A Methodology for Evaluating Wireless Network Security Protocols











- Slides: 48

A Methodology for Evaluating Wireless Network Security Protocols David Rager Kandaraj Piamrat

Outline ► Introduction ► Explanation of Terms ► Evaluation Methodology ► Analysis of WEP, WPA, and RSN ► Graphical Results ► Conclusion

Introduction ► Difference properties of wireless network comparing to wired network ► Two lines of defense in wireless network security § Preventive approach § Intrusion Detection and Response approach ► WEP WPA RSN

Explanation of Terms ► WEP – Wired Equivalent Protocol (attempt #1) ► WPA – Wi-Fi Protected Access (attempt #2) ► RSN – Robust Secure Network (attempt #3) ► EAP – Extensible Authentication Protocol ► TKIP – Temporal Key Integrity Protocol ► AES – Advanced Encryption Standard

Explanation of Terms (cont. ) ► CCMP – Counter mode with Cipher block Chaining Message authentication code Protocol ► ICV – Integrity Check Value ► MIC – Message Integrity Check ► RADIUS – Remote Authentication Dial in User Service ► IV – Initialization Vector

Evaluation Methodology ► Authentication Capability ► Encryption Strength ► Integrity Guarantees ► Prevention of Attacks ► Identity Protection ► Ease and Cost of Implementation ► Power Consumption ► Novel Ideas

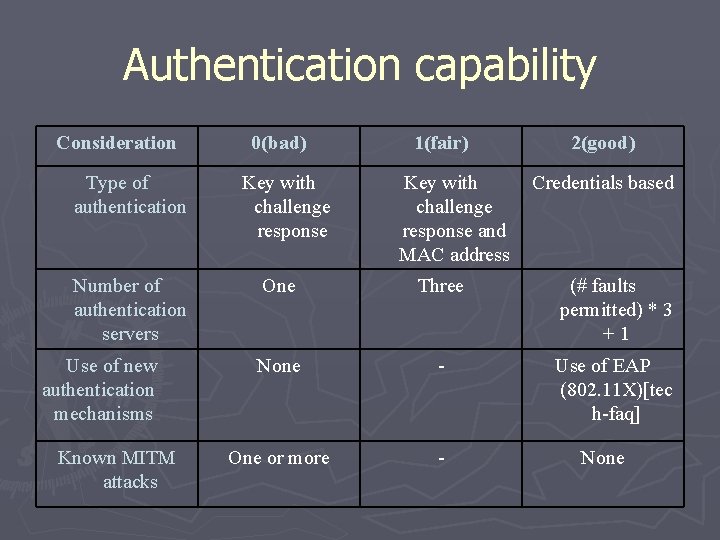
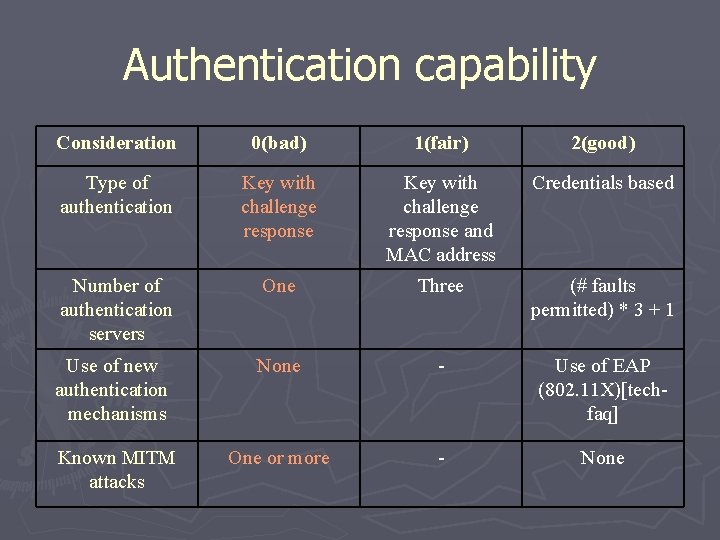
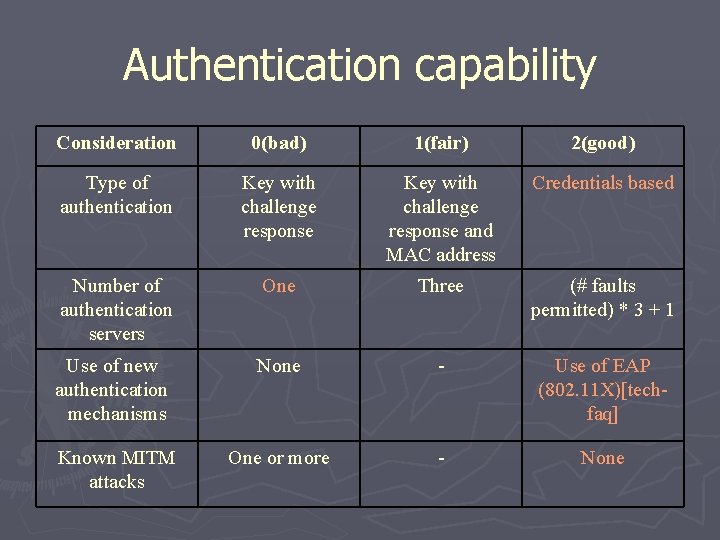
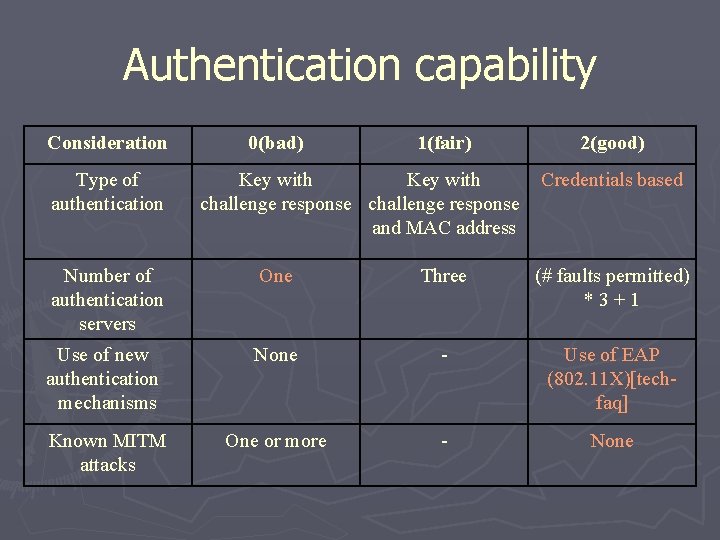
Authentication capability Consideration Type of authentication Number of authentication servers Use of new authentication mechanisms Known MITM attacks 0(bad) Key with challenge response 1(fair) Key with challenge response and MAC address 2(good) Credentials based One Three (# faults permitted) * 3 +1 None - Use of EAP (802. 11 X)[tec h-faq] One or more - None

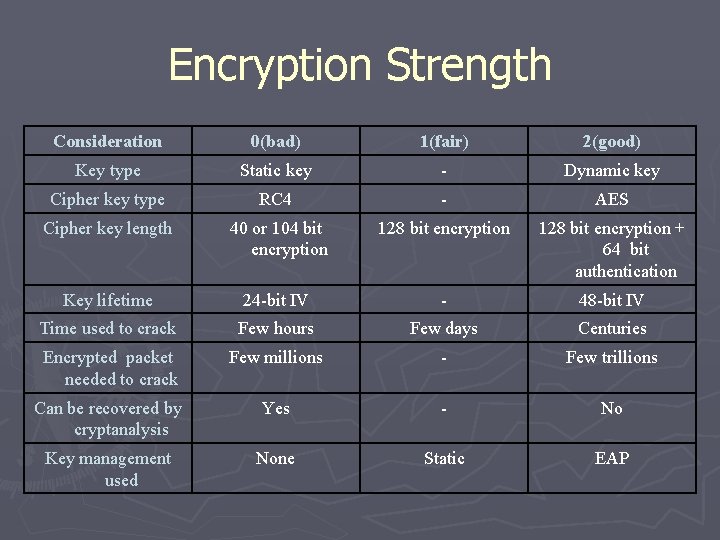
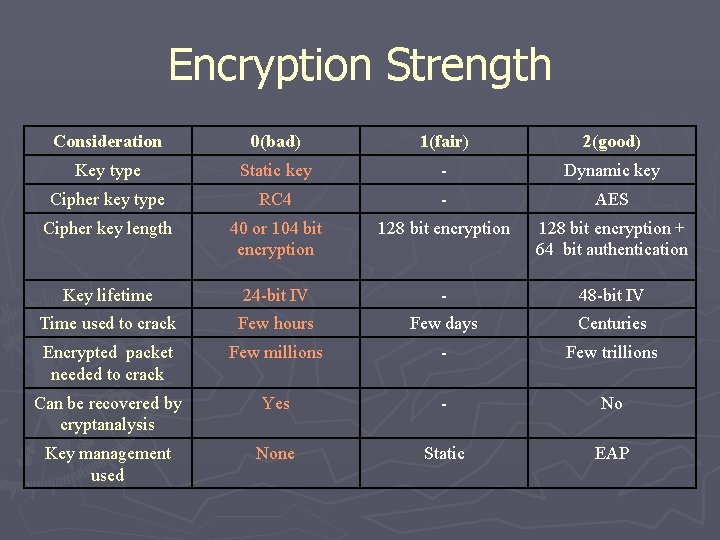
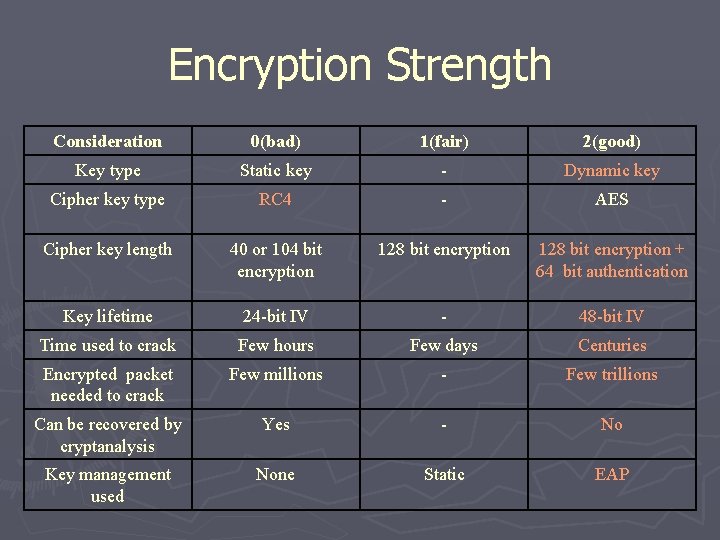
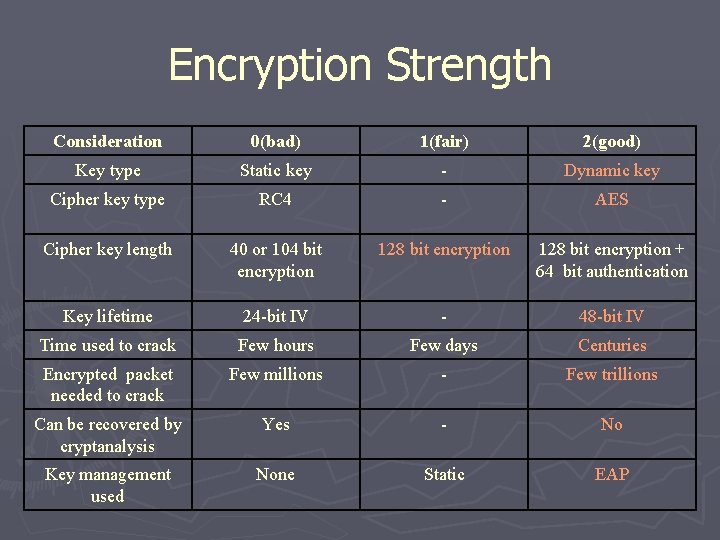
Encryption Strength Consideration 0(bad) 1(fair) 2(good) Key type Static key - Dynamic key Cipher key type RC 4 - AES Cipher key length 40 or 104 bit encryption 128 bit encryption + 64 bit authentication Key lifetime 24 -bit IV - 48 -bit IV Time used to crack Few hours Few days Centuries Encrypted packet needed to crack Few millions - Few trillions Can be recovered by cryptanalysis Yes - No Key management used None Static EAP

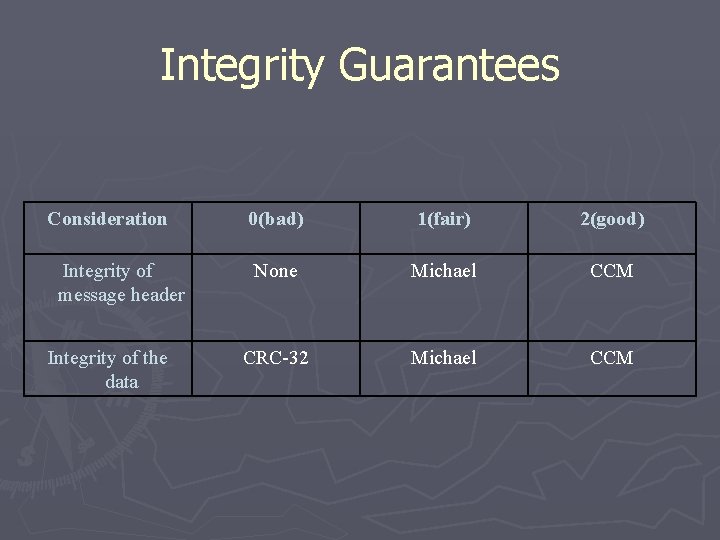
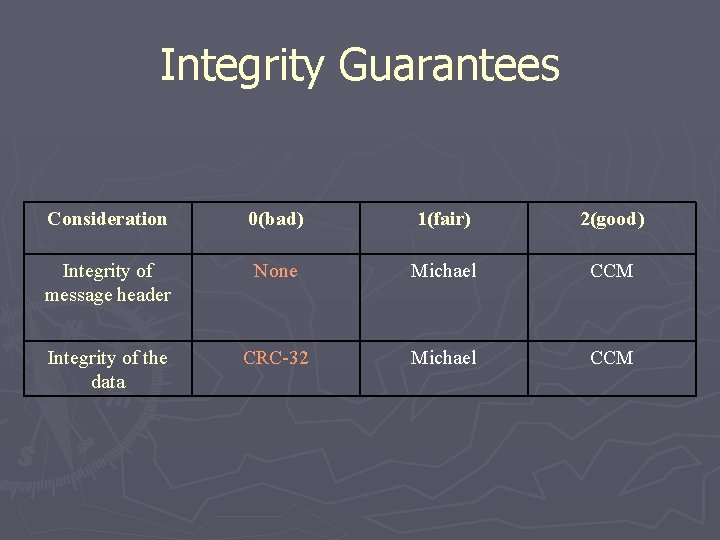
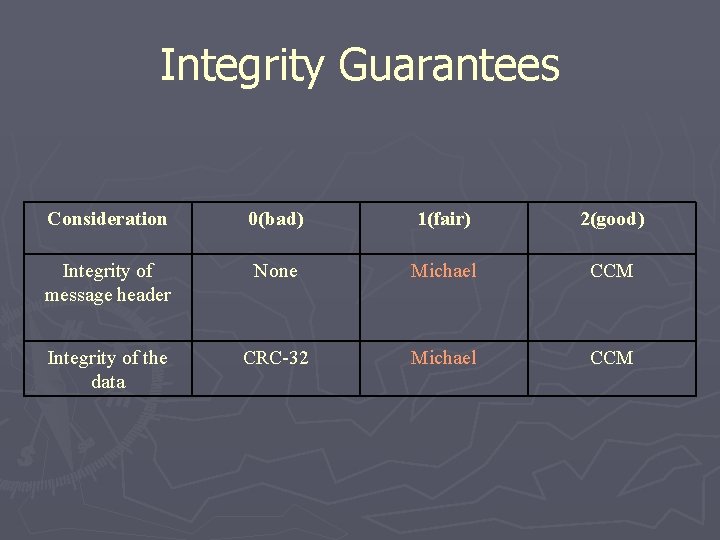
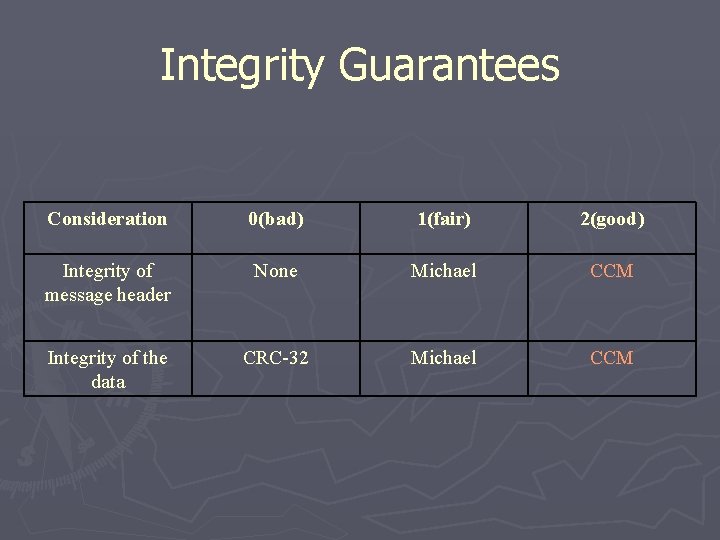
Integrity Guarantees Consideration Integrity of message header Integrity of the data 0(bad) 1(fair) 2(good) None Michael CCM CRC-32 Michael CCM

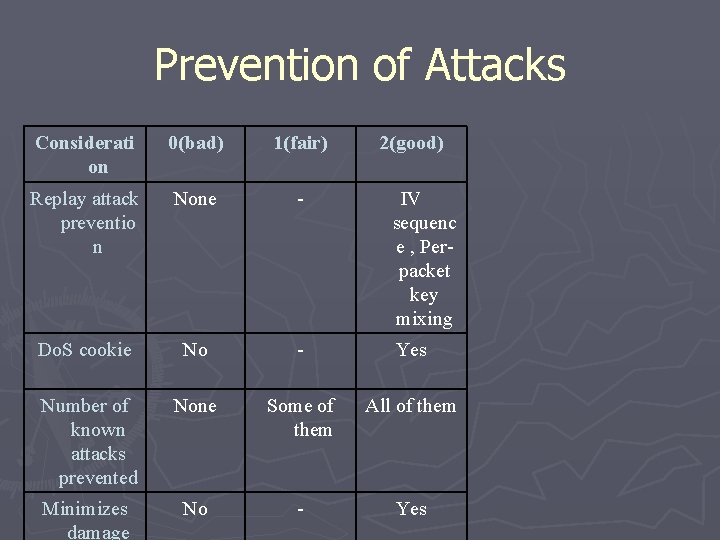
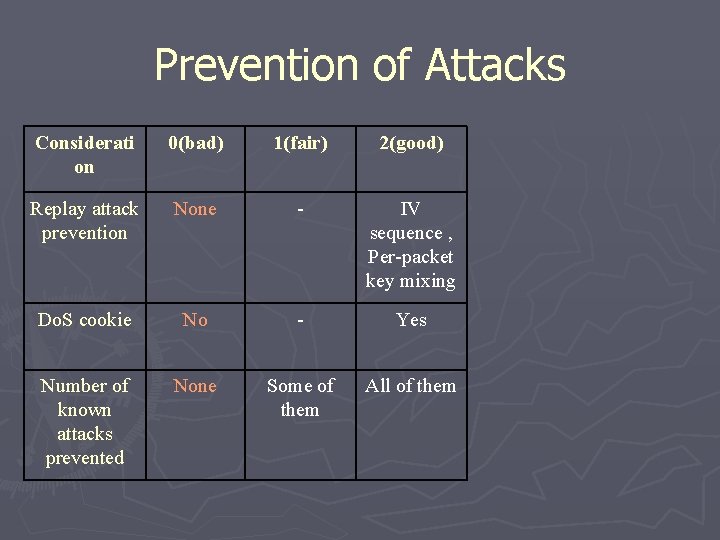
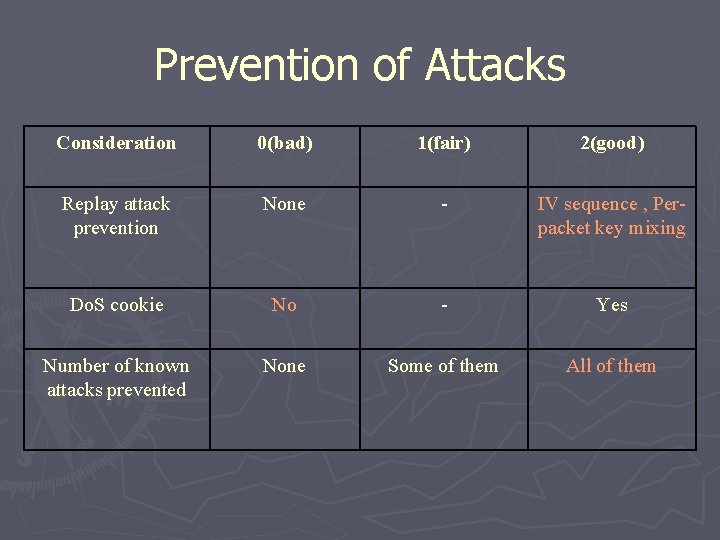
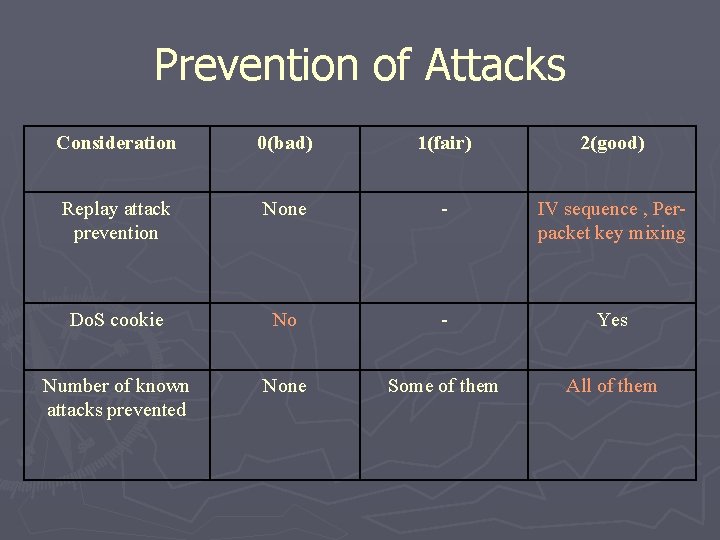
Prevention of Attacks Considerati on 0(bad) 1(fair) 2(good) Replay attack preventio n None - IV sequenc e , Perpacket key mixing Do. S cookie No - Yes Number of known attacks prevented None Some of them All of them Minimizes damage No - Yes

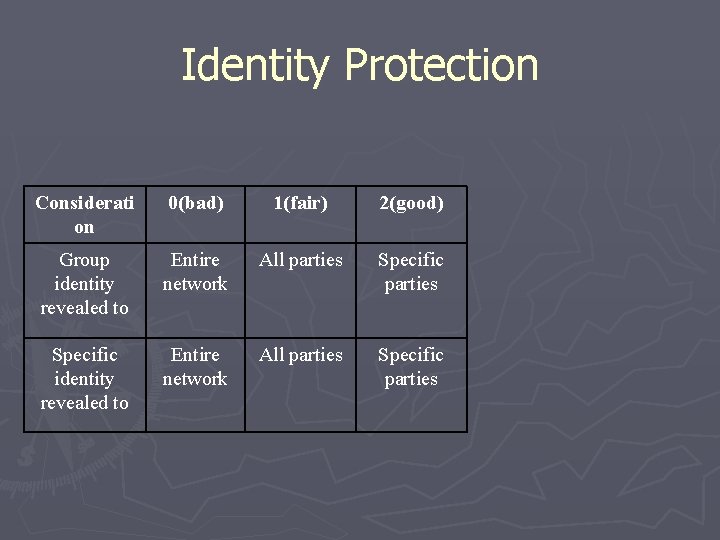
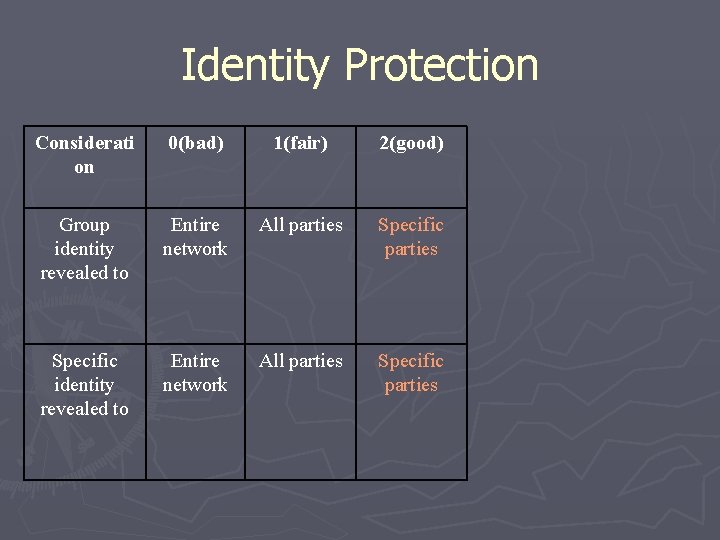
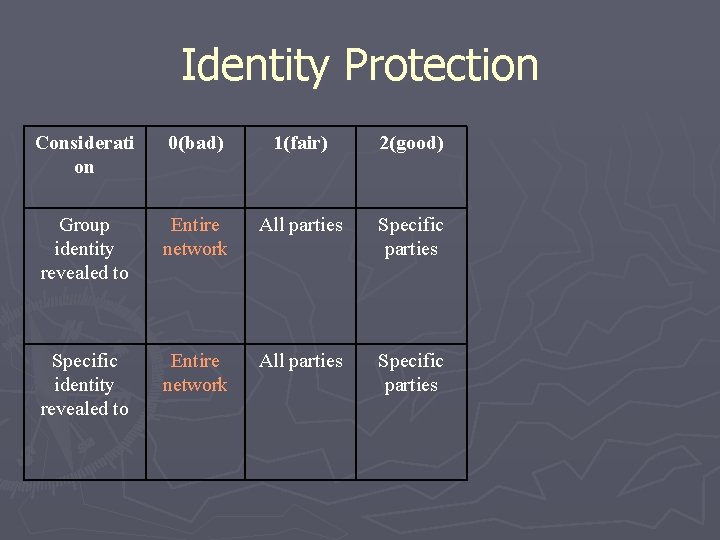
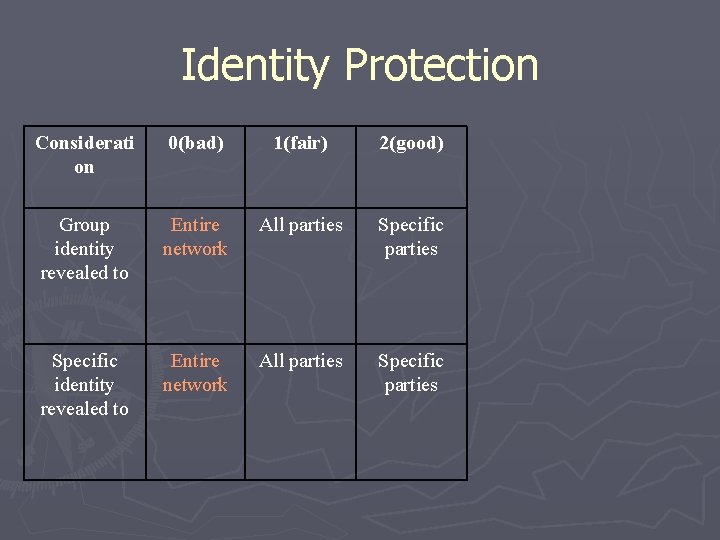
Identity Protection Considerati on 0(bad) 1(fair) 2(good) Group identity revealed to Entire network All parties Specific parties

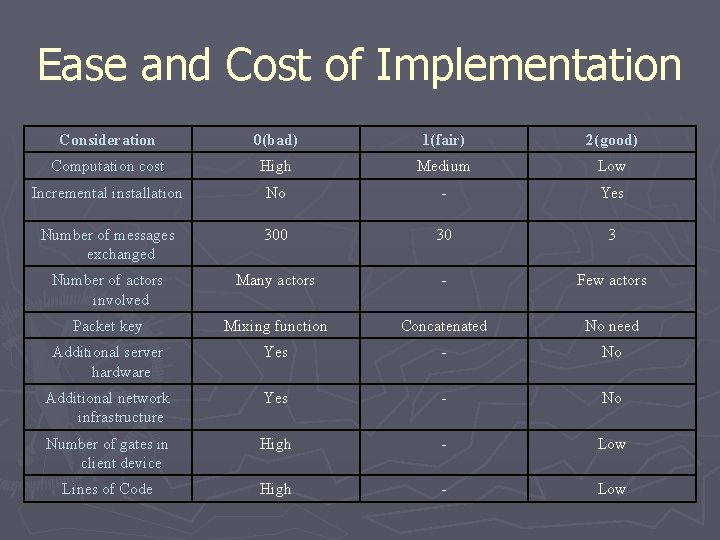
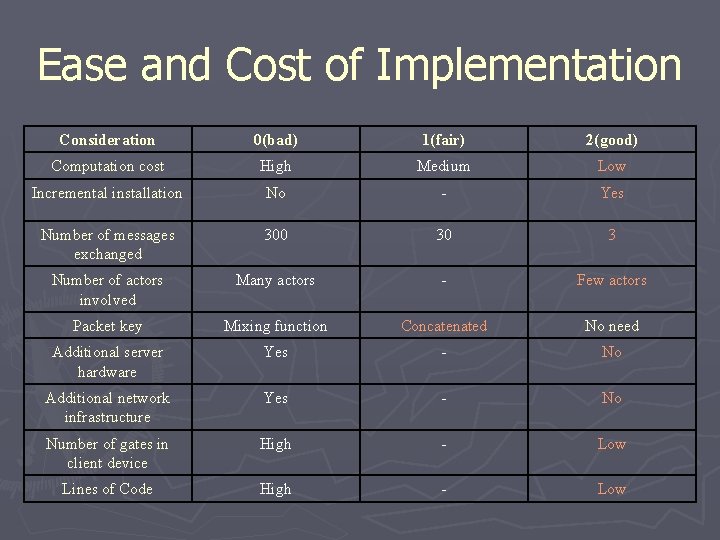
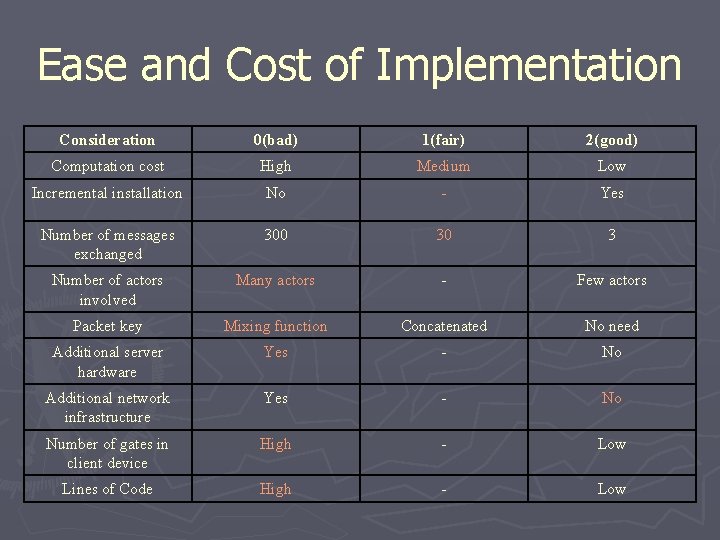
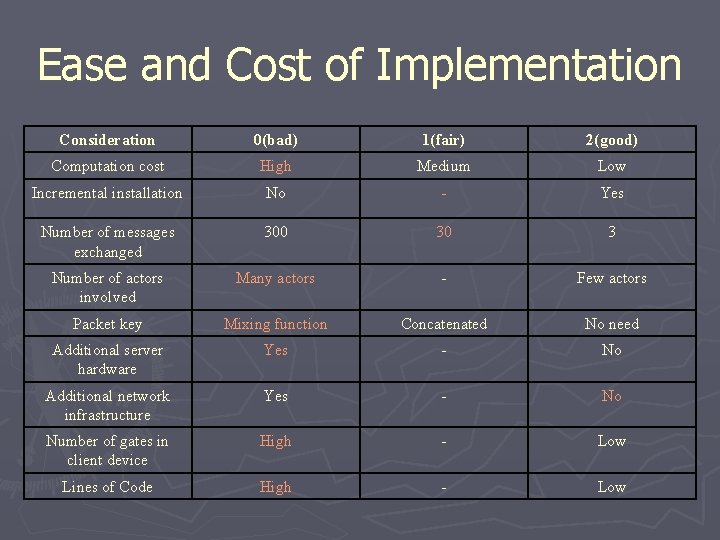
Ease and Cost of Implementation Consideration 0(bad) 1(fair) 2(good) Computation cost High Medium Low Incremental installation No - Yes Number of messages exchanged 300 30 3 Number of actors involved Many actors - Few actors Packet key Mixing function Concatenated No need Additional server hardware Yes - No Additional network infrastructure Yes - No Number of gates in client device High - Low Lines of Code High - Low

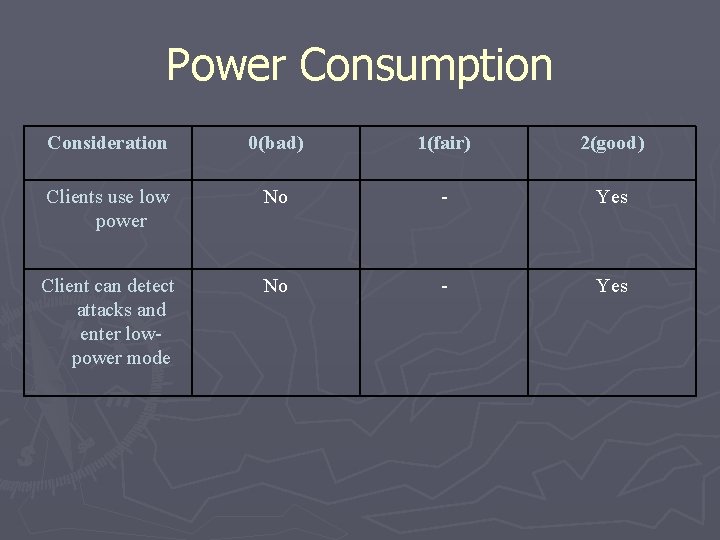
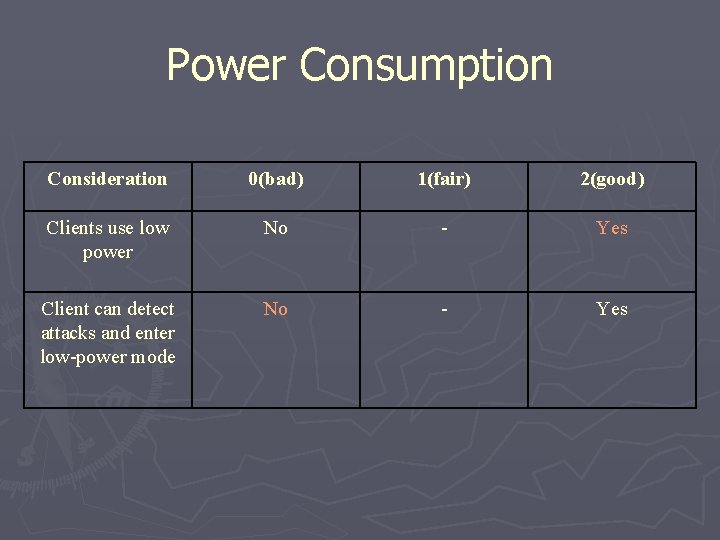
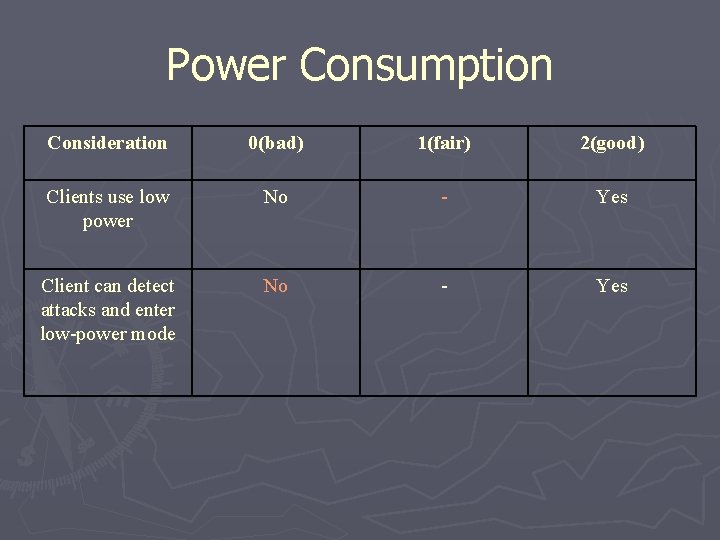
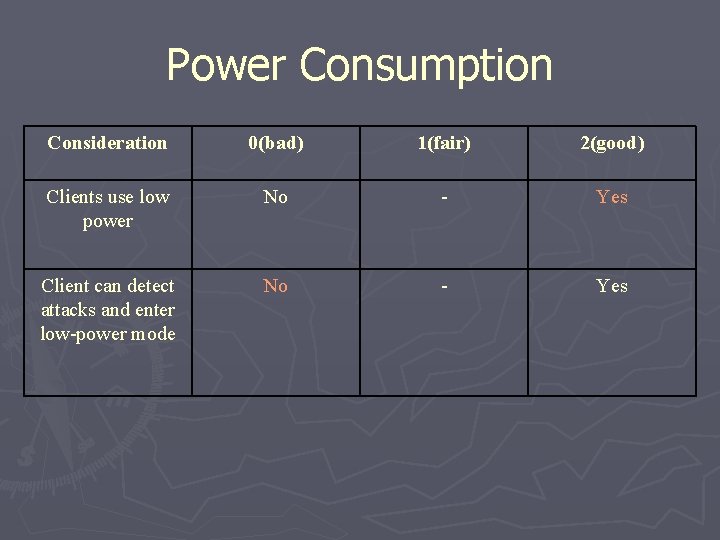
Power Consumption Consideration 0(bad) 1(fair) 2(good) Clients use low power No - Yes Client can detect attacks and enter lowpower mode No - Yes

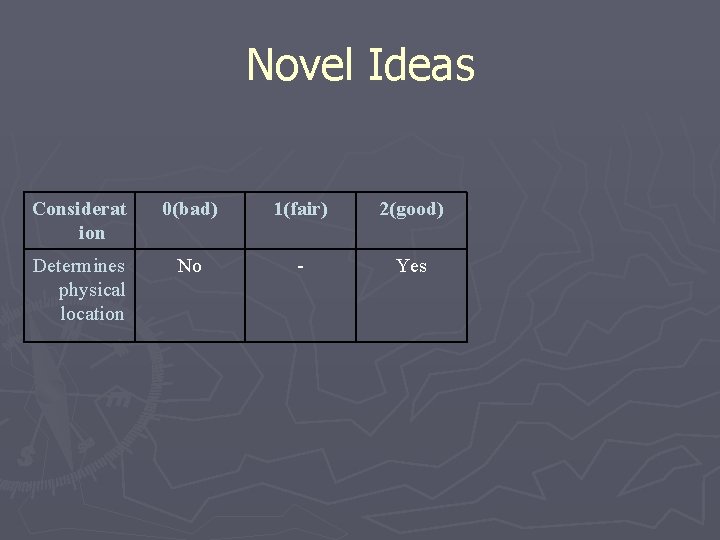
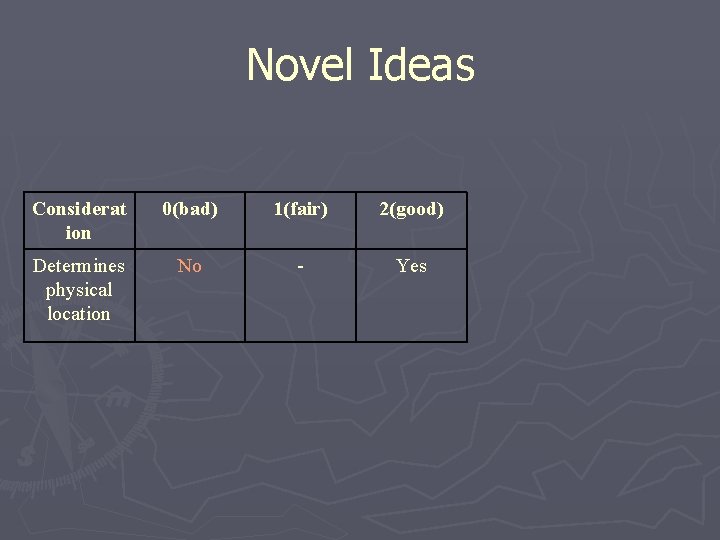
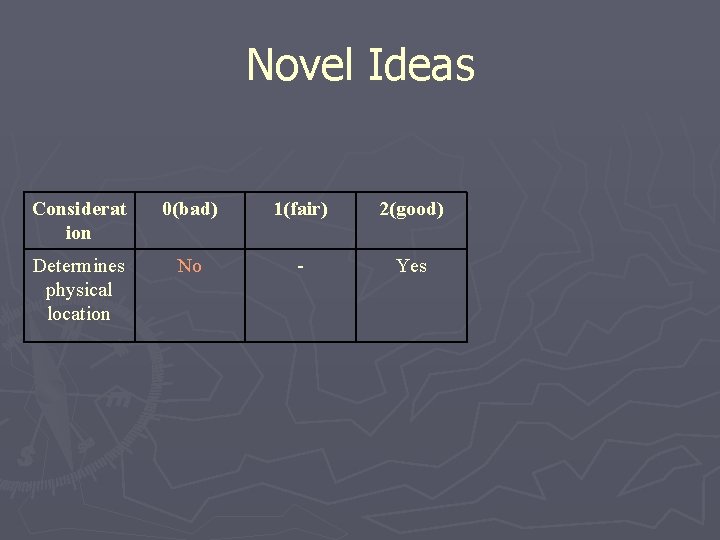
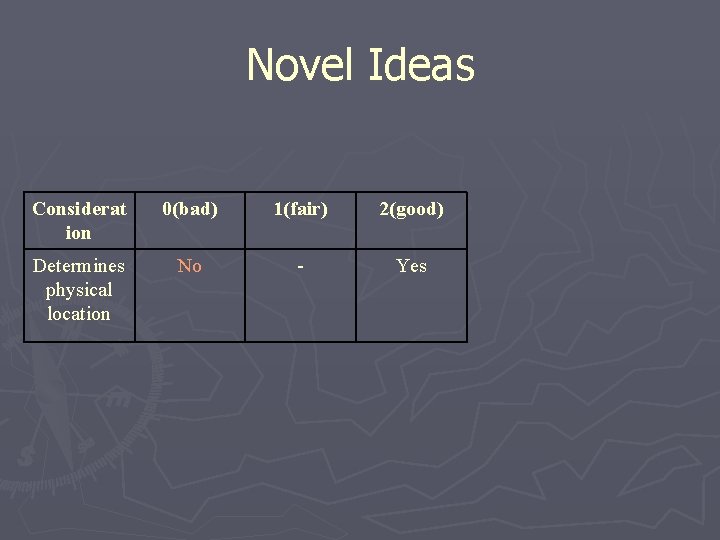
Novel Ideas Considerat ion 0(bad) 1(fair) 2(good) Determines physical location No - Yes

Analysis of WEP

Authentication capability Consideration 0(bad) 1(fair) 2(good) Type of authentication Key with challenge response and MAC address Credentials based Number of authentication servers One Three (# faults permitted) * 3 + 1 Use of new authentication mechanisms None - Use of EAP (802. 11 X)[techfaq] Known MITM attacks One or more - None

Encryption Strength Consideration 0(bad) 1(fair) 2(good) Key type Static key - Dynamic key Cipher key type RC 4 - AES Cipher key length 40 or 104 bit encryption 128 bit encryption + 64 bit authentication Key lifetime 24 -bit IV - 48 -bit IV Time used to crack Few hours Few days Centuries Encrypted packet needed to crack Few millions - Few trillions Can be recovered by cryptanalysis Yes - No Key management used None Static EAP

Integrity Guarantees Consideration 0(bad) 1(fair) 2(good) Integrity of message header None Michael CCM Integrity of the data CRC-32 Michael CCM

Prevention of Attacks Considerati on 0(bad) 1(fair) 2(good) Replay attack prevention None - IV sequence , Per-packet key mixing Do. S cookie No - Yes Number of known attacks prevented None Some of them All of them

Identity Protection Considerati on 0(bad) 1(fair) 2(good) Group identity revealed to Entire network All parties Specific parties

Ease and Cost of Implementation Consideration 0(bad) 1(fair) 2(good) Computation cost High Medium Low Incremental installation No - Yes Number of messages exchanged 300 30 3 Number of actors involved Many actors - Few actors Packet key Mixing function Concatenated No need Additional server hardware Yes - No Additional network infrastructure Yes - No Number of gates in client device High - Low Lines of Code High - Low

Power Consumption Consideration 0(bad) 1(fair) 2(good) Clients use low power No - Yes Client can detect attacks and enter low-power mode No - Yes

Novel Ideas Considerat ion 0(bad) 1(fair) 2(good) Determines physical location No - Yes

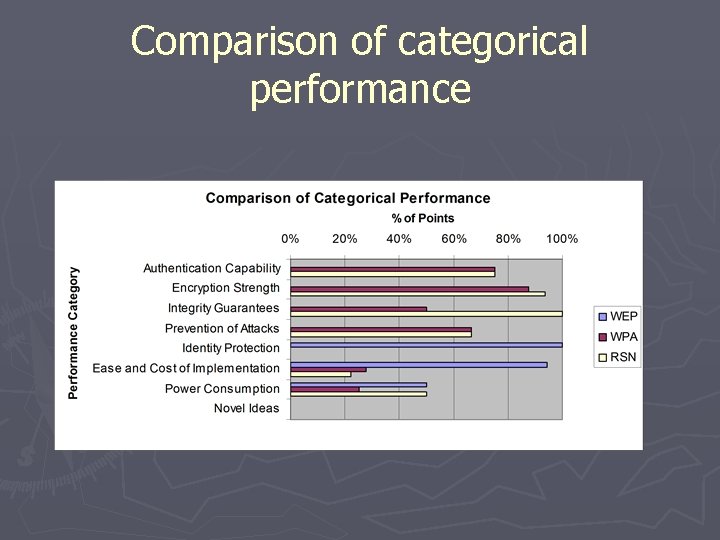
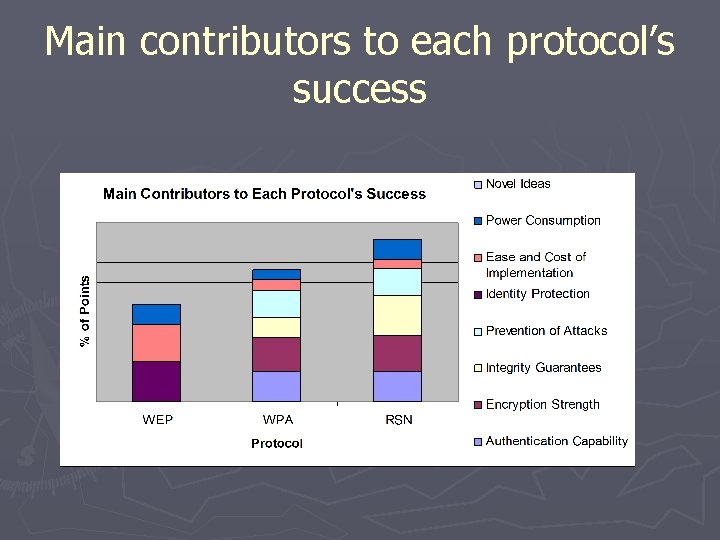
Scores of WEP ► Authentication Capability (0/8) ► Encryption Strength (0/16) ► Integrity Guarantees (0/4) ► Prevention of Attacks (0/6) ► Identity Protection (4/4) ► Ease and Cost of Implementation (17/18) ► Power Consumption (2/4) ► Novel Ideas (0/2) Total Score = 2. 44/8 = 30. 56 %

Analysis of WPA

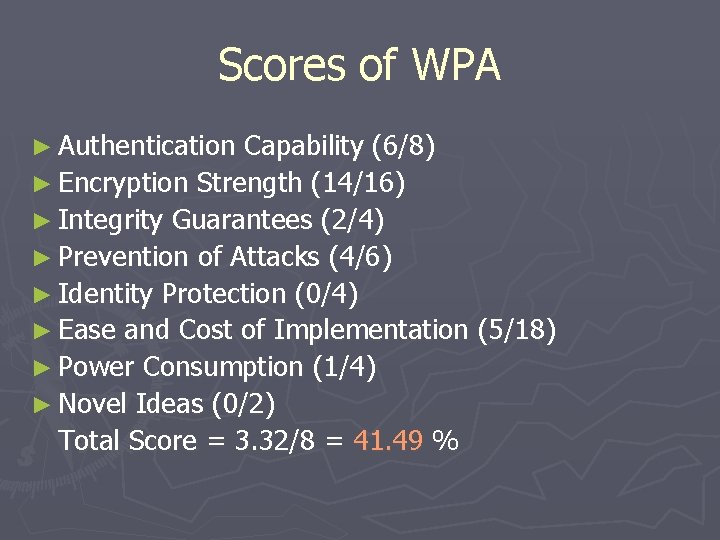
Authentication capability Consideration 0(bad) 1(fair) 2(good) Type of authentication Key with challenge response and MAC address Credentials based Number of authentication servers One Three (# faults permitted) * 3 + 1 Use of new authentication mechanisms None - Use of EAP (802. 11 X)[techfaq] Known MITM attacks One or more - None

Encryption Strength Consideration 0(bad) 1(fair) 2(good) Key type Static key - Dynamic key Cipher key type RC 4 - AES Cipher key length 40 or 104 bit encryption 128 bit encryption + 64 bit authentication Key lifetime 24 -bit IV - 48 -bit IV Time used to crack Few hours Few days Centuries Encrypted packet needed to crack Few millions - Few trillions Can be recovered by cryptanalysis Yes - No Key management used None Static EAP

Integrity Guarantees Consideration 0(bad) 1(fair) 2(good) Integrity of message header None Michael CCM Integrity of the data CRC-32 Michael CCM

Prevention of Attacks Consideration 0(bad) 1(fair) 2(good) Replay attack prevention None - IV sequence , Perpacket key mixing Do. S cookie No - Yes Number of known attacks prevented None Some of them All of them

Identity Protection Considerati on 0(bad) 1(fair) 2(good) Group identity revealed to Entire network All parties Specific parties

Ease and Cost of Implementation Consideration 0(bad) 1(fair) 2(good) Computation cost High Medium Low Incremental installation No - Yes Number of messages exchanged 300 30 3 Number of actors involved Many actors - Few actors Packet key Mixing function Concatenated No need Additional server hardware Yes - No Additional network infrastructure Yes - No Number of gates in client device High - Low Lines of Code High - Low

Power Consumption Consideration 0(bad) 1(fair) 2(good) Clients use low power No - Yes Client can detect attacks and enter low-power mode No - Yes

Novel Ideas Considerat ion 0(bad) 1(fair) 2(good) Determines physical location No - Yes

Scores of WPA ► Authentication Capability (6/8) ► Encryption Strength (14/16) ► Integrity Guarantees (2/4) ► Prevention of Attacks (4/6) ► Identity Protection (0/4) ► Ease and Cost of Implementation (5/18) ► Power Consumption (1/4) ► Novel Ideas (0/2) Total Score = 3. 32/8 = 41. 49 %

Analysis of RSN

Authentication capability Consideration Type of authentication 0(bad) 1(fair) Key with challenge response and MAC address 2(good) Credentials based Number of authentication servers One Three (# faults permitted) *3+1 Use of new authentication mechanisms None - Use of EAP (802. 11 X)[techfaq] Known MITM attacks One or more - None

Encryption Strength Consideration 0(bad) 1(fair) 2(good) Key type Static key - Dynamic key Cipher key type RC 4 - AES Cipher key length 40 or 104 bit encryption 128 bit encryption + 64 bit authentication Key lifetime 24 -bit IV - 48 -bit IV Time used to crack Few hours Few days Centuries Encrypted packet needed to crack Few millions - Few trillions Can be recovered by cryptanalysis Yes - No Key management used None Static EAP

Integrity Guarantees Consideration 0(bad) 1(fair) 2(good) Integrity of message header None Michael CCM Integrity of the data CRC-32 Michael CCM

Prevention of Attacks Consideration 0(bad) 1(fair) 2(good) Replay attack prevention None - IV sequence , Perpacket key mixing Do. S cookie No - Yes Number of known attacks prevented None Some of them All of them

Identity Protection Considerati on 0(bad) 1(fair) 2(good) Group identity revealed to Entire network All parties Specific parties

Ease and Cost of Implementation Consideration 0(bad) 1(fair) 2(good) Computation cost High Medium Low Incremental installation No - Yes Number of messages exchanged 300 30 3 Number of actors involved Many actors - Few actors Packet key Mixing function Concatenated No need Additional server hardware Yes - No Additional network infrastructure Yes - No Number of gates in client device High - Low Lines of Code High - Low

Power Consumption Consideration 0(bad) 1(fair) 2(good) Clients use low power No - Yes Client can detect attacks and enter low-power mode No - Yes

Novel Ideas Considerat ion 0(bad) 1(fair) 2(good) Determines physical location No - Yes

Scores of RSN ► Authentication Capability (6/8) ► Encryption Strength (15/16) ► Integrity Guarantees (4/4) ► Prevention of Attacks (4/6) ► Identity Protection (0/4) ► Ease and Cost of Implementation (4/18) ► Power Consumption (2/4) ► Novel Ideas (0/2) Total Score = 4. 08/8 = 50. 95 %

Graphical Results

Comparison of categorical performance

Main contributors to each protocol’s success

Conclusion ► We have defined specific metrics for protocol evaluation. ► We evaluate different wireless security protocol based on these metrics. ► Questions ?