A Guide to Managing and Maintaining Your PC

















- Slides: 65

A+ Guide to Managing and Maintaining Your PC, 7 e Chapter 17 Networking Essentials

Objectives • Identify the 7 OSI layers and its different functions • Understand TCP/IP protocol and how it relates to OSI layers • Identify different hardware and application associated with OSI layers • Understand different important protocols used under TCP/IP A+ Guide to Managing and Maintaining Your PC, 7 e 2

The OSI Reference Model • Networks rely upon standards • Open Systems Interconnection (OSI) reference model – Fundamental network communications model • OSI model product of two standards organizations – International Organization for Standardization (ISO) – American National Standards Institute (ANSI) • OSI is theoretical, not specific hardware or software • OSI guidelines analogized to a grammar Hands-on Networking Fundamentals 3

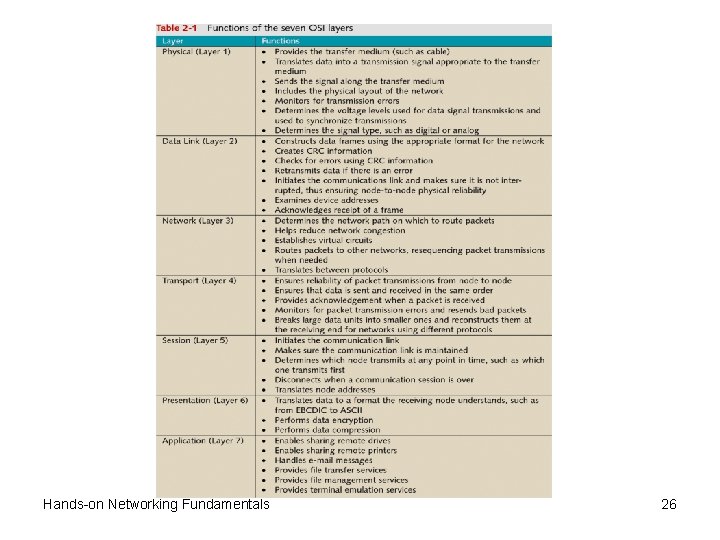
The OSI Reference Model (continued) • Accomplishments of the OSI model – – Enabling communications among LANs, MANs, WANs Standardizing network equipment Enabling backward compatibility to protect investments Enabling development of software and hardware with common interfaces – Making worldwide networks possible; e. g. , the Internet • OSI model consists of seven distinct layers – Physical, Data Link, Network, Transport, Session, Presentation, and Application Hands-on Networking Fundamentals 4

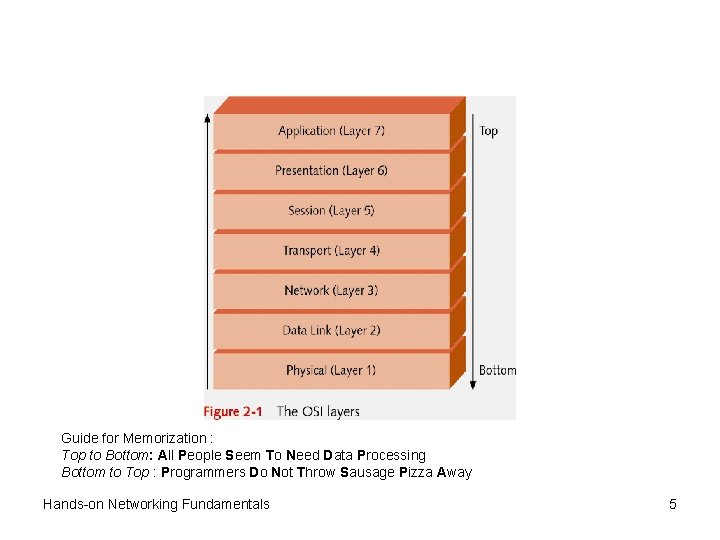
Guide for Memorization : Top to Bottom: All People Seem To Need Data Processing Bottom to Top : Programmers Do Not Throw Sausage Pizza Away Hands-on Networking Fundamentals 5

The OSI Reference Model (continued) • Set of layers in OSI model is called a stack • Layers called by actual name or placement in stack • Layers also divided into three groups – Bottom: handles physical communications – Middle: coordinates communication between nodes – Top: involves data presentation • Contact between two network devices – Communications traverse layered stack in each device – Each layer handles specific tasks – Each layer communicates with next layer using protocol Hands-on Networking Fundamentals 6

Physical Layer • Layer purpose: transmit and receive signals with data • Responsibilities of the Physical layer (Layer 1) – All data transfer mediums • wire cable, fiber optics, radio waves, and microwaves – – – Network connectors The network topology Signaling and encoding methods Data transmission devices Network interfaces Detection of signaling errors Hands-on Networking Fundamentals 7

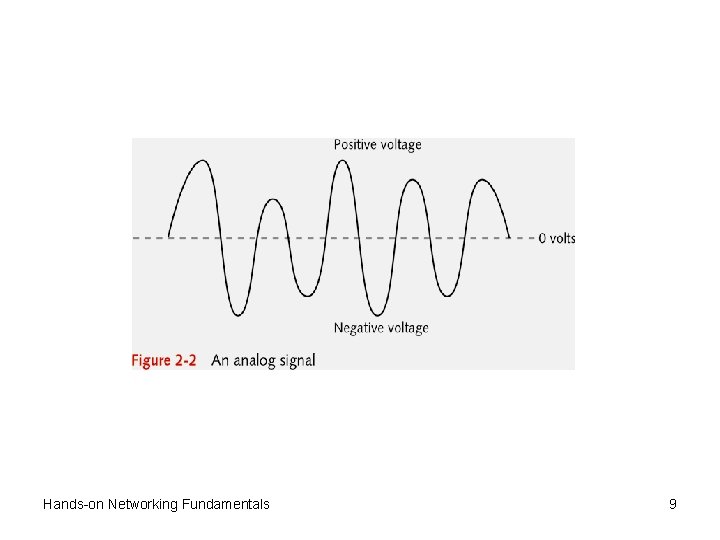
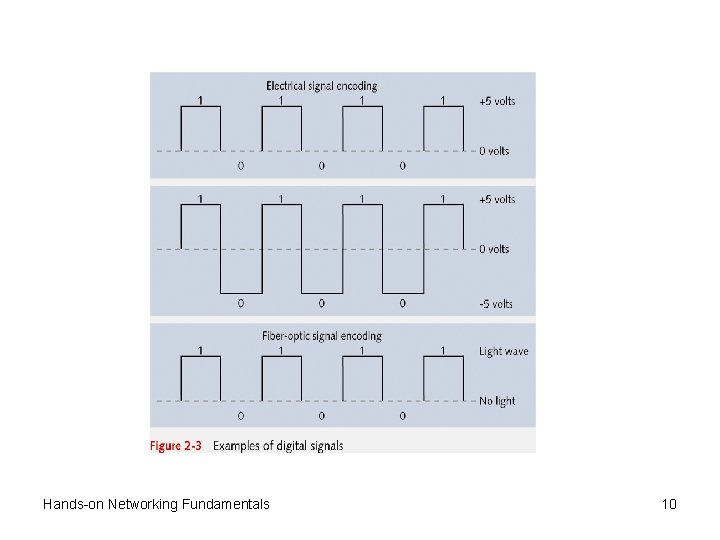
Physical Layer (continued) • Network signals are either analog or digital • Analog signal – Wave pattern with positive and negative voltages – Examples: ordinary telephone or radio signal – Used in WANs that employ analog modems • Digital signal generates binary 1 s or 0 s – Most common signaling method on LANs and highspeed WANs – Example 1: +5 volts produces 1, 0 volts produce 0 – Example 2: +5 volts produces 1, -5 volts produce 0 – Example 3 (Fiber-optics): presence of light is 1, else 0 Hands-on Networking Fundamentals 8

Hands-on Networking Fundamentals 9

Hands-on Networking Fundamentals 10

Physical Layer (continued) • Physical network problems affect physical layer – Example 1: broken cable – Example 2: electrical or magnetic interference • Electromagnetic interference (EMI) – Caused by magnetic force fields – Generated by certain electrical devices • Fans, electric motors, portable heaters, air-conditioners • Radio frequency interference (RFI) – Caused by electrical devices emitting radio waves • Radio and television stations, radio operators, cable TV – Problem when frequency matches network signal Hands-on Networking Fundamentals 11

Data Link Layer • Layer purpose: format bits into frames • Frame: discrete unit of information – Contains control and address information – Does not contain routing information • Steps required to activate data link – Two nodes establish physical connection – Data Link layers connected logically through protocols – Data Link layer decodes signal into individual frames • Cyclic redundancy check (CRC): monitor duplication – Calculates size of information fields in frame – Data Link layer at sender inserts value at end of frame – Receiving Data Link layer checks value in frame Hands-on Networking Fundamentals 12

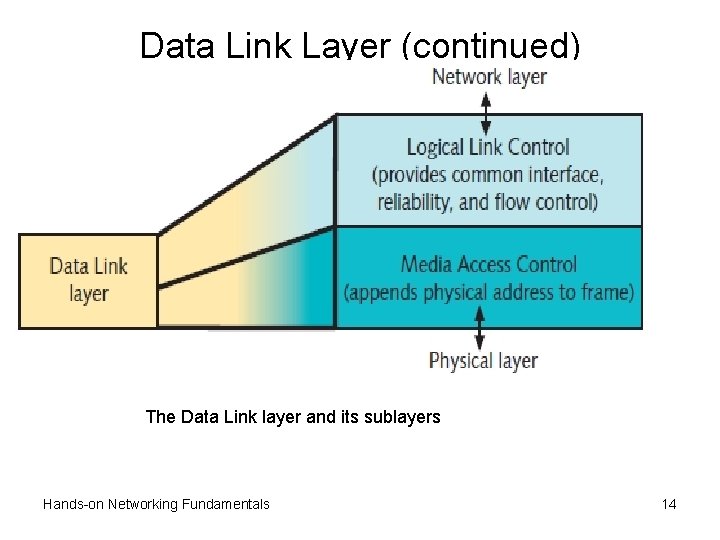
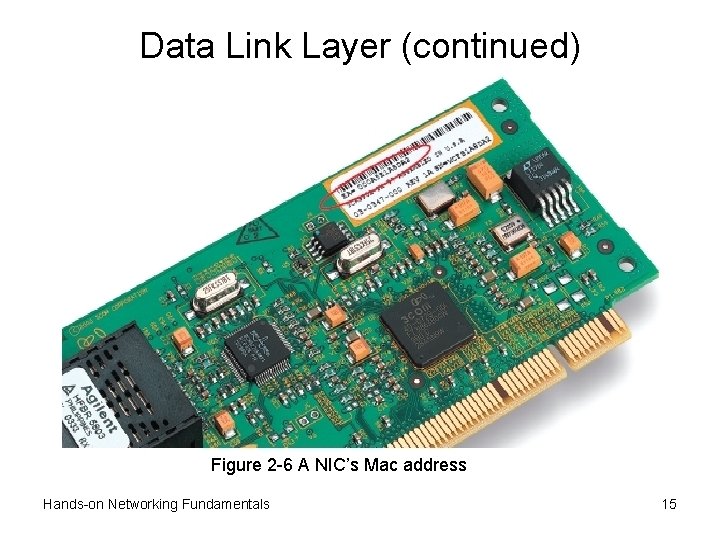
Data Link Layer (continued) • Logical link control sublayer (LLC) – Initiates communication link between two nodes – Guards against interruptions to link – Link to Network layer may be connection-oriented • Media access control sublayer (MAC) – Examines physical (device or MAC) address in frame – Frame discarded if address does not match workstation – Regulates communication sharing • MAC address burned into chip on network interface – Coded as a hexadecimal number; e. g. , 0004 AC 8428 DE • First half refers to vendor, second half unique to device Hands-on Networking Fundamentals 13

Data Link Layer (continued) The Data Link layer and its sublayers Hands-on Networking Fundamentals 14

Data Link Layer (continued) Figure 2 -6 A NIC’s Mac address Hands-on Networking Fundamentals 15

Network Layer • Layer purpose: control passage of packets on network – Physical routes: cable and wireless paths – Logical routes: software paths • Packet: discrete unit of information (like a frame) – Formatted for transmission as signal over network – Composed of data bits in fields of information – Corresponds to network information sent at Network layer of OSI model • Specific tasks of Network layer – Optimize physical and logical routes – Permit routers to move packets between networks Hands-on Networking Fundamentals 16

Network Layer (continued) • Discovery: process of information gathering – Obtain metrics about location of networks and nodes • Virtual circuits: logical communication paths – Send and receive data – Known only to Network layers between nodes – Benefit: manage parallel data paths • Extra duties using virtual circuits – – Checks (and corrects) packet sequence Addresses packets Resizes packets to match receiving network protocol Synchronizes flow of data between Network layers Hands-on Networking Fundamentals 17

Transport Layer • Layer purpose: reliable data transmission – Ensures data sent and received in same order – Receiving node sends acknowledgement ("ack") • Transport layer support of virtual circuits – Tracks unique identification value assigned to circuit • Value called a port or socket • Port assigned by Session layer – Establishes level of packet checking • Five reliability measures used by protocols • Transport layer mediates between different protocols Hands-on Networking Fundamentals 18

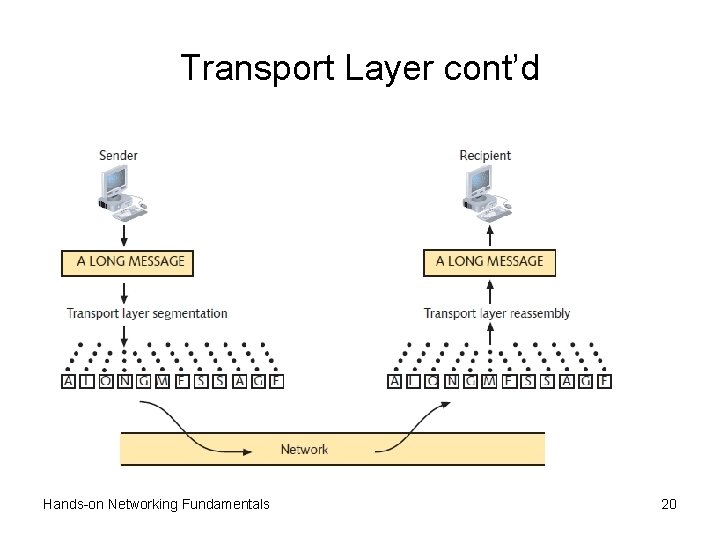
Transport Layer cont’d • MTU (maximum transmission unit) – Largest data unit network will carry – Ethernet default: 1500 bytes – Discovery routine used to determine MTU • Reassembly – Process of reconstructing segmented data units • Sequencing – Method of identifying segments belonging to the same group of subdivided data Hands-on Networking Fundamentals 19

Transport Layer cont’d Hands-on Networking Fundamentals 20

Session Layer • Multiple goals – – – Establish and maintain link between two nodes Provide for orderly transmission between nodes Determine how long node can transmit Determine how to recover from transmission errors Link unique address to each node (like a zip code) Hands-on Networking Fundamentals 21

Presentation Layer • Primary purpose: manages data formatting – Acts like a syntax checker – Ensures data is readable to receiving Presentation layer • Translates between distinct character codes – EBCDIC (Extended Binary Coded Decimal Interchange Code) • 8 -bit coding method for 256 -character set • Used mainly by IBM computers – ASCII (American Standard Code for Information Interchange) • 8 -bit character coding method for 128 characters • Used by workstations running Windows XP, Fedora, Linux Hands-on Networking Fundamentals 22

Presentation Layer (continued) • Two additional responsibilities – Encryption: scrambling data to foil unauthorized users • Example 1: account password encrypted on LAN • Example 2: credit card encrypted on a LAN • Encryption tool: Secure Sockets Layer (SSL) – Data compression: compact data to conserve space • Presentation layer at receiving node decompresses data Hands-on Networking Fundamentals 23

Application Layer • Services managed by Application layer – – File transfer, file management, remote access to files Remote access to printers Message handling for electronic mail Terminal emulation • Connecting workstations to network services – Link application into electronic mail – Providing database access over the network • Microsoft Windows redirector – Makes computer visible to another for network access – Example: access shared folder using redirector Hands-on Networking Fundamentals 24

Hands-on Networking Fundamentals 25

Hands-on Networking Fundamentals 26

Activity – One-liner OSI • On your assign OSI layer given to you make a one liner statement that would summarize that layer. Write it on the blank paper that I gave you and come to the front when I call your layer. Criteria Points Exactly describe in summarized format the layer. 10 points Describe well the layer but missed some points. 7 to 9 points Completely miss the idea and essence of the layer. 6 points or less A+ Guide to Managing and Maintaining Your PC, 7 e 27

Network Hardware associated in OSI Routers & Intelligent Switches Hubs Hands-on Networking Fundamentals 28

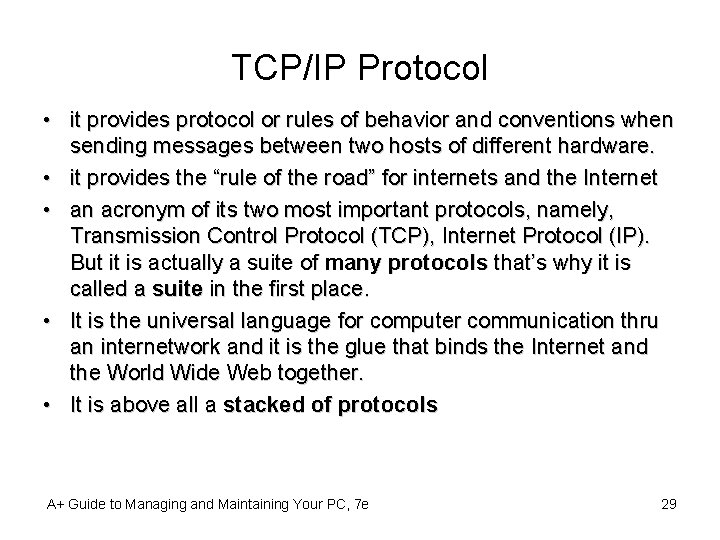
TCP/IP Protocol • it provides protocol or rules of behavior and conventions when sending messages between two hosts of different hardware. • it provides the “rule of the road” for internets and the Internet • an acronym of its two most important protocols, namely, Transmission Control Protocol (TCP), Internet Protocol (IP). But it is actually a suite of many protocols that’s why it is called a suite in the first place. • It is the universal language for computer communication thru an internetwork and it is the glue that binds the Internet and the World Wide Web together. • It is above all a stacked of protocols A+ Guide to Managing and Maintaining Your PC, 7 e 29

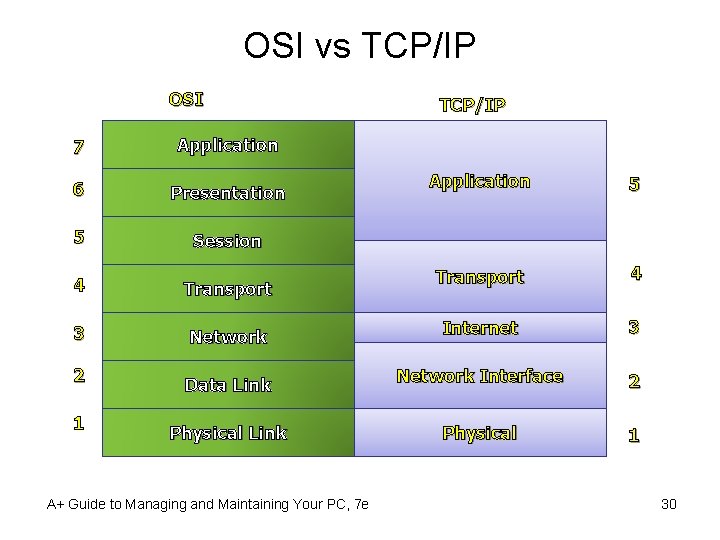
OSI vs TCP/IP OSI 7 Application 6 Presentation 5 Session TCP/IP Application 5 Transport 4 4 Transport 3 Network Internet 3 Data Link Network Interface 2 Physical Link Physical 1 2 1 A+ Guide to Managing and Maintaining Your PC, 7 e 30

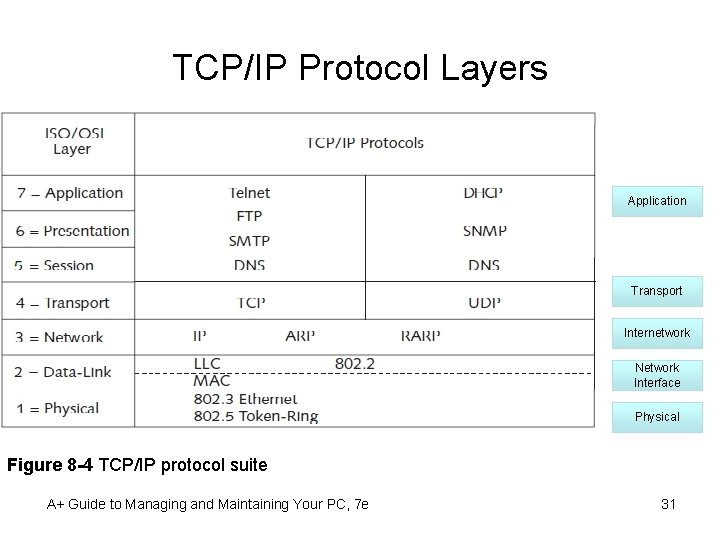
TCP/IP Protocol Layers Application Transport Internetwork Network Interface Physical Figure 8 -4 TCP/IP protocol suite A+ Guide to Managing and Maintaining Your PC, 7 e 31

Role of the Physical Layer • Specifies the physical (connectors, plugs, adapters) and electrical (voltage and currents) interface between data communication device and the network. • It corresponds to the layer 1 of OSI reference model. Copyright © 2012 Cengage Learning. All rights reserved. 32

Role of the Network Access Layer • Provides a physical (MAC) address for the network interface • Verifies that incoming frames have the correct destination MAC address • Defines and follows media access rules • Receives packets from the Internetwork layer and encapsulates them to create frames • De-encapsulates received frames and sends the resulting packets to the Internetwork layer Copyright © 2012 Cengage Learning. All rights reserved. 33

Role of the Network Access Layer • Provides frame error detection in the form of a CRC code • Transmits and receives bit signals • Defines the signaling needed to transmit bits, whether electrical, light pulses, or radio waves • Defines the media and connectors needed to make a physical network connection Copyright © 2012 Cengage Learning. All rights reserved. 34

Role of the Internetwork Layer The Internetwork layer is where administrators usually do the most network configuration This is where the IP protocol operates and is the heart of the TCP/IP protocol suite Responsible for four main tasks: Defines and verifies IP addresses Routes packets through an internetwork Resolves MAC addresses from IP addresses Delivers packets efficiently Copyright © 2012 Cengage Learning. All rights reserved. 35

Defines and Verifies IP Addresses • An IP address is assigned to every computer and network device using TCP/IP for communications • IP addresses are used for two main purposes – To identify a network device at the Internetwork layer – To identify the network on which a device resides • When a device receives an IP packet, it compares the destination IP address with its own – If it matches or is a broadcast, the packet is processed – It is does not match then it is discarded Copyright © 2012 Cengage Learning. All rights reserved. 36

Routes Packets Through an Internetwork • The Internetwork layer determines the best way to get a packet from network to network until it reaches its destination • Most large internetworks, such as the Internet, have multiple paths for getting from one network to another • Routers work at the Internetwork layer and it is their job to select the best path to the destination – Routers use the network identifier portion of IP addresses along with their routing tables to determine the best path Copyright © 2012 Cengage Learning. All rights reserved. 37

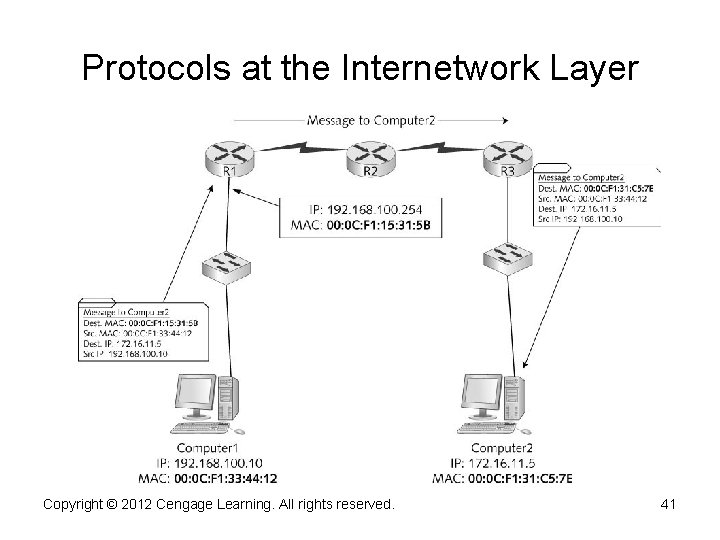
Resolves MAC Addresses from IP Addresses • Every frame contains source and destination physical MAC and logical IP addresses • When a packet is ready to be sent to the Network access layer, the destination device’s MAC address must be retrieved before the frame header can be constructed • TCP/IP uses Address Resolution Protocol (ARP) to find MAC addresses Copyright © 2012 Cengage Learning. All rights reserved. 38

Protocols at the Internetwork Layer • Address Resolution Protocol (cont. ) – To avoid sending an ARP request every time an IP packet is sent, PCs and other devices store learned IP address/MAC address pairs in an ARP cache, which is a temporary location in RAM – If the destination computer is on another network, the computer uses ARP to retrieve the MAC address of the router configured as its default gateway • The packet is delivered to the router and the router determines where the packet should go next to get to its destination • When the packet gets to the destination network, the router on the destination network uses ARP to get the destination computer’s MAC address Copyright © 2012 Cengage Learning. All rights reserved. • Simulation 9 – The changing frame header 39

RARP (Reverse Address Resolution Protocol) • Problem: cannot use ARP – If device does not know its own IP address • Solution: RARP – Client sends broadcast message with MAC address • Receives IP address in reply • RARP server maintains table – Contains MAC addresses, associated IP addresses • RARP originally developed diskless workstations Network+ Guide to Networks, 5 th Edition 40

Protocols at the Internetwork Layer Copyright © 2012 Cengage Learning. All rights reserved. 41

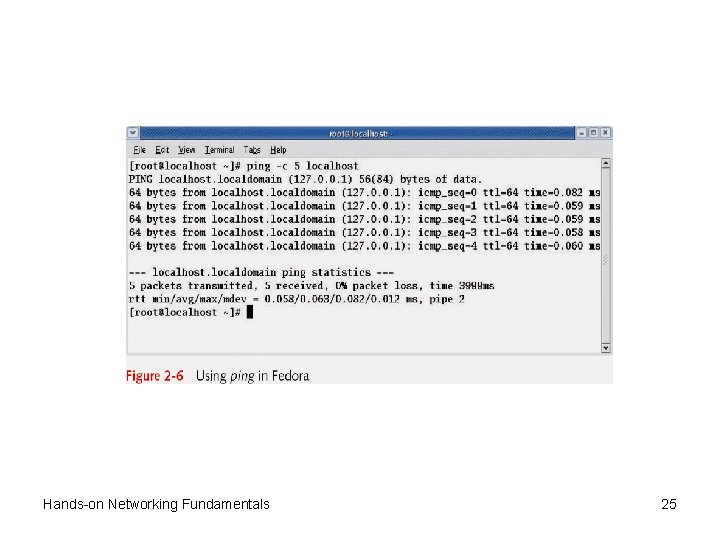
Protocols at the Internetwork Layer • Internet Control Message Protocol (ICMP) – Used to send error and control messages between systems or devices – Specialized IP packet with its own header – Ping program uses ICMP Echo packets to request a response from another computer or to verify whether it is available for communication – An ICMP Reply indicates whether the host is reachable and how long the message’s round trip from sender to receiver took Copyright © 2012 Cengage Learning. All rights reserved. 42

Delivers Packets Efficiently • Internetwork-layer protocols are primarily focused on efficient delivery of packets – Internetwork-layer protocols don’t include features such as flow control, delivery confirmation, or message assembly – These features require overhead to ensure reliable delivery – Rely on the protocols in the Transport and Application layers to provide these reliability features – Considered a connectionless protocol – relies on upper-layer protocols to ensure the packet’s safe journey Copyright © 2012 Cengage Learning. All rights reserved. 43

Role of the Transport Layer • Transport layer provides reliability needed to handle the unpredictable nature of the Internet • Two protocols: – Transmission Control Protocol (TCP): • Connection-oriented and designed for reliable transfer of information in complex internetworks – User Datagram Protocol (UDP): • Connectionless and designed for efficient communication of generally small amounts of data – Both: • Work with segments • Provide a means to identify the source and destination applications involved in a communication • Protect data in the segment with a checksum Copyright © 2012 Cengage Learning. All rights reserved. 44

TCP (Transmission Control Protocol) • Transport layer protocol • Provides reliable data delivery services – Connection-oriented subprotocol • Establish connection before transmitting – Sequencing and checksums – Flow control • Data does not flood node • TCP segment format – Encapsulated by IP datagram in Network layer • Becomes IP datagram’s “data” Network+ Guide to Networks, 5 th Edition 45

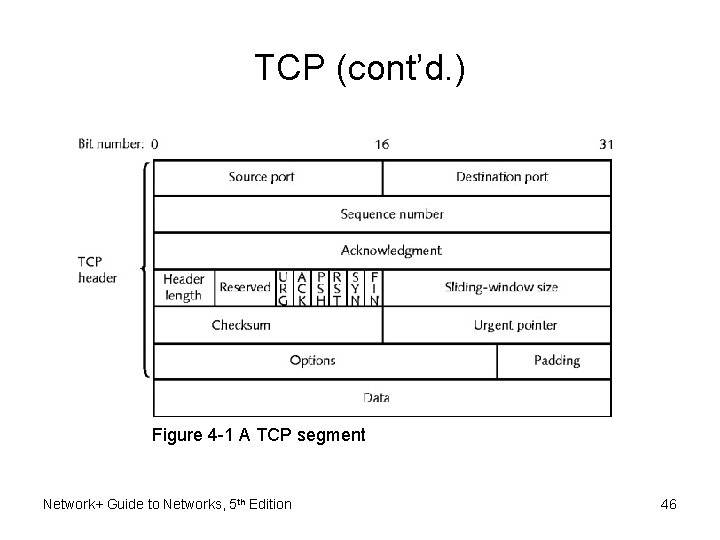
TCP (cont’d. ) Figure 4 -1 A TCP segment Network+ Guide to Networks, 5 th Edition 46

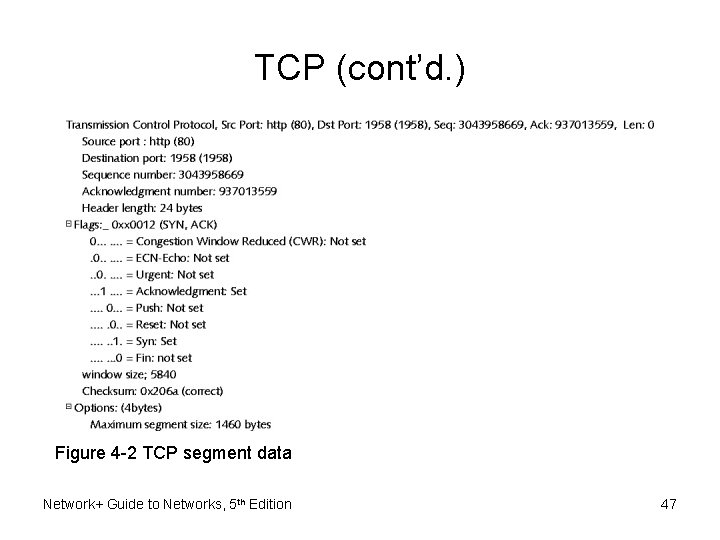
TCP (cont’d. ) Figure 4 -2 TCP segment data Network+ Guide to Networks, 5 th Edition 47

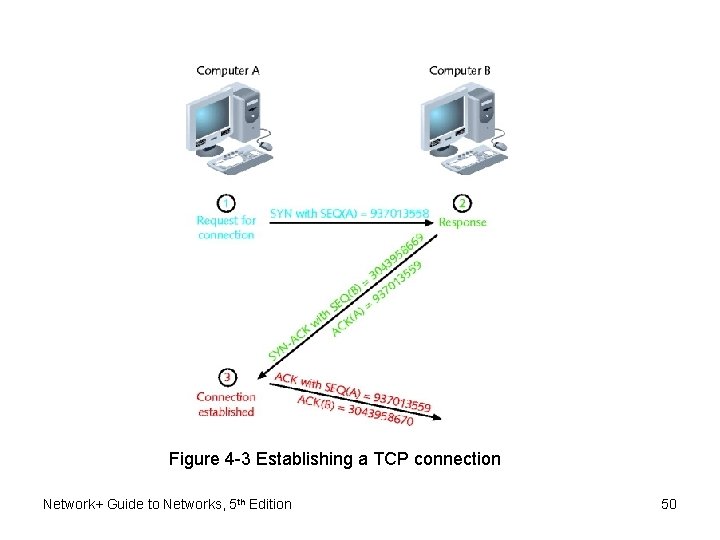
TCP (cont’d. ) • Three segments establish connection • Computer A issues message to Computer B – Sends segment • SYN field: Random synchronize sequence number • Computer B receives message – Sends segment • ACK field: sequence number Computer A sent plus 1 • SYN field: Computer B random number Network+ Guide to Networks, 5 th Edition 48

TCP (cont’d. ) • Computer A responds – Sends segment • ACK field: sequence number Computer B sent plus 1 • SYN field: Computer B random number • FIN flag indicates transmission end Network+ Guide to Networks, 5 th Edition 49

Figure 4 -3 Establishing a TCP connection Network+ Guide to Networks, 5 th Edition 50

UDP (User Datagram Protocol) • Transport layer protocol • Provides unreliable data delivery services – Connectionless transport service • No assurance packets received in correct sequence • No guarantee packets received at all • No error checking, sequencing – Lacks sophistication • More efficient than TCP • Useful situations – Great volume of data transferred quickly Network+ Guide to Networks, 5 th Edition 51

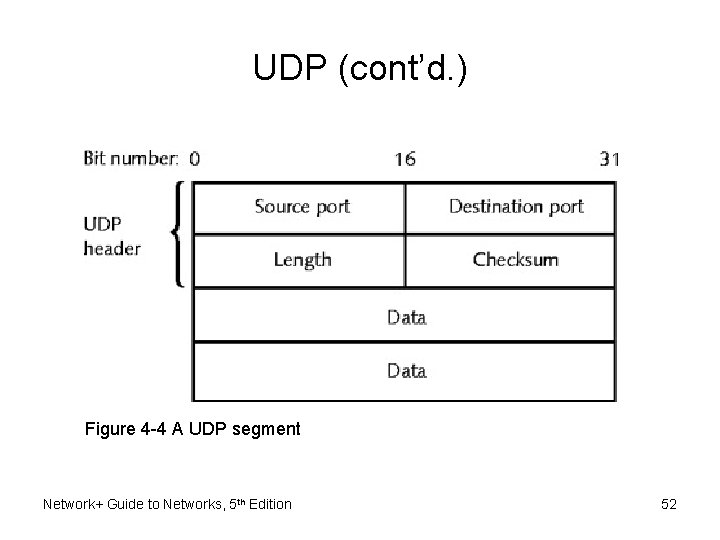
UDP (cont’d. ) Figure 4 -4 A UDP segment Network+ Guide to Networks, 5 th Edition 52

Role of the Application Layer • The Application layer provides network services to user applications that access network resources • With most Application layer protocols, both a client and a server version exist • The Application layer provides these functions: – Access by applications to network services – Client/server data access – Name resolution – Dynamic address assignment – Authentication/user logon – Data formatting and translation Copyright © 2012 Cengage Learning. All rights reserved. 53

HTTP: Protocol of the World Wide Web • Originally, its main purpose was to transfer static web pages written in HTML • Now, it is also used for general file transfer and downloading/displaying multimedia files • Uses TCP as its Transport-layer protocol • Default TCP port number is 80 Copyright © 2012 Cengage Learning. All rights reserved. 54

POP 3, IMAP, and SMTP: E-mail Protocols • Post Office Protocol version 3 (POP 3) is used to download incoming messages from e-mail servers to local desktops (uses TCP port 110) • Internet Message Access Protocol (IMAP) is used to manage email messages locally, yet stores them on a server (uses TCP port 143) • Simple Mail Transfer Protocol (SMTP) is the standard protocol for sending email over the Internet (uses TCP port 25) Copyright © 2012 Cengage Learning. All rights reserved. 55

DHCP (Dynamic Host Configuration Protocol) • Assigns network device unique IP address – Automatically • Application layer protocol • Developed by IETF (BOOTP replacement) • Operation – Similar to BOOTP – Lower administrative burden • Administrator does not maintain table – Requires DHCP service on DHCP server • Many reasons to use Network+ Guide to Networks, 5 th Edition 56

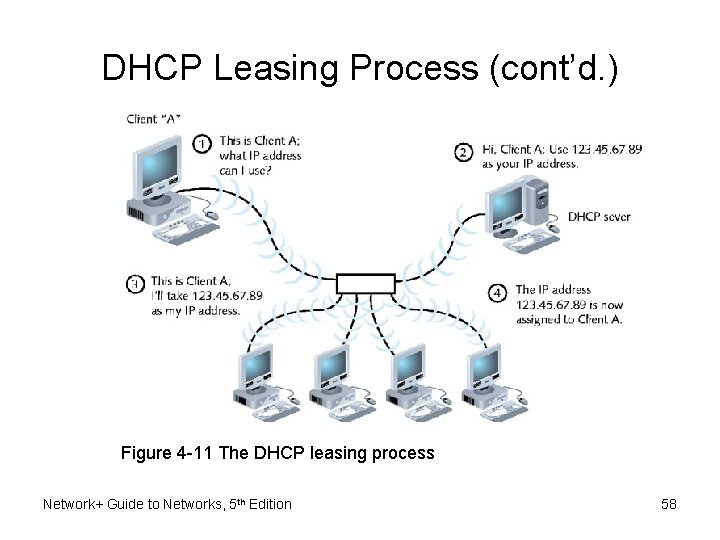
DHCP Leasing Process • Device borrows (leases) IP address – Devices use IP address temporarily • Specified time limit • Lease time – Determine when client obtains IP address at log on – User may force lease termination • DHCP service configuration – Specify leased address range – Configure lease duration • Several steps to negotiate client’s first lease Network+ Guide to Networks, 5 th Edition 57

DHCP Leasing Process (cont’d. ) Figure 4 -11 The DHCP leasing process Network+ Guide to Networks, 5 th Edition 58

Terminating a DHCP Lease • Lease expiration – Automatic • Established in server configuration – Manually terminated at any time • Client’s TCP/IP configuration • Server’s DHCP configuration • Circumstances requiring lease termination – DHCP server fails and replaced • Windows: release of TCP/IP settings • DHCP services run on several server types – Installation and configurations vary Network+ Guide to Networks, 5 th Edition 59

Domain Name System • DNS is a name-to-address resolution protocol that keeps a list of computer names and their IP addresses • With a DNS, a user can use a computer’s name instead of its IP address • Example: – When you enter www. course. com in your Web browser, the browser contacts the DNS server specified in your OS’s IP configuration and requests that the url be resolved to an IP address – Once the IP address for the website is returned, your computer can contact Web server to request a Web page • DNS uses UDP because DNS messages usually consist of a single packet of data Copyright © 2012 Cengage Learning. All rights reserved. 60

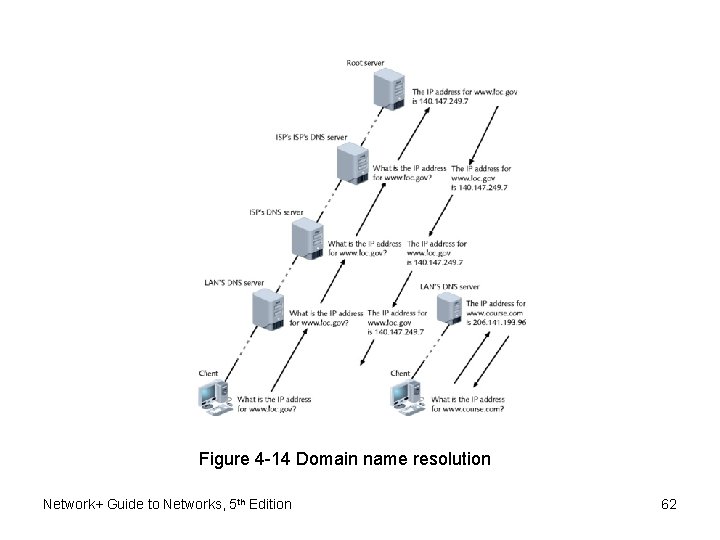
DNS (Domain Name System) • DNS redundancy – Many computers across globe related in hierarchical manner – Root servers • 13 computers (ultimate authorities) Network+ Guide to Networks, 5 th Edition 61

Figure 4 -14 Domain name resolution Network+ Guide to Networks, 5 th Edition 62

DNS (cont’d. ) • Three components – Resolvers • Any hosts on Internet needing to look up domain name information – Name servers (DNS servers) • Databases of associated names, IP addresses • Provide information to resolvers on request – Namespace • Abstract database of Internet IP addresses, associated names • Describes how name servers of the world share DNS information Network+ Guide to Networks, 5 th Edition 63

Summary • A network is a system interconnecting two or more PCs – Basic network types • PAN, LAN, Wireless LAN, MAN, or WAN • There are many broadband technologies – Cable and DSL popular • Major issue for wireless networks is security • Types of hardware – Adapters, routers, hubs, switches A+ Guide to Managing and Maintaining Your PC, 7 e 64

Summary (cont’d. ) • Three layers of communication – Hardware, operating system, application • An IP address is a 32 -bit address identifying network node • TCP/IP protocol suite uses protocols at the application level • Connecting to a wired network • Connecting to a wireless networks – Public, unsecured hotspots or private, secured hotspots A+ Guide to Managing and Maintaining Your PC, 7 e 65