Access Control Matrix csci 5233 computer security integrity





![Add Right s S, o O n Primitive command: enter r into a[s, o] Add Right s S, o O n Primitive command: enter r into a[s, o]](https://slidetodoc.com/presentation_image_h2/11be2d05b8db9ac232e89a4f023eec10/image-17.jpg)
![Delete Right s S, o O n Primitive command: delete r from a[s, o] Delete Right s S, o O n Primitive command: delete r from a[s, o]](https://slidetodoc.com/presentation_image_h2/11be2d05b8db9ac232e89a4f023eec10/image-18.jpg)







- Slides: 28

Access Control Matrix csci 5233 computer security & integrity 1

Outline n Overview n Access Control Matrix Model – Boolean Expression Evaluation – History n Protection State Transitions – Commands – Conditional Commands n Special Rights – Principle of Attenuation of Privilege csci 5233 computer security & integrity 2

Overview n State – The collection of the current values of all memory locations, all secondary storage, and all registers and other components of the system. n Protection state of system – a subset of the states that are relevant to protection n Access control matrix – A tool that can describe protection state – Matrix describing rights of subjects – State transitions change elements of matrix csci 5233 computer security & integrity 3

Overview n Access control matrix model – The most precise model used to describe a protection state – It characterizes the rights of each subject with respect to every other entity, which can be active or passive. – The set of objects = the set of all protected entities – The set of subjects = the set of active objects, such as processes and users. – The ACM captures the relationships between the subjects and the objects. – When a command changes the state of the system, a state transition occurs. csci 5233 computer security & integrity 4

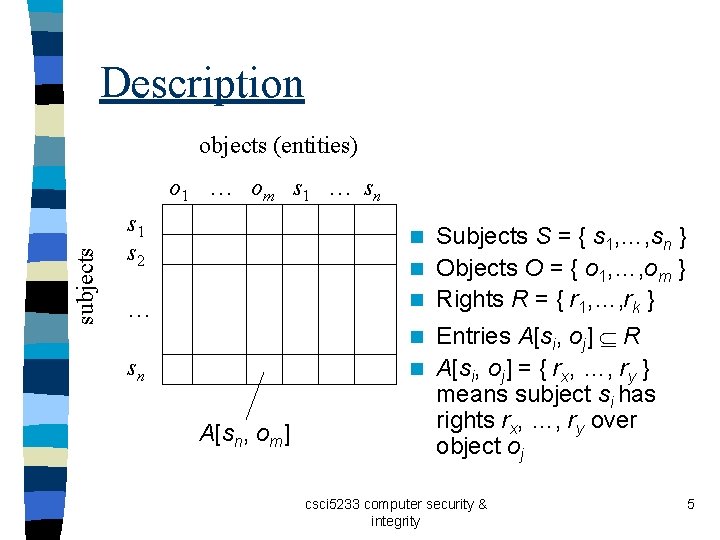
Description objects (entities) subjects o 1 … om s 1 … sn s 1 s 2 Subjects S = { s 1, …, sn } n Objects O = { o 1, …, om } n Rights R = { r 1, …, rk } n … Entries A[si, oj] R n A[si, oj] = { rx, …, ry } means subject si has rights rx, …, ry over object oj n sn A[sn, om] csci 5233 computer security & integrity 5

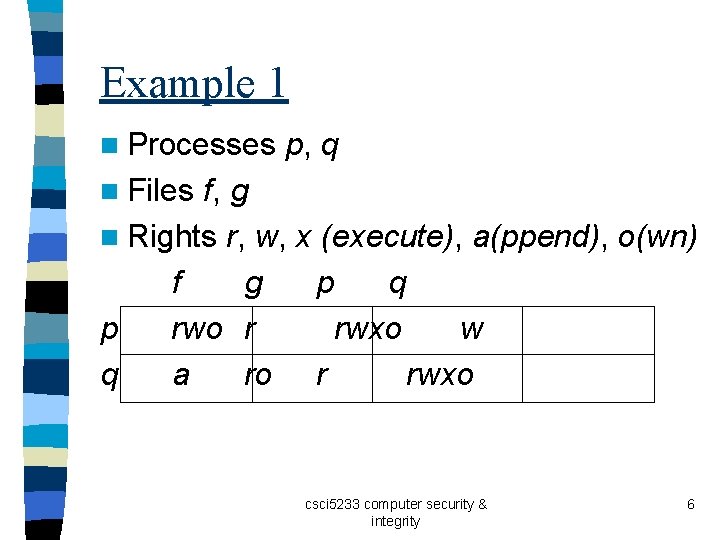
Example 1 n Processes p, q n Files f, g n Rights r, w, x (execute), a(ppend), o(wn) f g p q p rwo r rwxo w q a ro r rwxo csci 5233 computer security & integrity 6

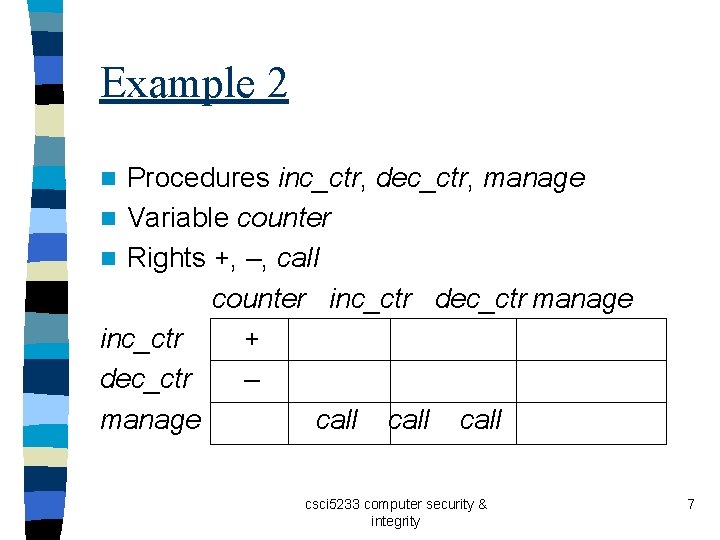
Example 2 Procedures inc_ctr, dec_ctr, manage n Variable counter n Rights +, –, call counter inc_ctr dec_ctr manage inc_ctr + dec_ctr – manage call n csci 5233 computer security & integrity 7

Boolean Expression Evaluation ACM may be used for control of access to database fields n ACM controls access to database fields n – Subjects have attributes (e. g. , name, role, groups, programs, etc. ) – Verbs define type of access (e. g. , read, write, paint, temp_ctl) – Rules associated with (objects, verb) pair (e. g. , object = recipes; verb = write; rule = ‘creative’ in subject. group) n Subject attempts to access object – Rule for (object, verb) evaluated, grants or denies access csci 5233 computer security & integrity 8

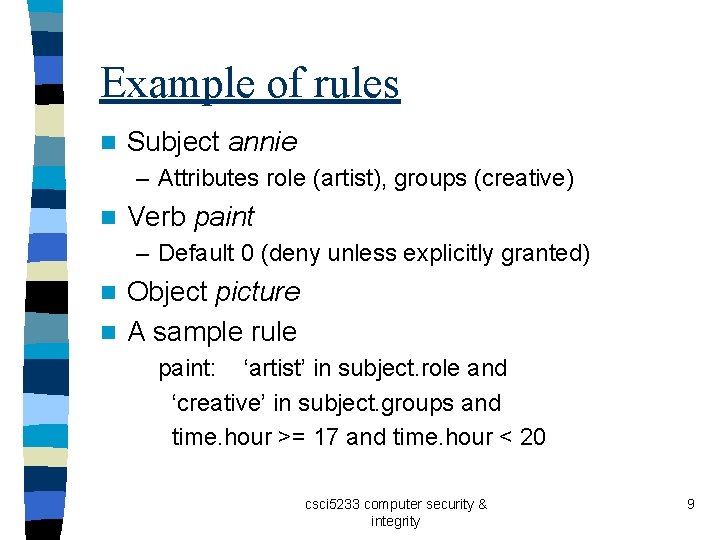
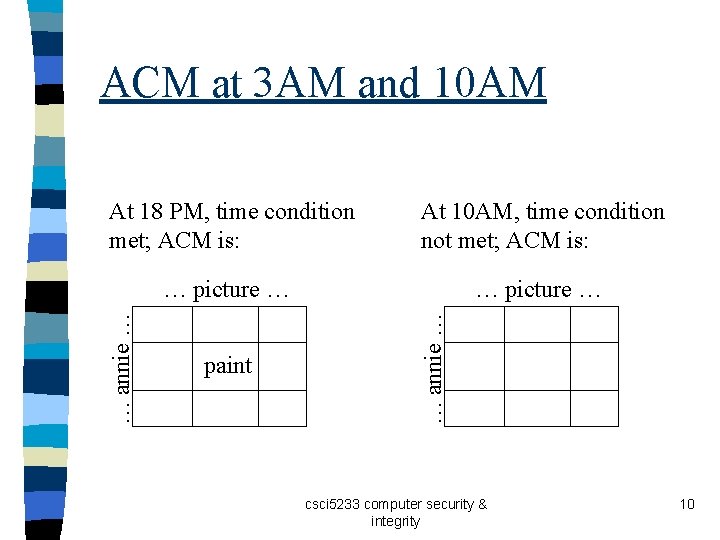
Example of rules n Subject annie – Attributes role (artist), groups (creative) n Verb paint – Default 0 (deny unless explicitly granted) Object picture n A sample rule n paint: ‘artist’ in subject. role and ‘creative’ in subject. groups and time. hour >= 17 and time. hour < 20 csci 5233 computer security & integrity 9

ACM at 3 AM and 10 AM … picture … paint … annie … At 10 AM, time condition not met; ACM is: … annie … At 18 PM, time condition met; ACM is: csci 5233 computer security & integrity 10

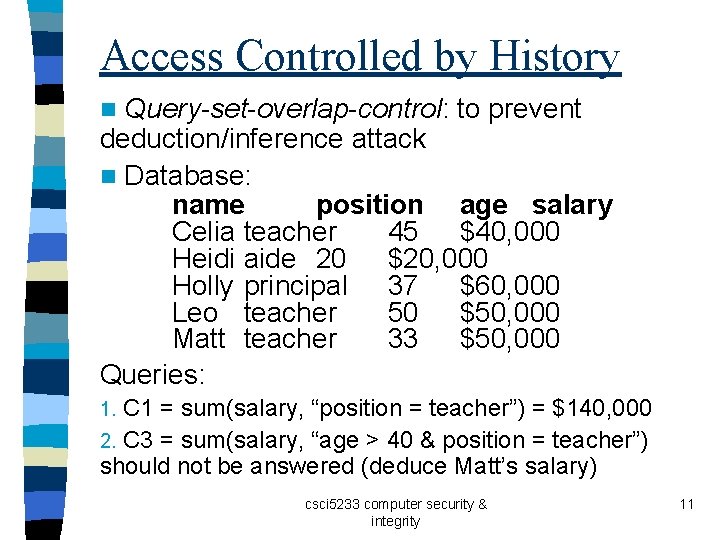
Access Controlled by History Query-set-overlap-control: to prevent deduction/inference attack n Database: name position age salary Celia teacher 45 $40, 000 Heidi aide 20 $20, 000 Holly principal 37 $60, 000 Leo teacher 50 $50, 000 Matt teacher 33 $50, 000 Queries: n C 1 = sum(salary, “position = teacher”) = $140, 000 2. C 3 = sum(salary, “age > 40 & position = teacher”) should not be answered (deduce Matt’s salary) 1. csci 5233 computer security & integrity 11

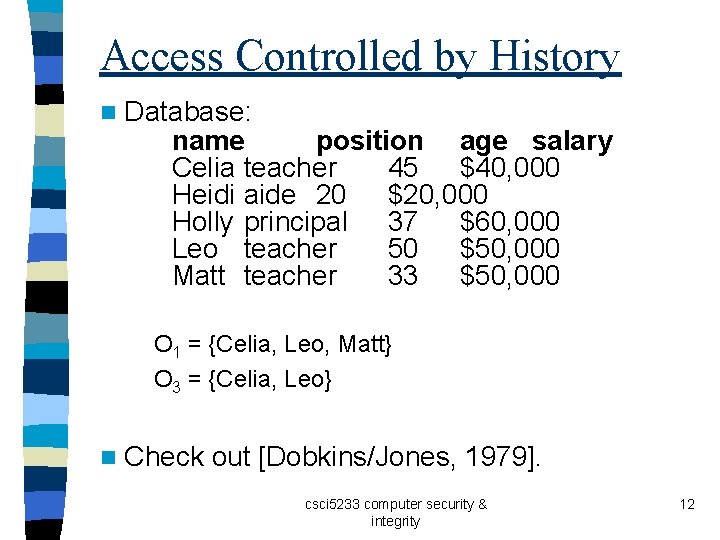
Access Controlled by History n Database: name position age salary Celia teacher 45 $40, 000 Heidi aide 20 $20, 000 Holly principal 37 $60, 000 Leo teacher 50 $50, 000 Matt teacher 33 $50, 000 O 1 = {Celia, Leo, Matt} O 3 = {Celia, Leo} n Check out [Dobkins/Jones, 1979]. csci 5233 computer security & integrity 12

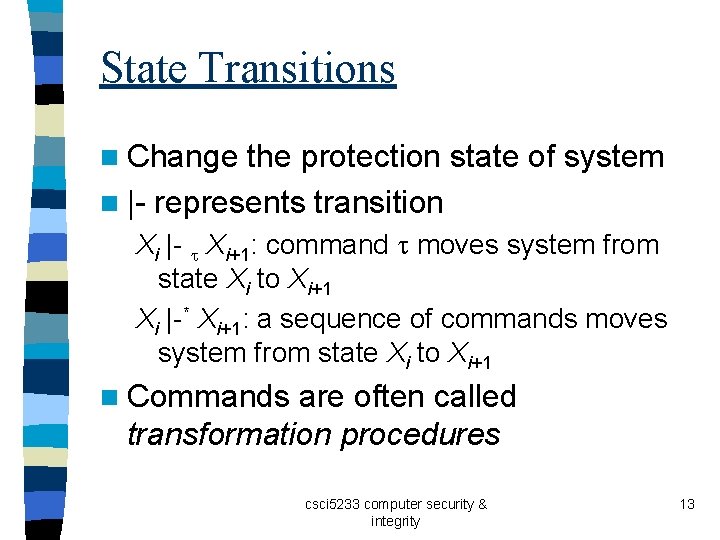
State Transitions n Change the protection state of system n |- represents transition Xi |- t Xi+1: command t moves system from state Xi to Xi+1 Xi |-* Xi+1: a sequence of commands moves system from state Xi to Xi+1 n Commands are often called transformation procedures csci 5233 computer security & integrity 13

Primitive Operations n create subject s – Creates new row, column in ACM; n create object o – creates new column in ACM n destroy subject s – Deletes row, column from ACM n destroy object o – deletes column from ACM n enter r into A[s, o] – Adds r rights for subject s over object o n delete r from A[s, o] – Removes r rights from subject s over object o csci 5233 computer security & integrity 14

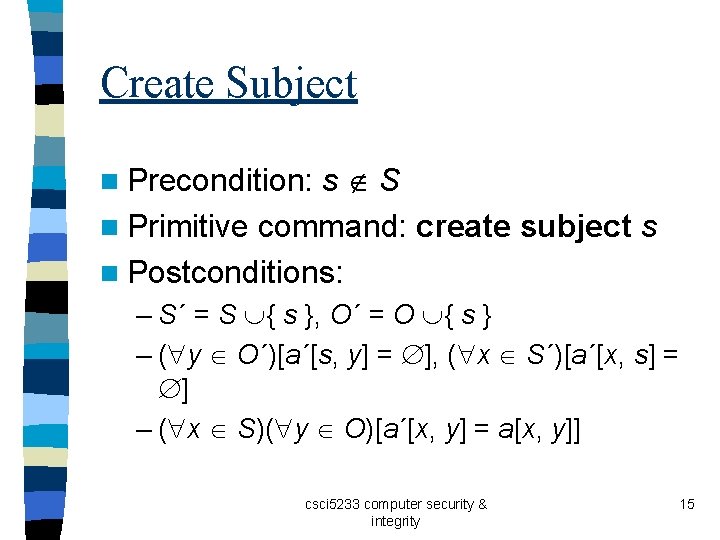
Create Subject s S n Primitive command: create subject s n Postconditions: n Precondition: – S´ = S { s }, O´ = O { s } – ( y O´)[a´[s, y] = ], ( x S´)[a´[x, s] = ] – ( x S)( y O)[a´[x, y] = a[x, y]] csci 5233 computer security & integrity 15

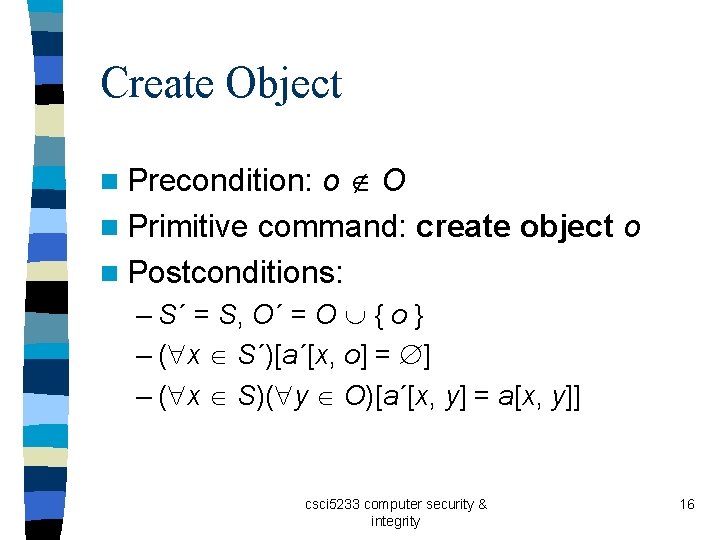
Create Object o O n Primitive command: create object o n Postconditions: n Precondition: – S´ = S, O´ = O { o } – ( x S´)[a´[x, o] = ] – ( x S)( y O)[a´[x, y] = a[x, y]] csci 5233 computer security & integrity 16
![Add Right s S o O n Primitive command enter r into as o Add Right s S, o O n Primitive command: enter r into a[s, o]](https://slidetodoc.com/presentation_image_h2/11be2d05b8db9ac232e89a4f023eec10/image-17.jpg)
Add Right s S, o O n Primitive command: enter r into a[s, o] n Postconditions: n Precondition: – S´ = S, O´ = O – a´[s, o] = a[s, o] { r } – ( x S´ – { s })( y O´ – { o }) [a´[x, y] = a[x, y]] csci 5233 computer security & integrity 17
![Delete Right s S o O n Primitive command delete r from as o Delete Right s S, o O n Primitive command: delete r from a[s, o]](https://slidetodoc.com/presentation_image_h2/11be2d05b8db9ac232e89a4f023eec10/image-18.jpg)
Delete Right s S, o O n Primitive command: delete r from a[s, o] n Postconditions: n Precondition: – S´ = S, O´ = O – a´[s, o] = a[s, o] – { r } – ( x S´ – { s })( y O´ – { o }) [a´[x, y] = a[x, y]] csci 5233 computer security & integrity 18

Destroy Subject s S n Primitive command: destroy subject s n Postconditions: n Precondition: – S´ = S – { s }, O´ = O – { s } – ( y O´)[a´[s, y] = ], ( x S´)[a´[x, s] = ] – ( x S´)( y O´) [a´[x, y] = a[x, y]] csci 5233 computer security & integrity 19

Destroy Object o o n Primitive command: destroy object o n Postconditions: n Precondition: – S´ = S, O´ = O – { o } – ( x S´)[a´[x, o] = ] – ( x S´)( y O´) [a´[x, y] = a[x, y]] csci 5233 computer security & integrity 20

Creating File n Process p creates file f with r and w permission command create • file(p, f) create object f; enter own into A[p, f]; enter r into A[p, f]; enter w into A[p, f]; end csci 5233 computer security & integrity 21

Mono-Operational Commands n Single primitive operation in a command n Example: Make process p the owner of file g command make • owner(p, g) enter own into A[p, g]; end csci 5233 computer security & integrity 22

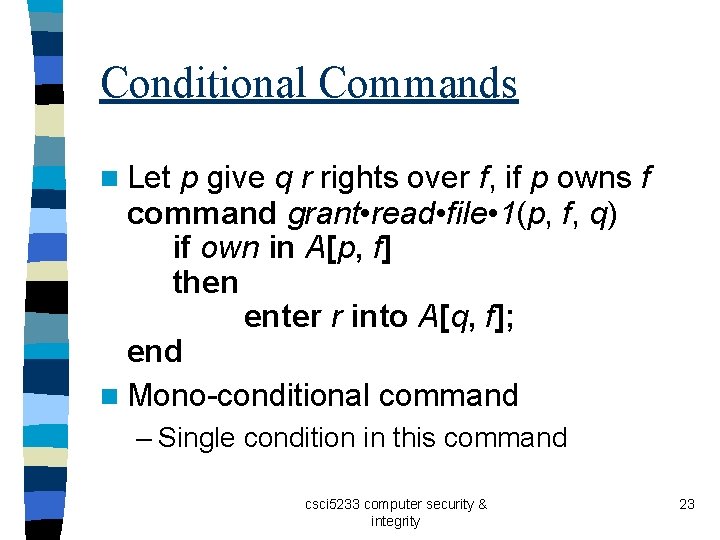
Conditional Commands n Let p give q r rights over f, if p owns f command grant • read • file • 1(p, f, q) if own in A[p, f] then enter r into A[q, f]; end n Mono-conditional command – Single condition in this command csci 5233 computer security & integrity 23

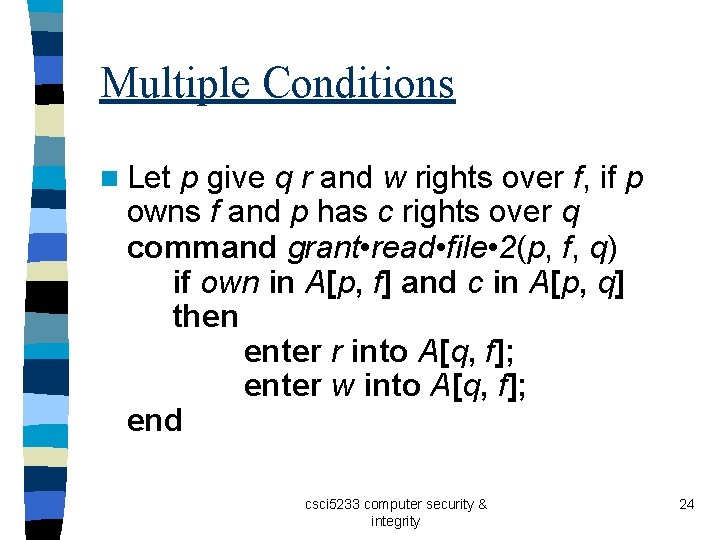
Multiple Conditions n Let p give q r and w rights over f, if p owns f and p has c rights over q command grant • read • file • 2(p, f, q) if own in A[p, f] and c in A[p, q] then enter r into A[q, f]; enter w into A[q, f]; end csci 5233 computer security & integrity 24

Copy Right n Allows possessor to give rights to another n Often attached to a right, so only applies to that right – r is read right that cannot be copied – rc is read right that can be copied n Is copy flag copied when giving r rights? – Depends on model, instantiation of model csci 5233 computer security & integrity 25

Own Right n Usually allows the possessor to change entries in ACM column – So owner of object can add, delete rights for others – May depend on what system allows • Can’t give rights to specific (set of) users • Can’t pass copy flag to specific (set of) users csci 5233 computer security & integrity 26

Attenuation of Privilege n The principle says you can’t give rights you do not possess. – Restricts addition of rights within a system – Usually ignored for owner • Why? Owner gives herself rights, gives them to others, deletes her rights. csci 5233 computer security & integrity 27

Key Points n Access control matrix simplest abstraction mechanism for representing protection state n Transitions alter protection state n 6 primitive operations alter matrix – Transitions can be expressed as commands composed of these operations and, possibly, conditions csci 5233 computer security & integrity 28