A Review of Current Routing Protocols for Ad








- Slides: 83

A Review of Current Routing Protocols for Ad Hoc Mobile Wireless Networks q q q IEEE Personal Communications, April 1999, pp. 46 -55 E. Royer and C. -K. Toh MANET: 1

Introduction q Two types of wireless networks: l infrastructured network: Ø base stations are the bridges Ø a mobile host will communicate with the nearest base station Ø handoff is taken when a host roams from one base to another l ad hoc network: Ø infrastructureless: no fixed base stations Ø without the assistance of base stations for communication Ø Due to transmission range constraint, ü two MHs need multi-hop routing for communication Ø quickly and unpredictably changing topology 2

MANET q MANET = Mobile Ad Hoc Networks l a set of mobile hosts, each with a transceiver l no base stations; no fixed network infrastructure l multi-hop communication l needs a routing protocol which can handle changing topology 3

Applications of MANET q battlefields q nature disaster areas q fleet in oceans q historical cites q festival ground 4

Related Research q IEEE 802. 11 for Wireless LANs l MAC l PHY q IETF manet group l to stimulate research and discuss possible standards in this area q Routing Protocols: l unicast – AODV, DSR, ZRP, TORA, CBRP, CEDAR l multicast – MAODV, AMRoute, ODMRP, AMRIS 5

Resources and Applications q NS-2: l AODV, DSR, DSDV, TORA q Telcordia: Intelligent Transportation System l AODV l MAODV: to distributed emergency information 6

Challenge of Ad Hoc Networks q No centralized entity q Mobile host is no longer just an end system q Acting as an intermediate system q Changing network topology over time q Every node can be mobile 7

Routing in MANET: 8

Can Existing Internet Routing Protocols Be Used for MANET? q Link-state Routing q Distance-vector Routing 9

Link State Routing: Dijkstra’s Algorithm q Each node keeps its link state to its neighbors. q From each node, we gradually expand a spanning tree, until all nodes are scanned. 10

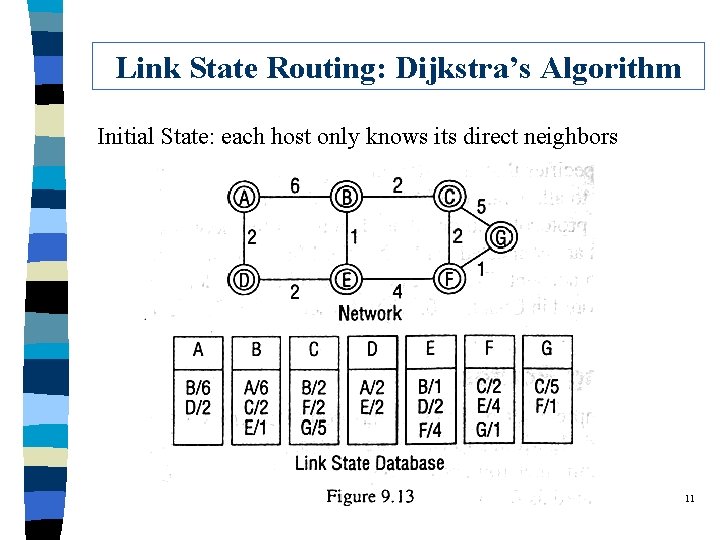
Link State Routing: Dijkstra’s Algorithm Initial State: each host only knows its direct neighbors 11

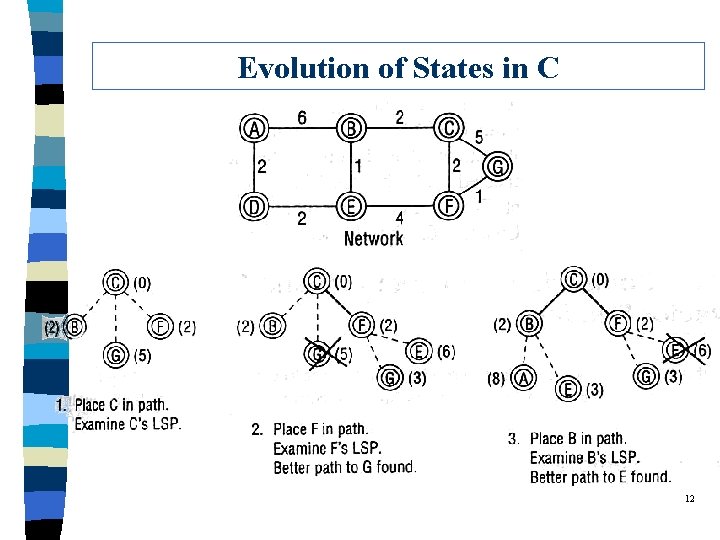
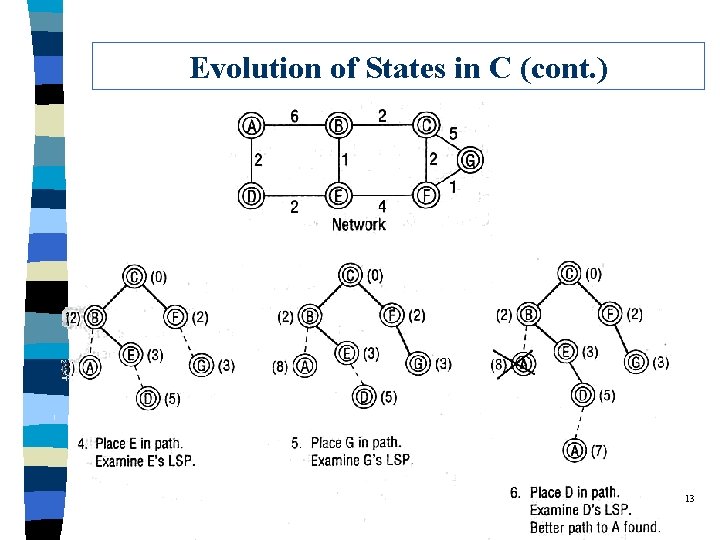
Evolution of States in C 12

Evolution of States in C (cont. ) 13

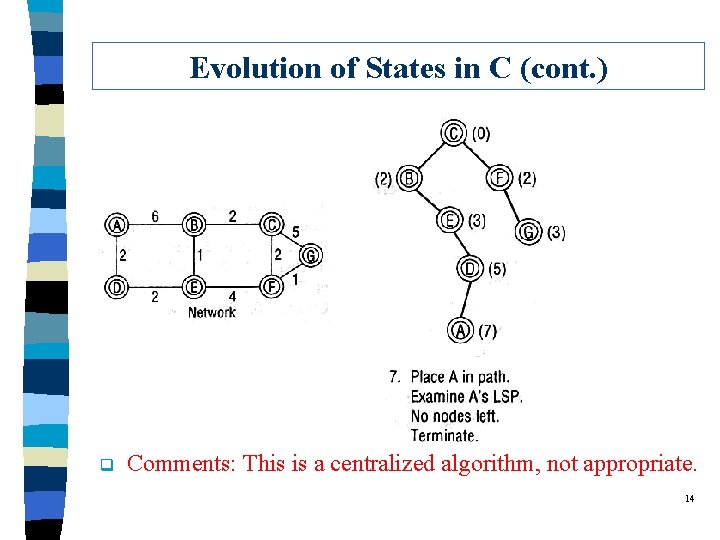
Evolution of States in C (cont. ) q Comments: This is a centralized algorithm, not appropriate. 14

Overview of Current Routing Protocols 15

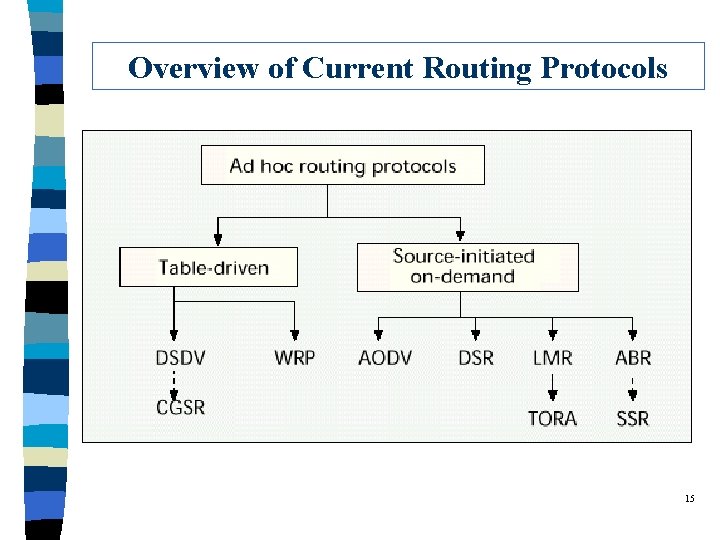
On-demand vs. Table-driven q Table-Driven Routing Protocol: l proactive!! l continuously evaluate the routes l attempt to maintain consistent, up-to-date routing information Ø when a route is needed, one may be ready immediately l when the network topology changes Ø the protocol responds by propagating updates throughout the network to maintain a consistent view 16

q Source-Initiated On-Demand Routing Protocol: l reactive!! l on-demand style: create routes only when it is desired by the source node Ø route discovery: invoke a route-determination procedure Ø the procedure is terminated when ü a route has been found ü no route is found after all route permutations are examined l longer delay: sometimes a route may not be ready for use immediately when data packets come 17

Table-Driven Routing Protocols q Protocol 1: l DSDV: Destination Sequence Distance Vector q Protocol 2: l CGSR: Clustered Gateway Switch Routing MANET: 18

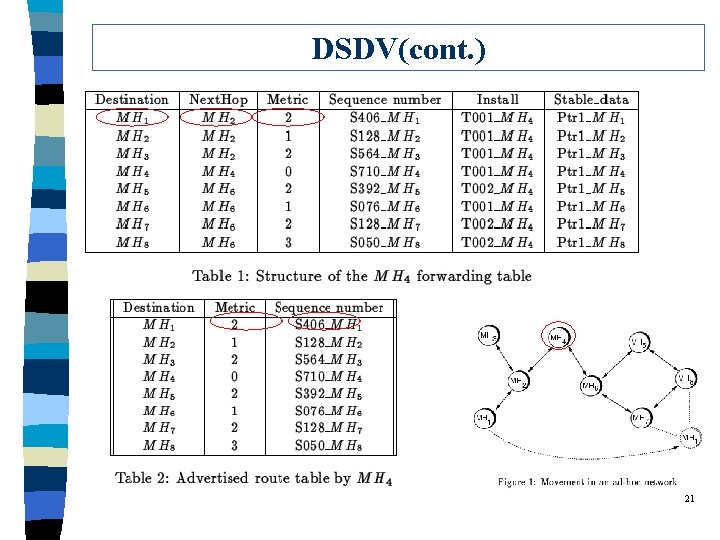
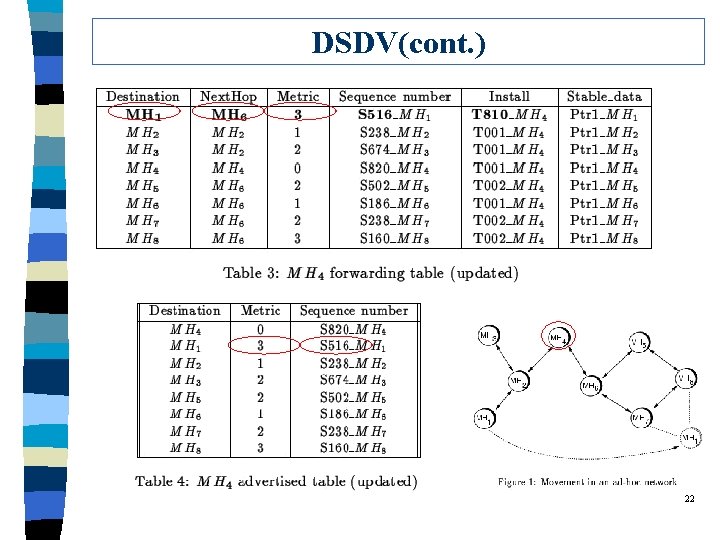
Protocol 1: DSDV (Destination Sequence Distance Vector) q q q “Highly Dynamic Destination-Sequence Distance-Vector Routing (DSDV) for Mobile Computers” Charles E. Perkins & Pravin Bhagwat Dated: 1994 Computer Communications Review, ‘ 94 pp. 234 -244 19

DSDV Outline q Each node keeps a routing table to all other nodes. l based on next-hop routing q Once its routing table changes, a node broadcasts its table to other nodes. 20

DSDV(cont. ) 21

DSDV(cont. ) 22

Protocol 2: CGSR (Clusterhead Gateway Switch Routing) q “Routing in Clustered Multihop, Mobile Wireless Networks with Fading Channel”, C. -C. Chiang, 1996, Proc. IEEE SICON ’ 97, pp. 197 -211. 23

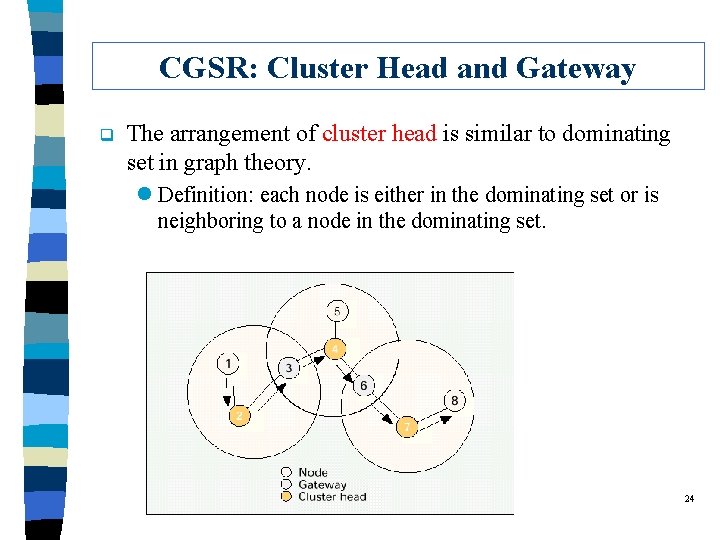
CGSR: Cluster Head and Gateway q The arrangement of cluster head is similar to dominating set in graph theory. l Definition: each node is either in the dominating set or is neighboring to a node in the dominating set. 24

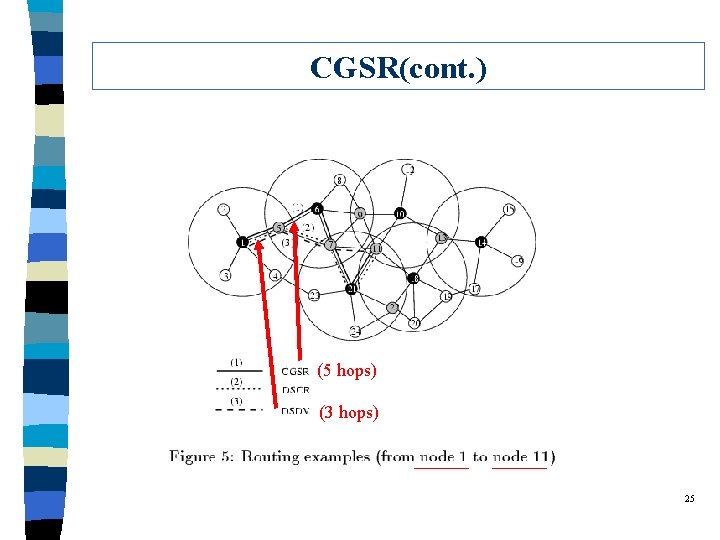
CGSR(cont. ) (5 hops) (3 hops) 25

CGSR (cont. ) q A routing table among cluster heads are maintained. l also based on the DSDV manner q Data forwarding steps: l from cluster head to cluster head Ø in a hierarchical manner l then from cluster head to cluster members l between two cluster heads, gateways are used to forward the packets q q Adv: less routing information to be kept Disadv: longer route 26

Source-Initiated On-Demand Routing Protocols q q q AODV DSR TORA ABR SSR ZRP MANET: 27

Protocol 1: AODV q AODV: Ad hoc On-demand Distance Vector routing protocol l On track to become an IETF Experimental RFC q References l C. E. Perkins, E. M. Belding-Royer, and S. R. Das, “Ad hoc On-Demand Distance Vector (AODV) Routing, ” IETF Internet Draft, draft-ietf-manet-aodv-13. txt, Feb. 17, 2003 (work in progress). l C. E. Perkins and E. M. Royer, “Ad hoc On-Demand Distance Vector Routing, ” Proceedings 2 nd IEEE Workshop on Mobile Computing Systems and Applications, February 1999, pp. 90 -100. 28

AODV Concepts (1) q Pure on-demand routing protocol l A node does not perform route discovery or maintenance until it needs a route to another node or it offers its services as an intermediate node l Nodes that are not on active paths do not maintain routing information and do not participate in routing table exchanges q q Uses a broadcast route discovery mechanism Uses hop-by-hop routing l Routes are based on dynamic table entries maintained at intermediate nodes l Comparison: Dynamic Source Routing (DSR) uses source routing 29

AODV Concepts (2) q Local HELLO messages are used to determine local connectivity l Can reduce response time to routing requests l Can trigger updates when necessary q Sequence numbers are assigned to routes and routing table entries l to supersede stale cached routing entries q Every node maintains two counters l Node sequence number l Broadcast ID 30

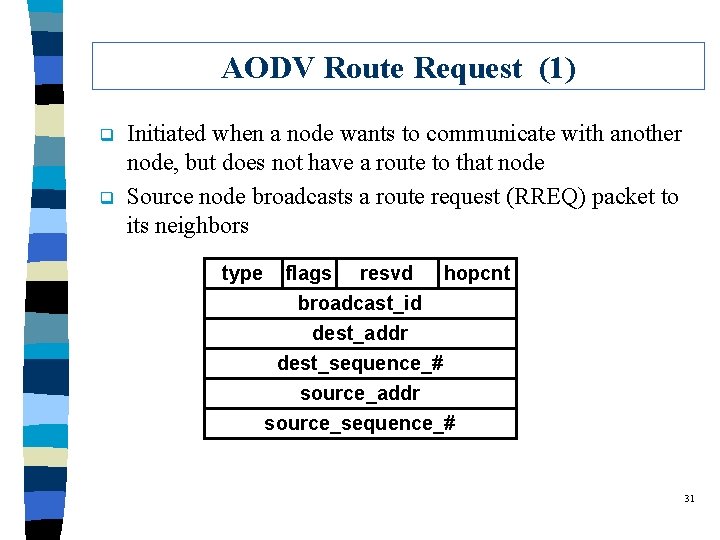
AODV Route Request (1) q q Initiated when a node wants to communicate with another node, but does not have a route to that node Source node broadcasts a route request (RREQ) packet to its neighbors type flags resvd hopcnt broadcast_id dest_addr dest_sequence_# source_addr source_sequence_# 31

AODV Route Request (2) q Sequence numbers l Source sequence indicates “freshness” of reverse route to the source l Destination sequence number indicates freshness of route to the destination q Every neighbor receives the RREQ and either … l Returns a route reply (RREP) packet, or l Forwards the RREQ to its neighbors q (source_addr, broadcast_id) uniquely identifies the RREQ l broadcast_id is incremented for every RREQ packet sent l Receivers can identify and discard duplicate RREQ packets 32

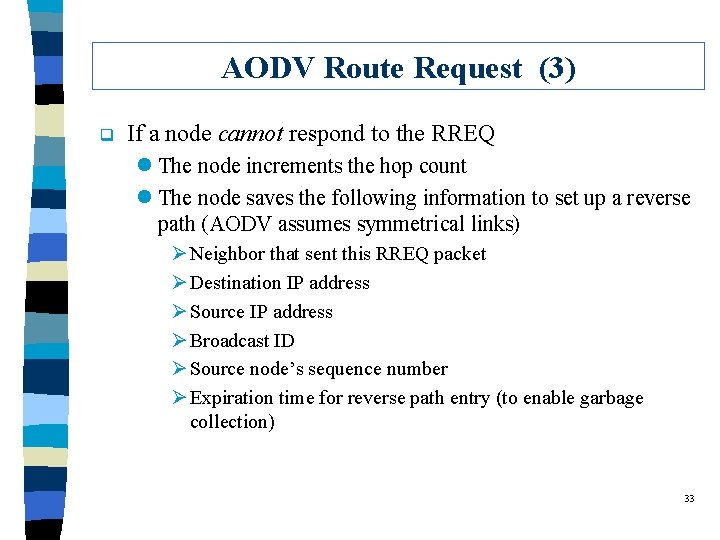
AODV Route Request (3) q If a node cannot respond to the RREQ l The node increments the hop count l The node saves the following information to set up a reverse path (AODV assumes symmetrical links) Ø Neighbor that sent this RREQ packet Ø Destination IP address Ø Source IP address Ø Broadcast ID Ø Source node’s sequence number Ø Expiration time for reverse path entry (to enable garbage collection) 33

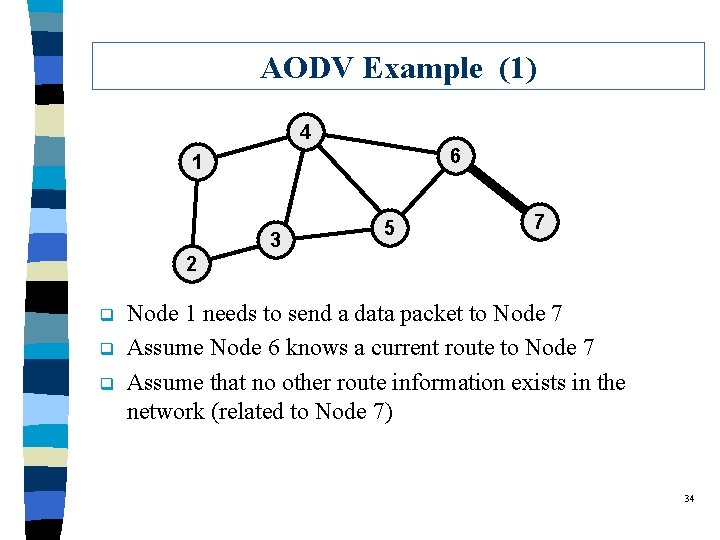
AODV Example (1) 4 6 1 3 5 7 2 q q q Node 1 needs to send a data packet to Node 7 Assume Node 6 knows a current route to Node 7 Assume that no other route information exists in the network (related to Node 7) 34

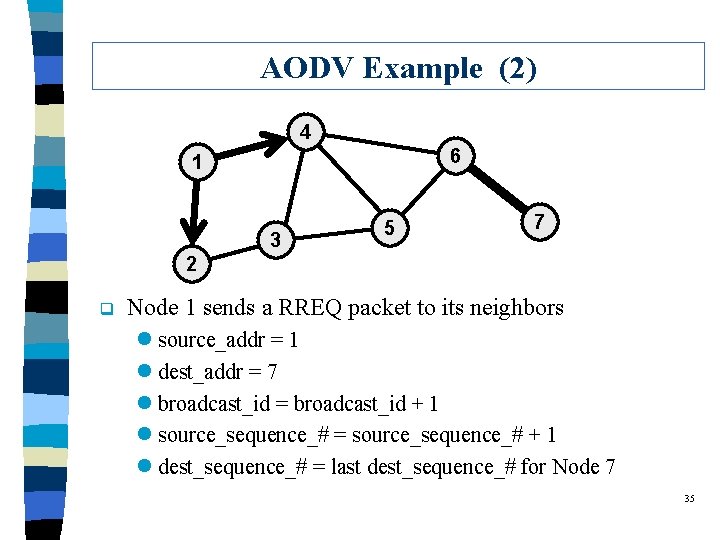
AODV Example (2) 4 6 1 3 5 7 2 q Node 1 sends a RREQ packet to its neighbors l source_addr = 1 l dest_addr = 7 l broadcast_id = broadcast_id + 1 l source_sequence_# = source_sequence_# + 1 l dest_sequence_# = last dest_sequence_# for Node 7 35

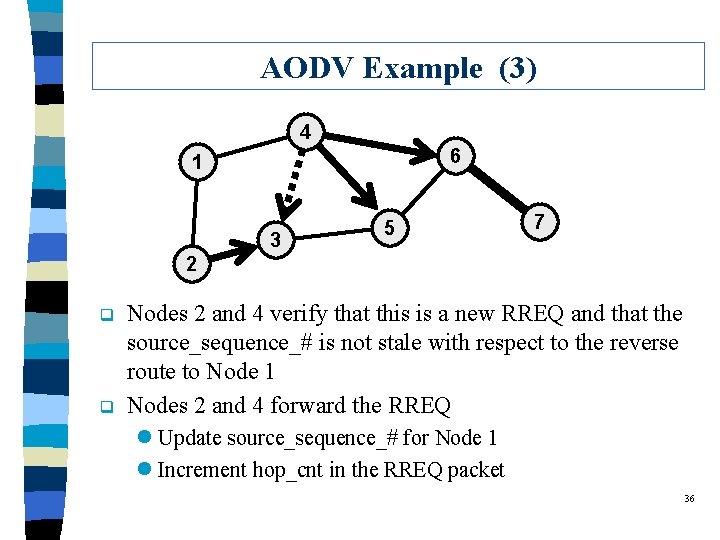
AODV Example (3) 4 6 1 3 5 7 2 q q Nodes 2 and 4 verify that this is a new RREQ and that the source_sequence_# is not stale with respect to the reverse route to Node 1 Nodes 2 and 4 forward the RREQ l Update source_sequence_# for Node 1 l Increment hop_cnt in the RREQ packet 36

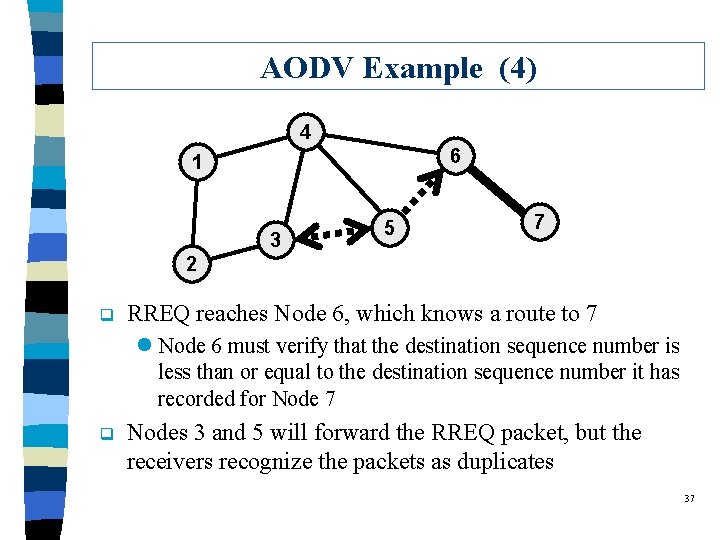
AODV Example (4) 4 6 1 3 5 7 2 q RREQ reaches Node 6, which knows a route to 7 l Node 6 must verify that the destination sequence number is less than or equal to the destination sequence number it has recorded for Node 7 q Nodes 3 and 5 will forward the RREQ packet, but the receivers recognize the packets as duplicates 37

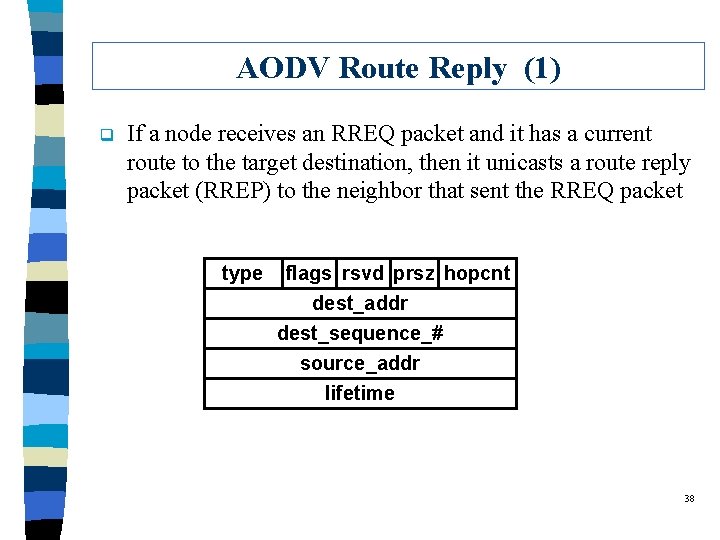
AODV Route Reply (1) q If a node receives an RREQ packet and it has a current route to the target destination, then it unicasts a route reply packet (RREP) to the neighbor that sent the RREQ packet type flags rsvd prsz hopcnt dest_addr dest_sequence_# source_addr lifetime 38

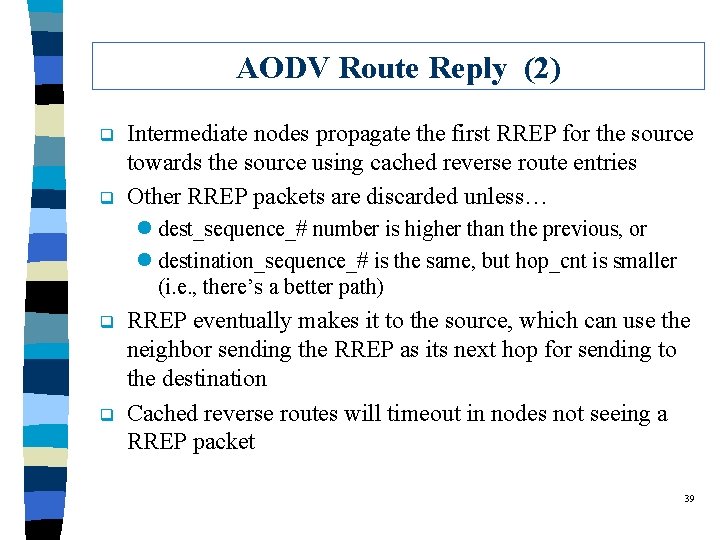
AODV Route Reply (2) q q Intermediate nodes propagate the first RREP for the source towards the source using cached reverse route entries Other RREP packets are discarded unless… l dest_sequence_# number is higher than the previous, or l destination_sequence_# is the same, but hop_cnt is smaller (i. e. , there’s a better path) q q RREP eventually makes it to the source, which can use the neighbor sending the RREP as its next hop for sending to the destination Cached reverse routes will timeout in nodes not seeing a RREP packet 39

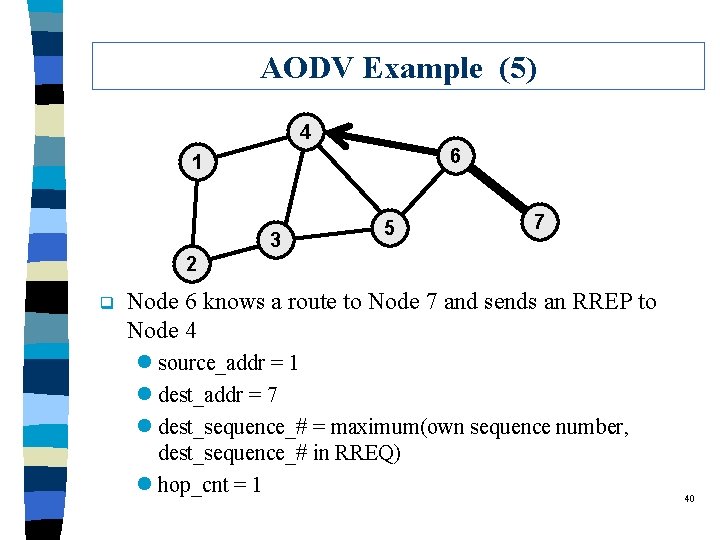
AODV Example (5) 4 6 1 3 5 7 2 q Node 6 knows a route to Node 7 and sends an RREP to Node 4 l source_addr = 1 l dest_addr = 7 l dest_sequence_# = maximum(own sequence number, dest_sequence_# in RREQ) l hop_cnt = 1 40

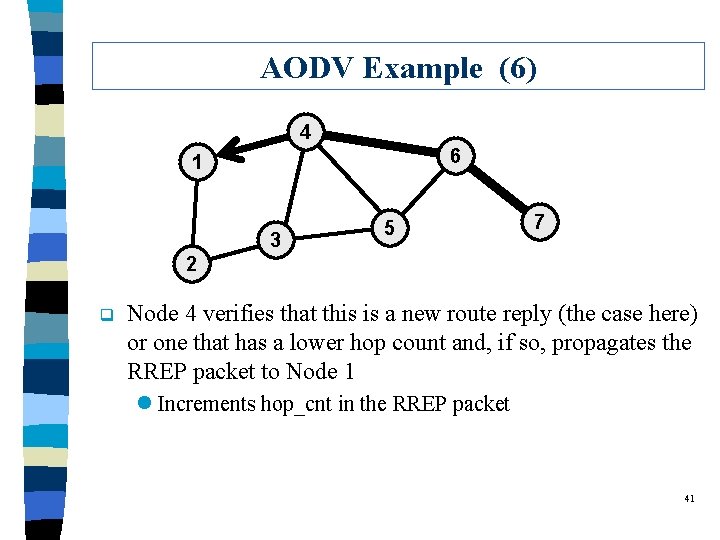
AODV Example (6) 4 6 1 3 5 7 2 q Node 4 verifies that this is a new route reply (the case here) or one that has a lower hop count and, if so, propagates the RREP packet to Node 1 l Increments hop_cnt in the RREP packet 41

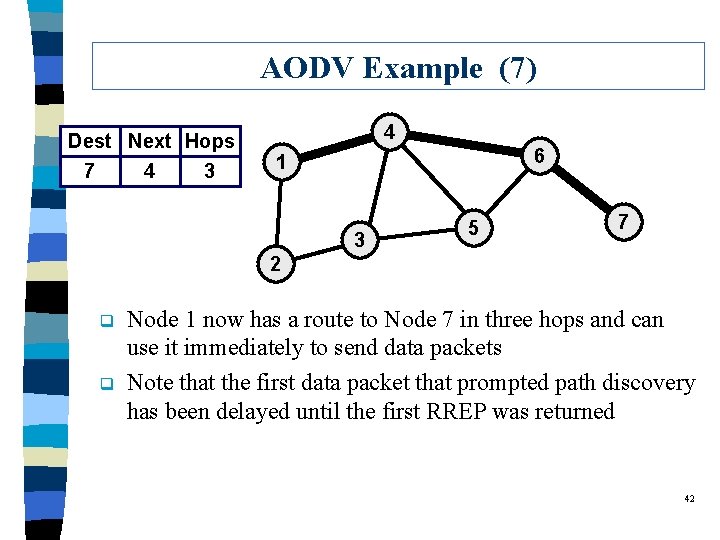
AODV Example (7) Dest Next Hops 7 4 3 4 6 1 3 5 7 2 q q Node 1 now has a route to Node 7 in three hops and can use it immediately to send data packets Note that the first data packet that prompted path discovery has been delayed until the first RREP was returned 42

AODV Route Maintenance q Route changes can be detected by… l Failure of periodic HELLO packets l Failure or disconnect indication from the link level l Failure of transmission of a packet to the next hop (can detect by listening for the retransmission if it is not the final destination) q q The upstream (toward the source) node detecting a failure propagates an route error (RERR) packet to the source node with a new destination sequence number and a hop count of infinity (unreachable) The source (or another node on the path) can rebuild a path by sending a RREQ packet 43

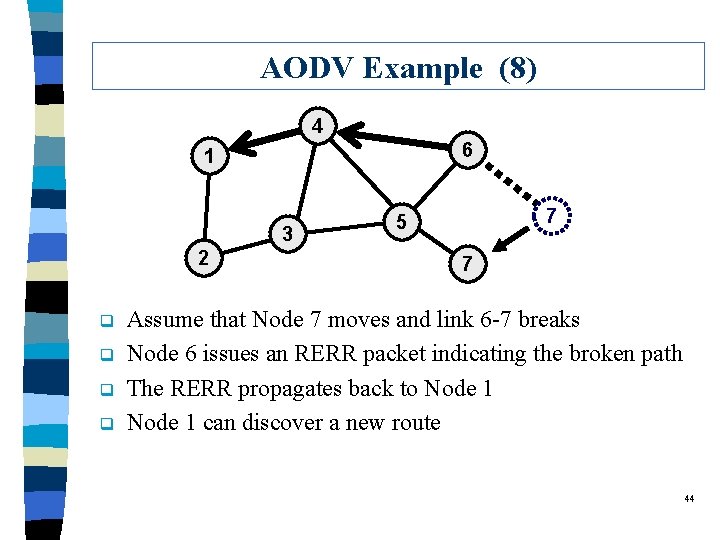
AODV Example (8) 4 6 1 3 2 q q 7 5 7 Assume that Node 7 moves and link 6 -7 breaks Node 6 issues an RERR packet indicating the broken path The RERR propagates back to Node 1 can discover a new route 44

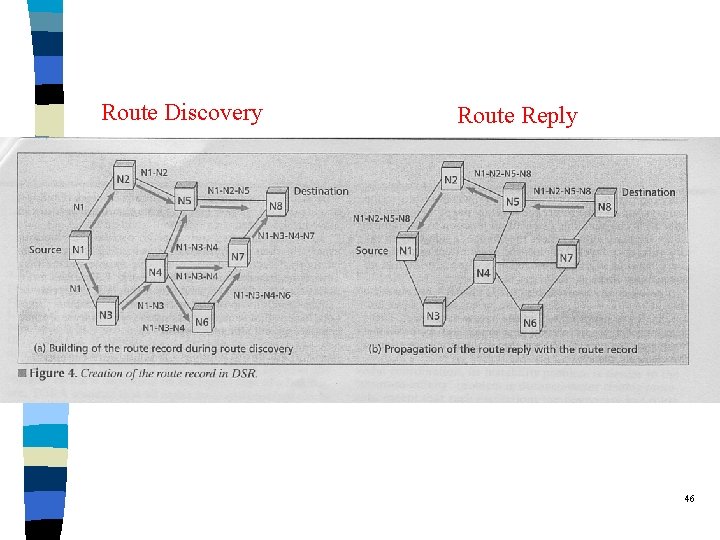
Protocol 2: DSR (Dynamic Source Routing) q q “Dynamic Source Routing in Ad-Hoc Wireless Networks”, D. B. Johnson and D. A. Maltz, Mobile Computing, 1996, pp. 153 -181. on-demand Each host maintains a route cache which contains all routes it has learnt. Source Routing: l routes are denoted with complete information (each hop is registered) q Two major parts: l route discovery l route maintenance 45

Route Discovery Route Reply 46

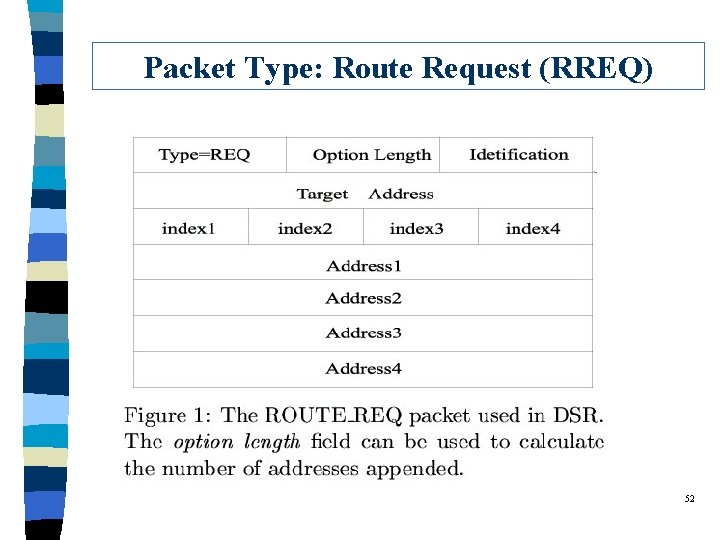
Route Discovery of DSR q When a host has a packet to send, it first consults its route cache. l If there is an unexpired route, then it will use it. l Otherwise, a route discovery will be performed. q Route Discovery: l There is a “route record” field in the packet. Ø The source node will add its address to the record. Ø On receipt of the packet, a host will add its address to the “route record” and rebroadcast the packet. l To limit the number of ROUTE_REQUEST packets: Ø Each node only rebroadcasts the packet at most once. Ø Each node will consult its route cache to see if a route is already known. 47

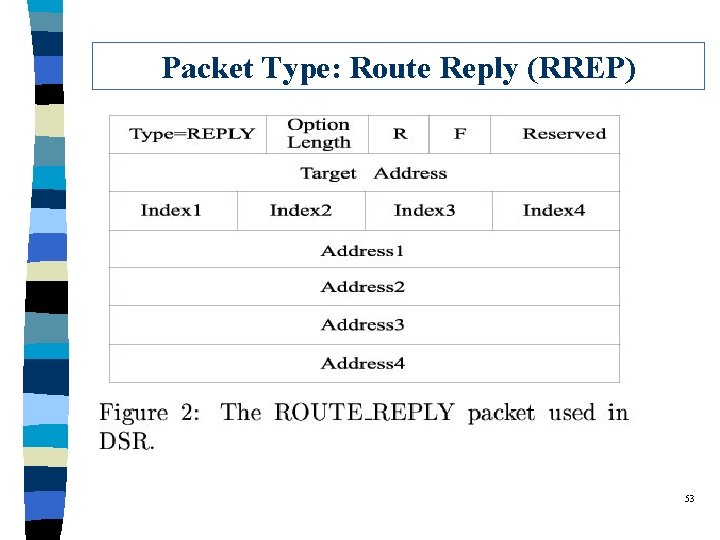
ROUTE_REPLY of DSR q A ROUTE_REPLY packet is generated when l the route request packet reaches the destination l an intermediate host has an unexpired route to the destination q The ROUTE_REPLY packet will contain a route generated in two manner: l from destination: Ø the route that was traversed by the ROUTE_REQUEST packet l from intermediate host: Ø the route that was traversed by the ROUTE_REQUEST packet concatenated with the route in the intermediate host’s route cache 48

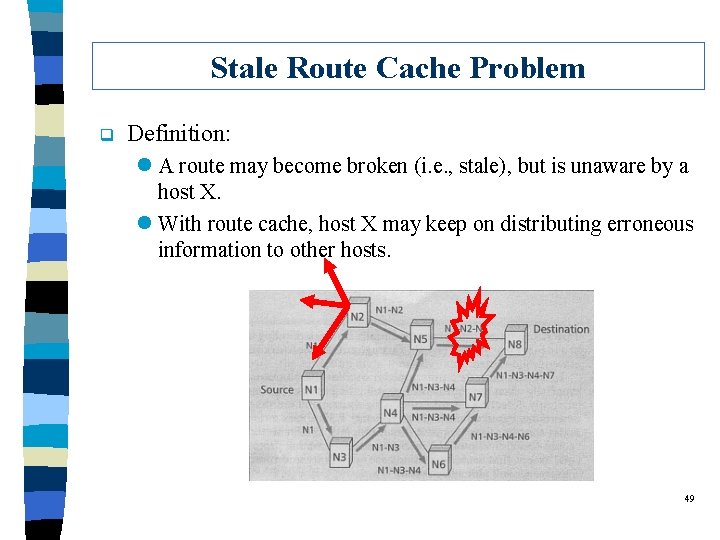
Stale Route Cache Problem q Definition: l A route may become broken (i. e. , stale), but is unaware by a host X. l With route cache, host X may keep on distributing erroneous information to other hosts. 49

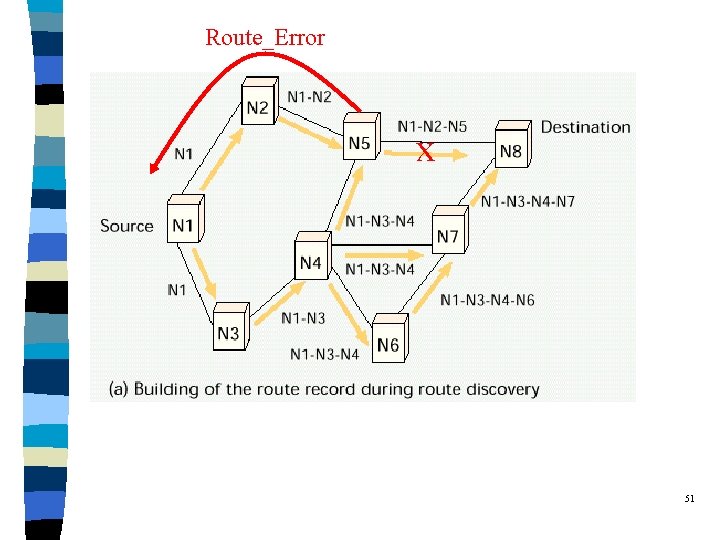
Route Maintenance of DSR q When the data link layer encounters a link breakage, a ROUTE_ERROR packet will be initiated. l The packet will traverse in the backward direction to the source. l The source will then initiate another ROUTE_REQUEST. l Example: (next page) q Maintenance of route cache: l All routes which contain the breakage hop have to be removed from the route cache. 50

Route_Error x 51

Packet Type: Route Request (RREQ) 52

Packet Type: Route Reply (RREP) 53

Packet Type: Data Packet 54

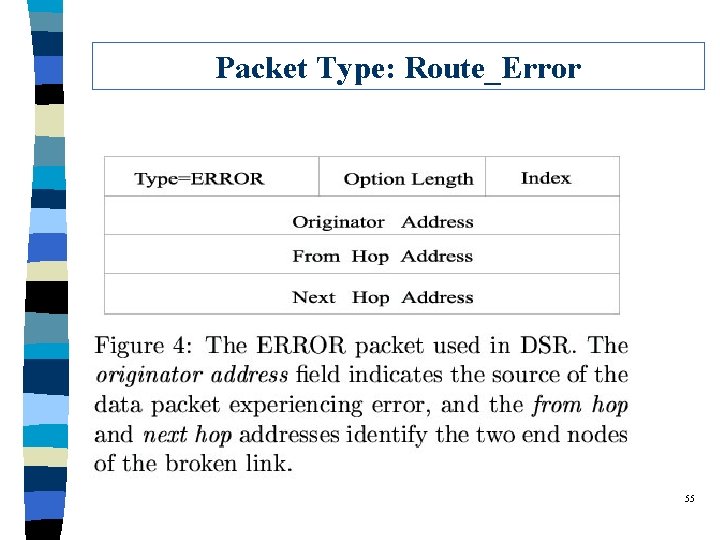
Packet Type: Route_Error 55

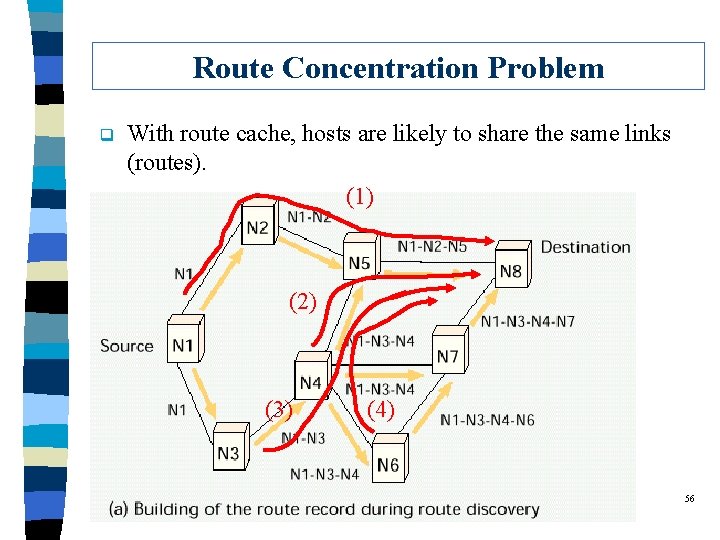
Route Concentration Problem q With route cache, hosts are likely to share the same links (routes). (1) (2) (3) (4) 56

Protocol 3: TORA (Temporally Ordered Routing Algorithm) q “A Highly Adaptive Distributed Routing Algorithm for Mobile Wireless Networks”, University of Maryland, V. D. Park and M. S. Corson, 1996, Proc. INFOCOM ’ 97. 57

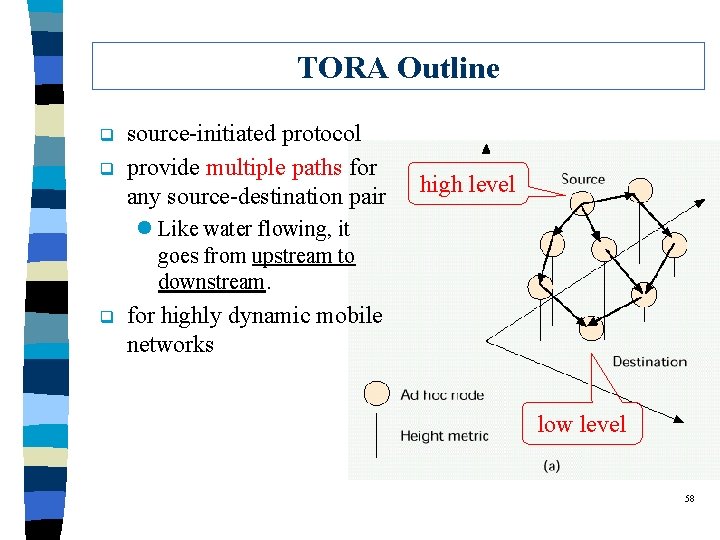
TORA Outline q q source-initiated protocol provide multiple paths for any source-destination pair high level l Like water flowing, it goes from upstream to downstream. q for highly dynamic mobile networks low level 58

Main Idea q q Regard the network as a directed graph. For each destination, a DAG (directed acyclic graph) will be maintained. l Note: There are n copies of DAG’s, each associated with one destination, where n is the number of hosts. l In the following discussion, we only discuss one DAG associated with a destination. q The DAG is accomplished by assigning each node i a height metric hi. l A link from i to j means hi > hj. 59

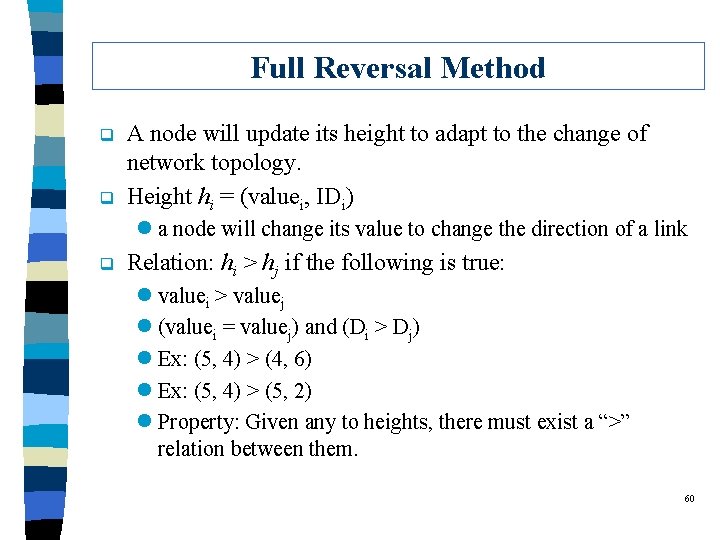
Full Reversal Method q q A node will update its height to adapt to the change of network topology. Height hi = (valuei, IDi) l a node will change its value to change the direction of a link q Relation: hi > hj if the following is true: l valuei > valuej l (valuei = valuej) and (Di > Dj) l Ex: (5, 4) > (4, 6) l Ex: (5, 4) > (5, 2) l Property: Given any to heights, there must exist a “>” relation between them. 60

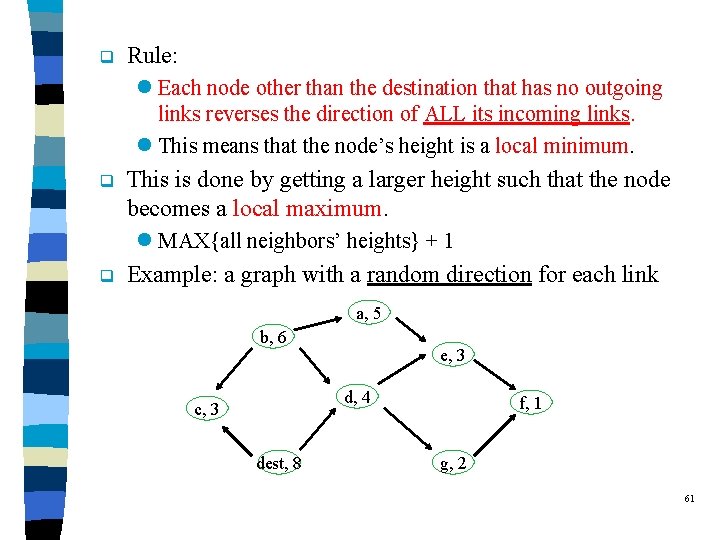
q Rule: l Each node other than the destination that has no outgoing links reverses the direction of ALL its incoming links. l This means that the node’s height is a local minimum. q This is done by getting a larger height such that the node becomes a local maximum. l MAX{all neighbors’ heights} + 1 q Example: a graph with a random direction for each link a, 5 b, 6 e, 3 d, 4 c, 3 dest, 8 f, 1 g, 2 61

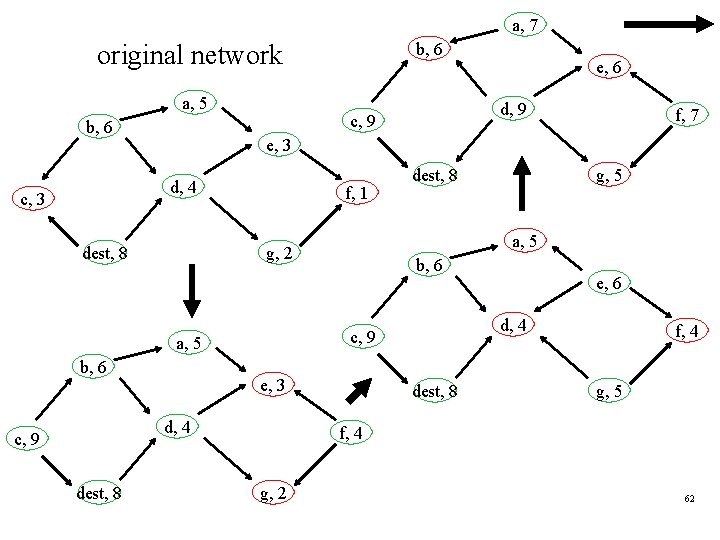
a, 7 b, 6 original network a, 5 b, 6 f, 1 b, 6 dest, 8 b, 6 e, 3 e, 6 d, 4 c, 9 d, 4 g, 5 a, 5 g, 2 a, 5 dest, 8 f, 7 e, 3 dest, 8 c, 9 d, 9 c, 9 d, 4 c, 3 e, 6 dest, 8 f, 4 g, 5 f, 4 g, 2 62

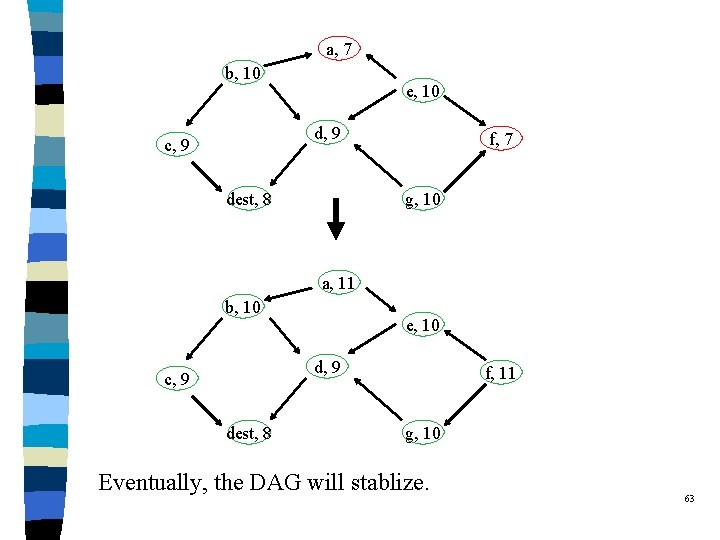
a, 7 b, 10 e, 10 d, 9 c, 9 dest, 8 f, 7 g, 10 a, 11 b, 10 e, 10 d, 9 c, 9 dest, 8 f, 11 g, 10 Eventually, the DAG will stablize. 63

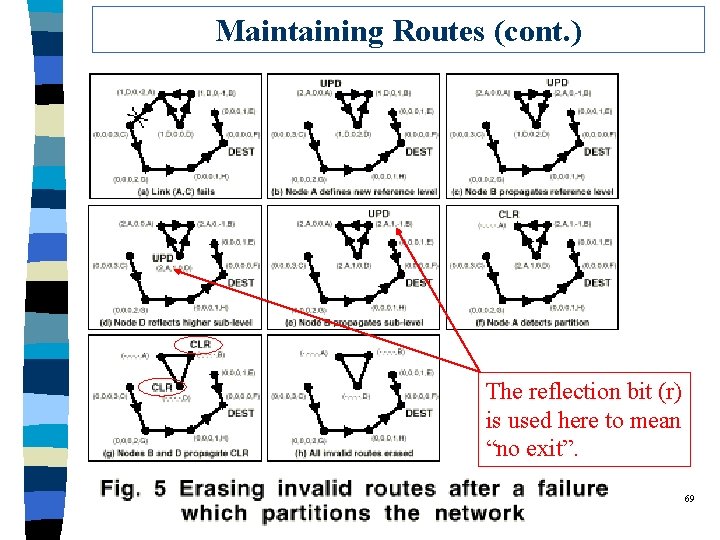
TORA Details q Three basic functions: l route creation l route maintenance l route erasure q Three control packets: l query (QRY) l update (UPD) l clear (CLR) 64

Data Structure q Each node keep a 5 -tuple (τ, oid, r, δ, i) l τ: time of the link failure. l oid (originator ID): Ø Unique identifier of the node that defined a new reference level Ø Most likely, the node who detects link breakage. l r: reflection indicator bit. Ø initially set to 0. l δ: propagation ordering parameter (i. e. , height) l i: node ID 65

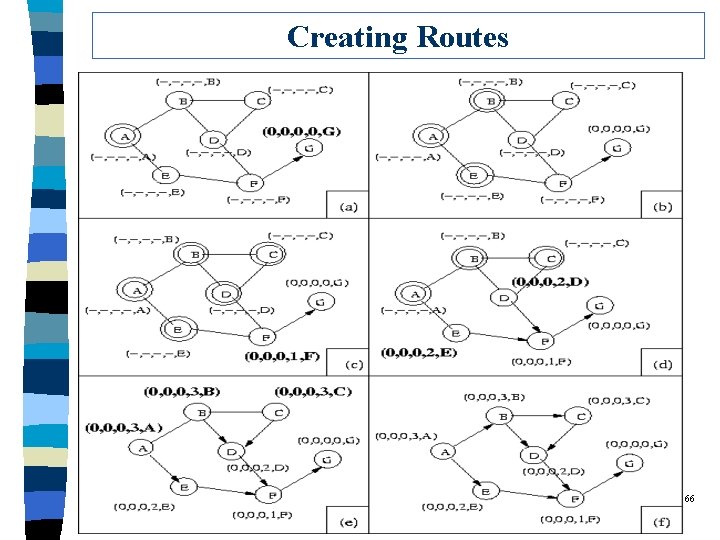
Creating Routes 66

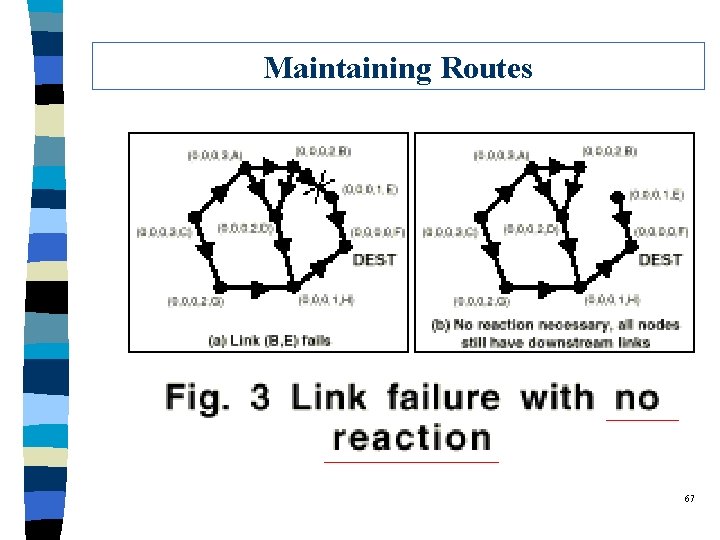
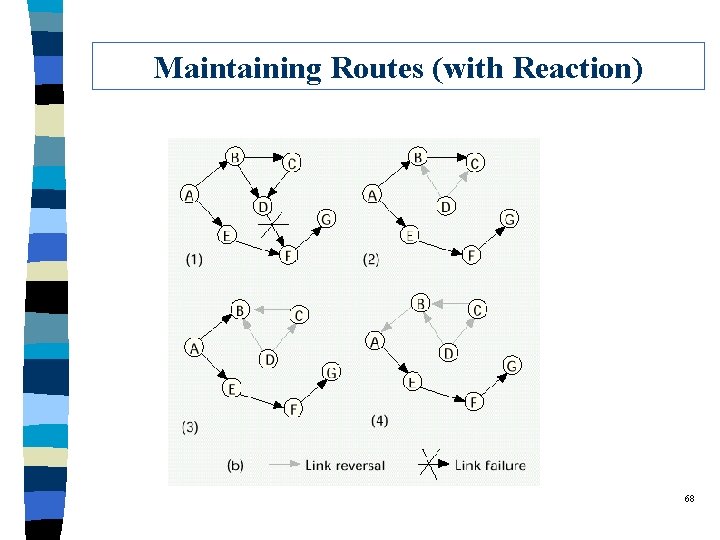
Maintaining Routes 67

Maintaining Routes (with Reaction) 68

Maintaining Routes (cont. ) The reflection bit (r) is used here to mean “no exit”. 69

Protocol 4: ABR (Associativity-Based Routing) q ABR considers the stability of a link. l The metric is called degree of association stability. q Basic Idea: l Each node periodically generates a beacon to signify its existence. l On receipt of the beacon, a neighboring node will increase the “tick” of the sender by 1. Ø A higher degree of association stability (i. e. , ticks) may indicate a low mobility of that node. Ø A low degree of association stability may indicate a high mobility of that node. l When a link becomes broken, the node will set the tick of the other node to 0. 70

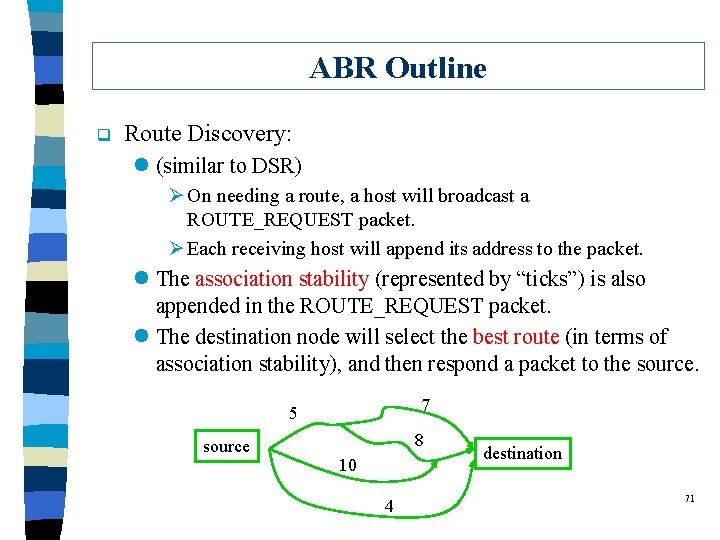
ABR Outline q Route Discovery: l (similar to DSR) Ø On needing a route, a host will broadcast a ROUTE_REQUEST packet. Ø Each receiving host will append its address to the packet. l The association stability (represented by “ticks”) is also appended in the ROUTE_REQUEST packet. l The destination node will select the best route (in terms of association stability), and then respond a packet to the source. 7 5 source 8 10 4 destination 71

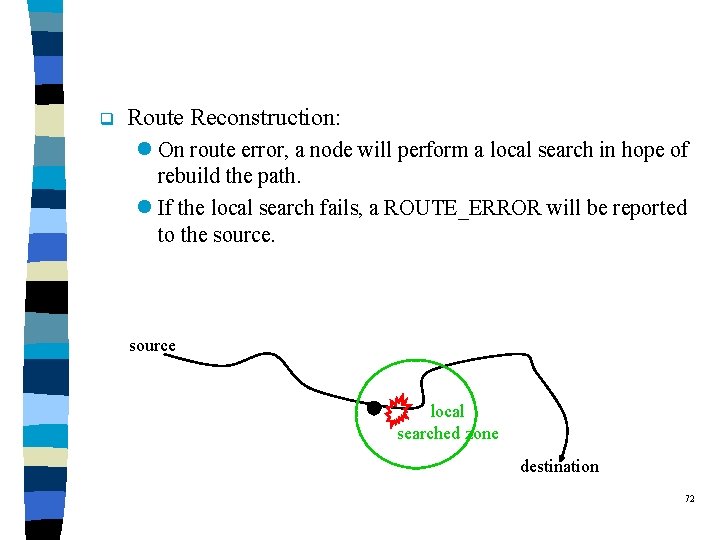
q Route Reconstruction: l On route error, a node will perform a local search in hope of rebuild the path. l If the local search fails, a ROUTE_ERROR will be reported to the source local searched zone destination 72

Protocol 5: SSA (Signal Stability-Based Adaptive Routing) q q q “Signal Stability-Based Adaptive Routing (SSA) for Ad Hoc Wireless Networks” University of Maryland R. Dube, C. D. Rais, K. -Y. Wang & S. K. Tripathi IEEE Personal Communications, ‘ 97 pp. 36 -45 73

Basic Idea of SSA q Observation: l The ABR only considers the connectivity to nodes. q Two more metrics: l signal stability: Ø the strength of a signal Ø provided by link layer l location stability Ø how fast a host moves Ø could be measure by: ü the change of signal strength over a period of time ü location devices (such as GPS) 74

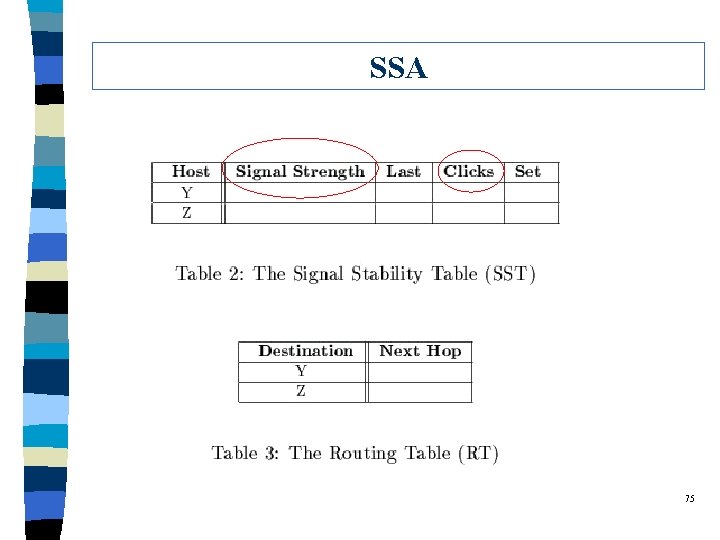
SSA 75

SSA(cont. ) 76

Protocol 6: ZRP (Zone Routing Protocol) q q The Zone Routing Protocol (ZRP) for Ad Hoc Networks Cornell University Z. J. Haas and M. R. Pearlman draft-ietf-manet-zone-zrp-01. txt, 1998 77

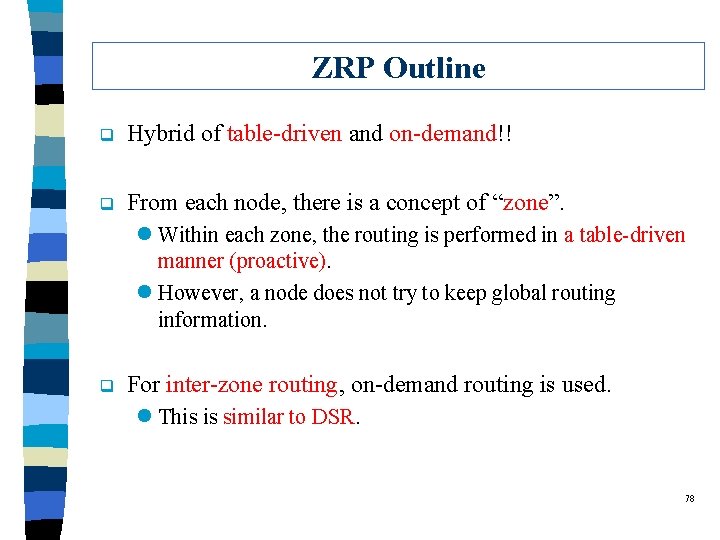
ZRP Outline q Hybrid of table-driven and on-demand!! q From each node, there is a concept of “zone”. l Within each zone, the routing is performed in a table-driven manner (proactive). l However, a node does not try to keep global routing information. q For inter-zone routing, on-demand routing is used. l This is similar to DSR. 78

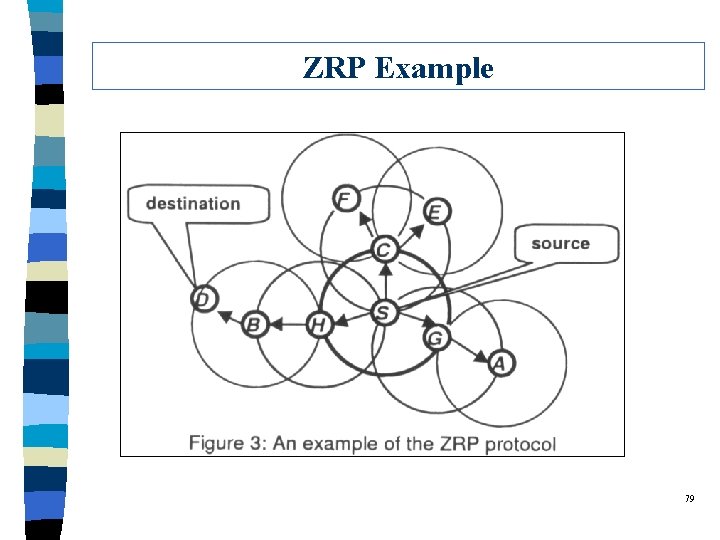
ZRP Example 79

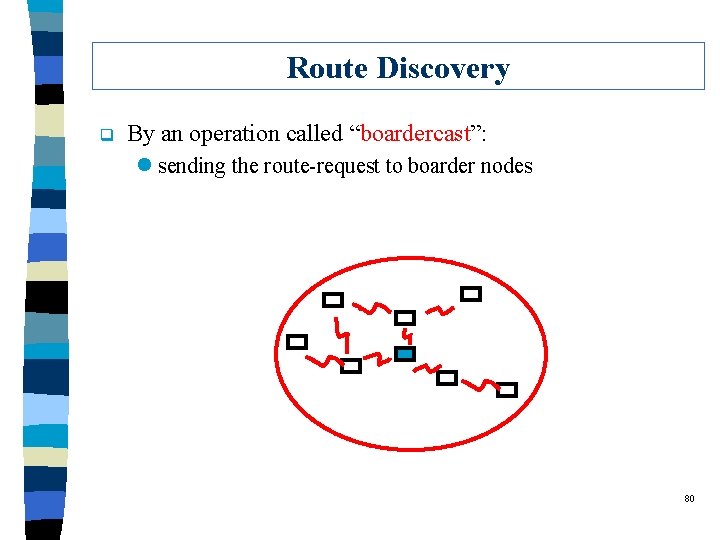
Route Discovery q By an operation called “boardercast”: l sending the route-request to boarder nodes 80

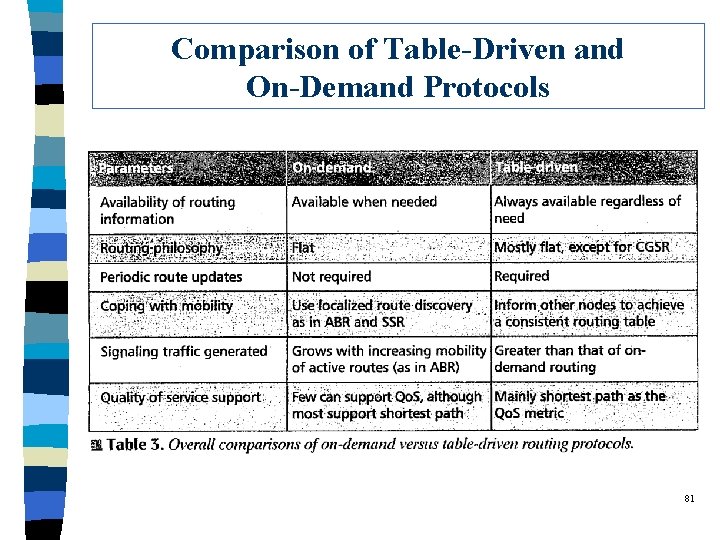
Comparison of Table-Driven and On-Demand Protocols 81

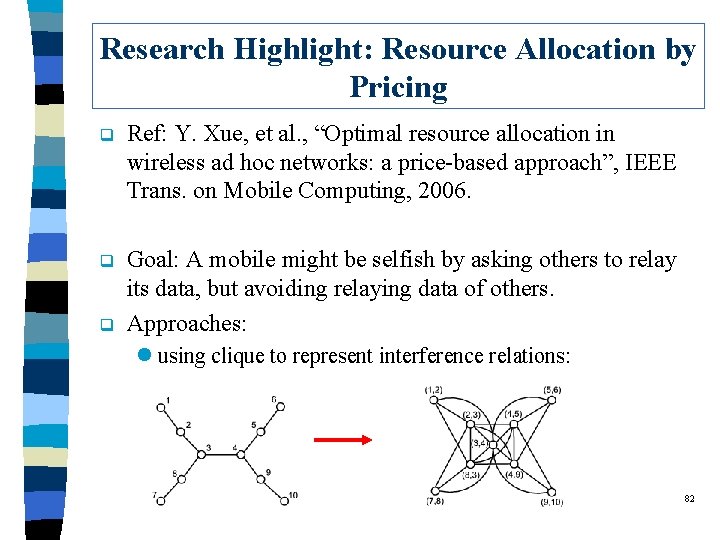
Research Highlight: Resource Allocation by Pricing q Ref: Y. Xue, et al. , “Optimal resource allocation in wireless ad hoc networks: a price-based approach”, IEEE Trans. on Mobile Computing, 2006. q Goal: A mobile might be selfish by asking others to relay its data, but avoiding relaying data of others. Approaches: q l using clique to represent interference relations: 82

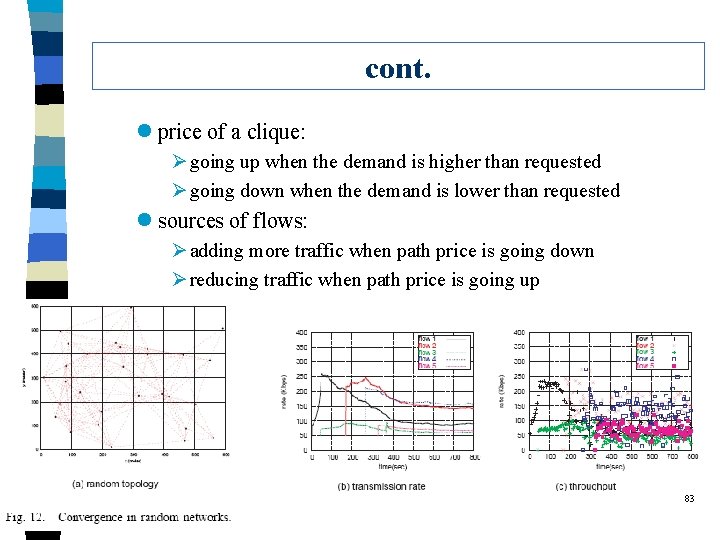
cont. l price of a clique: Ø going up when the demand is higher than requested Ø going down when the demand is lower than requested l sources of flows: Ø adding more traffic when path price is going down Ø reducing traffic when path price is going up 83