured • Means either do nothing or the OS default setting is applied • Be mindful of double negatives in the wording • do not allow …………… -> enable or disable 17

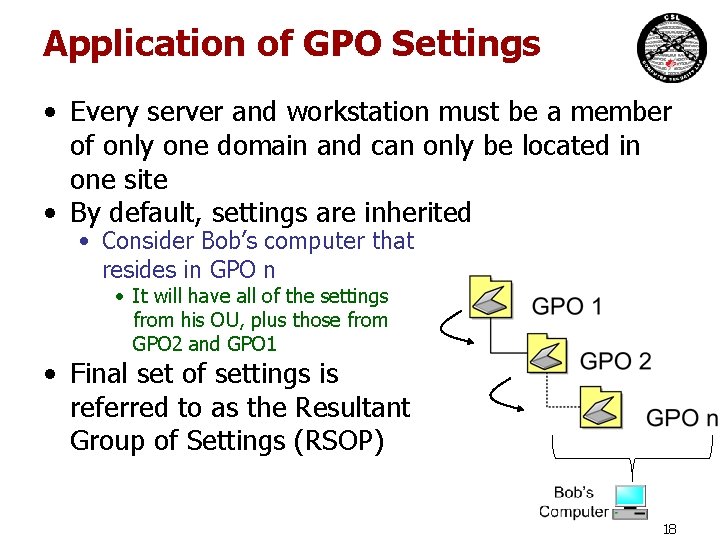
Application of GPO Settings • Every server and workstation must be a member of only one domain and can only be located in one site • By default, settings are inherited • Consider Bob’s computer that resides in GPO n • It will have all of the settings from his OU, plus those from GPO 2 and GPO 1 • Final set of settings is referred to as the Resultant Group of Settings (RSOP) 18

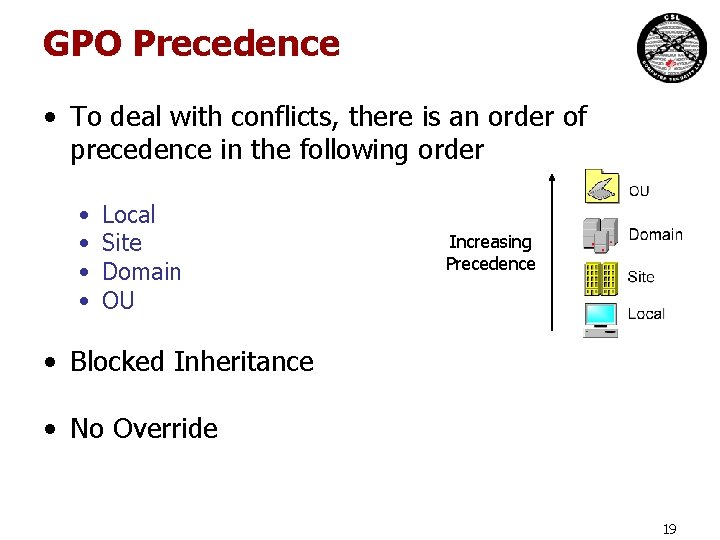
GPO Precedence • To deal with conflicts, there is an order of precedence in the following order • • Local Site Domain OU Increasing Precedence • Blocked Inheritance • No Override 19

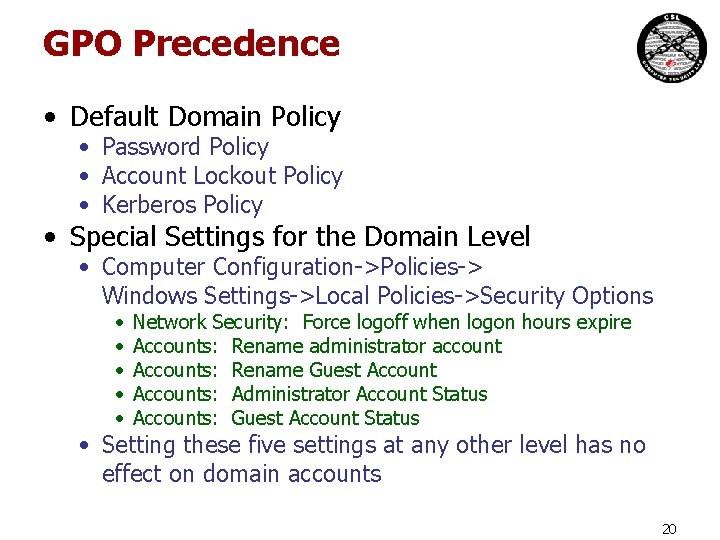
GPO Precedence • Default Domain Policy • Password Policy • Account Lockout Policy • Kerberos Policy • Special Settings for the Domain Level • Computer Configuration->Policies-> Windows Settings->Local Policies->Security Options • • • Network Security: Force logoff when logon hours expire Accounts: Rename administrator account Accounts: Rename Guest Accounts: Administrator Account Status Accounts: Guest Account Status • Setting these five settings at any other level has no effect on domain accounts 20

Questions? 21

References 1. 2. 3. 4. 5. 6. 7. 8. Brian Lachine, SCINS Operating System Notes, 2013. Moskowitz, Jeremy, Group Policy, Security and the Managed Desktop, 2010 Price, Brad & John, Mastering Active Directory for Windows Server 2008, 2008. Allen, Robbie, Active Directory Cookbook, 2 nd Edition, 2006 Glenn, Walter, Windows Server 2003 Active Directory and Network Infrastructure, 2004 Active Directory Schema - http: //msdn. microsoft. com/enus/library/windows/desktop/ms 675085%28 v=vs. 85%29. aspx Group Policy - http: //technet. microsoft. com/enus/windowsserver/bb 310732. aspx Group Policy Reference – Spreadsheets, http: //www. microsoft. com/enus/download/details. aspx? id=25250 22

8. Microsoft Security Compliance Manager http: //technet. microsoft. com/en-us/library/cc 677002. aspx 9. Microsoft Threats and Countermeasures Guide http: //technet. microsoft. com/enus/library/hh 125921(v=ws. 10). aspx 10. CIS Benchmarks, http: //www. cisecurity. org/ 23