Access Control Matrix CSSE 490 Computer Security Mark





- Slides: 10

Access Control Matrix CSSE 490 Computer Security Mark Ardis, Rose-Hulman Institute March 9, 2004 1

Acknowledgements Many of these slides came from Matt Bishop, author of Computer Security: Art and Science 2

Chapter 2: Access Control Matrix l l l Overview Access Control Matrix Model Special Rights • Principle of Attenuation of Privilege 3

Overview l Protection state of system • Describes current settings, values of system relevant to protection l Access control matrix • Describes protection state precisely • Matrix describing rights of subjects (processes • and users) State transitions change elements of matrix 4

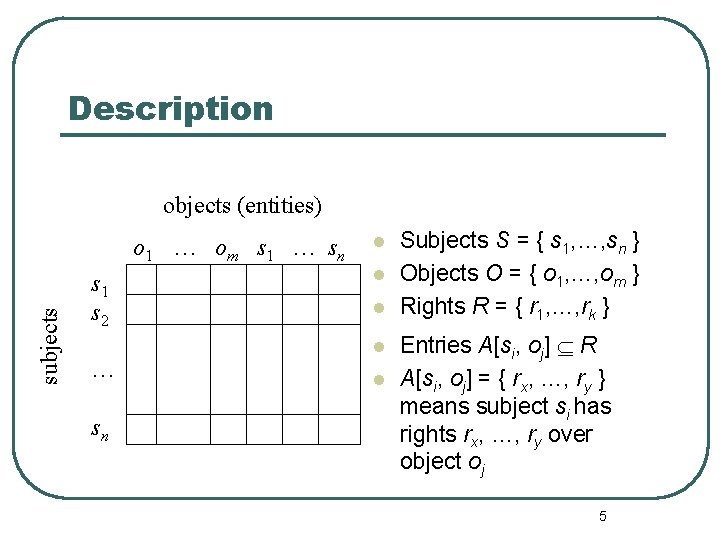
Description objects (entities) subjects o 1 … om s 1 … sn s 1 s 2 … sn l l l Subjects S = { s 1, …, sn } Objects O = { o 1, …, om } Rights R = { r 1, …, rk } Entries A[si, oj] R A[si, oj] = { rx, …, ry } means subject si has rights rx, …, ry over object oj 5

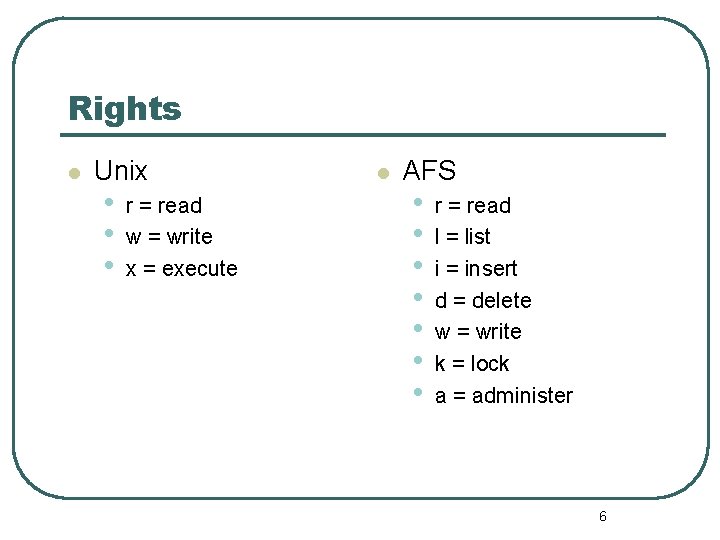
Rights l Unix • • • r = read w = write x = execute l AFS • • r = read l = list i = insert d = delete w = write k = lock a = administer 6

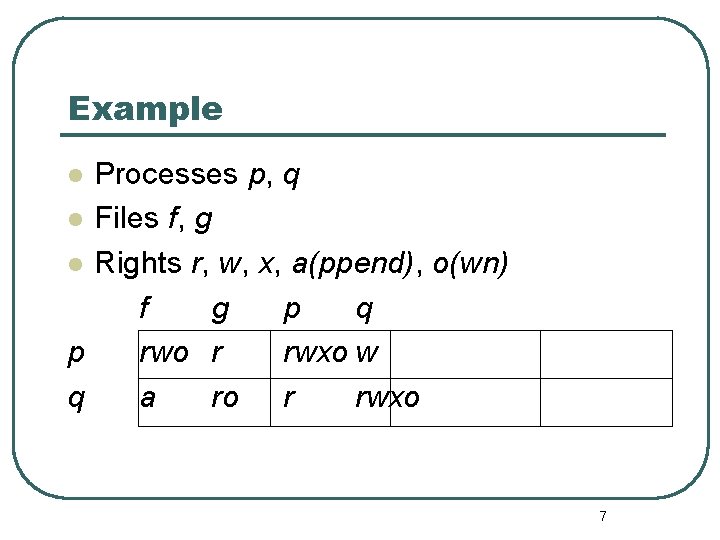
Example Processes p, q l Files f, g l Rights r, w, x, a(ppend), o(wn) f g p q p rwo r rwxo w q a ro r rwxo l 7

Copy Right l l Allows possessor to give rights to another Often attached to a right, so only applies to that right • r is read right that cannot be copied • rc is read right that can be copied l Is copy flag copied when giving r rights? • Depends on model, instantiation of model 8

Own Right l Usually allows possessor to change entries in ACM column • So owner of object can add, delete rights for • others May depend on what system allows • Can’t give rights to specific (set of) users • Can’t pass copy flag to specific (set of) users 9

Attenuation of Privilege l Principle says you can’t give rights you do not possess • Restricts addition of rights within a system • Usually ignored for owner • Why? 10