80386 DX Programming Model The basic programming model

80386 DX
Programming Model • The basic programming model consists of the following aspects: – Registers – Instruction Set – Addressing Modes – Data Types – Memory Organization – Interrupts and Exceptions 2
Programming Model • The basic programming model consists of the following aspects: – Registers – Instruction Set – Addressing Modes – Data Types – Memory Organization – Interrupts and Exceptions 3

Register Overview • The Intel 386 DX has 32 register resources in the following categories: – General Purpose Registers – Segment Registers – Instruction Pointer and Flags – Control Registers – System Address Registers – Debug Registers – Test Registers 4
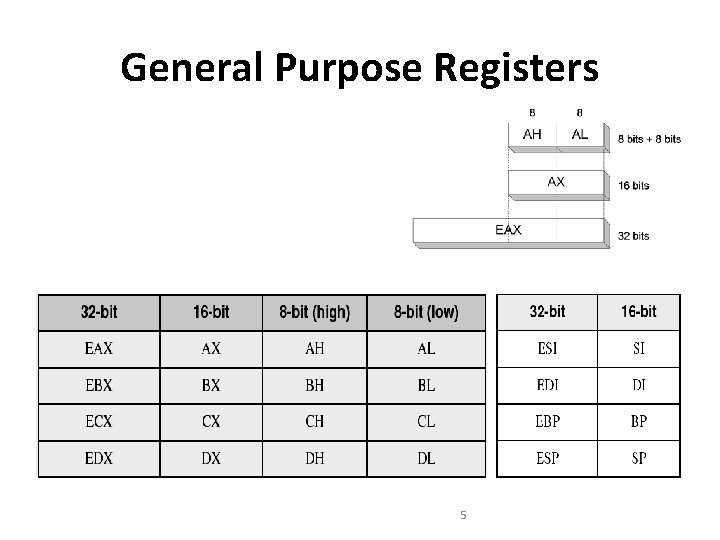
General Purpose Registers 5
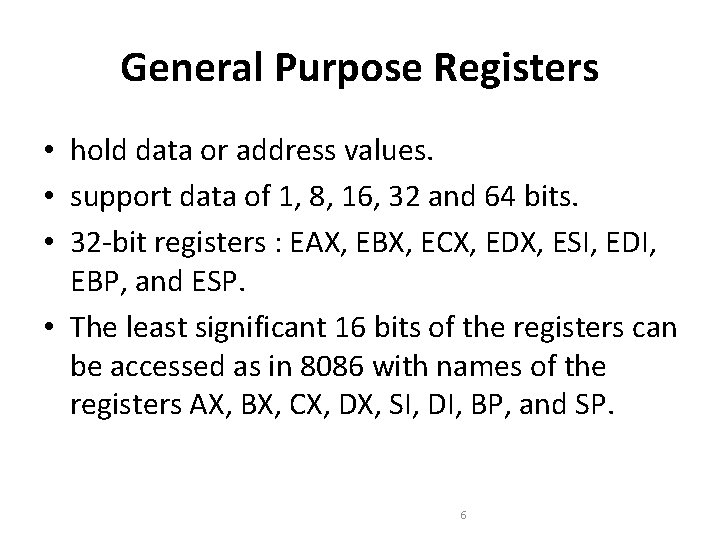
General Purpose Registers • hold data or address values. • support data of 1, 8, 16, 32 and 64 bits. • 32 -bit registers : EAX, EBX, ECX, EDX, ESI, EDI, EBP, and ESP. • The least significant 16 bits of the registers can be accessed as in 8086 with names of the registers AX, BX, CX, DX, SI, DI, BP, and SP. 6
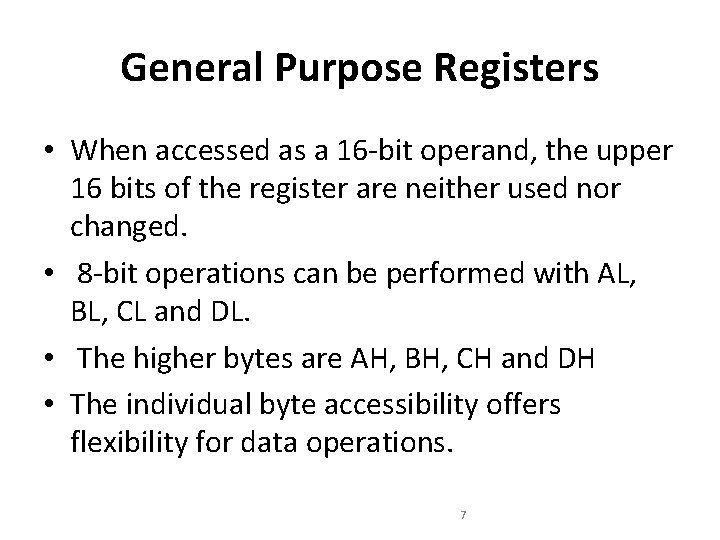
General Purpose Registers • When accessed as a 16 -bit operand, the upper 16 bits of the register are neither used nor changed. • 8 -bit operations can be performed with AL, BL, CL and DL. • The higher bytes are AH, BH, CH and DH • The individual byte accessibility offers flexibility for data operations. 7
Segment Registers 8
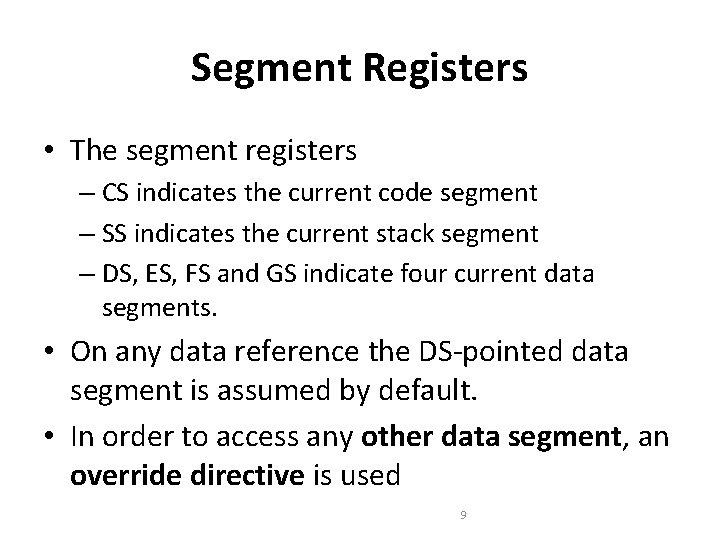
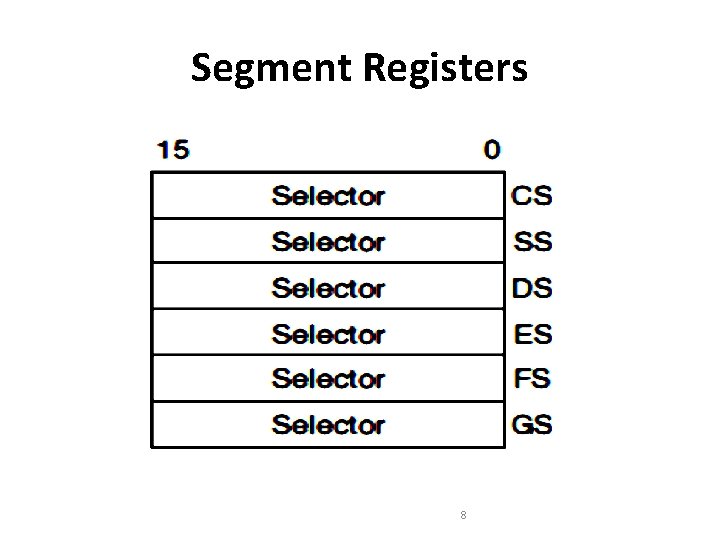
Segment Registers • The segment registers – CS indicates the current code segment – SS indicates the current stack segment – DS, ES, FS and GS indicate four current data segments. • On any data reference the DS-pointed data segment is assumed by default. • In order to access any other data segment, an override directive is used 9
Instruction Pointer 10
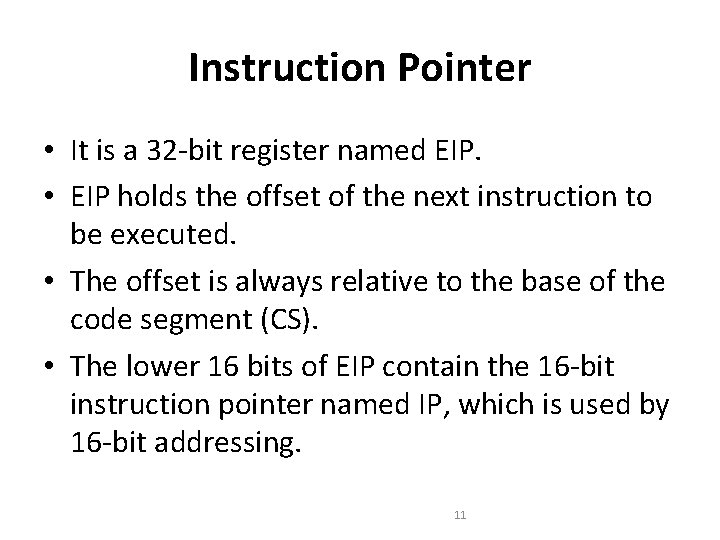
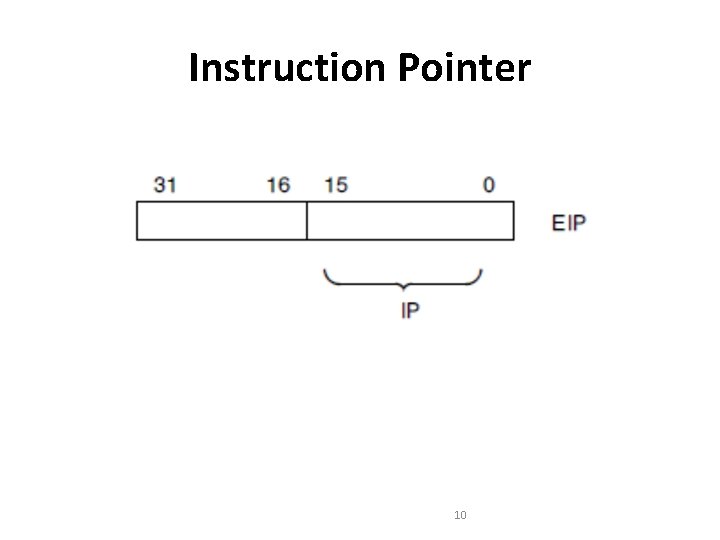
Instruction Pointer • It is a 32 -bit register named EIP. • EIP holds the offset of the next instruction to be executed. • The offset is always relative to the base of the code segment (CS). • The lower 16 bits of EIP contain the 16 -bit instruction pointer named IP, which is used by 16 -bit addressing. 11
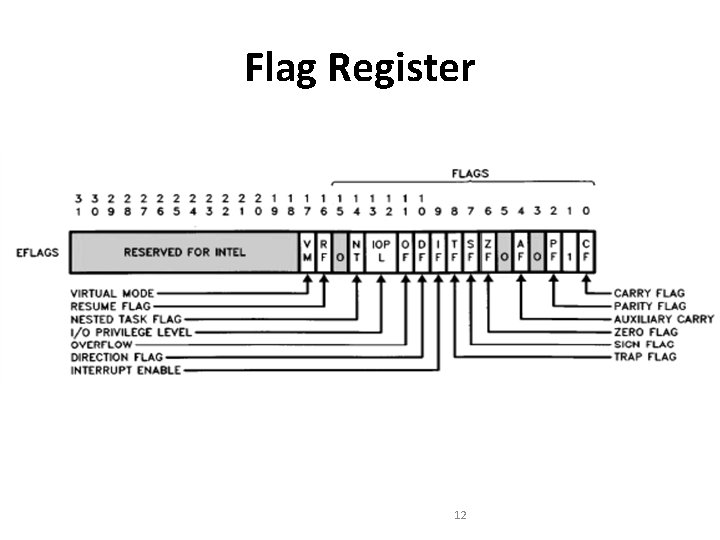
Flag Register 12
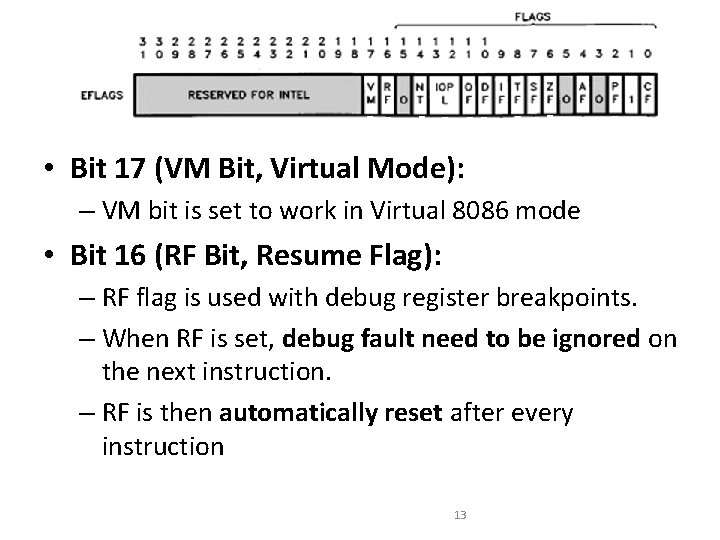
• Bit 17 (VM Bit, Virtual Mode): – VM bit is set to work in Virtual 8086 mode • Bit 16 (RF Bit, Resume Flag): – RF flag is used with debug register breakpoints. – When RF is set, debug fault need to be ignored on the next instruction. – RF is then automatically reset after every instruction 13
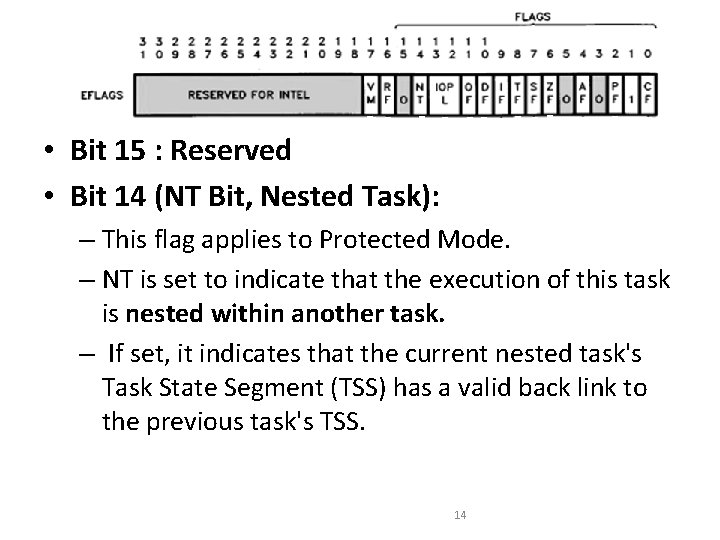
Flag Register • Bit 15 : Reserved • Bit 14 (NT Bit, Nested Task): – This flag applies to Protected Mode. – NT is set to indicate that the execution of this task is nested within another task. – If set, it indicates that the current nested task's Task State Segment (TSS) has a valid back link to the previous task's TSS. 14
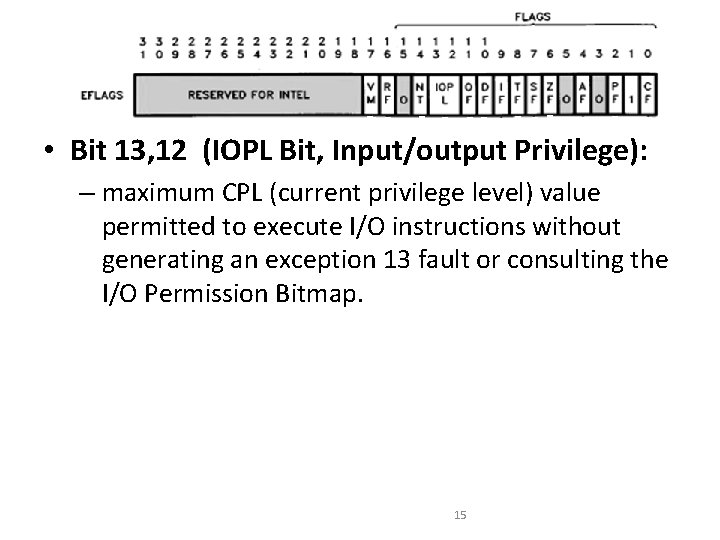
• Bit 13, 12 (IOPL Bit, Input/output Privilege): – maximum CPL (current privilege level) value permitted to execute I/O instructions without generating an exception 13 fault or consulting the I/O Permission Bitmap. 15
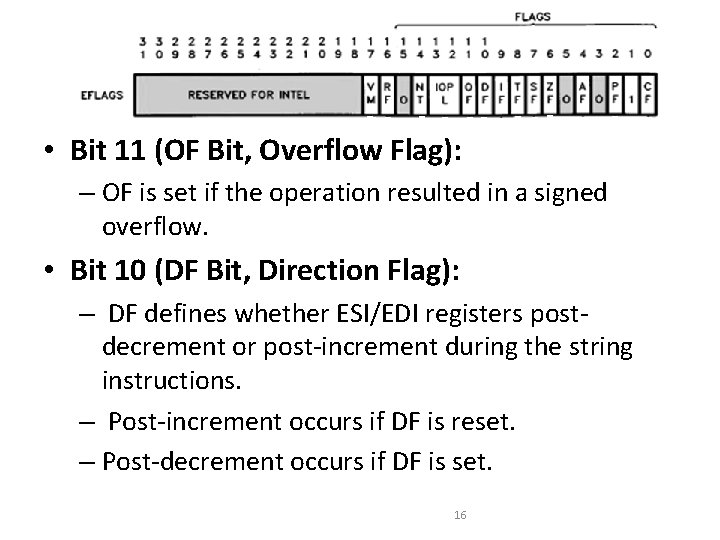
• Bit 11 (OF Bit, Overflow Flag): – OF is set if the operation resulted in a signed overflow. • Bit 10 (DF Bit, Direction Flag): – DF defines whether ESI/EDI registers postdecrement or post-increment during the string instructions. – Post-increment occurs if DF is reset. – Post-decrement occurs if DF is set. 16
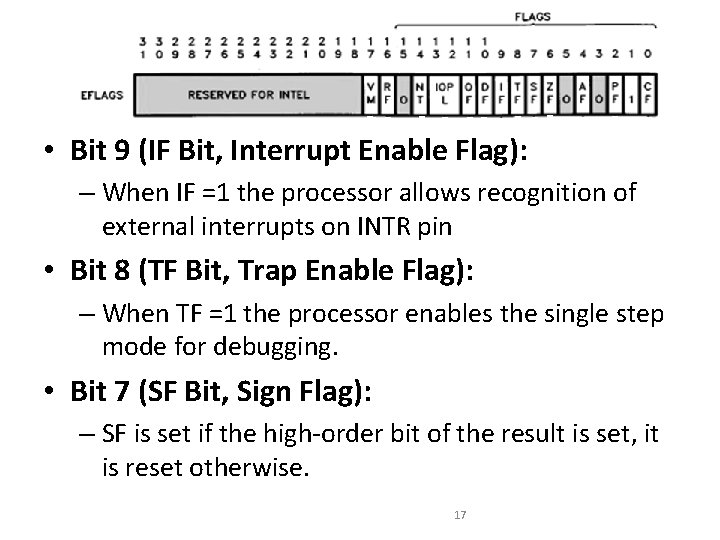
Flag Register • Bit 9 (IF Bit, Interrupt Enable Flag): – When IF =1 the processor allows recognition of external interrupts on INTR pin • Bit 8 (TF Bit, Trap Enable Flag): – When TF =1 the processor enables the single step mode for debugging. • Bit 7 (SF Bit, Sign Flag): – SF is set if the high-order bit of the result is set, it is reset otherwise. 17
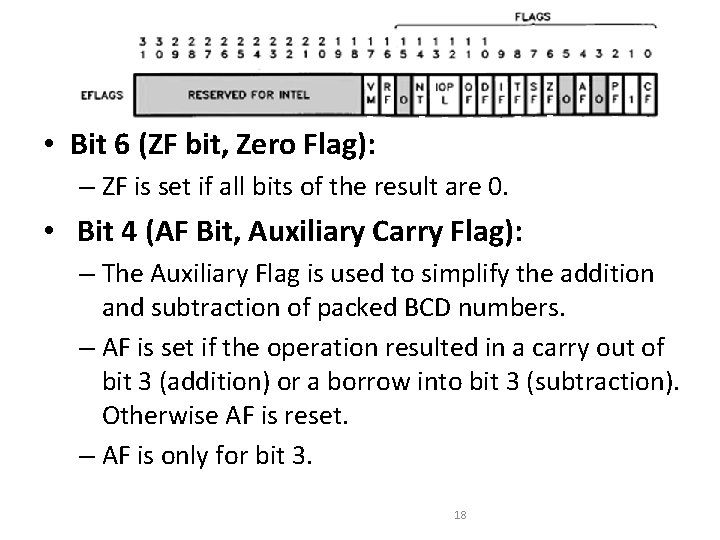
Flag Register • Bit 6 (ZF bit, Zero Flag): – ZF is set if all bits of the result are 0. • Bit 4 (AF Bit, Auxiliary Carry Flag): – The Auxiliary Flag is used to simplify the addition and subtraction of packed BCD numbers. – AF is set if the operation resulted in a carry out of bit 3 (addition) or a borrow into bit 3 (subtraction). Otherwise AF is reset. – AF is only for bit 3. 18
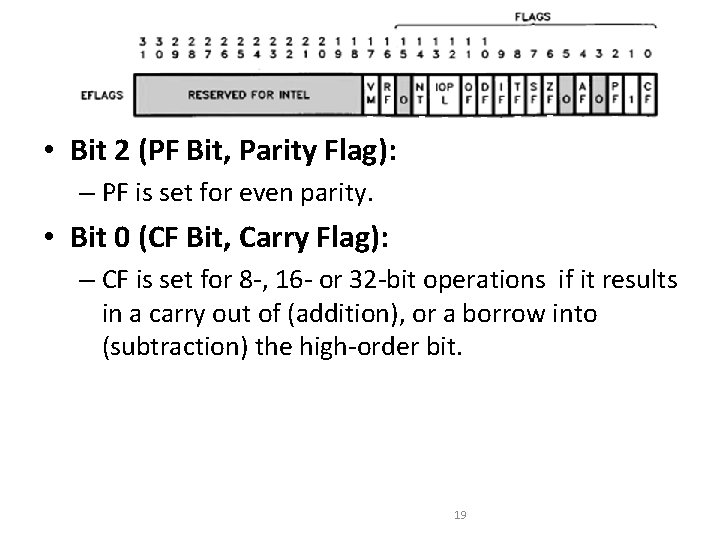
Flag Register • Bit 2 (PF Bit, Parity Flag): – PF is set for even parity. • Bit 0 (CF Bit, Carry Flag): – CF is set for 8 -, 16 - or 32 -bit operations if it results in a carry out of (addition), or a borrow into (subtraction) the high-order bit. 19
Control Registers • Intel 386 DX has 3 control registers(CR 0, CR 2 and CR 3) of 32 bits to hold machine state of a global nature • These registers along with System Address Registers hold machine state that affects all tasks in the system • To access Control Registers, load and store instructions are defined 20
CR 0 : Machine Control Register • CR 0 contains 6 defined bits for control and status purposes. • The low-order 16 bits of CR 0 is defined as Machine Status Word • To operate only on the low-order 16 -bits of CR 0, LMSW and SMSW instructions are used. • For 32 -bit operations the system should use MOV CR 0, Reg instruction. 21
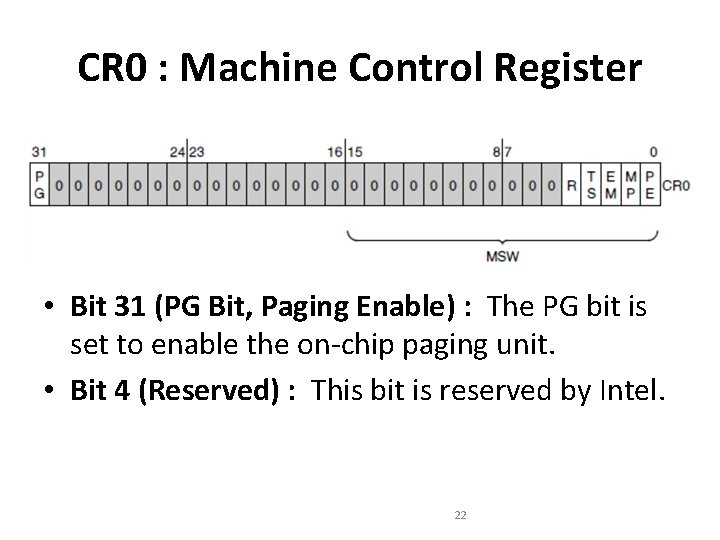
CR 0 : Machine Control Register • Bit 31 (PG Bit, Paging Enable) : The PG bit is set to enable the on-chip paging unit. • Bit 4 (Reserved) : This bit is reserved by Intel. 22
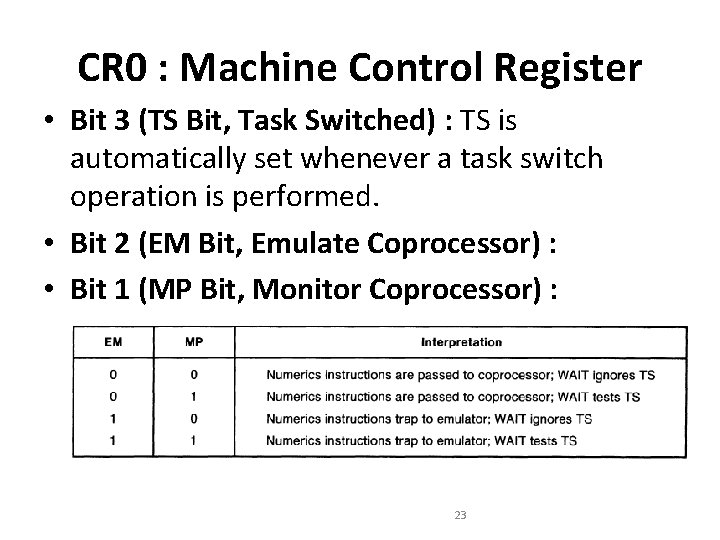
CR 0 : Machine Control Register • Bit 3 (TS Bit, Task Switched) : TS is automatically set whenever a task switch operation is performed. • Bit 2 (EM Bit, Emulate Coprocessor) : • Bit 1 (MP Bit, Monitor Coprocessor) : 23

CR 0 : Machine Control Register • Bit 0 (PE Bit, Protection Enable) : – PE =1, enable the Protected Mode. – If PE =0, processor operates in Real Mode. 24
CR 1 : Reserved • CR 1 is reserved for use in future Intel processors 25
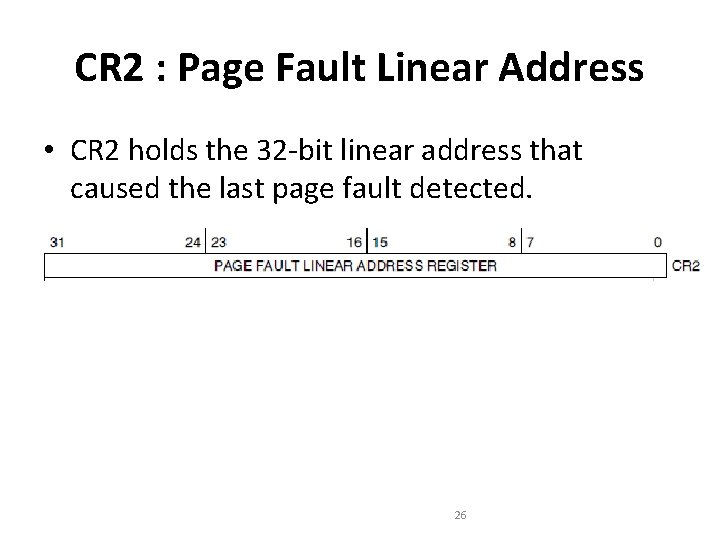
CR 2 : Page Fault Linear Address • CR 2 holds the 32 -bit linear address that caused the last page fault detected. 26
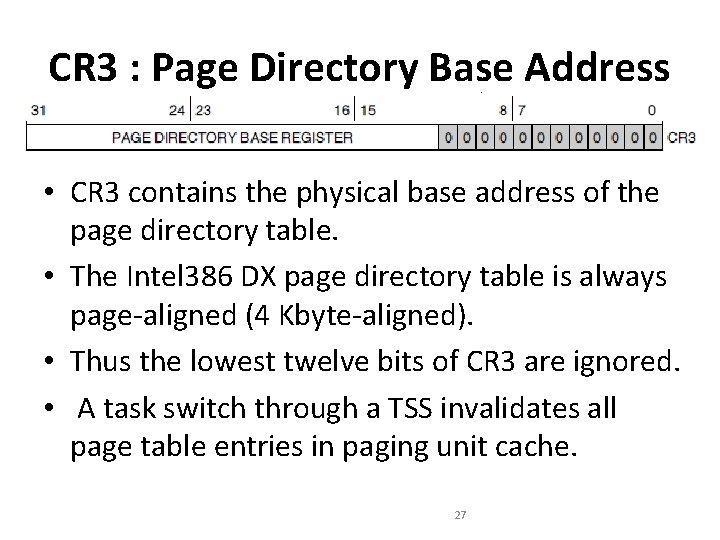
CR 3 : Page Directory Base Address • CR 3 contains the physical base address of the page directory table. • The Intel 386 DX page directory table is always page-aligned (4 Kbyte-aligned). • Thus the lowest twelve bits of CR 3 are ignored. • A task switch through a TSS invalidates all page table entries in paging unit cache. 27

System Address Registers • Four special registers are defined to reference the tables. • These tables or segments are: – GDT (Global Descriptor Table) – IDT (Interrupt Descriptor Table) – LDT (Local Descriptor Table) – TSS (Task State Segment) 28

System Address Registers • The addresses of these tables and segments are stored in special registers, the System Address and System Segment Registers. • These registers are named GDTR, IDTR, LDTR and TR, respectively 29

GDTR and IDTR • These registers hold: – 32 -bit linear base address and – 16 -bit limit of GDT and IDT respectively. • GDT and IDT segments are global to all tasks in the system. 30
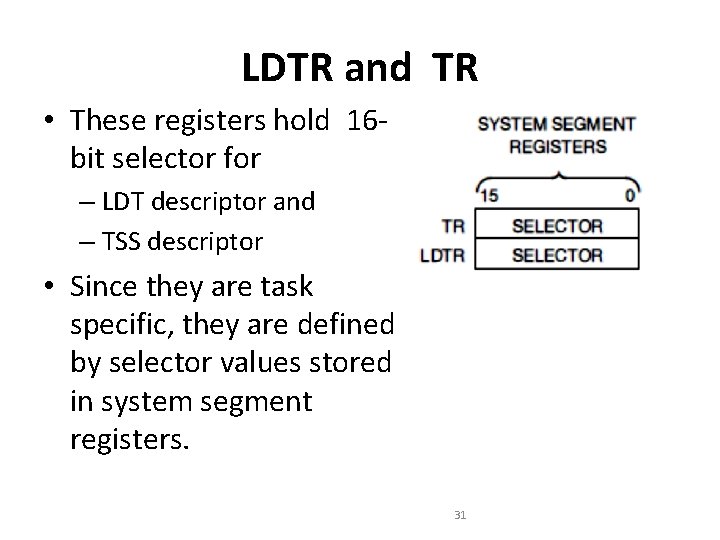
LDTR and TR • These registers hold 16 bit selector for – LDT descriptor and – TSS descriptor • Since they are task specific, they are defined by selector values stored in system segment registers. 31
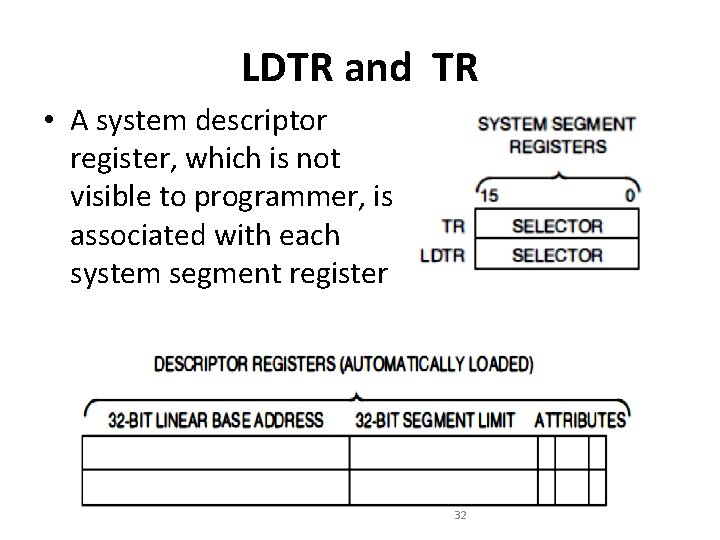
LDTR and TR • A system descriptor register, which is not visible to programmer, is associated with each system segment register 32

Debug Registers • Debugging of 80386 allows data access breakpoints as well as code execution breakpoints. • 80386 contains 6 debug registers to specify – 4 breakpoints – Breakpoint Control options – Breakpoint Status
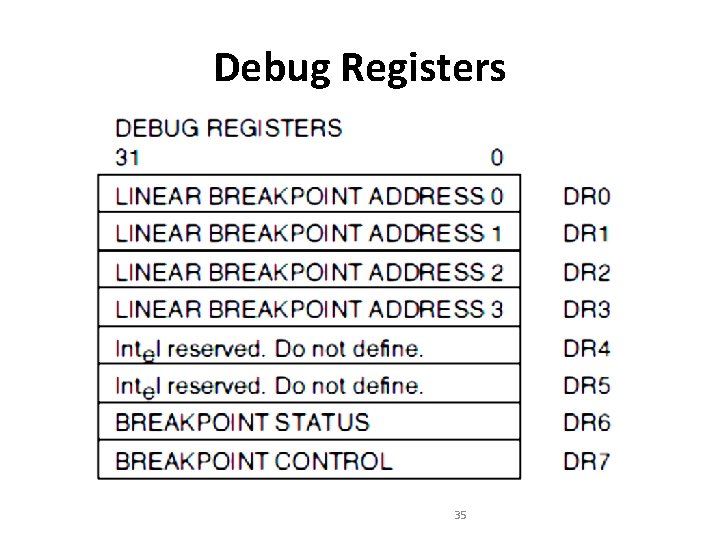
Debug Registers 35
Linear Breakpoint Address Registers • Breakpoint addresses are 32 -bit linear addresses • While debugging, Intel 386 h/w continuously compares the linear breakpoint addresses in DR 0 -DR 3 with the linear addresses generated by executing software. 36
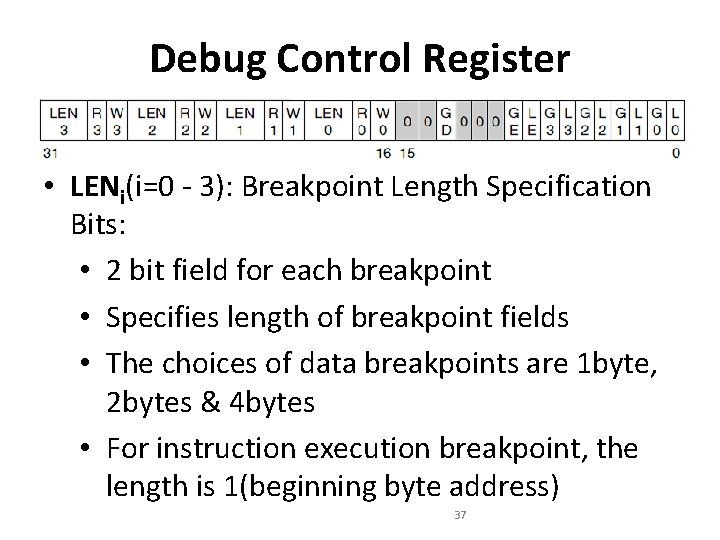
Debug Control Register • LENi(i=0 - 3): Breakpoint Length Specification Bits: • 2 bit field for each breakpoint • Specifies length of breakpoint fields • The choices of data breakpoints are 1 byte, 2 bytes & 4 bytes • For instruction execution breakpoint, the length is 1(beginning byte address) 37
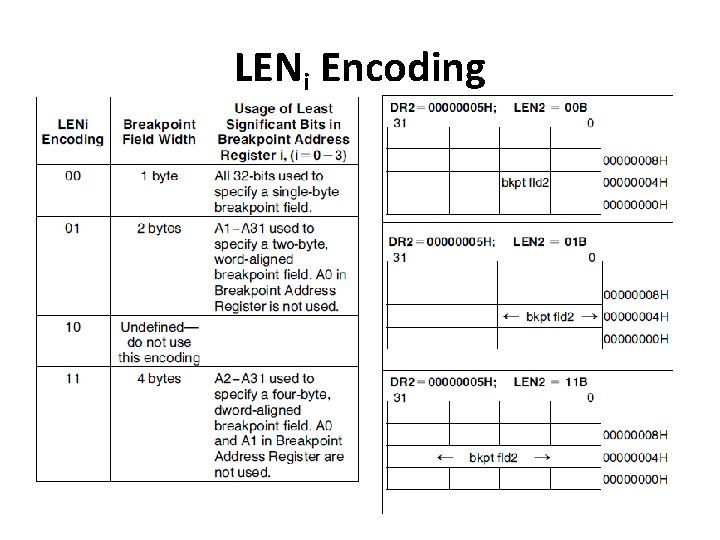
LENi Encoding
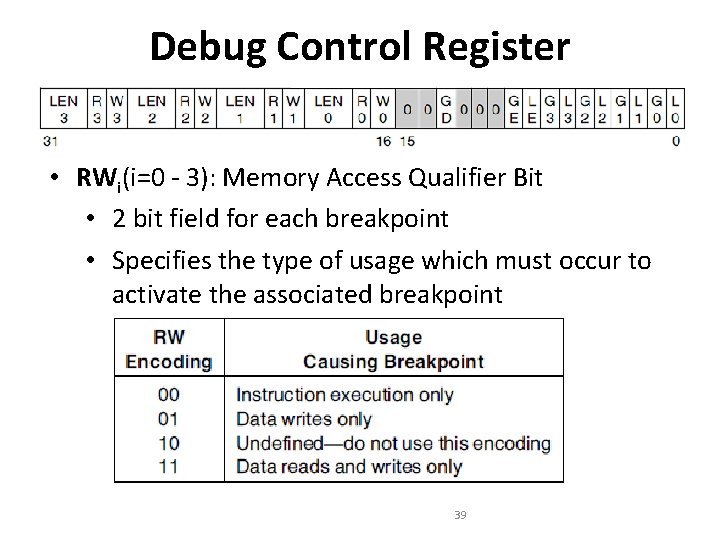
Debug Control Register • RWi(i=0 - 3): Memory Access Qualifier Bit • 2 bit field for each breakpoint • Specifies the type of usage which must occur to activate the associated breakpoint 39
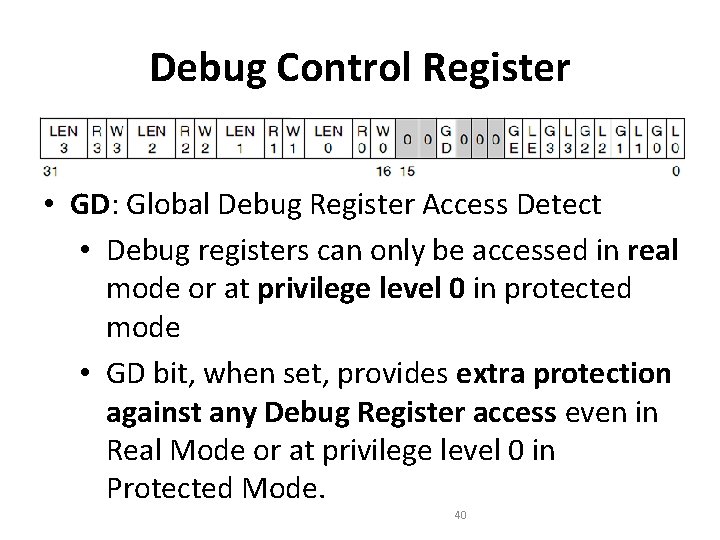
Debug Control Register • GD: Global Debug Register Access Detect • Debug registers can only be accessed in real mode or at privilege level 0 in protected mode • GD bit, when set, provides extra protection against any Debug Register access even in Real Mode or at privilege level 0 in Protected Mode. 40
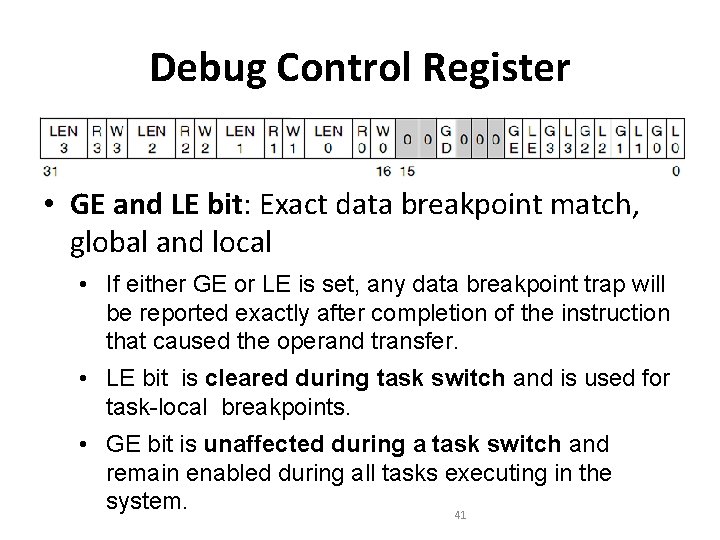
Debug Control Register • GE and LE bit: Exact data breakpoint match, global and local • If either GE or LE is set, any data breakpoint trap will be reported exactly after completion of the instruction that caused the operand transfer. • LE bit is cleared during task switch and is used for task-local breakpoints. • GE bit is unaffected during a task switch and remain enabled during all tasks executing in the system. 41
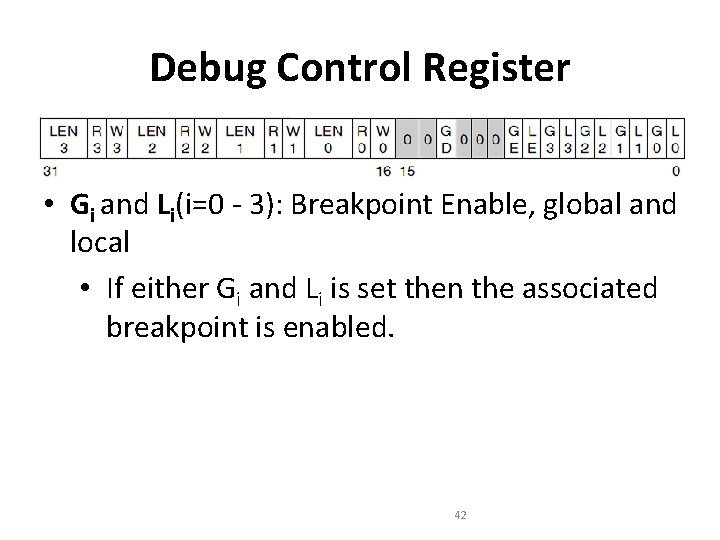
Debug Control Register • Gi and Li(i=0 - 3): Breakpoint Enable, global and local • If either Gi and Li is set then the associated breakpoint is enabled. 42
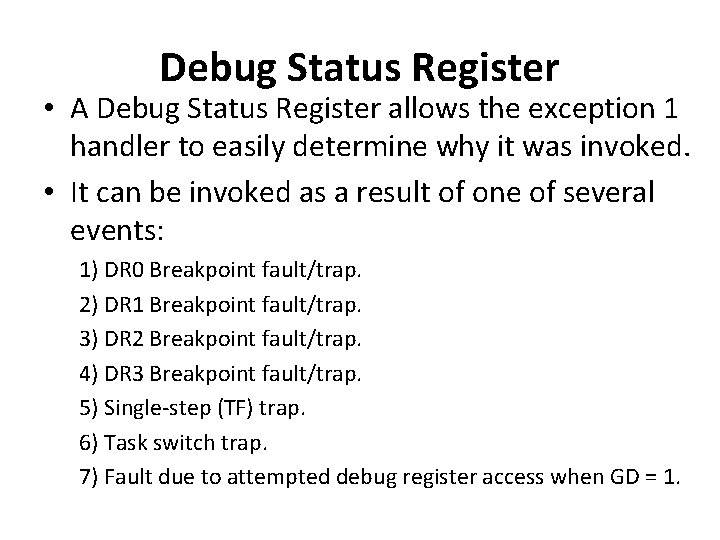
Debug Status Register • A Debug Status Register allows the exception 1 handler to easily determine why it was invoked. • It can be invoked as a result of one of several events: 1) DR 0 Breakpoint fault/trap. 2) DR 1 Breakpoint fault/trap. 3) DR 2 Breakpoint fault/trap. 4) DR 3 Breakpoint fault/trap. 5) Single-step (TF) trap. 6) Task switch trap. 7) Fault due to attempted debug register access when GD = 1.
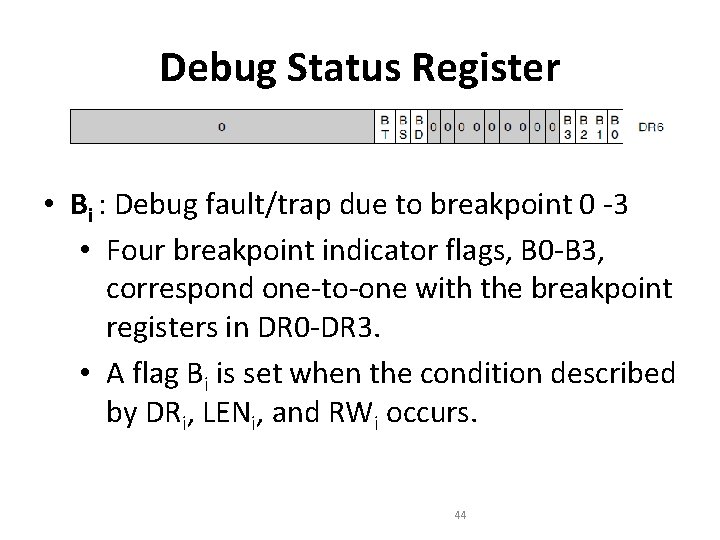
Debug Status Register • Bi : Debug fault/trap due to breakpoint 0 -3 • Four breakpoint indicator flags, B 0 -B 3, correspond one-to-one with the breakpoint registers in DR 0 -DR 3. • A flag Bi is set when the condition described by DRi, LENi, and RWi occurs. 44
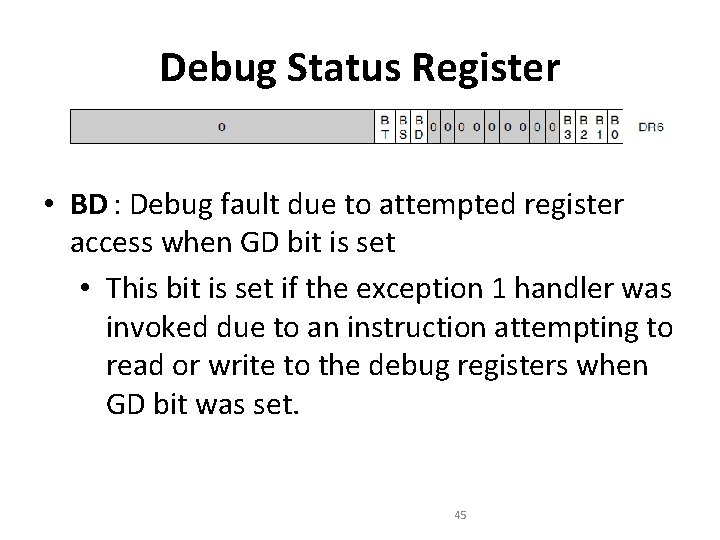
Debug Status Register • BD : Debug fault due to attempted register access when GD bit is set • This bit is set if the exception 1 handler was invoked due to an instruction attempting to read or write to the debug registers when GD bit was set. 45
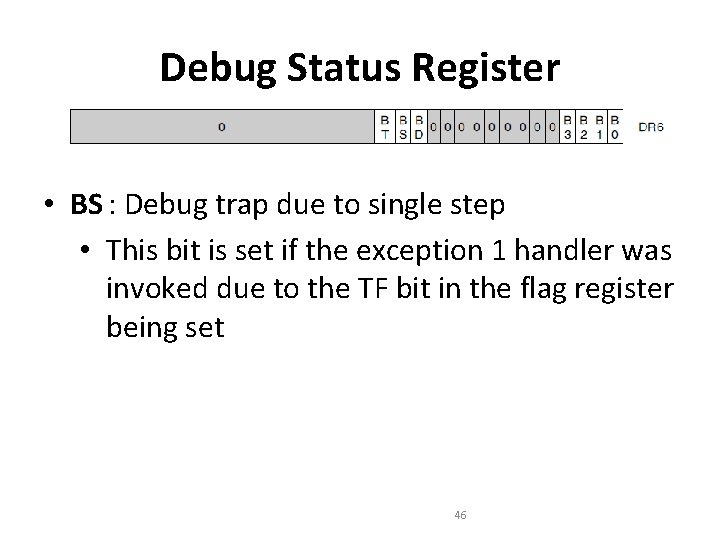
Debug Status Register • BS : Debug trap due to single step • This bit is set if the exception 1 handler was invoked due to the TF bit in the flag register being set 46
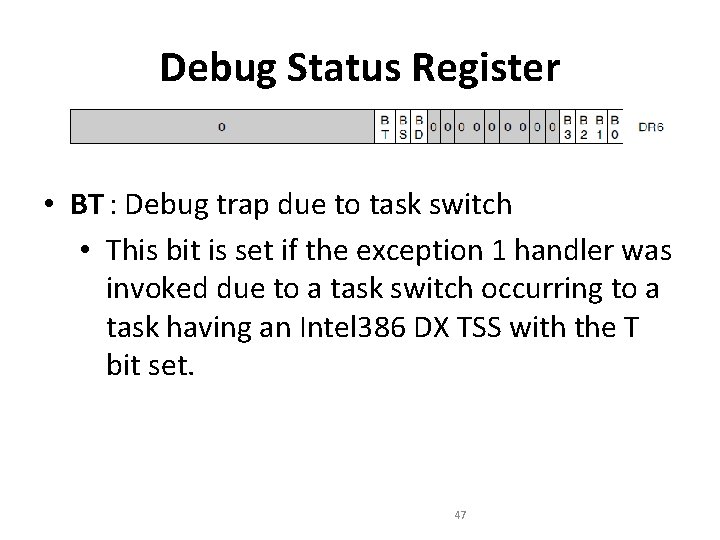
Debug Status Register • BT : Debug trap due to task switch • This bit is set if the exception 1 handler was invoked due to a task switch occurring to a task having an Intel 386 DX TSS with the T bit set. 47
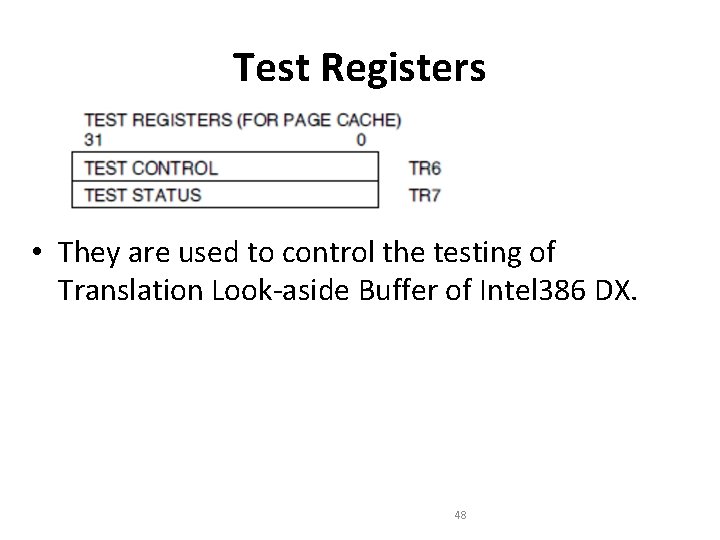
Test Registers • They are used to control the testing of Translation Look-aside Buffer of Intel 386 DX. 48
Programming Model • The basic programming model consists of the following aspects: – Registers – Instruction Set – Addressing Modes – Data Types – Memory Organization – Interrupts and Exceptions 49
Programming Model • The basic programming model consists of the following aspects: – Registers – Instruction Set – Addressing Modes – Data Types – Memory Organization – Interrupts and Exceptions 50
Addressing Modes • The Intel 386 DX provides 11 addressing modes for instructions to specify operands. • Register Operand Mode: • The operand is located in one of the 8 -, 16 - or 32 bit general registers. • Example : ADD EAX, EBX • Immediate Operand Mode: • The operand is included in the instruction as part of the opcode. • Example : CLI, STI 51
Addressing Modes The remaining 9 modes provide a mechanism for specifying the effective address of an operand. • The linear address consists of two components: • • the segment base address and • an effective address. 52
Addressing Modes • The effective address is calculated by using four address elements: • DISPLACEMENT: An 8 -, or 32 -bit immediate value • BASE: The contents of any general purpose register. It point to the start of the local variable area. • INDEX: The contents of any general purpose register except for ESP. The index registers are used to access the elements of an array, or a string of characters. • SCALE: The index register's value can be multiplied by a scale factor, either 1, 2, 4 or 8. Scaled index mode is especially useful for accessing arrays or structures. 53
Addressing Modes • Combinations of these 4 components make up the 9 additional addressing modes • The effective address (EA) of an operand is calculated according to the following formula: EA = Base Register+ (Index Register * Scaling) + Displacement. • This calculation can be shown as follows: 54
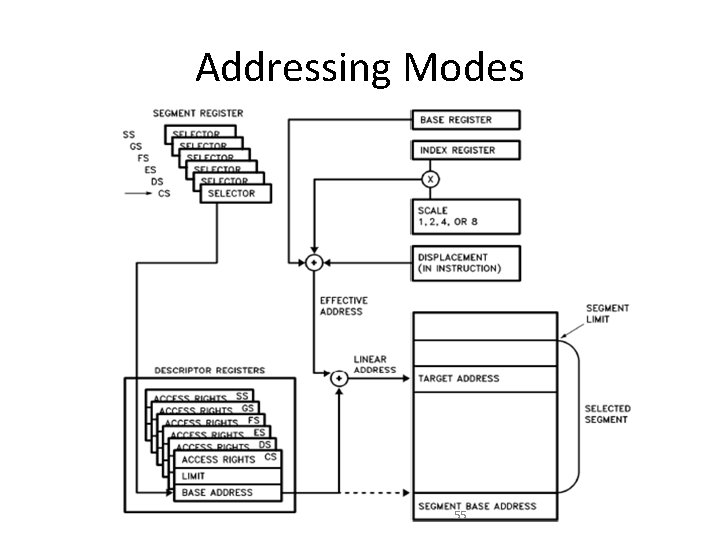
Addressing Modes 55
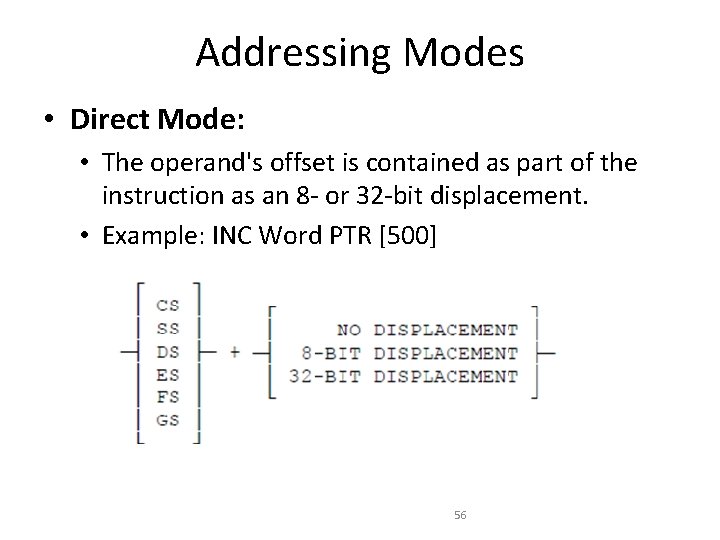
Addressing Modes • Direct Mode: • The operand's offset is contained as part of the instruction as an 8 - or 32 -bit displacement. • Example: INC Word PTR [500] 56
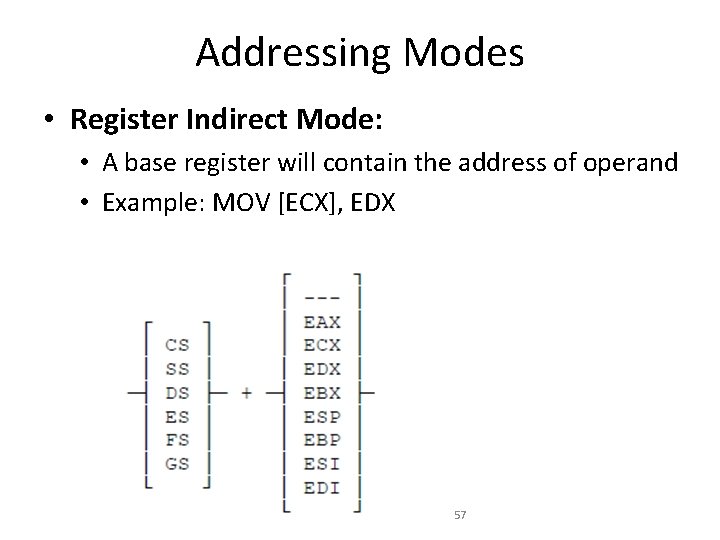
Addressing Modes • Register Indirect Mode: • A base register will contain the address of operand • Example: MOV [ECX], EDX 57
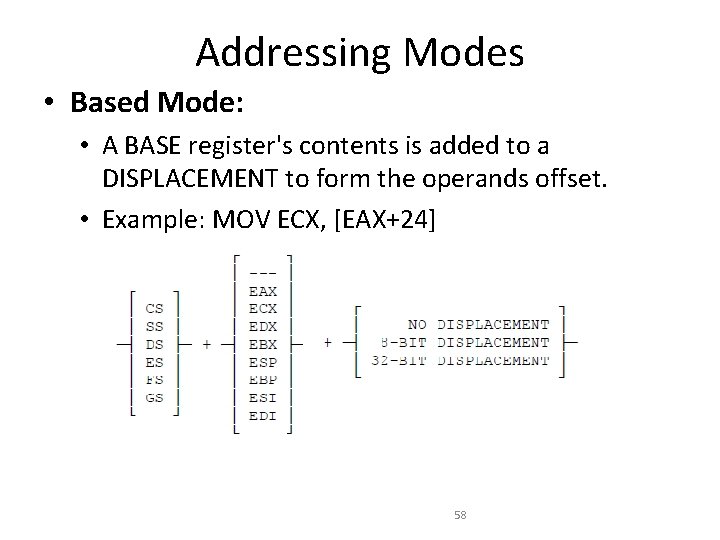
Addressing Modes • Based Mode: • A BASE register's contents is added to a DISPLACEMENT to form the operands offset. • Example: MOV ECX, [EAX+24] 58
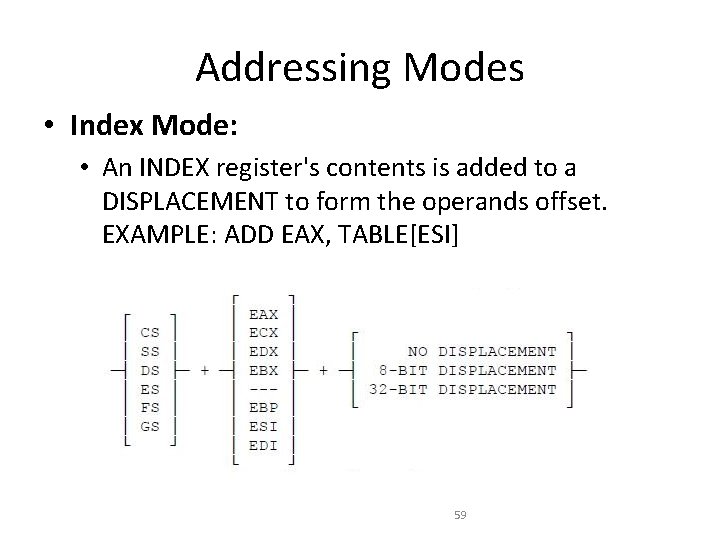
Addressing Modes • Index Mode: • An INDEX register's contents is added to a DISPLACEMENT to form the operands offset. EXAMPLE: ADD EAX, TABLE[ESI] 59
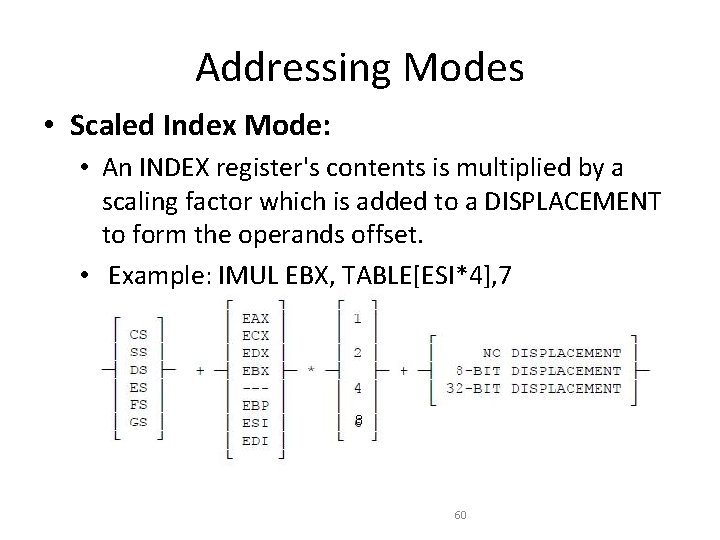
Addressing Modes • Scaled Index Mode: • An INDEX register's contents is multiplied by a scaling factor which is added to a DISPLACEMENT to form the operands offset. • Example: IMUL EBX, TABLE[ESI*4], 7 8 60
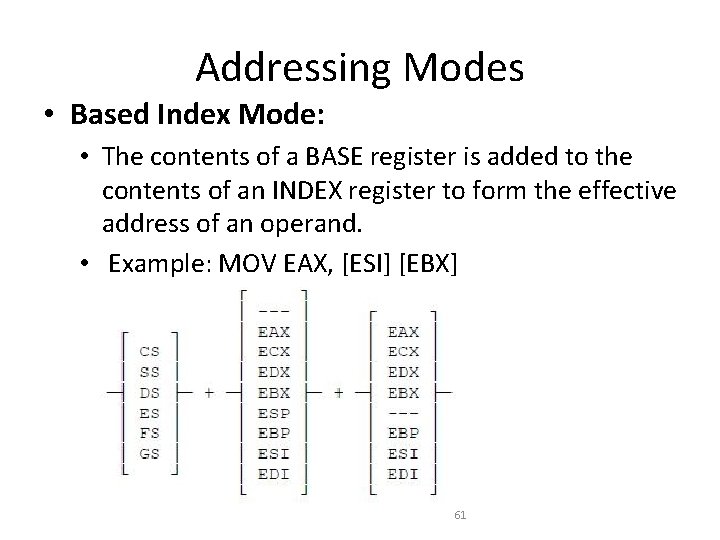
Addressing Modes • Based Index Mode: • The contents of a BASE register is added to the contents of an INDEX register to form the effective address of an operand. • Example: MOV EAX, [ESI] [EBX] 61
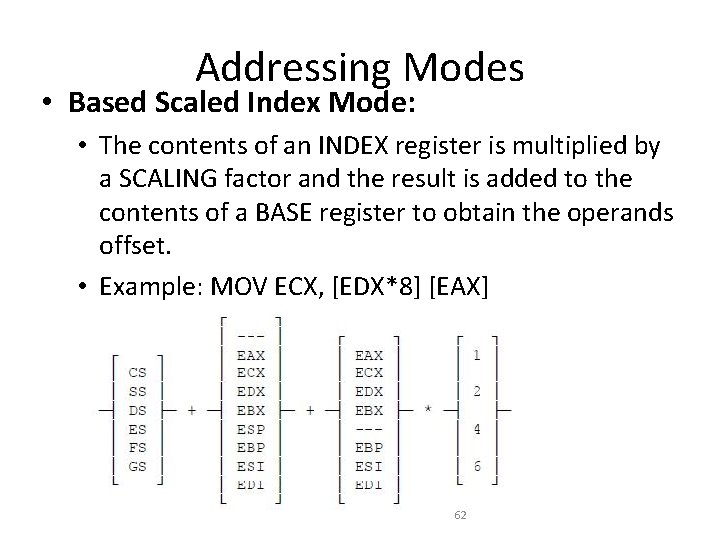
Addressing Modes • Based Scaled Index Mode: • The contents of an INDEX register is multiplied by a SCALING factor and the result is added to the contents of a BASE register to obtain the operands offset. • Example: MOV ECX, [EDX*8] [EAX] 62
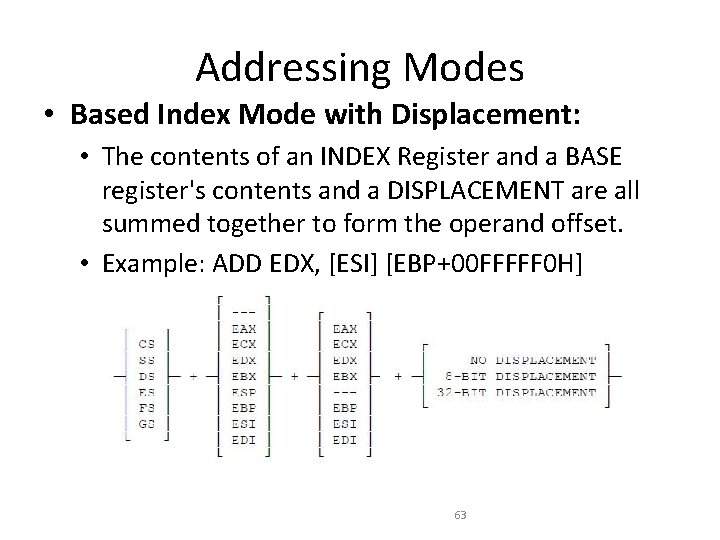
Addressing Modes • Based Index Mode with Displacement: • The contents of an INDEX Register and a BASE register's contents and a DISPLACEMENT are all summed together to form the operand offset. • Example: ADD EDX, [ESI] [EBP+00 FFFFF 0 H] 63
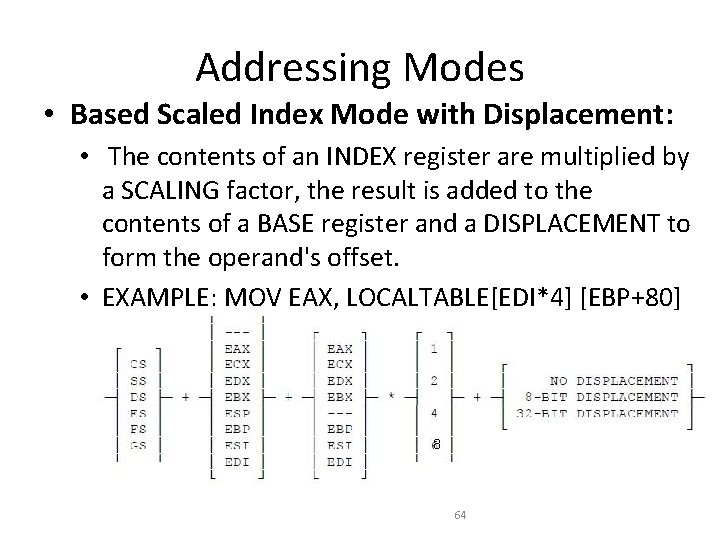
Addressing Modes • Based Scaled Index Mode with Displacement: • The contents of an INDEX register are multiplied by a SCALING factor, the result is added to the contents of a BASE register and a DISPLACEMENT to form the operand's offset. • EXAMPLE: MOV EAX, LOCALTABLE[EDI*4] [EBP+80] 8 64
Programming Model • The basic programming model consists of the following aspects: – Registers – Instruction Format – Addressing Modes – Data types – Memory organization and segmentation – Interrupts and Exceptions 65
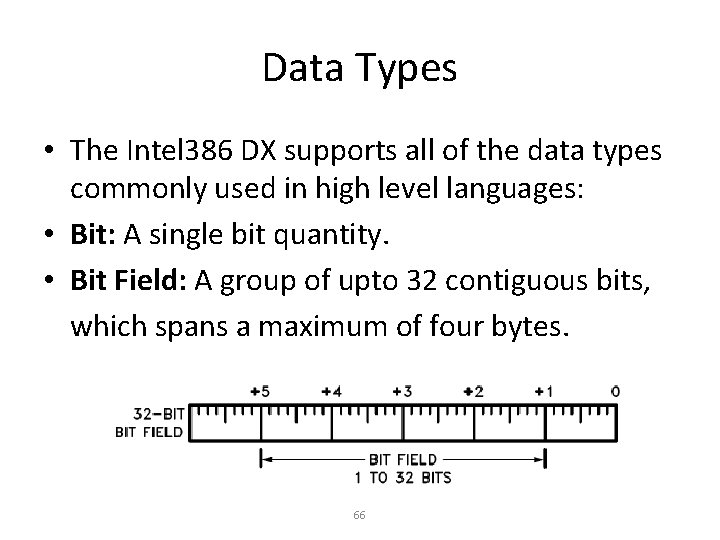
Data Types • The Intel 386 DX supports all of the data types commonly used in high level languages: • Bit: A single bit quantity. • Bit Field: A group of upto 32 contiguous bits, which spans a maximum of four bytes. 66
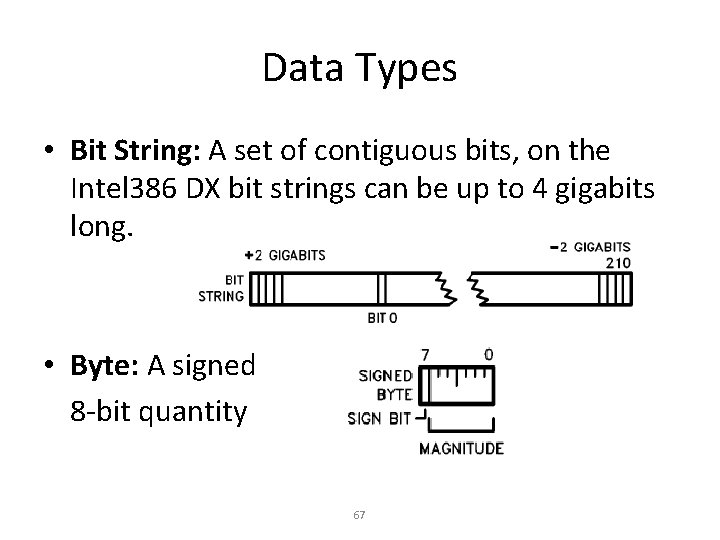
Data Types • Bit String: A set of contiguous bits, on the Intel 386 DX bit strings can be up to 4 gigabits long. • Byte: A signed 8 -bit quantity 67
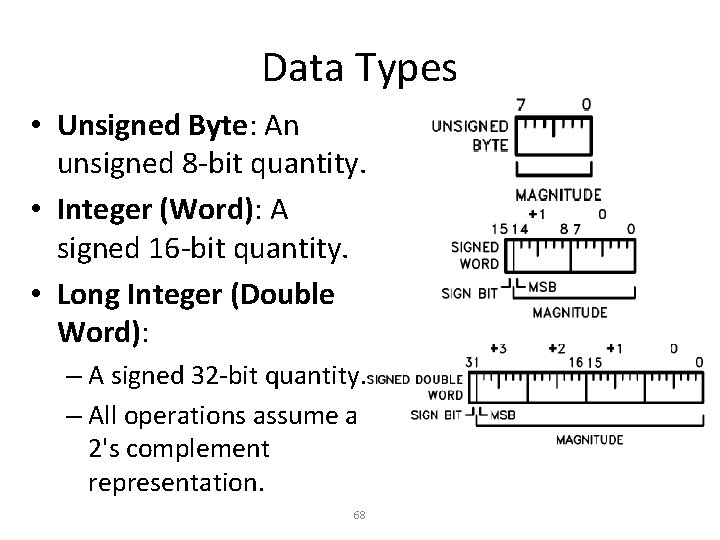
Data Types • Unsigned Byte: An unsigned 8 -bit quantity. • Integer (Word): A signed 16 -bit quantity. • Long Integer (Double Word): – A signed 32 -bit quantity. – All operations assume a 2's complement representation. 68
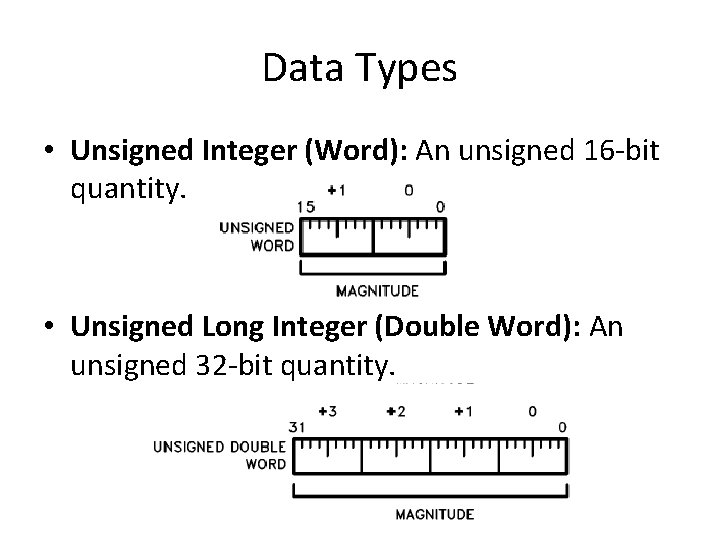
Data Types • Unsigned Integer (Word): An unsigned 16 -bit quantity. • Unsigned Long Integer (Double Word): An unsigned 32 -bit quantity. 69
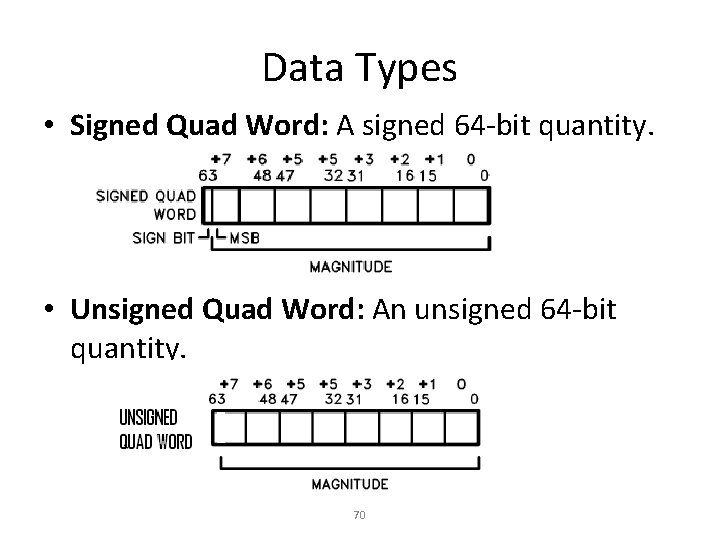
Data Types • Signed Quad Word: A signed 64 -bit quantity. • Unsigned Quad Word: An unsigned 64 -bit quantity. 70
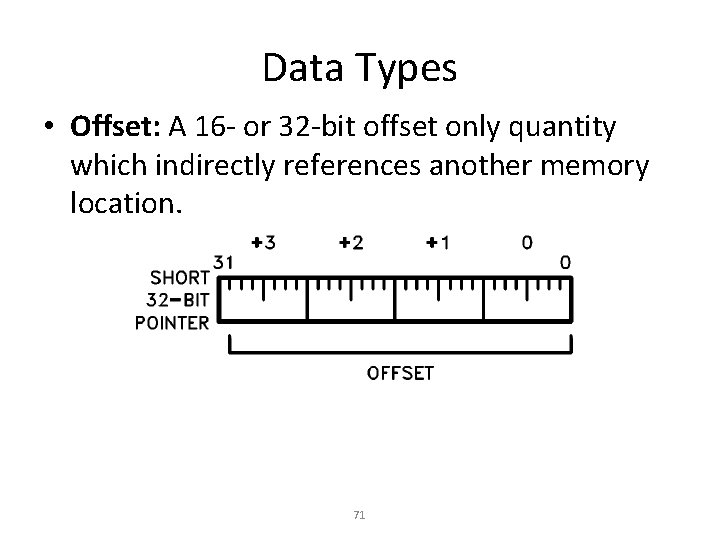
Data Types • Offset: A 16 - or 32 -bit offset only quantity which indirectly references another memory location. 71
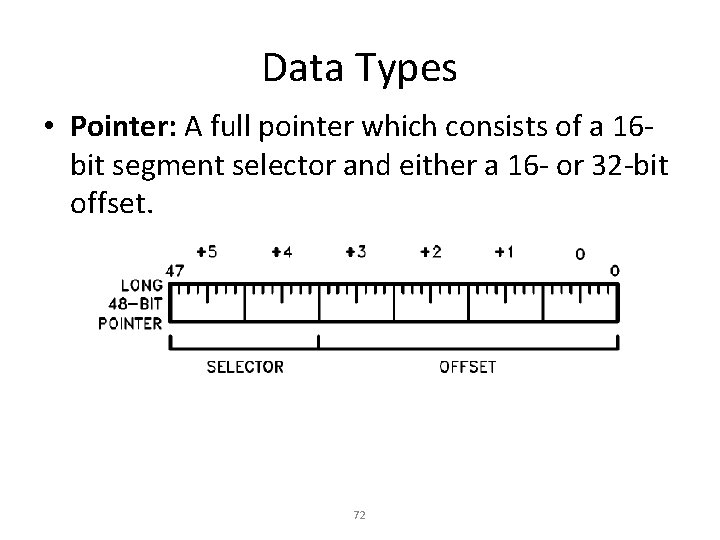
Data Types • Pointer: A full pointer which consists of a 16 bit segment selector and either a 16 - or 32 -bit offset. 72
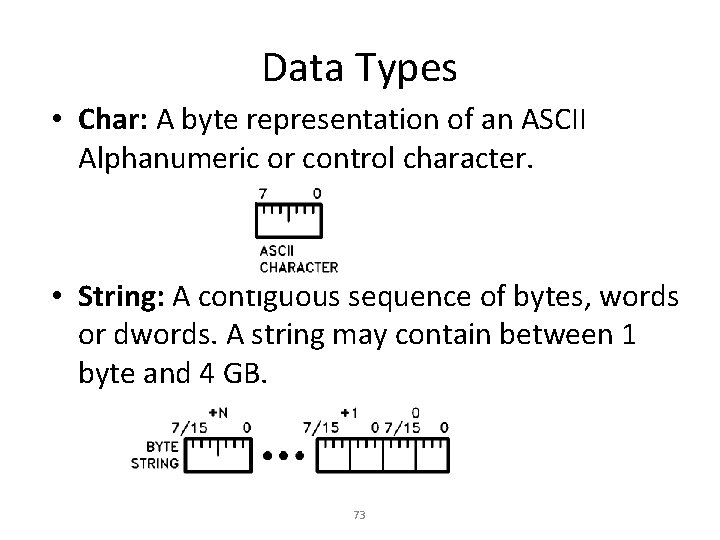
Data Types • Char: A byte representation of an ASCII Alphanumeric or control character. • String: A contiguous sequence of bytes, words or dwords. A string may contain between 1 byte and 4 GB. 73
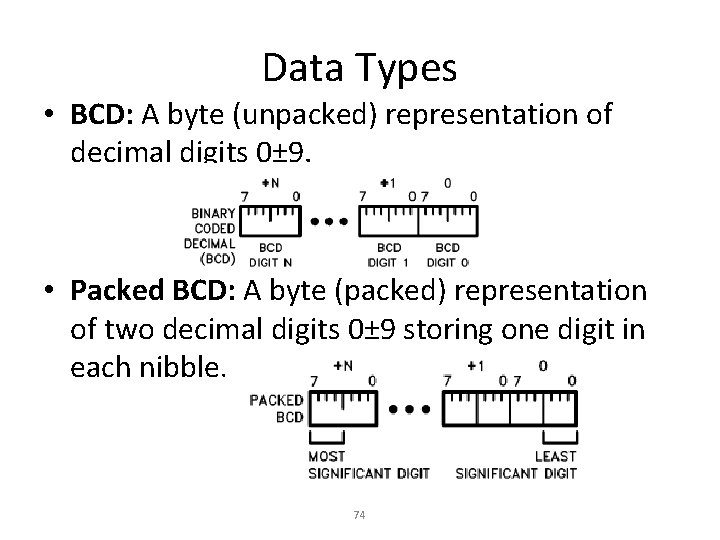
Data Types • BCD: A byte (unpacked) representation of decimal digits 0± 9. • Packed BCD: A byte (packed) representation of two decimal digits 0± 9 storing one digit in each nibble. 74
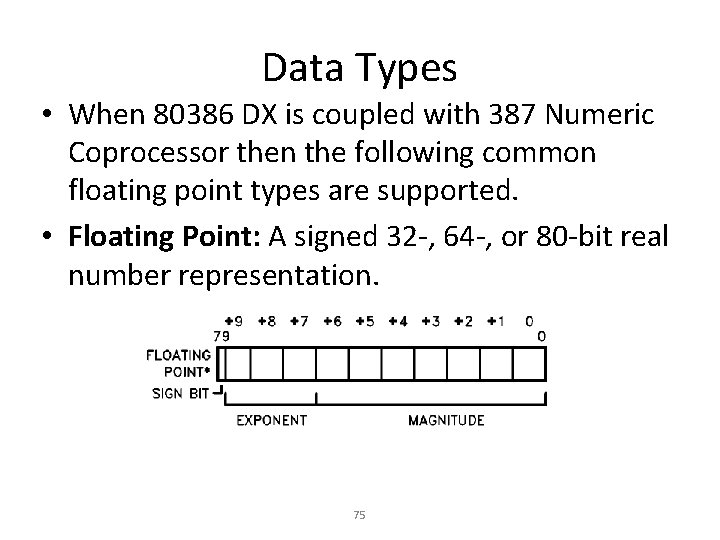
Data Types • When 80386 DX is coupled with 387 Numeric Coprocessor then the following common floating point types are supported. • Floating Point: A signed 32 -, 64 -, or 80 -bit real number representation. 75
Programming Model • The basic programming model consists of the following aspects: – Registers – Instruction Format – Addressing Modes – Data types – Memory Organization and Segmentation – Interrupts and Exceptions 76
- Slides: 76