Access Control Solution for Transportation and Logistics Acsys











- Slides: 25

Access Control Solution for Transportation and Logistics Acsys Technologies Company Ltd EN 1303(G 5)

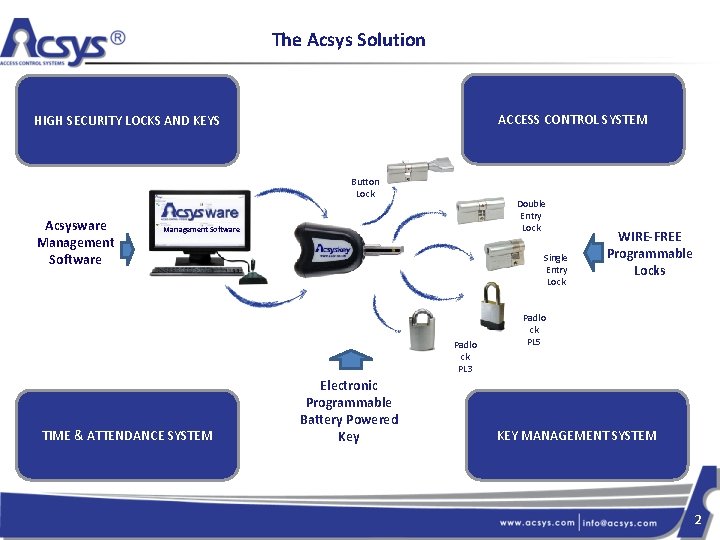
The Acsys Solution ACCESS CONTROL SYSTEM HIGH SECURITY LOCKS AND KEYS Button Lock Acsysware Management Software Double Entry Lock Management Software Single Entry Lock Padlo ck PL 3 TIME & ATTENDANCE SYSTEM Electronic Programmable Battery Powered Key WIRE-FREE Programmable Locks Padlo ck PL 5 KEY MANAGEMENT SYSTEM 2

The Acsys Solution • The Acsyslock and Acsyskey are both electronically programmable using the Acsysware Management Software. The Communication between locks/keys and software is Secured using AES 128 bit Encryption. • The Acsyskey is IMPOSSIBLE to copy/duplicate/read or corrupt, and can be supplied with an RFID tag • The Acsyslocks are IMPOSSIBLE to pick, bump or demagnetize and is protected with anti-drilling safeguards making the unauthorized removal lengthy and uncertain • 1 Key can be programmed to open up to 100, 000 doors/padlocks • The access times and dates of every key can be different for every lock • Usual Lost/stolen keys problems are solved by making keys “Time-restricted”, by issuing KEYPAD keys and because Acsys allows blacklisting of keys in locks. • Embedded memory in both lock and key logs the last 1000 accesses by Time/Date/User ID which can be downloaded/viewed/exported on the Acsysware Management Software. • No wiring/maintenance required as the sole power source of the system is the key, also making the locks easy to place and replace in case of architectural/design changes. • As there are no batteries in the lock, all lock formats are available including Padlocks giving the user total control over outside (gates, storage, car parks) and inside (front door, inside doors) • Keys can be programmed through USB, through VPN/Intranet on the IP Programmer, and through 3 G on a laptop computer making Access Rights Distribution controlled, secured as well as convenient. • Every user is identified on the software by picture ID, name, and all relevant contacts making the ownership of the key easy to verify • The Acsys solution is all of the following : • Access Control system = decide who goes where and when • Key Management system= add/remove/edit/delete any keys/locks/users from the system at any time • Time & Attendance system = verify who went where and when • Total Access solution for inside/outside/multi-site 3

4 4

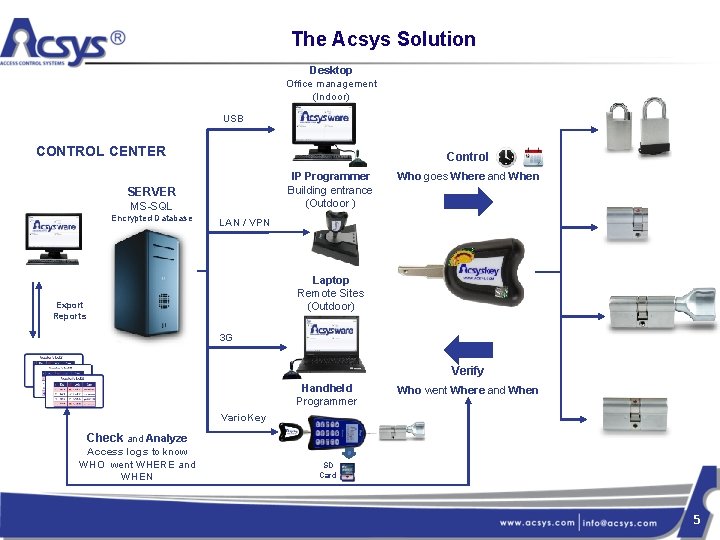
The Acsys Solution Desktop Office management (Indoor) USB CONTROL CENTER Control IP Programmer Building entrance (Outdoor ) SERVER MS-SQL Encrypted Database Who goes Where and When LAN / VPN Laptop Remote Sites (Outdoor) Export Reports 3 G Verify Handheld Programmer Who went Where and When Vario. Key Check and Analyze Access logs to know WHO went WHERE and WHEN SD Card 5

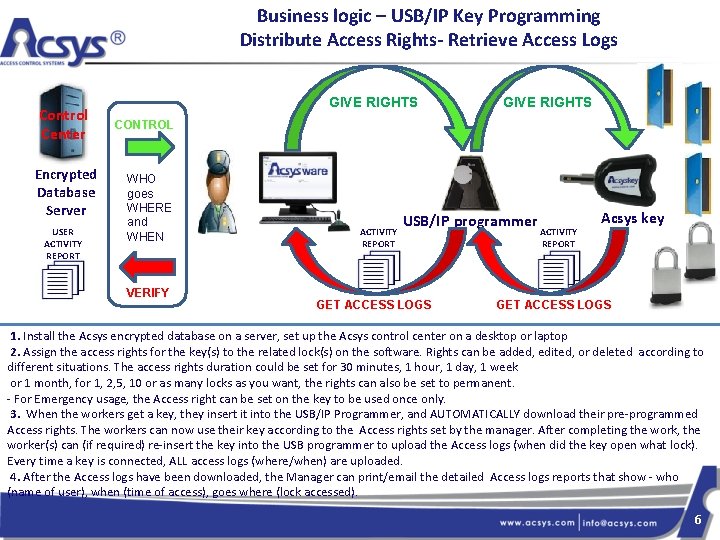
Business logic – USB/IP Key Programming Distribute Access Rights- Retrieve Access Logs Control Center Encrypted Database Server USER ACTIVITY REPORT GIVE RIGHTS CONTROL WHO goes WHERE and WHEN VERIFY ACTIVITY REPORT USB/IP programmer GET ACCESS LOGS ACTIVITY REPORT Acsys key GET ACCESS LOGS 1. Install the Acsys encrypted database on a server, set up the Acsys control center on a desktop or laptop 2. Assign the access rights for the key(s) to the related lock(s) on the software. Rights can be added, edited, or deleted according to different situations. The access rights duration could be set for 30 minutes, 1 hour, 1 day, 1 week or 1 month, for 1, 2, 5, 10 or as many locks as you want, the rights can also be set to permanent. - For Emergency usage, the Access right can be set on the key to be used once only. 3. When the workers get a key, they insert it into the USB/IP Programmer, and AUTOMATICALLY download their pre-programmed Access rights. The workers can now use their key according to the Access rights set by the manager. After completing the work, the worker(s) can (if required) re-insert the key into the USB programmer to upload the Access logs (when did the key open what lock). Every time a key is connected, ALL access logs (where/when) are uploaded. 4. After the Access logs have been downloaded, the Manager can print/email the detailed Access logs reports that show - who (name of user), when (time of access), goes where (lock accessed). 6

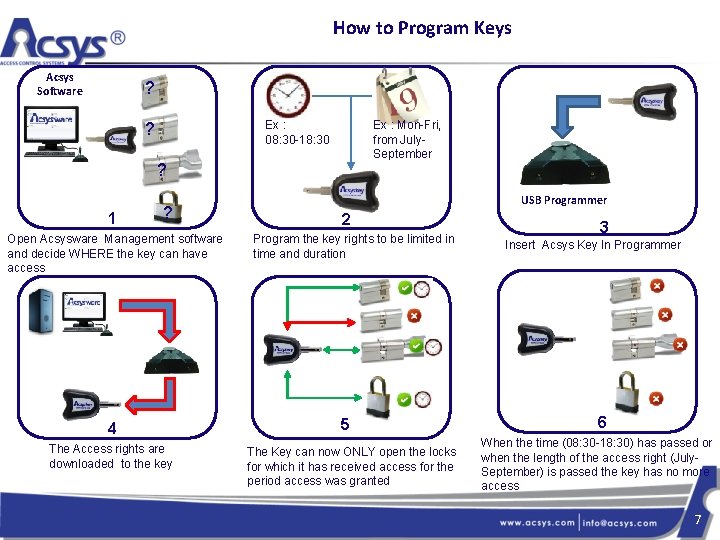
How to Program Keys Acsys Software ? Ex : 08: 30 -18: 30 ? Ex : Mon-Fri, from July. September ? 1 ? Open Acsysware Management software and decide WHERE the key can have access 4 The Access rights are downloaded to the key USB Programmer 2 Program the key rights to be limited in time and duration 5 The Key can now ONLY open the locks for which it has received access for the period access was granted 3 Insert Acsys Key In Programmer 6 When the time (08: 30 -18: 30) has passed or when the length of the access right (July. September) is passed the key has no more access 7

Acsys Technologies Solutions for the Logistic and Transportation Industry 8

Known Problems in the Logistics Industry PROBLEMS • • With Mechanical locks or Padlocks, you can’t control or record before Departure: • IF the Truck or Container was locked and by who • When the truck or the container was reopened During Transportation Mechanical locks or padlocks are at a disadvantage because : • It is easy to open locks when the shipment is under way • Because keys can be copied, even if there is a theft, the driver can argue that its someone else, and there is no way to know if someone opened it or not during transport. • Mechanical lock and padlocks are easy to drill, easy to bump, easy to pick…and if there is no proof of ‘Break and entry’ the insurance claim is an issue • Mechanical/Series Keys do not give the Operator Key Control, which is of concern with Thefts, as lost keys can invalidate an Insurance Policy SOLUTIONS • • • Acsys keys can not be copied One key can open 100, 000 locks The Certifying Authority can Decide in advance who can open which lock at what time or how many times they can open it Control and verify which locks were opened by downloading the information from the locks and keys (Last 1000 events-which door/which day/what time) High security locks and that cannot be picked, drilled or bumped Wire free! Easy installation! Time & Attendance function and you can control who goes where and when Program different keys to have access on various padlocks on different locations RFID capable keys that can be programmed to operate a Card System (RFID, POS , Mifare 1) and; Acsys is the only company who can provide the most secure padlock in the World 9

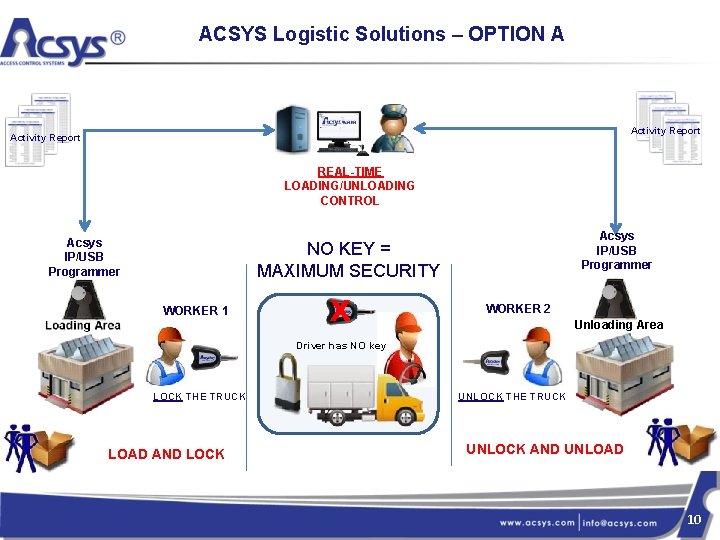
ACSYS Logistic Solutions – OPTION A Activity Report REAL-TIME LOADING/UNLOADING CONTROL Acsys IP/USB Programmer NO KEY = MAXIMUM SECURITY WORKER 1 x WORKER 2 Unloading Area Driver has NO key LOCK THE TRUCK LOAD AND LOCK UNLOCK THE TRUCK UNLOCK AND UNLOAD 10

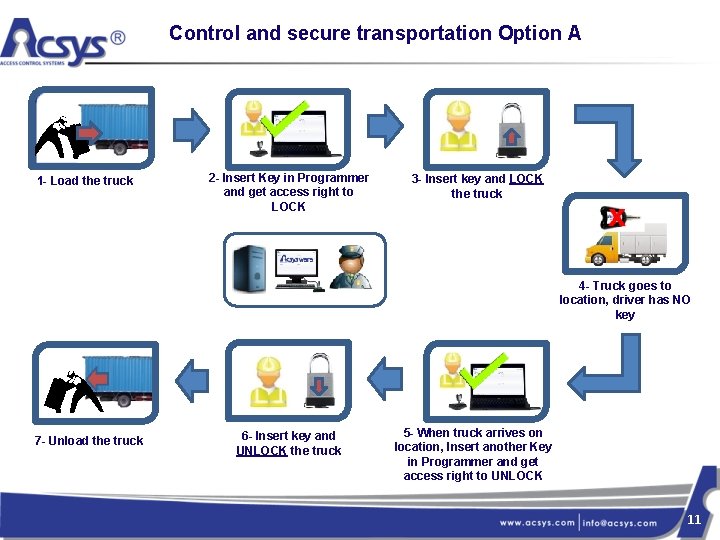
Control and secure transportation Option A 1 - Load the truck 2 - Insert Key in Programmer and get access right to LOCK 3 - Insert key and LOCK the truck 4 - Truck goes to location, driver has NO key 7 - Unload the truck 6 - Insert key and UNLOCK the truck 5 - When truck arrives on location, Insert another Key in Programmer and get access right to UNLOCK 11

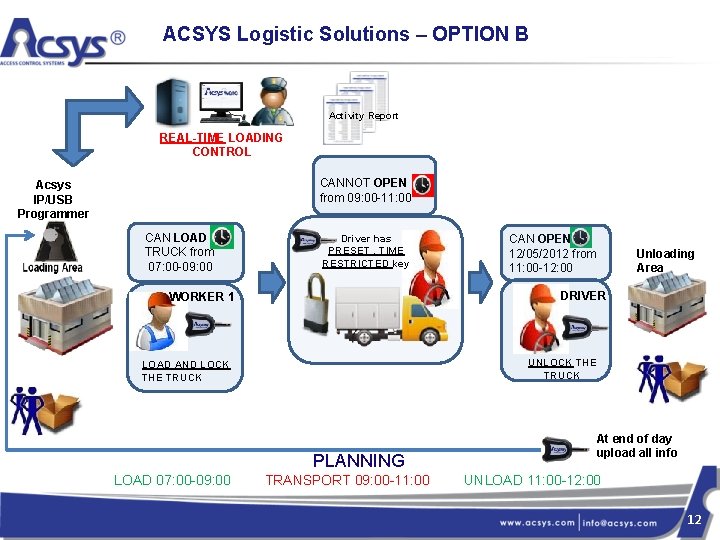
ACSYS Logistic Solutions – OPTION B Activity Report REAL-TIME LOADING CONTROL CANNOT OPEN from 09: 00 -11: 00 Acsys IP/USB Programmer CAN LOAD TRUCK from 07: 00 -09: 00 Driver has PRESET , TIME RESTRICTED key Unloading Area DRIVER WORKER 1 UNLOCK THE TRUCK LOAD AND LOCK THE TRUCK PLANNING LOAD 07: 00 -09: 00 CAN OPEN 12/05/2012 from 11: 00 -12: 00 TRANSPORT 09: 00 -11: 00 At end of day upload all info UNLOAD 11: 00 -12: 00 12

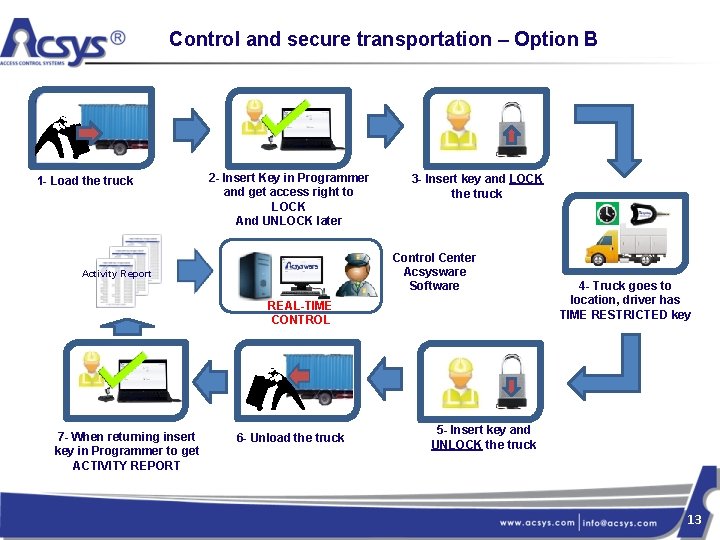
Control and secure transportation – Option B 1 - Load the truck 2 - Insert Key in Programmer and get access right to LOCK And UNLOCK later 3 - Insert key and LOCK the truck Control Center Acsysware Software Activity Report REAL-TIME CONTROL 7 - When returning insert key in Programmer to get ACTIVITY REPORT 6 - Unload the truck 4 - Truck goes to location, driver has TIME RESTRICTED key 5 - Insert key and UNLOCK the truck 13

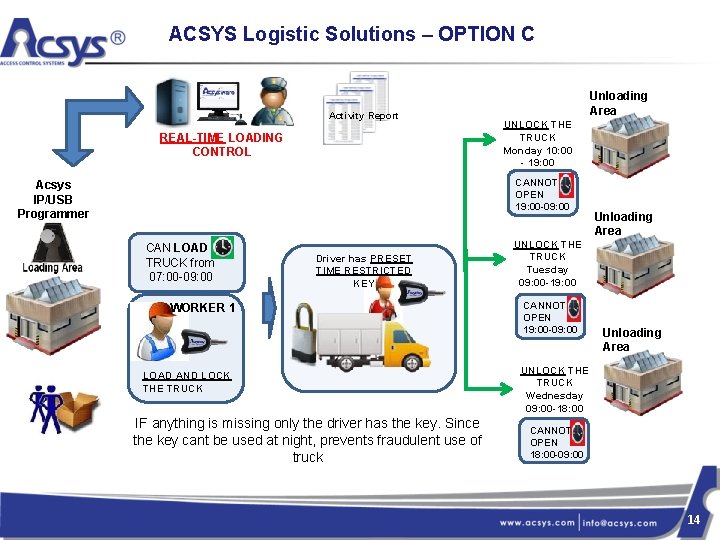
ACSYS Logistic Solutions – OPTION C Activity Report REAL-TIME LOADING CONTROL Unloading Area UNLOCK THE TRUCK Monday 10: 00 - 19: 00 CANNOT OPEN 19: 00 -09: 00 Acsys IP/USB Programmer CAN LOAD TRUCK from 07: 00 -09: 00 Driver has PRESET TIME RESTRICTED KEY WORKER 1 LOAD AND LOCK THE TRUCK IF anything is missing only the driver has the key. Since the key cant be used at night, prevents fraudulent use of truck Unloading Area UNLOCK THE TRUCK Tuesday 09: 00 -19: 00 CANNOT OPEN 19: 00 -09: 00 Unloading Area UNLOCK THE TRUCK Wednesday 09: 00 -18: 00 CANNOT OPEN 18: 00 -09: 00 14

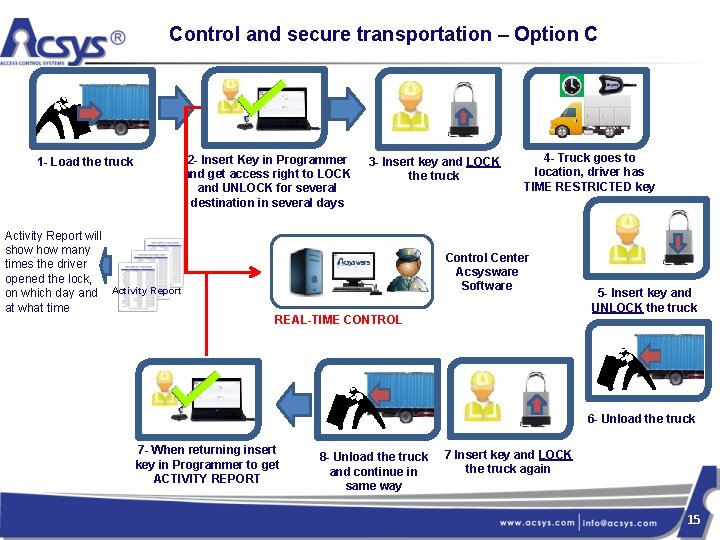
Control and secure transportation – Option C 2 - Insert Key in Programmer and get access right to LOCK and UNLOCK for several destination in several days 1 - Load the truck Activity Report will show many times the driver opened the lock, on which day and Activity Report at what time 3 - Insert key and LOCK the truck 4 - Truck goes to location, driver has TIME RESTRICTED key Control Center Acsysware Software REAL-TIME CONTROL 5 - Insert key and UNLOCK the truck 6 - Unload the truck 7 - When returning insert key in Programmer to get ACTIVITY REPORT 8 - Unload the truck and continue in same way 7 Insert key and LOCK the truck again 15

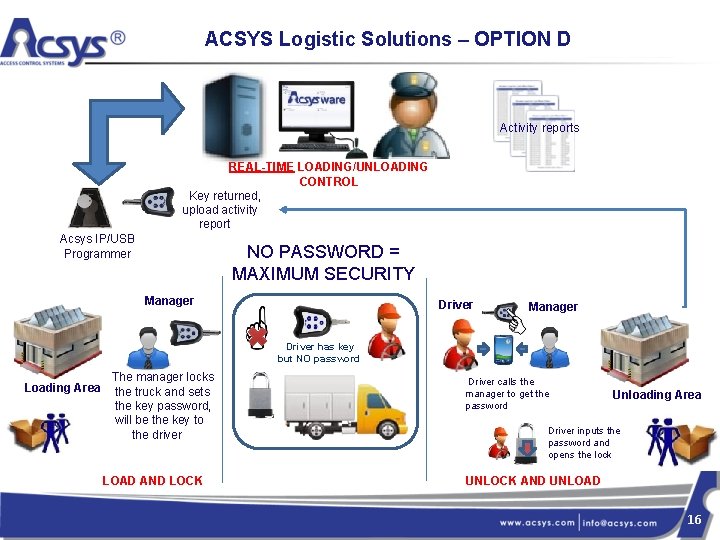
ACSYS Logistic Solutions – OPTION D Activity reports REAL-TIME LOADING/UNLOADING CONTROL Key returned, upload activity report Acsys IP/USB Programmer NO PASSWORD = MAXIMUM SECURITY Manager Driver has key but NO password Loading Area The manager locks the truck and sets the key password, will be the key to the driver LOAD AND LOCK Driver calls the manager to get the password Unloading Area Driver inputs the password and opens the lock UNLOCK AND UNLOAD 16

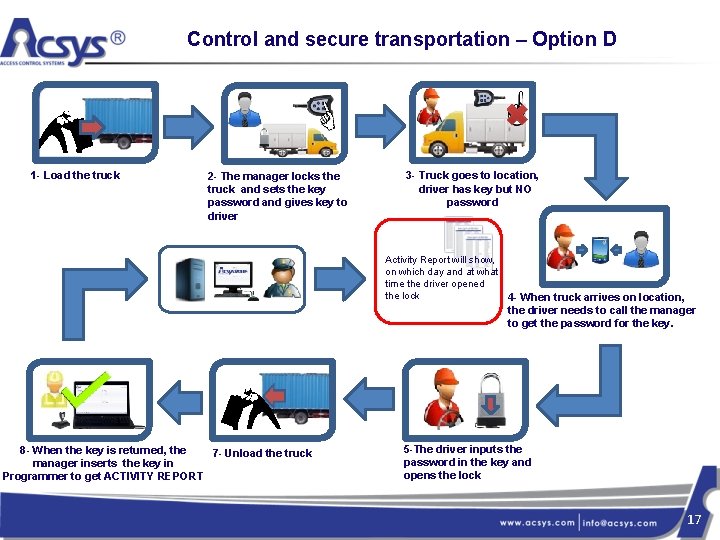
Control and secure transportation – Option D 1 - Load the truck 2 - The manager locks the truck and sets the key password and gives key to driver 3 - Truck goes to location, driver has key but NO password Activity Report will show, on which day and at what time the driver opened the lock 8 - When the key is returned, the 7 - Unload the truck manager inserts the key in Programmer to get ACTIVITY REPORT 4 - When truck arrives on location, the driver needs to call the manager to get the password for the key. 5 -The driver inputs the password in the key and opens the lock 17

Products Specifications 18

Products Specifications – Keys SPECIFICATIONS Materials: Key housing – reinforced ABS Key blade in stainless steel Splash Water resistant Operating Temperature: -10 o. C to +50 o. C LED Information: Green: Access Granted Orange: Access refused because no access during that time period Red: Access Refused 4 blinks(Color depends on the above): Low Battery State Dimensions: 65 x 35 x 18 mm Weight: 30 g Power source: Two 1. 5 v batteries Battery type : LR 1/MN 9100 Autonomy : 2 years Memory : Tracking history of the last 1000 logs Rohs and CE compliant, manufactured to ISO standards. Powered by 2 x LR 1 batteries 19

Products Specifications – LOCKS SPECIFICATIONS Materials: Made of Brass with stainless steel plating Opening codes are purely electronic Operating Temperature: -20 o. C to + 65 o. C Dimensions: 10/30 mm to 10/70 mm for single entry locks 30/30 mm to 70/70 mm for double-entry & button locks European standards Single Entry MECHATRONIC Lock Double Entry MECHATRONIC Lock Power source: None; powered by inserting key. Memory : Tracking history of the last 1000 logs Memory of blacklisted keys: 500 banned keys Rohs and CE compliant, manufactured to ISO standards. Button MECHATRONIC Lock EASY TO INSTALL Step 1 : remove screw Step 2 : remove old lock Step 3 : insert Acsys lock Step 4 : insert screw INSTANT ACCESS CONTROL 20

Products Specifications – PADLOCKS SPECIFICATIONS Materials: ACSYS PADLOCK PL 3 ACSYS PADLOCK PL 5 Shell in case hardened steel Shackle in case hardened boron steel Fitted with a 30/10 stainless steel cylinder Power source: None; powered by inserting key. Memory : Tracking history of the last 1000 logs Memory of blacklisted keys: 500 banned keys Rohs and CE compliant, manufactured to ISO standards. The MOST secure padlock in the world 21

The most secure padlock in the world How to use the HASP Step 1 Step 2 Step 3 Step 4 22

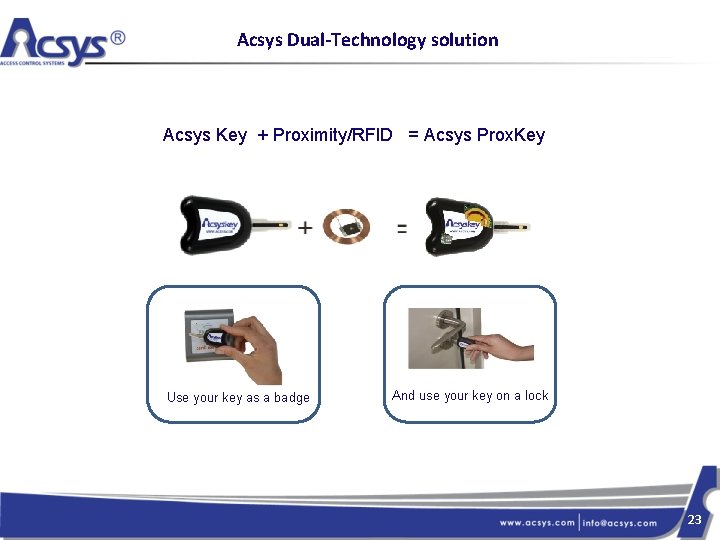
Acsys Dual-Technology solution Acsys Key + Proximity/RFID = Acsys Prox. Key Use your key as a badge And use your key on a lock 23

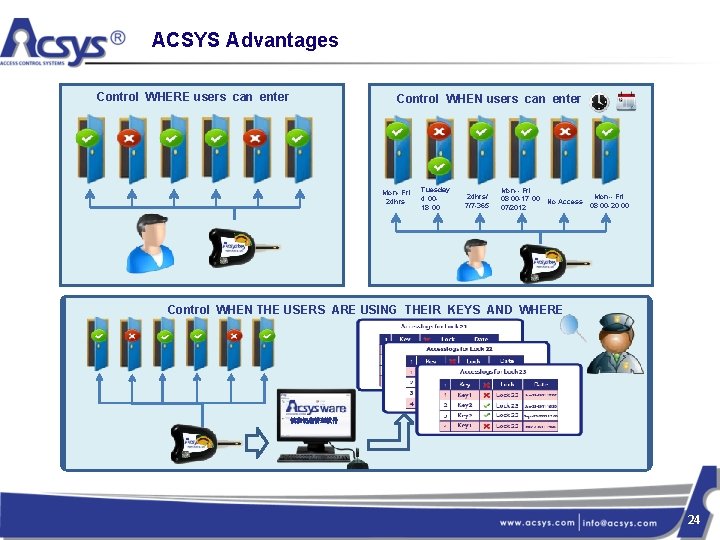
ACSYS Advantages Control WHERE users can enter Control WHEN users can enter Mon- Fri 24 hrs Tuesday 4: 0018: 00 24 hrs/ 7/7 -365 Mon-- Fri 08: 00 -17: 00 No Access Mon-- Fri 08: 00 -20: 00 07/2012 Control WHEN THE USERS ARE USING THEIR KEYS AND WHERE 锁和钥匙管理软件 24

Better security, better life! Contact us: UTIS Jeddah – Saudi Arabia Mobile: 0504667387 Email: info@utis. sa