A PeertoPeer Approach to Resource Discovery in MultiAgent





![Results, contributions Related work [Bauer&Wang 92] show that DFS of the cache network, performs Results, contributions Related work [Bauer&Wang 92] show that DFS of the cache network, performs](https://slidetodoc.com/presentation_image_h/1afb72153cdf91bc7b2cc911c6742921/image-9.jpg)





- Slides: 44

A Peer-to-Peer Approach to Resource Discovery in Multi-Agent Systems Vassilios V. Dimakopoulos and Evaggelia Pitoura Distributed Data Management Lab Dept. of Computer Science, Univ. of Ioannina, Greece http: //softsys. cs. uoi. gr Dimakopoulos & Pitoura University of Ioannina

Multi-agent systems (MAS) l l 2 Cooperating agents: Each agent offers some resources (computation, data, etc) To fulfill its goals, an agent requires resources provided by other agents Closed MAS: each agent knows all others and what they offer vs Open MAS CIA 03 Dimakopoulos & Pitoura - University of Ioannina

Open MAS l l 3 How does an agent get information about other agents/resources? Common approach: directory-based (e. g. middle agent) Disadvantage: many agents and resources make the directory a performance/ reliability bottleneck Proposal: consider a p 2 p approach CIA 03 Dimakopoulos & Pitoura - University of Ioannina

P 2 P + agents In P 2 P, Peers (agents) offer resources Similar Problem: How to locate the peer(s) that offer a particular resource § Structured: based on the name or content of the resource place it at the appropriate node (Chord, CAN etc) vs § Unstructured: no assumption about the location of resources (Napster, Gnutella) We apply fully decentralized unstructured p 2 p approaches 4 CIA 03 Dimakopoulos & Pitoura - University of Ioannina

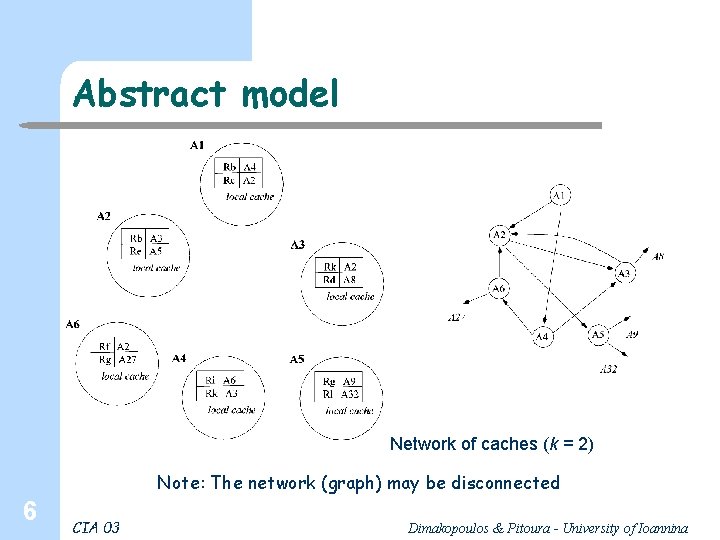
Overview l Each agent v has a cache with k entries, containing information for k resources i. e. for each of the k resources, the cache holds the contact information for an agent that provides it l l 5 If an agent v has contact information for agent u then v knows u. Network of caches : if v knows u there is a link from v to u CIA 03 Dimakopoulos & Pitoura - University of Ioannina

Abstract model Network of caches (k = 2) Note: The network (graph) may be disconnected 6 CIA 03 Dimakopoulos & Pitoura - University of Ioannina

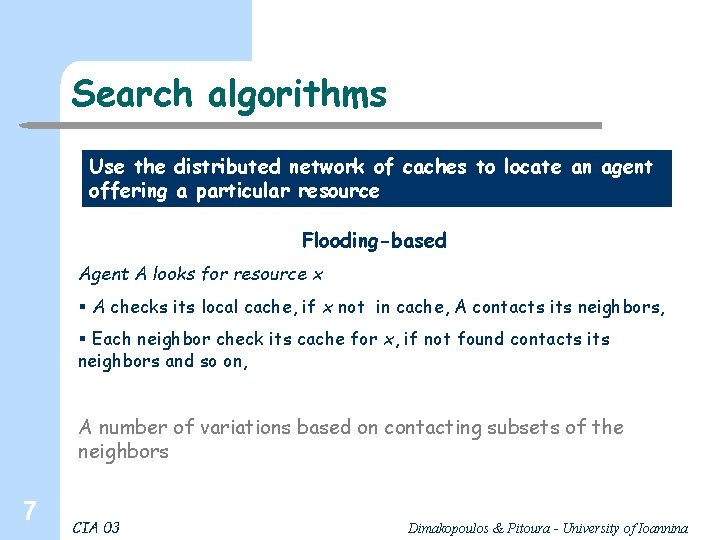
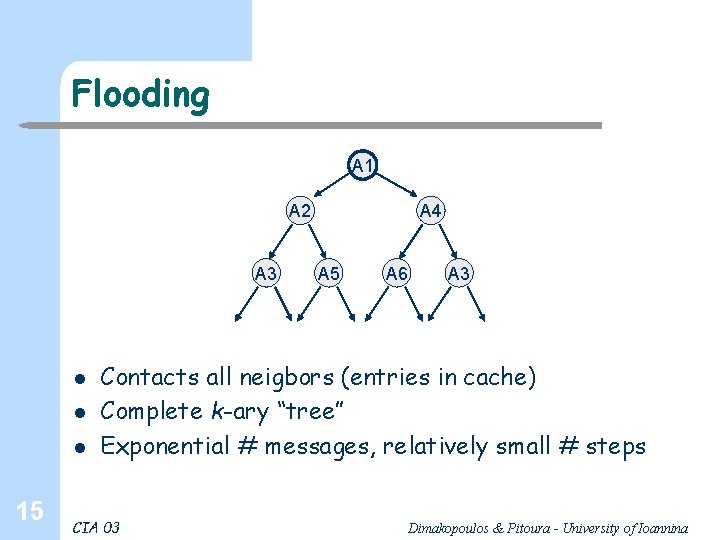
Search algorithms Use the distributed network of caches to locate an agent offering a particular resource Flooding-based Agent A looks for resource x § A checks its local cache, if x not in cache, A contacts its neighbors, § Each neighbor check its cache for x, if not found contacts its neighbors and so on, A number of variations based on contacting subsets of the neighbors 7 CIA 03 Dimakopoulos & Pitoura - University of Ioannina

Results, contributions Use the distributed network of caches to locate an agent offering a particular resource Algorithms for searching § Flooding (as in e. g. , Gnutella), §Teeming (randomized flooding), § Random paths Performance Analysis Analytical model validated by simulation Updates § Flooding-based propagation, § Inverted cache 8 CIA 03 Dimakopoulos & Pitoura - University of Ioannina
![Results contributions Related work BauerWang 92 show that DFS of the cache network performs Results, contributions Related work [Bauer&Wang 92] show that DFS of the cache network, performs](https://slidetodoc.com/presentation_image_h/1afb72153cdf91bc7b2cc911c6742921/image-9.jpg)
Results, contributions Related work [Bauer&Wang 92] show that DFS of the cache network, performs better than flooding for particular topologies [Shehory 00] Lattice-like cache network (each agent knows about exactly four other agents 9 CIA 03 Dimakopoulos & Pitoura - University of Ioannina

Talk outline § Brief presentation of the analytical model § Performance results related to the search procedures § Updates § Conclusions and Future Work 10 CIA 03 Dimakopoulos & Pitoura - University of Ioannina

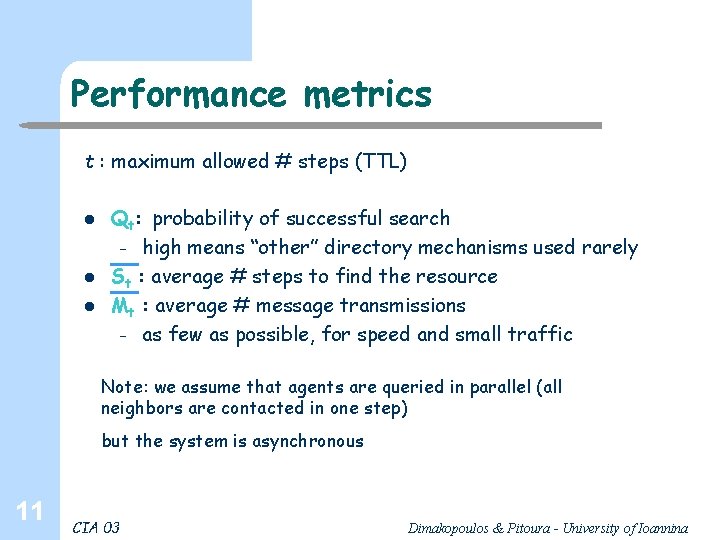
Performance metrics t : maximum allowed # steps (TTL) l l l Qt: probability of successful search – high means “other” directory mechanisms used rarely St : average # steps to find the resource Mt : average # message transmissions – as few as possible, for speed and small traffic Note: we assume that agents are queried in parallel (all neighbors are contacted in one step) but the system is asynchronous 11 CIA 03 Dimakopoulos & Pitoura - University of Ioannina

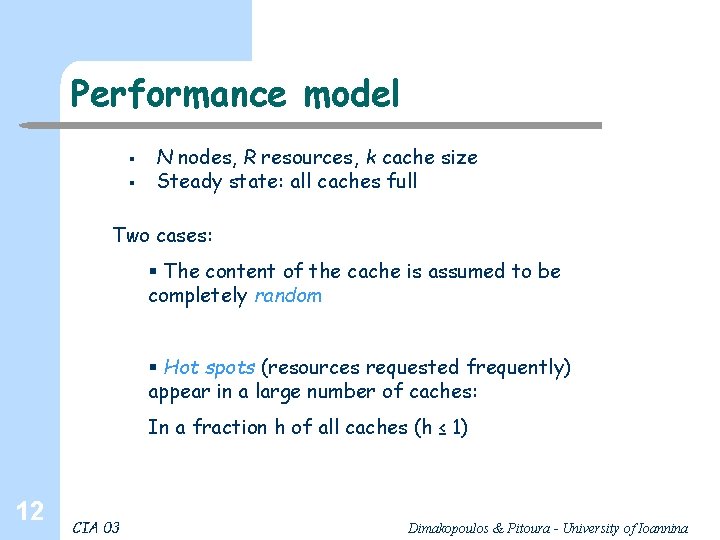
Performance model § § N nodes, R resources, k cache size Steady state: all caches full Two cases: § The content of the cache is assumed to be completely random § Hot spots (resources requested frequently) appear in a large number of caches: In a fraction h of all caches (h ≤ 1) 12 CIA 03 Dimakopoulos & Pitoura - University of Ioannina

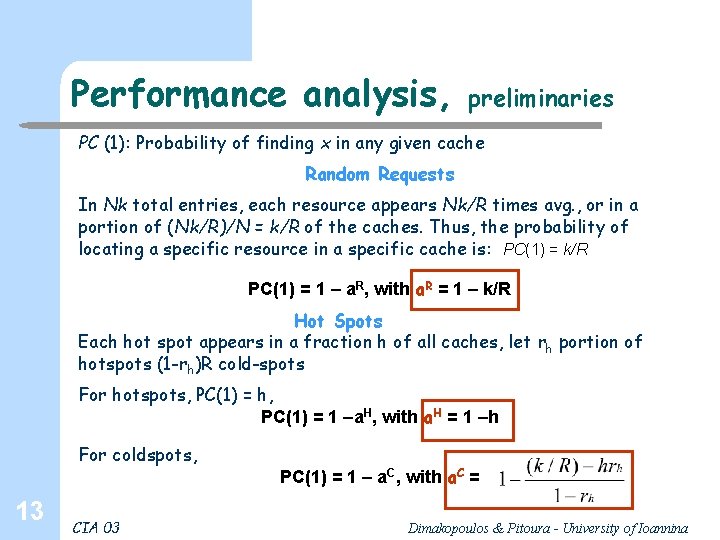
Performance analysis, preliminaries PC (1): Probability of finding x in any given cache Random Requests In Nk total entries, each resource appears Nk/R times avg. , or in a portion of (Nk/R)/N = k/R of the caches. Thus, the probability of locating a specific resource in a specific cache is: PC(1) = k/R PC(1) = 1 – a. R, with a. R = 1 – k/R Hot Spots Each hot spot appears in a fraction h of all caches, let rh portion of hotspots (1 -rh)R cold-spots For hotspots, PC(1) = h, PC(1) = 1 –a. H, with a. H = 1 –h For coldspots, 13 CIA 03 PC(1) = 1 – a. C, with a. C = Dimakopoulos & Pitoura - University of Ioannina

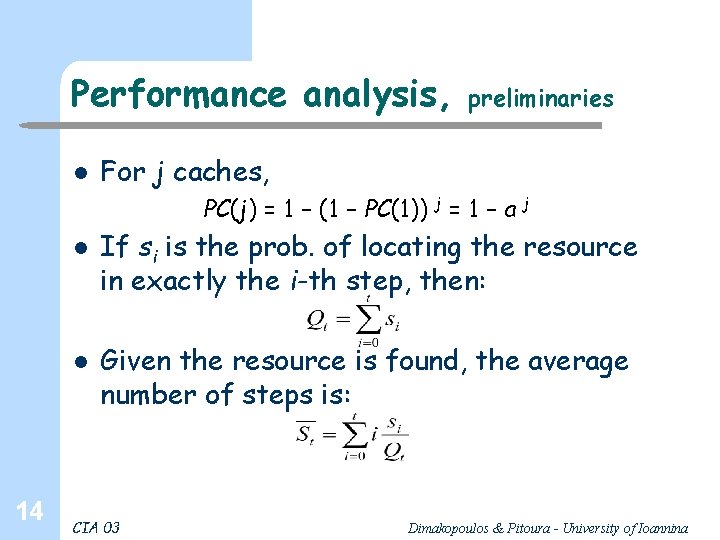
Performance analysis, l preliminaries For j caches, PC(j) = 1 – (1 – PC(1)) j = 1 – a j l l 14 If si is the prob. of locating the resource in exactly the i-th step, then: Given the resource is found, the average number of steps is: CIA 03 Dimakopoulos & Pitoura - University of Ioannina

Flooding A 1 A 2 A 3 l l l 15 A 4 A 5 A 6 A 3 Contacts all neigbors (entries in cache) Complete k-ary “tree” Exponential # messages, relatively small # steps CIA 03 Dimakopoulos & Pitoura - University of Ioannina

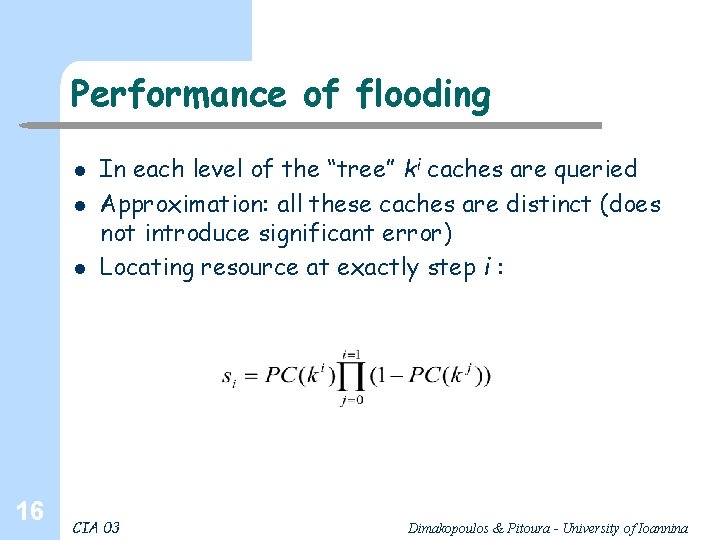
Performance of flooding l l l 16 In each level of the “tree” ki caches are queried Approximation: all these caches are distinct (does not introduce significant error) Locating resource at exactly step i : CIA 03 Dimakopoulos & Pitoura - University of Ioannina

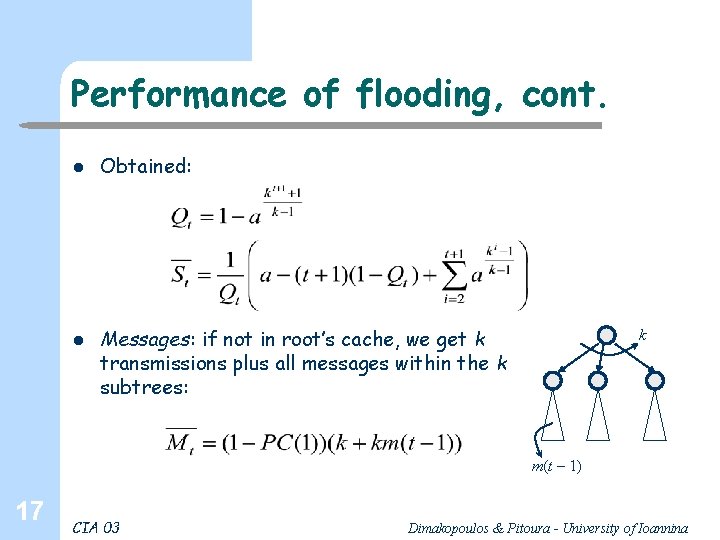
Performance of flooding, cont. l l Obtained: Messages: if not in root’s cache, we get k transmissions plus all messages within the k subtrees: k m(t – 1) 17 CIA 03 Dimakopoulos & Pitoura - University of Ioannina

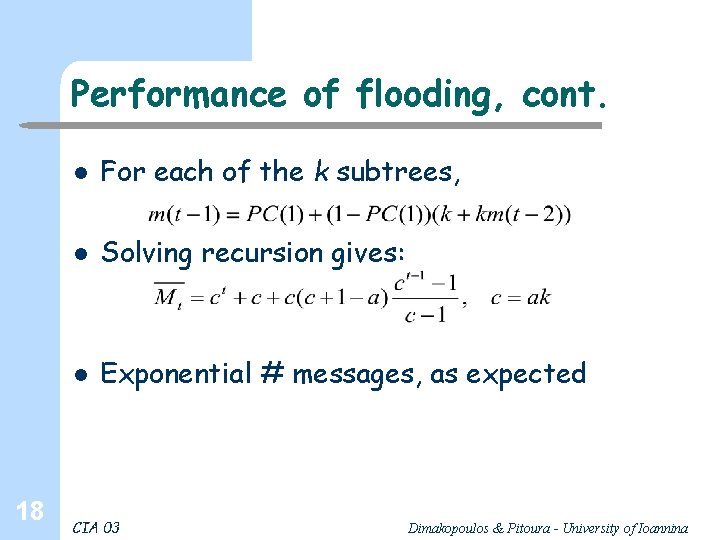
Performance of flooding, cont. 18 l For each of the k subtrees, l Solving recursion gives: l Exponential # messages, as expected CIA 03 Dimakopoulos & Pitoura - University of Ioannina

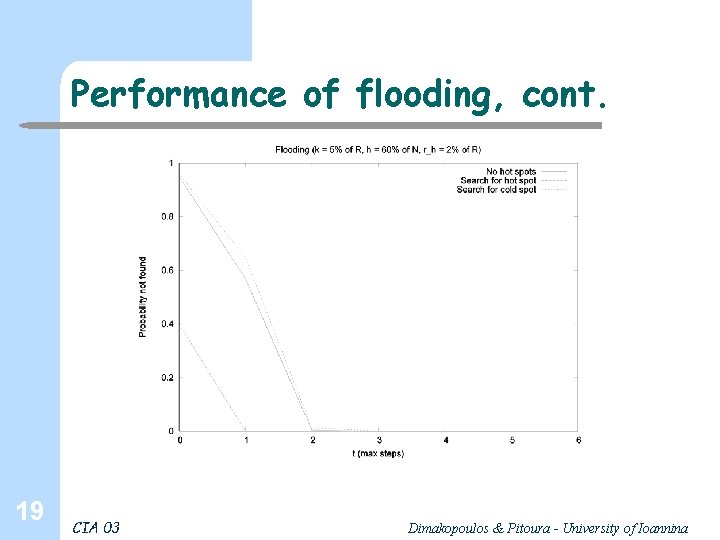
Performance of flooding, cont. 19 CIA 03 Dimakopoulos & Pitoura - University of Ioannina

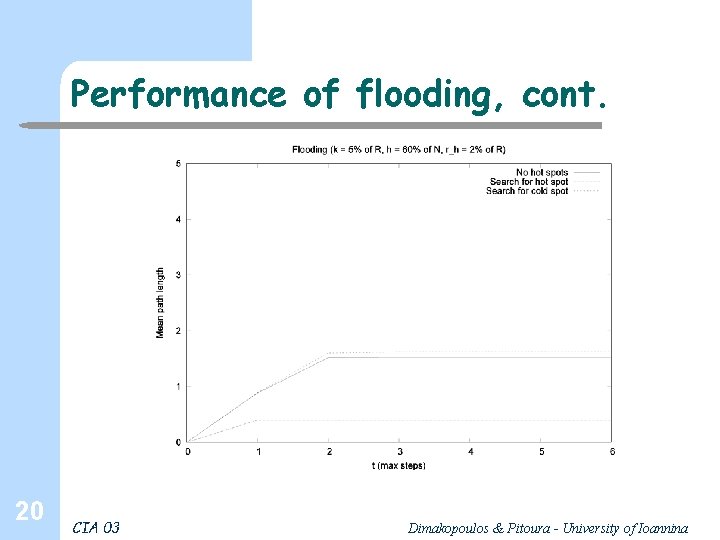
Performance of flooding, cont. 20 CIA 03 Dimakopoulos & Pitoura - University of Ioannina

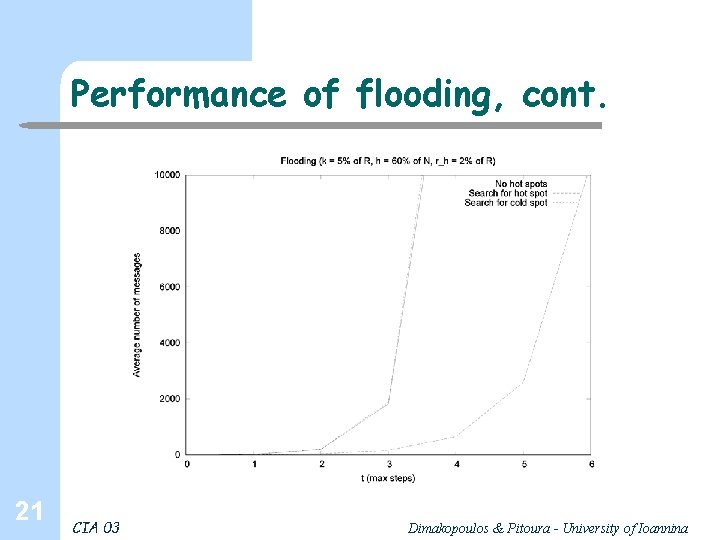
Performance of flooding, cont. 21 CIA 03 Dimakopoulos & Pitoura - University of Ioannina

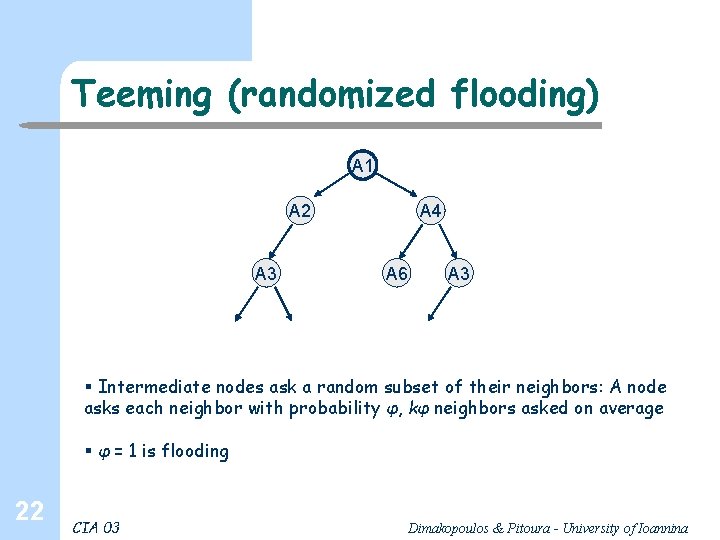
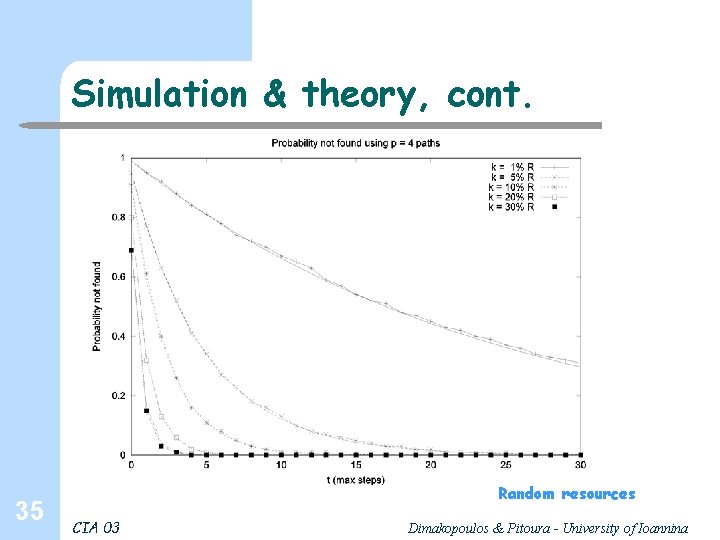
Teeming (randomized flooding) A 1 A 2 A 3 A 4 A 6 A 3 § Intermediate nodes ask a random subset of their neighbors: A node asks each neighbor with probability φ, kφ neighbors asked on average § φ = 1 is flooding 22 CIA 03 Dimakopoulos & Pitoura - University of Ioannina

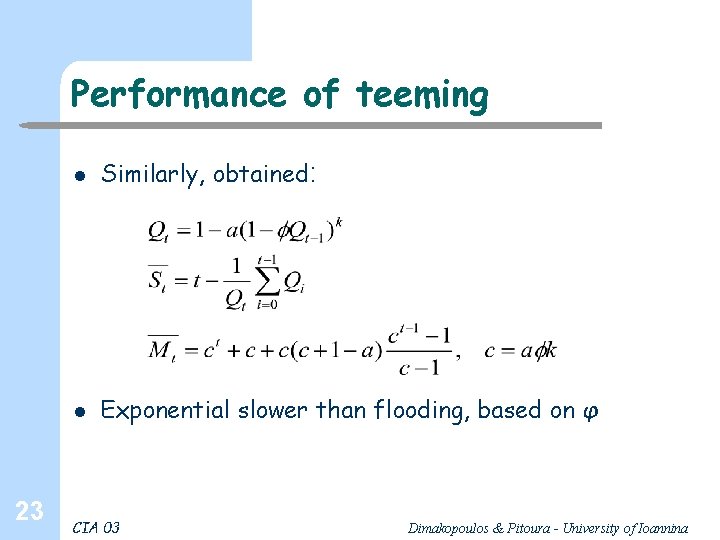
Performance of teeming 23 l Similarly, obtained: l Exponential slower than flooding, based on φ CIA 03 Dimakopoulos & Pitoura - University of Ioannina

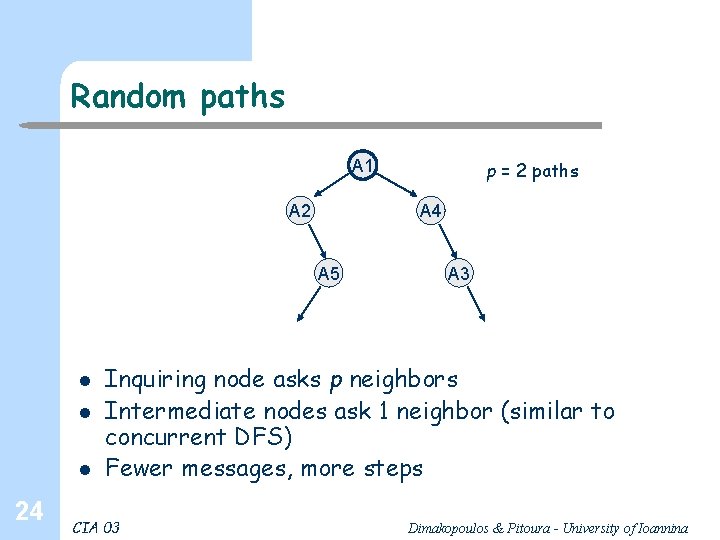
Random paths A 1 A 2 A 4 A 5 l l l 24 p = 2 paths A 3 Inquiring node asks p neighbors Intermediate nodes ask 1 neighbor (similar to concurrent DFS) Fewer messages, more steps CIA 03 Dimakopoulos & Pitoura - University of Ioannina

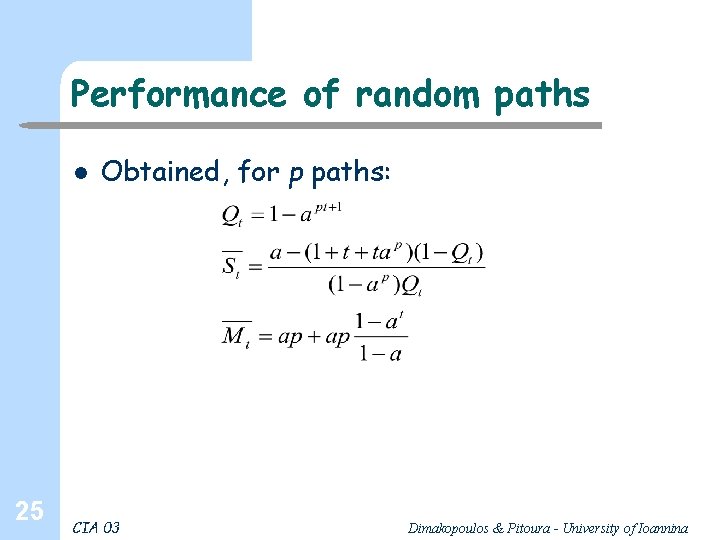
Performance of random paths l 25 Obtained, for p paths: CIA 03 Dimakopoulos & Pitoura - University of Ioannina

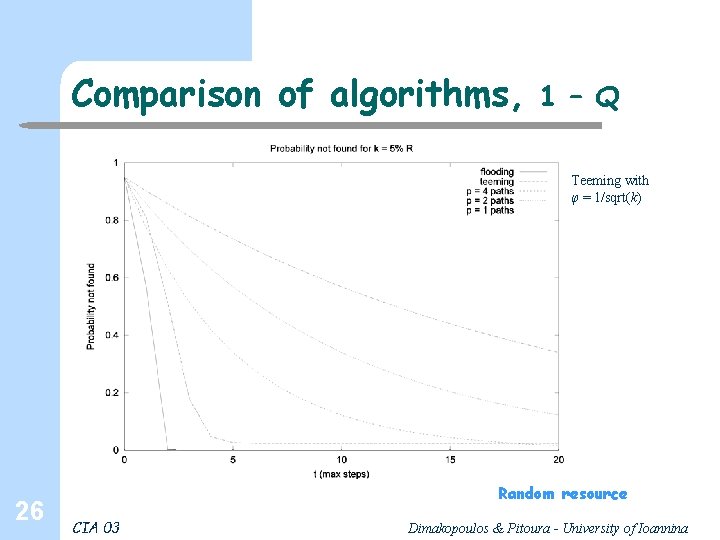
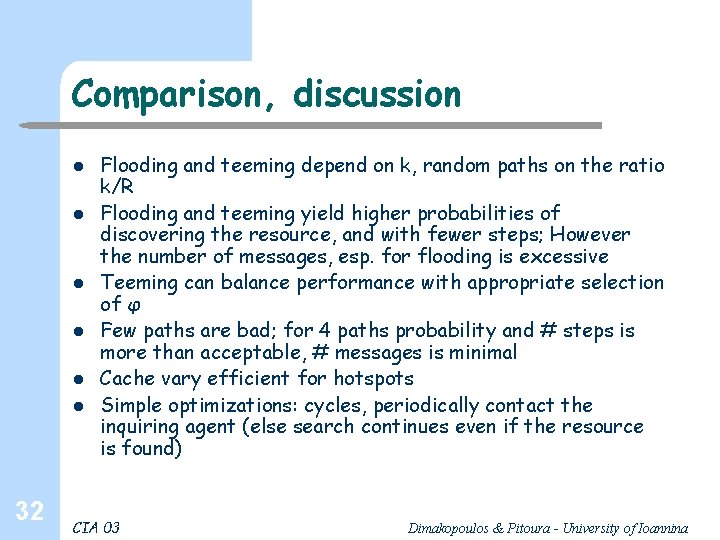
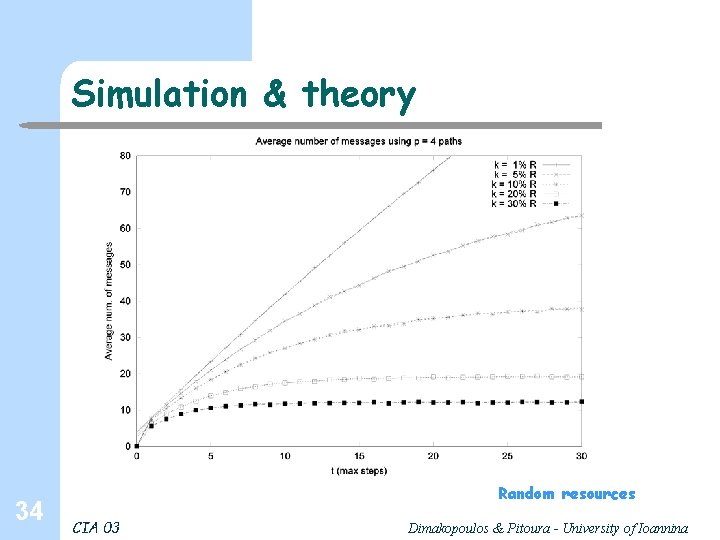
Comparison of algorithms, 1 – Q Teeming with φ = 1/sqrt(k) 26 Random resource CIA 03 Dimakopoulos & Pitoura - University of Ioannina

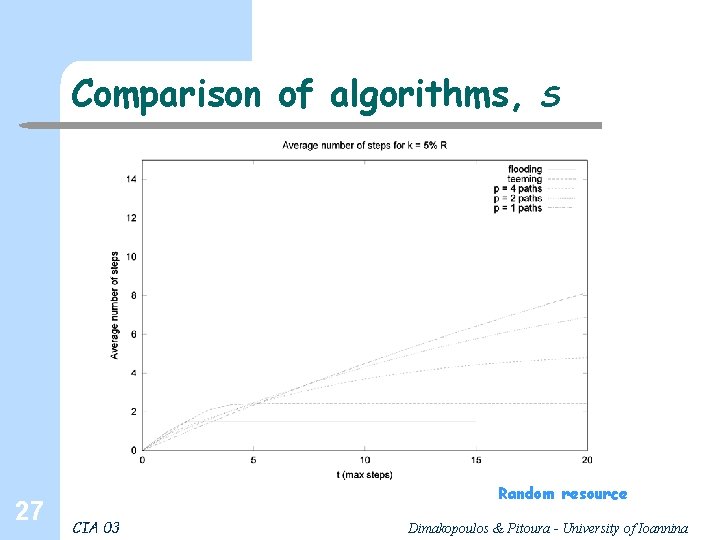
Comparison of algorithms, 27 S Random resource CIA 03 Dimakopoulos & Pitoura - University of Ioannina

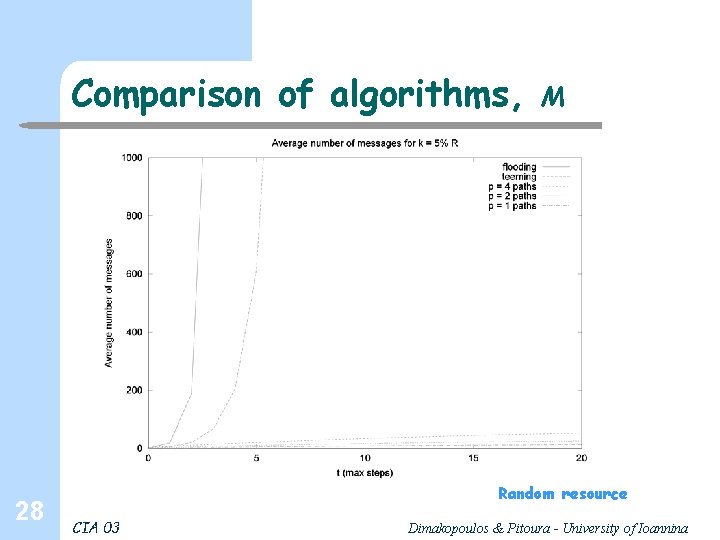
Comparison of algorithms, 28 M Random resource CIA 03 Dimakopoulos & Pitoura - University of Ioannina

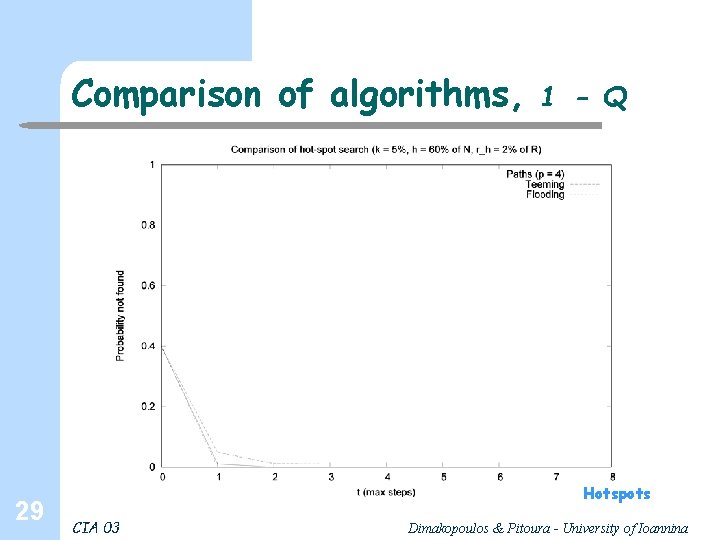
Comparison of algorithms, 29 1 - Q Hotspots CIA 03 Dimakopoulos & Pitoura - University of Ioannina

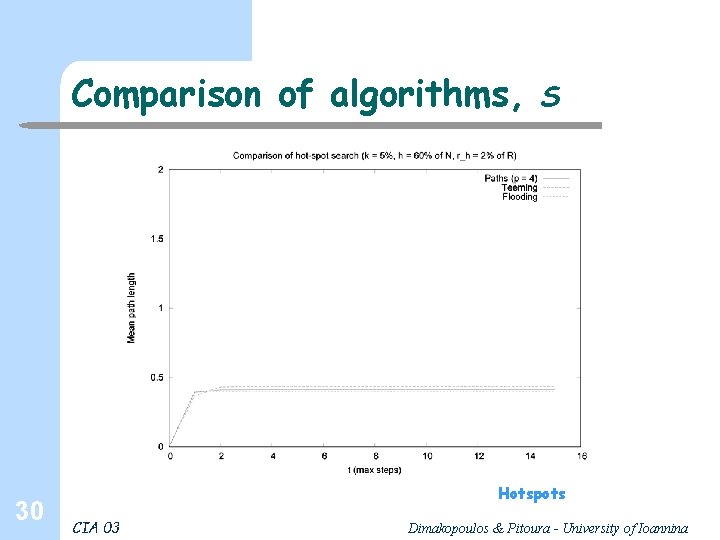
Comparison of algorithms, 30 S Hotspots CIA 03 Dimakopoulos & Pitoura - University of Ioannina

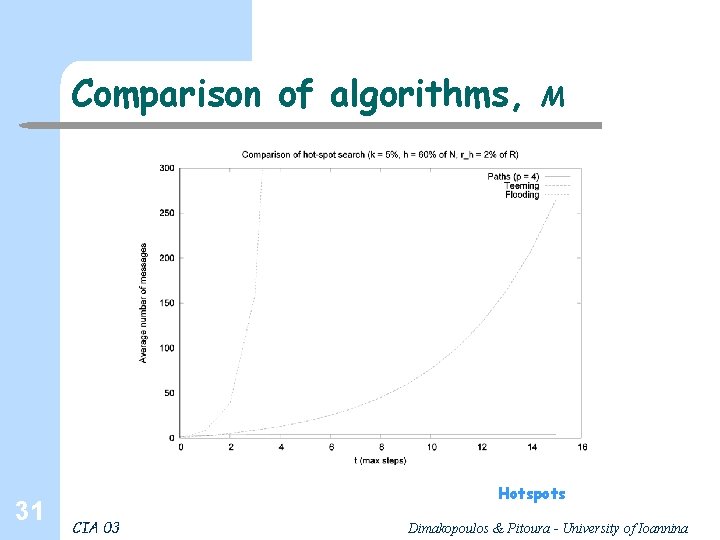
Comparison of algorithms, 31 M Hotspots CIA 03 Dimakopoulos & Pitoura - University of Ioannina

Comparison, discussion l l l 32 Flooding and teeming depend on k, random paths on the ratio k/R Flooding and teeming yield higher probabilities of discovering the resource, and with fewer steps; However the number of messages, esp. for flooding is excessive Teeming can balance performance with appropriate selection of φ Few paths are bad; for 4 paths probability and # steps is more than acceptable, # messages is minimal Cache vary efficient for hotspots Simple optimizations: cycles, periodically contact the inquiring agent (else search continues even if the resource is found) CIA 03 Dimakopoulos & Pitoura - University of Ioannina

Simulation l l l 33 Simulators for all algorithms constructed 200 to 500 resources 1000 to 5000 agents/caches Initially all caches filled randomly Search for a uniformly random resource, 1000 repetitions Analysis confirmed with negligible error (less than 0. 5% in most cases) CIA 03 Dimakopoulos & Pitoura - University of Ioannina

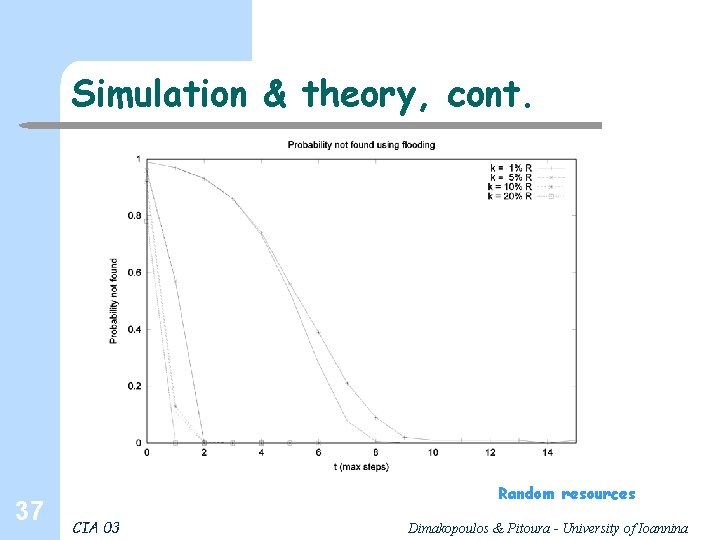
Simulation & theory 34 Random resources CIA 03 Dimakopoulos & Pitoura - University of Ioannina

Simulation & theory, cont. 35 Random resources CIA 03 Dimakopoulos & Pitoura - University of Ioannina

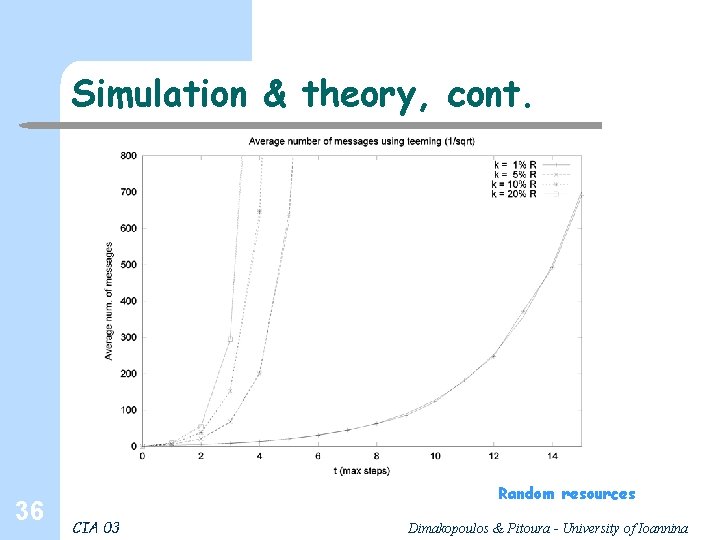
Simulation & theory, cont. 36 Random resources CIA 03 Dimakopoulos & Pitoura - University of Ioannina

Simulation & theory, cont. 37 Random resources CIA 03 Dimakopoulos & Pitoura - University of Ioannina

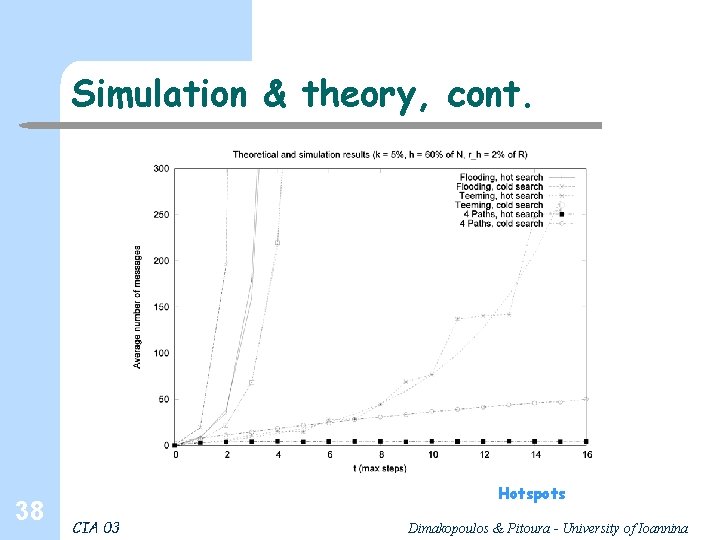
Simulation & theory, cont. 38 Hotspots CIA 03 Dimakopoulos & Pitoura - University of Ioannina

Updates Type of updates (1) Agent offers a new resource or cease to offer a resource (2) The contact information of an agent changes (e. g. , it moves) Discuss case 2 above – decentralized solution 39 CIA 03 Dimakopoulos & Pitoura - University of Ioannina

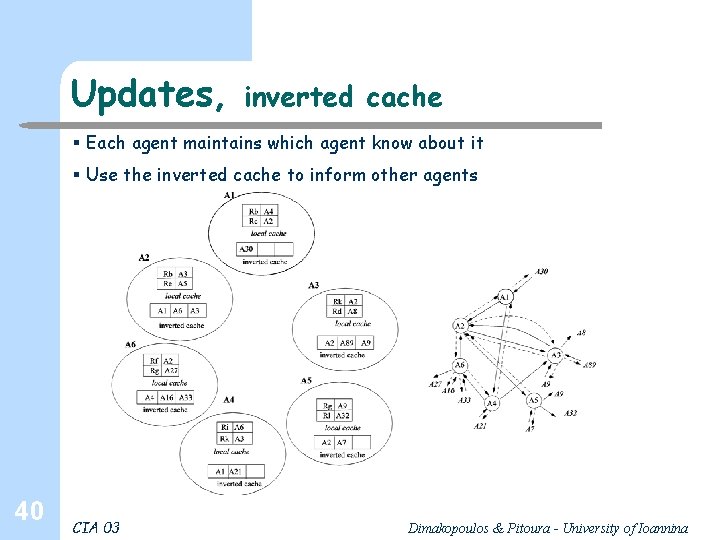
Updates, inverted cache § Each agent maintains which agent know about it § Use the inverted cache to inform other agents 40 CIA 03 Dimakopoulos & Pitoura - University of Ioannina

Updates, flooding § When an agent moves, it informs the agent in its cache and so on § Neighbor relationship is not symmetric, A knows B, B may not know A 41 CIA 03 Dimakopoulos & Pitoura - University of Ioannina

Summary l l l 42 A new scheme for open MAS: a distributed cache network Decentralized unstructured p 2 p resource discovery Algorithms proposed: classical flooding, teeming (randomized flooding), random paths Performance study of searching: analytical models for probability of locating, average # steps, average # messages Cache updates CIA 03 Dimakopoulos & Pitoura - University of Ioannina

Future Work § Prototype implementation (In progress) § Updates/Mobility (In progress) implementation in the Aglets platform completed experimental evaluations under way Performance evaluation § Caches evolve over time Cache replacement issues § Extend performance evaluation Random/Hot spots -> Small world network of caches 43 CIA 03 Dimakopoulos & Pitoura - University of Ioannina

A Peer-to-Peer Approach to Resource Discovery in Multi-Agent Systems QUESTIONS? Dimakopoulos & Pitoura University of Ioannina