About Me 3 rd year of IT Management

About Me • 3 rd year of IT Management • Doing my internship at Cylance • Started Malware Analysis early January
AVCrypt Ransomware “In-dev” ransomware that deletes numerous windows services as well as AV software before encrypting files Alias: Ransom: Win 32/Pactelung. A Discovered by @malwrhunterteam
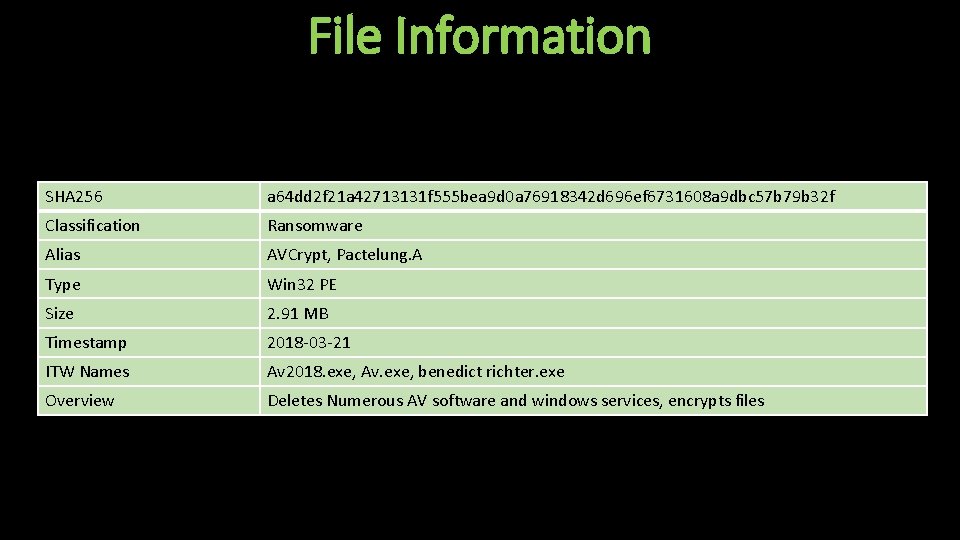
File Information SHA 256 a 64 dd 2 f 21 a 42713131 f 555 bea 9 d 0 a 76918342 d 696 ef 6731608 a 9 dbc 57 b 79 b 32 f Classification Ransomware Alias AVCrypt, Pactelung. A Type Win 32 PE Size 2. 91 MB Timestamp 2018 -03 -21 ITW Names Av 2018. exe, Av. exe, benedict richter. exe Overview Deletes Numerous AV software and windows services, encrypts files

In-dev Ransomware • • • Ransom note doesn’t contain any contact information – only “lol n” Displays an alert before it starts Numerous debug messages seen in IDA No attempts at obfuscation 4 samples seen in the wild to date Similar sounding ransomware recently hit a Japanese university
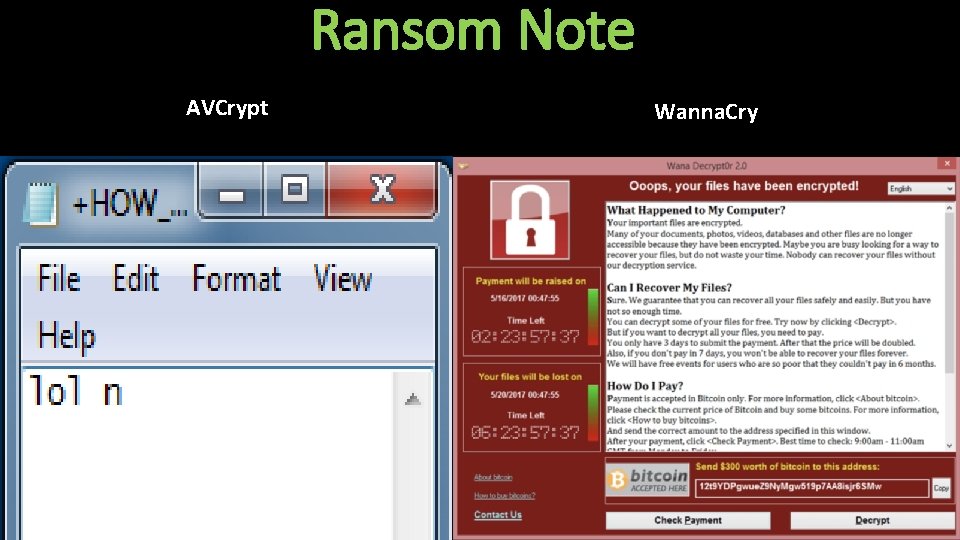
Ransom Note AVCrypt Wanna. Cry
Alert

Flow of Execution • Deletes AV software relating to Malwarebytes and Emsisoft • Deletes numerous Windows services and services relating to Malwarebytes & Windows Defender • Disables other Windows features, leaving victim machines very vulnerable to further infection • Drops zip file containing tor. exe • Contacts C 2 server bxp 44 w 3 qwwrmuupc[. ]onion • Encrypts files & adds “+” to beginning of encrypted files

Anti-Analysis Techniques • Tries to connect to www. Microsoft. com • Checks for presence of debugger
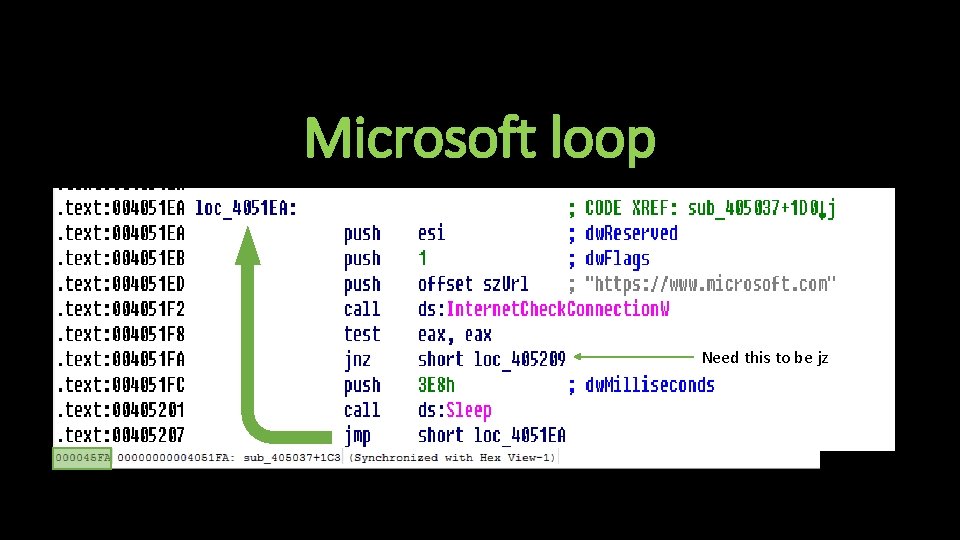
Microsoft loop Need this to be jz
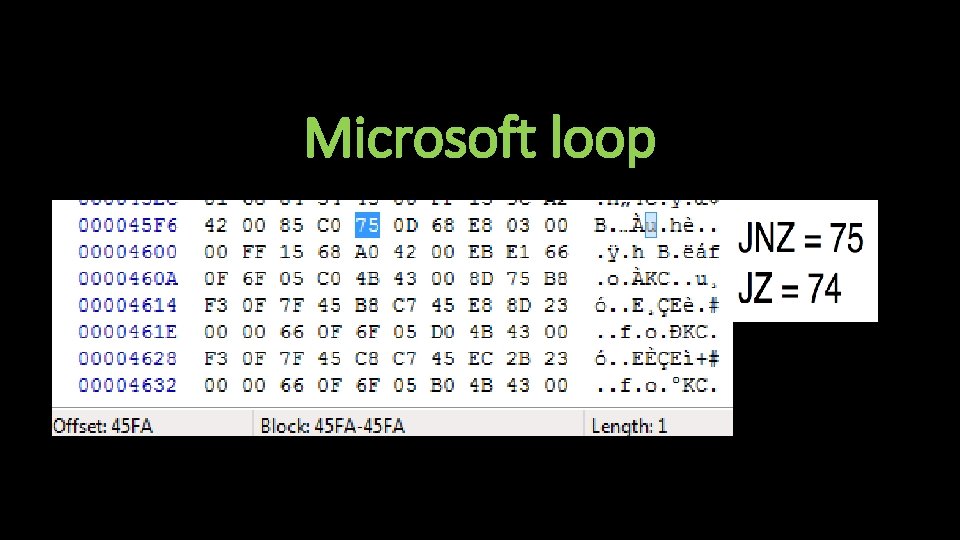
Microsoft loop
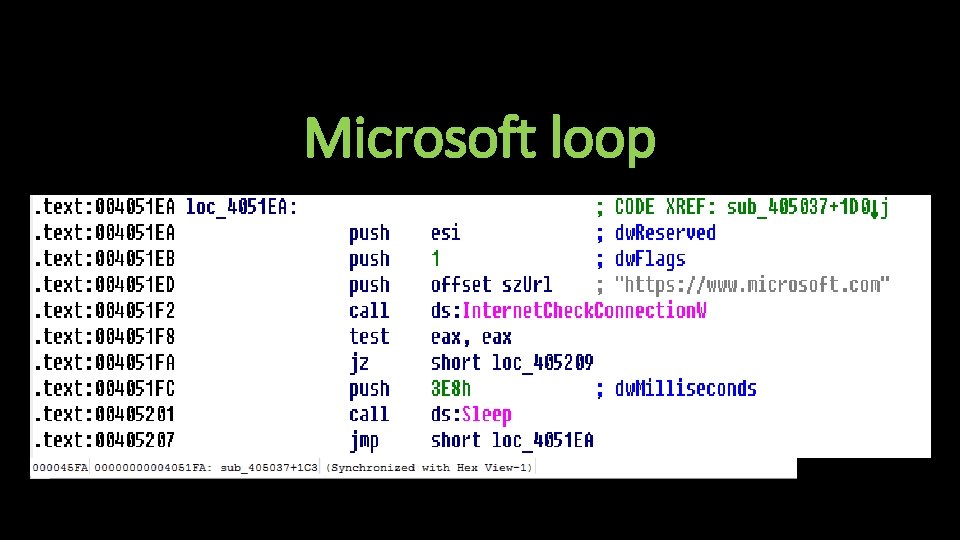
Microsoft loop
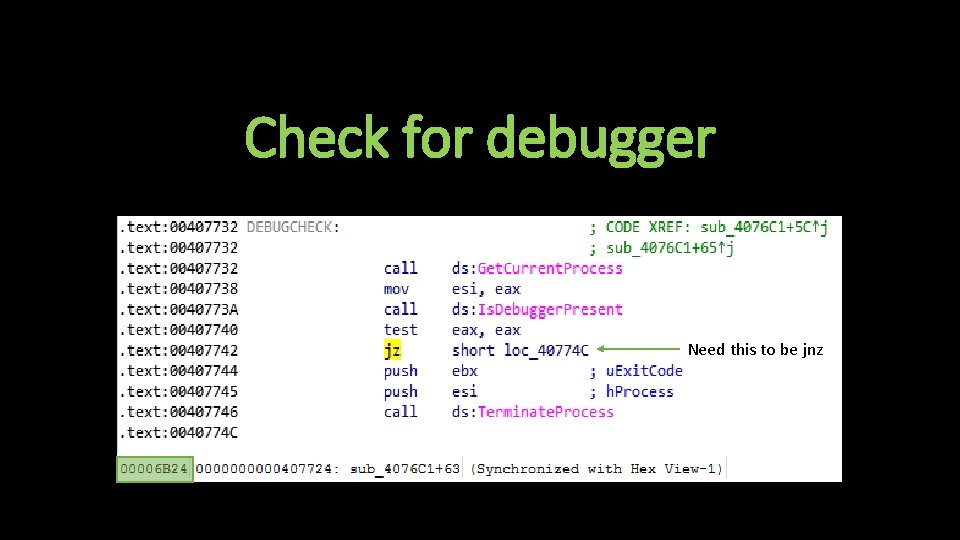
Check for debugger Need this to be jnz

Check for debugger

Check for debugger
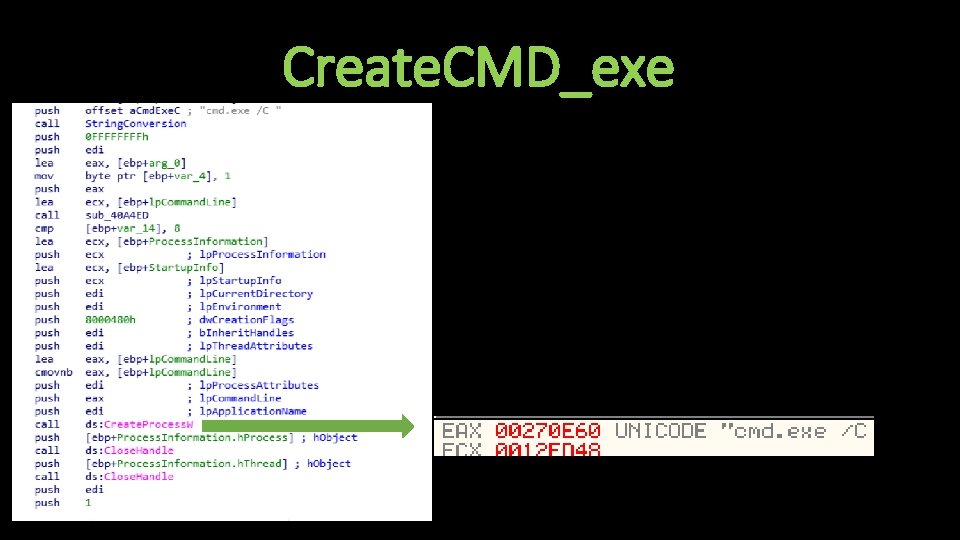
Create. CMD_exe

AV Removal
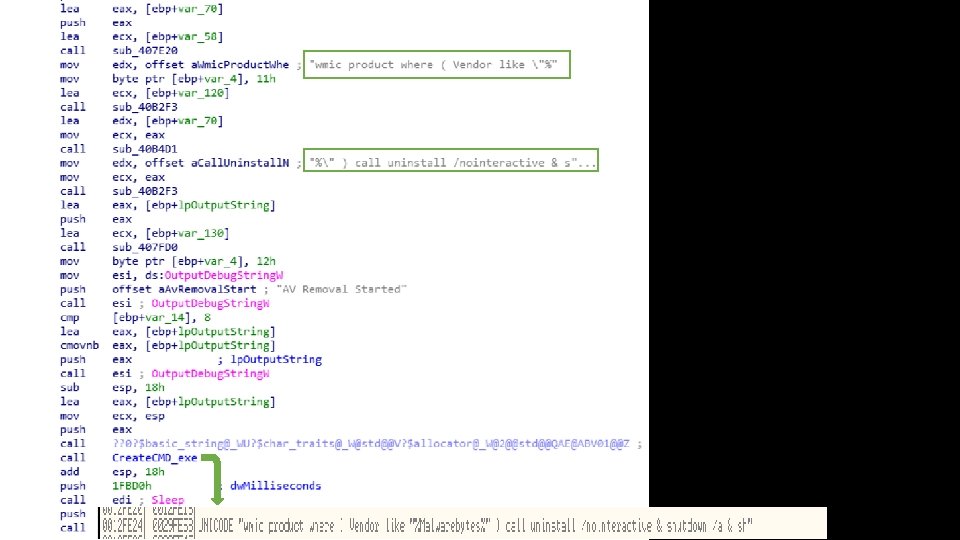
AV Removal

Service Removal
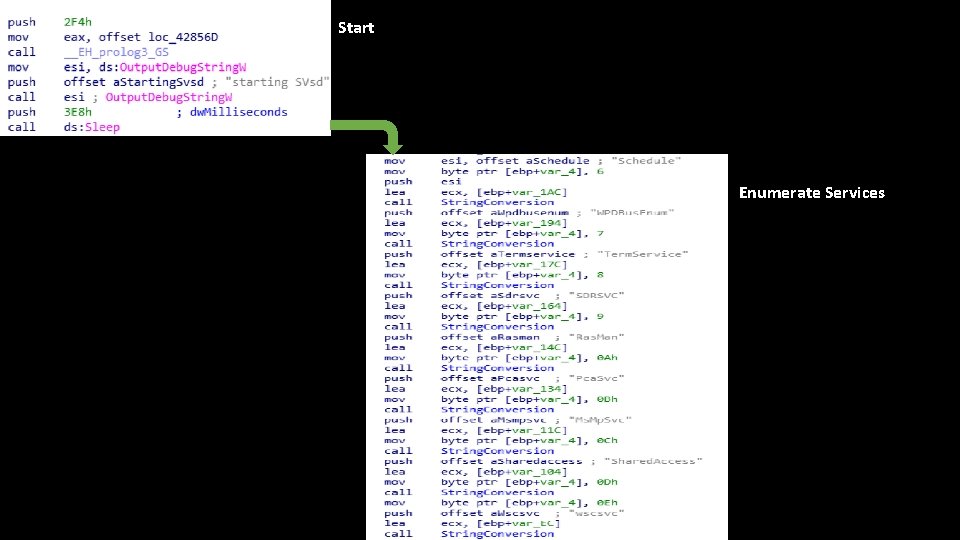
Start Enumerate Services
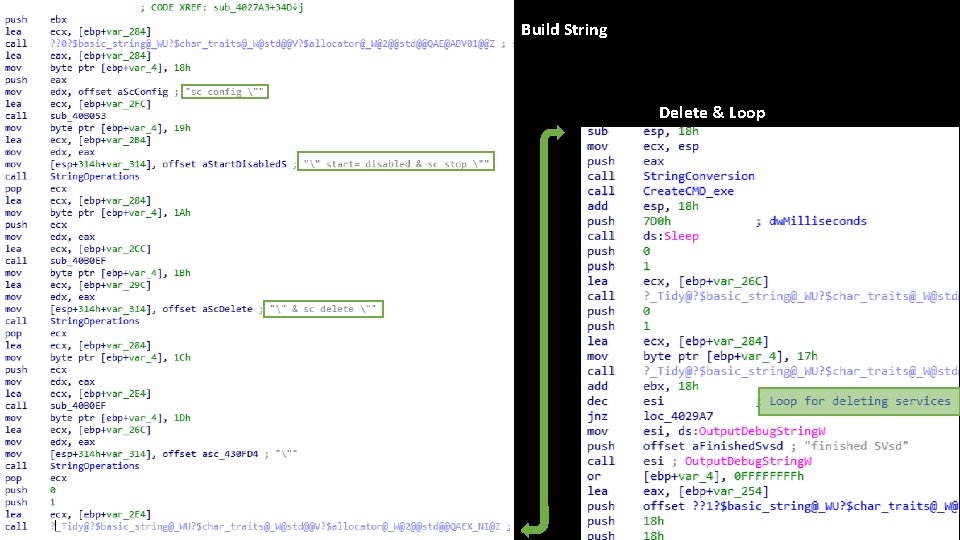
Build String Delete & Loop

Service Removal Start Enumerate Services Build String Delete & Loops until esi counter is depleted (when all specified services are deleted)

List of Services Removed MBAMService MBAMSwiss. Army MBAMChameleon MBAMWeb. Protection MBAMFarflt MBAMProtection ESProtection. Driver Schedule WPDBus. Enum Term. Service SDRSVC Ras. Man Pca. Svc Ms. Mp. Svc Shared. Access Wscsvc Srservice VSS Swprv Wer. Svc Mps. Svc Win. Defend wuauserv

Other Features Disabled Windows Smart Screen Check exe Signatures Disable Realtime monitoring Deletes Backup Catalog Deletes volume snapshots
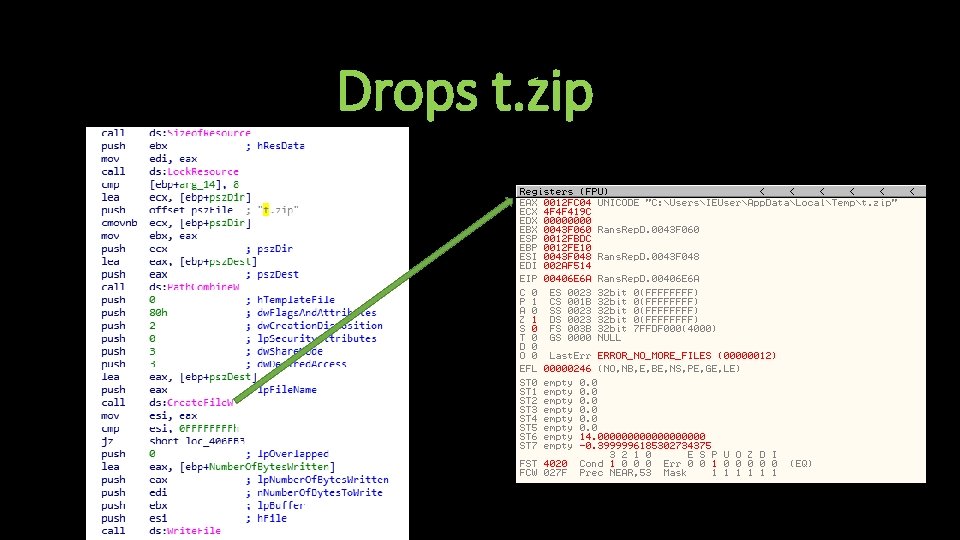
Drops t. zip
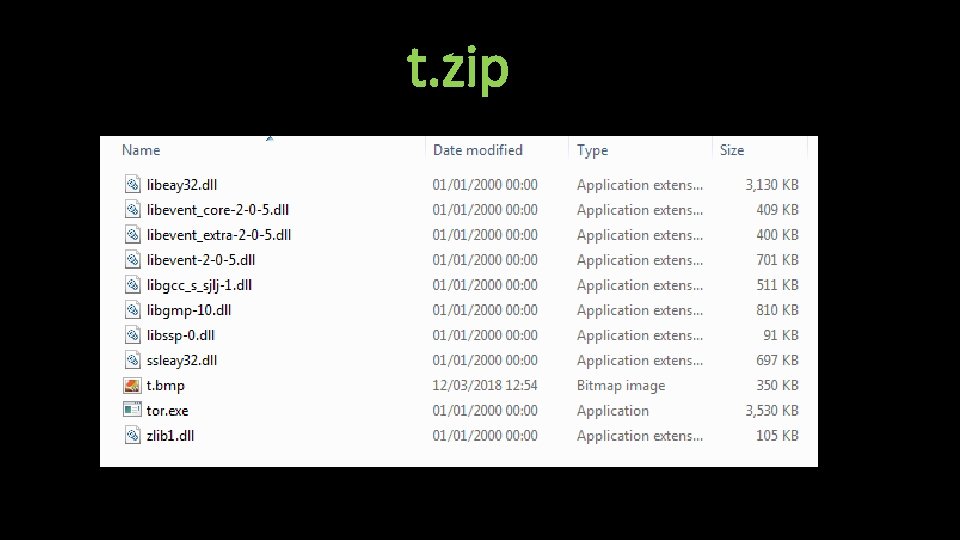
t. zip
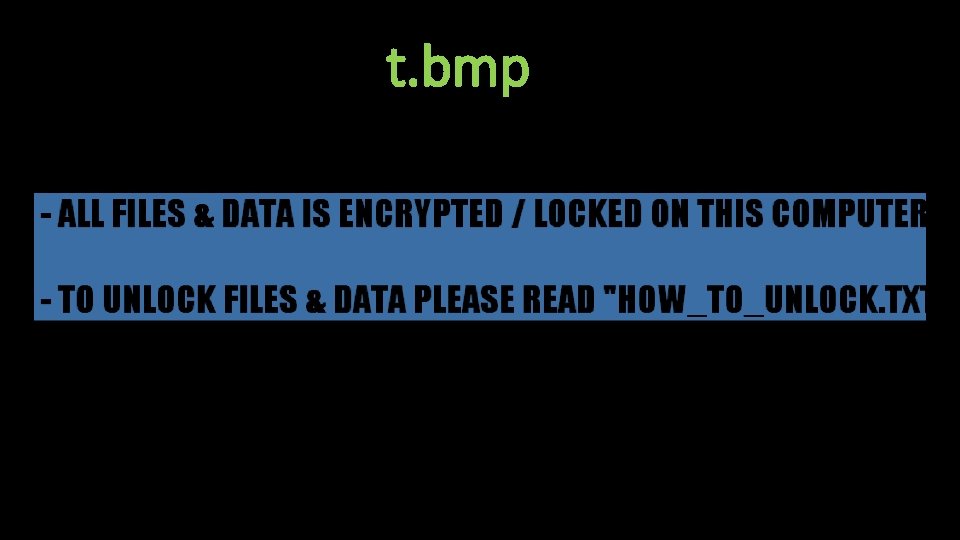
t. bmp
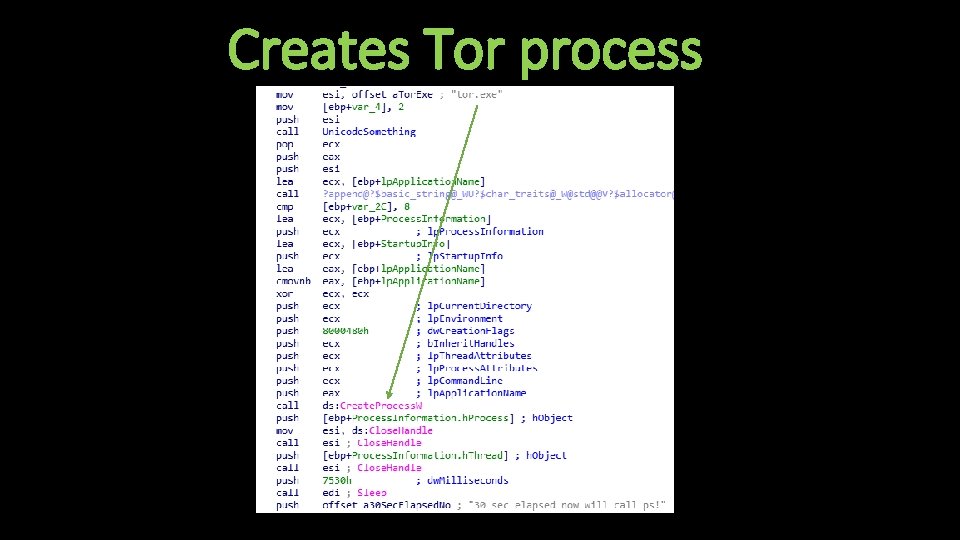
Creates Tor process

Checks for Tor process Continues to search processes
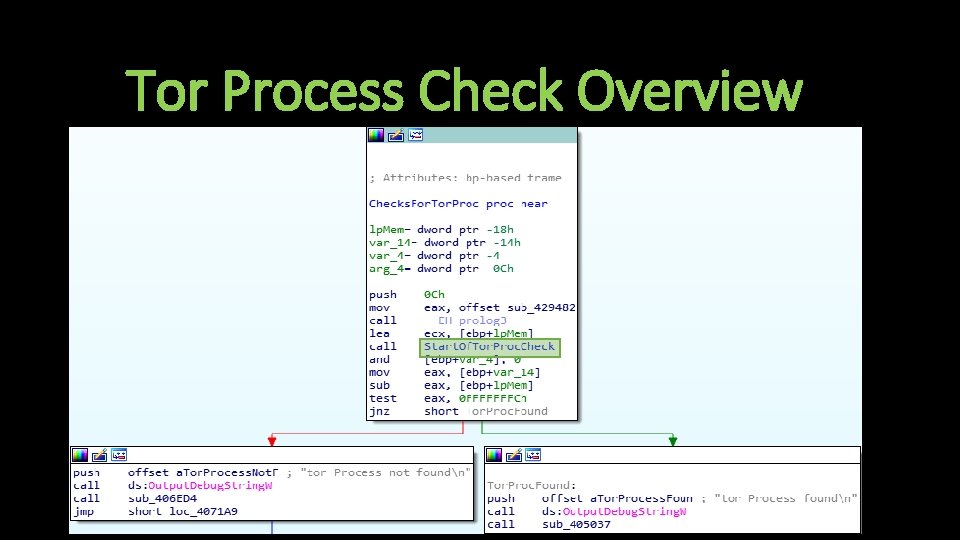
Tor Process Check Overview
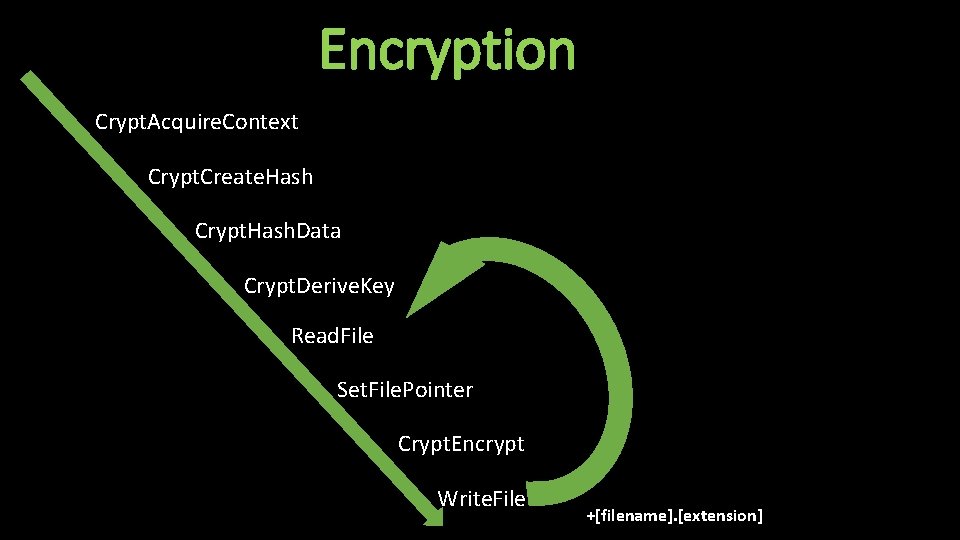
Encryption Crypt. Acquire. Context Crypt. Create. Hash Crypt. Hash. Data Crypt. Derive. Key Read. File Set. File. Pointer Crypt. Encrypt Write. File +[filename]. [extension]
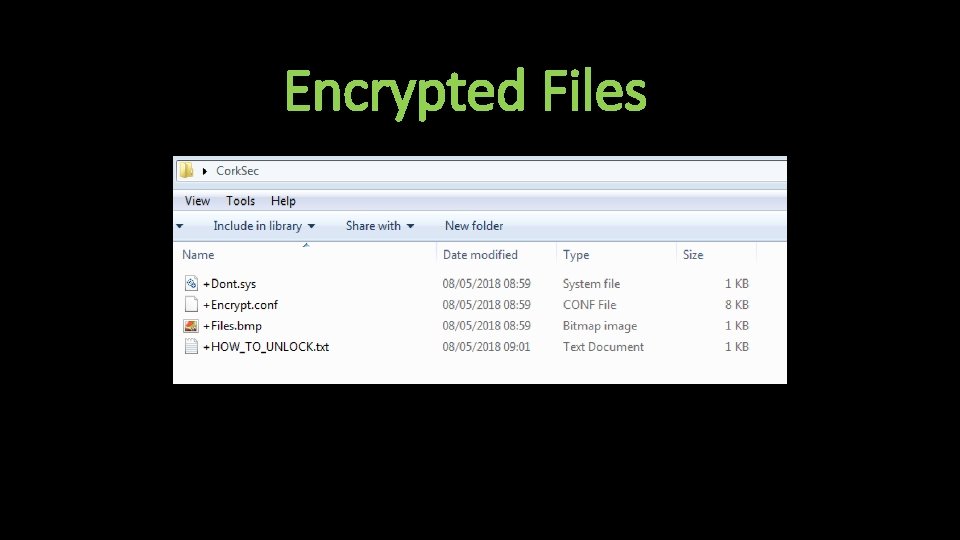
Encrypted Files
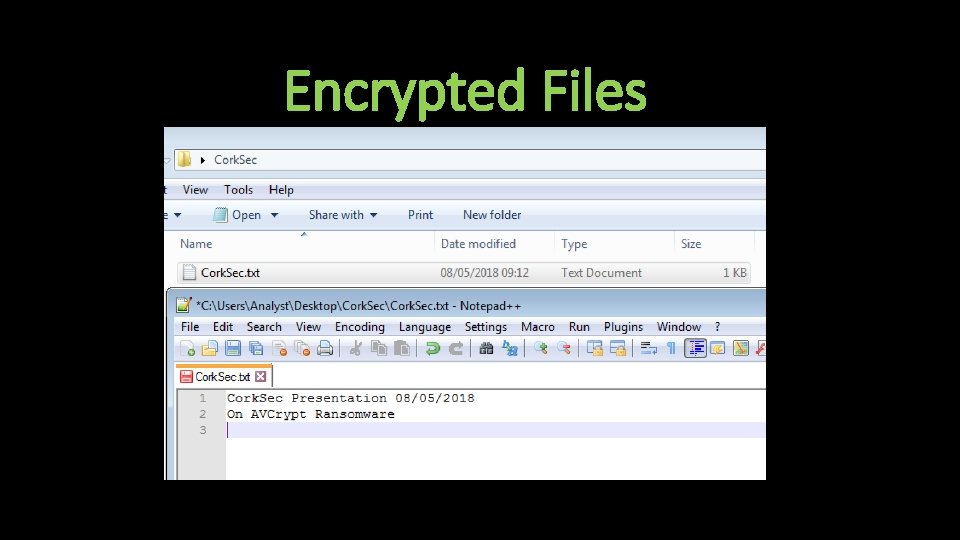
Encrypted Files
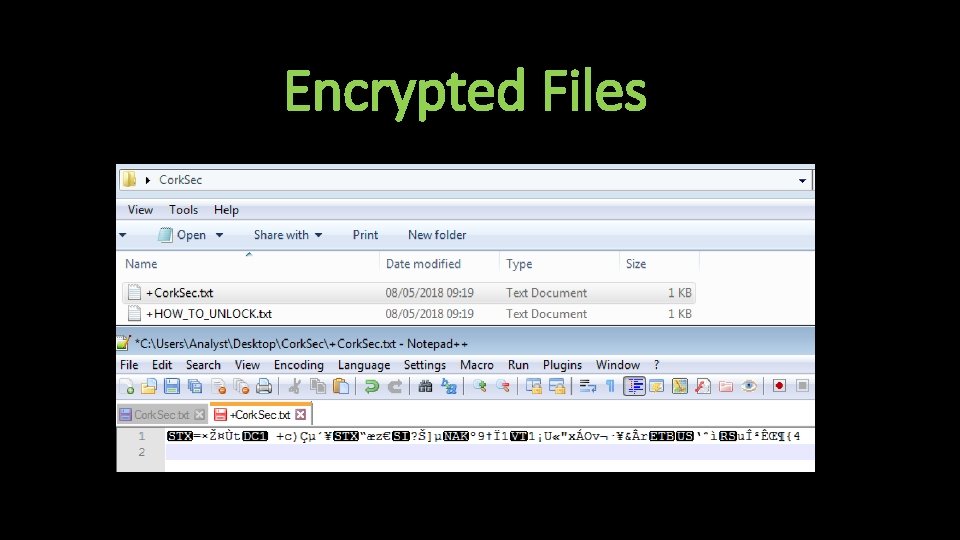
Encrypted Files

Indicators Of Compromise (IOC’s) Hashes: • SHA 256: a 64 dd 2 f 21 a 42713131 f 555 bea 9 d 0 a 76918342 d 696 ef 6731608 a 9 dbc 57 b 79 b 32 f • SHA 256: 58 c 7 c 883785 ad 27434 ca 8 c 9 fc 20 b 02885 c 9 c 24 e 884 d 7 f 6 f 1 c 0 cc 2908 a 3 e 111 f 2 • SHA 256: ecc 12 fb 24 c 964 d 174 a 1 bcbcd 0 b 6 ab 5 d 698 d 342 d 4 a 79 dee 4 d 72 c 4033 d 01 a 88 e 33 • SHA 256: 4 a 133 dab 4 be 4 fb 71 f 933 a 0164979 a 2 e 57 be 5 dd 4 c 54 bcada 70 df 50 c 069 bf 98253 C 2: • bxp 44 w 3 qwwrmuupc[. ]onion Files: • C: /Users/HOW_TO_UNLOCK. txt (seen in all other encrypted folders also) • C: /Users/bmp part. bmp • %TEMP%/t. zip • + symbol added to beginning of most files Mutex: • . $
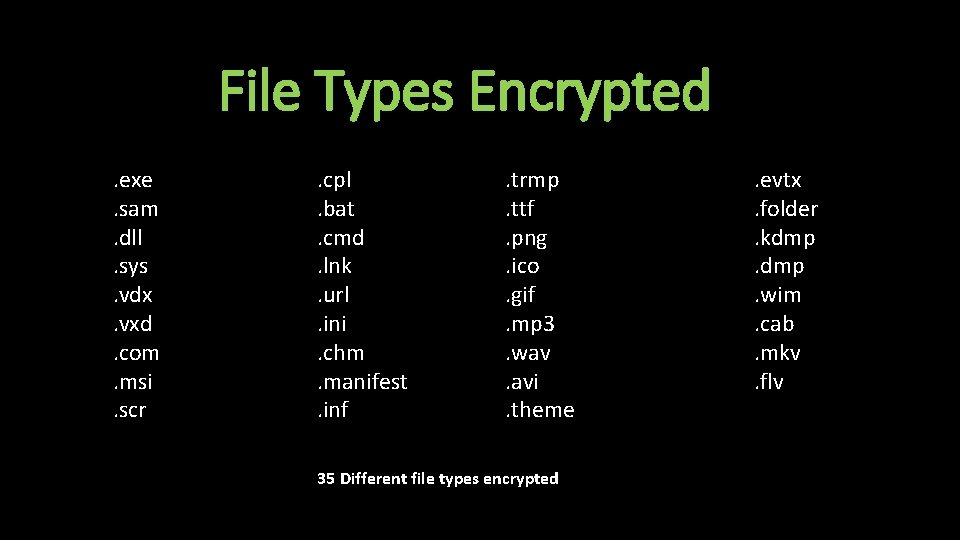
File Types Encrypted. exe. sam. dll. sys. vdx. vxd. com. msi. scr . cpl. bat. cmd. lnk. url. ini. chm. manifest. inf . trmp. ttf. png. ico. gif. mp 3. wav. avi. theme 35 Different file types encrypted . evtx. folder. kdmp. wim. cab. mkv. flv

YARA Rules YARA is the name of a tool primarily used in malware research and detection. It provides a rule-based approach to create descriptions of malware families Based on textual or binary patterns.
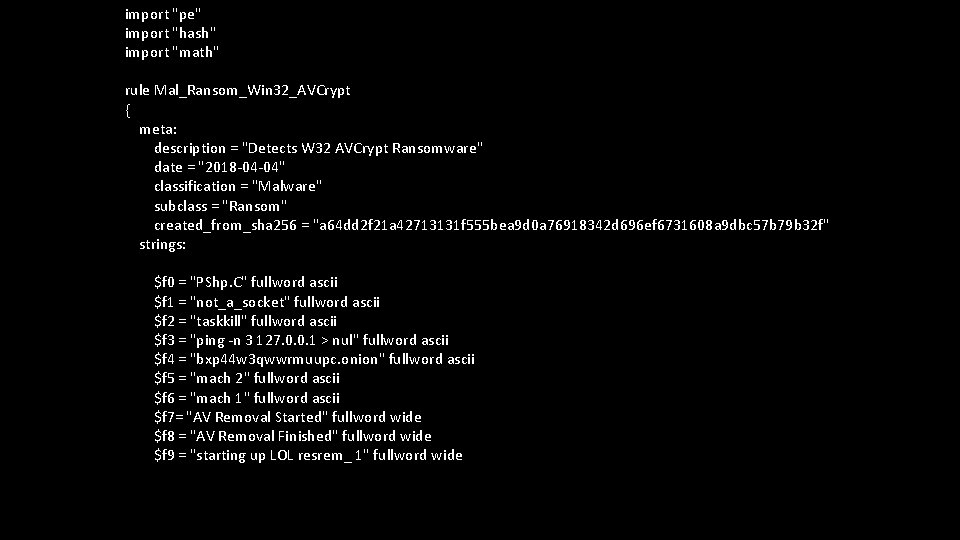
import "pe" import "hash" import "math" rule Mal_Ransom_Win 32_AVCrypt { meta: description = "Detects W 32 AVCrypt Ransomware" date = "2018 -04 -04" classification = "Malware" subclass = "Ransom" created_from_sha 256 = "a 64 dd 2 f 21 a 42713131 f 555 bea 9 d 0 a 76918342 d 696 ef 6731608 a 9 dbc 57 b 79 b 32 f" strings: $f 0 = "PShp. C" fullword ascii $f 1 = "not_a_socket" fullword ascii $f 2 = "taskkill" fullword ascii $f 3 = "ping -n 3 127. 0. 0. 1 > nul" fullword ascii $f 4 = "bxp 44 w 3 qwwrmuupc. onion" fullword ascii $f 5 = "mach 2" fullword ascii $f 6 = "mach 1" fullword ascii $f 7= "AV Removal Started" fullword wide $f 8 = "AV Removal Finished" fullword wide $f 9 = "starting up LOL resrem_ 1" fullword wide
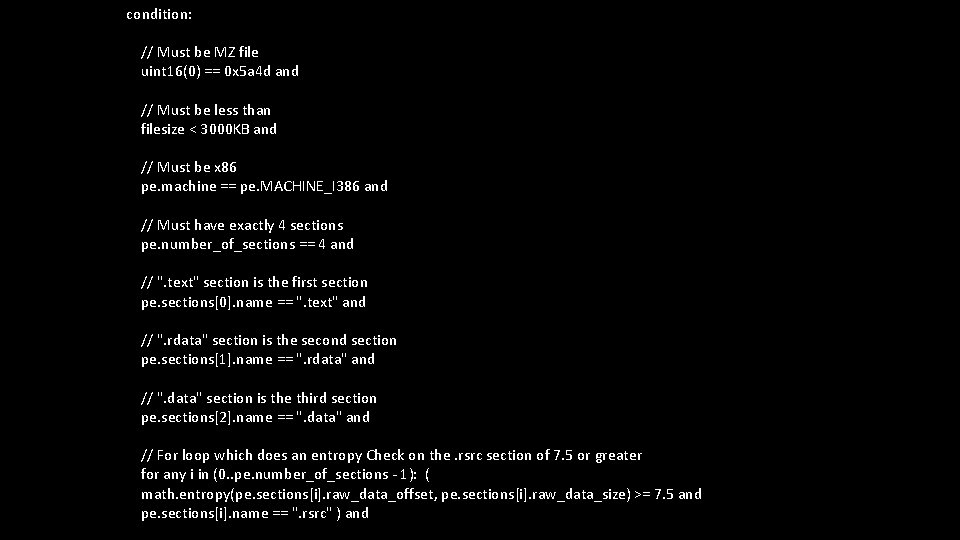
condition: // Must be MZ file uint 16(0) == 0 x 5 a 4 d and // Must be less than filesize < 3000 KB and // Must be x 86 pe. machine == pe. MACHINE_I 386 and // Must have exactly 4 sections pe. number_of_sections == 4 and // ". text" section is the first section pe. sections[0]. name == ". text" and // ". rdata" section is the second section pe. sections[1]. name == ". rdata" and // ". data" section is the third section pe. sections[2]. name == ". data" and // For loop which does an entropy Check on the. rsrc section of 7. 5 or greater for any i in (0. . pe. number_of_sections - 1): ( math. entropy(pe. sections[i]. raw_data_offset, pe. sections[i]. raw_data_size) >= 7. 5 and pe. sections[i]. name == ". rsrc" ) and
![// PE Entry Point is in the first section pe. sections[pe. section_index(pe. entry_point)]. virtual_address==0 // PE Entry Point is in the first section pe. sections[pe. section_index(pe. entry_point)]. virtual_address==0](http://slidetodoc.com/presentation_image_h2/7aeed7d9035d84f3ed365203e4723f96/image-39.jpg)
// PE Entry Point is in the first section pe. sections[pe. section_index(pe. entry_point)]. virtual_address==0 x 00001000 and // Section Permissions pe. sections[pe. section_index(". data")]. characteristics&pe. SECTION_MEM_WRITE and // Check for imports used to load the resource pe. imports("WININET. dll", "Internet. Check. Connection. W") and pe. imports("WS 2_32. dll", "socket") and pe. imports("WS 2_32. dll", "connect") and pe. imports("WS 2_32. dll", "send") and } // Must have Strings 9 of ($f*)

Virus. Total: Retrohunt • Scan all files on Virus. Total against your YARA rule • Returns list of hashes that match the rule you made • Check classifications of these hashes to determine accuracy of your rule
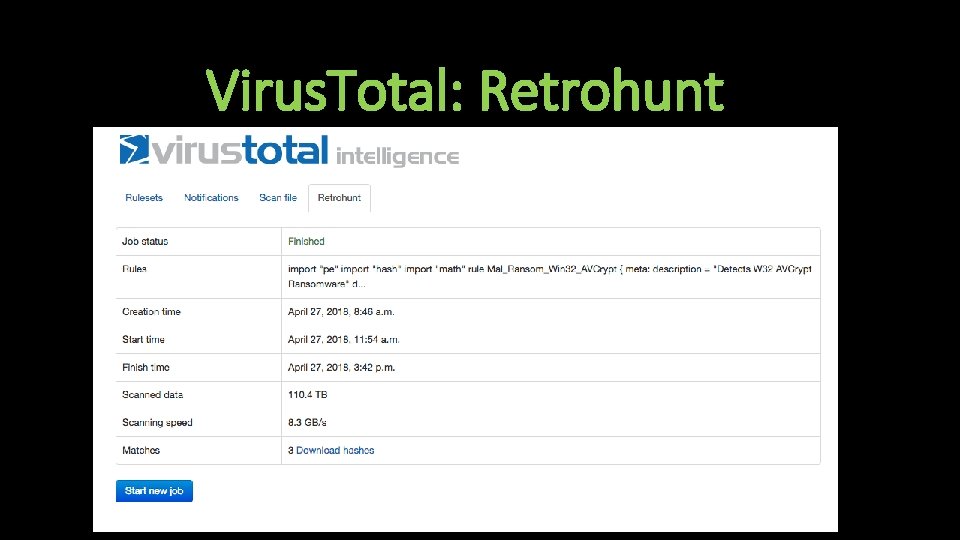
Virus. Total: Retrohunt
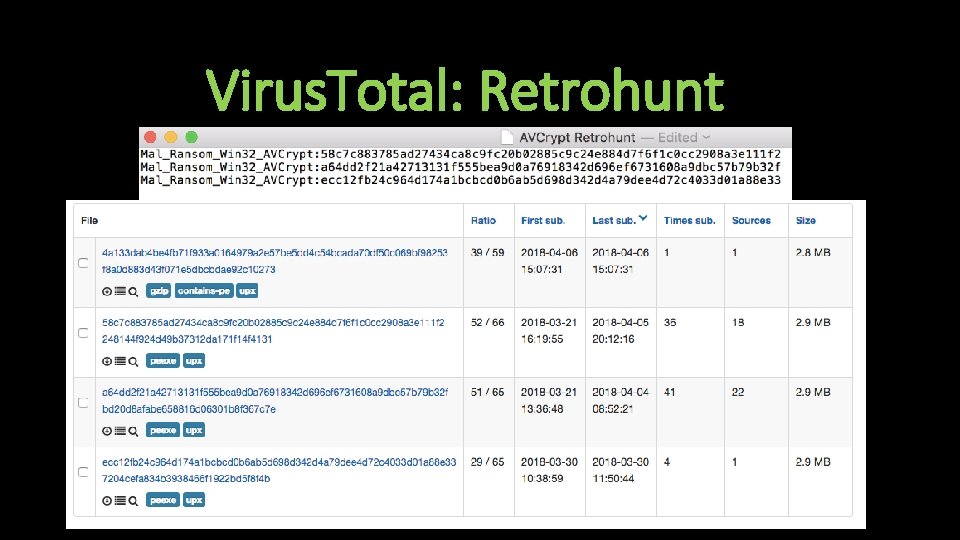
Virus. Total: Retrohunt

Questions?
- Slides: 43