A High Throughput String Matching Architecture for Intrusion




- Slides: 13

A High Throughput String Matching Architecture for Intrusion Detection and Prevention Authors: Lin Tan and Timothy Sherwood Publisher: Proceedings of the 32 nd International Symposium on Computer Architecture (ISCA’ 05) Present: Chen-Rong Chang Date: March, 4, 2009 Department of Computer Science and Information Engineering National Cheng Kung University, Taiwan R. O. C. 1

Outline n n n Aho-Corasick algorithm Bit-level AC state machine String Matching Engine Support for Non-Interrupting Update Theoretical optimal partitioning Performance 2

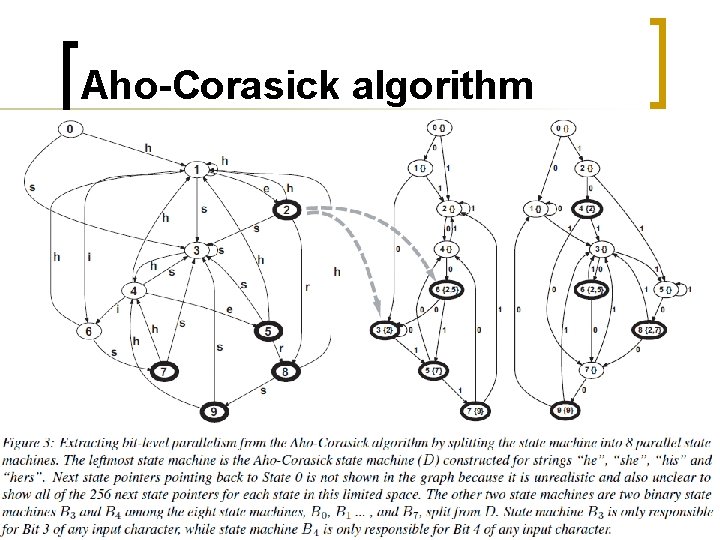
Aho-Corasick algorithm 3

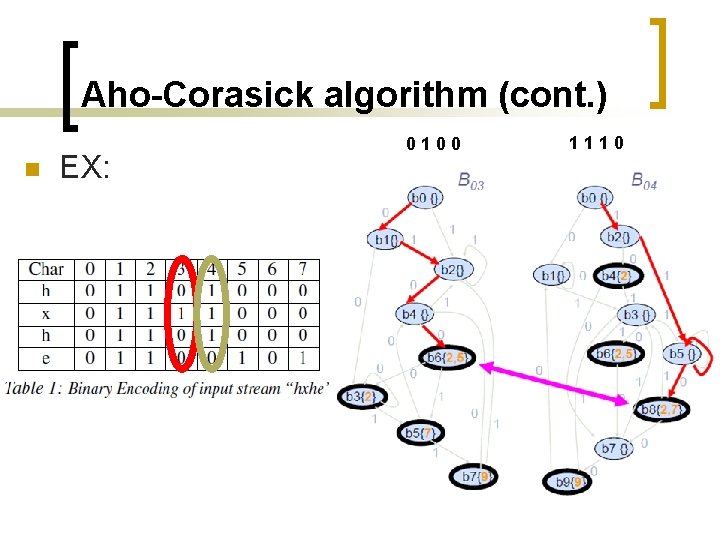
Aho-Corasick algorithm (cont. ) n EX: 0100 1110 4

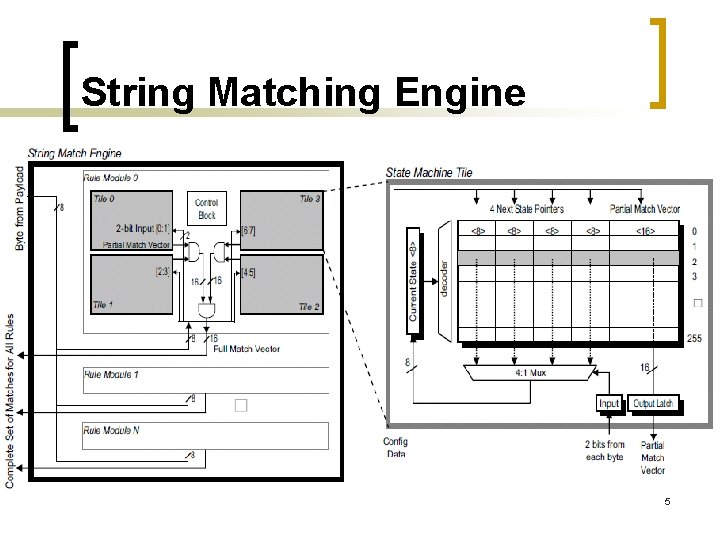
String Matching Engine 5

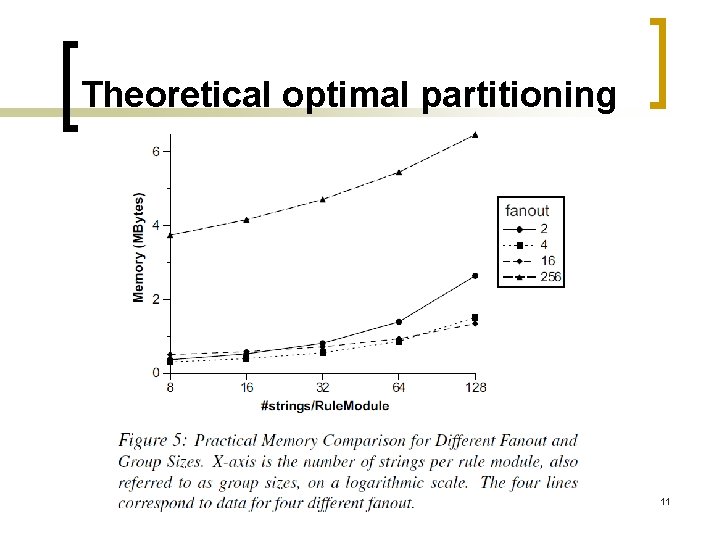
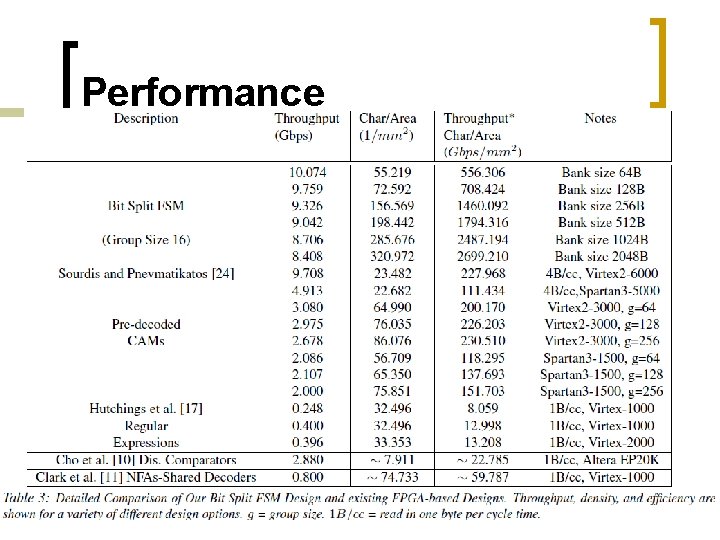
Partitioning the Rules n If we put 1, 000 strings into a big FSM and construct the bit ��. -split state machines, a partial match vector of more than 1, 000 bits. n The number of bits of partial match vector determine the maximum number of strings each tile can handle. n By analyzing the distribution of strings in Snort rule set, we find that generally 16 strings require approximately 256 states 6

Partitioning the Rules n A good solution is to sort all strings lexicographically and then divide them sequentially into groups so that all the common prefixes can share states and thus use less states in total. n While this is not the optimal solution, it beats the two alternatives, dividing by length and randomly. n Dividing by length would consume 21. 9% more states than the method we use, and the random grouping technique would use 12. 1% more states. 7

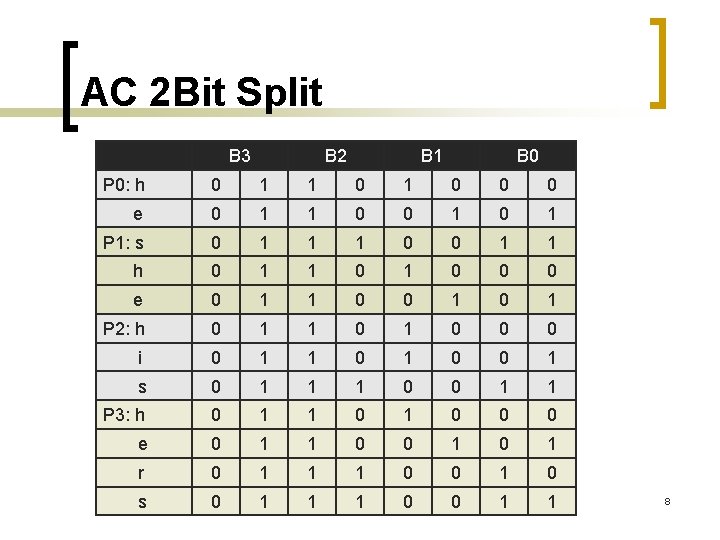
AC 2 Bit Split B 3 B 2 B 1 B 0 P 0: h 0 1 1 0 0 0 e 0 1 1 0 0 1 P 1: s 0 1 1 1 0 0 1 1 h 0 1 1 0 0 0 e 0 1 1 0 0 1 P 2: h 0 1 1 0 0 0 i 0 1 1 0 0 1 s 0 1 1 1 0 0 1 1 P 3: h 0 1 1 0 0 0 e 0 1 1 0 0 1 r 0 1 1 1 0 0 1 0 s 0 1 1 1 0 0 1 1 8

AC 2 Bit Split (cont. ) 0{} 01 11 11 11 2{} 10 01 0{} 10 10 1{} 10 11 3{0} 4{} 2{0} 10 01 6{0, 1} 4{0, 1, 2, 3} 10 10 5{2} 11 11 3{0, 1, 2} 01 11 10 01 B 3 11 B 2 7{3} 9

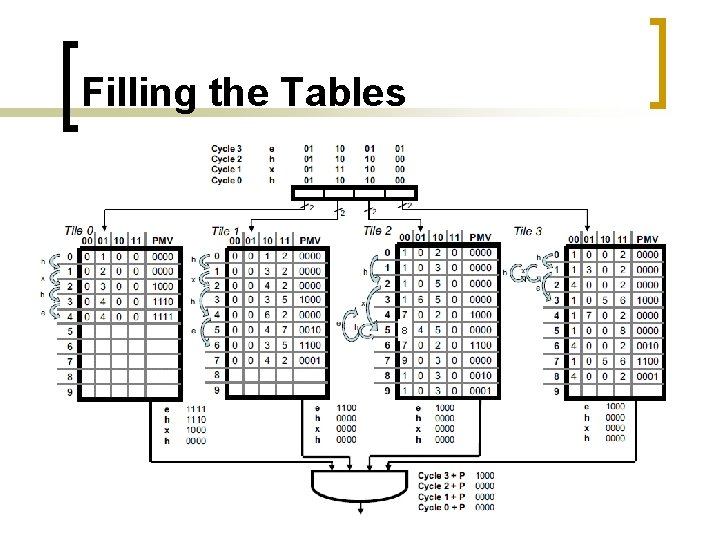
Filling the Tables 8 10

Theoretical optimal partitioning 11

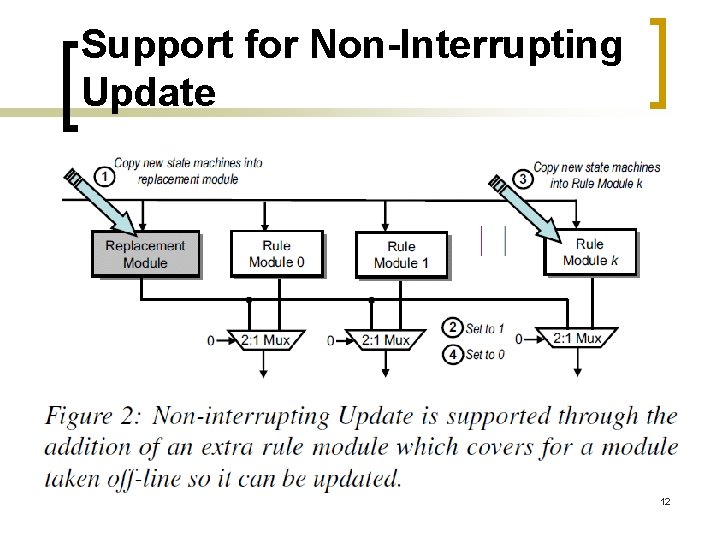
Support for Non-Interrupting Update 12

Performance 13