A traceable threshold signature scheme with multiple signing

A traceable threshold signature scheme with multiple signing policies Authors :Jun Shao, Zhenfu Cao Source :Computer & Security, Volume 25, Issue 3, May 2006, Pages 201 -206 Speaker:Shao-Nung Huang Date : 2006/11/15 1

Outline n n n n Introduction Review of Li et al. ’s scheme Review of Lee’s Scheme The proposed scheme Security discussions Conclusions References 2
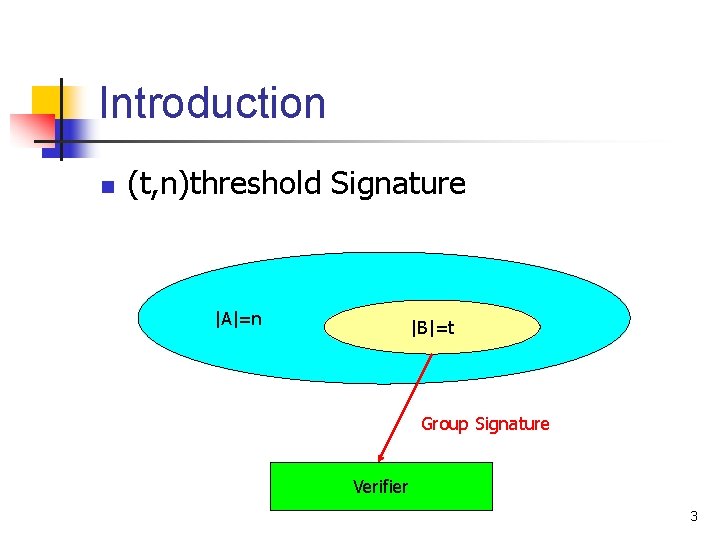
Introduction n (t, n)threshold Signature |A|=n |B|=t Group Signature Verifier 3

Review of Li et al. ’s scheme n n n Initialization phase Partial signature generation & verification phase Group signature generation & verification phase 4

Initialization phase n Needs a mutually trusted dealer to setup 5
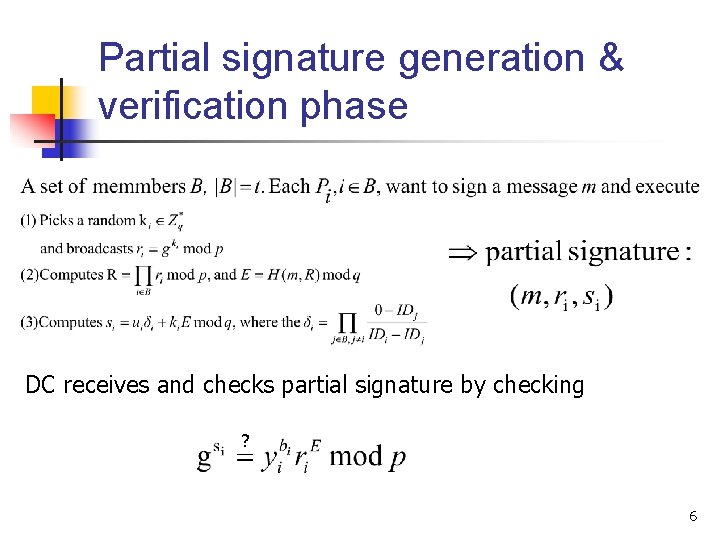
Partial signature generation & verification phase DC receives and checks partial signature by checking ? 6
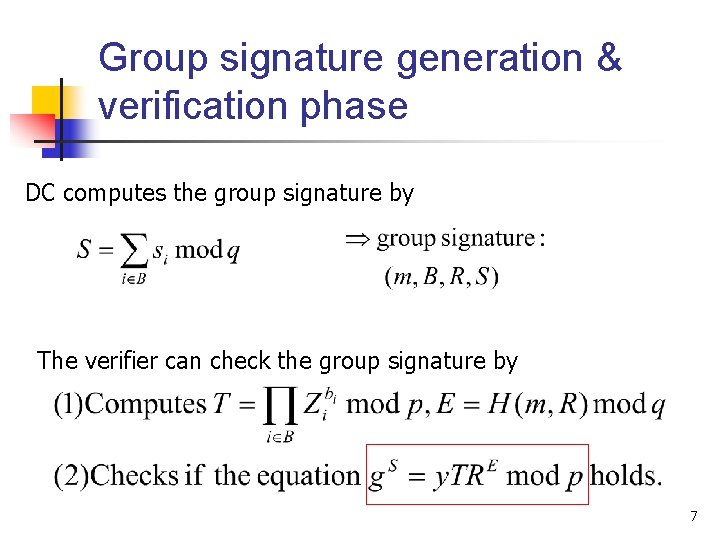
Group signature generation & verification phase DC computes the group signature by The verifier can check the group signature by 7

Review of Lee’s scheme n n n Initialization phase Partial signature generation Group signature generation & verification phase 8

Initialization phase n Needs a mutually trusted dealer to setup 9
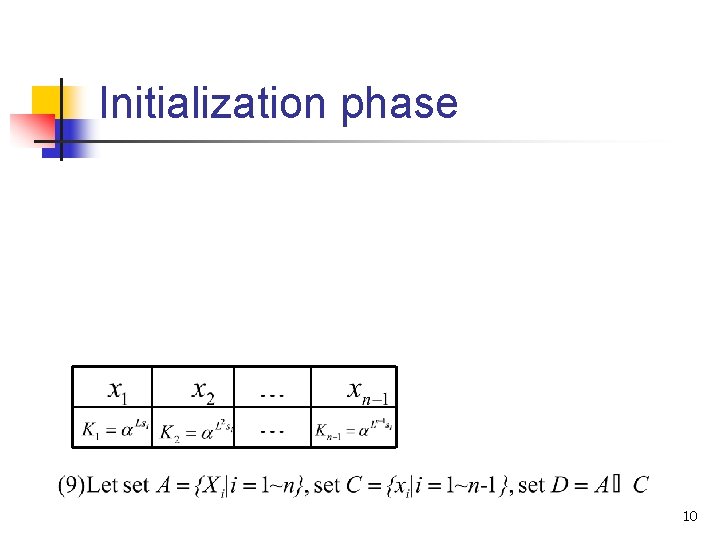
Initialization phase 10
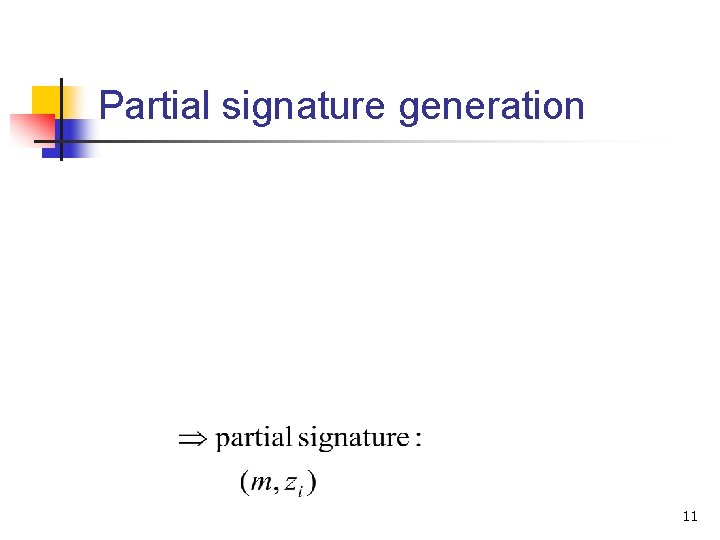
Partial signature generation 11
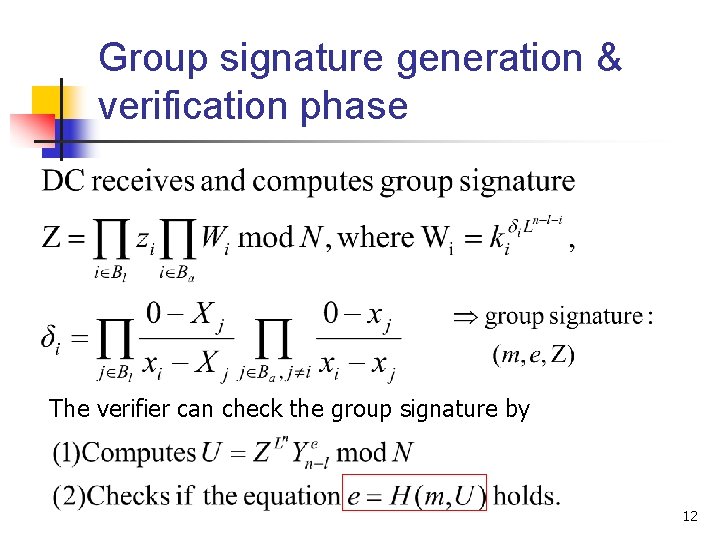
Group signature generation & verification phase The verifier can check the group signature by 12

The proposed scheme n n n Initialization phase Partial signature generation & verification phase Group signature generation & verification phase 13
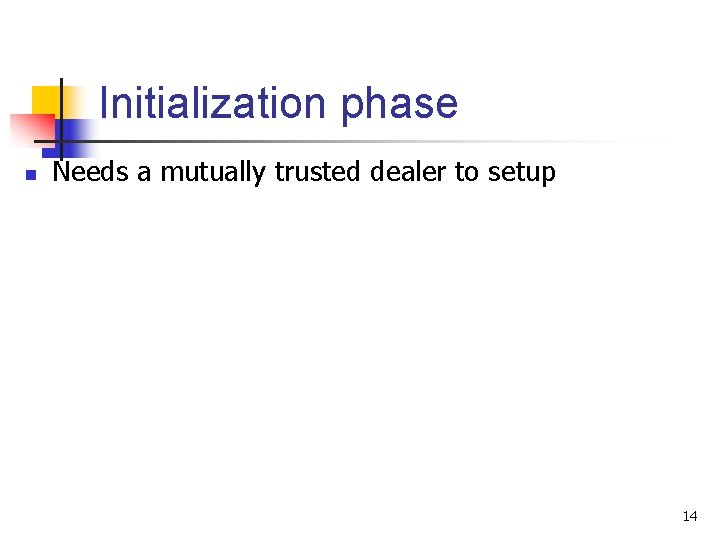
Initialization phase n Needs a mutually trusted dealer to setup 14

Initialization phase 15
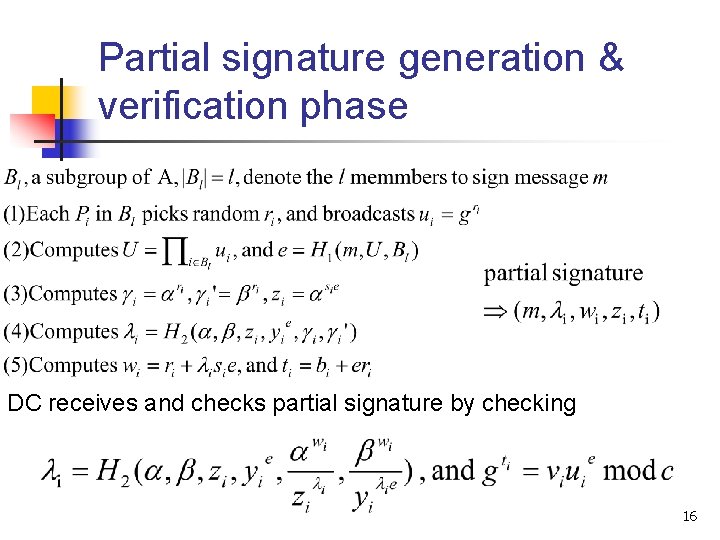
Partial signature generation & verification phase DC receives and checks partial signature by checking 16

Group signature generation & verification phase DC combines the partial signatures to the group signature The verifier can check the group signature by 17

Security discussions n n Consistency Unforgeability 18

Conclusions n n Based on the schemes of Li et al. and Lee We have devised a traceable threshold signature scheme with multiple signing policies. 19
- Slides: 19