A LowCost Method to Thwart Relay Attacks in




![Currently Proposed Defense Methods • Distance Bounding [BC 93, HK 05] [BC 93] Stefan Currently Proposed Defense Methods • Distance Bounding [BC 93, HK 05] [BC 93] Stefan](https://slidetodoc.com/presentation_image/4e571ae833988f22b0e684f3dd5f5ef8/image-6.jpg)












![References [BC 93] Stefan Brands and David Chaum. Distance-bounding protocols. In Theory and Application References [BC 93] Stefan Brands and David Chaum. Distance-bounding protocols. In Theory and Application](https://slidetodoc.com/presentation_image/4e571ae833988f22b0e684f3dd5f5ef8/image-34.jpg)
- Slides: 34

A Low-Cost Method to Thwart Relay Attacks in Wireless Sensor Networks Reza Shokri Tutors: Panos Papadimitratos, Marcin Poturalski 29 January 2008

Agenda • • • Neighbor Discovery and Relay Attacks Currently Proposed Defense Methods Our System Model A Low-Cost Method to Thwart Relay Attacks Analysis and Simulation Results Conclusion 2

Neighbor Discovery • Neighbor Discovery is the Building Block of Multi-Hop Communication in WSN. • Security Requirements – Authenticity (Authenticating the neighbors) – Availability (Discovering all neighbors) – Correctness (Verifying the neighborhood relation) • Threats – Impersonation Attacks – Denial of Service (e. g. Jamming Attack) – Relay Attack 3

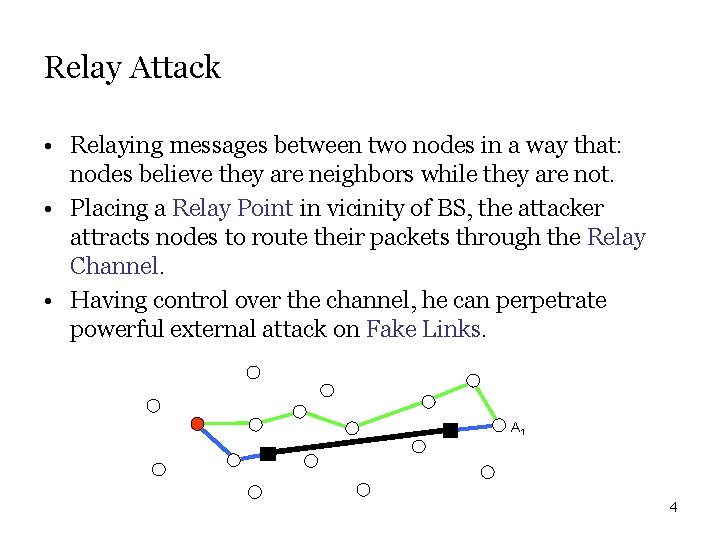
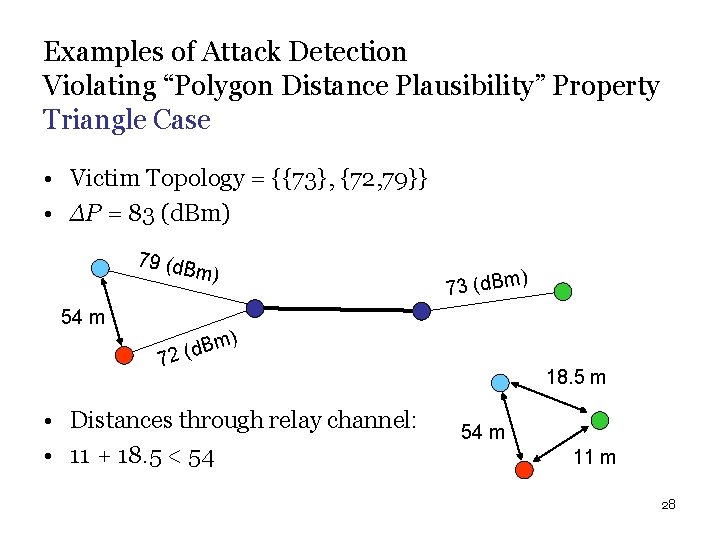
Relay Attack • Relaying messages between two nodes in a way that: nodes believe they are neighbors while they are not. • Placing a Relay Point in vicinity of BS, the attacker attracts nodes to route their packets through the Relay Channel. • Having control over the channel, he can perpetrate powerful external attack on Fake Links. A 1 4

Agenda • • • Neighbor Discovery and Relay Attacks Currently Proposed Defense Methods Our System Model A Low-Cost Method to Thwart Relay Attacks Analysis and Simulation Results Conclusion 5
![Currently Proposed Defense Methods Distance Bounding BC 93 HK 05 BC 93 Stefan Currently Proposed Defense Methods • Distance Bounding [BC 93, HK 05] [BC 93] Stefan](https://slidetodoc.com/presentation_image/4e571ae833988f22b0e684f3dd5f5ef8/image-6.jpg)
Currently Proposed Defense Methods • Distance Bounding [BC 93, HK 05] [BC 93] Stefan Brands and David Chaum. Distance-bounding protocols, 1993. • Location-based [HPJ 03, SRB 01] [HPJ 03] Y. -C. Hu, A. Perrig, and D. B. Johnson. Packet leashes: a defense against wormhole attacks in wireless networks, 2003. • Using Directional Antenna [HE 04] Lingxuan Hu and David Evans. Using directional antennas to prevent wormhole attacks, 2004. • Connectivity-based [BDV 05, MGD 07] [BDV 05] Levente Buttyán, László Dóra, and István Vajda. Statistical wormhole detection in sensor networks, 2005. 6

Observations • These solutions are – Impractical in wireless sensor networks because they require sophisticated hardware or trustworthy external information – Not resilient against strong adversaries. 7

Agenda • • • Neighbor Discovery and Relay Attacks Currently Proposed Defense Methods Our System Model A Low-Cost Method to Thwart Relay Attacks Analysis and Simulation Results Conclusion 8

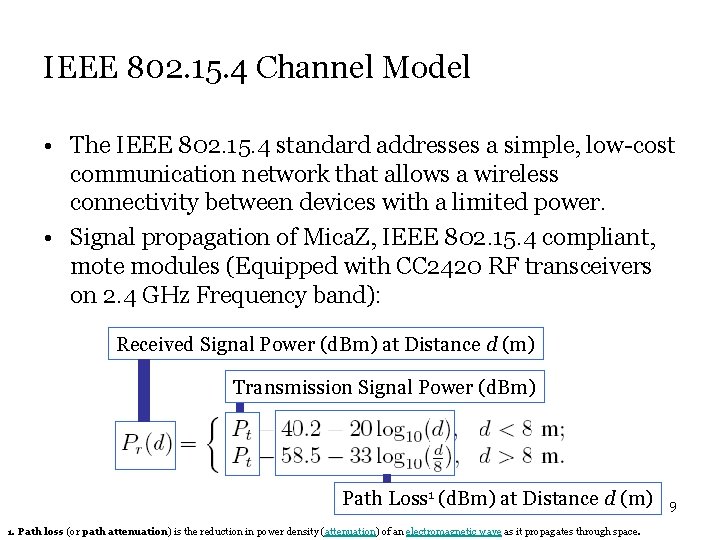
IEEE 802. 15. 4 Channel Model • The IEEE 802. 15. 4 standard addresses a simple, low-cost communication network that allows a wireless connectivity between devices with a limited power. • Signal propagation of Mica. Z, IEEE 802. 15. 4 compliant, mote modules (Equipped with CC 2420 RF transceivers on 2. 4 GHz Frequency band): Received Signal Power (d. Bm) at Distance d (m) Transmission Signal Power (d. Bm) Path Loss 1 (d. Bm) at Distance d (m) 1. Path loss (or path attenuation) is the reduction in power density (attenuation) of an electromagnetic wave as it propagates through space. 9

IEEE 802. 15. 4 Channel Model Received Signal Strength via Distance (on Mica. Z) 10

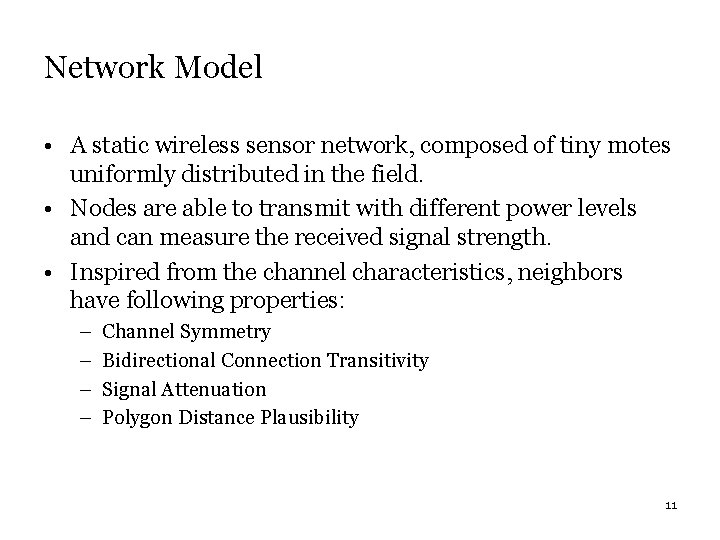
Network Model • A static wireless sensor network, composed of tiny motes uniformly distributed in the field. • Nodes are able to transmit with different power levels and can measure the received signal strength. • Inspired from the channel characteristics, neighbors have following properties: – – Channel Symmetry Bidirectional Connection Transitivity Signal Attenuation Polygon Distance Plausibility 11

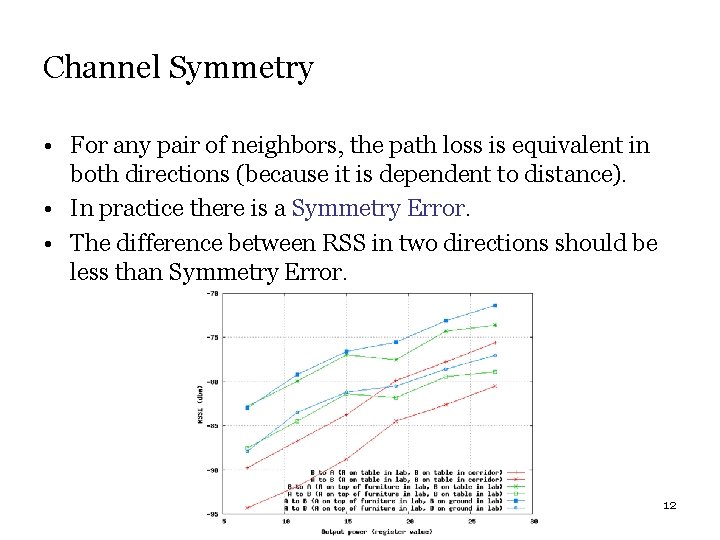
Channel Symmetry • For any pair of neighbors, the path loss is equivalent in both directions (because it is dependent to distance). • In practice there is a Symmetry Error. • The difference between RSS in two directions should be less than Symmetry Error. 12

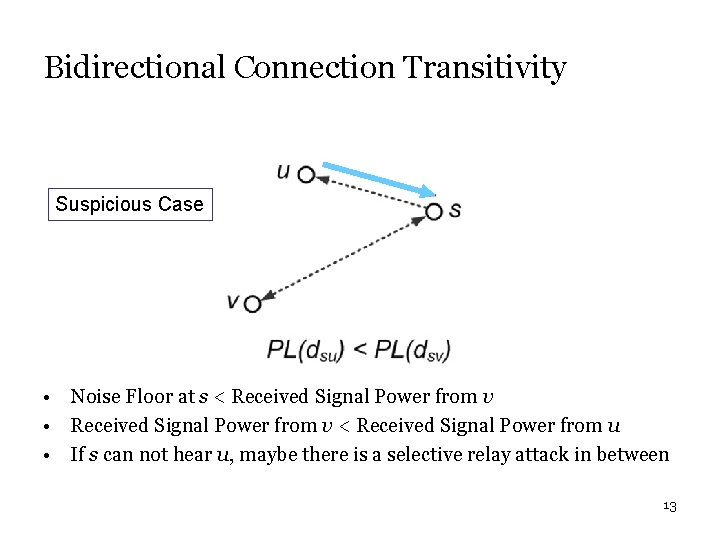
Bidirectional Connection Transitivity Suspicious Case • Noise Floor at s < Received Signal Power from v • Received Signal Power from v < Received Signal Power from u • If s can not hear u, maybe there is a selective relay attack in between 13

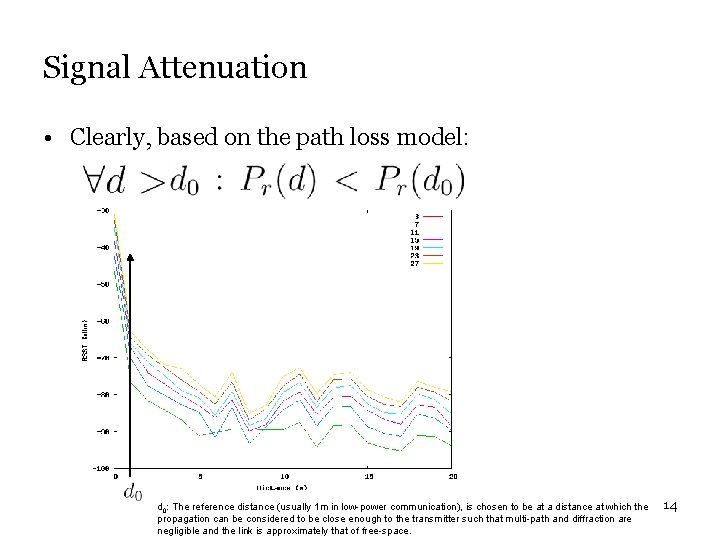
Signal Attenuation • Clearly, based on the path loss model: d 0: The reference distance (usually 1 m in low-power communication), is chosen to be at a distance at which the propagation can be considered to be close enough to the transmitter such that multi-path and diffraction are negligible and the link is approximately that of free-space. 14

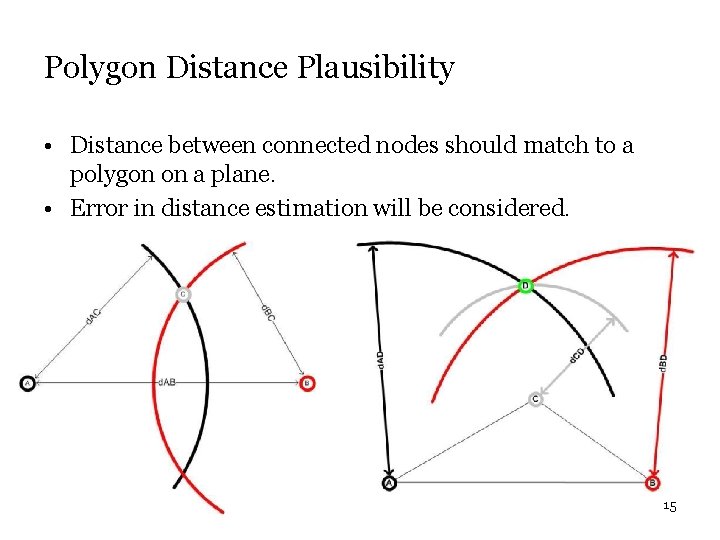
Polygon Distance Plausibility • Distance between connected nodes should match to a polygon on a plane. • Error in distance estimation will be considered. 15

We use currently proposed Security Association (SA) establishment protocol. • SA establishment framework: • After these (at most) three messages, nodes have established a shared key. • We use S in our protocol which stands for SA material. 16

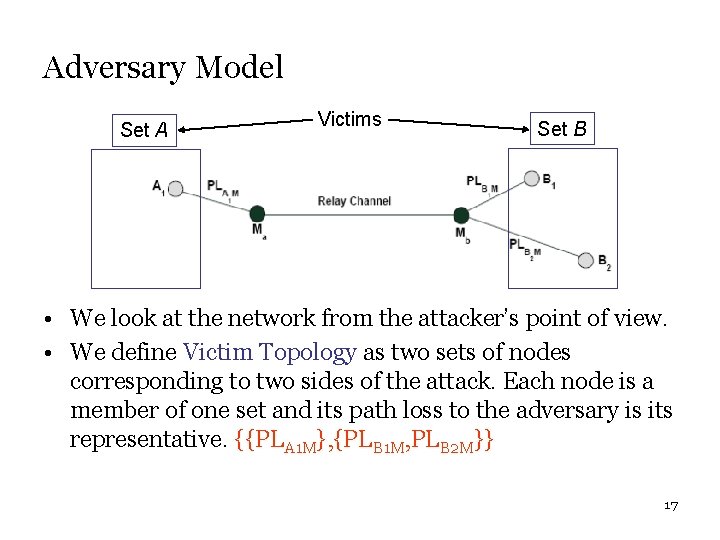
Adversary Model Set A Victims Set B • We look at the network from the attacker’s point of view. • We define Victim Topology as two sets of nodes corresponding to two sides of the attack. Each node is a member of one set and its path loss to the adversary is its representative. {{PLA 1 M}, {PLB 1 M, PLB 2 M}} 17

Attacker Strategy • Attacker Strategy represents how the attacker wants to deceive the victim network (for example by changing the signal power). • A Successful Strategy is the strategy that the attacker can deceive the nodes and remains undetected in the presence of secure neighbor discovery protocol. 18

Agenda • • • Neighbor Discovery and Relay Attacks Currently Proposed Defense Methods Our System Model A Low-Cost Method to Thwart Relay Attacks Analysis and Simulation Results Conclusion 19

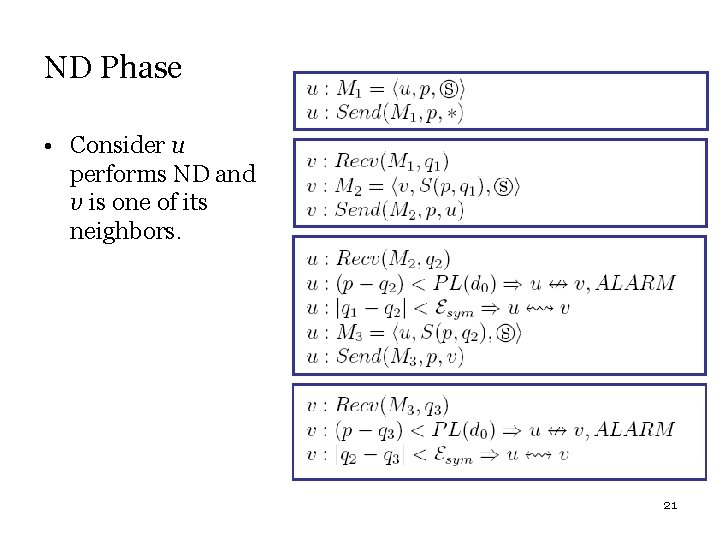
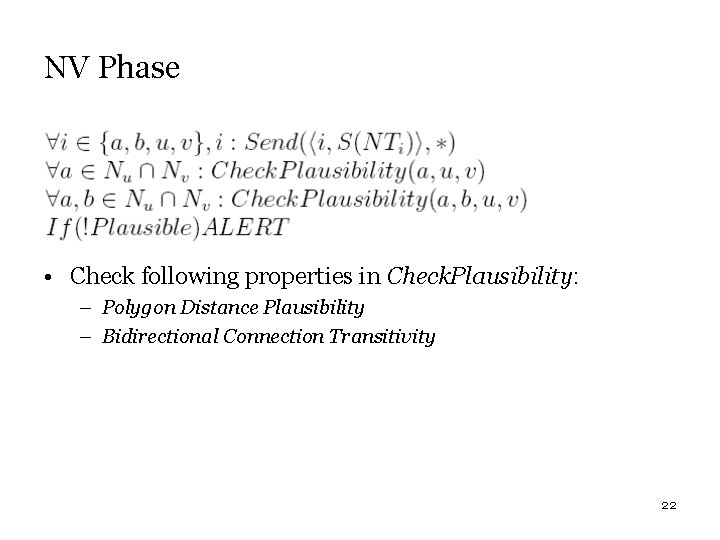
Protocol has two phases: Neighbor Discovery and Neighbor Verification. • Neighbor Discovery (ND) – Nodes simply look for their neighbors and perform SA establishment. – They check "Channel Symmetry" and "Signal Attenuation" properties. • Neighbor Verification (NV) – Nodes exchange their Neighbor Table and check the "Bidirectional Connection Transitivity" and “Polygon Distance Plausibility” properties. 20

ND Phase • Consider u performs ND and v is one of its neighbors. 21

NV Phase • Check following properties in Check. Plausibility: – Polygon Distance Plausibility – Bidirectional Connection Transitivity 22

Agenda • • • Neighbor Discovery and Relay Attacks Currently Proposed Defense Methods Our System Model A Low-Cost Method to Thwart Relay Attacks Analysis and Simulation Results Conclusion 23

Finding Successful Strategy for the Adversary • To fulfill the “Symmetry Property”: – Adversary adds a ∆Pi (d. Bm) to each packet he wants to relay for node i. – To maximize his chance, | ∆Pi - ∆Pj | should be minimized. 24

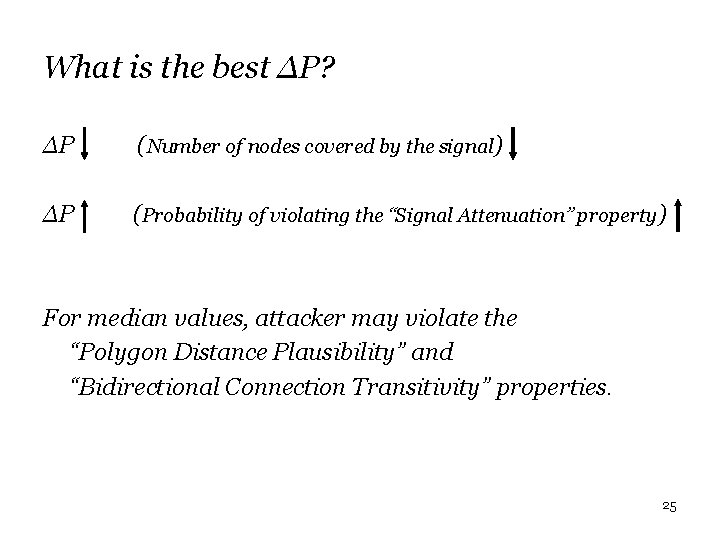
What is the best ∆P? ∆P (Number of nodes covered by the signal) ∆P (Probability of violating the “Signal Attenuation” property) For median values, attacker may violate the “Polygon Distance Plausibility” and “Bidirectional Connection Transitivity” properties. 25

“Selective Relay Strategy” is not always a successful strategy. • Can be detected by “Bidirectional Connection Transitivity” property. • Moreover, if – Nodes randomly use different power levels for NV. – Each node has a different identifier for each power level. – Identifiers of nodes are disclosed to their legitimate neighbors (after authentication). • Then, – Attacker can not link between two messages coming from a single node with different power levels (different identifiers). – Can not have a correct deterministic selective relay. 26

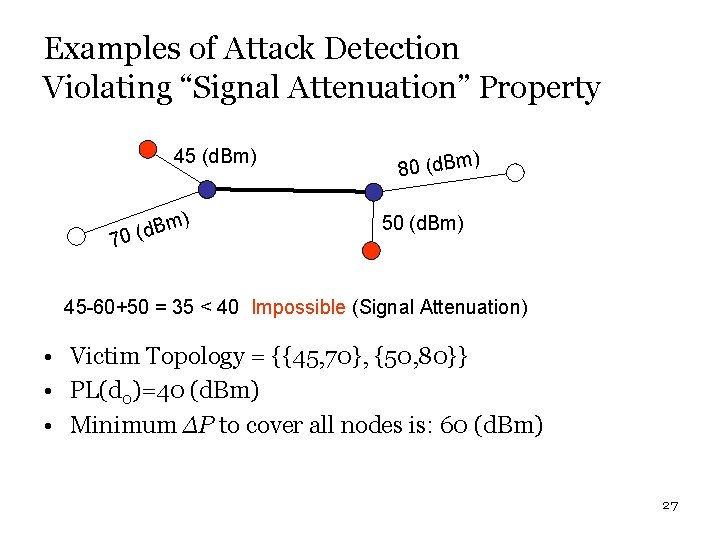
Examples of Attack Detection Violating “Signal Attenuation” Property 45 (d. Bm) Bm d ( 70 ) 80 (d. Bm ) 50 (d. Bm) 45 -60+50 = 35 < 40 Impossible (Signal Attenuation) • Victim Topology = {{45, 70}, {50, 80}} • PL(d 0)=40 (d. Bm) • Minimum ∆P to cover all nodes is: 60 (d. Bm) 27

Examples of Attack Detection Violating “Polygon Distance Plausibility” Property Triangle Case • Victim Topology = {{73}, {72, 79}} • ∆P = 83 (d. Bm) 79 (d. B m) 54 m d. Bm ( 2 7 73 (d. Bm ) ) • Distances through relay channel: • 11 + 18. 5 < 54 18. 5 m 54 m 11 m 28

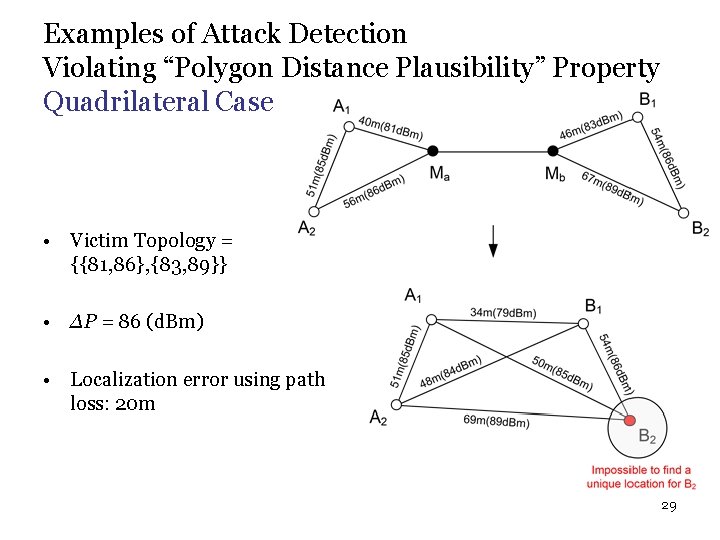
Examples of Attack Detection Violating “Polygon Distance Plausibility” Property Quadrilateral Case • Victim Topology = {{81, 86}, {83, 89}} • ∆P = 86 (d. Bm) • Localization error using path loss: 20 m 29

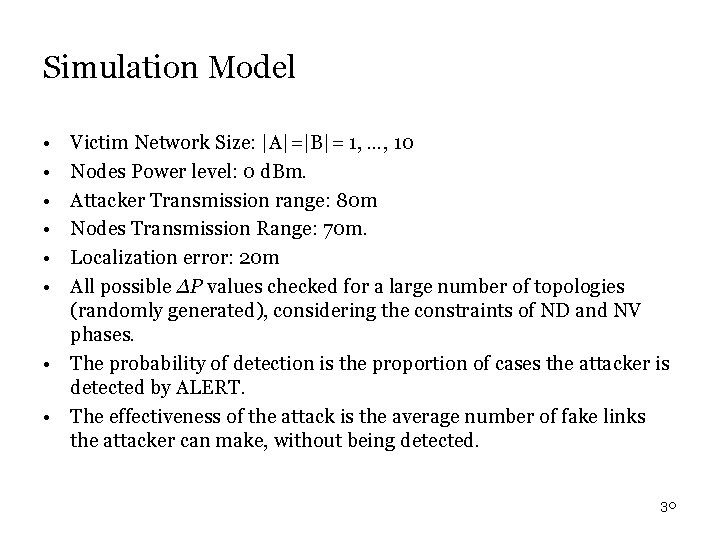
Simulation Model • • • Victim Network Size: |A|=|B|= 1, …, 10 Nodes Power level: 0 d. Bm. Attacker Transmission range: 80 m Nodes Transmission Range: 70 m. Localization error: 20 m All possible ∆P values checked for a large number of topologies (randomly generated), considering the constraints of ND and NV phases. • The probability of detection is the proportion of cases the attacker is detected by ALERT. • The effectiveness of the attack is the average number of fake links the attacker can make, without being detected. 30

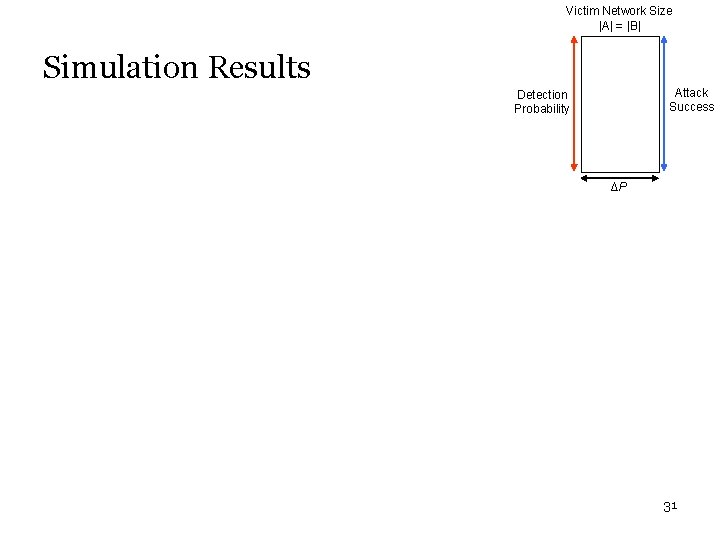
Victim Network Size |A| = |B| Simulation Results Attack Success Detection Probability ∆P 31

Agenda • • • Neighbor Discovery and Relay Attacks Currently Proposed Defense Methods Our System Model A Low-Cost Method to Thwart Relay Attacks Analysis and Simulation Results Conclusion 32

Conclusion and On-Going Work • We proposed a low-cost secure neighbor discovery protocol for wireless sensor networks. • Our protocol is based on basic principles of wireless channel and geometry. • We are implementing our protocol on real sensors to check its effectiveness in real situations. • Challenges are calibration of receivers to reduce the “Symmetry Error” and tuning the path loss model to have more precise distance measurement. 33
![References BC 93 Stefan Brands and David Chaum Distancebounding protocols In Theory and Application References [BC 93] Stefan Brands and David Chaum. Distance-bounding protocols. In Theory and Application](https://slidetodoc.com/presentation_image/4e571ae833988f22b0e684f3dd5f5ef8/image-34.jpg)
References [BC 93] Stefan Brands and David Chaum. Distance-bounding protocols. In Theory and Application of Cryptographic Techniques, 1993. [BDV 05] Levente Buttyán, László Dóra, István Vajda. Statistical wormhole detection in sensor networks. Lecture Notes in Computer Science, 2005. [HE 04] Lingxuan Hu and David Evans. Using directional antennas to prevent wormhole attacks. In NDSS, 2004. [HK 05] Gerhard P. Hancke and Markus G. Kuhn. An RFID distance bounding protocol. In SECURECOMM 2005. [HPJ 03] Y. -C. Hu, A. Perrig, and D. B. Johnson. Packet leashes: a defense against wormhole attacks in wireless networks. In INFOCOM 2003. [MGD 07] R. Maheshwari, J. Gao, and S. R. Das. Detecting wormhole attacks in wireless networks using connectivity information. In INFOCOM 2007. [PPS+07] Panos Papadimitratos, Marcin Poturalski, Patrick Schaller, Pascal lafourcade, David Basin, Srdjan Capkun, and Jean-Pierre Hubaux. Secure neighborhood discovery: A fundamental element for mobile ad hoc networking. Accepted in IEEE Communication Magazine, 2007. [SRB 01] Chris Savarese, Jan M. Rabaey, and Jan Beutel. Locationing in distributed adhoc wireless sensor networks. In ICASSP 2001. 34