A Signaturelike Primitive for Broadcastencryptionbased Systems Jeffrey Lotspiech

A Signature-like Primitive for Broadcast-encryptionbased Systems Jeffrey Lotspiech IBM Almaden Research Center

Overview Motivation Broadcast encryption basics The scheme Attacks/defenses Conclusion

Motivation – “Broadcast Encryption” A term describing a class of key management schemes n “One-way” cryptographic flow Essential for protection of physical media (e. g. , DVDs) n n Over one billion CPRM devices licensed so far (e. g. , SD cards, DVD RAM/R/RW) Used for AACS (new generation of DVDs) Not based on identity n n Great for high-privacy applications Not so great forensics Very friendly to consumer electronic devices

Motivation – “Electronic Sell-through” Download of a movie onto a recordable DVD n n Richer format compared to broadcast recording, therefore only for server/client download, not recorders Possible attack: “Garage replicator” There would be additional security if there were a “server blessing” n n E. g. , a server-signed token for the individual disc Easily accomplished by a public key infrastructure But, high overhead calculation
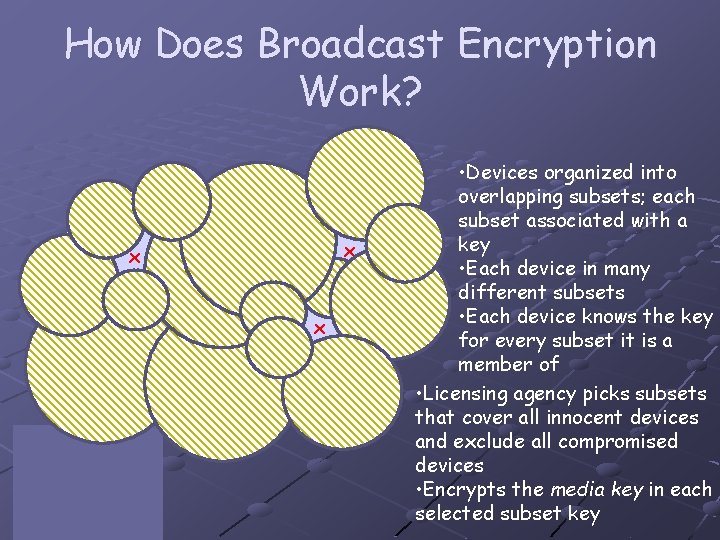
How Does Broadcast Encryption Work? x Devices x • Devices organized into overlapping subsets; each subset associated with a key • Each device in many different subsets • Each device knows the key for every subset it is a member of • Licensing agency picks subsets that cover all innocent devices and exclude all compromised devices • Encrypts the media key in each selected subset key

Media Key Block Identify subsets Encrypt Media Key for each Media key block
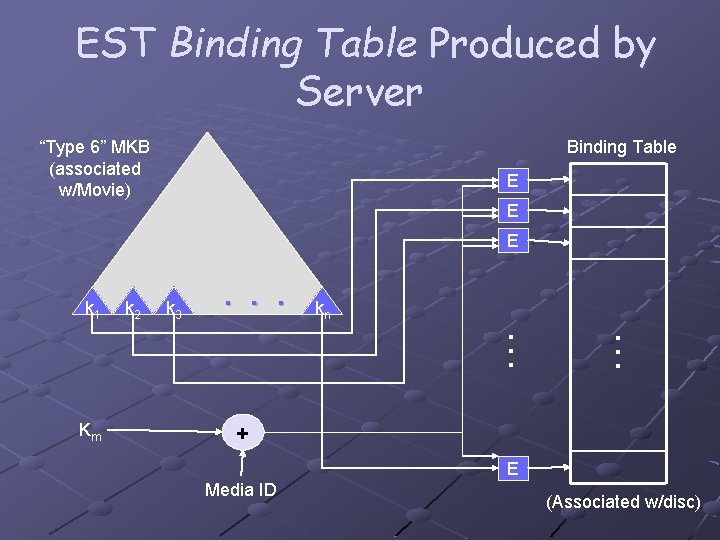
EST Binding Table Produced by Server “Type 6” MKB (associated w/Movie) Binding Table E E E k 1 k 2 k 3 . . . kn … … Km + E Media ID (Associated w/disc)
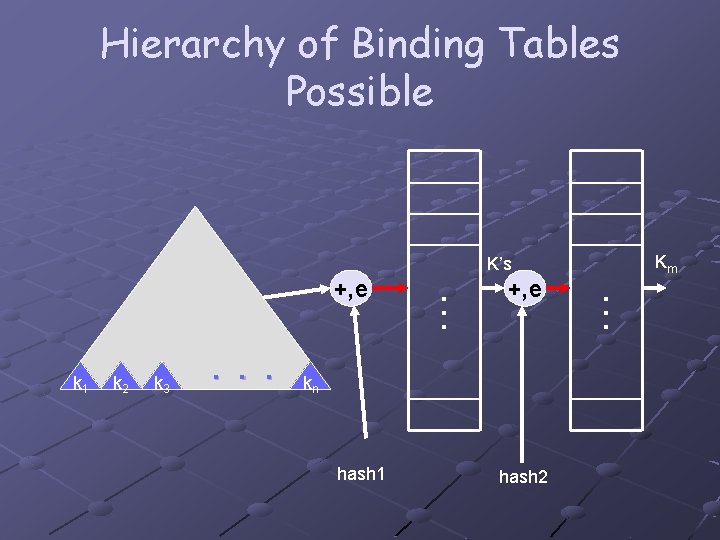
Hierarchy of Binding Tables Possible Km K’s k 2 k 3 . . . +, e kn hash 1 hash 2 … k 1 … +, e

Attacks A set of device keys helps very little n Binding table is valid for only one entry (e. g. , 1/1000 th of the market, under control of content owners) Licensing agency can respond effectively by subdividing new MKBs n E. g. , doubling size of binding table reduces attack to 1/1, 000 th of the market Makes “Garage Replicator” attack uneconomic n Other uses of stolen devices keys are more effective

Conclusions Only authorized servers can make widely playable EST downloads By using broadcast encryption instead of public key signatures: n n Transactions per second at the server greatly increased (for a given server cost) No difference in “disc insertion time” at player for pre-recorded versus EST download.
- Slides: 10