Access Control 113009 1 1 Access Control Two



























































































- Slides: 101

Access Control 11/30/09 1 1

Access Control • • Two parts to access control Authentication: Who goes there? • • Authorization: Are you allowed to do that? • • • Determine whether access is allowed Authenticate human to machine Authenticate machine to machine Once you have access, what can you do? Enforces limits on actions Note: Access control often used as synonym for authorization 11/30/09 2 2

Authentication • • Strong passwords Kerberos CHAP Digital Certificates 11/30/09 3

Who Goes There? • • How to authenticate a human to a machine? Can be based on… • Something you know • For example, a password • Something you have • For example, a smartcard • Something you are • For example, your fingerprint 11/30/09 4

2 - Factor Authentication • Requires 2 out of 3 of 1. 2. 3. • Something you know Something you have Something you are Examples • • ATM: Card and PIN Credit card: Card and signature Password generator: Device and PIN Smartcard with password/PIN 11/30/09 5

Something You Know • • Passwords Lots of things act as passwords! • • • PIN Social security number Mother’s maiden name Date of birth Name of your pet, etc. 11/30/09 6 6

Trouble with Passwords • “Passwords are one of the biggest practical problems facing security engineers today. ” • “Humans are incapable of securely storing highquality cryptographic keys, and they have unacceptable speed and accuracy when performing cryptographic operations. (They are also large, expensive to maintain, difficult to manage, and they pollute the environment. It is astonishing that these devices continue to be manufactured and deployed. )” 11/30/09 7

Why Passwords? • • • Why is “something you know” more popular than “something you have” and “something you are”? Cost: passwords are free Convenience: easier for SA to reset pwd than to issue user a new thumb 11/30/09 8

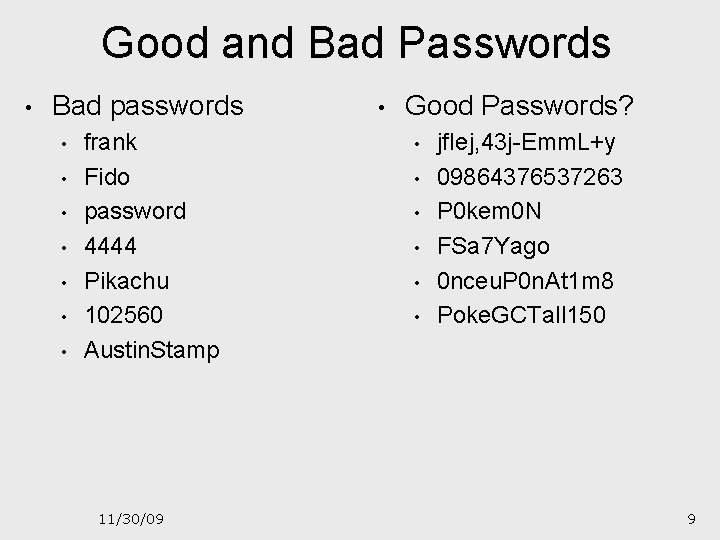
Good and Bad Passwords • Bad passwords • • frank Fido password 4444 Pikachu 102560 Austin. Stamp 11/30/09 • Good Passwords? • • • jf. Iej, 43 j-Emm. L+y 09864376537263 P 0 kem 0 N FSa 7 Yago 0 nceu. P 0 n. At 1 m 8 Poke. GCTall 150 9

Strong Passwords • • Minimum 6 to 8 characters in password At least one letter and one digit Case sensitive Avoid well-known substitutions • • • 0 for letter ‘O’ 2 for ‘to’ 4 for ‘for’ 5 for ‘S’ Set expiration date for password 11/30/09 10

Kerberos • • Developed at MIT in 1983 Meant for internal networks Passwords are sent in cleartext Developed for authenticating users in a single or multi-server environment Current version # is 5 Freeware (http: //web. mit. edu/is/help/kerberos) Sets up a key for every specified service for the authenticated user 11/30/09 11

Kerberos • How authentication works? • • • User logs in with userid and password User wants access to use a service (e. g. FTP) Request goes to an Authentication Server (AS) in encrypted form using the password of user AS verifies the user using the password associated with the userid AS sends two data items back to user. One of the data items is encrypted with user’s password. It is called the Ticket. The other data item is encrypted with the requested service’s master key, called the Session key. 11/30/09 12

Kerberos • The user decrypts the ticket with their password to verify that the response came from AS. Then the user creates an authenticator using their userid and timestamp. Finally, the user encrypts the authenticator with the session key and sends it to the service. The service decrypts the information with its master key and identifies the authenticator. Then the user is allowed to use the service. 11/30/09 13

Kerberos – Single service diagram User 1 Key Distribution Center 3 Authentication Server (AS) 4 2 Service 11/30/09 14

Kerberos • • The previous description is suited for a singleserver single-service environment. For multiserver multi-service environment a different authentication process is used. Upon initial login, the user is automatically authenticated and a Ticket-Granting Ticket (TGT) is created. The user sends the TGT for any service needed to the Ticket Granting Server (TGS) and obtains the necessary key to access the service. 11/30/09 15

Kerberos • Assumptions made by Kerberos systems: • • User has the correct password. Does not prevent dictionary attack to guess password Assumes physical security of all devices on the network Does not prevent denial of service attacks All authenticating devices must have their clocks synchronized in order for time stamps to match 11/30/09 16

Challenge Handshake Authentication Protocol • • • CHAP is a point-to-point protocol Used where hosts are connected to routers using switched circuits or dial-up lines Host asks the AS permission to use CHAP AS responds with permission to use CHAP AS sends a challenge message to host 11/30/09 17

Challenge Handshake Authentication Protocol • • Host selects a one-way hash function and hashes the message from AS. The hashed value is sent to AS. AS calculates the same hash value using the same hash function. If the values match then connection is maintained, otherwise the connection is terminated. Under CHAP, AS periodically sends challenge sequences to verify authenticity of host 11/30/09 18

Digital Certificates • • • Issued by trusted third parties known as Certificate Authorities (CAs) Verisign is a trusted third party Used to authenticate an individual or an organization Digital Certificates are usually given for a period of one year They can be revoked It is given at various security levels. Higher the security level, the CA verifies the authenticity of the certificate seeker more. 11/30/09 19

Digital Certificates • • Digital Certificates can be issued by any one as long as there are people willing to believe them Major CAs are: • • Verisign Geo. Trust Be. Trusted Thawte 11/30/09 20

Digital Certificates • • • Digital Certificates are part of the authentication mechanism. The other part is Digital Signature. When a user uses the digital signature, the user starts with their private key and encrypts the message and sends it. The receiver uses the sender’s public key and decrypts the message In traditional encryption, the sender uses the public key of the receiver and encrypts the message and sends it and the receiver decrypts the message with their private key 11/30/09 21

Digital Certificates • Additional authentication means used by CAs are: • • Security token Passive token Active token One time password 11/30/09 22

Digital Certificates • • • Security token is usually a hardware device such as a Smart Card If the security token is a software token, it is usually associated with a particular workstation Security tokens use two-factor authentication using a password and a device (or an appropriate hardware identifier) 11/30/09 23

Digital Certificates • • Passive token is a storage device that holds multiple keys. Appropriate key is transmitted using the transmission device used. Inexpensive to manufacture Sometimes an extra PIN is required to use the passive token Examples: • • Garage door opener ATM card 11/30/09 24

Digital Certificates • • • An Active token does not transmit any data, unlike a passive token Active tokens create another form of the base key (such as one-time password) or an encrypted form of the base key Smart cards are commonly used for active tokens 11/30/09 25

Digital Certificates • • A One-time password has a limited duration validity on a single use Generated using a counter-based token or a clock-based token Counter-based token is an active token that generates a one-time password based on a counter in the server and the secret key of the user Clock-based token is an active token that generates one-time passwords based on the server clock 11/30/09 26

Authentication vs Authorization • Authentication Who goes there? • • Authorization Are you allowed to do that? • • • Restrictions on who (or what) can access system Restrictions on actions of authenticated users Authorization is a form of access control Authorization enforced by • • Access Control Lists Capabilities 11/30/09 27

CAPTCHA • • • CAPTCHA Completely Automated Public Turing test to tell Computers and Humans Apart Automated test is generated and scored by a computer program Public program and data are public Turing test to tell… humans can pass the test, but machines cannot pass the test Like an inverse Turing test (sort of…) 11/30/09 28

CAPTCHA Paradox • • • “…CAPTCHA is a program that can generate and grade tests that it itself cannot pass…” “…much like some professors…” Paradox computer creates and scores test that it cannot pass! CAPTCHA used to restrict access to resources to humans (no computers) CAPTCHA useful for access control 11/30/09 29

CAPTCHA Uses? 1. Original motivation: automated “bots” stuffed ballot box in vote for best CS school 2. Free email services spammers used bots sign up for 1000’s of email accounts 1. CAPTCHA accts employed so only humans can get 3. Sites that do not want to be automatically indexed by search engines • • HTML tag only says “please do not index me” CAPTCHA would force human intervention 11/30/09 30

Do CAPTCHAs Exist? Test: Find 2 words in the following • • • Easy for most humans Difficult for computers (OCR problem) 11/30/09 31

CAPTCHA’s and AI 1. Computer recognition of distorted text is a challenging AI problem • 2. Same is true of distorted sound • 3. 4. 5. But humans can solve this problem Humans also good at solving this Hackers who break such a CAPTCHA have solved a hard AI problem Putting hacker’s effort to good use! May be other ways to defeat CAPTCHAs… 11/30/09 32

What is Ethics ? • • Study of what it means to "do the right thing" View ethical rules as • • fundamental & universal made up to provide a framework to interact with other people Behaving ethically is often practical Needs courage sometimes. . . 11/30/09 33

Ethics vs. Cyber. Ethics • Ethics: • • Set of principles or framework that you create to tell you what is right and what is wrong How you behave It defines who you are Cyber. Ethics: • • Application of ethics as related to computers and the Internet Includes responsible use of technology 11/30/09 34

Driving Without a License • • Can compare to a car • Can learn mechanics of driving a car Without laws/rules that govern that tool, results can be devastating • • • Accidents Hurt someone Using the Internet without a framework of responsible use can be just as devastating. 11/30/09 35

Real World vs. Virtual World Rules that apply to you in the real world apply to you in the virtual world or cyberspace. • Stealing • Giving out personal information • Copying someone else’s information • Reading someone else’s mail • Trashing someone’s personal property • Are these things okay to do in the Real World? • Then why would it be okay to do it in the virtual world? 11/30/09 36

Intellectual Property Rights • Intellectual property (IP)—creations of the mind, such as inventions, literary and artistic works, and symbols, names, images, and designs used in commerce © 11/30/09 ® 37

Intellectual Property Rights (cont. ) • Copyright—an exclusive grant from the government that allows the owner to reproduce a work, in whole or in part, and to distribute, perform, or display it to the public in any form or manner, including the Internet Digital watermarks—unique identifiers imbedded in digital content that make it possible to identify pirated works 11/30/09 38

Copyright Infringement • Enormous Potential for Abuse and Legal Action • “Who Will Ever Know…” • “Copyright Police” & Digital Tracking • Watermarks • Digital Download Trace • Web Bots & Search Spiders 11/30/09 39

Copyright • Copying and/or selling things that do not belong to you • • Movies - motion pciture Music CDs - sound recording Books - written text Artwork - graphic images, sculpture Architecture Computer programs - source codes After January 1, 1978 don’t need to copyright property 11/30/09 40

Copyrights • • • Anything that you produce is copyrighted. This includes written work, images, and audio. You own the rights to its reproduction, display, distribution, and adaptation to derivative works. Works before 1989 carry a copyright notice; works after 1989 do not. Official copyrighting gives you legal clout. 11/30/09 41

Intellectual Property • • Pirated software - the unauthorized use, duplication, distribution or sale of copyrighted software. Counterfeit software - software that is manufactured to look like the real thing and sold as such. 11/30/09 42

WHY INTELLECTUAL PROPERTY IS A SPECIAL ETHICAL ISSUE WHEN APPLIED TO SOFTWARE • • Easy to reproduce and distribute Tied to computer hardware Made possible a huge acceleration in the rate of innovation Can be used by several people at the same time 11/30/09 43

Copyright and Patent Protection Promoting Technical Progress Three theories: (a) The opportunity for profit from licensing software may be an incentive that entices good researchers to work on new software (b) Provides a way for researchers to openly publish their results (which would encourage future research based on their discoveries) while still making a profit from their works (c) Places society's resources in the hands of those most likely to use it for making future technological contributions 11/30/09 44

Plagiarism • Copying other people’s words and calling them your own • Turning in someone else’s homework • Copying off the internet and pasting it into your work without giving credit to the source 11/30/09 45

MP 3, Napster, and Intellectual Property Rights • The Problem • • • MP 3. com enabled users to listen to music from any computer with an Internet connection without paying royalties Napster supported the free distribution of music and other digitized content among millions utilizing peer-to-peer (P 2 P) technology These services could not be ignored because they could result in the destruction of millions of jobs and revenue 11/30/09 46

MP 3, Napster, and Intellectual Property Rights (cont. ) • The Solution • • Emusic. com filed a copyright infringement lawsuit against MP 3. com Copyright laws and copyright cases have been in existence for years but: • Were not written for digital content • Financial gain loophole was not closed 11/30/09 47

Internet Copyright Myths • No © Symbol Means No Copyright Exists • Material On the Net Is Automatically OK to Copy • It’s Free Advertising and Distribution for the Author • Attribution Makes Using the Material Legal • Copyrighted Material on a Free Website Is OK to Use • Material On the Web is Public Domain • I’m a teacher/student…Fair Use Protects Me 11/30/09 48

Copyright Myths • • • If it doesn’t have a copyright notice, it’s not copyrighted. If I don’t charge for it, it’s not a violation. If it’s on the Internet, it’s public domain. “My posting was just fair use!” “They e-mailed me a copy, so I can post it. ” 11/30/09 49

Fair Use: 4 Criteria All four criteria must be met to qualify as fair use. • • Purpose: Is it for educational, non-profit use? Nature: Is it a novel, short story, article, song, or movie? Consumables and works which require royalties may not be copied. Amount: How many copies are being made? Excessive quantities aren’t allowed. Effect: Is the creator being denied a profit due to copying? 11/30/09 50

Some Laws • The Digital Millennium Copyright Act (1998) • The Napster© Case • Hollywood vs. The DVD Hackers (De. CSS) • Strict Liability Applies • Statutory Damages of $20, 000 Per Case • $100, 000 Per Case for “Willful Infringement” • Fair Use DOES NOT Protect teachers/students 11/30/09 51

Privacy • Privacy—the right to be left alone and the right to be free of unreasonable personal intrusions • Two rules have been followed fairly closely in court decisions: 1. The right of privacy is not absolute. Privacy must be balanced against the needs of society 2. The public ’s right to know is superior to the individual’s right of privacy 11/30/09 52

Privacy/ Personal Information • • Freedom from being contacted without permission Infringe on other’s privacy - go where you’re not suppose to go Giving out any personal information on the Internet People lured to give information because of prizes or large amounts of money 11/30/09 53

Web-Site Self-Registration • Registration questionnaires 50% disclose personal information on a Web site for the chance to win a sweepstakes • Uses of the private information collected: • • • For planning the business May be sold to a third party Must not be used in an inappropriate manner 11/30/09 54

Cookies • Cookie—a small piece of data that is passed back and forth between a Web site and an end user’s browser as the user navigates the site; enables sites to keep track of users’ activities without asking for identification • • Cookies can be used to invade an individual’s privacy Personal information collected via cookies has the potential to be used in illegal and unethical ways 11/30/09 55

Protection of Privacy • • • Notice/awareness Choice/consent Access/participation Integrity/security Enforcement/redress • • Supported in the U. S. by the Federal Internet Privacy Protection Act Supported in the European Union by EU Data Protection Directive 11/30/09 56

Spam • Spamming—the practice of indiscriminately broadcasting messages over the Internet (e. g. , junk mail) • • • Spam comprised 25 to 50% of all e-mail Slows the internet in general; sometimes Shuts ISPs down completely Electronic Mailbox Protection Act ISPs are required to offer spam-blocking software Recipients of spam have the right to request termination of future spam from the same sender and to bring civil action if necessary 11/30/09 57

Privacy • E-mail is completely insecure. • Each e-mail you send results in at least 3 or 4 copies being stored on different computers. • You can take measures to protect your e-mail. 11/30/09 58

Privacy and Ethics • • Information privacy laws • • • Federal Privacy Act of 1974 Electronic Communications Privacy Act of 1986 Communications Act of 1996 HIPAA of 1996 Computer Security Act of 1987 Gramm – Leach – Bliley Act of 1999 USA PATRIOT Act of 2001 Sarbanes – Oxley Act of 2002 Ethical aspects of information handling 11/30/09 59

Information Privacy • • • Privacy refers to personally identifiable information about an individual or an organization Privacy does not mean absolute freedom from observation Privacy means “state of being free from unsanctioned intrusion” Financial and medical institutions treat privacy as part of their compliance requirements Information is collected by cookies and points of sale 11/30/09 60

Information Privacy • • Privacy is a risk management issue Ability to collect information from multiple sources and combine them in different ways have resulted in powerful databases that can shed more light than previously possible 11/30/09 61

Information Privacy Laws • Federal Privacy Act of 1974 • • Requires all government agencies from protecting the privacy information of individuals and businesses Certain agencies have exemption to release aggregate data • • • Census Bureau National Archives Congress Comptroller General Credit agencies 11/30/09 62

Information Privacy Laws • Electronic Communications Privacy Act of 1986 • • Regulates interception of wire, electronic, and oral communications Works in conjunction with the Fourth Amendment providing protection against unlawful search and seizure 11/30/09 63

Information Privacy Laws • Computer Security Act of 1987 • • • Deals with federal government’s information systems Mandates that all federal information systems containing classified information have security mechanisms built-in Requires periodic training for all people dealing with classified information about handling secure systems 11/30/09 64

Information Privacy Laws • Communications Act of 1996 • • Regulates interstate and international communications Communications decency was part of this Act 11/30/09 65

Information Privacy Laws • Health Insurance Portability and Accountability Act (HIPAA) of 1996 • • • Protect confidentiality and security of health care data Electronic signatures are allowed Patients have a right to know who have access to their information and who accessed it 11/30/09 66

Information Privacy Laws • HIPAA’s five core principles: • • • Consumer controls medical information Medical information can be used only within predefined boundaries People using the private information are accountable for its use Balance public impact on use of information over individual protection Provide security for all information 11/30/09 67

Information Privacy Laws • Gramm – Leach – Bliley Act of 1999 • • Deals with financial services Focuses on privacy aspects of information handling by banks, insurance companies, securities firms, and other financial service providers like tax preparers Emphasizes privacy of information held by these financial institutions Distinguishes between a customer and consumer Customer is one who has a continuing relationship with the provider such as a bank Consumer is one who uses the services of the provider occasionally, such as a check cashing service Only customers’ privacy is protected 11/30/09 68

Information Privacy Laws • USA PATRIOT Act of 2001 • • • Uniting and Strengthening America by Providing Appropriate Tools Required to Intercept and Obstruct Terrorism Gives extensive powers to the government to suspend notification provisions of existing laws Provides authorization for information search without knowledge of the individual 11/30/09 69

Sarbanes – Oxley Act • The law requires: • • The relevance for us is with reference to ethical aspects Establishment of a public company accounting oversight board Independence of auditor with respect to the company being audited Enhanced financial disclosures Conflicts of interest disclosure of people and firms involved in audit White collar crime penalty enhancements Corporate accountability 11/30/09 70

Access Device Fraud Act of 1984 (18 USC § 1029) • Bars interstate commerce in counterfeit access devices • Any unauthorized device designed or used for fraudulent access to resources • Money (funds transfers, payments. . . ) • Services (phone, network, cable TV. . . ) • • Includes credit cards obtained fraudulently or generated independently for fraud Also governs equipment for making such devices 11/30/09 71

Computer Fraud and Abuse Act of 1986 (18 USC § 1030) • • CFA is the most important US law governing behavior in cyberspace Protects federal-interest computers • • • Governments at any level Governmental agencies including military Financial institutions Medical institutions Contractors to these institutions 11/30/09 72

CFA cont’d • Prohibits unauthorized access • • • Obtaining or trafficking in confidential data Installing unauthorized software Mentions reckless disregard of consequences Fines up to $250, 000 & 5 years in prison Robert T. Morris Jr convicted under CFA • • Internet worm of 2 Nov 1988 90, 000 computers down for 1 -2 days 400 hours community service $10, 500 fine 3 years probation 11/30/09 73

Wire Fraud (18 USC § 1343) • • • Fraudulent activity involving interstate wire (electronic) communications Thus use of electronic communications in carrying out some other fraud exacerbates the crime Unauthorized access to confidential information • • Was not considered to be enough basis for conviction under Wire Fraud statutes Needed to show monetary damages 11/30/09 74

Wire Fraud (cont’d) • US v. Riggs & Neidorf 1990 • Robert Riggs obtained enhanced-911 manual illegally from Bell. South • Allegedly “secret” document worth “$100, 000” • • • Craig Neidorf altered document, posted on BBS Prosecuted under Wire Fraud Act Case collapsed • Actually turned out to be available to public for $13 11/30/09 75

Wire Fraud (cont’d) US v. La. Macchia (1994) • • • David La. Macchia was 21 year-old MIT student Invited anyone to upload and download illegal copies of proprietary software Could not be tried under copyright violations 18 USC § 506(a) because he derived no personal monetary benefit 11/30/09 76

Wire Fraud (cont’d) • • La. Macchia indicted under Wire Fraud statute Case dismissed • • • No money, no fraud SCOTUS ruled that illegal copies of intellectual property are not property that is “stolen, converted or taken by fraud” under Stolen Property Act Led directly to passage of the No Electronic Theft Act of 1997 • Removed requirement for financial gain from 17 USC § 506(a) as basis for prosecution 11/30/09 77

Criminal Infringement of Copyright (17 USC § 506 a) Copyright Act of 1976 (amended 1982) • Motives: • • • Method: • • • Commercial advantage Private financial gain Unauthorized reproduction or distribution 180 day period 1 or more copies of copyright work(s) Total retail value > $1, 000 Requirement: • Must show intent 11/30/09 78

Counterfeit Trademarks (18 USC § 2320) • Trademark Counterfeit Act of 1984 • • • Intentional trafficking in counterfeit goods and services Max penalties • • • “Trafficking in Counterfeit Goods or Services” $2 M + 10 years in jail for individual $5 M for corporate entity Repeat offenders • • $5 M + 20 years for recidivist $15 M for corporation 11/30/09 79

Mail Fraud (18 USC § 1341) • • • Use of U. S. Postal Service in furtherance of a fraud is itself a felony Use of e-mail and phone in such schemes also covered Pyramid sales schemes may be mail fraud • • • Junk e-mail includes list of names Put your name on list, remove oldest Send out useless instructions by US Mail US Postal Inspectors have declared the instructions to be pro forma only Can send copies of e-mail to Postmasters in each ZIP code for followup 11/30/09 80

Identity Theft and Assumption Deterrence Act (18 USC § 1028) • Identity theft fastest growing form of fraud today • • • Criminals use SSN, public records to establish line of credit in victim’s name Debts assigned to victim Burden of proof of innocence placed on victim Catastrophic results on innocent people Felony • Up to 20 years jail 11/30/09 81

RICO (18 USC § 1961) • • Racketeer Influenced and Corrupt Organizations Act Attacks organized crime groups • • • Racketeering includes violence, obscenity, fraud, interstate gambling, copyright violations. . Fines, imprisonment up to life, forfeiture Victims may sue for damages in civil court • • Recover triple damages + fees Controversial because of application to businesses not thought of as gangs 11/30/09 82

Wire and Electronic Communications Interception and Interception of Oral Communications (18 USC § 2511) • Prohibits interference with communications • • • Wire Oral Electronic Radio transmissions Several exceptions • • Consent given by one party (except in conspiracies) Lawful warrants FCC activities Intelligence gathering by US govt agents 11/30/09 83

Unlawful Access to Stored Communications (18 USC § 2701) • • Governs e-mail, stored and transmitted documents Intentional access without authorization Interference with access Government access permitted under warrant • • Provider of service must cooperate Penalties • • Max ½ to 2 years jail + fine Depends on purpose, recidivism 11/30/09 84

Electronic Communications Privacy Act of 1986* • Bars intentional attack on wire, oral or electronic communications including • • Interception Attempt to intercept Conspiracy to intercept Fines and imprisonment • • Felony to use content of illegally-intercepted communications if perpetrator knows or should know it was illegally obtained One party to a communication may authorize interception for lawful reason 11/30/09 85

ECPA (cont’d) • Communications carriers • • • May intercept, disclose and use client communications Must be as part of necessary procedures Or for property or rights protection Permission of sender or any recipient of a message can authorize disclosure or publication Wireless phone calls are also protected by ECPA • • Cellular mobile phones Wireless domestic phones 11/30/09 86

ECPA (cont’d) • ECPA does not apply to purely internal messaging • • • However, reasonable expectation of privacy may interfere with corporate surveillance Be sure to ensure NO expectation of privacy in use of corporate e-mail resources Smyth v. Pillsbury • • Smyth & other employees assured of confidentiality in use of company e-mail system & specifically told e-mail would not be used as grounds for termination of employment Pillsbury fired Smyth for “unprofessional” comments in email to supervisor Smyth sued Pillsbury for wrongful dismissal Judge dismissed case because he denied reasonable expectation of privacy in use of corporate e-mail 11/30/09 87

ECPA (cont’d) • Exceptions for law enforcement • • • With suitable warrant or subpoena Under emergency conditions Steve Jackson Games & Operation Sundevil • • • Related to the Bell. South claims against Riggs and Neidorf concerning 911 documentation Secret Service raided Steve Jackson Games and thought games manuals were hacking instructions (!) Seized SJG’s computers & deleted data from disks Caused layoffs, delays in publishing, serious $$ losses Jackson sued, alleging violations of ECPA Judge decided in favor of SJG: search and seizure of computers not warranted under ECPA 11/30/09 88

Cyber Stalking • • • 47 United States Code 223 telecommunications harassment statute Amended January 5, 2006 Section 113 of the Violence Against Women Act - addition to 47 USC 223 11/30/09 89

Section 113 • • Prohibits anyone from using a telephone or telecommunications device without disclosing his identity and with intent to annoy, abuse, threaten, or harass any person Penalties: Up to 2 years imprisonment or fines 11/30/09 90

Spam “Spam accounts for 9 out of every 10 emails in the United States. ” Message. Labs, Inc. , an email management and security company based in New York. “We do not object to the use of this slang term to describe UCE (unsolicited commercial email), although we do object to the use of the word “spam” as a trademark and the use of our product image in association with that term” www. hormel. com 11/30/09 91

Can-Spam Act of 2003 • • Controlling the Assault of Non-Solicited Pornography and Marketing Act (Can-Spam) Signed into law by President Bush on Dec 16, 2003 • • Took effect Jan 1, 2004 Unsolicited commercial email must: • • • Be labeled Include Opt-Out instructions No false headers • FTC is authorized (but not required) to establish a “do-not-email” registry • www. spamlaws. com –lists all the latest in federal, state, and international laws 11/30/09 92

The Hacker Ethic Argue that they follow an ethic that both guides their behavior and justifies their break-ins • All information should be free • Belongs to everyone and there should be no boundaries or restraints to prevent anyone from examining information 11/30/09 93

Implications • • Privacy is no longer possible Not individual property • • Anyone may access / alter Loss of control Accuracy cannot be trusted Economic arguments • Expense of info collection and protection 11/30/09 94

The Idle System Argument • Systems not in service to provide a generalpurpose user environment • • Used in commerce, medicine, public safety, research, and government functions Unused capacity is present for future needs and sudden surges of activity 11/30/09 95

The Student Hacker Argument • Doing no harm and changing nothing • simply learning about how computer systems operate or write complex programs Arguments against • Not educational • Intruder can cause accidental damage • Systems could not be fully trusted 11/30/09 96

The Social Protector Argument • • Hackers break into systems to watch for instances of data abuse and to help keep "Big Brother" at bay Protectors rather than criminals Arguments against • Ends justify means – assumes ability to achieve good end • Resulted in more data restrictions 11/30/09 97

THE TEN COMMANDMENTS FOR COMPUTER ETHICS from the Computer Ethics Institute ✔ ✔ ✔ ✔ ✔ Thou shalt not use a computer to harm other people. Thou shalt not interfere with other people's computer work. Thou shalt not snoop around in other people's files. Thou shalt not use a computer to steal. Thou shalt not use a computer to bear false witness. Thou shalt not use or copy software for which you have not paid. Thou shalt not use other people's computer resources without authorization. Thou shalt not appropriate other people's intellectual output. Thou shalt think about the social consequences of the program you write. Thou shalt use a computer in ways that show consideration and respect. 11/30/09 98

Assessment #2 • 75 Questions • • • Books and Notes Week 8 • • Wk 8 – 15, Wk 9 – 7, Wk 10 – 13, Wk 11 – 10, Wk 12 – 10, Wk 13 – 16, BONUS - 4 Access control, firewall types, NAT, PAT, Cisco PIX, limitations, defense in depth, diversity of defense Week 9 • VPN definition, devices used, features, limitations, protocols, uses 11/30/09 99

Assessment #2 • Week 10 • • Week 11 • • IDS types, actions it can take, types of attacks they can see, False Positives/Negatives, etc. Disaster Recovery, backups, site locations, Cold/Warm/Hot sites, Acceptable Use Policies, Incident Response Policies & Team members, Business Continuity Plans Week 12 • Biometrics technical properties, major components, Type I/II Errors, characteristics each method uses, Static/Dynamic, Multimode 11/30/09 100

Assessment #2 • Week 13 • Authentication, Kerberos, RADIUS, laws, ethics, CAPTCHA, copyrights, patents 11/30/09 101