A Brief Summary and Demonstration of Hash functions
A Brief Summary and Demonstration of Hash functions Collisions 01204427 June 2011 1
Topics Overview of attacks MD 5, SHA-0 and SHA-1 attack Attack Demo 2

Hash Collision at present Hash collision situations MD 5 and SHA-0 already broken SHA-1 insecure Real existing collisions algorithms and methods 3
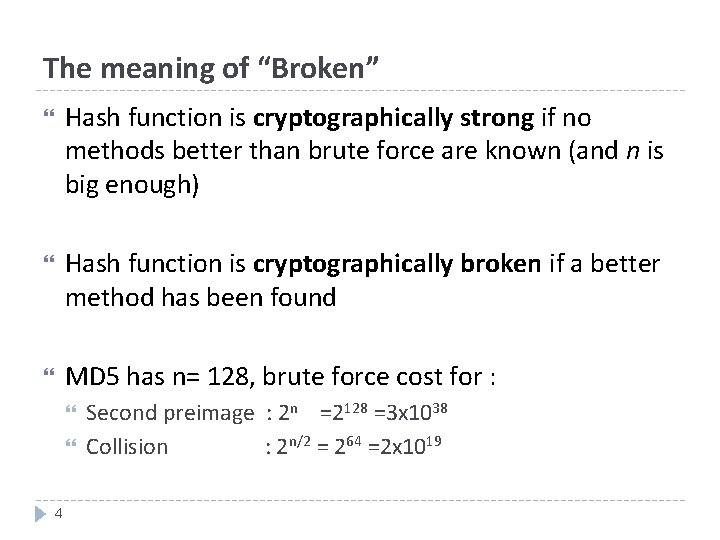
The meaning of “Broken” Hash function is cryptographically strong if no methods better than brute force are known (and n is big enough) Hash function is cryptographically broken if a better method has been found MD 5 has n= 128, brute force cost for : 4 Second preimage : 2 n =2128 =3 x 1038 Collision : 2 n/2 = 264 =2 x 1019
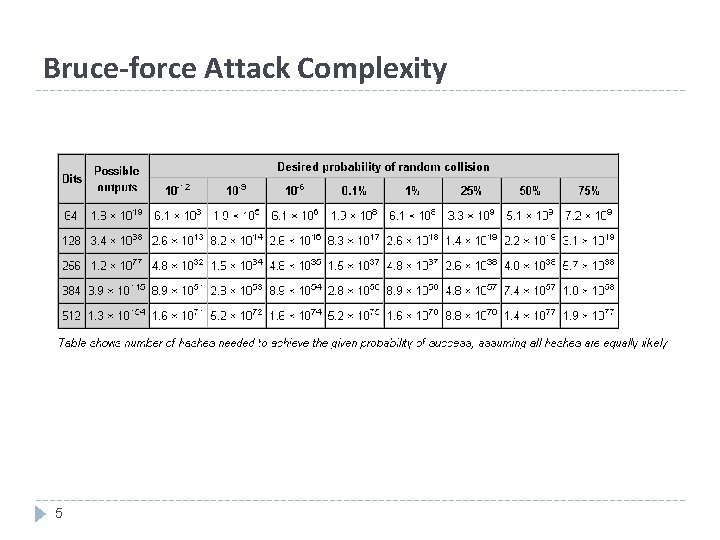
Bruce-force Attack Complexity 5

What is regarded as secure? 264 hash computations is at the edge of feasibility with realistic investments in equipment and time 128 bit hash not safe anymore against brute force collision attack 280 hash computations is still infeasible 6 unless with major investments in equipment and time 160 bit hash still safe against brute force collision attack
Today’s Cryptanalysis (second) preimage attack: not known for MD 5, SHA-1, SHA-2 Collisions attack: 7 MD 5: found SHA-1: found SHA-2: no attack known
Topics Overview of attacks MD 5, SHA-0 and SHA-1 attack Attack Demo 8

MD 5 Attack 2004 First collision for MD 5 presented Two 128 byte messages with same MD 5 hash value Identical prefix collision attack 15 minutes up to an hour on a IBM P 690 with about 239 2005 Attack method released 2006 Chosen-prefix collision (CPC) attack Choose two arbitrary files (same length) Make them collide by appending 716 ‘random’ bytes 9
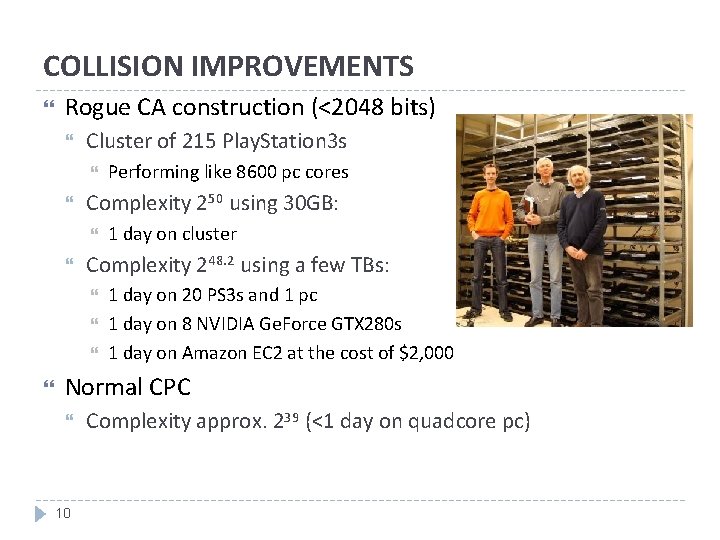
COLLISION IMPROVEMENTS Rogue CA construction (<2048 bits) Cluster of 215 Play. Station 3 s Complexity 250 using 30 GB: 1 day on cluster Complexity 248. 2 using a few TBs: Performing like 8600 pc cores 1 day on 20 PS 3 s and 1 pc 1 day on 8 NVIDIA Ge. Force GTX 280 s 1 day on Amazon EC 2 at the cost of $2, 000 Normal CPC 10 Complexity approx. 239 (<1 day on quadcore pc)

MD 5 Breakers Xiaoyun Wang (China) collisions for MD 5 in 2004 in a few hours on a big computer Marc Stevens (Amsterdam) 11 MSc thesis 2007, TU/e improved method, fully automated collisions can now be found in about 1 second on a standard laptop
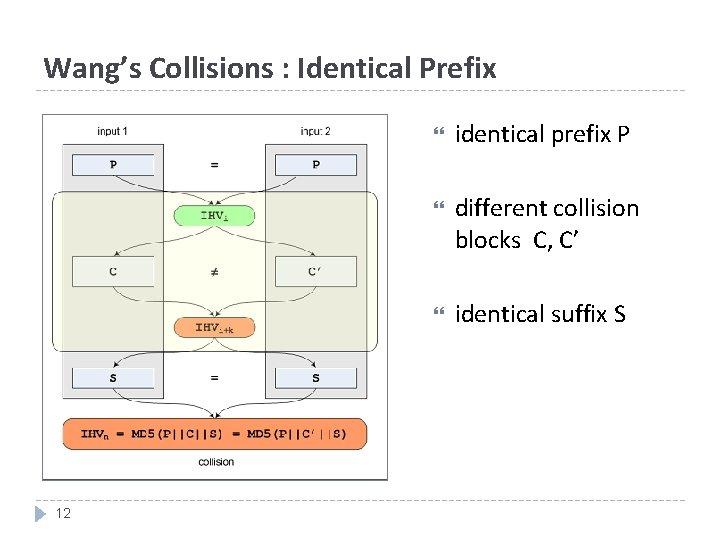
Wang’s Collisions : Identical Prefix 12 identical prefix P different collision blocks C, C’ identical suffix S
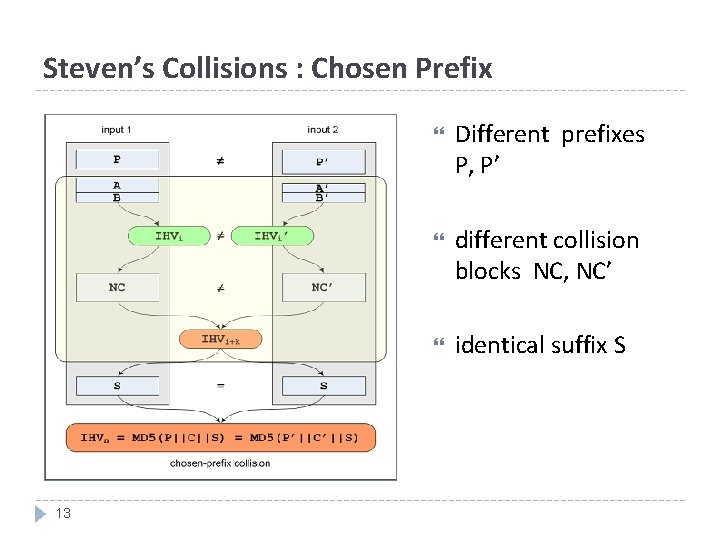
Steven’s Collisions : Chosen Prefix 13 Different prefixes P, P’ different collision blocks NC, NC’ identical suffix S

SHA-0 Attack 1998 2004 Full collisions found with 251 operations 80, 000 CPU hours with Itanium 2 2004 Possible collisions attack with 261 operations Collisions with 240 operations for SHA-0, MD 5 and other 2005 14 Collisions with 239 operations

SHA-1 Attack 2005 2006 Collisons found in 280 operatons of reduced version of SHA-1 -53 out of 80 rounds SHA-1 -64 with 235 operations 2010 15 SHA-1 -73 with 235 operations Project Hash. Clash : claim fully near collision attack with estimated complexity of 257. 5
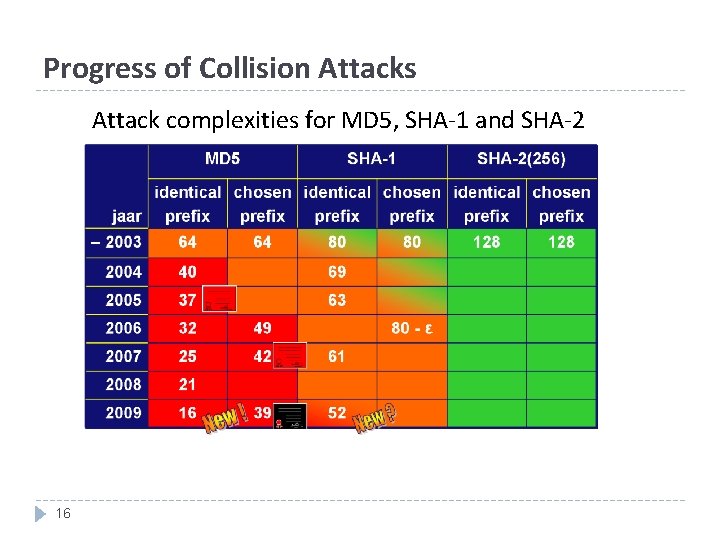
Progress of Collision Attacks Attack complexities for MD 5, SHA-1 and SHA-2 16
Topics Overview of attacks MD 5, SHA-0 and SHA-1 attack Attack Demo 17
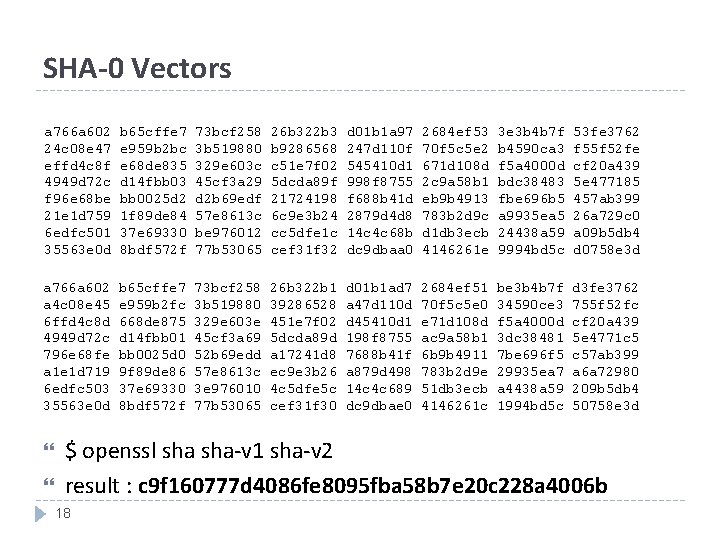
SHA-0 Vectors a 766 a 602 24 c 08 e 47 effd 4 c 8 f 4949 d 72 c f 96 e 68 be 21 e 1 d 759 6 edfc 501 35563 e 0 d b 65 cffe 7 e 959 b 2 bc e 68 de 835 d 14 fbb 03 bb 0025 d 2 1 f 89 de 84 37 e 69330 8 bdf 572 f 73 bcf 258 3 b 519880 329 e 603 c 45 cf 3 a 29 d 2 b 69 edf 57 e 8613 c be 976012 77 b 53065 26 b 322 b 3 b 9286568 c 51 e 7 f 02 5 dcda 89 f 21724198 6 c 9 e 3 b 24 cc 5 dfe 1 c cef 31 f 32 d 01 b 1 a 97 247 d 110 f 545410 d 1 998 f 8755 f 688 b 41 d 2879 d 4 d 8 14 c 4 c 68 b dc 9 dbaa 0 2684 ef 53 70 f 5 c 5 e 2 671 d 108 d 2 c 9 a 58 b 1 eb 9 b 4913 783 b 2 d 9 c d 1 db 3 ecb 4146261 e 3 e 3 b 4 b 7 f b 4590 ca 3 f 5 a 4000 d bdc 38483 fbe 696 b 5 a 9935 ea 5 24438 a 59 9994 bd 5 c 53 fe 3762 f 55 f 52 fe cf 20 a 439 5 e 477185 457 ab 399 26 a 729 c 0 a 09 b 5 db 4 d 0758 e 3 d a 766 a 602 a 4 c 08 e 45 6 ffd 4 c 8 d 4949 d 72 c 796 e 68 fe a 1 e 1 d 719 6 edfc 503 35563 e 0 d b 65 cffe 7 e 959 b 2 fc 668 de 875 d 14 fbb 01 bb 0025 d 0 9 f 89 de 86 37 e 69330 8 bdf 572 f 73 bcf 258 3 b 519880 329 e 603 e 45 cf 3 a 69 52 b 69 edd 57 e 8613 c 3 e 976010 77 b 53065 26 b 322 b 1 39286528 451 e 7 f 02 5 dcda 89 d a 17241 d 8 ec 9 e 3 b 26 4 c 5 dfe 5 c cef 31 f 30 d 01 b 1 ad 7 a 47 d 110 d d 45410 d 1 198 f 8755 7688 b 41 f a 879 d 498 14 c 4 c 689 dc 9 dbae 0 2684 ef 51 70 f 5 c 5 e 0 e 71 d 108 d ac 9 a 58 b 1 6 b 9 b 4911 783 b 2 d 9 e 51 db 3 ecb 4146261 c be 3 b 4 b 7 f 34590 ce 3 f 5 a 4000 d 3 dc 38481 7 be 696 f 5 29935 ea 7 a 4438 a 59 1994 bd 5 c d 3 fe 3762 755 f 52 fc cf 20 a 439 5 e 4771 c 5 c 57 ab 399 a 6 a 72980 209 b 5 db 4 50758 e 3 d $ openssl sha-v 1 sha-v 2 result : c 9 f 160777 d 4086 fe 8095 fba 58 b 7 e 20 c 228 a 4006 b 18
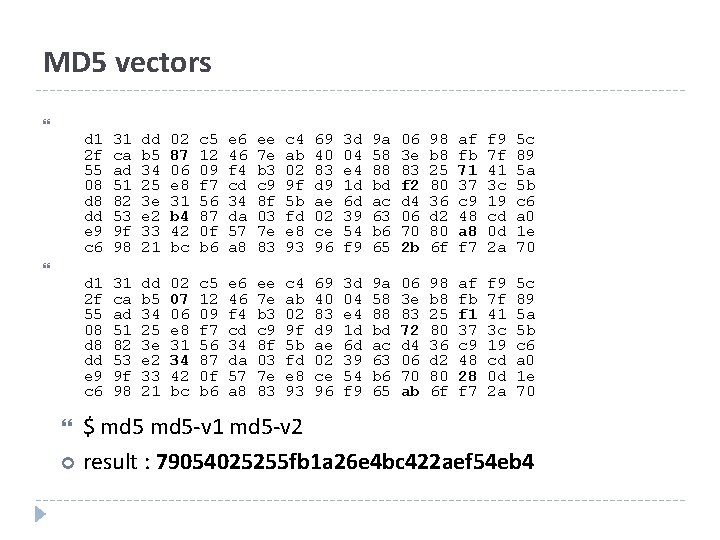
MD 5 vectors d 1 2 f 55 08 d 8 dd e 9 c 6 31 ca ad 51 82 53 9 f 98 dd b 5 34 25 3 e e 2 33 21 02 87 06 e 8 31 b 4 42 bc c 5 12 09 f 7 56 87 0 f b 6 e 6 46 f 4 cd 34 da 57 a 8 ee 7 e b 3 c 9 8 f 03 7 e 83 c 4 ab 02 9 f 5 b fd e 8 93 69 40 83 d 9 ae 02 ce 96 3 d 04 e 4 1 d 6 d 39 54 f 9 9 a 58 88 bd ac 63 b 6 65 06 3 e 83 f 2 d 4 06 70 2 b 98 b 8 25 80 36 d 2 80 6 f af fb 71 37 c 9 48 a 8 f 7 f 9 7 f 41 3 c 19 cd 0 d 2 a 5 c 89 5 a 5 b c 6 a 0 1 e 70 d 1 2 f 55 08 d 8 dd e 9 c 6 31 ca ad 51 82 53 9 f 98 dd b 5 34 25 3 e e 2 33 21 02 07 06 e 8 31 34 42 bc c 5 12 09 f 7 56 87 0 f b 6 e 6 46 f 4 cd 34 da 57 a 8 ee 7 e b 3 c 9 8 f 03 7 e 83 c 4 ab 02 9 f 5 b fd e 8 93 69 40 83 d 9 ae 02 ce 96 3 d 04 e 4 1 d 6 d 39 54 f 9 9 a 58 88 bd ac 63 b 6 65 06 3 e 83 72 d 4 06 70 ab 98 b 8 25 80 36 d 2 80 6 f af fb f 1 37 c 9 48 28 f 7 f 9 7 f 41 3 c 19 cd 0 d 2 a 5 c 89 5 a 5 b c 6 a 0 1 e 70 $ md 5 -v 1 md 5 -v 2 result : 79054025255 fb 1 a 26 e 4 bc 422 aef 54 eb 4
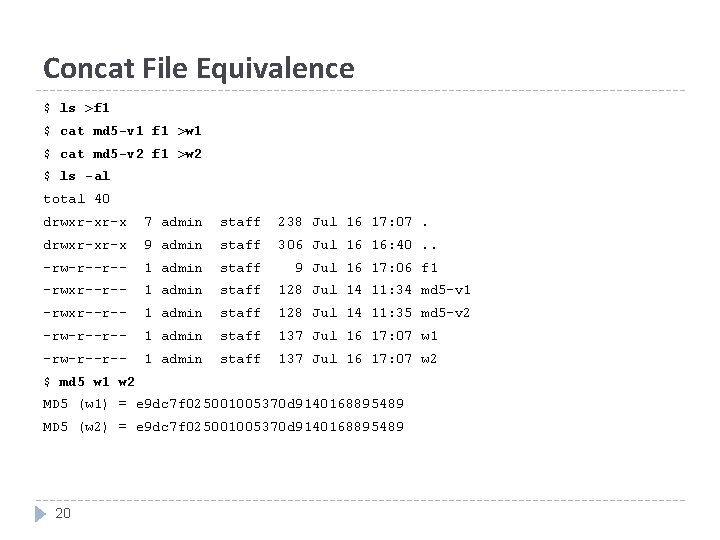
Concat File Equivalence $ ls >f 1 $ cat md 5 -v 1 f 1 >w 1 $ cat md 5 -v 2 f 1 >w 2 $ ls -al total 40 drwxr-xr-x 7 admin staff 238 Jul 16 17: 07. drwxr-xr-x 9 admin staff 306 Jul 16 16: 40. . -rw-r--r-- 1 admin staff 9 Jul 16 17: 06 f 1 -rwxr--r-- 1 admin staff 128 Jul 14 11: 34 md 5 -v 1 -rwxr--r-- 1 admin staff 128 Jul 14 11: 35 md 5 -v 2 -rw-r--r-- 1 admin staff 137 Jul 16 17: 07 w 1 -rw-r--r-- 1 admin staff 137 Jul 16 17: 07 w 2 $ md 5 w 1 w 2 MD 5 (w 1) = e 9 dc 7 f 025001005370 d 9140168895489 MD 5 (w 2) = e 9 dc 7 f 025001005370 d 9140168895489 20
But how’s about $ md 5 -s windows MD 5 ("windows") = 0 f 4137 ed 1502 b 5045 d 6083 aa 258 b 5 c 42 http: //md 5. rednoize. com/ 21
- Slides: 21