Access Control List Step 1 Step 2 accesslist
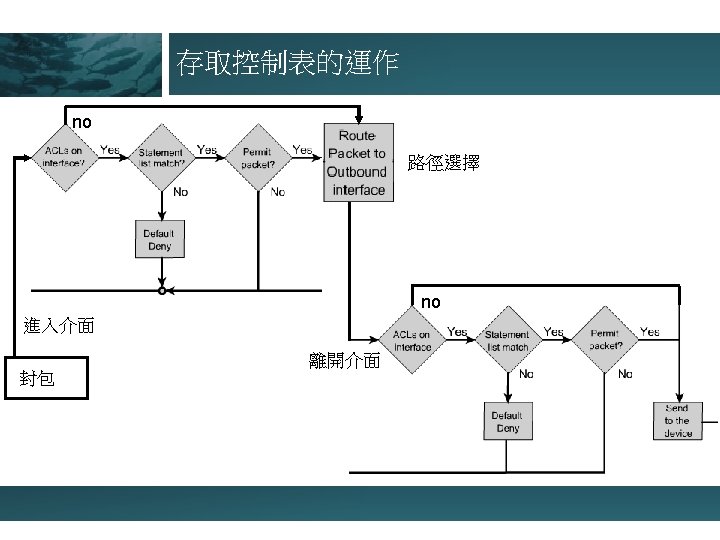





- Slides: 18

Access Control List (存取控制表) 王振生



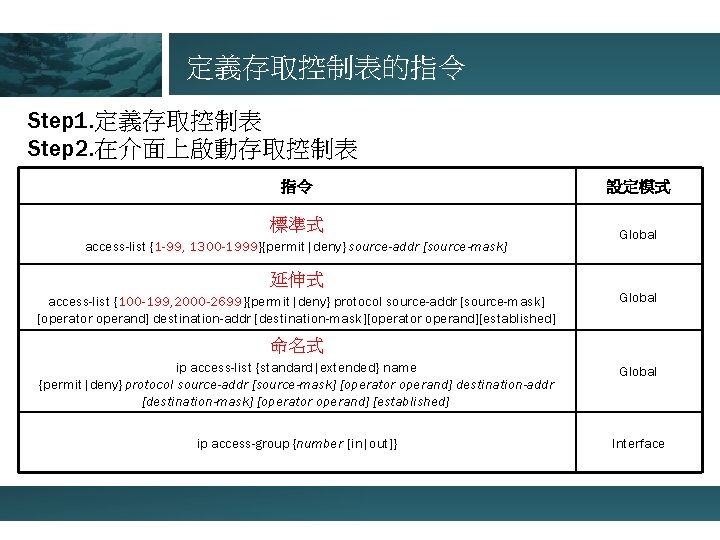
定義存取控制表的指令 Step 1. 定義存取控制表 Step 2. 在介面上啟動存取控制表 指令 標準式 access-list {1 -99, 1300 -1999}{permit|deny} source-addr [source-mask] 設定模式 Global 延伸式 access-list {100 -199, 2000 -2699}{permit|deny} protocol source-addr [source-mask] [operator operand] destination-addr [destination-mask][operator operand][established] Global 命名式 ip access-list {standard|extended} name {permit|deny} protocol source-addr [source-mask] [operator operand] destination-addr [destination-mask] [operator operand] [established] Global ip access-group {number [in|out]} Interface

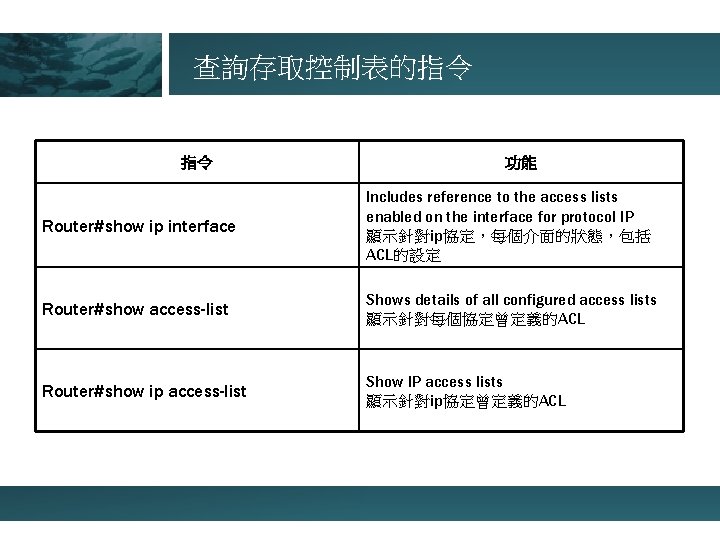
查詢存取控制表的指令 指令 功能 Router#show ip interface Includes reference to the access lists enabled on the interface for protocol IP 顯示針對ip協定,每個介面的狀態,包括 ACL的設定 Router#show access-list Shows details of all configured access lists 顯示針對每個協定曾定義的ACL Router#show ip access-list Show IP access lists 顯示針對ip協定曾定義的ACL


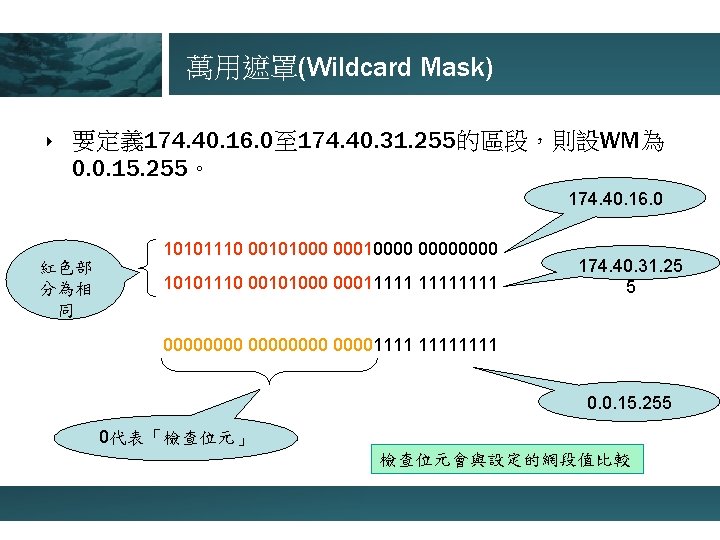
萬用遮罩(Wildcard Mask) ‣ 要定義 174. 40. 16. 0至 174. 40. 31. 255的區段,則設WM為 0. 0. 15. 255。 174. 40. 16. 0 紅色部 分為相 同 10101110 00101000 00010000 10101110 00101000 00011111 174. 40. 31. 25 5 000000001111 0. 0. 15. 255 0代表「檢查位元」 檢查位元會與設定的網段值比較

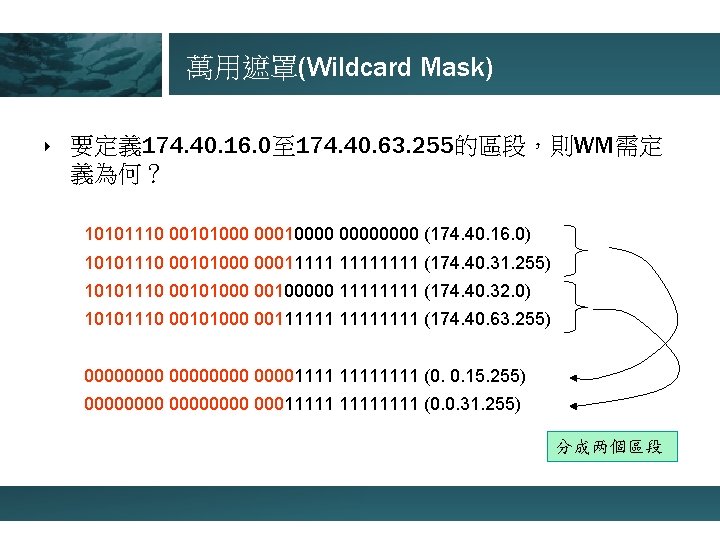
萬用遮罩(Wildcard Mask) ‣ 要定義 174. 40. 16. 0至 174. 40. 63. 255的區段,則WM需定 義為何? 10101110 00101000 00010000 (174. 40. 16. 0) 10101110 00101000 00011111 (174. 40. 31. 255) 10101110 00101000 00100000 1111 (174. 40. 32. 0) 10101110 00101000 00111111 (174. 40. 63. 255) 000000001111 (0. 0. 15. 255) 00000000 00011111 (0. 0. 31. 255) 分成两個區段


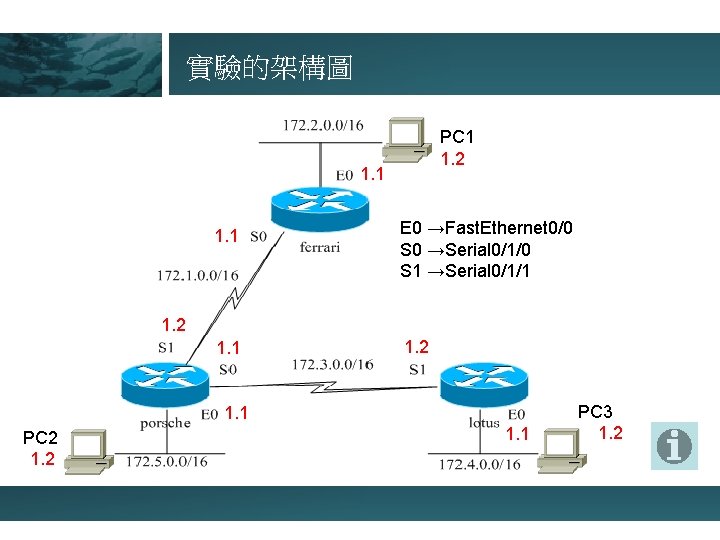
實驗的架構圖 PC 1 1. 2 1. 1 E 0 →Fast. Ethernet 0/0 S 0 →Serial 0/1/0 S 1 →Serial 0/1/1 1. 2 1. 1 PC 3 1. 2



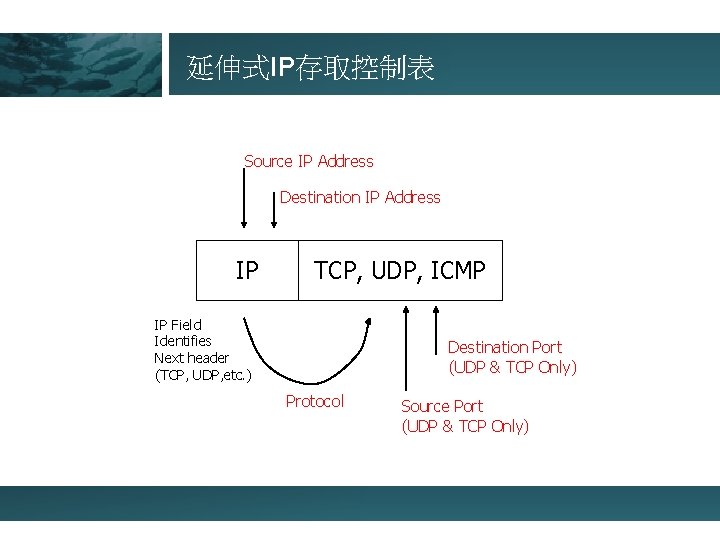
延伸式IP存取控制表 Source IP Address Destination IP Address IP TCP, UDP, ICMP IP Field Identifies Next header (TCP, UDP, etc. ) Destination Port (UDP & TCP Only) Protocol Source Port (UDP & TCP Only)

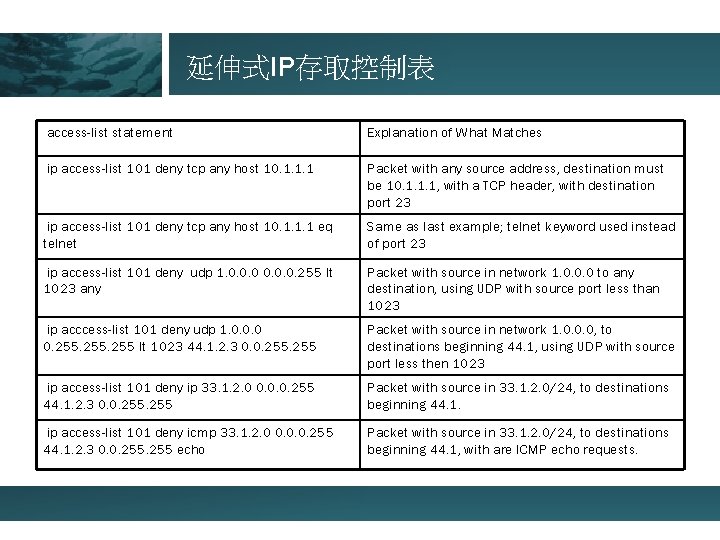
延伸式IP存取控制表 access-list statement Explanation of What Matches ip access-list 101 deny tcp any host 10. 1. 1. 1 Packet with any source address, destination must be 10. 1. 1. 1, with a TCP header, with destination port 23 ip access-list 101 deny tcp any host 10. 1. 1. 1 eq telnet Same as last example; telnet keyword used instead of port 23 ip access-list 101 deny udp 1. 0. 0. 0. 255 lt 1023 any Packet with source in network 1. 0. 0. 0 to any destination, using UDP with source port less than 1023 ip acccess-list 101 deny udp 1. 0. 0. 0 0. 255 lt 1023 44. 1. 2. 3 0. 0. 255 Packet with source in network 1. 0. 0. 0, to destinations beginning 44. 1, using UDP with source port less then 1023 ip access-list 101 deny ip 33. 1. 2. 0 0. 0. 0. 255 44. 1. 2. 3 0. 0. 255 Packet with source in 33. 1. 2. 0/24, to destinations beginning 44. 1. ip access-list 101 deny icmp 33. 1. 2. 0 0. 0. 0. 255 44. 1. 2. 3 0. 0. 255 echo Packet with source in 33. 1. 2. 0/24, to destinations beginning 44. 1, with are ICMP echo requests.



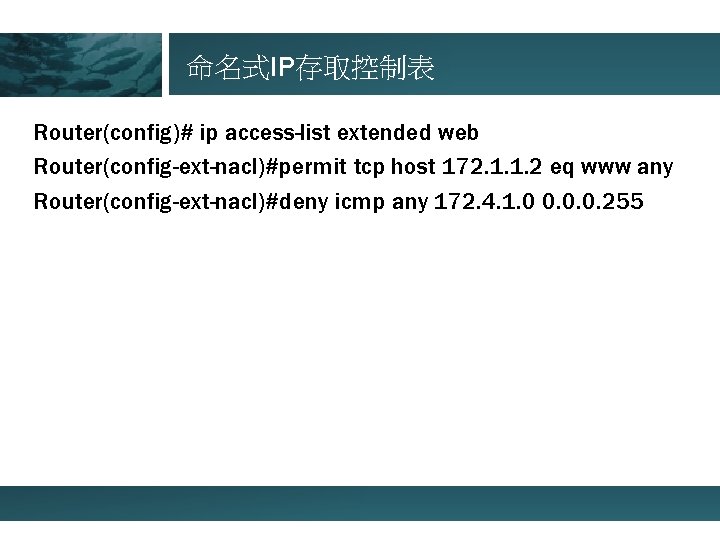
命名式IP存取控制表 Router(config)# ip access-list extended web Router(config-ext-nacl)#permit tcp host 172. 1. 1. 2 eq www any Router(config-ext-nacl)#deny icmp any 172. 4. 1. 0 0. 0. 0. 255
