Access Control in Collaborative Systems William Tolone GailJoon

Access Control in Collaborative Systems William Tolone, Gail-Joon Ahn, Tanusree Pai & Seng-Phil Hong

Outline • • • Collaborative Environments Access Control Requirements Access Control Models Assessment Conclusion

Collaborative Environments • Facebook • Code Repositories • Webcourses

Access Control Requirements • • Applied at a distributed level Should be able to adapt Scalability Fine-grained control Exclusion of unauthorized users Easy specification of access rights Ability to dynamically change access policies Reasonable performance and resource cost

Outline • • • Collaborative Environments Access Control Requirements Access Control Models Assessment Conclusion
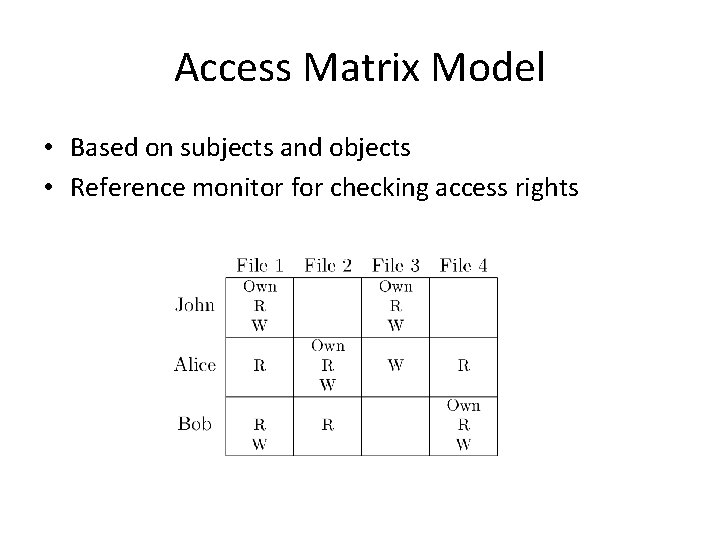
Access Matrix Model • Based on subjects and objects • Reference monitor for checking access rights
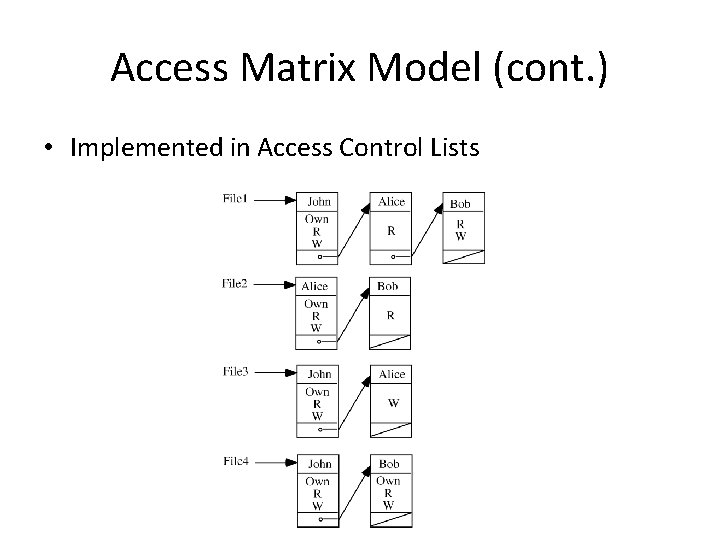
Access Matrix Model (cont. ) • Implemented in Access Control Lists

Access Matrix Model (cont. ) • Shortcomings – Not complex enough – No ability to dynamically change policy – Can’t address objects not owned by users
Roll-Based Access Control (RBAC) • • Permissions assigned to roles rather than users Users associated to roles More scalable Shortcomings – Roles are too static
Task-Based Access Control (TBAC) • • • Derivative of subject-object model Contains information based on task Access granted in steps related to the task Active model Shortcomings – Context only based on task progression – Management, delegation, revocation are not covered – Not very applicable outside enterprise • May use roles as an interface
Team-Based Access Control (TMAC) • Similar to RBAC • Covers case when different roles collaborate together • User context describes user’s role in team • Shortcomings – Hasn’t fully been developed
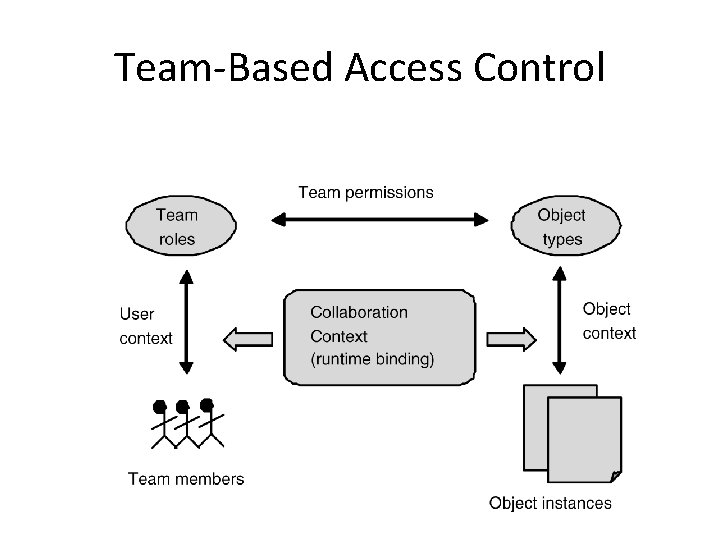
Team-Based Access Control

Spatial Access Control • Divides collaboration environment into regions • User credentials used to determine access • Shortcomings – Only navigational access requirements – Must divide application into regions

Context-Aware Access Control • Extension of RBAC • Environment roles defined at time of activation • Shortcomings – Hasn’t been fully developed/tested

Outline • • • Collaborative Environments Access Control Requirements Access Control Models Assessment Conclusion

Assessment • Criteria – Complexity – Transparency – Ease of use – Applicability – Collaboration Support – Policy Specification – Policy Enforcement – Fine Grained Control – Active/Passive – Contextual
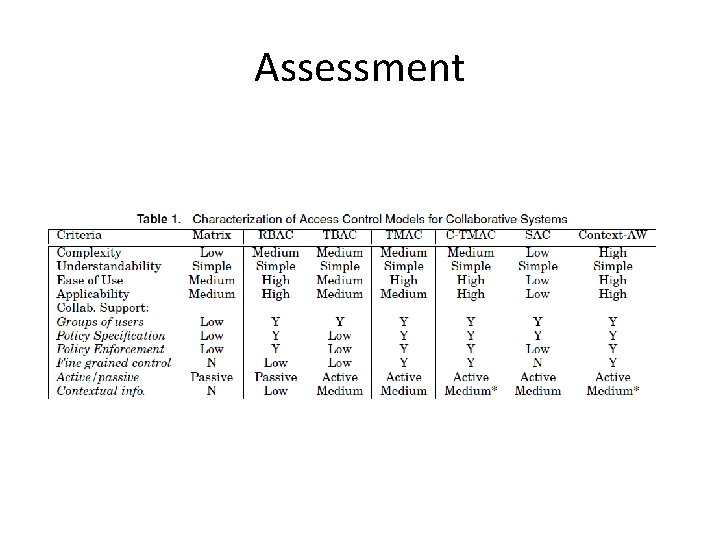
Assessment

Conclusion • • Roles are well accepted Importance of context Active systems are preferable Scalability required
- Slides: 18