About ISACA Romania Business Model for Information Security

About ISACA Romania ~ Business Model for Information Security www. isaca. org

About ISACA • A nonprofit, independent membership association • Founded in 1969 as the EDP Auditors Association, ISACA helps its members and their employers ensure trust in, and value from, information systems. • A leading global provider of knowledge, certifications, community, advocacy and education on information systems assurance, control and security, enterprise governance of IT, and ITrelated risk and compliance www. isaca. org www. isaca. ro

ISACA Worldwide and in Romania • More than 95, 000 constituents in more than 160 countries in Asia, Latin America, Europe, Africa, North America and Oceania • Members include internal and external auditors, CEOs, CFOs, CIOs, educators, information security and control professionals, business managers, students, and IT consultants • Members in Romania: 271 as of 10 -October 2011 www. isaca. org out of which: CGEIT: 17 CRISC: 51 CISA: 140 CISM: 47 www. isaca. ro

Four industry-leading certifications • • Certified Information Systems Auditor (CISA), a globally respected designation for experienced IS audit, control and security professionals. More than 79, 000 have earned the CISA designation since its inception in 1978. Certified Information Security Manager (CISM), a groundbreaking designation for leaders who manage an organization’s information security. More than 14, 000 have earned the CISM designation since it was established in 2002. Certified in the Governance of Enterprise IT (CGEIT), for professionals who manage, provide advisory and/or assurance services, and/or who otherwise support the governance of an enterprise’s IT. More than 4, 500 professionals have earned the CGEIT designation since it was established in 2007. Certified in Risk and Information Systems Control (CRISC), for IT professionals who have experience with risk identification, assessment and evaluation; risk response; risk monitoring; IS control design and implementation; and IS control monitoring and maintenance. More than 1, 000 professionals have been certified sinception in 2010. www. isaca. org www. isaca. ro

ISACA frameworks and initiatives COBIT is a complete, internationally accepted framework for the governance of IT that helps business and IT executives and management achieve business goals and related IT goals complimentary download at www. isaca. org/cobit IT Assurance Framework (ITAF) provides guidance on the design, conduct and reporting of IT audit and assurance assignments, and establishes standards that address IT audit and assurance professional roles and responsibilities; - free download at www. isaca. org/itaf Business Model for Information Security (BMIS) provides a view of information security program activities within the context the larger enterprise to integrate the disparate security program components into a holistic system of information protection - free download at www. isaca. org/bmis o Risk IT: Based on COBIT, is a framework that helps enterprises increase their return on investment by managing risks effectively, rather than trying to eliminate them completely. The Risk IT Framework is available - free download at www. isaca. org/riskit Other initiatives: Val IT, ISACA Journal, ITGI, research, guidance, tools and techniques www. isaca. org More information available on www. isaca. org and www. isaca. ro

The Business Model for Information Security (BMIS) presents a holistic, dynamic solution for designing, implementing and managing information security. BMIS creates opportunities for the information security programme to establish itself as a solid business enabler by considering security’s impact on the business. www. isaca. org

If only. . . • • • www. isaca. org I had better tools Users understood security I had enough resources Security was a top priority We had stronger regulations People read and understood security policies
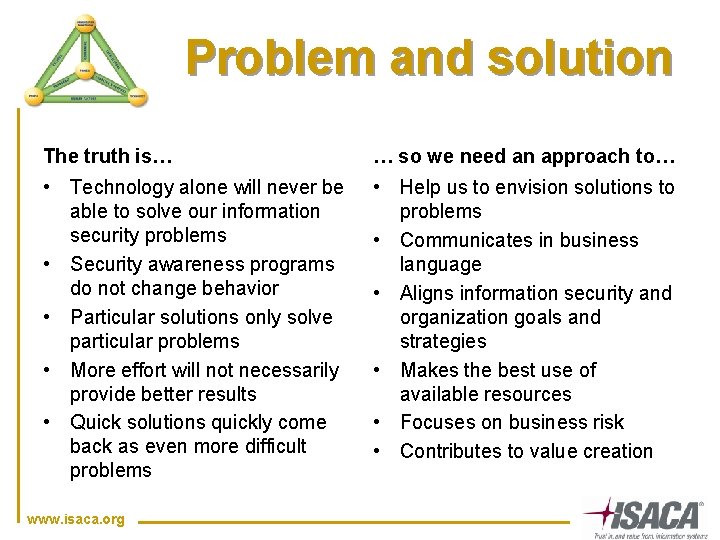
Problem and solution The truth is… … so we need an approach to… • Technology alone will never be able to solve our information security problems • Security awareness programs do not change behavior • Particular solutions only solve particular problems • More effort will not necessarily provide better results • Quick solutions quickly come back as even more difficult problems • Help us to envision solutions to problems • Communicates in business language • Aligns information security and organization goals and strategies • Makes the best use of available resources • Focuses on business risk • Contributes to value creation www. isaca. org
A model is… • The representation of something • A representative form, style or pattern • A simplified representation or description of a system or complex entity, designed to facilitate calculations and predictions • A systematic description of an object or phenomenon that shares important characteristics • A description of a complex entity or process www. isaca. org

A security model can tell us… • How to look at a problem – to determine causes rather than symptoms • How to use resources for maximum impact – as “less” often provides “more” • How components interact and influence • How to identify and use leverage points www. isaca. org
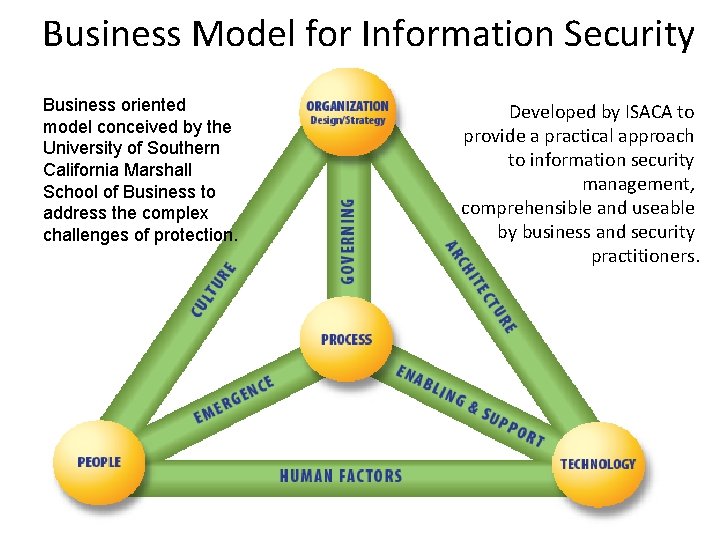
Business Model for Information Security Business oriented model conceived by the University of Southern California Marshall School of Business to address the complex challenges of protection. Developed by ISACA to provide a practical approach to information security management, comprehensible and useable by business and security practitioners.
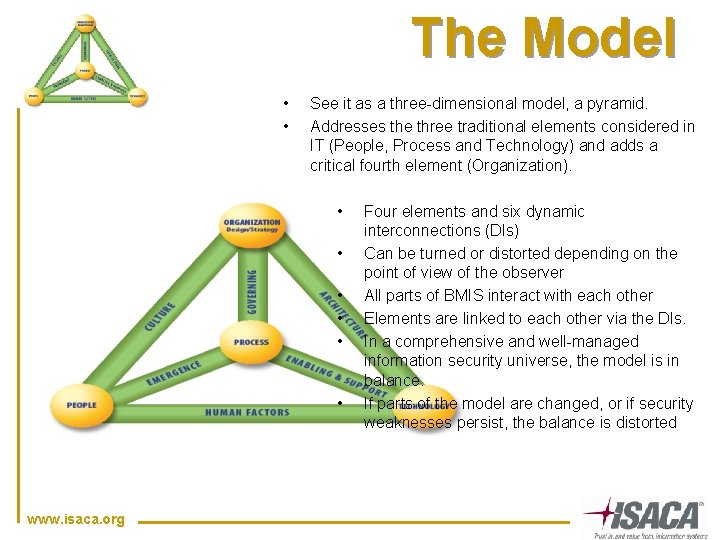
The Model • • See it as a three-dimensional model, a pyramid. Addresses the three traditional elements considered in IT (People, Process and Technology) and adds a critical fourth element (Organization). • • • www. isaca. org Four elements and six dynamic interconnections (DIs) Can be turned or distorted depending on the point of view of the observer All parts of BMIS interact with each other Elements are linked to each other via the DIs. In a comprehensive and well-managed information security universe, the model is in balance. If parts of the model are changed, or if security weaknesses persist, the balance is distorted
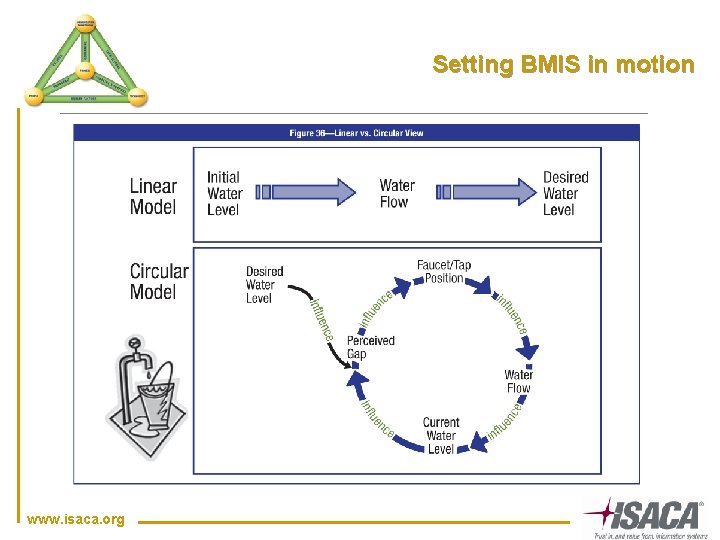
Setting BMIS in motion www. isaca. org
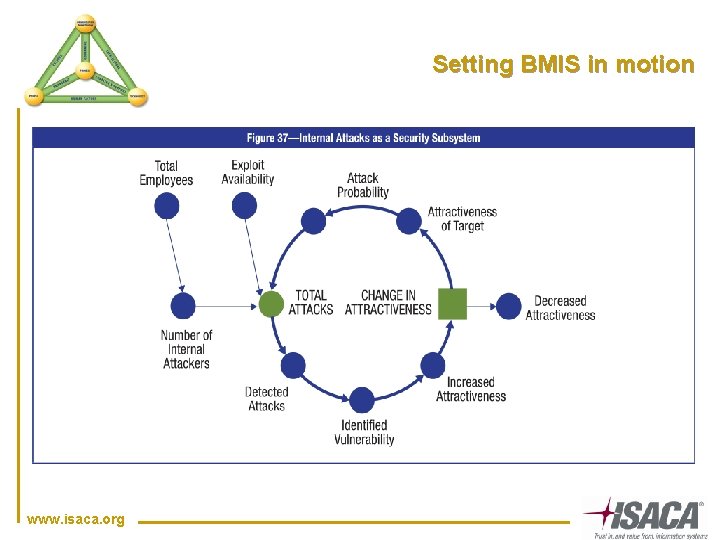
Setting BMIS in motion www. isaca. org
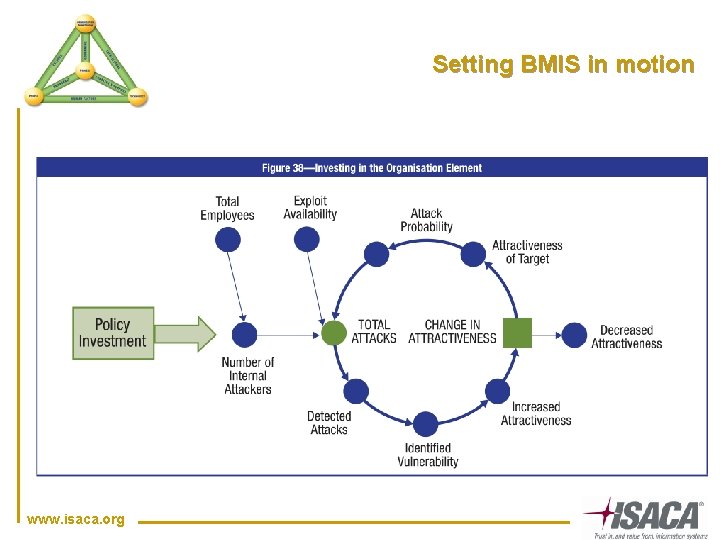
Setting BMIS in motion www. isaca. org
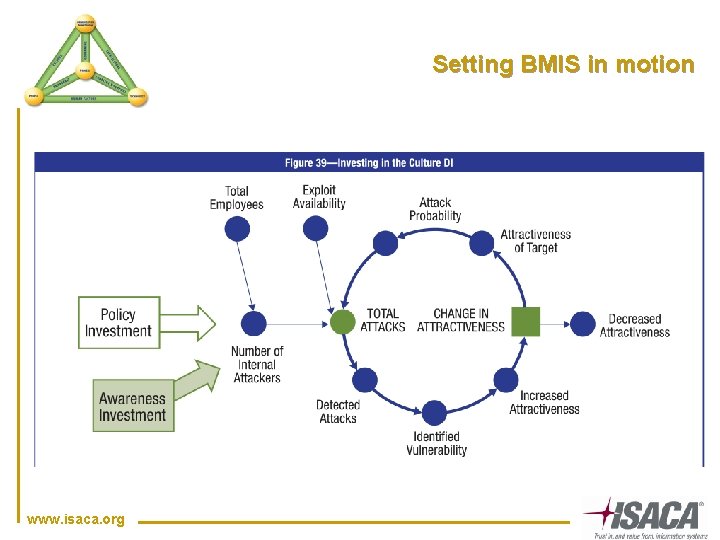
Setting BMIS in motion www. isaca. org
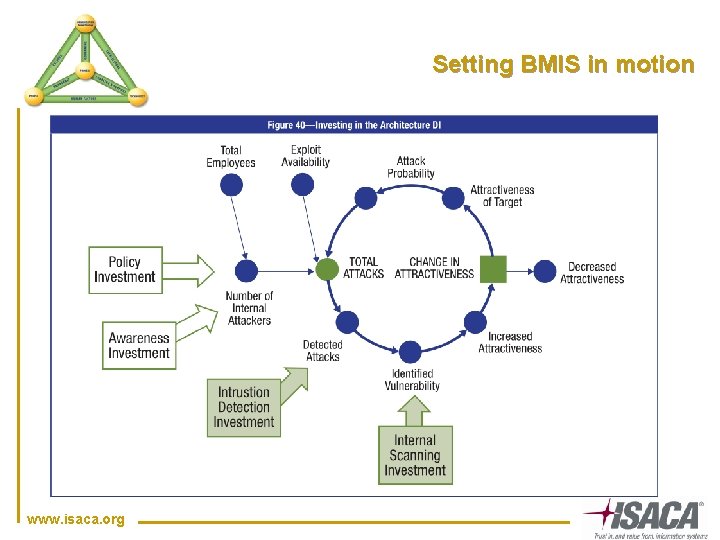
Setting BMIS in motion www. isaca. org
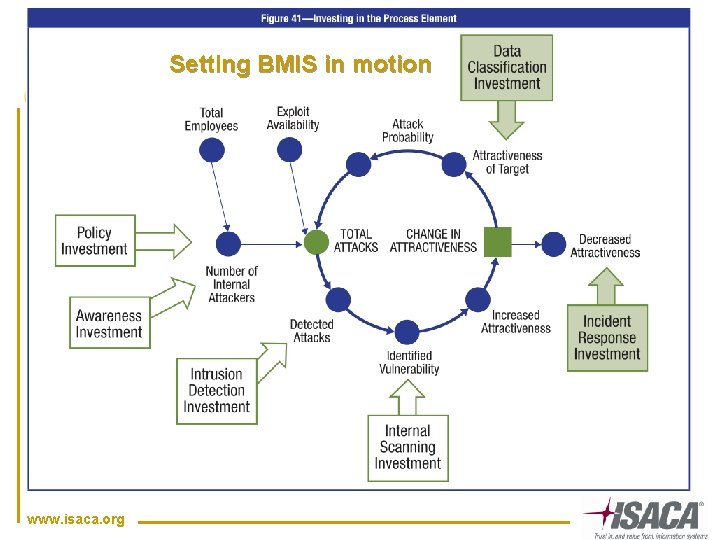
Setting BMIS in motion www. isaca. org
Conclusion • Any system, whether simple or complex, will react to changes from the inside and outside. • The system will either feed back or feed forward, depending on the circular dependencies. • A ‘systems approach ‘ instead of ‘more of the same’ approach • The actions can be reflected in a tabular format (example above) and linked to a framework: More on BMIS at www. isaca. org/bmis www. isaca. org

What should we expect From the environment: • Evolving challenges, as security professionals • Need for new solutions • Increase management of information security risks From ISACA and BMIS: • • Additional research reports exploring the Dynamic Interconnections Assessment on the impact on IS programme performance Practical guidance on using the BMIS model in various scenarios BMIS as a foundation for the upcoming Cobit Security Framework www. isaca. org

Radu Herinean ISACA Romania Chapter President radu. herinean@isaca. org – contact@isaca. org THANK YOU! www. isaca. org www. isaca. ro
- Slides: 21