A LearningBased Approach to Reactive Security Ben Rubinstein

A Learning-Based Approach to * Reactive Security Ben Rubinstein Microsoft Research Silicon Valley With: Adam Barth 1, Mukund Sundararajan 2, John Mitchell 3, Dawn Song 1, Peter Bartlett 1 1 UC * Appeared Berkeley 2 Google 3 Stanford at Financial Crypto. & Data Security 2010

Proactive vs. Reactive Security What's important is to understand the delineation between what’s considered “acceptable” and “unacceptable” spending. The goal is to prevent spending on reactive security “firefighting”. – John N. Stewart, VP (CSO), Cisco Systems • Conventional wisdom for CISOs – Adopt forward-looking, proactive, approach to managing security risks – Reactive security is akin to myopic bug chasing Reactive Security TRUST Conference F'10 2

Strategic Reactive Security • Good reactive security – Should be strategic and not “firefighting” – Under certain conditions keeps up with or beats proactive approaches – Machine Learning & Economics can help Reactive Security TRUST Conference F'10 3

Focus on Truly Adversarial Attacker • No probabilistic assumptions on attacker • Allow attacker to be omniscient • Consider reactive defender with limited knowledge of – System vulnerabilities – Attacker’s incentives – Attacker’s rationality Reactive Security TRUST Conference F'10 4

Focus on Incentives • We model attacker cost and payoff, combined as – additive profit; or multiplicative ROA An effective defense need not be perfect–but it should reduce attacker’s utility relative to attacking other systems. Reactive Security TRUST Conference F'10 5

Results in a Nutshell • If… – Security budget is fungible – Attack costs linear in defense allocation – No catastrophic attacks to defender • Attacker’s utility against reactive defense approaches utility under fixed proactive • In many cases reactive is much better Reactive Security TRUST Conference F'10 6
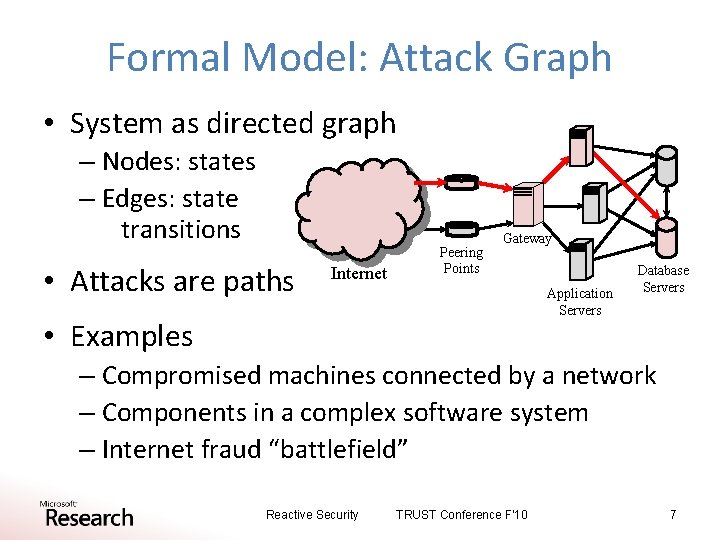
Formal Model: Attack Graph • System as directed graph – Nodes: states – Edges: state transitions • Attacks are paths Internet Peering Points Gateway Application Servers • Examples Database Servers – Compromised machines connected by a network – Components in a complex software system – Internet fraud “battlefield” Reactive Security TRUST Conference F'10 7
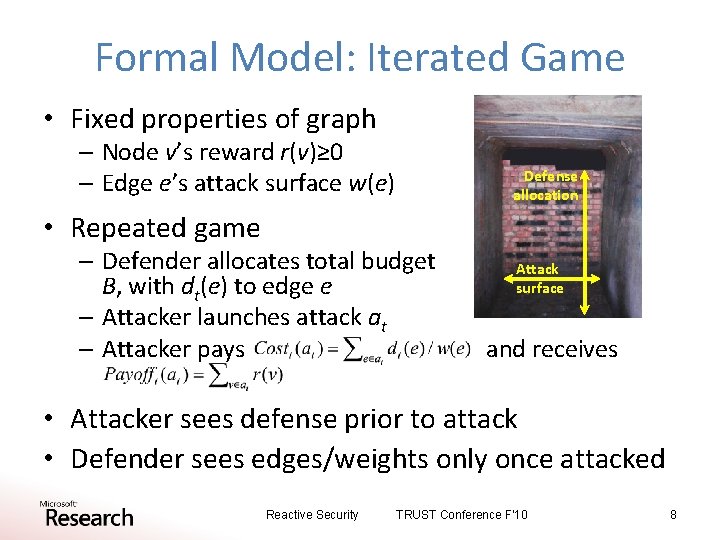
Formal Model: Iterated Game • Fixed properties of graph – Node v’s reward r(v)≥ 0 – Edge e’s attack surface w(e) Defense allocation • Repeated game – Defender allocates total budget B, with dt(e) to edge e – Attacker launches attack at – Attacker pays Attack surface and receives • Attacker sees defense prior to attack • Defender sees edges/weights only once attacked Reactive Security TRUST Conference F'10 8

Proactive Defender(s) • Pro’s of analysis: includes defenders who – Have perfect knowledge of the entire graph – Have perfect knowledge of the attacks – Play rationally given in/complete information • Con’s of analysis – We (mostly) assume proactive plays fixed strategy Reactive Security TRUST Conference F'10 9

Strategic Reactive Defender All edges initially unseen Observe attacked edges Count #times edge attacked Multiplicative update Re-normalize in [0, 1]; allocate this times budget B • Based on Multiplicative Weights algorithm of Online Learning Theory • Unseen edges get no allocation • Budget is increased on attacked edges • Allocation due to “the past” is exponentially down-weighed since 0<β<1 Reactive Security TRUST Conference F'10 10
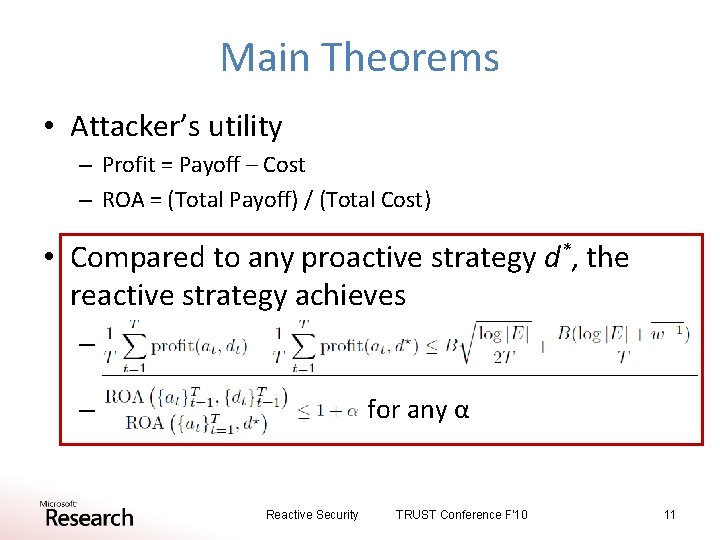
Main Theorems • Attacker’s utility – Profit = Payoff – Cost – ROA = (Total Payoff) / (Total Cost) • Compared to any proactive strategy d*, the reactive strategy achieves – for any α – Reactive Security TRUST Conference F'10 11
Robustness & Extensions • Robustness – Proactive not robust to uncertainty in attacker’s utility; reactive is!! – Reactive can do much better under uncertain payoffs • Extensions – Hypergraphs / Datalog – Multiple attackers – Adaptive proactive defenders Reactive Security TRUST Conference F'10 12

Conclusions • Incentives-based, fully-adversarial risk model • Learning-based defender performs close to or better than fixed proactive defenders • Recommendations for CISOs – Employ monitoring tools to help focus on real attacks – Make security organization more agile – Avoid overreacting to the most recent attack; consider past attacks (down-weighed exponentially) Reactive Security TRUST Conference F'10 13
Thanks!!

Model Case Studies • Perimeter defense – Non-zero reward at one vertex – Rational attacker will select minimum-cost path from start to reward – Rational defense is to maximize minimum-cost path: allocate budget to minimum-cut Reactive Security TRUST Conference F'10 15
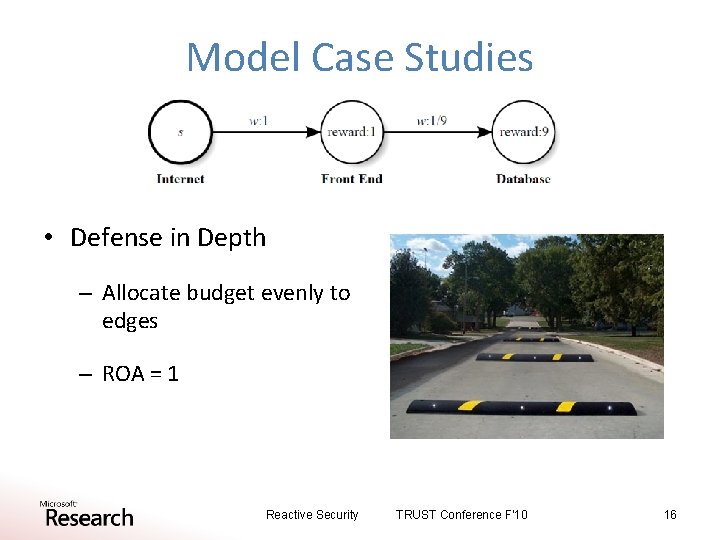
Model Case Studies • Defense in Depth – Allocate budget evenly to edges – ROA = 1 Reactive Security TRUST Conference F'10 16
Proof Sketch • Profit when edges are known – Simple reduction to standard regret bound of Freund. Schapire for Multiplicative Update alg • Profit under hidden edges – Simulation argument shows that a slight modification to Mult. Up produces same allocations as Mult. Up on observed graph – Care taken with – Algorithms’ profits bounded by • ROA under hidden edges – Ratio of two numbers is small if numbers are large & similar. Need: Reactive Security TRUST Conference F'10 17
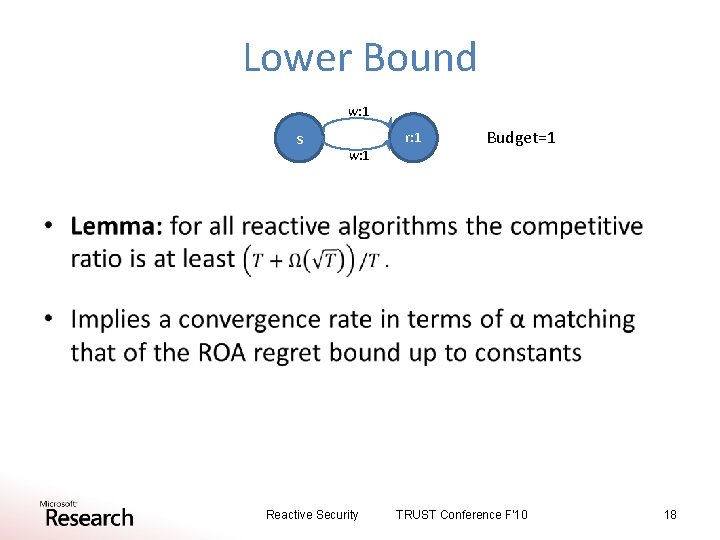
Lower Bound w: 1 s r: 1 w: 1 Budget=1 • Reactive Security TRUST Conference F'10 18
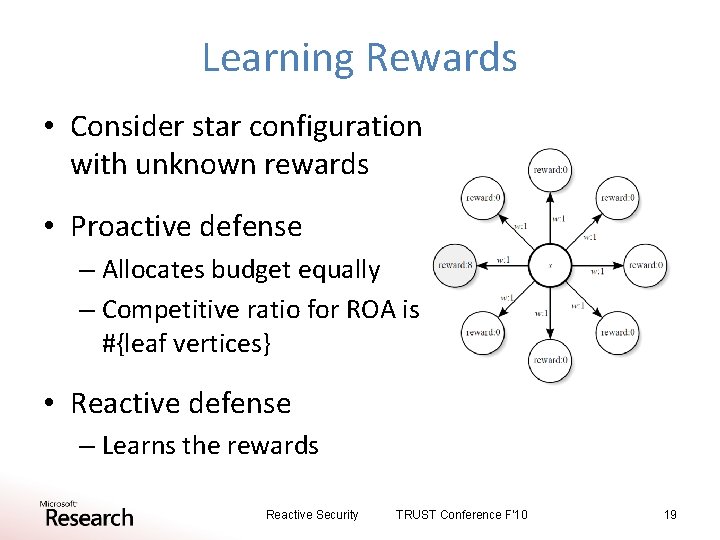
Learning Rewards • Consider star configuration with unknown rewards • Proactive defense – Allocates budget equally – Competitive ratio for ROA is #{leaf vertices} • Reactive defense – Learns the rewards Reactive Security TRUST Conference F'10 19

Robustness to Objective • Given defense budget of 9 • Proactive defender assuming profit-seeking – Allocates 9 to right-hand edge: 1 profit for all attacks – ROA for left-hand edge is infinite!! • Reactive defender’s play is invariant Reactive Security TRUST Conference F'10 20
- Slides: 20