Abstract 1 2 3 4 A new method

Abstract 1) 2) 3) 4) A new method to support UMTS WLAN vertical handover using SCTP Interworking techniques and architectures for WLAN 3 G integration toward 4 G mobile data networks IEEE 802. 11 roaming and authentication in wireless LAN cellular mobile networks 心得
Magazine 1 l A new method to support UMTS WLAN vertical handover using SCTP
Note Abstract l l l UMTS networks and WLANs Third generation cellular networks UMTS/WLAN vertical handover problem Overview of Mobile SCTP VERTICAL HANDOVER PROCEDURES
UMTS networks and WLANs l UMTS l WLANs • wide area connectivity • low data rate • high mobility • higher data rate • low mobility
Third generation cellular networks l Both UMTS and WLANs • WLAN offer higher bandwidth • Mobile users accessing the Internet via UMTS/WLAN are free to move • Handover between UMTS and WLANs • MIP from IETF • provides transparent support for host mobility • routing architecture of mobile host • Difficult to maintain the continuity between UMTS and WLAN • Point of this article
UMTS/WLAN vertical handover problem l UMTS/WLAN verti cal handover support via two types of SCTP • single homing asymmetric config uration • dual homing symmetric configu ration l Inte grated UMTS/WLAN network architecture • tightly coupled solutions :connect UMTS and WLAN • loose coupling solutions :separate out UMTS and • WLAN loose coupling offers several advantages over tight coupling
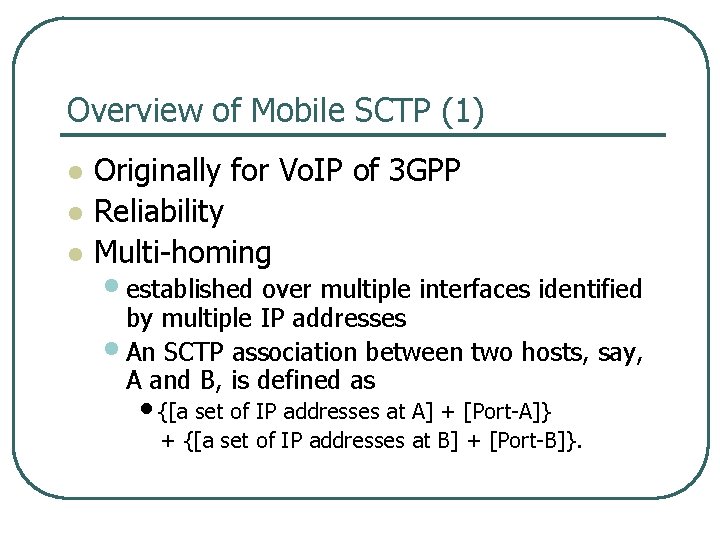
Overview of Mobile SCTP (1) l l l Originally for Vo. IP of 3 GPP Reliability Multi homing • established over multiple interfaces identified by multiple IP addresses • An SCTP association between two hosts, say, A and B, is defined as • {[a set of IP addresses at A] + [Port A]} + {[a set of IP addresses at B] + [Port B]}.

Overview of Mobile SCTP (2) l l base version of SCTP cannot be used directly to support UMTS/ WLAN vertical handover Fortunately, the recently proposed DAR extension for SCTP enables the endpoints to add, delete, or change the IP addresses during an active SCTP association using address configuration (ASCONF) messages. • basis of m. SCTP
Overview of Mobile SCTP (3) l m. SCTP • Using for supporting UMTS/WLAN vertical handover • capabilities to add, delete, and change the IP addresses dynamically during an active SCTP association
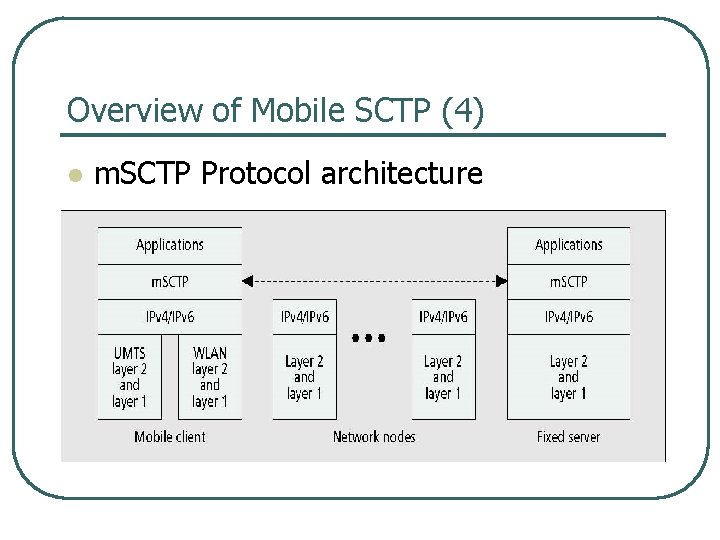
Overview of Mobile SCTP (4) l m. SCTP Protocol architecture
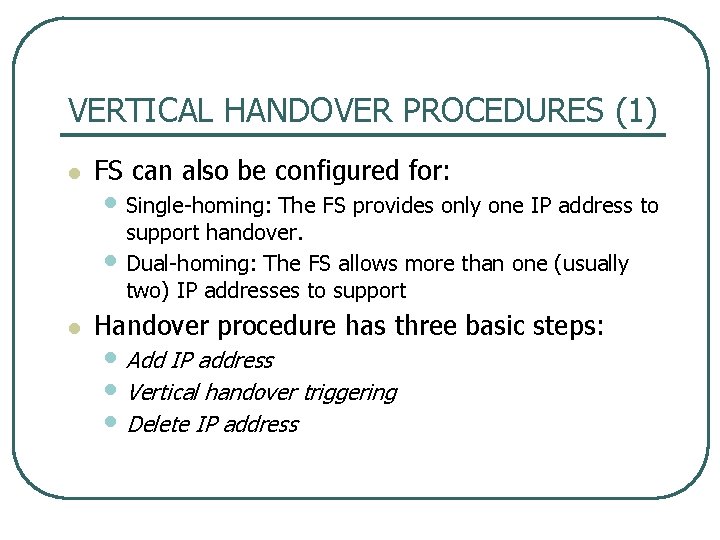
VERTICAL HANDOVER PROCEDURES (1) l FS can also be configured for: • Single homing: The FS provides only one IP address to • l support handover. Dual homing: The FS allows more than one (usually two) IP addresses to support Handover procedure has three basic steps: • Add IP address • Vertical handover triggering • Delete IP address
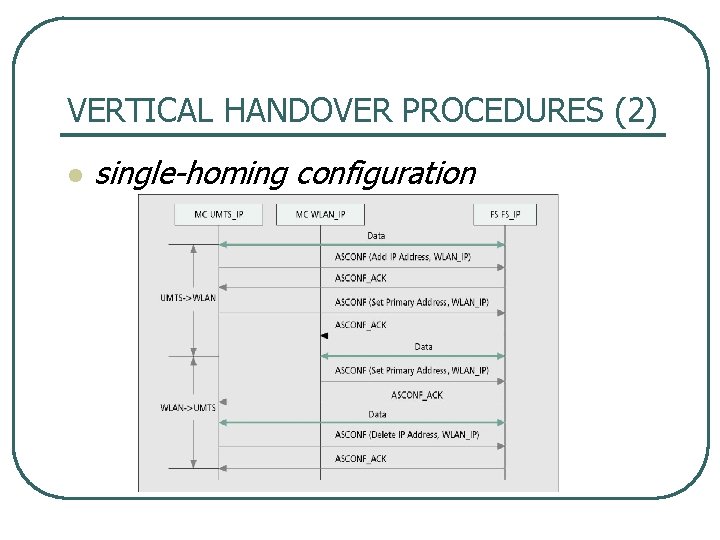
VERTICAL HANDOVER PROCEDURES (2) l single homing configuration
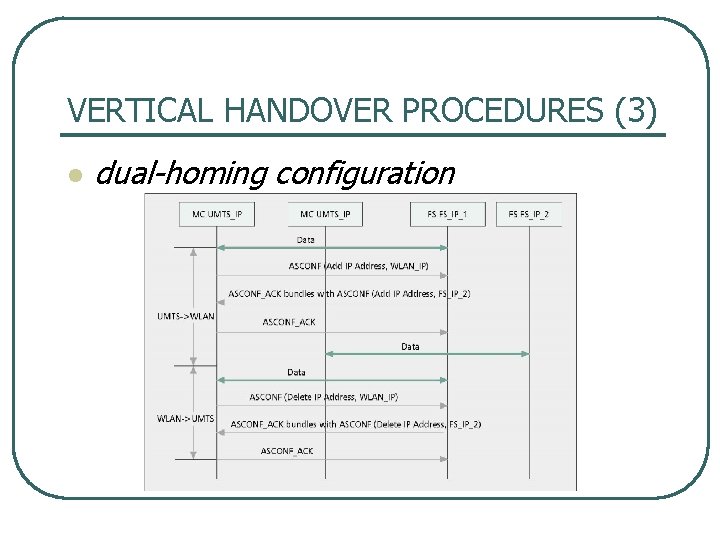
VERTICAL HANDOVER PROCEDURES (3) l dual homing configuration
SIMULATION RESULTS AND DISCUSSIONS (1) l use network simulator ns 2 to perform the simulations and obtain • set to be 384 kb/s for the UMTS link and 2 Mb/s for the WLAN link • delay is set to 100 ms • FTP traffic is started at the MC at time 1 s • handover triggering process is acti vated at time 5 s
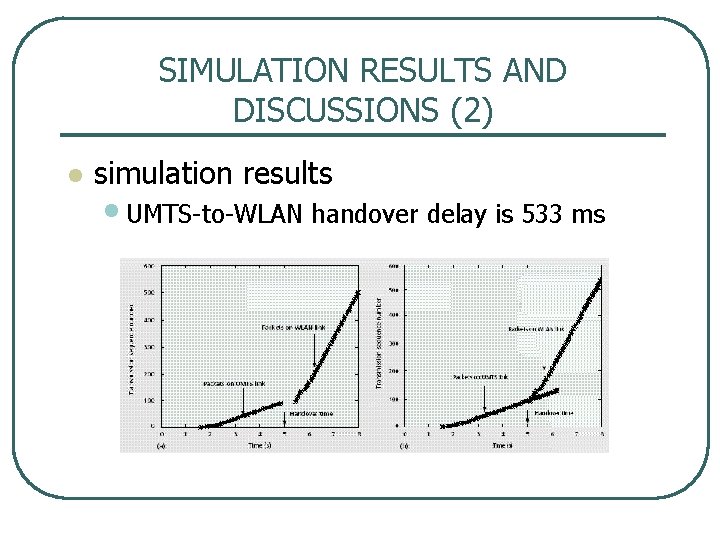
SIMULATION RESULTS AND DISCUSSIONS (2) l simulation results • UMTS to WLAN handover delay is 533 ms
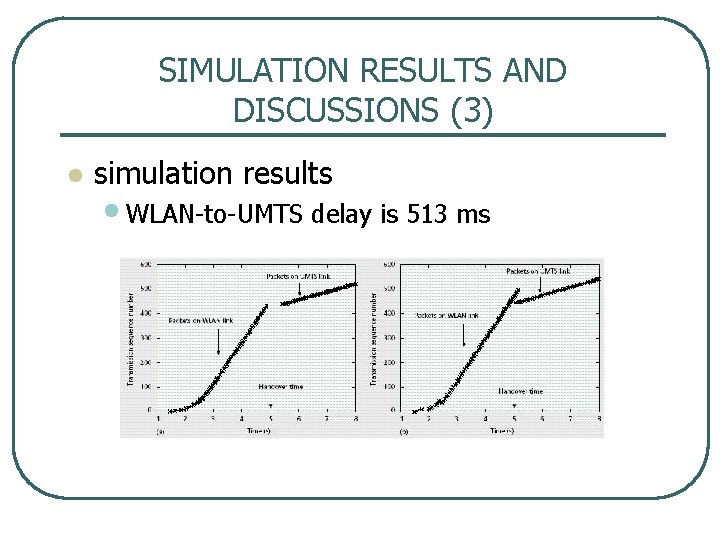
SIMULATION RESULTS AND DISCUSSIONS (3) l simulation results • WLAN to UMTS delay is 513 ms
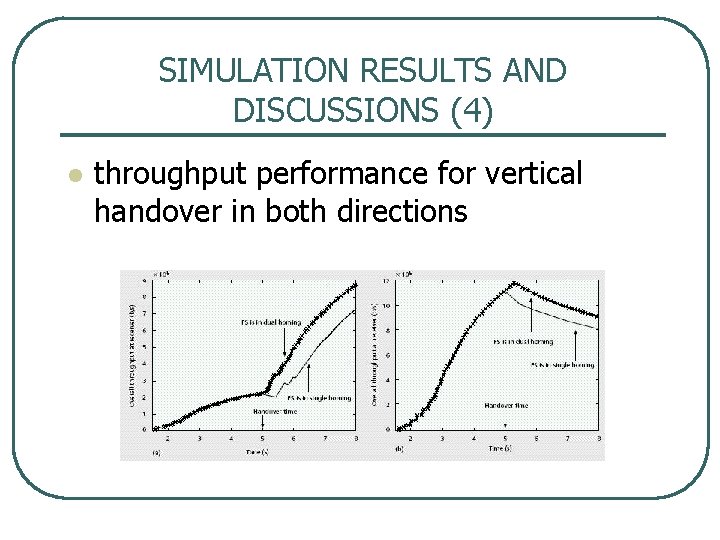
SIMULATION RESULTS AND DISCUSSIONS (4) l throughput performance for vertical handover in both directions

Magazine 2 l Interworking techniques and architectures for WLAN 3 G integration toward 4 G mobile data networks
Note Abstract l WLAN/3 G inter workingfunction INTERWORKING MODEL AND REQUIREMENTS NETWORK SELECTION INTERWORKING SCENARIOS 3 G Based Access Control and Charging l Access to 3 G Packet Switched Services l CONCLUSIONS l l • REFERENCE POINTS
WLAN/3 G inter workingfunction l WLAN/3 G inter workingtechniques and architectures can support • Authentication • Authorization • Accounting • WLAN sharing • Consis tent service provisioning
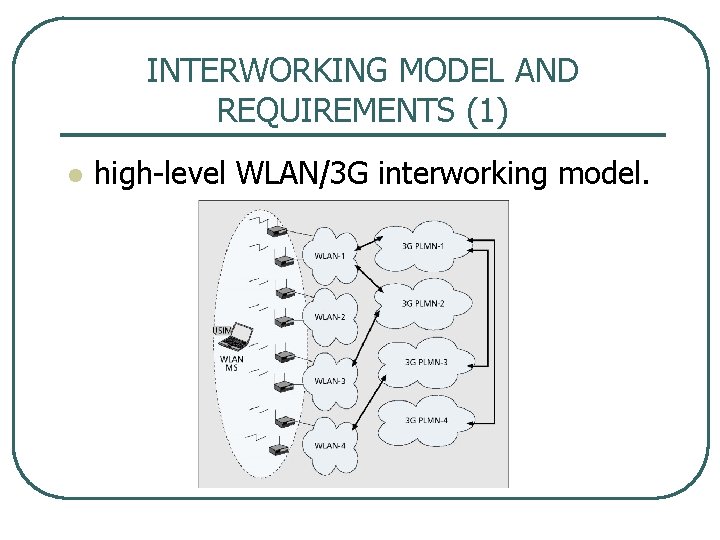
INTERWORKING MODEL AND REQUIREMENTS (1) l high level WLAN/3 G interworking model.
INTERWORKING MODEL AND REQUIREMENTS (2) l WLAN/3 G interworking must • provide 3 G based authentication • support 802. 1 X access control • support the legacy UAM and open access control schemes
NETWORK SELECTION l MS needs to perform the following selection proce dures • • l Select a WLAN that supports interworking with 3 G PLMNs MS must select one of the PLMNs several solutions of network selection problem • • broadcast an SSID with a suitable format transmitting a probe request including a predefined well known (3 G specific) SSID
INTERWORKING SCENARIOS (1) l l l Scenario 1 — Common Billing and Customer Care Scenario 2 — 3 G Based Access Control and Charging Scenario 3 — Access to 3 G Packet Switched Services Scenario 4 — Access to 3 G Packet Switched Based Ser vices with Service Continuity Scenario 5 — Access to 3 G Packet Switched Based Ser vices with Seamless Service Continuity Scenario 6 — Access to 3 G Circuit Switched Based Ser vices with Seamless Mobility
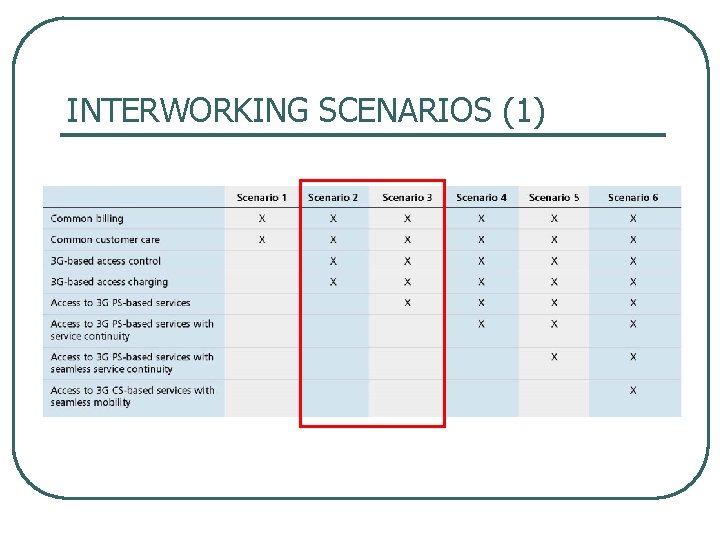
INTERWORKING SCENARIOS (1)
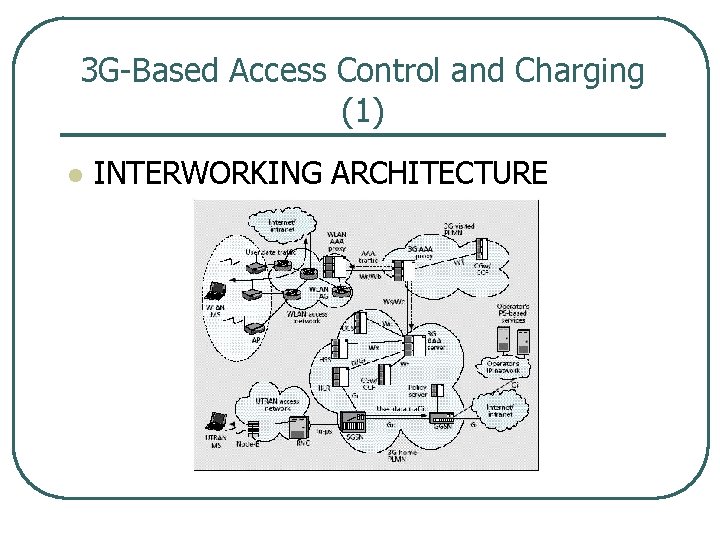
3 G Based Access Control and Charging (1) l INTERWORKING ARCHITECTURE
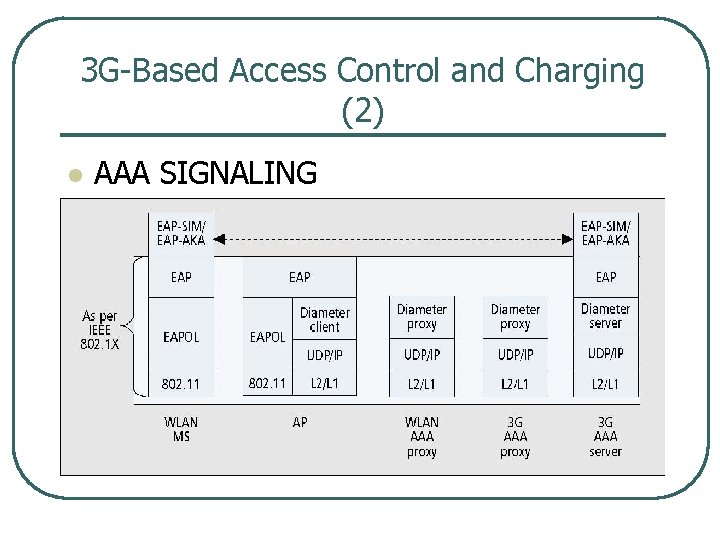
3 G Based Access Control and Charging (2) l AAA SIGNALING
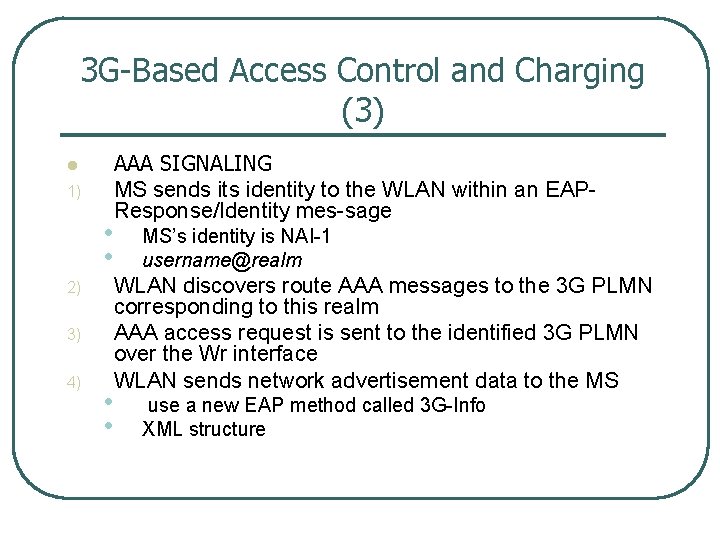
3 G Based Access Control and Charging (3) l 1) 2) 3) 4) AAA SIGNALING MS sends its identity to the WLAN within an EAP Response/Identity mes sage • • MS’s identity is NAI 1 username@realm • • use a new EAP method called 3 G Info XML structure WLAN discovers route AAA messages to the 3 G PLMN corresponding to this realm AAA access request is sent to the identified 3 G PLMN over the Wr interface WLAN sends network advertisement data to the MS
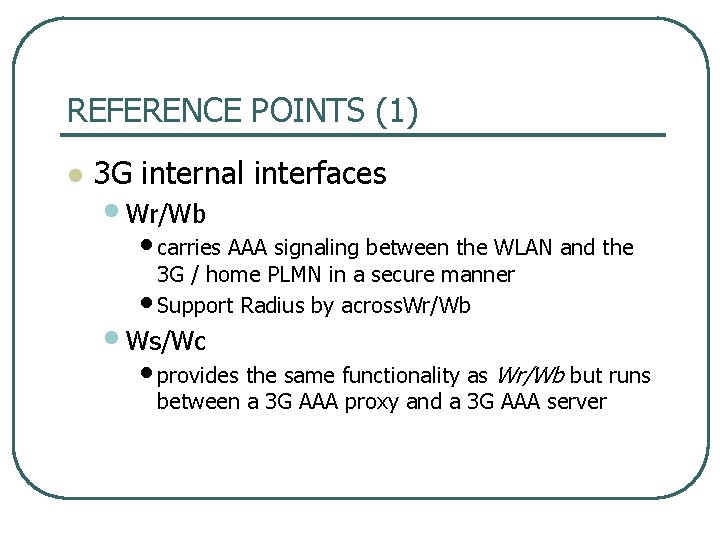
REFERENCE POINTS (1) l 3 G internal interfaces • Wr/Wb • carries AAA signaling between the WLAN and the 3 G / home PLMN in a secure manner • Support Radius by across. Wr/Wb • Ws/Wc • provides the same functionality as Wr/Wb but runs between a 3 G AAA proxy and a 3 G AAA server
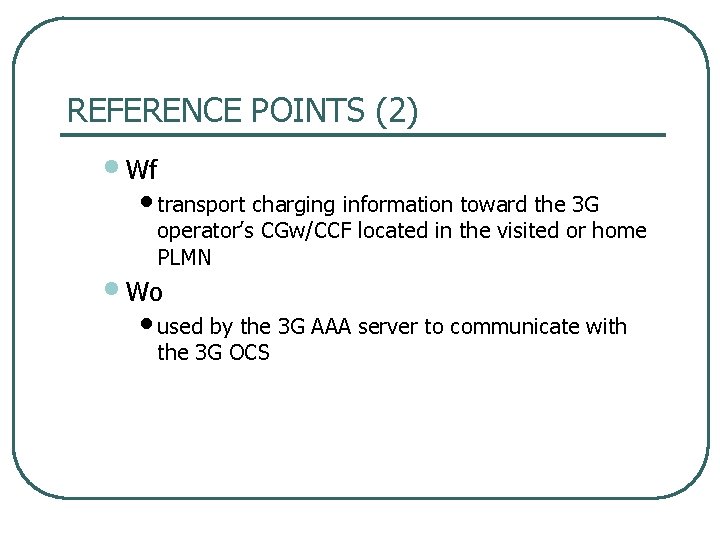
REFERENCE POINTS (2) • Wf • transport charging information toward the 3 G operator’s CGw/CCF located in the visited or home PLMN • Wo • used by the 3 G AAA server to communicate with the 3 G OCS
REFERENCE POINTS (3) • Wx • between the 3 G AAA server and the HSS • used primarily for accessing the WLAN subscription profiles of the users • D/Gr • used for exchanging subscription information between the 3 G AAA server and the HLR by means of the MAP protocol
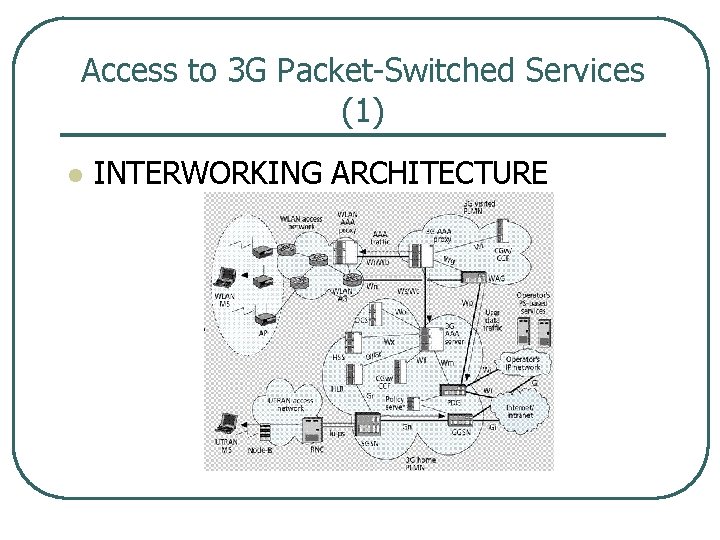
Access to 3 G Packet Switched Services (1) l INTERWORKING ARCHITECTURE
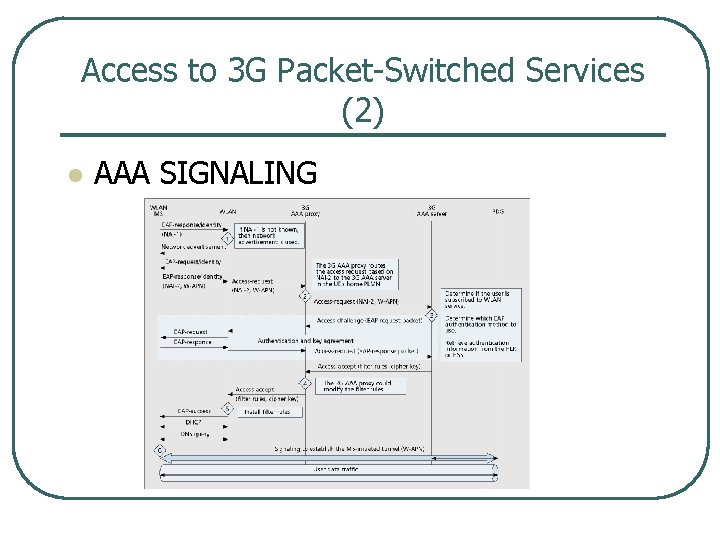
Access to 3 G Packet Switched Services (2) l AAA SIGNALING
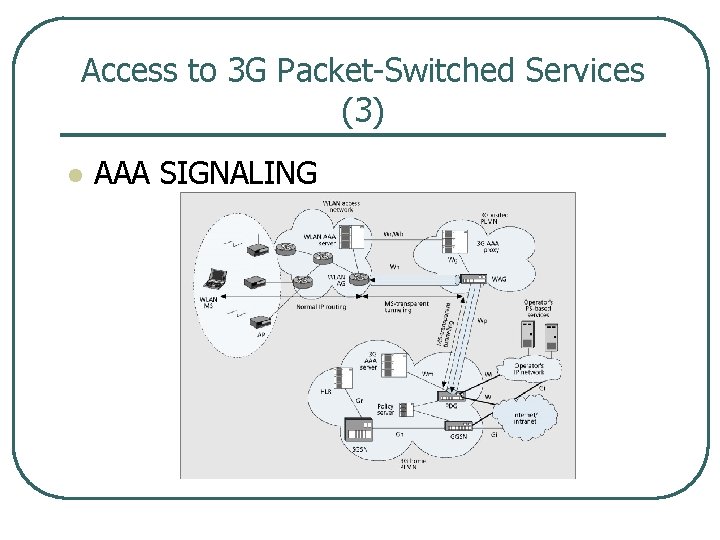
Access to 3 G Packet Switched Services (3) l AAA SIGNALING
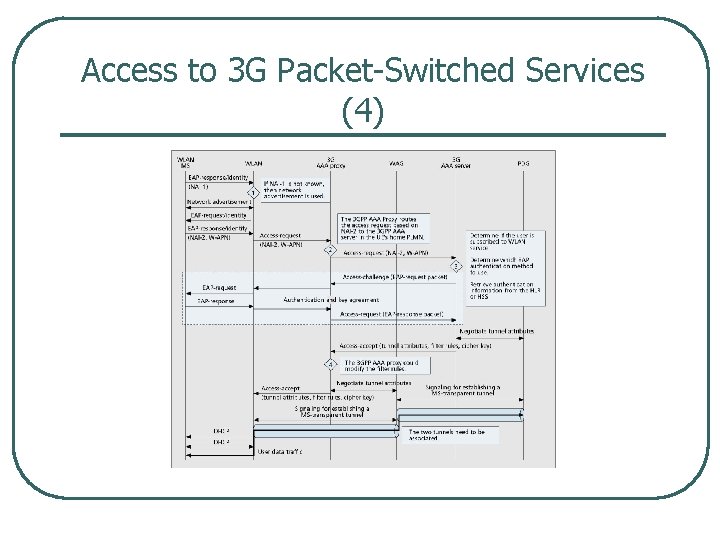
Access to 3 G Packet Switched Services (4)
REFERENCE POINTS (1) l l several additional interfaces Wn • used for transporting tunneled user data between the WLAN and the WAG l Wm • located between the 3 G AAA serv er and PDG • used to enable the 3 G AAA server to retrieve tunneling attributes and an MS’s IP configuration parameters from/via the PDG
REFERENCE POINTS (2) l Wi l Wg • provided via the Wi interface based on IP • used by the 3 G AAA proxy to deliver routing policy enforce ment information to the WAG l Wp • transports tunneled user data traffic between the WAG and the PDG
CONCLUSIONS l maintain access to the same 3 G packet switched services across several radio access technologies • l such as IEEE 802. 11, Hiper. Lan/2, UTRAN, and GERAN Ses sion mobility is an additional requirement that needs further consideration and presents consid erable technical challenges
Magazine 3 l IEEE 802. 11 roaming and authentication in wireless LAN cellular mobile networks
Note Abstract l l l l l Integrate wireless LAN service IEEE 802. 11 WIRELESS LAN ROAMING RADIUS PROXY IEEE 802. 11 HORIZONTAL ROAMING MOBILE IP HANDOFF PERFORMANCE IMPROVEMENT WIRELESS TRANSMISSION PRIVACY SECURITY ANALYSIS AUTHENTICATION AND KEY NEGOTIATION DEMONSTRATION SUMMARY
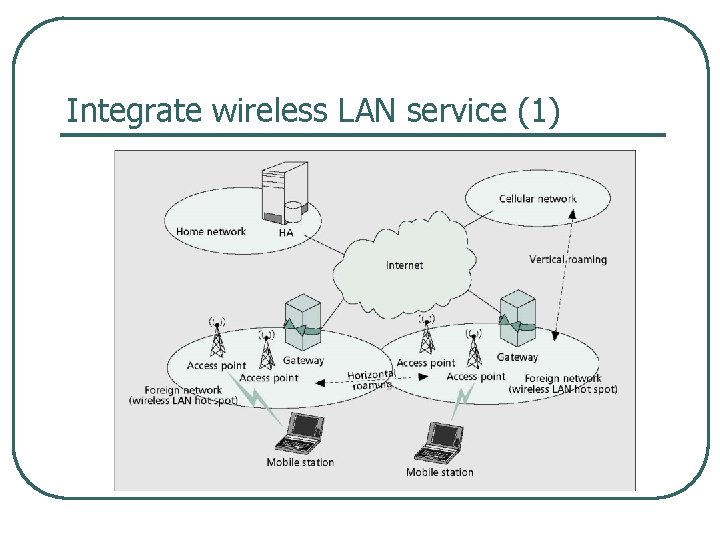
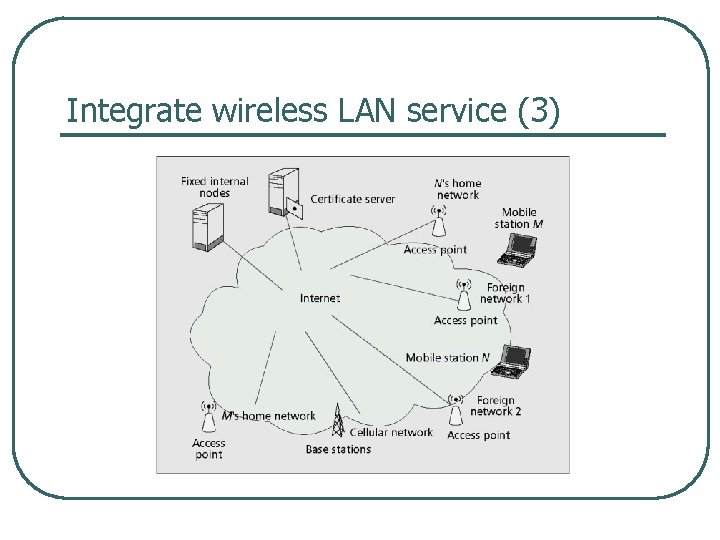
Integrate wireless LAN service (1)
Integrate wireless LAN service (2) l IEEE 802. 11 service integration functionality • integrate into cellular networks l l Wireless network security Service quality • refers to handoff speed and packet loss rate
Integrate wireless LAN service (3)
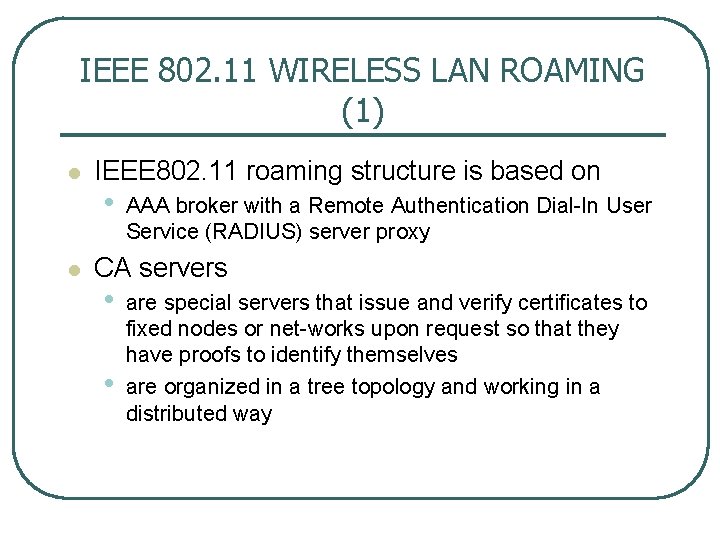
IEEE 802. 11 WIRELESS LAN ROAMING (1) l l IEEE 802. 11 roaming structure is based on • AAA broker with a Remote Authentication Dial In User Service (RADIUS) server proxy CA servers • • are special servers that issue and verify certificates to fixed nodes or net works upon request so that they have proofs to identify themselves are organized in a tree topology and working in a distributed way
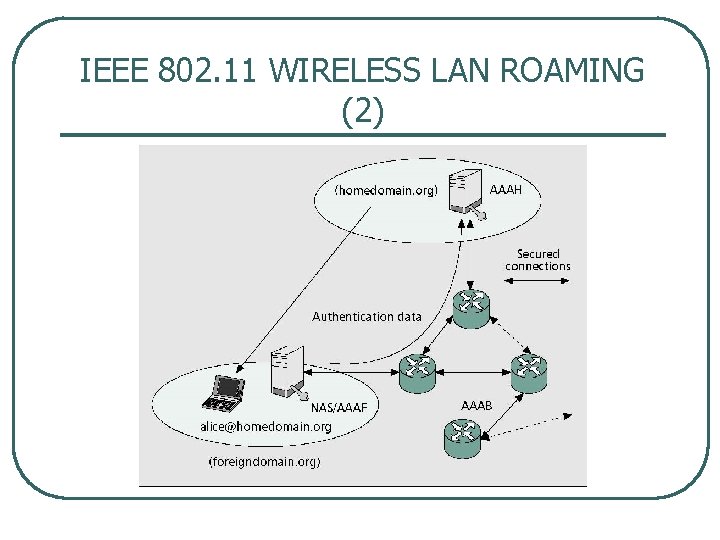
IEEE 802. 11 WIRELESS LAN ROAMING (2)
RADIUS PROXY l RADIUS server retrieves • remote server’s domain from the user’s request • includes the network access identifier • identifier@domain_name
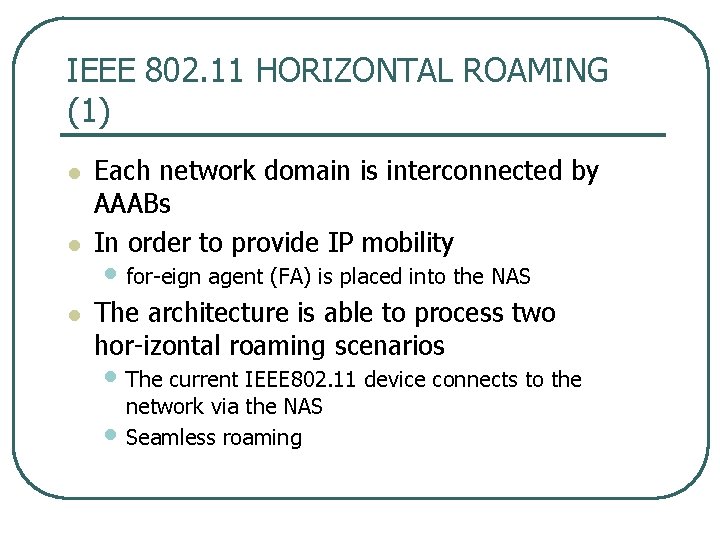
IEEE 802. 11 HORIZONTAL ROAMING (1) l l l Each network domain is interconnected by AAABs In order to provide IP mobility • for eign agent (FA) is placed into the NAS The architecture is able to process two hor izontal roaming scenarios • The current IEEE 802. 11 device connects to the • network via the NAS Seamless roaming
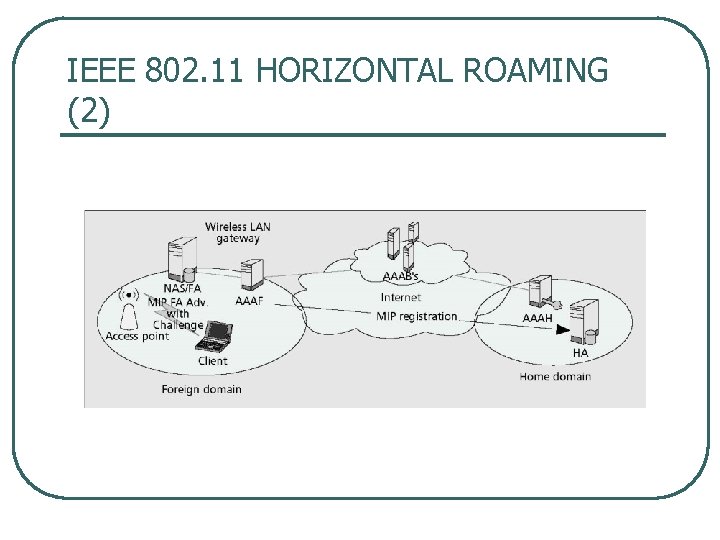
IEEE 802. 11 HORIZONTAL ROAMING (2)
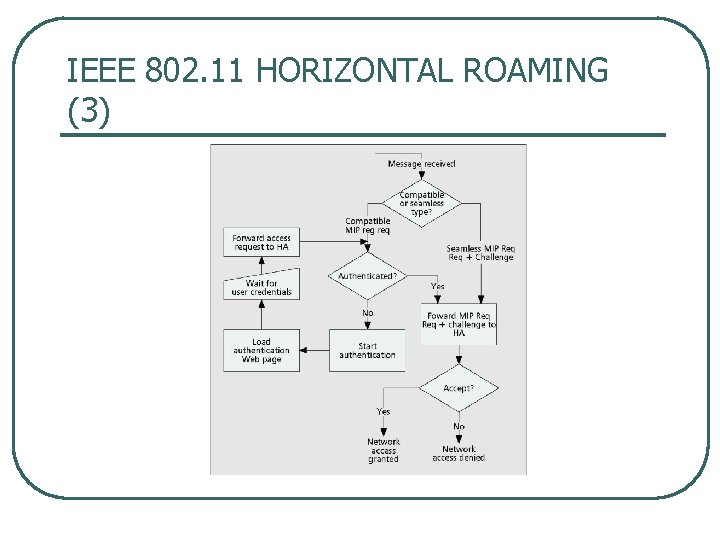
IEEE 802. 11 HORIZONTAL ROAMING (3)
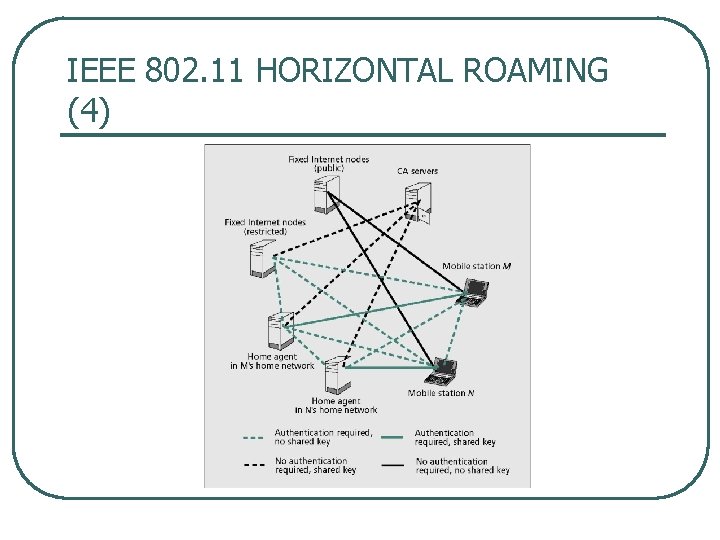
IEEE 802. 11 HORIZONTAL ROAMING (4)
MOBILE IP HANDOFF PERFORMANCE IMPROVEMENT (1) l roam between a wireless LAN and a cellular network • l l l routed to the mobile station through its HA HA redi rects the data flow to the new IP address For typical data applications is not necessary to use real time seamless handoff For real time Internet applica tions like voice or streaming video ,handoff latency and packet loss performance have become more and more critical
MOBILE IP HANDOFF PERFORMANCE IMPROVEMENT (2) l In order to reduce the latency of Mobile IP handoff • used to assist Mobile IP handoff • pre registration and authentication data can • be sent to the mobile station before it moves Additional flow control should be taken in the handover perio
WIRELESS TRANSMISSION PRIVACY (1) l l l built in WEP encryption cannot guaran tee data transmission privacy User location updates are transparent to the scheme since user mobility is handled in the network layer FA just relays the authentication message between the mobile station and its home network

WIRELESS TRANSMISSION PRIVACY (2) l Authenticating parties share a secret key • stored in either the mobile station or its Subscriber Identity Mod ule (SIM) card l Authenticating parties do not share a secret key • authentication between two mobile stations or a mobile station and a fixed Internet server l Visit the Internet public resourc • no authentica tion is needed
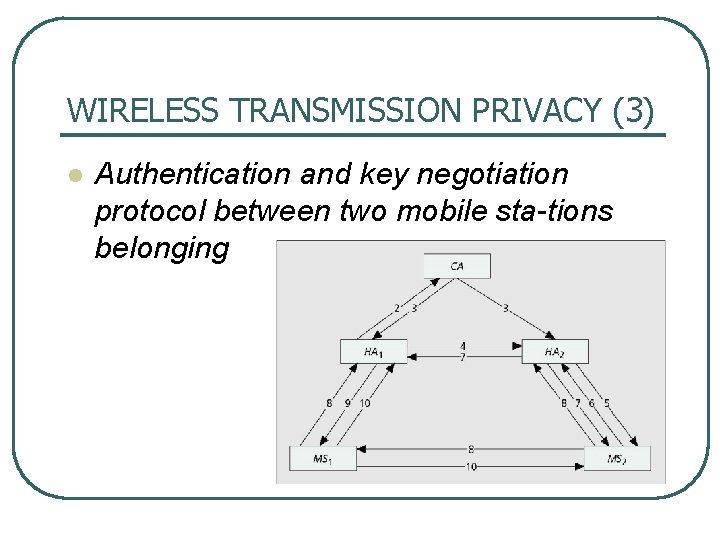
WIRELESS TRANSMISSION PRIVACY (3) l Authentication and key negotiation protocol between two mobile sta tions belonging
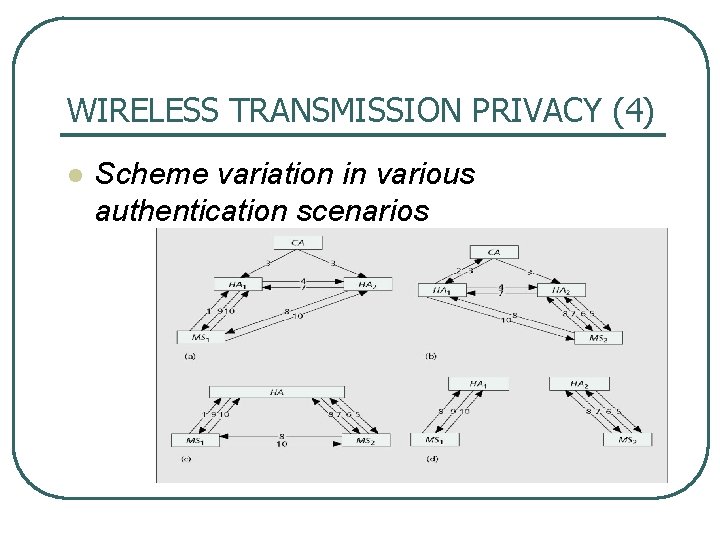
WIRELESS TRANSMISSION PRIVACY (4) l Scheme variation in various authentication scenarios
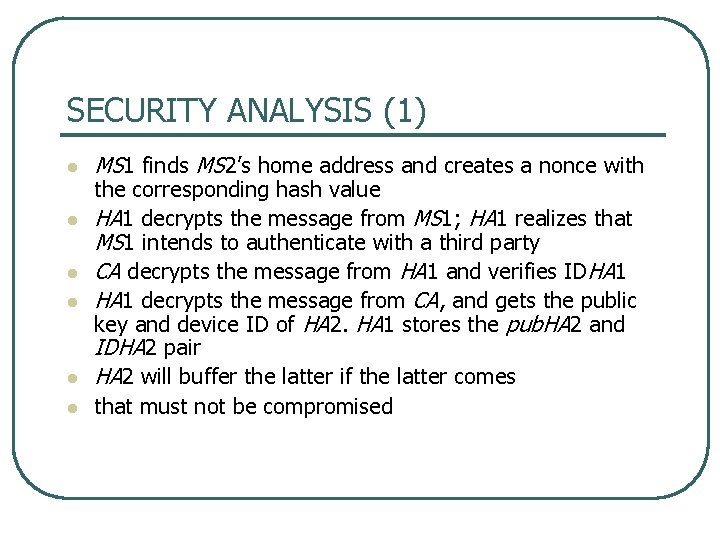
SECURITY ANALYSIS (1) l l l MS 1 finds MS 2’s home address and creates a nonce with the corresponding hash value HA 1 decrypts the message from MS 1; HA 1 realizes that MS 1 intends to authenticate with a third party CA decrypts the message from HA 1 and verifies IDHA 1 decrypts the message from CA, and gets the public key and device ID of HA 2. HA 1 stores the pub. HA 2 and IDHA 2 pair HA 2 will buffer the latter if the latter comes that must not be compromised
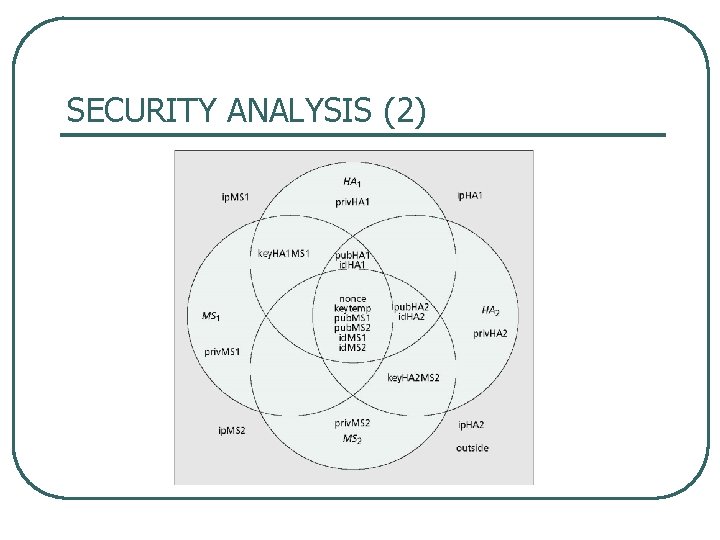
SECURITY ANALYSIS (2)
AUTHENTICATION AND KEY NEGOTIATION DEMONSTRATION l demonstration uses RSA as the public key algo rithm • DES as the symmetric algorithm • MD 5 as one way hash functions l If the slowest net work connection speed is 14. 4 kb/s in the cellu lar network with overhead of the transmission considered • data transmission can be fin ished in less than 3 s
SUMMARY l l l The proposed architecture offers a smooth transition of wireless LAN hot spots from non roaming supported to seamless roam ing supported A fast network switchover mechanism is available to improve the performance of stream ing applications wireless transmis sion security is carefully considered


Q&A
Thanks for your listen.
- Slides: 64