Access control in a hierarchy using oneway hash


![Example (K 1) (K 2=H 1(K 1)) (K 3=H 2(K 1)) [H 1(K 3)] Example (K 1) (K 2=H 1(K 1)) (K 3=H 2(K 1)) [H 1(K 3)]](https://slidetodoc.com/presentation_image/4de238575e28e585ddd3c283d7c3d84e/image-13.jpg)
- Slides: 13

Access control in a hierarchy using one-way hash functions Authors: Cungang Yang and Celia Li Source: Computers & Security, vol. 23, pp. 659 -664, 2004 Reporter: Jung-wen Lo (駱榮問) Date: 2006/03/02

Outline n Introduction q q n Hierarchical Structure Drawback of Akl & Taylor Proposed Scheme q q Key Assignment and Key Derivation Dynamic Access Control n n n Adding node Deleting Node Changing Relationships q q n n Adding Deleting Significances Comments 2

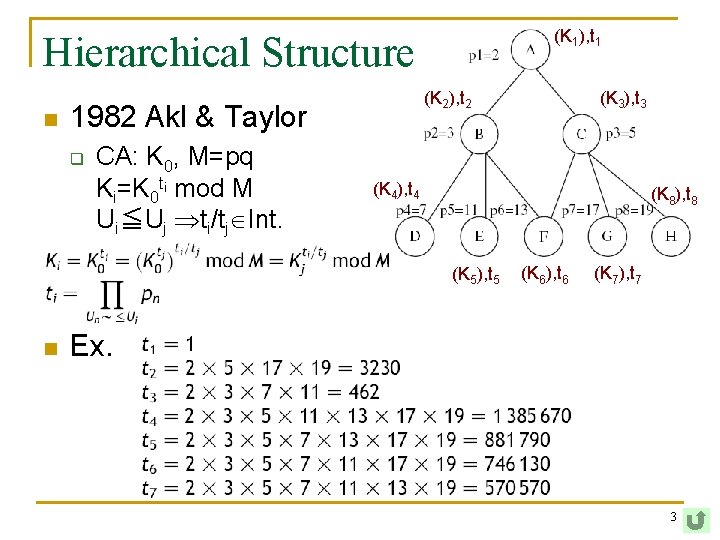
(K 1), t 1 Hierarchical Structure n (K 2), t 2 1982 Akl & Taylor q CA: K 0, M=pq Ki=K 0 ti mod M Ui≦Uj ti/tj Int. (K 4), t 4 (K 8), t 8 (K 5), t 5 n (K 3), t 3 (K 6), t 6 (K 7), t 7 Ex. 3

Drawback of Akl & Taylor n n n Large storage when hierarchy is large Carefully chose public parameters => Users may collaborate key Add a new node may use all secret keys and can be gotten by all other nodes e. g. Add new node of C public parameters=2× 3× 5× 7× 11× 13× 17× 19 4

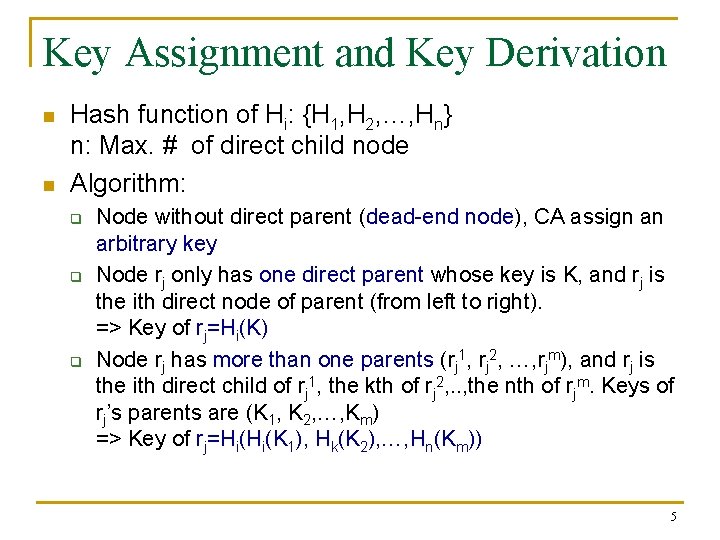
Key Assignment and Key Derivation n n Hash function of Hi: {H 1, H 2, …, Hn} n: Max. # of direct child node Algorithm: q q q Node without direct parent (dead-end node), CA assign an arbitrary key Node rj only has one direct parent whose key is K, and rj is the ith direct node of parent (from left to right). => Key of rj=Hi(K) Node rj has more than one parents (rj 1, rj 2, …, rjm), and rj is the ith direct child of rj 1, the kth of rj 2, . . , the nth of rjm. Keys of rj’s parents are (K 1, K 2, …, Km) => Key of rj=Hi(Hi(K 1), Hk(K 2), …, Hn(Km)) 5

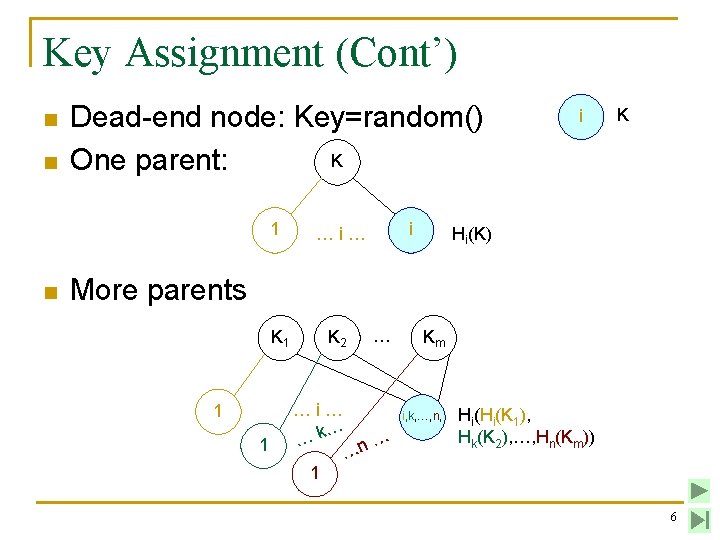
Key Assignment (Cont’) n n Dead-end node: Key=random() K One parent: 1 n i …i… i K Hi(K) More parents K 1 1 1 K 2 … …i… … … …k n … 1 Km i, k, …, n, Hi(Hi(K 1), Hk(K 2), …, Hn(Km)) 6

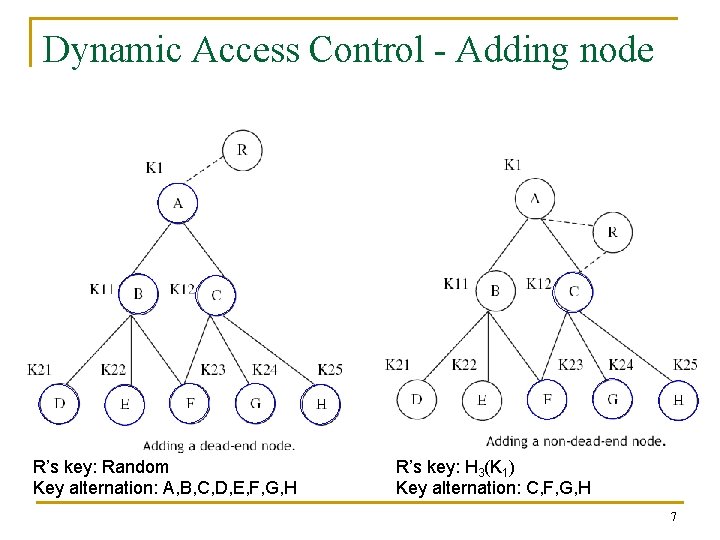
Dynamic Access Control - Adding node R’s key: Random Key alternation: A, B, C, D, E, F, G, H R’s key: H 3(K 1) Key alternation: C, F, G, H 7

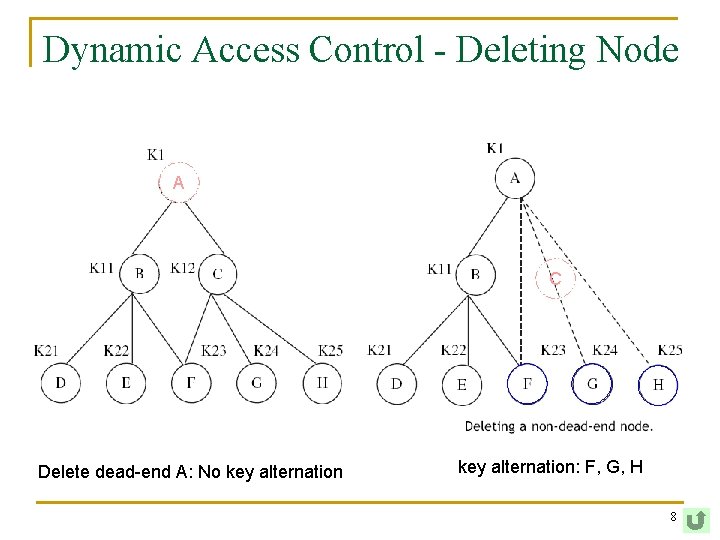
Dynamic Access Control - Deleting Node A C Delete dead-end A: No key alternation: F, G, H 8

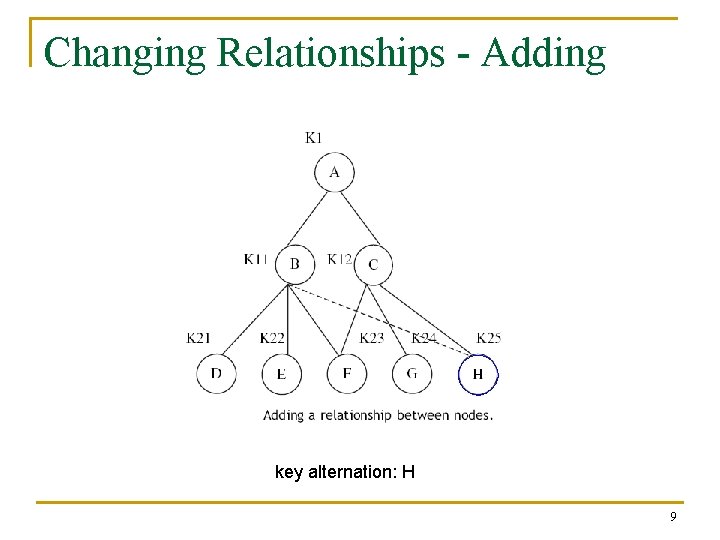
Changing Relationships - Adding key alternation: H 9

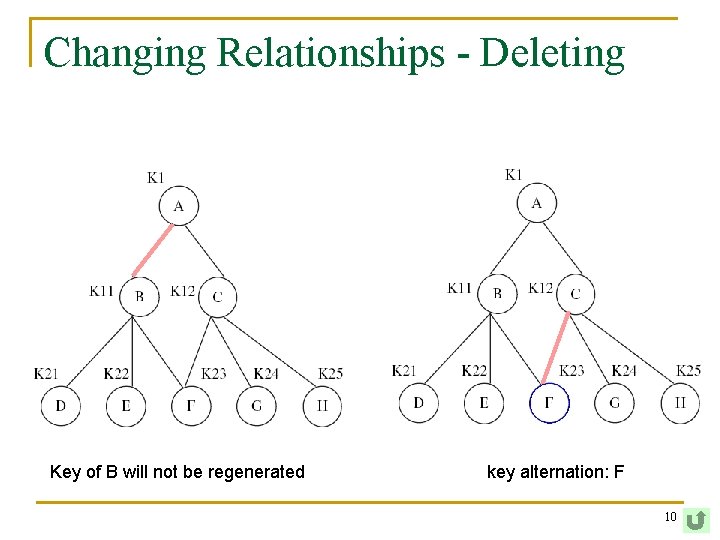
Changing Relationships - Deleting Key of B will not be regenerated key alternation: F 10

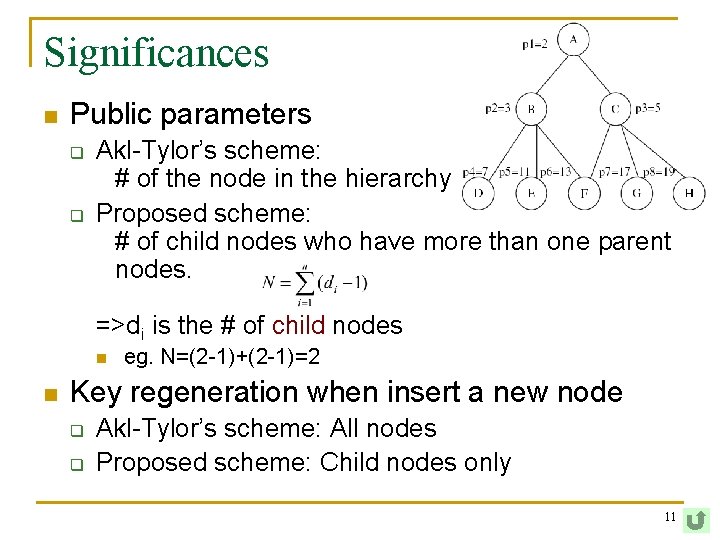
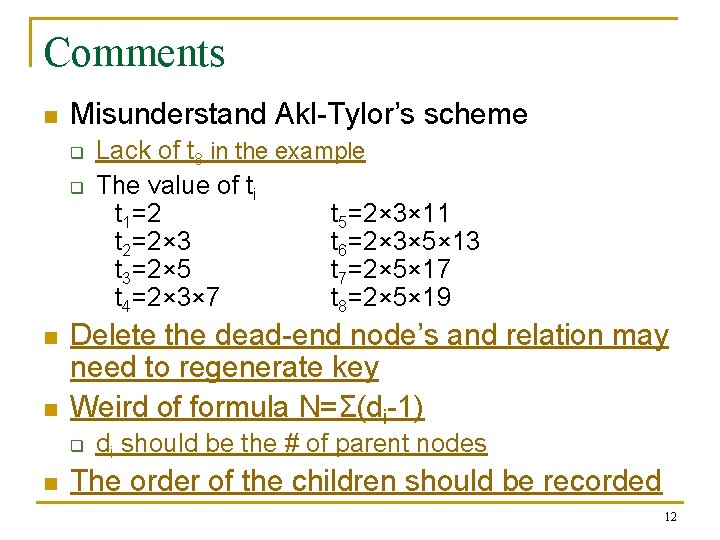
Significances n Public parameters q q Akl-Tylor’s scheme: # of the node in the hierarchy Proposed scheme: # of child nodes who have more than one parent nodes. =>di is the # of child nodes n n eg. N=(2 -1)+(2 -1)=2 Key regeneration when insert a new node q q Akl-Tylor’s scheme: All nodes Proposed scheme: Child nodes only 11

Comments n Misunderstand Akl-Tylor’s scheme q q n n Delete the dead-end node’s and relation may need to regenerate key Weird of formula N=Σ(di-1) q n Lack of t 8 in the example The value of ti t 1=2 t 5=2× 3× 11 t 2=2× 3 t 6=2× 3× 5× 13 t 3=2× 5 t 7=2× 5× 17 t 4=2× 3× 7 t 8=2× 5× 19 di should be the # of parent nodes The order of the children should be recorded 12
![Example K 1 K 2H 1K 1 K 3H 2K 1 H 1K 3 Example (K 1) (K 2=H 1(K 1)) (K 3=H 2(K 1)) [H 1(K 3)]](https://slidetodoc.com/presentation_image/4de238575e28e585ddd3c283d7c3d84e/image-13.jpg)
Example (K 1) (K 2=H 1(K 1)) (K 3=H 2(K 1)) [H 1(K 3)] [H 3(K 2)] (K 4=H 1(K 2)=H 1(K 1))) (K 8) (K 5=H 2(H 1(K 1))) (K 7) (K 6=H 3(K 2), H 1(K 3)) 13