A Java implemented key collision attack on the





- Slides: 15

A Java implemented key collision attack on the Data Encryption Standard (DES) John Loughran, Tom Dowling NUI, Maynooth, Co. Kildare, Ireland PPPJ ‘ 03

Java Cryptography • Used Java Cryptographic Extension (JCE) based on Java Cryptographic Architecture (JCA) • • Contains java. security and javax. crypto packages Used Austrian IAIK version of the JCE • Contains classes which simplify encryption process • • E. g. factory methods to return instances of a class as: Cipher crypt. Object = Cipher. get. Instance(“DES”); 17 th June 2003 Java implemented DES attack 2

Data Encryption Standard (DES) • DES is a symmetric block cipher • Same key for encryption and decryption • Works on blocks of fixed length • DES has 256 different keys • = 70 000 000 000 17 th June 2003 Java implemented DES attack 3

Birthday Paradox • Brute force attack: Try all 256 possible keys • 70 000 000 • Birthday attack: Reduces complexity of attack to 228 i. e. sqrt(256) ~ 200 000 • • For a set with n (256 for DES) possible keys In two subsets of randomly generated keys of size sqrt(n) (228 for DES) • • 17 th June 2003 Probability of a match is 0. 63 [Stallings, 2003] Java implemented DES attack 4

The Biham Algorithm • A known plaintext header is used E. g. Postcript file header: “%!PS-Ado” This plaintext header is encrypted using 228 different random DES keys Resulting (ciphertext, key) pairs stored in a table Compare 228 incoming ciphertexts of the same header whose keys are unknown with table When a match is found the corresponding key is returned The key can be used to decrypt the message or even substitute a favourable message • • • 17 th June 2003 Java implemented DES attack 5

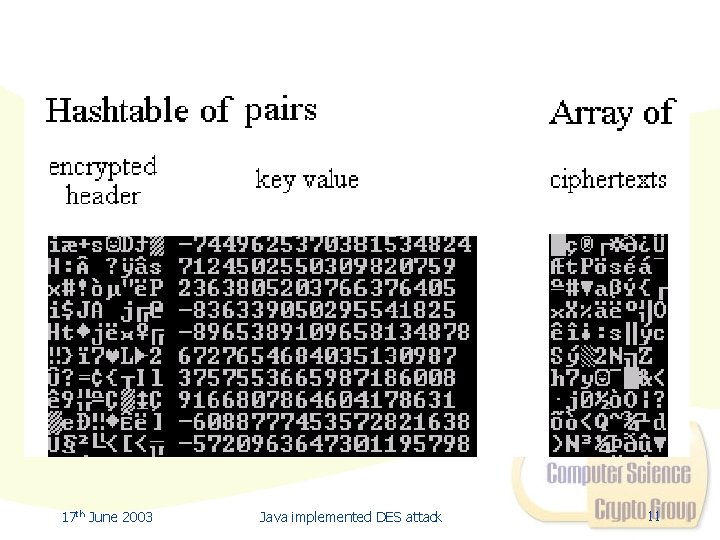
Implementing the Attack • Used the JCE to generate the keys as: • Key. Generator key. Gen = Key. Generator. get. Instance(“DES”); • key. Gen. init(new Secure. Random()); • Key key = key. Gen. generate. Key(); • Stored (ciphertext, key) pairs in Hashtables • Searching complexity of O(1) 17 th June 2003 Java implemented DES attack 6

Memory Considerations • Unable to keep a Hashtable with 228 pairs in memory • • • Even using a Pentium 4, 2 GHz, 1 GB RAM, 60 GB HD With virtual memory set to 4 GB Despite increasing Java heap size to max using switch at runtime: • 17 th June 2003 C: >java –Xms 1640 m –Xmx 1640 m Crack. DES Java implemented DES attack 7

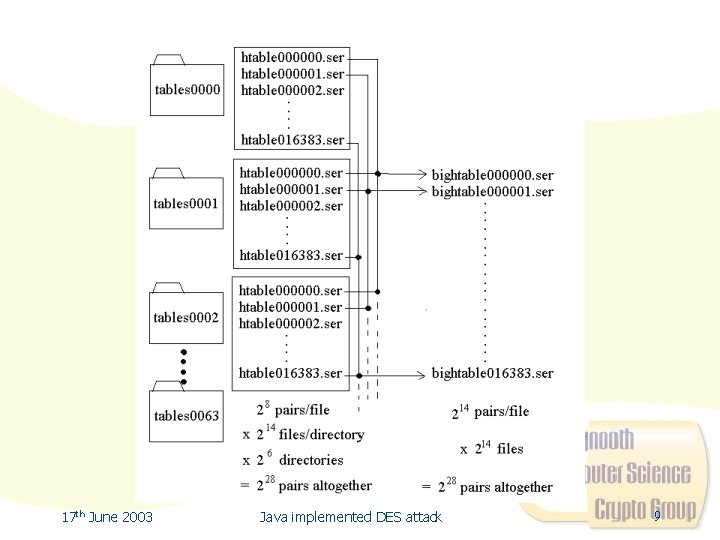
Multiple Hashtable Approach • 214 Hashtables each containing 214 (ciphertext, key) pairs were generated • During generations pairs were allocated to a particular Hashtable based on the mod 16394 of the hash. Code() of the ciphertext • Hashtables were finally stored on disk as files bightable 000000. ser to bightable 016383. ser after various merging operations 17 th June 2003 Java implemented DES attack 8

17 th June 2003 Java implemented DES attack 9

Finding a Key • Arrays of ciphertexts of the same plaintext header were generated to simulate incoming ciphertexts with unknown keys • Each ciphertext was examined as follows: • • • Its hash. Code() mod 16384 was obtained The corresponding Hashtable was read in and searched If a matching ciphertext was found the corresponding key was returned 17 th June 2003 Java implemented DES attack 10

17 th June 2003 Java implemented DES attack 11

Time Considerations • To speed up the search process the “incoming” ciphertexts were split up into arrays such that • • Each array contained ciphertexts whose hash. Code() mod 16384 were the same Thus only one Hashtable needs to be read in for each array • This reduced the estimated time needed to find a key from 6. 2 years to 2. 3 hours! 17 th June 2003 Java implemented DES attack 12

Space Optimisation • Storing only the key value as a Long object rather than a Key object reduced the space required for the Hashtables from an estimated 55 GB to 8 GB • This necessitates creating a Key object from the returned key value using Secret. Key methods from the JCE 17 th June 2003 Java implemented DES attack 13

Conclusions • Biham algorithm implemented successfully in Java • Use of JCE in cryptanalysis demonstrated • Space and time optimisations mean that DES can now be cracked in 2 hours on a single PC using Java • Possible future work on implementation of a parallel search using a distributed system 17 th June 2003 Java implemented DES attack 14

Website • This presentation and the full text of thesis including references and appendices can be downloaded from my website: • 17 th June 2003 http: //homepage. eircom. net/~johnloughran Java implemented DES attack 15