9 Principles of Reliable Data Transport Part 1
9. Principles of Reliable Data Transport – Part 1 n n Basic concepts Stop-and-wait protocol Go-Back-N protocol Selective Repeat protocol Roch Guerin (with adaptations from Jon Turner and John De. Hart, and material from Kurose and Ross)
Preliminaries n Physical channels are never completely reliable » wireless links subject to interference » transmission noise can introduce bit errors » routers & switches may drop packets due to buffer overflow n Reliable communication relies on (1) detection (of lost or corrupted packets) and (2) retransmissions as necessary » sender retains copy until it knows packet has been received » receiver notifies sender and delivers (to application) each piece of data once, and only once, preferably in order n Protocol design specifies coordination between sender and receiver, and depends on nature of “channel” » may corrupt packets, but never lose them » may corrupt and/or lose packets but never re-order them » may corrupt, lose or re-order packets 2
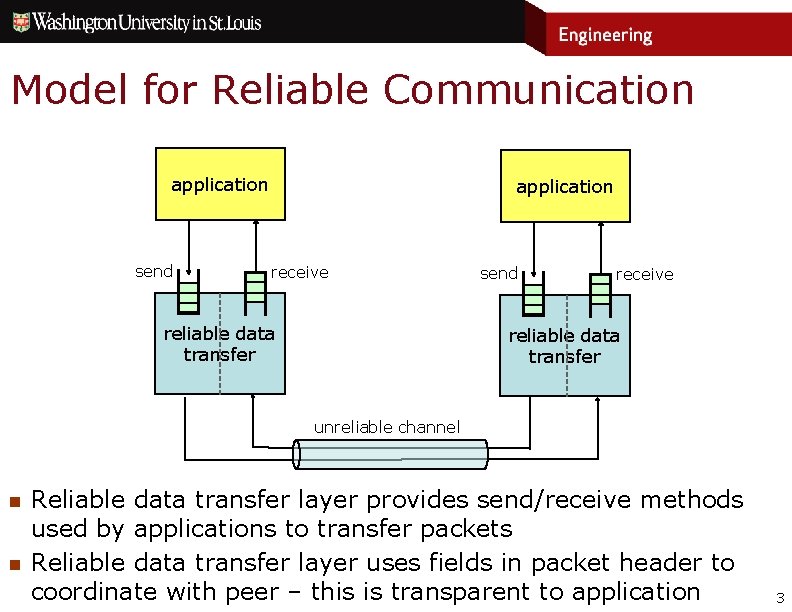
Model for Reliable Communication application send application receive reliable data transfer send receive reliable data transfer unreliable channel n n Reliable data transfer layer provides send/receive methods used by applications to transfer packets Reliable data transfer layer uses fields in packet header to coordinate with peer – this is transparent to application 3
Basic Concepts n n focus separately on sender and receiver behavior receiver acknowledges packets from sender » positive acks and/or negative acks (nack) n sender transmits and retransmits based on information provided by the receiver » time-out to trigger action if ack/nack is not received within a certain time-frame » both packets and acks can get lost n sequence numbers in each packet » sequence number in ack identifies received packet(s) » size of seq. num. field determines # packets that can be sent before acknowledgments must be received • simplest protocol uses 1 bit sequence number – sends one packet and waits for ack before sending another 4
Basic Protocols – RDT 1. 0 – 3. 0 n n RDT 1. 0: RDT over reliable channel RDT 2. 0: RDT over channel with bit errors » Stop and wait » Acks and Nacks n n RDT 2. 1: RDT 2. 0 plus 1 -bit sequence number RDT 2. 2: RDT 2. 1 with duplicate Acks instead of Nacks » Stop and wait » Acks but no need for Nacks n RDT 3. 0: RDT over channel with bit errors and pkt loss » Stop and wait. Also called alternating-bit protocol » RDT 2. 2 plus timeouts • Sender can ignore duplicate Acks and wait for timeout n And beyond… » Pipelined RDT protocols (next time) 5
Basic Protocol – RDT 2. x (2. 0 & 2. 1) n Assume channel may corrupt but never lose packets » receiver can always detect if packet has been corrupted n Simple protocol for such a channel uses acks and nacks » sender transmits one packet at a time and waits for ack/nack or erroneous packet » receiver sends ack when it receives packet correctly, sends nack when it receives a packet with an error n Is this enough? » packets, acks and nacks can all get corrupted 6
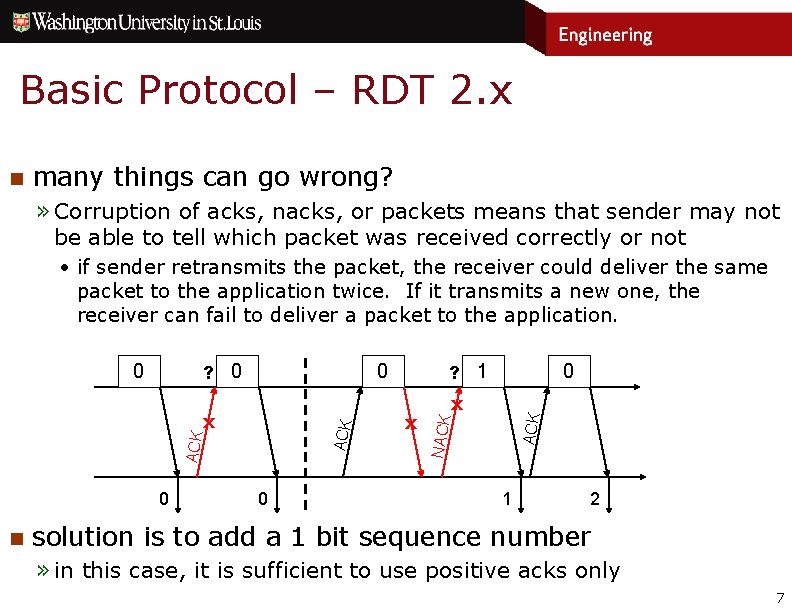
Basic Protocol – RDT 2. x n many things can go wrong? » Corruption of acks, nacks, or packets means that sender may not be able to tell which packet was received correctly or not • if sender retransmits the packet, the receiver could deliver the same packet to the application twice. If it transmits a new one, the receiver can fail to deliver a packet to the application. 0 ACK x 0 n 0 ? 1 x 0 x ACK ? 0 NACK 0 1 2 solution is to add a 1 bit sequence number » in this case, it is sufficient to use positive acks only 7
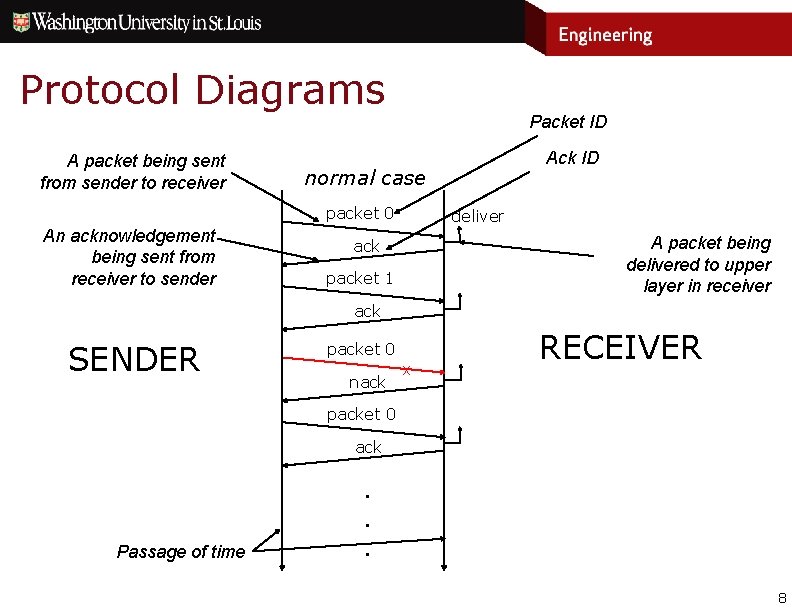
Protocol Diagrams A packet being sent from sender to receiver Packet ID normal case packet 0 An acknowledgement being sent from receiver to sender Ack ID deliver A packet being delivered to upper layer in receiver ack packet 1 ack SENDER packet 0 nack x RECEIVER packet 0 ack Passage of time . . . 8
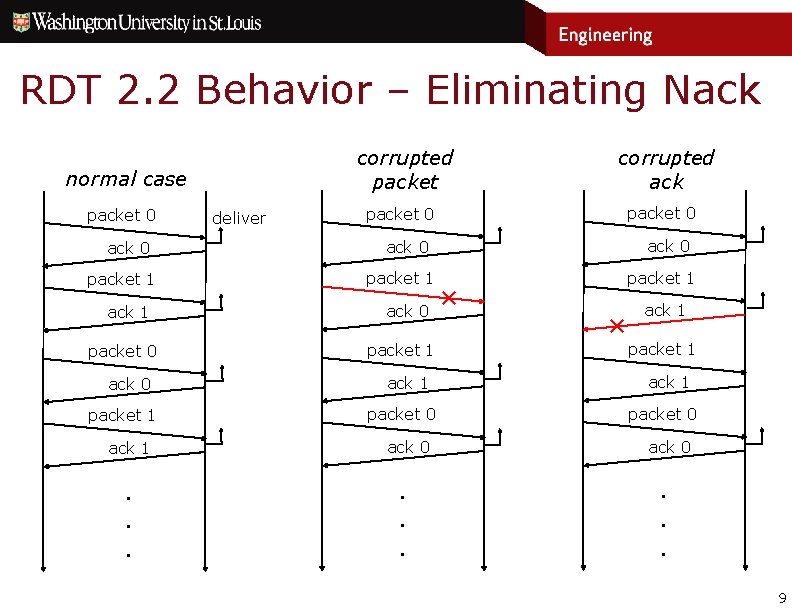
RDT 2. 2 Behavior – Eliminating Nack corrupted packet normal case packet 0 ack 0 packet 1 ack 1 . . . deliver corrupted ack packet 0 ack 0 packet 1 ack 1 packet 0 ack 0 . . . packet 1 ✕ ✕ ack 1 packet 1 ack 1 packet 0 ack 0 . . . 9
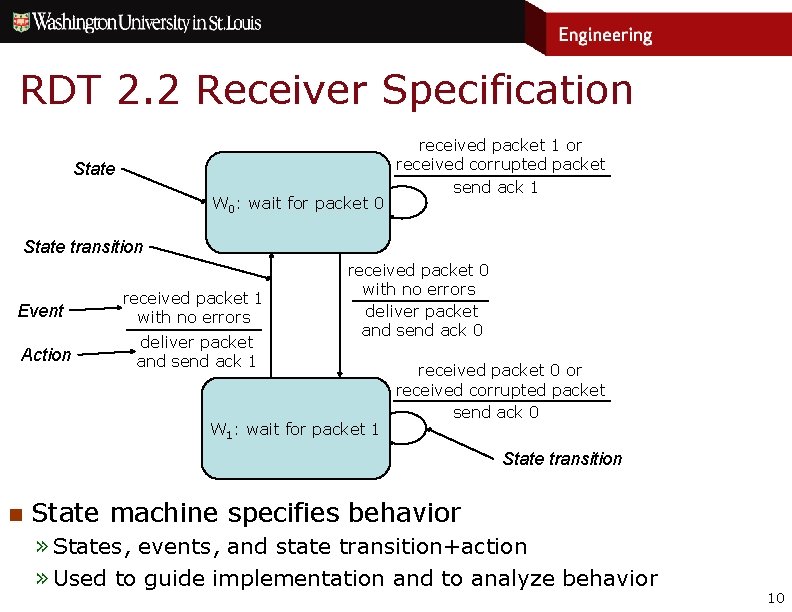
RDT 2. 2 Receiver Specification State W 0: wait for packet 0 received packet 1 or received corrupted packet send ack 1 State transition Event Action received packet 1 with no errors deliver packet and send ack 1 received packet 0 with no errors deliver packet and send ack 0 W 1: wait for packet 1 received packet 0 or received corrupted packet send ack 0 State transition n State machine specifies behavior » States, events, and state transition+action » Used to guide implementation and to analyze behavior 10
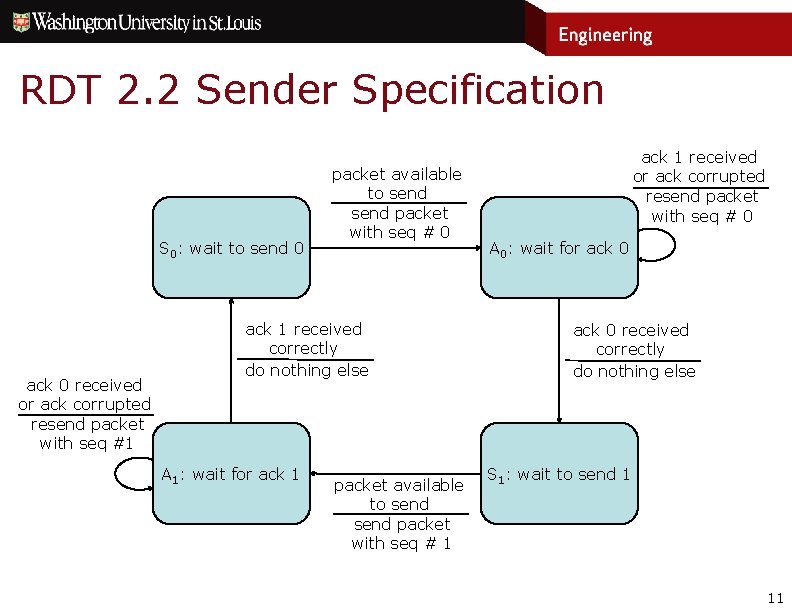
RDT 2. 2 Sender Specification S 0: wait to send 0 ack 0 received or ack corrupted resend packet with seq #1 packet available to send packet with seq # 0 ack 1 received correctly do nothing else A 1: wait for ack 1 packet available to send packet with seq # 1 ack 1 received or ack corrupted resend packet with seq # 0 A 0: wait for ack 0 received correctly do nothing else S 1: wait to send 1 11

A More Realistic Protocol n RDT 2. x assumed the channel can corrupt packets but never loses them entirely » means receiver always gets something whenever a packet is sent and sender always receives an “ack” after sending a packet n In practice, packets can also be lost “without a trace” » receiver never acks lost packet, since does not know it was sent » sender left waiting for ack, but no ack ever comes n Recovering from lost packets » option 1: keep sending packet repeatedly until ack received • means that in normal case, sender/receiver both do extra work » option 2: sender waits for ack for a limited time period, then re-sends the packet if ack fails to arrive in time • works well if maximum ack delay is known and does not change n Still operating with 1 -bit sequence number 12
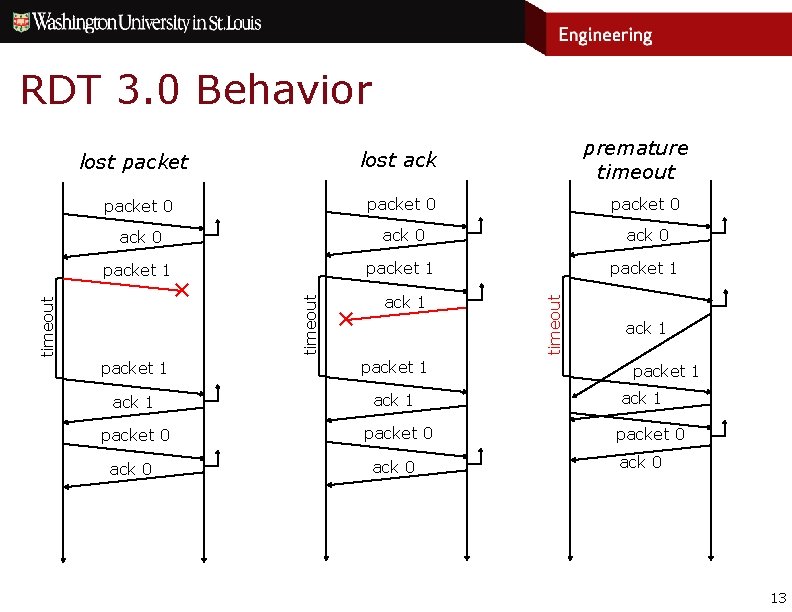
RDT 3. 0 Behavior lost packet 0 ack 0 packet 1 ✕ ✕ ack 1 packet 1 ack 1 packet 0 ack 0 timeout packet 0 timeout premature timeout lost ack 1 packet 1 ack 1 packet 0 ack 0 13
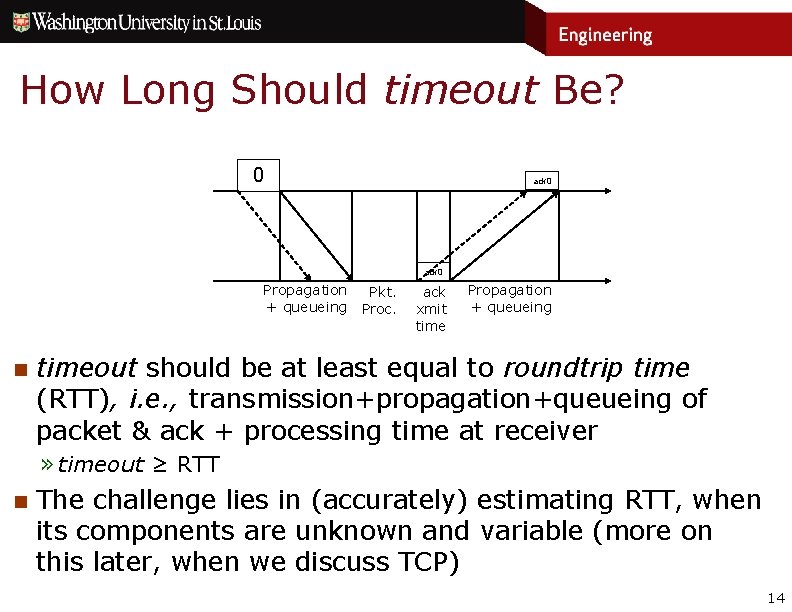
How Long Should timeout Be? 0 ack 0 Propagation + queueing n Pkt. Proc. ack xmit time Propagation + queueing timeout should be at least equal to roundtrip time (RTT), i. e. , transmission+propagation+queueing of packet & ack + processing time at receiver » timeout ≥ RTT n The challenge lies in (accurately) estimating RTT, when its components are unknown and variable (more on this later, when we discuss TCP) 14
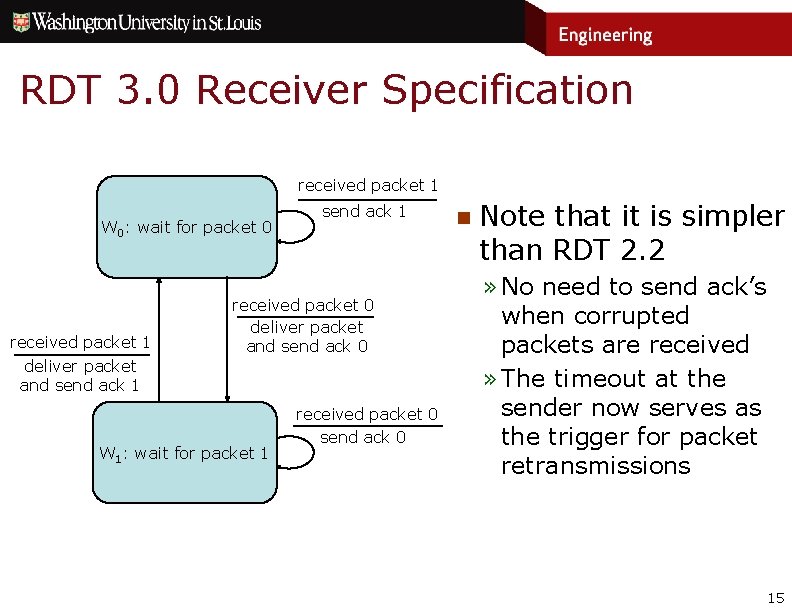
RDT 3. 0 Receiver Specification received packet 1 W 0: wait for packet 0 received packet 1 send ack 1 received packet 0 deliver packet and send ack 1 W 1: wait for packet 1 received packet 0 send ack 0 n Note that it is simpler than RDT 2. 2 » No need to send ack’s when corrupted packets are received » The timeout at the sender now serves as the trigger for packet retransmissions 15
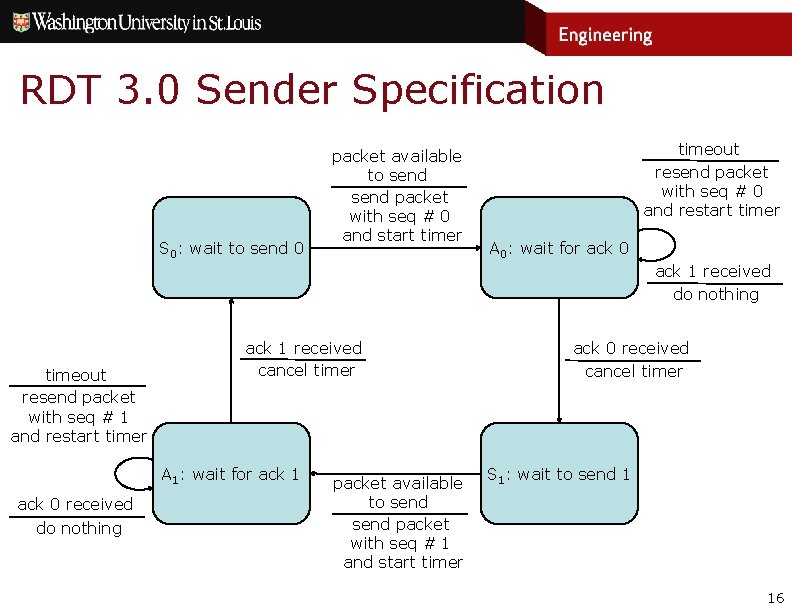
RDT 3. 0 Sender Specification S 0: wait to send 0 packet available to send packet with seq # 0 and start timer timeout resend packet with seq # 0 and restart timer A 0: wait for ack 0 ack 1 received do nothing timeout resend packet with seq # 1 and restart timer ack 1 received cancel timer A 1: wait for ack 1 ack 0 received do nothing packet available to send packet with seq # 1 and start timer ack 0 received cancel timer S 1: wait to send 1 16
RDT 3. 0 Performance n RDT 3. 0 sends only one packet at a time » works well if delay between sender and receiver is small » inefficient if RTT >> transmission time of a packet (tpkt=L/C) n Consider a 1 Gb/s link with 10 ms delay in each direction » RDT 3. 0 sends only one packet every 20 ms, » but link is capable of sending 20 million bits in 20 ms, so for typical packet sizes, only tiny fraction of link’s capacity is used 17
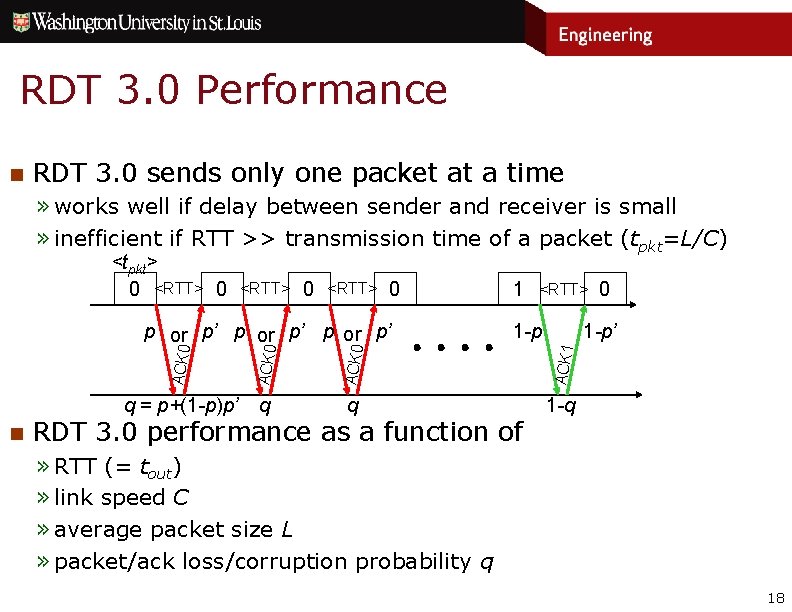
RDT 3. 0 Performance n RDT 3. 0 sends only one packet at a time » works well if delay between sender and receiver is small » inefficient if RTT >> transmission time of a packet (tpkt=L/C) <tpkt> 0 <RTT> 0 n <RTT> ACK 0 ACK 1 q = p+(1 -p)p’ q q 1 -q RDT 3. 0 performance as a function of 0 1 -p’ ACK 0 1 -p ACK 0 p or p’ 1 » RTT (= tout) » link speed C » average packet size L » packet/ack loss/corruption probability q 18
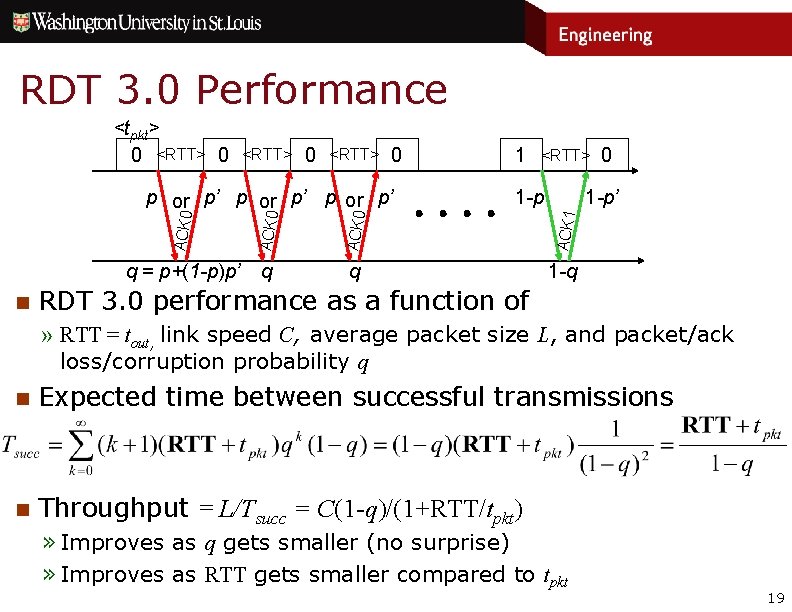
RDT 3. 0 Performance <tpkt> 0 <RTT> 0 n <RTT> 0 ACK 1 1 -p’ ACK 0 1 -p ACK 0 p or p’ 1 q = p+(1 -p)p’ q q 1 -q RDT 3. 0 performance as a function of » RTT = tout, link speed C, average packet size L, and packet/ack loss/corruption probability q n Expected time between successful transmissions n Throughput = L/Tsucc = C(1 -q)/(1+RTT/tpkt) » Improves as q gets smaller (no surprise) » Improves as RTT gets smaller compared to tpkt 19
Exercise 1. Consider this scenario for RDT 2. 2 (no losses). Two packets are sent. » the not » the but the corrupted packet + corrupted ack first packet and its ack are corrupted second packet is corrupted, when it is sent a second time, packet is not corrupted, but ack is Draw a time-space diagram (like those on the previous slide) describing this scenario, showing how RDT 2. 2 recovers and delivers packets to the receiving application. 20
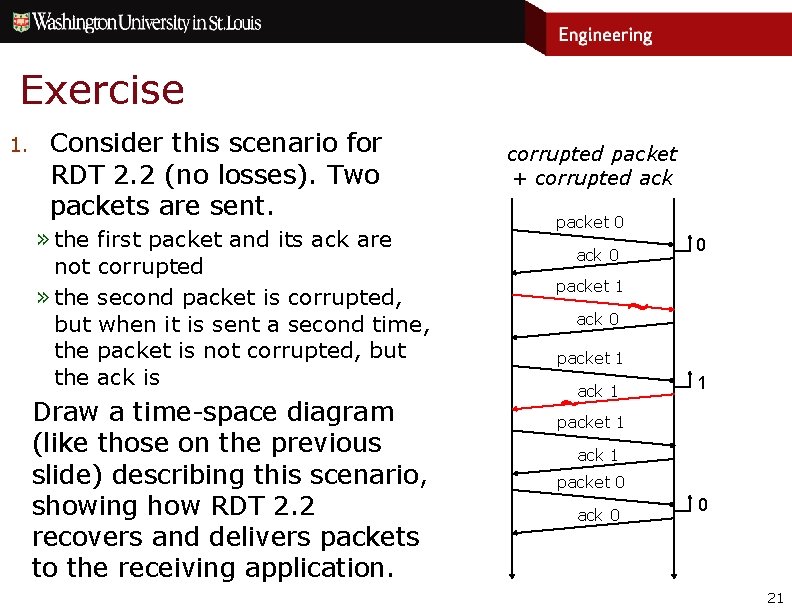
Exercise 1. Consider this scenario for RDT 2. 2 (no losses). Two packets are sent. » the not » the but the first packet and its ack are corrupted second packet is corrupted, when it is sent a second time, packet is not corrupted, but ack is Draw a time-space diagram (like those on the previous slide) describing this scenario, showing how RDT 2. 2 recovers and delivers packets to the receiving application. corrupted packet + corrupted ack packet 0 0 ack 0 packet 1 ack 0 ~ packet 1 ack 1 ~ packet 1 1 ack 1 packet 0 ack 0 0 21
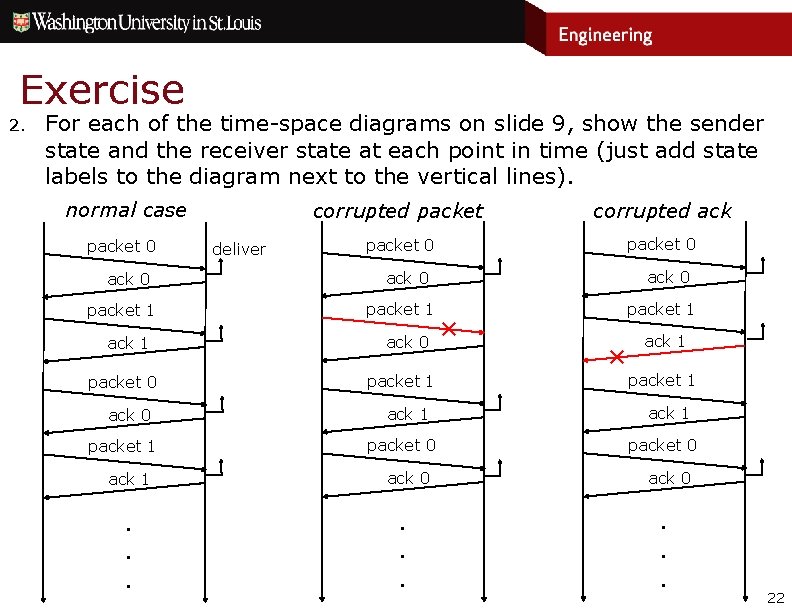
Exercise 2. For each of the time-space diagrams on slide 9, show the sender state and the receiver state at each point in time (just add state labels to the diagram next to the vertical lines). normal case packet 0 ack 0 packet 1 ack 1 . . . deliver corrupted packet corrupted ack packet 0 ack 0 packet 1 ack 1 packet 0 ack 0 . . . packet 1 ✕ ✕ ack 1 packet 1 ack 1 packet 0 ack 0 . . . 22
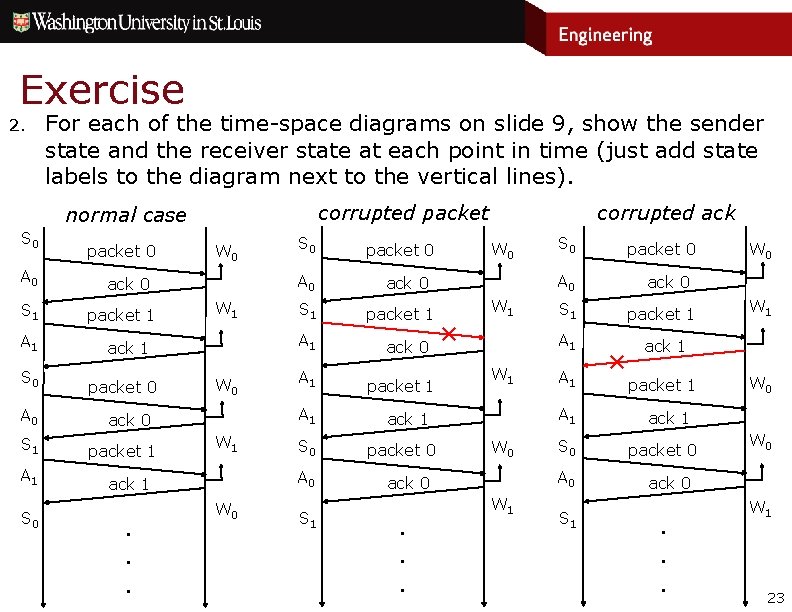
Exercise 2. For each of the time-space diagrams on slide 9, show the sender state and the receiver state at each point in time (just add state labels to the diagram next to the vertical lines). S 0 A 0 S 1 A 1 S 0 packet 0 W 1 W 0 W 1 S 0 A 0 ack 1 . . . A 1 ack 0 packet 1 S 1 A 1 ack 1 packet 0 S 0 A 0 ack 0 packet 1 corrupted ack corrupted packet normal case W 0 S 1 W 0 packet 0 ack 0 packet 1 W 1 ✕ W 1 W 0 A 1 ack 1 S 0 A 0 ack 0 . . . packet 1 A 1 W 1 S 1 W 0 ack 0 S 1 A 1 ack 1 packet 0 A 0 ack 0 packet 1 S 0 ✕ packet 1 W 0 ack 1 packet 0 W 0 ack 0 . . . W 1 23
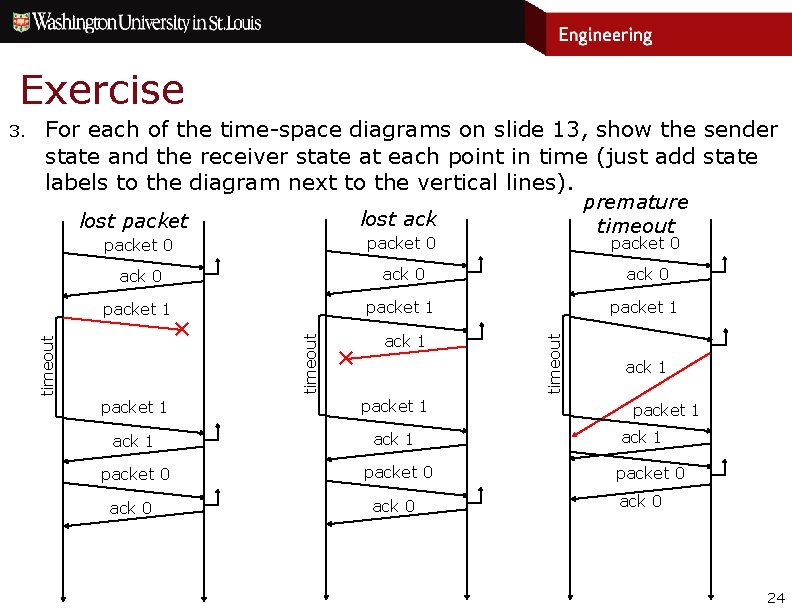
Exercise For each of the time-space diagrams on slide 13, show the sender state and the receiver state at each point in time (just add state labels to the diagram next to the vertical lines). premature timeout lost ack lost packet 0 ack 0 packet 1 ✕ ack 1 packet 1 ack 1 packet 0 ack 0 packet 0 timeout ✕ timeout 3. ack 1 packet 1 ack 1 packet 0 ack 0 24
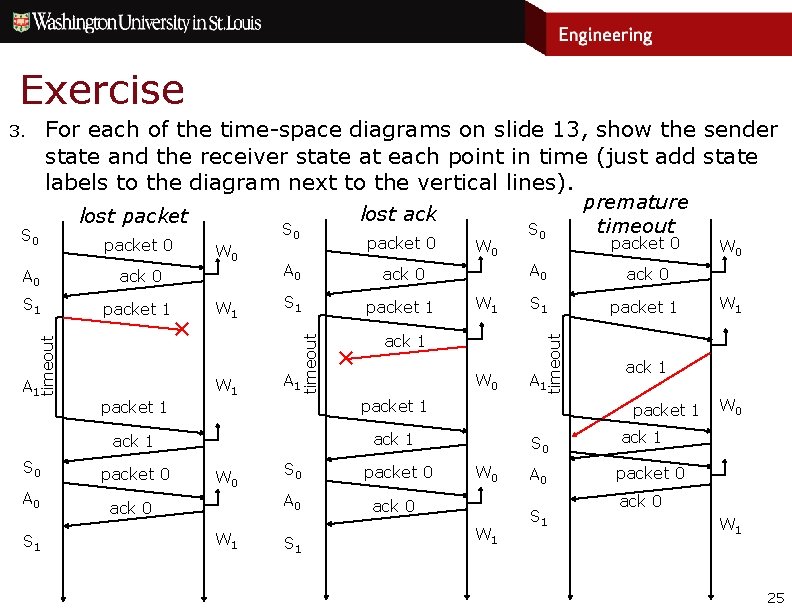
Exercise For each of the time-space diagrams on slide 13, show the sender state and the receiver state at each point in time (just add state labels to the diagram next to the vertical lines). packet 0 ack 0 S 1 packet 1 timeout A 0 A 1 packet 1 ✕ W 0 W 1 S 0 packet 0 A 0 ack 0 S 1 packet 1 ✕ W 0 W 1 S 1 packet 1 W 0 A 1 packet 1 S 0 A 0 W 1 S 1 packet 0 ack 0 W 1 S 0 ack 1 A 0 packet 0 S 1 W 0 W 1 ack 1 packet 1 ack 1 W 0 S 0 premature timeout A 0 ack 1 A 1 ack 1 S 0 lost ack timeout S 0 lost packet timeout 3. W 0 ack 0 W 1 25
Exercise 4. 1 Gb/s link with 20 ms RTT, L=10, 000 bits, q=10 -6 » What is the link throughput under RDT 3. 0 » What is the best possible throughput if the maximum packet size is 12, 000 bits? 26

Exercise 4. 1 Gb/s link with 20 ms RTT, L=10, 000 bits, q=10 -6 » What is the link throughput under RDT 3. 0 Throughput = C(1 -q)/(1+RTT/tpkt)=109(1 -10 -6)/(1+2 x 10 -2/10 -5) ~ 109/2001~500 kbps » What is the best possible throughput if the maximum packet size is 12, 000 bits? If q is unchanged, the only difference is that tpkt increases to 1. 2 x 10 -5, so that the throughput is now about 600 kbps. Still about 2000 times slower than the link capacity! If we assume q=0, the throughput hardly improves since 1 -10 -6~1 -0 27
- Slides: 27