Abstract Enterprise businesses trust ITADs to securely destroy
Abstract Enterprise businesses trust ITADs to securely destroy their IT assets to the point that data cannot be recovered. Adding an additional level of security with software-based data erasure guarantees that even the most challenging IT assets (like SSDs) are completely wiped prior to destruction. Erasure also fits within Article 17 of GDPR requirements, the ‘Right to Erasure, ’ which requires businesses to permanently remove customer information upon request. Learn how you can prepare your organization to meet these requirements in this session with Fredrik Forslund, Director of Cloud and Data Center Erasure Solutions for Blancco Technology Group. Blancco Proprietary & Confidential. Do Not Copy or Distribute. Copyright © 2018 Blancco Oy Ltd. All rights reserved.

Meet GDPR ‘Right to Erasure’ Requirements: Erase Customer Data Permanently & Securely Fredrik Forslund, VP Enterprise & Cloud Erasure Solutions, Blancco Proprietary & Confidential. Do Not Copy or Distribute. Copyright © 2018 Blancco Oy Ltd. All rights reserved.

1995 Blancco Proprietary & Confidential. Do Not Copy or Distribute. Copyright © 2018 Blancco Oy Ltd. All rights reserved.

Directive 95/46/EC is adopted The European Data Protection Directive (Directive 95/46/EC) on the protection of individuals with regard to the processing of personal data and on the free movement of such data is adopted. Blancco Proprietary & Confidential. Do Not Copy or Distribute. Copyright © 2018 Blancco Oy Ltd. All rights reserved. 1995 24/10/1995

1997 Blancco Proprietary & Confidential. Do Not Copy or Distribute. Copyright © 2018 Blancco Oy Ltd. All rights reserved.

1997 Blancco Proprietary & Confidential. Do Not Copy or Distribute. Copyright © 2018 Blancco Oy Ltd. All rights reserved.

The General Data Protection Regulation will apply from this day Did you know? Appointment of a Data Protection Officer Some organisations, for instance those whose core activities involve regular and systematic monitoring of personal or sensitive data on a large scale as well as public sector organisations, will have to appoint a Data Protection Officer to ensure they comply with the GDPR. Blancco Proprietary & Confidential. Do Not Copy or Distribute. Copyright © 2018 Blancco Oy Ltd. All rights reserved. 2018 25/05/2018: “In the UK, it is echoed by an almost identical Data Protection Bill”
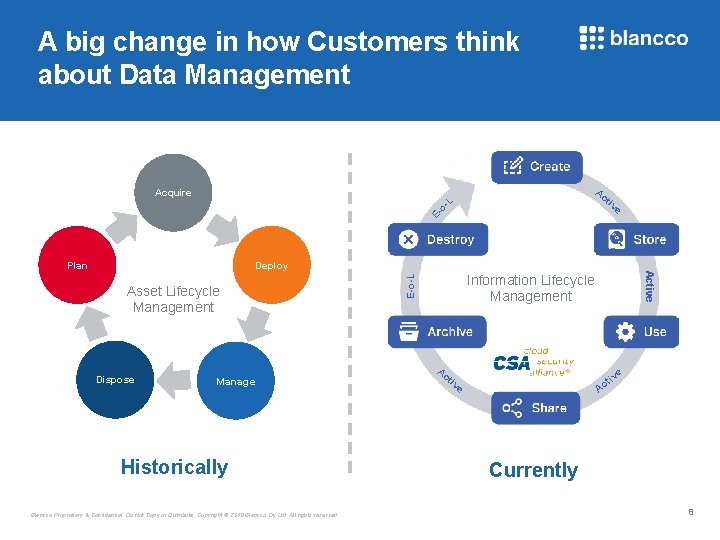
A big change in how Customers think about Data Management Ac Acquire L tiv E- o- e Deploy Dispose Manage Historically Blancco Proprietary & Confidential. Do Not Copy or Distribute. Copyright © 2018 Blancco Oy Ltd. All rights reserved. Information Lifecycle Management E-o-L Asset Lifecycle Management Active Plan Ac iv tiv e t Ac e Currently 8
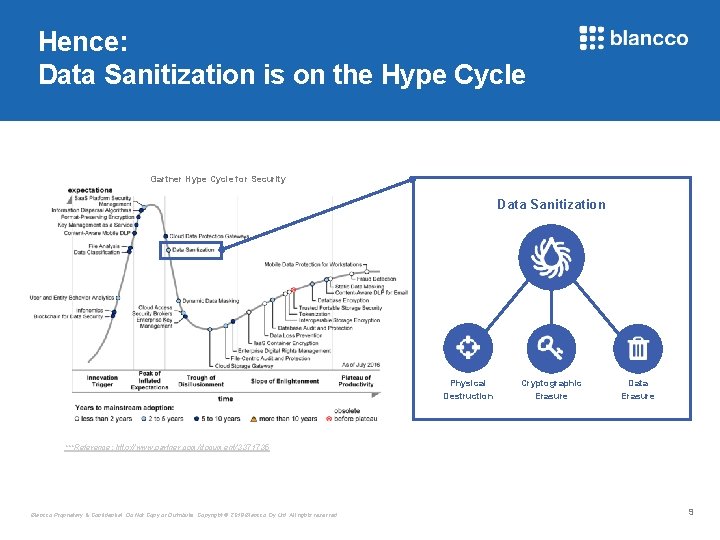
Hence: Data Sanitization is on the Hype Cycle Gartner Hype Cycle for Security Data Sanitization Physical Destruction Cryptographic Erasure Data Erasure ***Reference: http: //www. gartner. com/document/3371735 Blancco Proprietary & Confidential. Do Not Copy or Distribute. Copyright © 2018 Blancco Oy Ltd. All rights reserved. 9
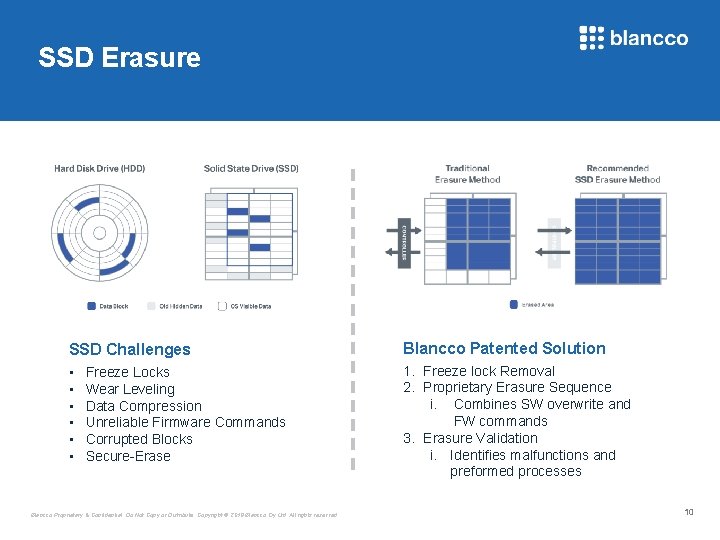
SSD Erasure SSD Challenges Blancco Patented Solution • • • 1. Freeze lock Removal 2. Proprietary Erasure Sequence i. Combines SW overwrite and FW commands 3. Erasure Validation i. Identifies malfunctions and preformed processes Freeze Locks Wear Leveling Data Compression Unreliable Firmware Commands Corrupted Blocks Secure-Erase Blancco Proprietary & Confidential. Do Not Copy or Distribute. Copyright © 2018 Blancco Oy Ltd. All rights reserved. 10

The greater of € 20 million or 4% of global annual turnover Consequences are Steep Based on several factors: Whether the infringement was intentional or negligent Whether the controller or processor took any steps to mitigate the damage Technical and organizational measures that had been implemented by the controller or processor Prior infringements by the controller or processor The degree of cooperation with the regulator The types of personal data involved The way the regulator found out about the infringement Blancco Proprietary & Confidential. Do Not Copy or Distribute. Copyright © 2018 Blancco Oy Ltd. All rights reserved. 11
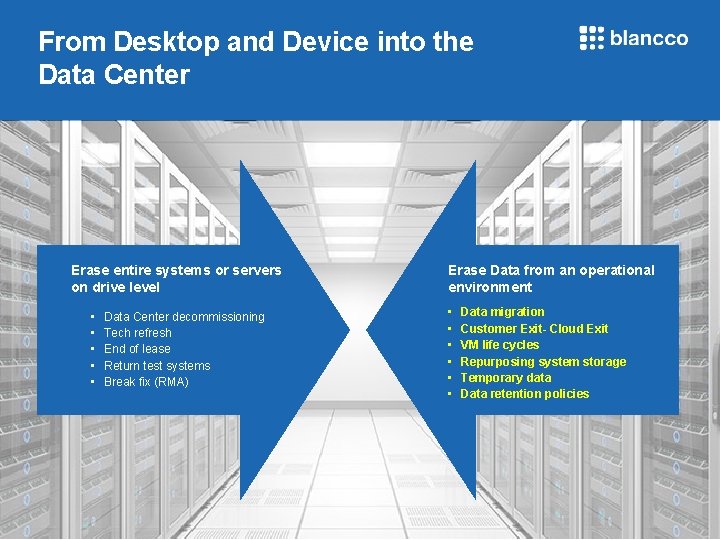
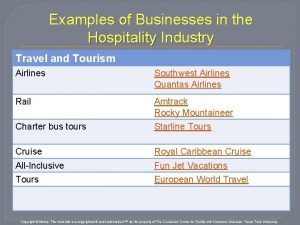
From Desktop and Device into the Data Center Erase entire systems or servers on drive level • • • Data Center decommissioning Tech refresh End of lease Return test systems Break fix (RMA) Blancco Proprietary & Confidential. Do Not Copy or Distribute. Copyright © 2018 Blancco Oy Ltd. All rights reserved. Erase Data from an operational environment • • • Data migration Customer Exit- Cloud Exit VM life cycles Repurposing system storage Temporary data Data retention policies
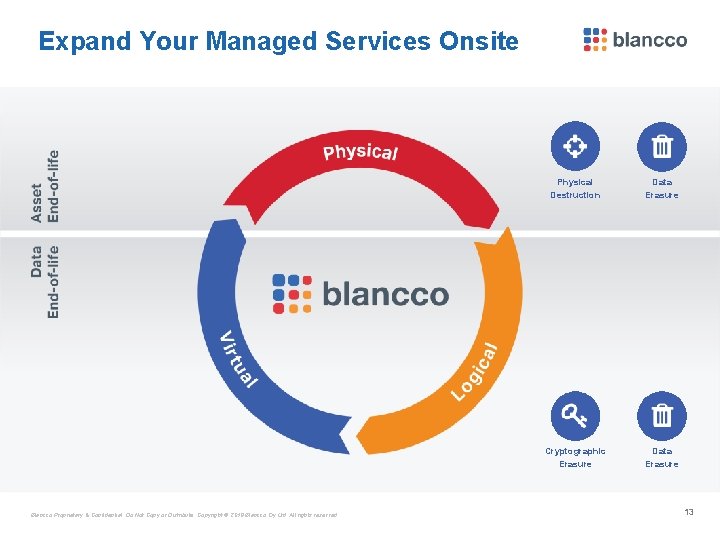
Expand Your Managed Services Onsite Blancco Proprietary & Confidential. Do Not Copy or Distribute. Copyright © 2018 Blancco Oy Ltd. All rights reserved. Physical Destruction Data Erasure Cryptographic Erasure Data Erasure 13

Example Use Case Requirement Secure data erasure for customer exit Regulatory need to remove customer details using a certified solution Customer details on SMB shares, local & hosted email & paper How Discovery using standard MS Windows tools Blancco File Eraser erases mailboxes & files, “freespace” tool Secure report generated for every erasure performed Timeline Sales cycle approx. 2 weeks. Execution of project 2 days on site. Blancco Proprietary & Confidential. Do Not Copy or Distribute. Copyright © 2018 Blancco Oy Ltd. All rights reserved. 14
Mitigate Risks Posed by Dark Data According to Veritas Global Databerg Report, 85% of Stored Data Is Either Dark or Redundant, Obsolete, or Trivial (ROT) Blancco Proprietary & Confidential. Do Not Copy or Distribute. Copyright © 2018 Blancco Oy Ltd. All rights reserved.

What are the Negatives Associated with Hoarding Data? • Cost • Compliance • Increased attack surface • Readiness to respond to customer request Blancco Proprietary & Confidential. Do Not Copy or Distribute. Copyright © 2018 Blancco Oy Ltd. All rights reserved. 16
Calculate Your Customers’ Cost Savings Cost of Cloud Storage Vs. Data Erasure 350 Blancco Proprietary & Confidential. Do Not Copy or Distribute. Copyright © 2018 Blancco Oy Ltd. All rights reserved. 17
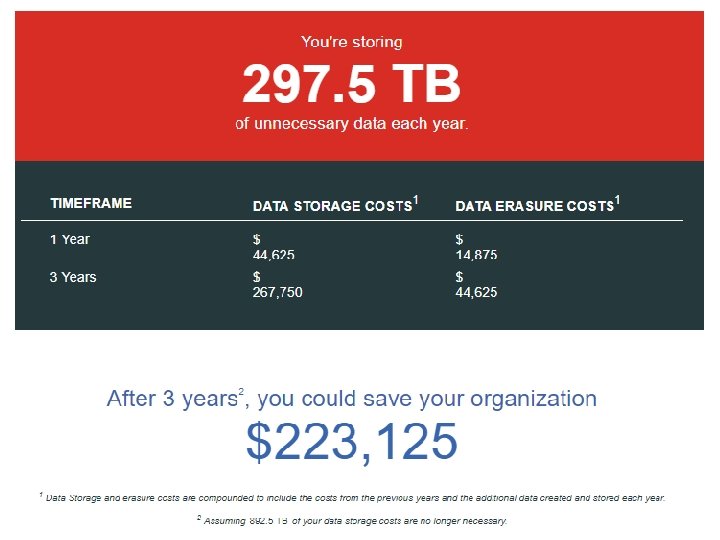
Blancco Proprietary & Confidential. Do Not Copy or Distribute. Copyright © 2018 Blancco Oy Ltd. All rights reserved.

Data Retention! Blancco Proprietary & Confidential. Do Not Copy or Distribute. Copyright © 2018 Blancco Oy Ltd. All rights reserved.

‘The Right to be Forgotten’ Article 17 of the new regulation focuses on the right to erasure. Blancco Proprietary & Confidential. Do Not Copy or Distribute. Copyright © 2018 Blancco Oy Ltd. All rights reserved. • Data subject will have the right to obtain from the controller the erasure of personal data concerning him or her • The controller shall have the obligation to erase personal data without undue delay • The controller shall take reasonable steps, including technical measures, to inform controllers of any links to, or copy or replication of, of the data subject’s personal data 20
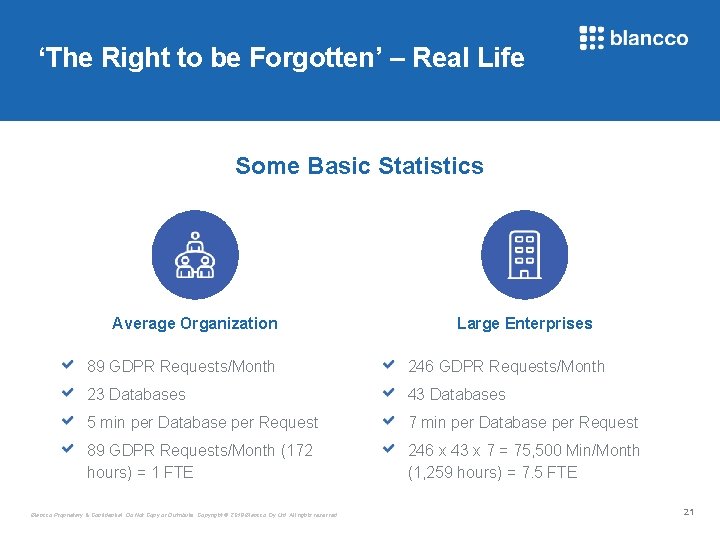
‘The Right to be Forgotten’ – Real Life Some Basic Statistics Average Organization Large Enterprises 89 GDPR Requests/Month 246 GDPR Requests/Month 23 Databases 43 Databases 5 min per Database per Request 7 min per Database per Request 89 GDPR Requests/Month (172 hours) = 1 FTE 246 x 43 x 7 = 75, 500 Min/Month (1, 259 hours) = 7. 5 FTE Blancco Proprietary & Confidential. Do Not Copy or Distribute. Copyright © 2018 Blancco Oy Ltd. All rights reserved. 21
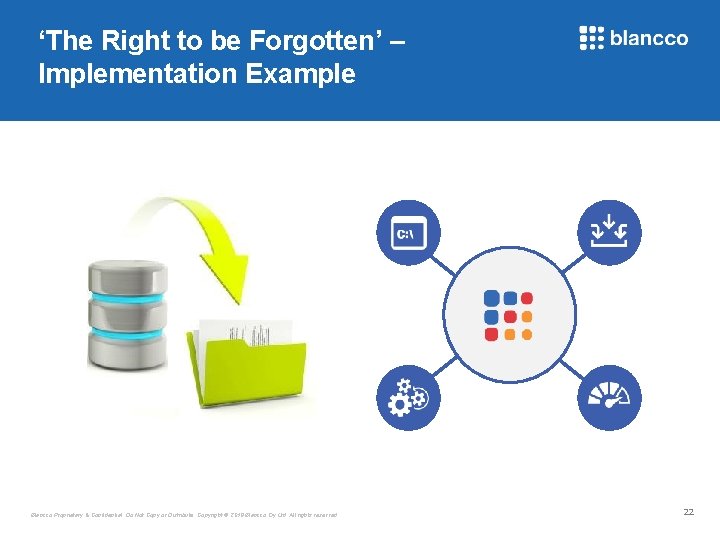
‘The Right to be Forgotten’ – Implementation Example Blancco Proprietary & Confidential. Do Not Copy or Distribute. Copyright © 2018 Blancco Oy Ltd. All rights reserved. 22

Challenge! Provide Customers with a Certificate or Proof of Erasure Blancco Proprietary & Confidential. Do Not Copy or Distribute. Copyright © 2018 Blancco Oy Ltd. All rights reserved.
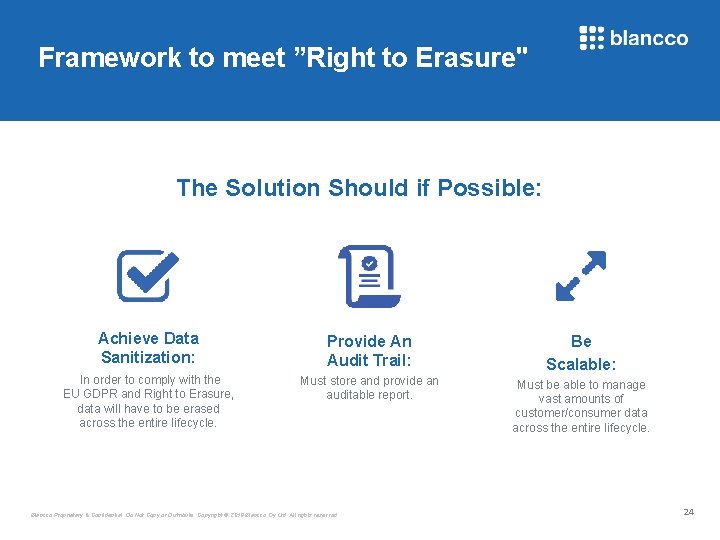
Framework to meet ”Right to Erasure" The Solution Should if Possible: Achieve Data Sanitization: Provide An Audit Trail: In order to comply with the EU GDPR and Right to Erasure, data will have to be erased across the entire lifecycle. Be Scalable: Must store and provide an auditable report. Must be able to manage vast amounts of customer/consumer data across the entire lifecycle. Blancco Proprietary & Confidential. Do Not Copy or Distribute. Copyright © 2018 Blancco Oy Ltd. All rights reserved. 24

Already a Billion Dollar Industry • Legal advisers • Consultants • Hiring of DPOs globally • How can you make this into an opportunity for you? – Enterprise- create efficient process and gain consumer trust and confidence. Have no data leaks! – ITADs or other service providers- go on-site, help with additional use cases and pain points. Blancco Proprietary & Confidential. Do Not Copy or Distribute. Copyright © 2018 Blancco Oy Ltd. All rights reserved. 25

Examples from a large Global TELCO RFP published in end of January • Provide a report of the legal requirements (legal compliance risks) in the 15 operating offices across EU • Perform Gap Assessment and Identify each gap across all operations and highlight the consequences of noncompliance in each instance and a suggested corrective action plan • Map all personal data across the organization, including the data owners, current storage and processing practices • Provide draft policies on data protection, classification and retention for the use in the organization • Investigation and advice on potential historic or current data breaches Blancco Proprietary & Confidential. Do Not Copy or Distribute. Copyright © 2018 Blancco Oy Ltd. All rights reserved. 26

Continued • Provide a short monthly update report to the Chief Finance Officer, HR Director, Technical Director and Chief Executive of progress made and key concerns arising during project • Guidance to write the Consent for (Employees, Customers, Adults, Children, Website, etc. ) • Review the third party’s contracts (Processors) to be compliant with the GDPR • Perform risk management and risk treatment plan – Data Protection Impact Assessment Blancco Proprietary & Confidential. Do Not Copy or Distribute. Copyright © 2018 Blancco Oy Ltd. All rights reserved. 27

Continued • Create Incident Management Policy complied with the GDPR • Develop Data Retention and Destruction Policy • Network topology – a high level view of the environment. • Data Classification or Data Impact Assessment report/output Blancco Proprietary & Confidential. Do Not Copy or Distribute. Copyright © 2018 Blancco Oy Ltd. All rights reserved. 28
Blancco Proprietary & Confidential. Do Not Copy or Distribute. Copyright © 2018 Blancco Oy Ltd. All rights reserved. 29

Thank You! Fredrik Forslund VP Enterprise & Cloud Erasure Solutions fredrik. forslund@blancco. com Blancco Proprietary & Confidential. Do Not Copy or Distribute. Copyright © 2018 Blancco Oy Ltd. All rights reserved.
- Slides: 30