Access Control Authentication and Public Key Infrastructure Lesson

Access Control, Authentication and Public Key Infrastructure Lesson 1 Access Control Framework, Assessing Risk, and Impact on Access Control © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved.
Access Control Enables an authorized person to control access to areas and resources in a given physical facility or computer-based information system Access Control, Authentication, and PKI © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 2

When and Where Is Access Control Needed? People need access to certain objects within the same or different systems to perform their work Sensitive data (human resources, payroll, mergers, acquisitions, and senior level personnel changes) needs protection Access Control, Authentication, and PKI © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 3
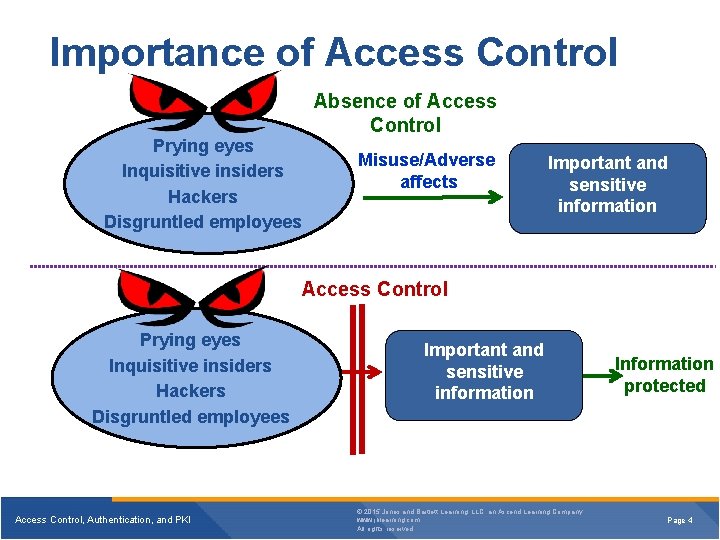
Importance of Access Control Prying eyes Inquisitive insiders Hackers Disgruntled employees Absence of Access Control Misuse/Adverse affects Important and sensitive information Access Control Prying eyes Inquisitive insiders Hackers Disgruntled employees Access Control, Authentication, and PKI Important and sensitive information © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Information protected Page 4

Primary Components of Access Control Policies: Defined from laws, requirements, and industry guides Subjects: People who need to access or are restricted from accessing Objects: Resources or information that need protection Access Control, Authentication, and PKI © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 5
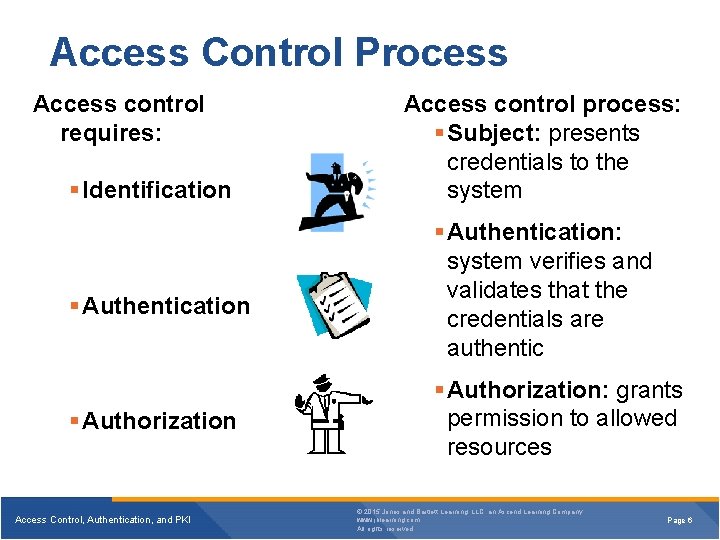
Access Control Process Access control requires: Identification Authentication Authorization Access Control, Authentication, and PKI Access control process: Subject: presents credentials to the system Authentication: system verifies and validates that the credentials are authentic Authorization: grants permission to allowed resources © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 6
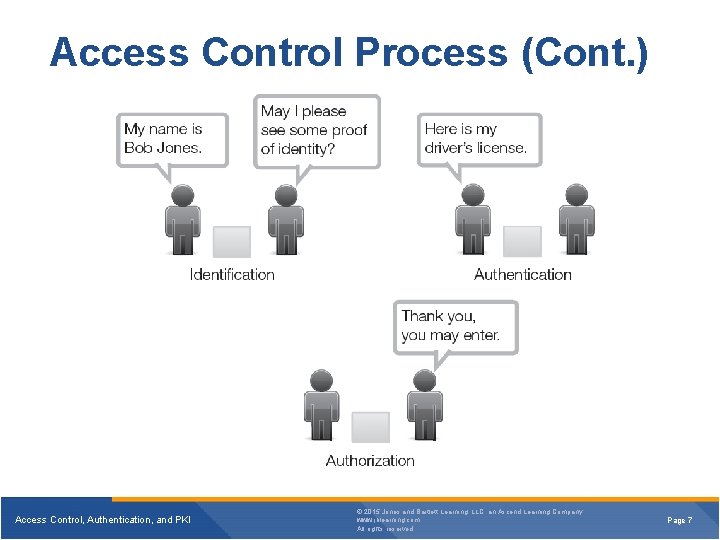
Access Control Process (Cont. ) Access Control, Authentication, and PKI © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 7

User IAA Process 2 1 3 2. 2 2. 3 1 Identification— user presents credentials: Account name and password (passphrase, tokens, and biometrics) Access Control, Authentication, and PKI 2 Authentication server operating system: 1. Receives and compares credentials with authorized credentials 2. If matched correctly, access granted otherwise denial notice sent to user 3 Authorization— mainframe application server or database: 1. Recognizes authorized credentials 2. Facilitates requests of authorized resources 3. Denies access to unauthorized resources © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 8
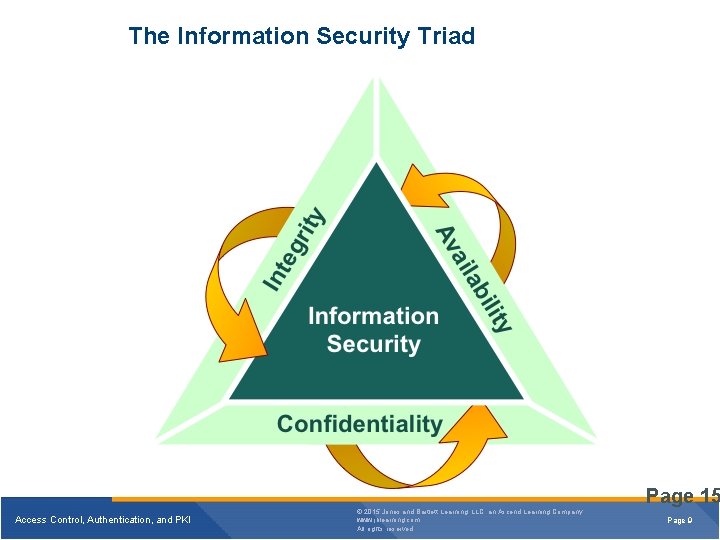
The Information Security Triad Page 15 Access Control, Authentication, and PKI © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 9

Logical Access Controls Who: Identity of subject What: Type of access being requested When: Combined with subject identity, access can be granted during one time period and denied at another time Where: Physical or logical location Why: Defined purpose for which access must be granted to a subject How: Type of access that can be granted to a subject Access Control, Authentication, and PKI © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 10
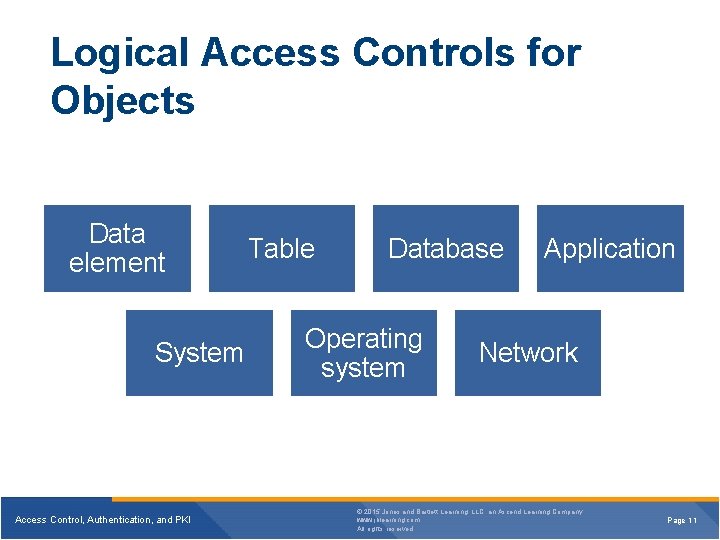
Logical Access Controls for Objects Data element System Access Control, Authentication, and PKI Table Database Operating system Application Network © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 11

Authentication Elements Authentication elements can be any of the following or a combination of the following elements: Something you know: password/passphrase, PIN number PIN - 9723 PASSWORD Drmb 9^w. X Something you are: biometrics, retina, fingerprint, facial Something you have: tokens, dongles, device Access Control, Authentication, and PKI © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 12
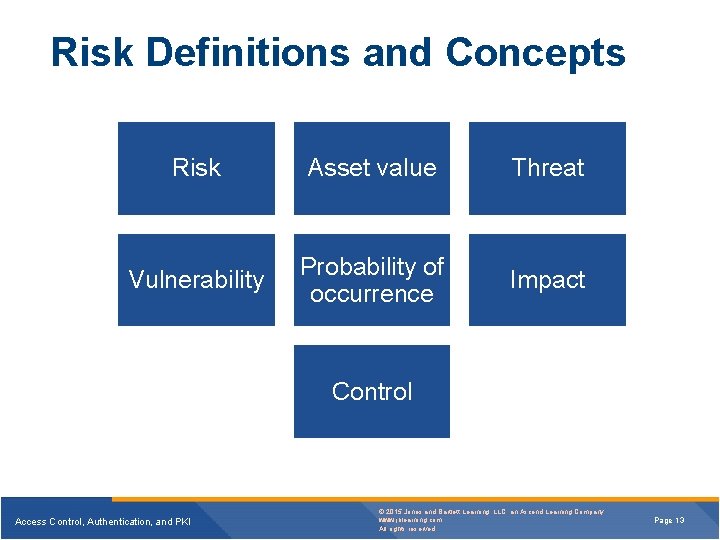
Risk Definitions and Concepts Risk Asset value Threat Vulnerability Probability of occurrence Impact Control Access Control, Authentication, and PKI © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 13

Risk Assessment Determine which risks exist in environment or may occur in future Measure level of risk by calculating the probability of occurrence and the potential impact on your environment Risk = Probability X Impact Access Control, Authentication, and PKI © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 14
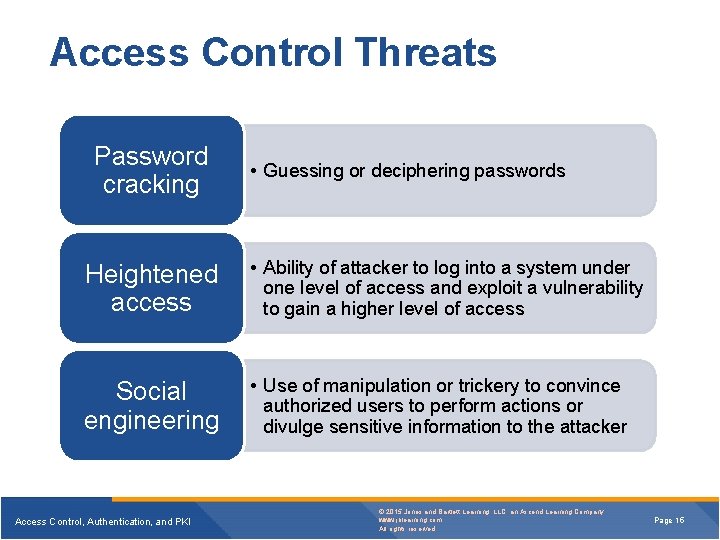
Access Control Threats Password cracking • Guessing or deciphering passwords Heightened access • Ability of attacker to log into a system under one level of access and exploit a vulnerability to gain a higher level of access Social engineering • Use of manipulation or trickery to convince authorized users to perform actions or divulge sensitive information to the attacker Access Control, Authentication, and PKI © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 15

Access Control Vulnerabilities Insecure passwords Insecure storage Insecure password hashes Insecure applications run at too high of a privilege level Users Access Control, Authentication, and PKI © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 16

Risk Assessment Quantitative Qualitative Access Control, Authentication, and PKI • Involves numeric data and calculations to identify and rank the risks facing an organization • Relies upon expert opinion rather than math © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 17
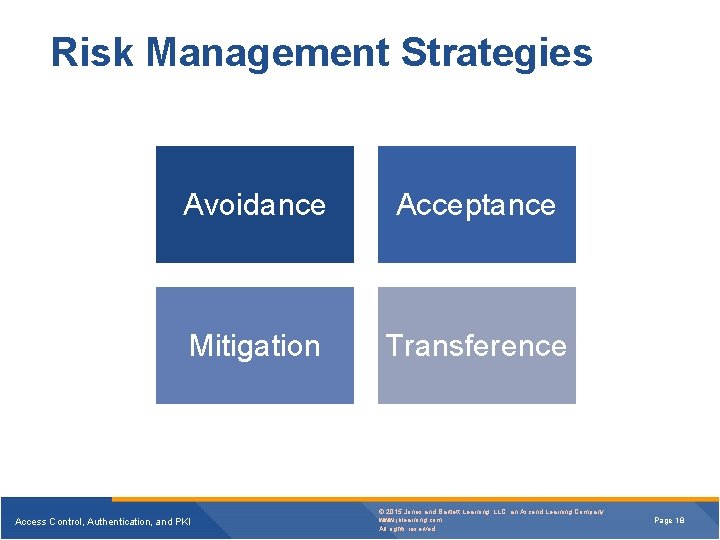
Risk Management Strategies Avoidance Acceptance Mitigation Transference Access Control, Authentication, and PKI © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 18

Considerations for Designing a Risk Assessment Create a risk assessment policy Define goals and objectives Describe a consistent approach or model Inventory all IT infrastructure and assets Determine the value of each asset Quantitatively or qualitatively Access Control, Authentication, and PKI © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 19

Considerations for Designing a Risk Assessment (Cont. ) Determine a “yardstick” or consistent measurement to determine the criticality of an asset Categorize each asset’s place within the infrastructure as critical, major, or minor Access Control, Authentication, and PKI © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 20
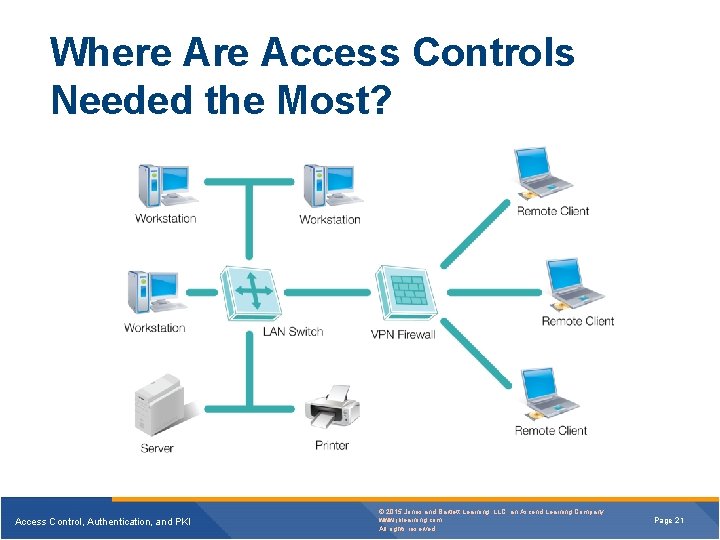
Where Access Controls Needed the Most? Access Control, Authentication, and PKI © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 21
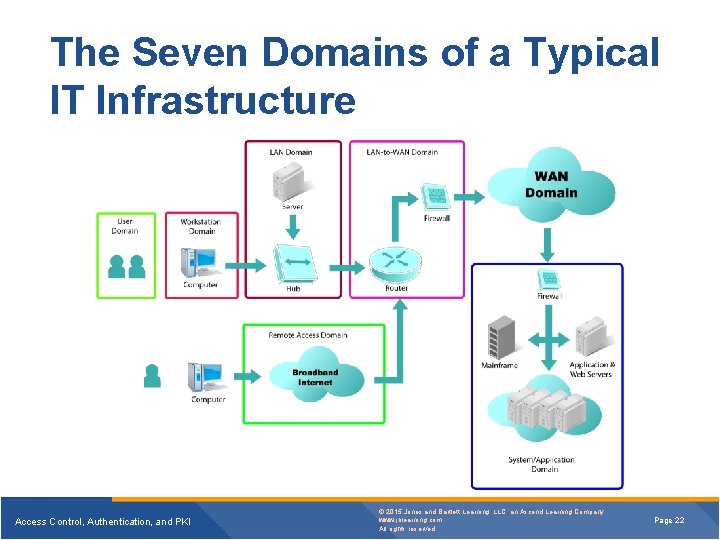
The Seven Domains of a Typical IT Infrastructure Access Control, Authentication, and PKI © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 22
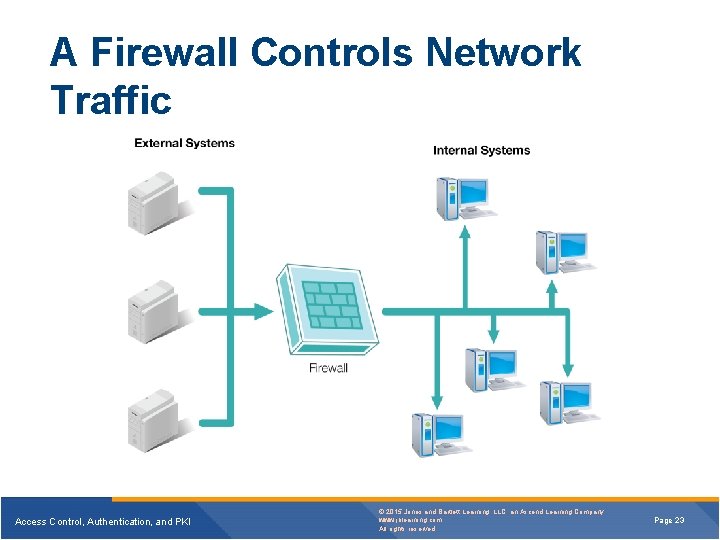
A Firewall Controls Network Traffic Access Control, Authentication, and PKI © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 23

Virtual Labs Configuring an Active Directory Domain Controller Managing Windows Accounts and Organizational Units Complete Labs 1 & 2 and Quizzes 1 and 2 Multiple attempts on quizzes Due on Sunday at 11: 59 PM EST Access Control, Authentication, and PKI © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 24
- Slides: 24