A Sketch Algorithm to Monitor High Packet Delay










- Slides: 29

A Sketch Algorithm to Monitor High Packet Delay in Network Traffic Jiaqi Zhu, Kai Zhang, Qun Huang 1

Motivation • Network measurement provides information for management • • • Heavy hitter Heavy changer Superspreader Packet delay … 2

Motivation • Network measurement provides information for management • • • Heavy hitter Heavy changer Superspreader Packet delay – indicator of network health … 3

Motivation • Network measurement provides information for management. • • • Heavy hitter Heavy changer Superspreader Packet delay – indicator of network health … • We focus on Intra-Flow Packet Delay (IFPD) • The time span between two adjacent packets of one flow • Helpful to monitor network health 4

Related Works • Lightweight delay monitoring methods • By sampling / injecting probe packets • LDA [Kompella et al. 09]; RLI [Lee et al. 10]; LDS [Sanjuàs-Cuxart et al. 11]; OPA [Wang et al. 19]; Fine. Comb [Lee et al. 11] • Not giving every IFPD in detail 5

Our work • Propose a sketch-based approach to detect high IFPD • High accuracy • Low space usage • Experiments on real-world traces 6

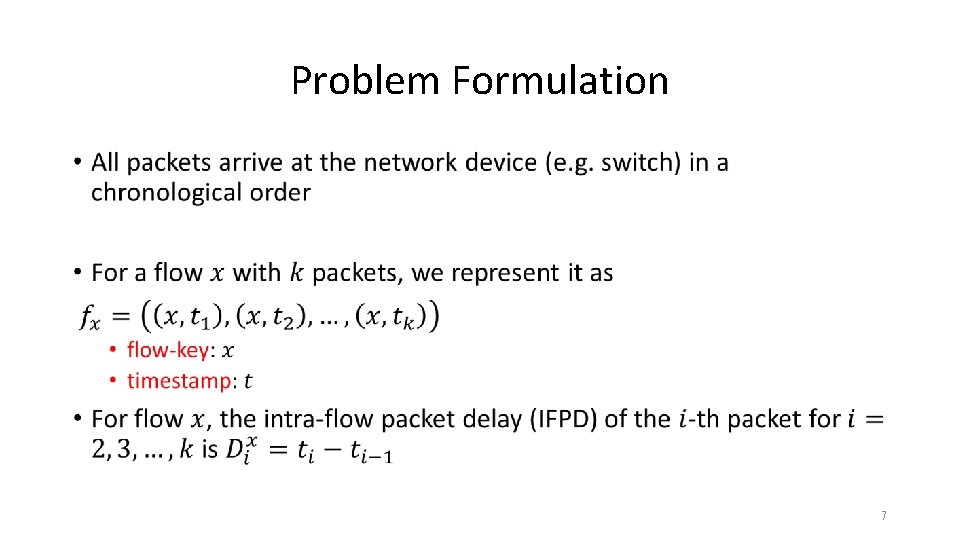
Problem Formulation • 7

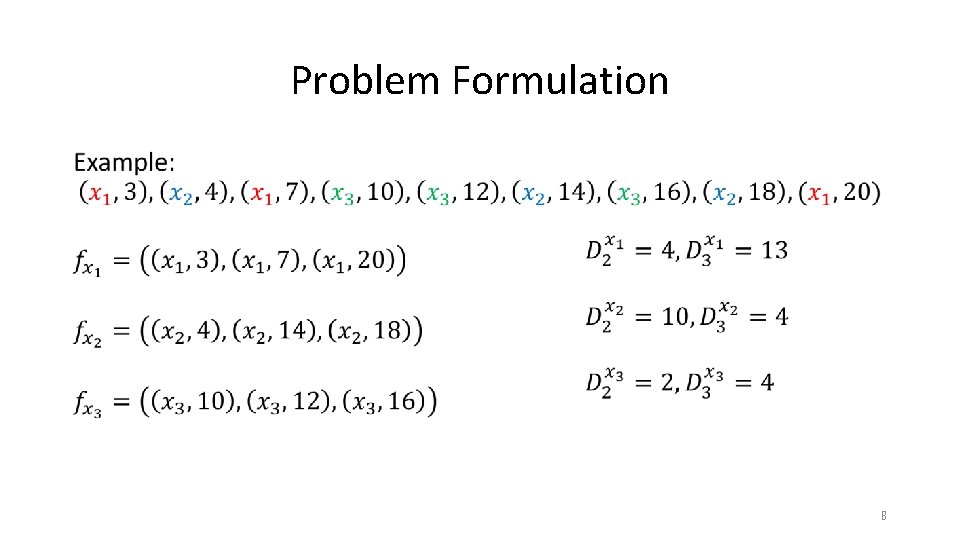
Problem Formulation • 8

Problem Formulation • Our Goal: High IFPD Detection Given a threshold �� , our primary goal is to report all packets whose IFPD exceeds �� • Accurate algorithm consumes too much resource • Use approximation algorithm • High accuracy • High precision and recall • Low error • Low resource usage 9

Sketch Algorithms • A family of data structures comprising of multiple buckets • Each bucket accommodates multiple flows • Use independent hash functions to mitigate the errors • Widely used in network measurement • Flow size estimation • Heavy hitter detection 10

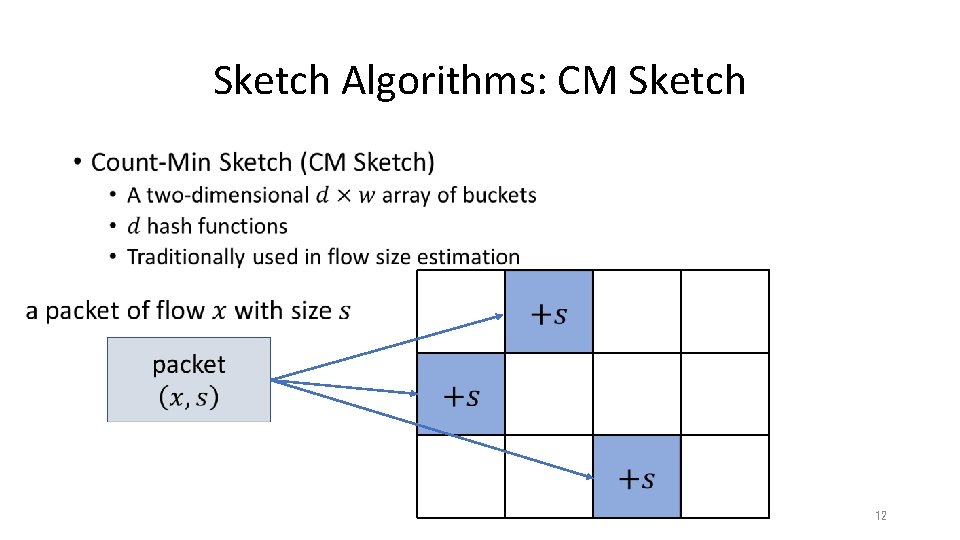
Sketch Algorithms: CM Sketch • 11

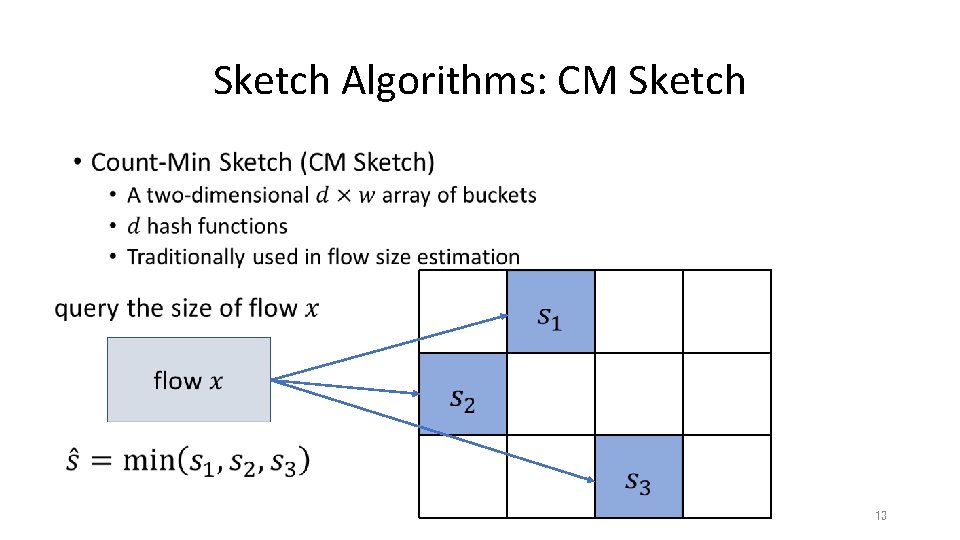
Sketch Algorithms: CM Sketch • 12

Sketch Algorithms: CM Sketch • 13

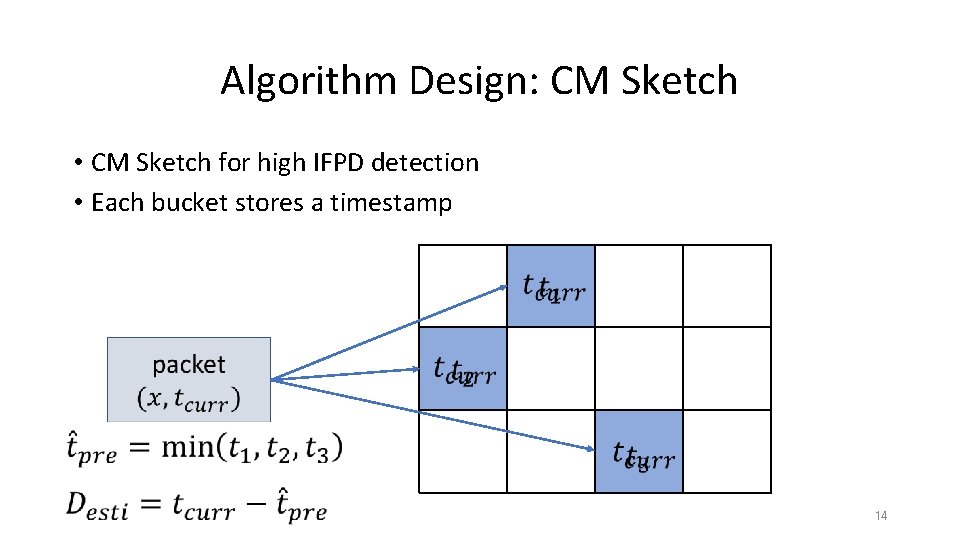
Algorithm Design: CM Sketch • CM Sketch for high IFPD detection • Each bucket stores a timestamp 14

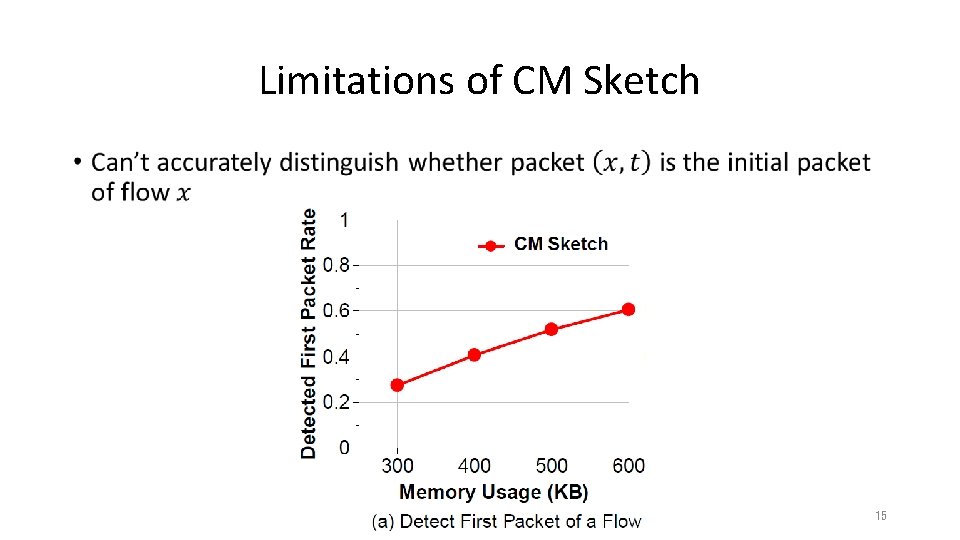
Limitations of CM Sketch • 15

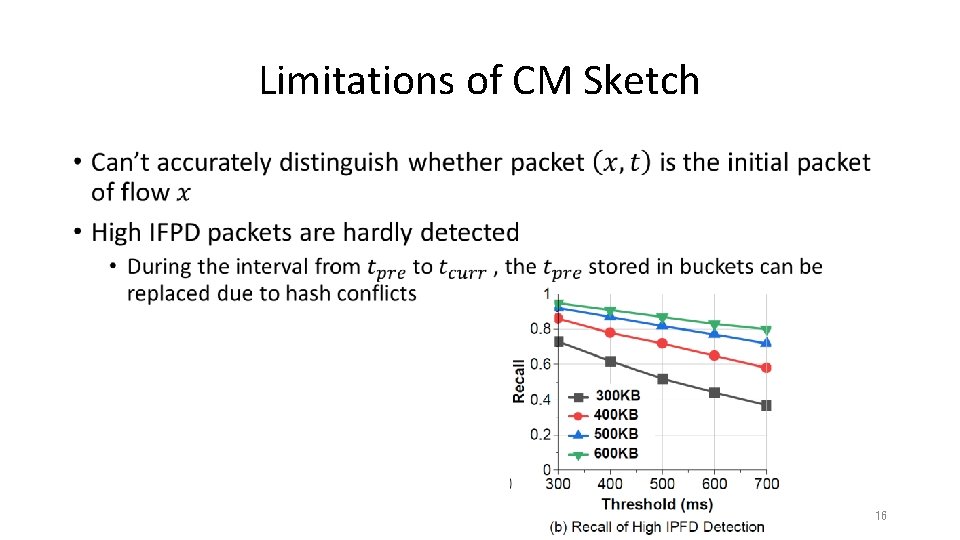
Limitations of CM Sketch • 16

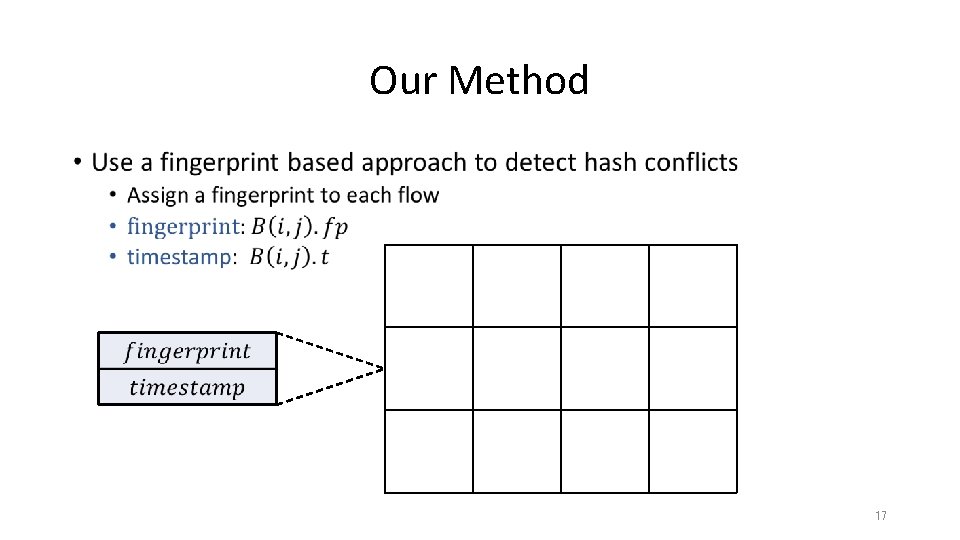
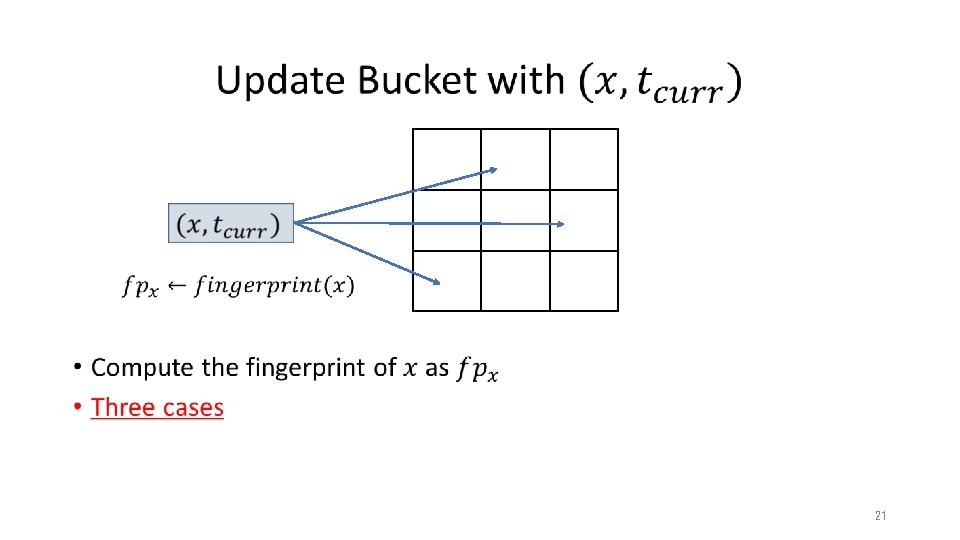
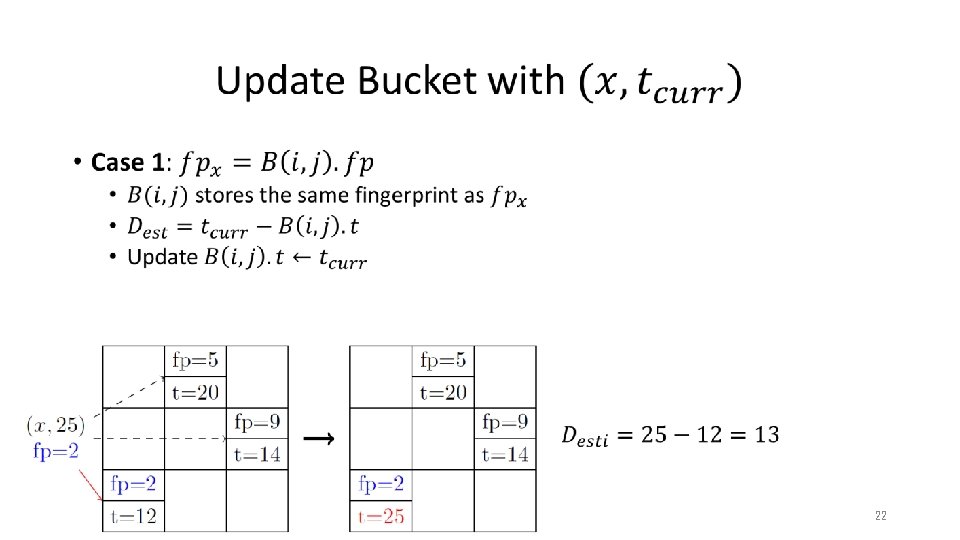
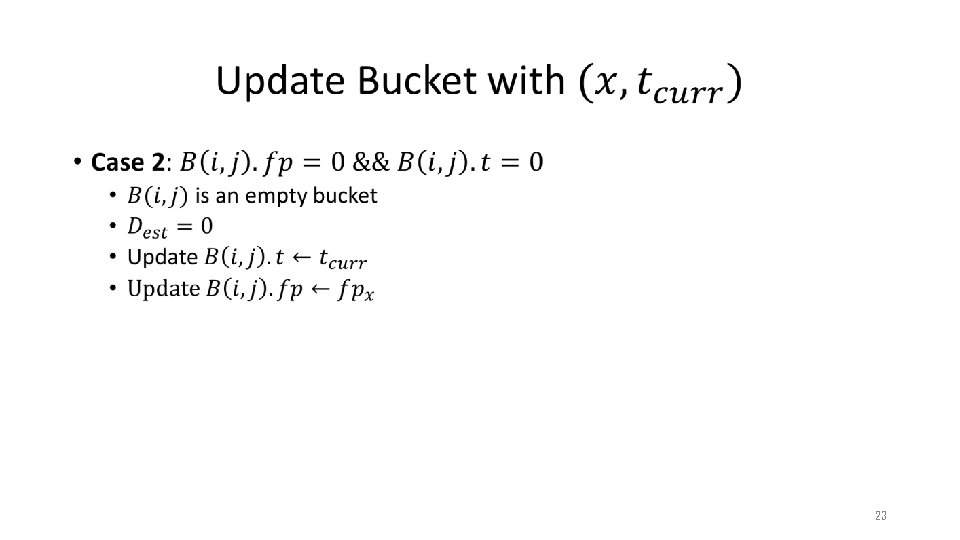
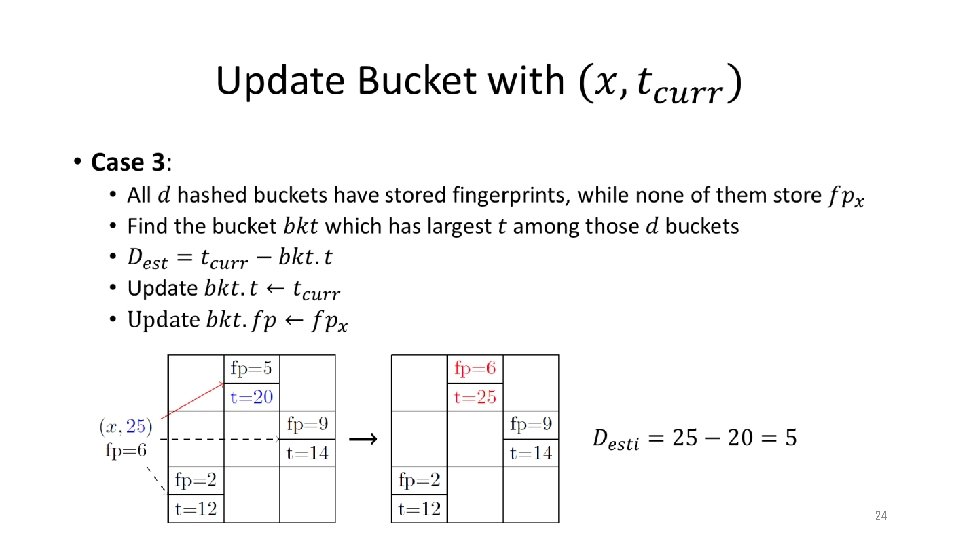
Our Method • 17

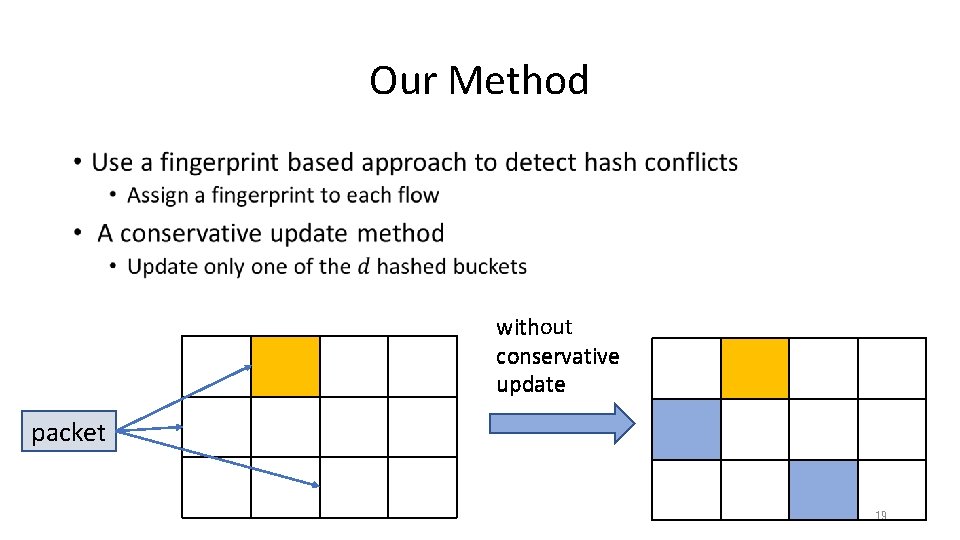
Our Method • 18

Our Method • without with conservative update packet 19

Our Method • 20





Experimental Setup • Implementation: C++ • Dataset: CAIDA traces • divide each trace into segments of 2 seconds • each segment has 1, 000 packets of 90, 000 flows • Baseline: • CM Sketch with a Bloom Filter (CM-BF) • Use a bloom filter to detect the first packet of a flow • Our Method 25

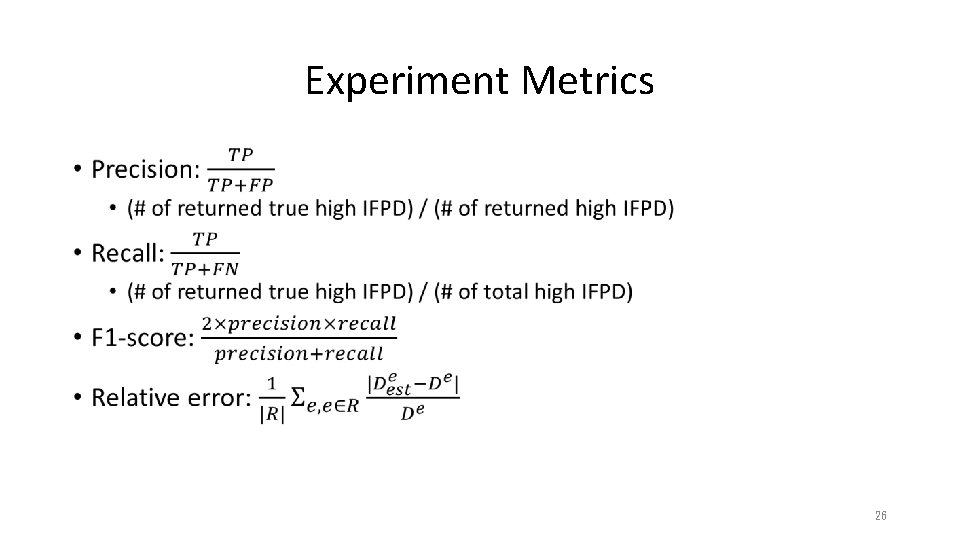
Experiment Metrics • 26

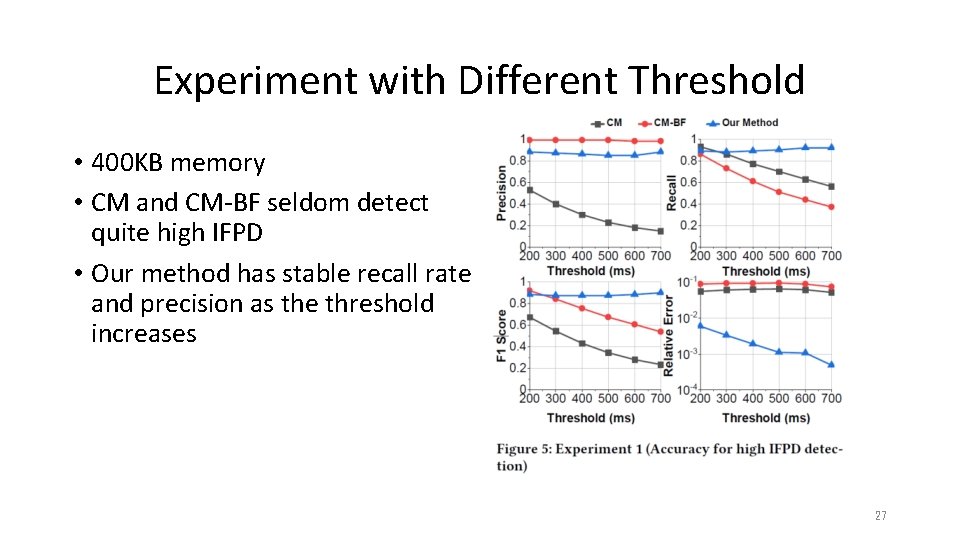
Experiment with Different Threshold • 400 KB memory • CM and CM-BF seldom detect quite high IFPD • Our method has stable recall rate and precision as the threshold increases 27

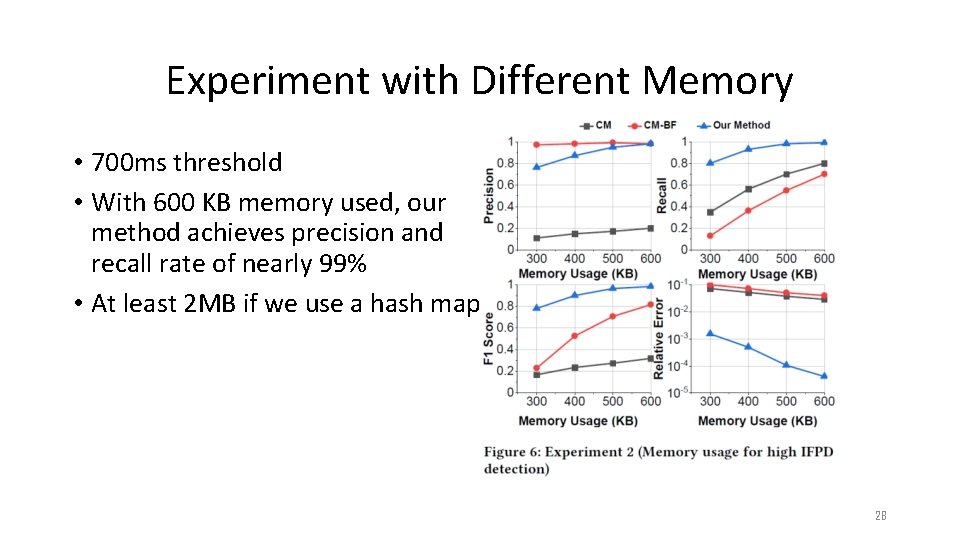
Experiment with Different Memory • 700 ms threshold • With 600 KB memory used, our method achieves precision and recall rate of nearly 99% • At least 2 MB if we use a hash map 28

Conclusion • High intra-flow packet delay (IFPD) detection • Find limitations of traditional sketch algorithms • Propose a new sketch algorithm • Use fingerprints to detect hash conflicts • A conservative update method • A replacement strategy • The evaluation driven by real world traces shows our method has high accuracy with low resource usage 29