A longest prefix first search tree for IP

- Slides: 32

A longest prefix first search tree for IP lookup Authors: Lih-Chyau Wuu, Tzong-Jye Liu, Kuo-Ming Chen Presenter: Chen-Yu Chung Date: 2008/09/24 Publisher/Conf. : Communications, 2005. ICC 2005 IEEE International Conference on

Outline o o o o Introduction The node struction LPFST construction IP lookup in LPFST updating operation Multiple LPFSTs construction Performance Conclusion

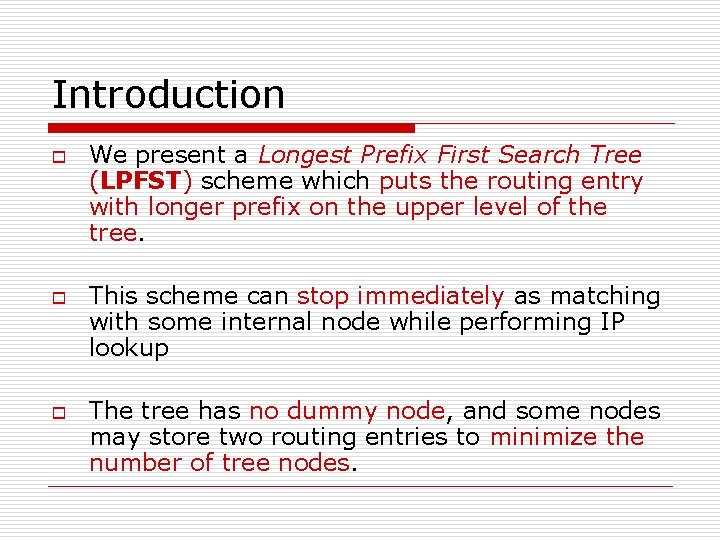
Introduction o o o We present a Longest Prefix First Search Tree (LPFST) scheme which puts the routing entry with longer prefix on the upper level of the tree. This scheme can stop immediately as matching with some internal node while performing IP lookup The tree has no dummy node, and some nodes may store two routing entries to minimize the number of tree nodes.

Outline o o o o Introduction The node struction LPFST construction IP lookup in LPFST updating operation Multiple LPFSTs construction Performance Conclusion

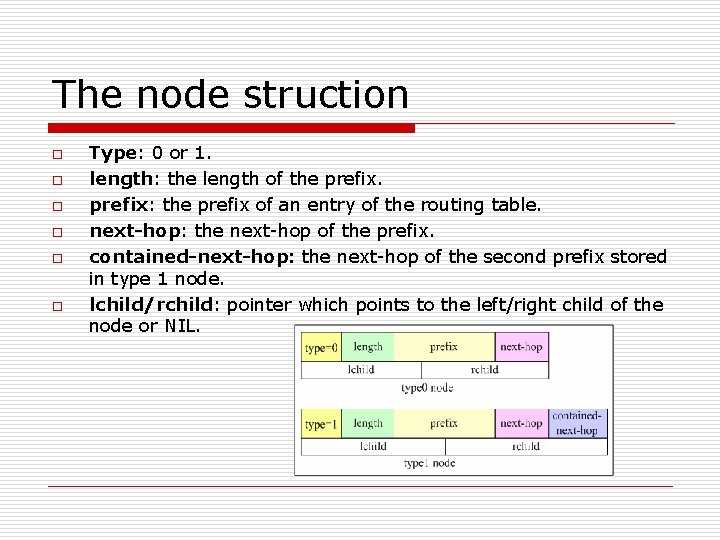
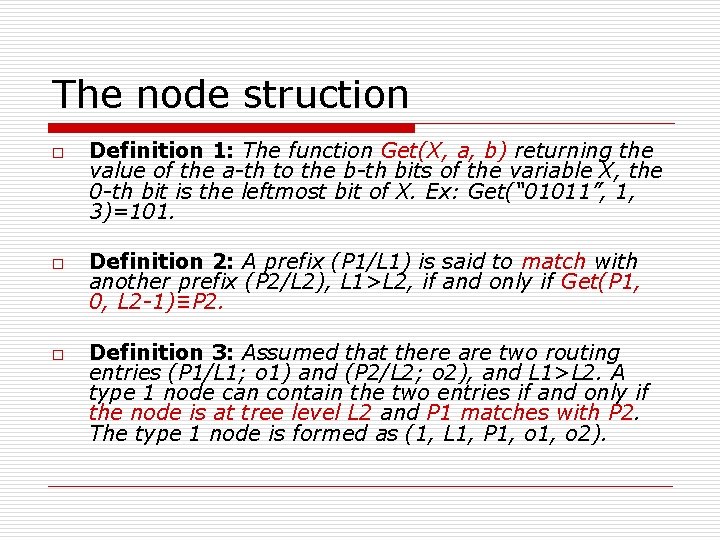
The node struction o o o Type: 0 or 1. length: the length of the prefix: the prefix of an entry of the routing table. next-hop: the next-hop of the prefix. contained-next-hop: the next-hop of the second prefix stored in type 1 node. lchild/rchild: pointer which points to the left/right child of the node or NIL.

The node struction o o o Definition 1: The function Get(X, a, b) returning the value of the a-th to the b-th bits of the variable X, the 0 -th bit is the leftmost bit of X. Ex: Get(“ 01011”, 1, 3)=101. Definition 2: A prefix (P 1/L 1) is said to match with another prefix (P 2/L 2), L 1>L 2, if and only if Get(P 1, 0, L 2 -1)≡P 2. Definition 3: Assumed that there are two routing entries (P 1/L 1; o 1) and (P 2/L 2; o 2), and L 1>L 2. A type 1 node can contain the two entries if and only if the node is at tree level L 2 and P 1 matches with P 2. The type 1 node is formed as (1, L 1, P 1, o 2).

Outline o o o o Introduction The node struction LPFST construction IP lookup in LPFST updating operation Multiple LPFSTs construction Performance Conclusion

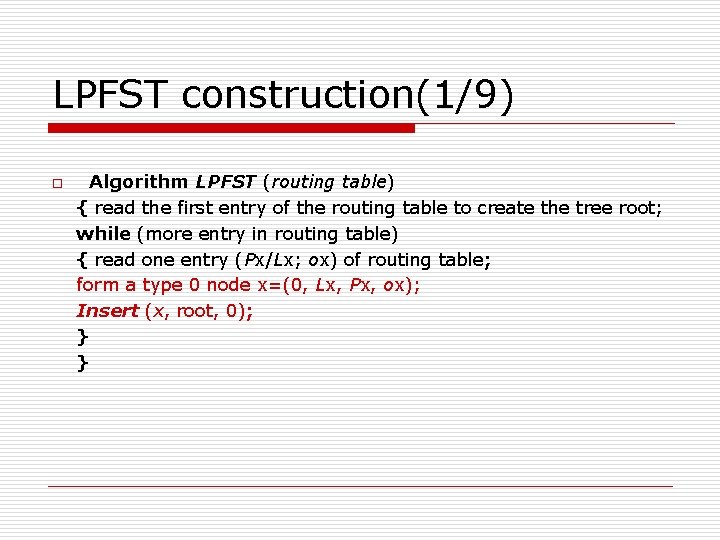
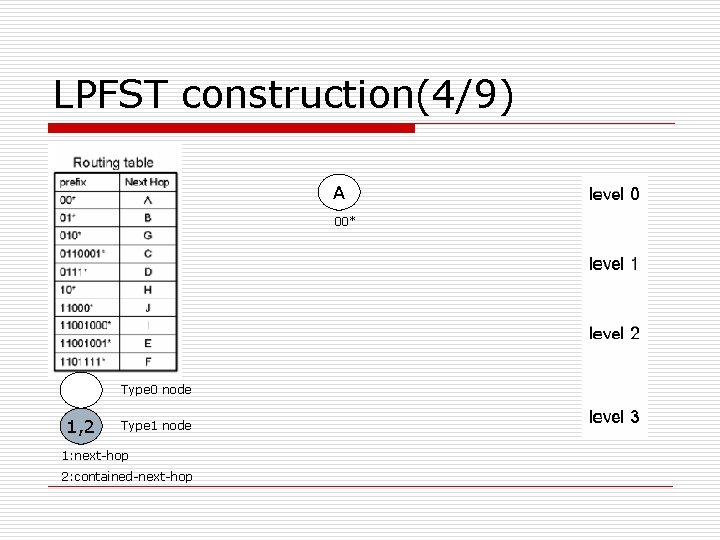
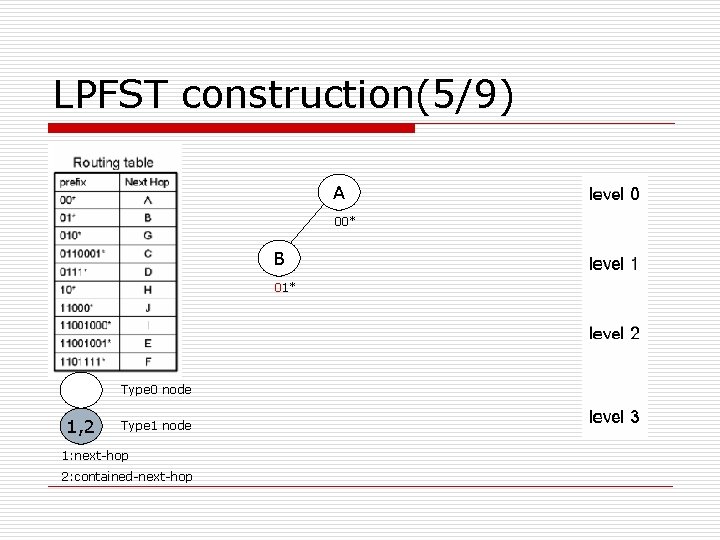
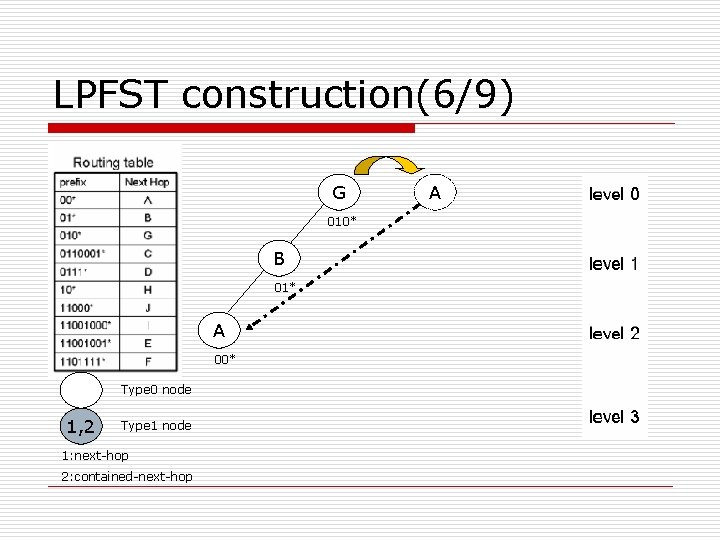
LPFST construction(1/9) o Algorithm LPFST (routing table) { read the first entry of the routing table to create the tree root; while (more entry in routing table) { read one entry (Px/Lx; ox) of routing table; form a type 0 node x=(0, Lx, Px, ox); Insert (x, root, 0); } }

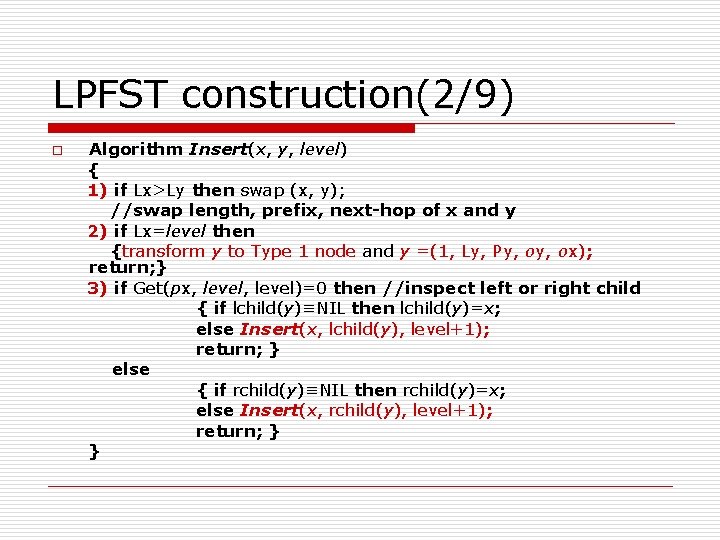
LPFST construction(2/9) o Algorithm Insert(x, y, level) { 1) if Lx>Ly then swap (x, y); //swap length, prefix, next-hop of x and y 2) if Lx=level then {transform y to Type 1 node and y =(1, Ly, Py, ox); return; } 3) if Get(px, level)=0 then //inspect left or right child { if lchild(y)≡NIL then lchild(y)=x; else Insert(x, lchild(y), level+1); return; } else { if rchild(y)≡NIL then rchild(y)=x; else Insert(x, rchild(y), level+1); return; } }

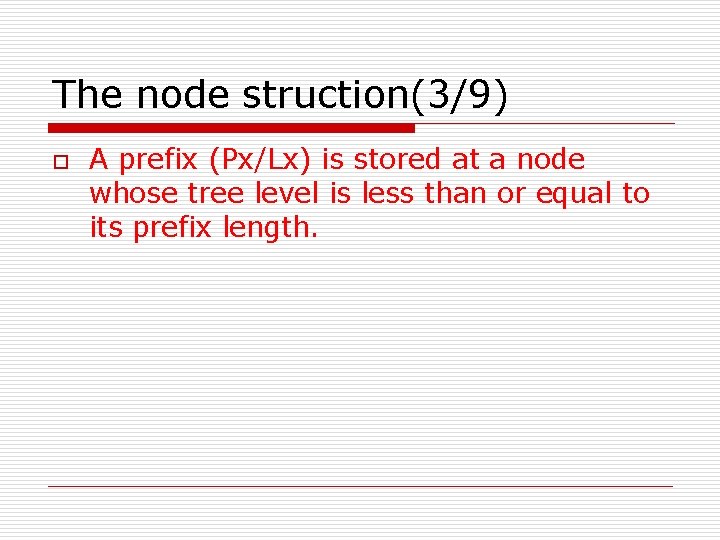
The node struction(3/9) o A prefix (Px/Lx) is stored at a node whose tree level is less than or equal to its prefix length.

LPFST construction(4/9) A 00* Type 0 node 1, 2 Type 1 node 1: next-hop 2: contained-next-hop

LPFST construction(5/9) A 00* B 01* Type 0 node 1, 2 Type 1 node 1: next-hop 2: contained-next-hop

LPFST construction(6/9) G 010* B 01* A 00* Type 0 node 1, 2 Type 1 node 1: next-hop 2: contained-next-hop A

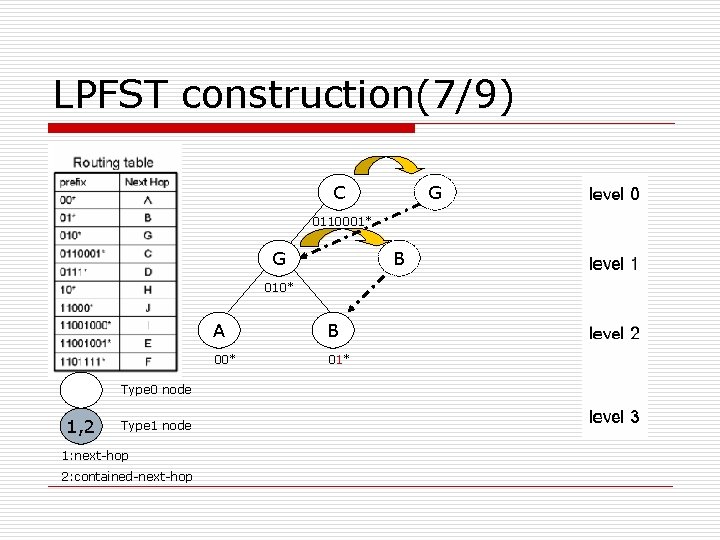
LPFST construction(7/9) C G 0110001* G B 010* Type 0 node 1, 2 Type 1 node 1: next-hop 2: contained-next-hop A B 00* 01*

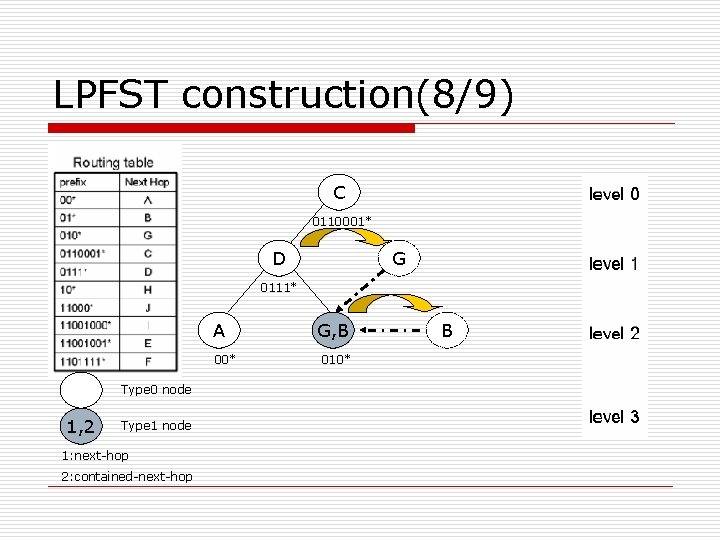
LPFST construction(8/9) C 0110001* D G 0111* A 00* Type 0 node 1, 2 Type 1 node 1: next-hop 2: contained-next-hop G, B 010* B

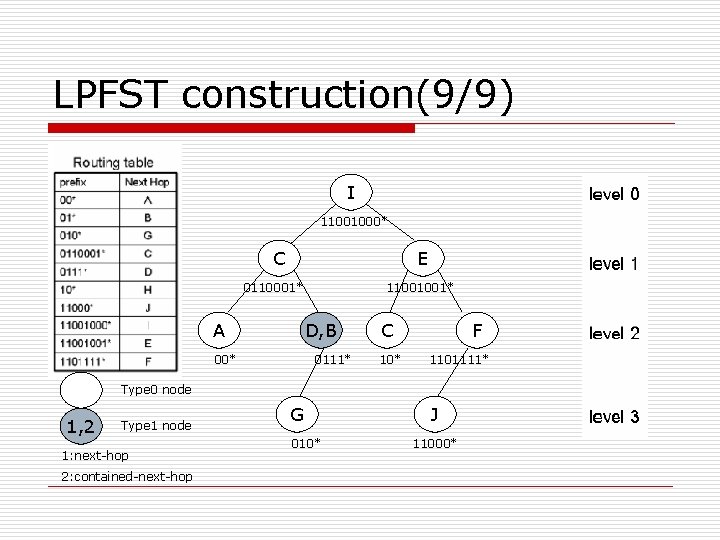
LPFST construction(9/9) I 11001000* C E 0110001* A 11001001* D, B 00* 0111* C 10* F 1101111* Type 0 node 1, 2 Type 1 node 1: next-hop 2: contained-next-hop G 010* J 11000*

Outline o o o o Introduction The node struction LPFST construction IP lookup in LPFST updating operation Multiple LPFSTs construction Performance Conclusion

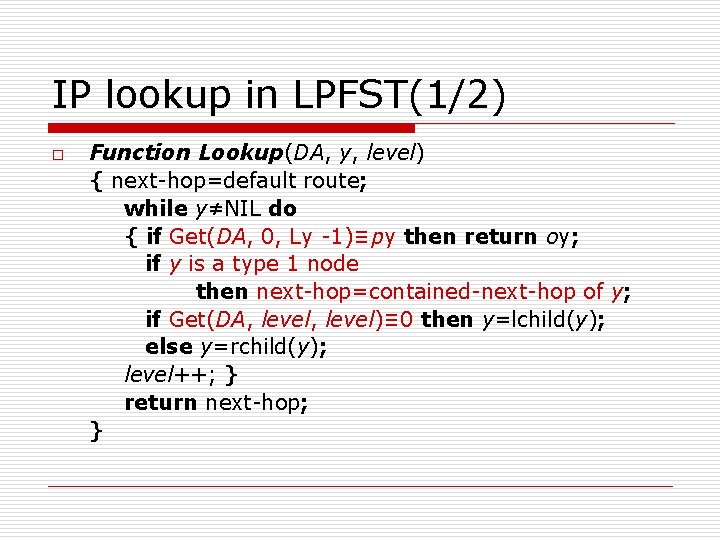
IP lookup in LPFST(1/2) o Function Lookup(DA, y, level) { next-hop=default route; while y≠NIL do { if Get(DA, 0, Ly -1)≡py then return oy; if y is a type 1 node then next-hop=contained-next-hop of y; if Get(DA, level)≡ 0 then y=lchild(y); else y=rchild(y); level++; } return next-hop; }

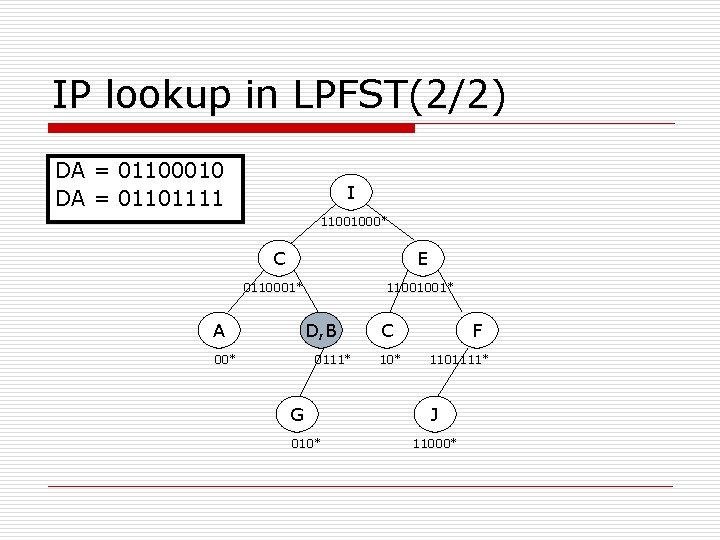
IP lookup in LPFST(2/2) DA = 01100010 DA = 01101111 I 11001000* C E 0110001* A 11001001* D, B 00* 0111* G 010* C 10* F 1101111* J 11000*

Outline o o o o Introduction The node struction LPFST construction IP lookup in LPFST updating operation Multiple LPFSTs construction Performance Conclusion

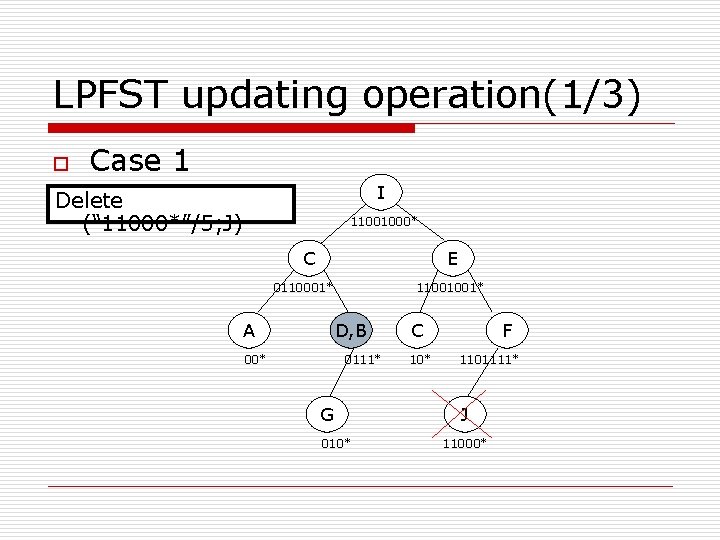
LPFST updating operation(1/3) o Case 1 I Delete (“ 11000*”/5; J) 11001000* C E 0110001* A 11001001* D, B 00* 0111* G 010* C 10* F 1101111* J 11000*

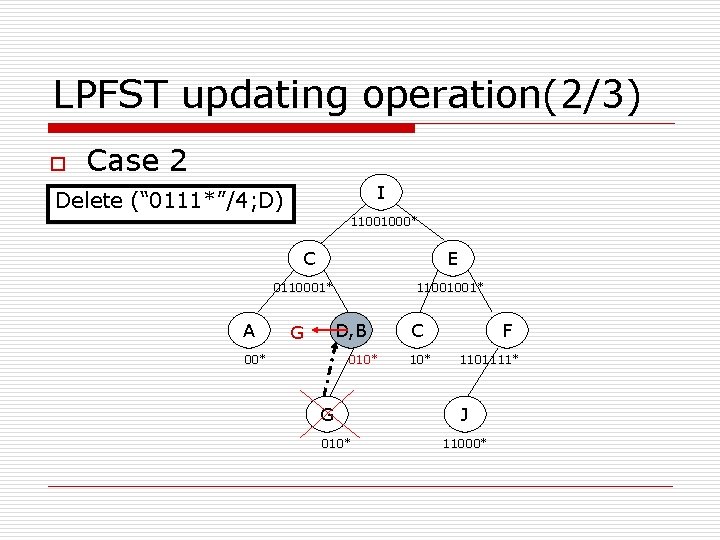
LPFST updating operation(2/3) o Case 2 I Delete (“ 0111*”/4; D) 11001000* C E 0110001* A 11001001* D, B G 00* 010* G 010* C 10* F 1101111* J 11000*

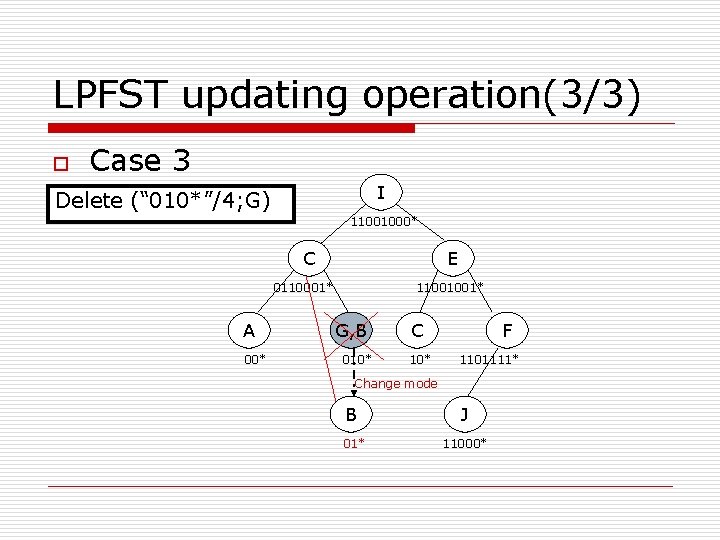
LPFST updating operation(3/3) o Case 3 I Delete (“ 010*”/4; G) 11001000* C E 0110001* A 00* 11001001* G, B 010* C 10* F 1101111* Change mode B J 01* 11000*

Outline o o o o Introduction The node struction LPFST construction IP lookup in LPFST updating operation Multiple LPFSTs construction Performance Conclusion

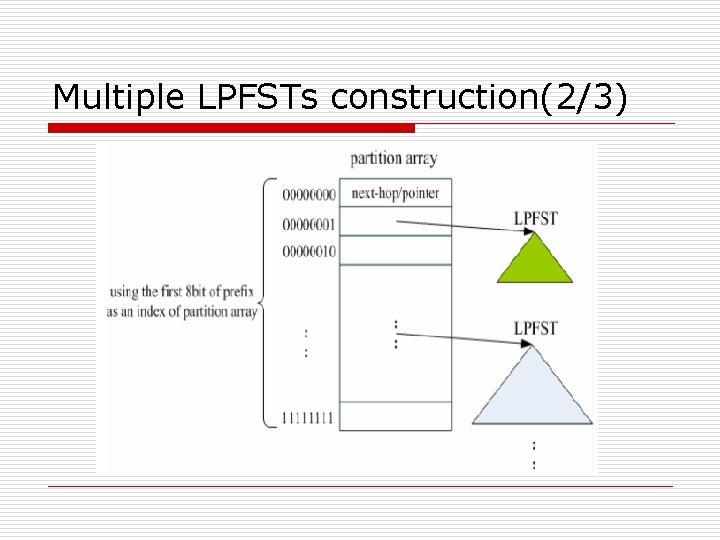
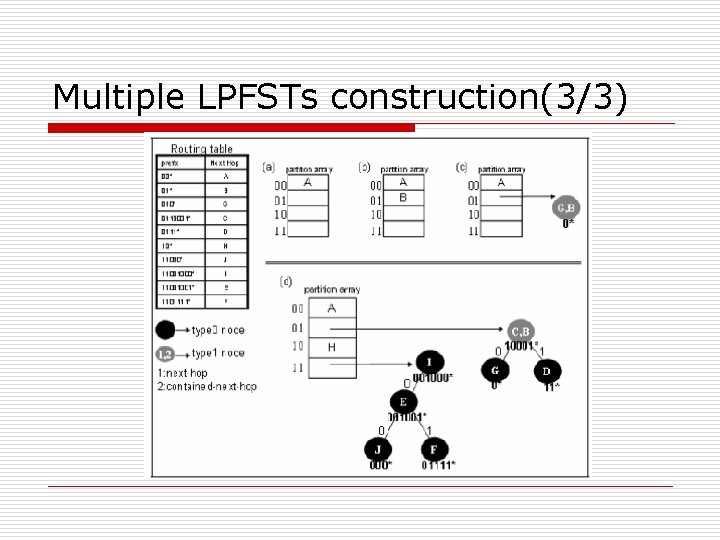
Multiple LPFSTs construction(1/3) o In Internet, there is no routing entry with prefix length less than eight. The height of LPFST can be lowered by partitioning it into several smaller LPFSTs, and the improved scheme is called as Partition Longest Prefix First Search Tree (PLPFST).

Multiple LPFSTs construction(2/3)

Multiple LPFSTs construction(3/3)

Outline o o o o Introduction The node struction LPFST construction IP lookup in LPFST updating operation Multiple LPFSTs construction Performance Conclusion

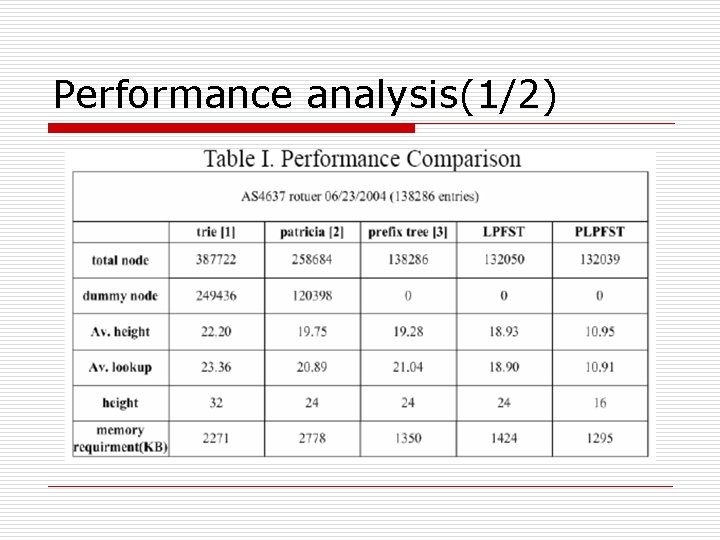
Performance analysis(1/2)

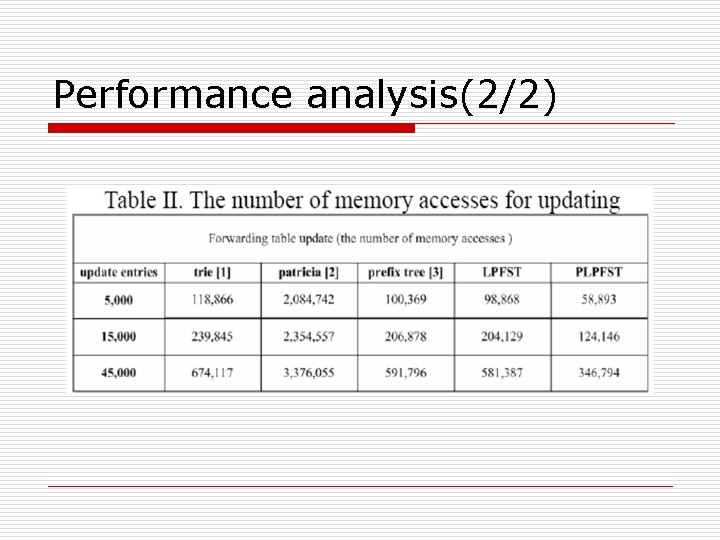
Performance analysis(2/2)

Outline o o o o Introduction The node struction LPFST construction IP lookup in LPFST updating operation Multiple LPFSTs construction Performance Conclusion

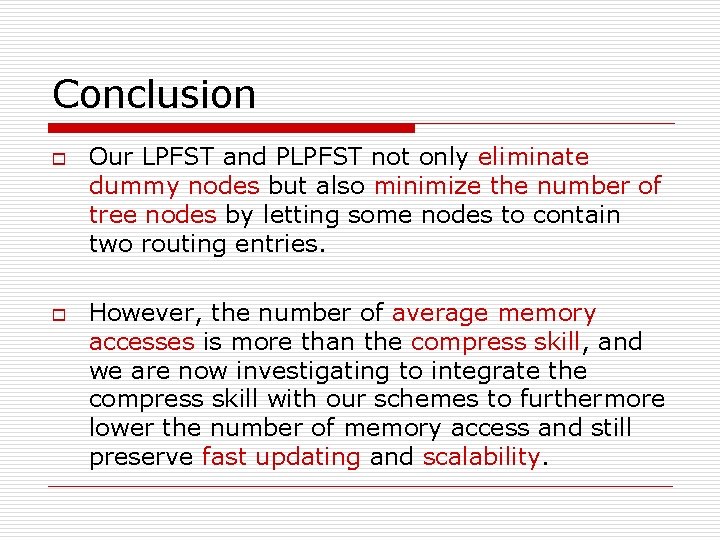
Conclusion o o Our LPFST and PLPFST not only eliminate dummy nodes but also minimize the number of tree nodes by letting some nodes to contain two routing entries. However, the number of average memory accesses is more than the compress skill, and we are now investigating to integrate the compress skill with our schemes to furthermore lower the number of memory access and still preserve fast updating and scalability.