A Tale of Research From Crowds to Deeper















- Slides: 27

A Tale of Research: From Crowds to Deeper Understandings Matthew Wright Jan. 25, 2006 6392 -017: Adv. Network Security

Overview • Act I: Hordes – Applying a tool elsewhere • Act 2: The “Predecessor Attack” – – How it works Proof Analysis Simulation • Act 3: (then) Future Directions

A New Application • Brian Levine & Clay Shields – Multicast & Networking • Properties of Multicast – many receivers – tree structure – subscription model • Status is unknown to routers and hosts • Bad for maintenance – efficient for streaming

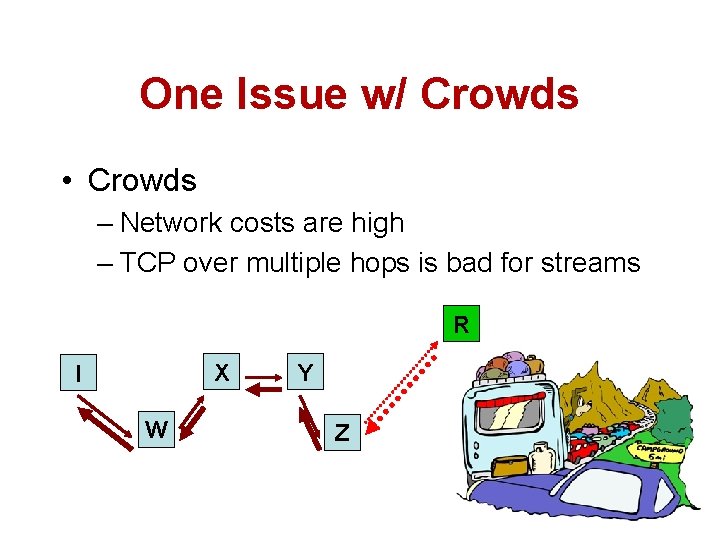
One Issue w/ Crowds • Crowds – Network costs are high – TCP over multiple hops is bad for streams R X I W Y Z

Hordes • Crowds 4 outgoing – (requests, ACKs) • Multicast 4 incoming streams – Everyone joins multiple trees – Don’t know who’s on each tree – Don’t know who’s listening

Act I Lessons • Understanding Prior Work – Find problems & try to solve them • Apply New Tools – Rather, old tools, but new to the area

Act II: Another Issue w/ Crowds • What does 5. 3. 2 say? • What does it not say?

Adding New Members • If paths are maintained indefinitely, any member joining the group would be immediately identifiable as the initiator. • Because of this, group joins occur in batches (e. g. , once every hour). • Each time new members are allowed in, new paths are created for all members.

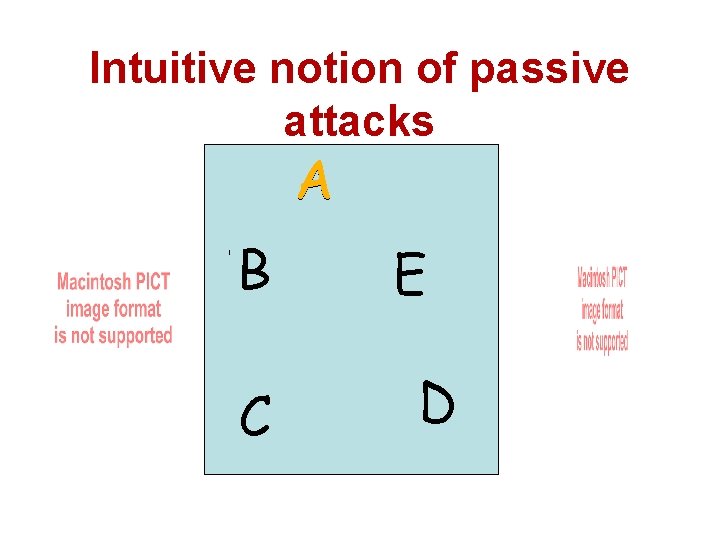
Intuitive notion of passive attacks A B W T C X Z E D Y

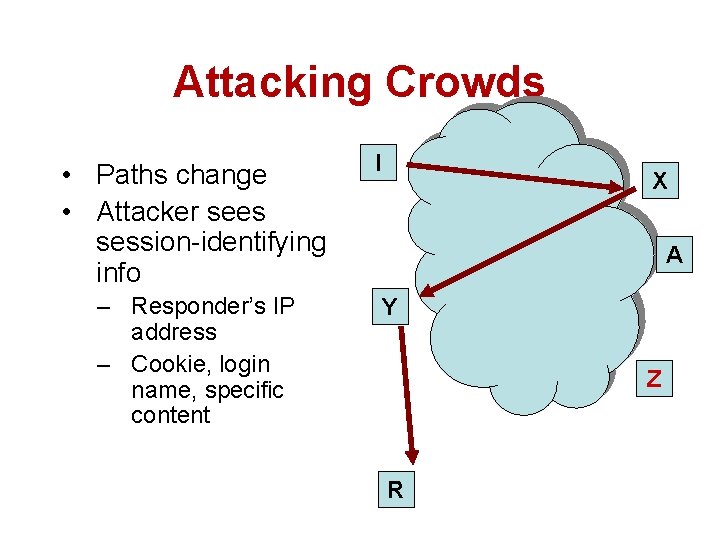
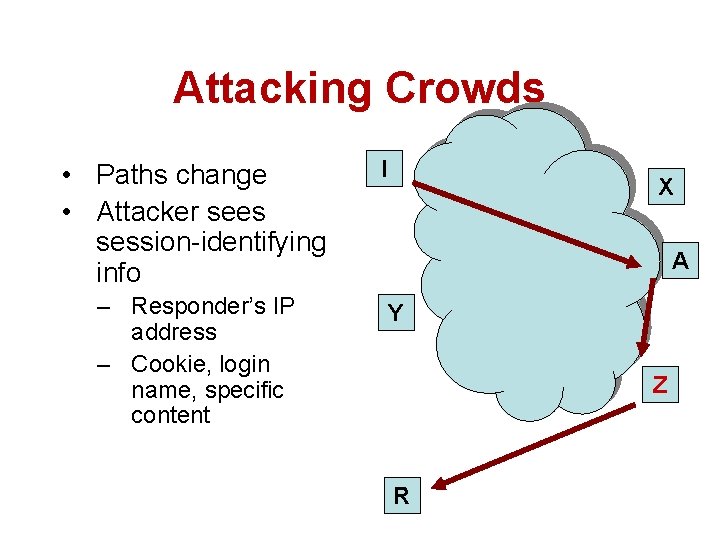
Attacking Crowds • Paths change • Attacker sees session-identifying info – Responder’s IP address – Cookie, login name, specific content I X A Y Z R

Attacking Crowds • Paths change • Attacker sees session-identifying info – Responder’s IP address – Cookie, login name, specific content I X A Y Z R

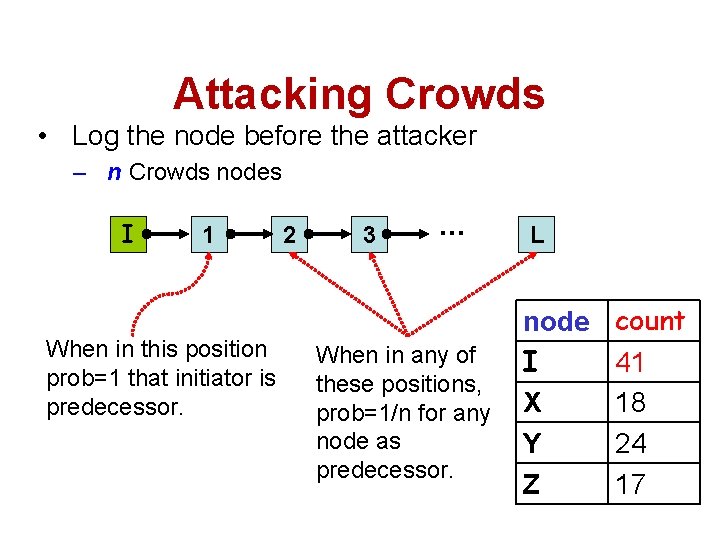
Attacking Crowds • Log the node before the attacker – n Crowds nodes I 1 When in this position prob=1 that initiator is predecessor. 2 3 … When in any of these positions, prob=1/n for any node as predecessor. L node I X Y Z count 41 18 24 17

Question • What are the contributions of WALS 02?

Attacking in General • Attack applies to any protocol for anonymity, provided that: – Paths* of proxies change – Uniformly random selection of paths – There exists a position of attackers: • see the initiator send messages in the session • determine the session information

Crowds Analysis • Goal: Quantify time required for attack to succeed • Notation – n is the number of Crowds nodes – c is the number of attackers nodes (c < n ) • Observations – Probability of selecting an attacker for a given position: (c / n ) n - nodes c - attackers

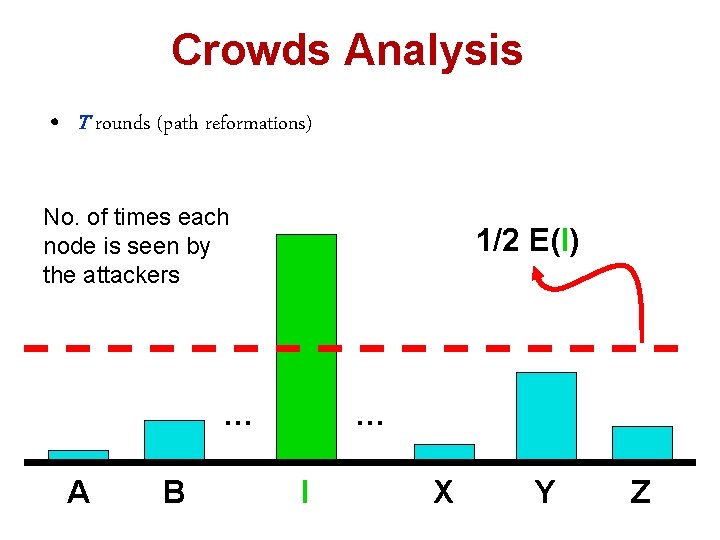
Crowds Analysis • T rounds (path reformations) No. of times each node is seen by the attackers 1/2 E(I) … A B … I X Y Z

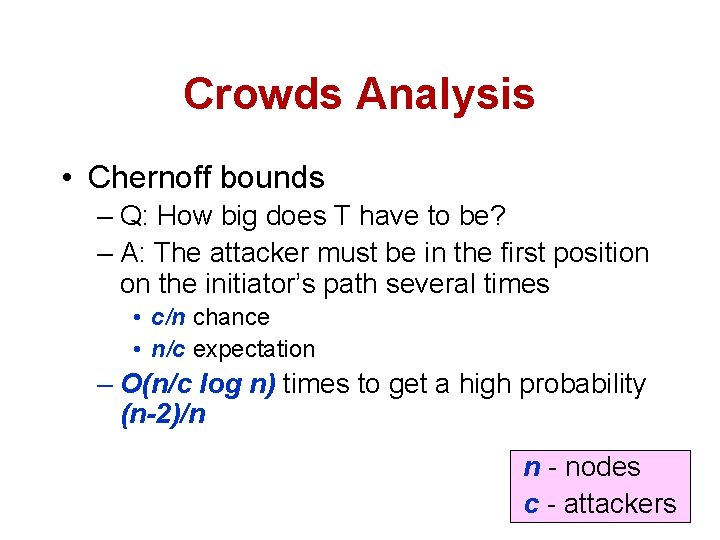
Crowds Analysis • Chernoff bounds – Q: How big does T have to be? – A: The attacker must be in the first position on the initiator’s path several times • c/n chance • n/c expectation – O(n/c log n) times to get a high probability (n-2)/n n - nodes c - attackers

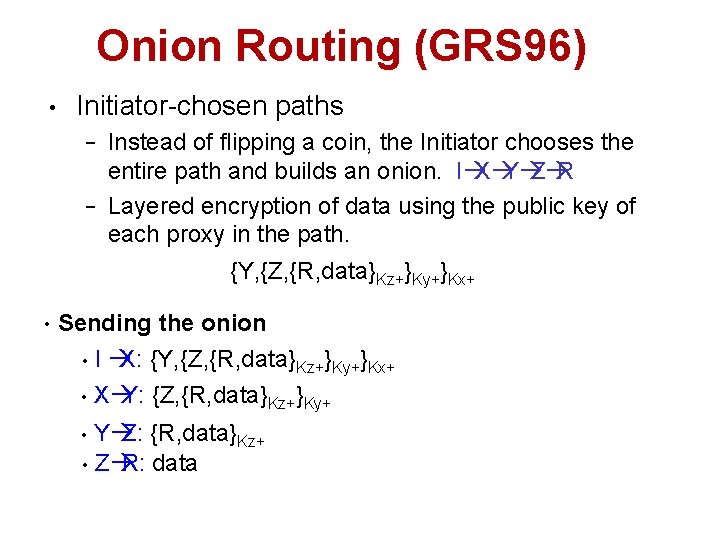
Onion Routing (GRS 96) • Initiator-chosen paths − − • Instead of flipping a coin, the Initiator chooses the entire path and builds an onion. IàXàYàZàR Layered encryption of data using the public key of each proxy in the path. {Z, {R, data} {Y, {Z, {R, data} data Kz+}Ky+ }Kx+ Sending the onion I àX: {Y, {Z, {R, data}Kz+}Ky+}Kx+ • Xà Y: {Z, {R, data}Kz+}Ky+ • YàZ: {R, data}Kz+ • Zà R: data •

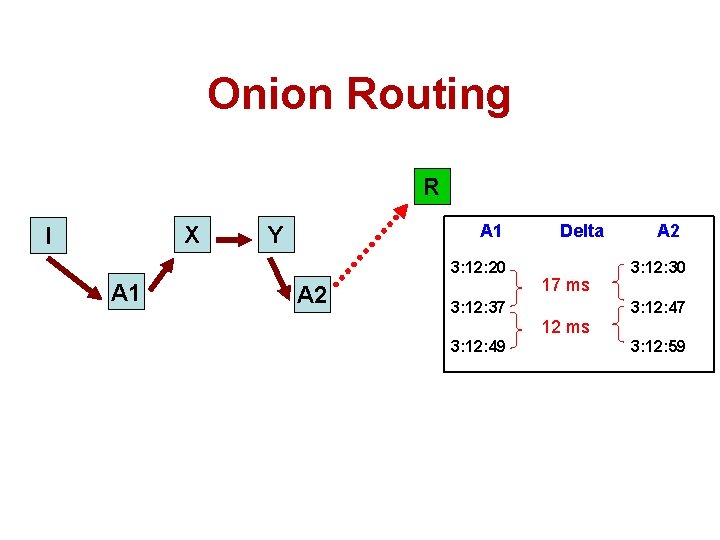
Onion Routing R X I A 1 Y 3: 12: 20 A 1 A 2 Delta 17 ms 3: 12: 37 A 2 3: 12: 30 3: 12: 47 12 ms 3: 12: 49 3: 12: 59

Mix-Nets (Ch 81+) • Same as Onion Routing • Added – Dummy messages – Batching – Message reordering • Stops Timing attacks

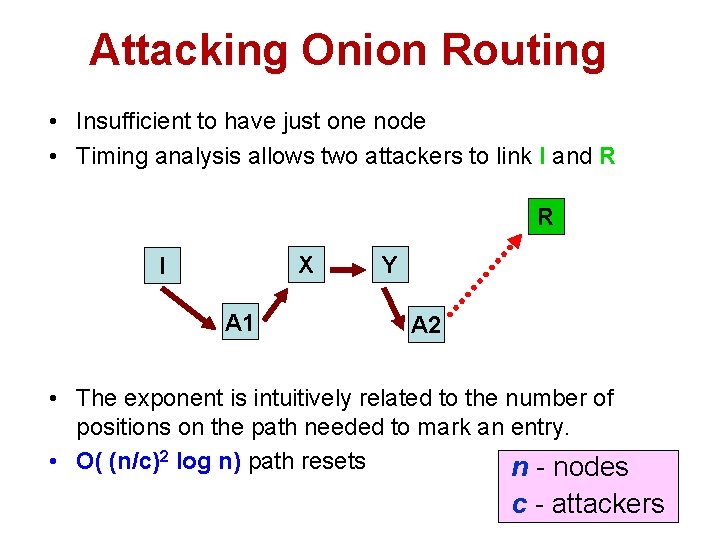
Attacking Onion Routing • Insufficient to have just one node • Timing analysis allows two attackers to link I and R R X I A 1 Y A 2 • The exponent is intuitively related to the number of positions on the path needed to mark an entry. • O( (n/c)2 log n) path resets n - nodes c - attackers

Attacking Mix-Nets • Mixing – – – • Stops timing attacks – – • O. R. attack no longer works Need the entire path to trace the message To attack Mix-nets, if the path is L nodes long, then L attackers have to appear in sequence. – • Reordering messages Dummy messages Delay In each round, chances are (c/n)L. O( (n/c)L log n) path resets n - nodes c - attackers

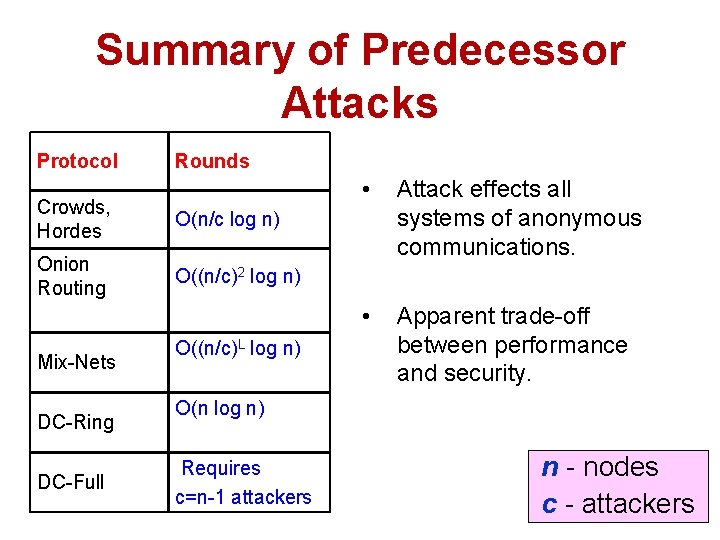
Summary of Predecessor Attacks Protocol Rounds Crowds, Hordes O(n/c log n) Onion Routing O((n/c)2 log n) Mix-Nets DC-Ring DC-Full O((n/c)L log n) • Attack effects all systems of anonymous communications. • Apparent trade-off between performance and security. O(n log n) Requires c=n-1 attackers n - nodes c - attackers

Act II Lessons • Answer open questions – Is it efficient enough for X application? – What are the tradeoffs here? • Generalize solutions (or attacks) – Where else does this apply? – Can it be modified to apply to a group? • With what costs/issues?

Act III: The next step • What did WALS 02 leave unanswered?

Questions (II) • Consequences for users? – You’re not secure forever • How tight are these bounds? • Are there defenses?

Assumptions that can be broken • We assumed that all nodes are chosen for each spot on the path with equal probability – What if nodes are chosen with a bias?
 Into the heart of jesus deeper and deeper i go
Into the heart of jesus deeper and deeper i go Cliques and crowds
Cliques and crowds Panic causal crowd
Panic causal crowd Flash crowds
Flash crowds Bustling crowds
Bustling crowds The chief determinant of popularity in high school is
The chief determinant of popularity in high school is The wisdom of crowds
The wisdom of crowds Conventional crowd
Conventional crowd When does a “folk tale” become a “tall tale”?
When does a “folk tale” become a “tall tale”? Go deeper in christ
Go deeper in christ Deeper life bible church netherlands
Deeper life bible church netherlands Dclm netherlands
Dclm netherlands Deeper life bible church netherlands
Deeper life bible church netherlands Dclm search the scriptures volume 1
Dclm search the scriptures volume 1 What is deeper exam
What is deeper exam Deeper life sunday message
Deeper life sunday message Dclm netherlands
Dclm netherlands Vdoe teacher direct
Vdoe teacher direct Deeper life bible church
Deeper life bible church Search the scriptures netherlands
Search the scriptures netherlands Growing deeper in god
Growing deeper in god Deeper life netherlands
Deeper life netherlands Deeper life netherlands
Deeper life netherlands Dclm netherlands
Dclm netherlands Deeper life bible church netherlands search the scriptures
Deeper life bible church netherlands search the scriptures Deeper life netherlands
Deeper life netherlands Vietnam war at home webquest answers
Vietnam war at home webquest answers Deeper life canada
Deeper life canada