A OneTime Password Authentication Method for Low Spec



- Slides: 13

A One-Time Password Authentication Method for Low Spec Machines and on Internet Protocols Author : Takasuke TSUJI, Akihiro SHIMIZU Source : IEICE Transactions on Communications, Vol. E 87 -B, No 6, June 2004, pp. 15941600 Speaker: Z. Y. Wu(吳紫嫣) Date : 2005/01/04 2021/9/20 1

Outline l l Introduction SAS-2 Application for Key-Free Systems Conclusion 2021/9/20 2

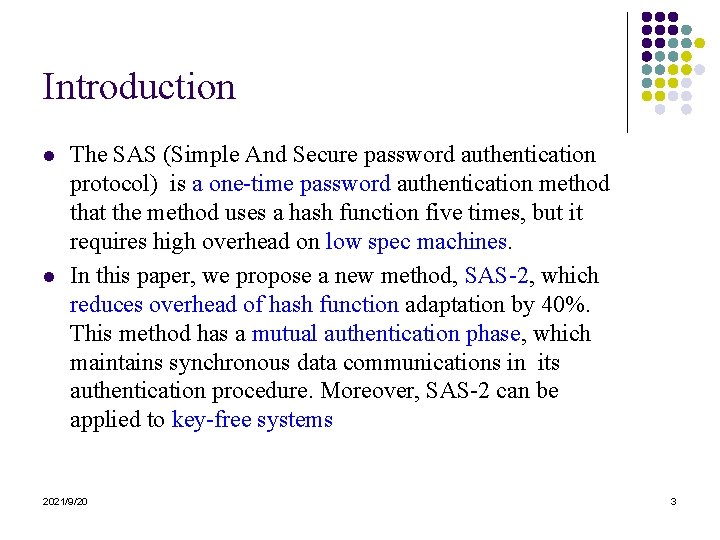
Introduction l l The SAS (Simple And Secure password authentication protocol) is a one-time password authentication method that the method uses a hash function five times, but it requires high overhead on low spec machines. In this paper, we propose a new method, SAS-2, which reduces overhead of hash function adaptation by 40%. This method has a mutual authentication phase, which maintains synchronous data communications in its authentication procedure. Moreover, SAS-2 can be applied to key-free systems 2021/9/20 3

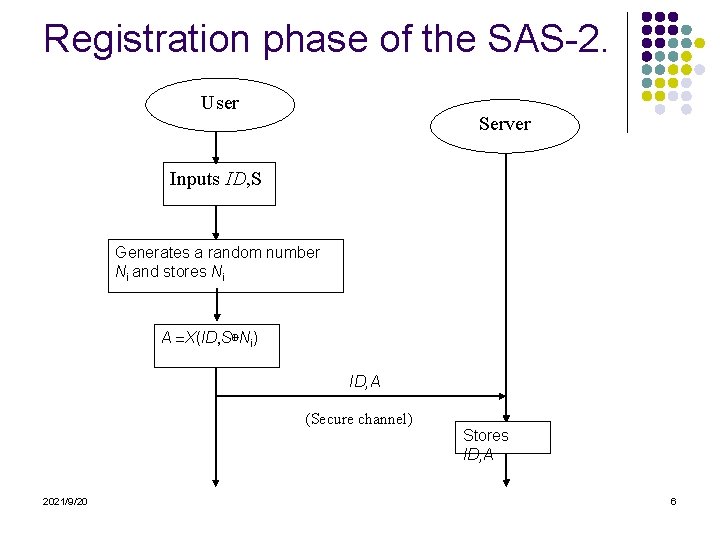
SAS-2 Protocol l The SAS-2 protocol consists of two phases: the registration phase and the authentication phase. l The registration process is performed only once, and the authentication procedure is executed every time the user login to the system. 2021/9/20 4

Definitions User is the computer user who employs the protocol for authentication. l Server is the server that authenticates users. l ID is the user’s identity. l S is the user’s password. l X, F and H are one-way hash functions. For example, H(x) means x is hashed once. l i is an integer indicating the number of authentication sessions. l Ni represents a random number corresponding to the ith authentication. l + represents the addition operation. l represents a bitwise XOR operation. 2021/9/20 5 l

Registration phase of the SAS-2. User Server Inputs ID, S Generates a random number Ni and stores Ni A =X(ID, S⊕Ni) ID, A (Secure channel) 2021/9/20 Stores ID, A 6

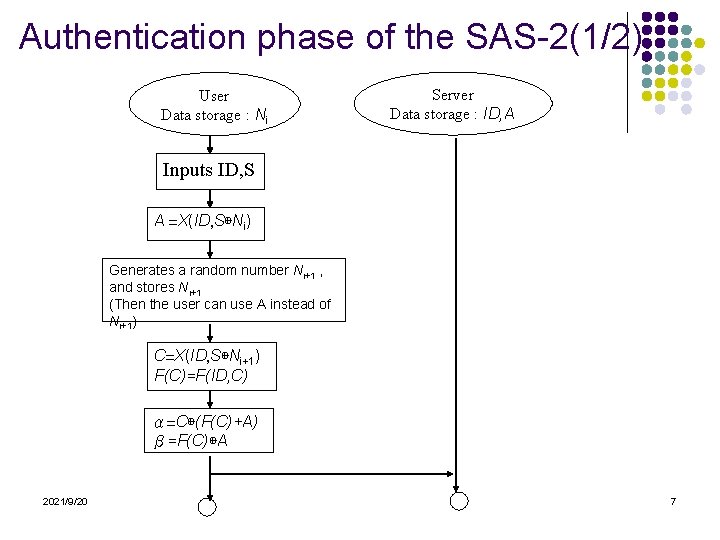
Authentication phase of the SAS-2(1/2). User Data storage : Ni Server Data storage : ID, A Inputs ID, S A =X(ID, S⊕Ni) Generates a random number Ni+1 , and stores Ni+1 (Then the user can use A instead of Ni+1) C=X(ID, S⊕Ni+1) F(C)=F(ID, C) α=C⊕(F(C)+A) β=F(C)⊕A 2021/9/20 7

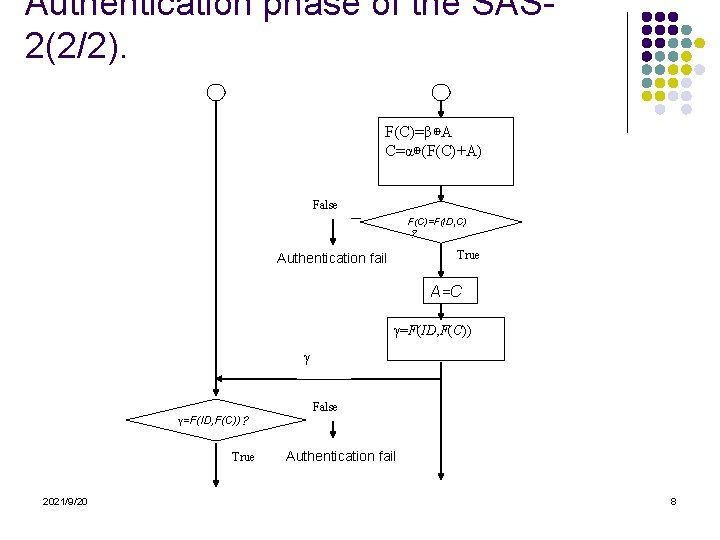
Authentication phase of the SAS 2(2/2). F(C)=β⊕A C=α⊕(F(C)+A) False F(C)=F(ID, C) ? True Authentication fail A=C γ=F(ID, F(C)) γ False γ=F(ID, F(C))? True 2021/9/20 Authentication fail 8

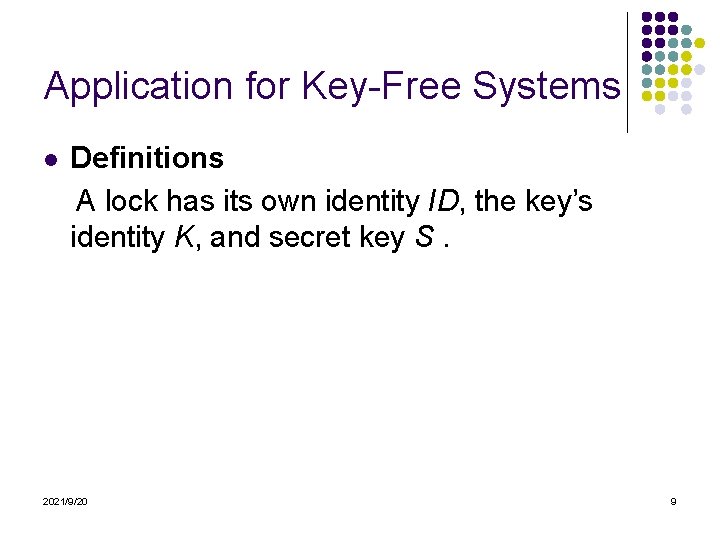
Application for Key-Free Systems l Definitions A lock has its own identity ID, the key’s identity K, and secret key S. 2021/9/20 9

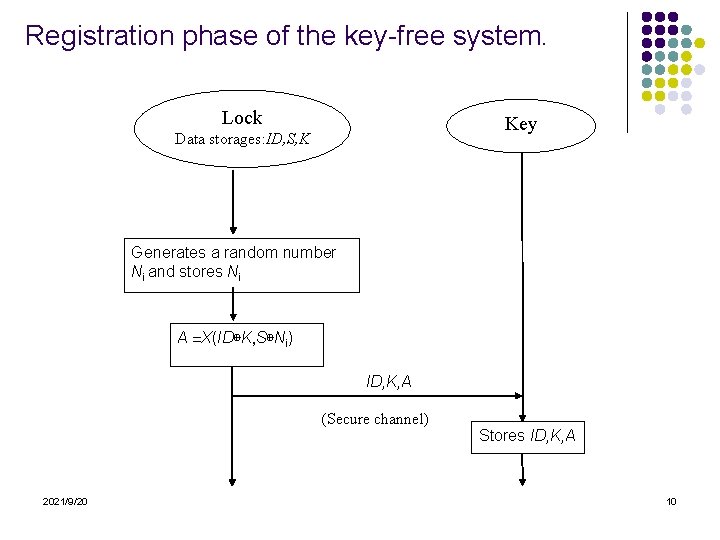
Registration phase of the key-free system. Lock Key Data storages: ID, S, K Generates a random number Ni and stores Ni A =X(ID⊕K, S⊕Ni) ID, K, A (Secure channel) 2021/9/20 Stores ID, K, A 10

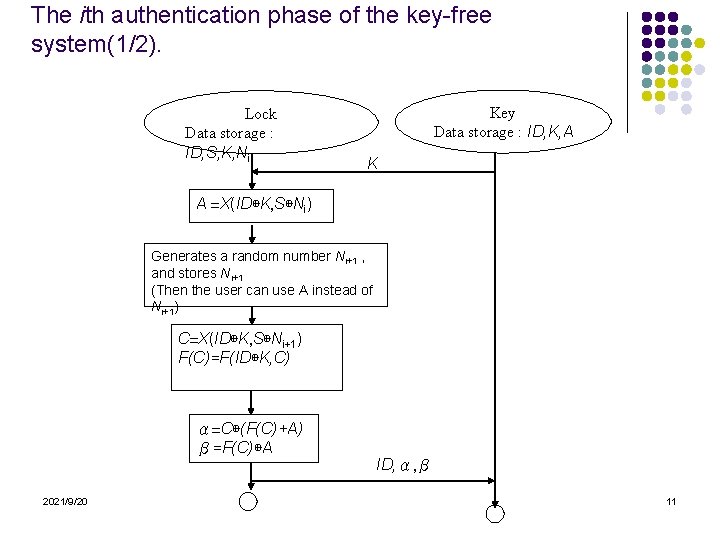
The ith authentication phase of the key-free system(1/2). Lock Data storage : ID, S, K, Ni Key Data storage : ID, K, A K A =X(ID⊕K, S⊕Ni) Generates a random number Ni+1 , and stores Ni+1 (Then the user can use A instead of Ni+1) C=X(ID⊕K, S⊕Ni+1) F(C)=F(ID⊕K, C) α=C⊕(F(C)+A) β=F(C)⊕A 2021/9/20 ID, α, β 11

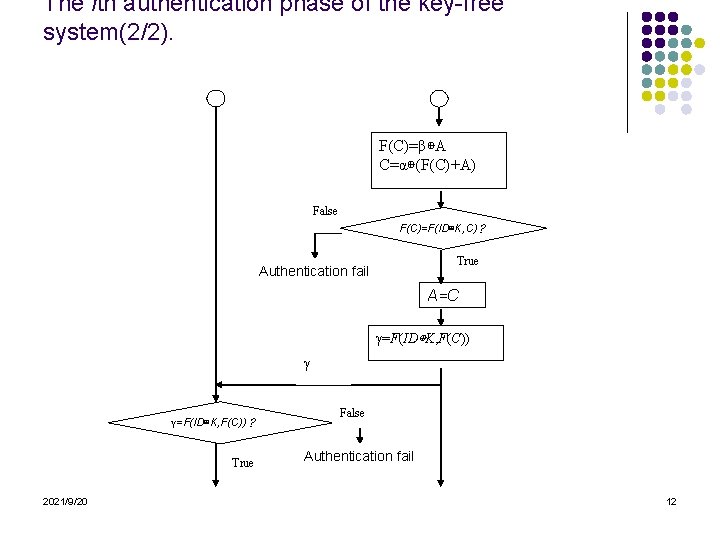
The ith authentication phase of the key-free system(2/2). F(C)=β⊕A C=α⊕(F(C)+A) False F(C)=F(ID⊕K, C)? True Authentication fail A=C γ=F(ID⊕K, F(C)) γ γ=F(ID⊕K, F(C))? True 2021/9/20 False Authentication fail 12

Conclusion l The SAS-2 method has variations, and we have considered all variations of the SAS-2 and have produced safe combinations. In addition, we suggest here an application for key-free systems using the SAS-2 method. 2021/9/20 13