ACCESS MATRIX IMPLEMENTATION AND COMPARISON By Rushabh Dharwadkar

ACCESS MATRIX IMPLEMENTATION AND COMPARISON By: Rushabh Dharwadkar Roll no: 411108 TE COMP

ACCESS MATRIX • In an Access matrix, there are columns which represent different system resources and rows representing different protection domains. Entries within the matrix indicate what access that domain has to that resource. 2
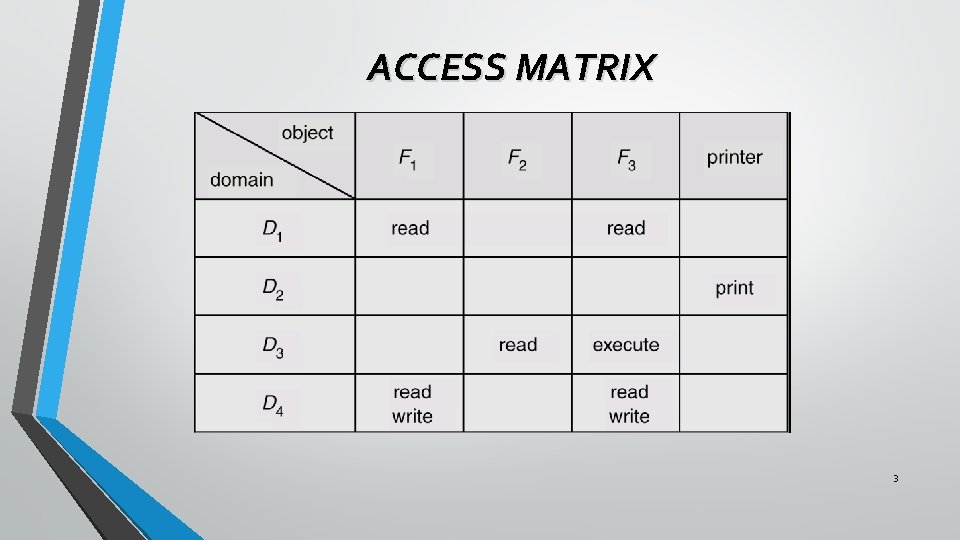
ACCESS MATRIX 3

IMPLEMENTATION OF ACCESS MATRIX There four ways listed below in which Access Matrix can be implemented effectively. üGlobal Table üAccess Lists for Objects üCapability Lists for Domains üLock-Key Mechanism 4

GLOBAL TABLE This is the simplest implementation of the access matrix. Contains a set of ordered triples <domain, object, rights-set> Whenever an operation M is executed on an object Oj within domain Di the global table is searched for a triple <Di, Oj, Rk > where M Є Rk If this triple is found, the operation is allowed to continue or else an exception is raised. 5

GLOBAL TABLE Ø Drawbacks • Table size is quite large so it cannot be kept in main memory so additional I/O is needed • Virtual Memory techniques are used for managing this table • Difficult to take advantage of special groupings I. e. If at all everyone can read a particular object, this object must have a separate entry in every domain. 6

ACCESS LISTS FOR OBJECTS When an operation M on an object Oj is attempted in domain Di we search the access list for object Oj , looking for an entry < Di , Rk > where M Є Rk lookin if the entry is found, we allow the operation , if it is not we check the default set, we allow the access. Otherwise the access is denied, and an exception condition occurs 7

CAPABILITY LISTS FOR DOMAINS • Capability can be secure pointer to object • • • OS controls who can acquire references requires that pointers be opaque natural model for type-safe languages 8

CAPABILITY LISTS FOR DOMAINS • Here we associate each row with each domain • They are a kind of secure pointers • An object is often represented by its physical name or address, called a Capability • To execute an operation M on object Oj the process executes the operation M, specifying the capability (or pointer) for Oj as a parameter • Simple possession of the capability means that the access is allowed 9

CAPABILITY LISTS FOR DOMAINS Capabilities are usually distinguished from each other in two ways. . Each object has a tag to denote whether it’s a capability or accessible data • Tags not directly accessible by application programs • Hardware/firmware support used to enforce this restriction • More than 1 bits used as a distinguishing attribute • Hardware can distinguish integers , characters and so on and other values 10
CAPABILITY LISTS FOR DOMAINS Address space associated with a program can b split into 2 parts Part 1 Part 2 • Is accessible to the program and contains its normal instructions • Contains the capability list and is accessible only by the OS ……. Segmented memory space is useful in this approach 11

LOCK-KEY MECHANISM • Compromise between access lists and capability lists • Each object has a list of unique bit patterns called locks • Each domain has a list of unique bit patterns called keys • List of keys for domain must b managed by the OS • Users are not allowed to examine or modify keys 12
COMPARISON 1. Global table • Simple, but the table can b large and often cannot take advantage of special groupings of objects or domains • Access lists correspond directly to the needs of users • Determining set access rights for each domain is difficult • Every access to the object must be checked, requiring a search of access list in large systems with long access lists, this is time consuming 13

COMPARISON 2. Capability Lists • • • Do not correspond directly to the needs of users Useful for localizing information for a given process Process attempting access must present a capability for that access Protection system needs to verify if the capability is valid Revocation of capabilities inefficient 14

COMPARISON 3. Lock-key mechanism • Compromise between access lists and capability lists • Effective and flexible depending on the length of keys • Keys passed freely from domain to domain • Access privileges effectively revoked by changing some of the locks associated with the objects 15
COMPARISON Most systems use a combination of access lists and capabilities • When a process tries to access an object, the access list is searched • If access is denied an exception occurs • Or else a capability is created and attached to the process • Capability is used to demonstrate swiftly that access is allowed • After last access capability is destroyed 16

Questions… 1. Explain access matrix as model of protection 2. How can a access matrix be implemented? 3. List and explain drawbacks of lock-key mechanism? 4. What are the disadvantages of capability lists? 17

Reference… • Operating Systems Concepts 8 th edition (Galvin) • Page no 603 -605 18

Thank u 19
- Slides: 19