802 11 DenialofService Attacks Real Vulnerabilities and Practical

802. 11 Denial-of-Service Attacks: Real Vulnerabilities and Practical Solutions John Bellardo and Stefan Savage Dept of CSE @ UC San Diego Seminar class presentation Supervisor: Dr. Huang Student: Chuming Chen & Xinliang Zheng CSE@USC

Outline • • 9/25/2020 Background information about IEEE 802. 11 Theoretical vulnerability analysis Practical 802. 11 attack infrastructure Deauthentication attack and defense Virtual carrier-sense attack and defense Conclusions References CSE@USC 2

Background information about IEEE 802. 11 • • • What is IEEE 802. 11 MAC frame Authentication and Association Transitions Hidden Terminal Problem Solution to Hidden Terminal Problem 9/25/2020 CSE@USC 3
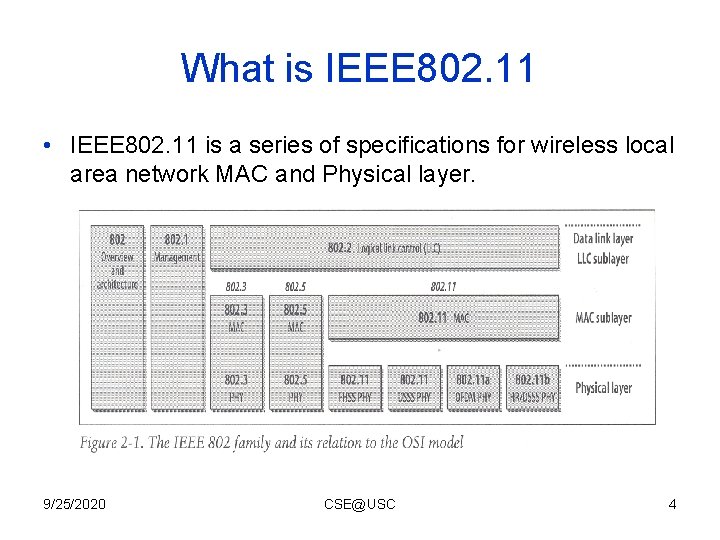
What is IEEE 802. 11 • IEEE 802. 11 is a series of specifications for wireless local area network MAC and Physical layer. 9/25/2020 CSE@USC 4
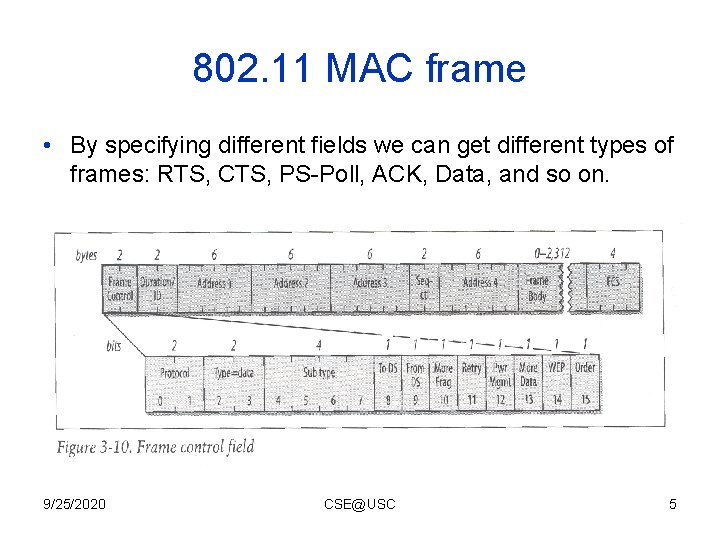
802. 11 MAC frame • By specifying different fields we can get different types of frames: RTS, CTS, PS-Poll, ACK, Data, and so on. 9/25/2020 CSE@USC 5
Type and Subtype Identifier • Management frames (type=00) – – Association request (0000) Association response (0001) Disassociation (1010) Deauthentication (1100) • Control frames (type=01) – Power Save (PS)-Poll (1010) – RTS (1011) – CTS (1100) • Data frame (type=10) – Data (0000) – Data+CF-Ack (0001) 9/25/2020 CSE@USC 6
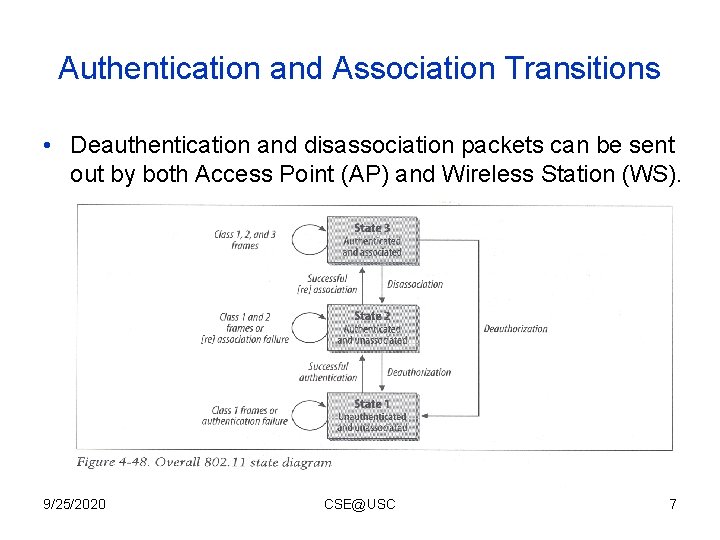
Authentication and Association Transitions • Deauthentication and disassociation packets can be sent out by both Access Point (AP) and Wireless Station (WS). 9/25/2020 CSE@USC 7
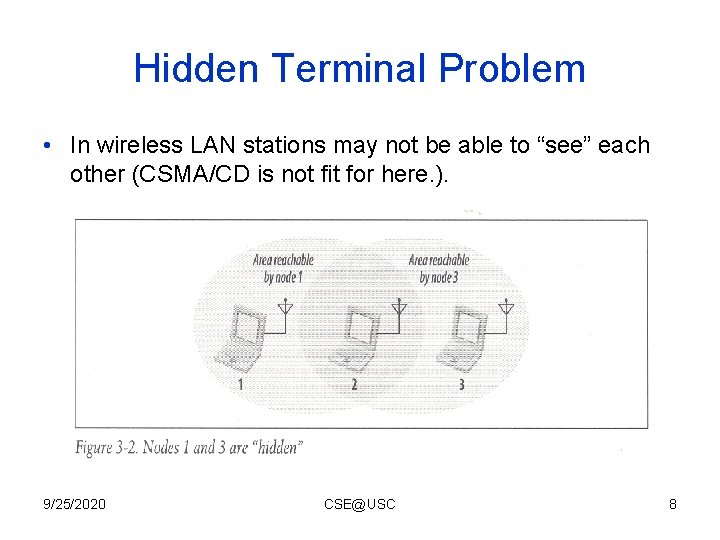
Hidden Terminal Problem • In wireless LAN stations may not be able to “see” each other (CSMA/CD is not fit for here. ). 9/25/2020 CSE@USC 8
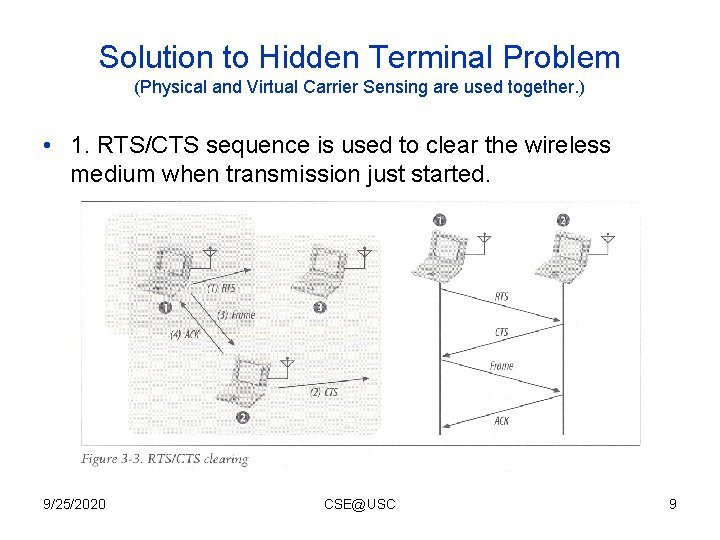
Solution to Hidden Terminal Problem (Physical and Virtual Carrier Sensing are used together. ) • 1. RTS/CTS sequence is used to clear the wireless medium when transmission just started. 9/25/2020 CSE@USC 9
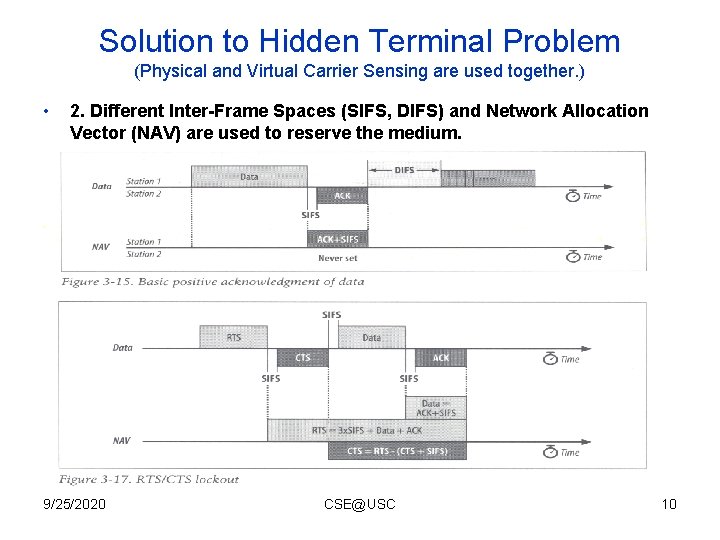
Solution to Hidden Terminal Problem (Physical and Virtual Carrier Sensing are used together. ) • 2. Different Inter-Frame Spaces (SIFS, DIFS) and Network Allocation Vector (NAV) are used to reserve the medium. 9/25/2020 CSE@USC 10

Theoretical vulnerability analysis • • 9/25/2020 Identity Vulnerabilities Picturing of Deauthentication Attack Media Access Vulnerabilities Picturing of Virtual Carrier-Sense Attack CSE@USC 11
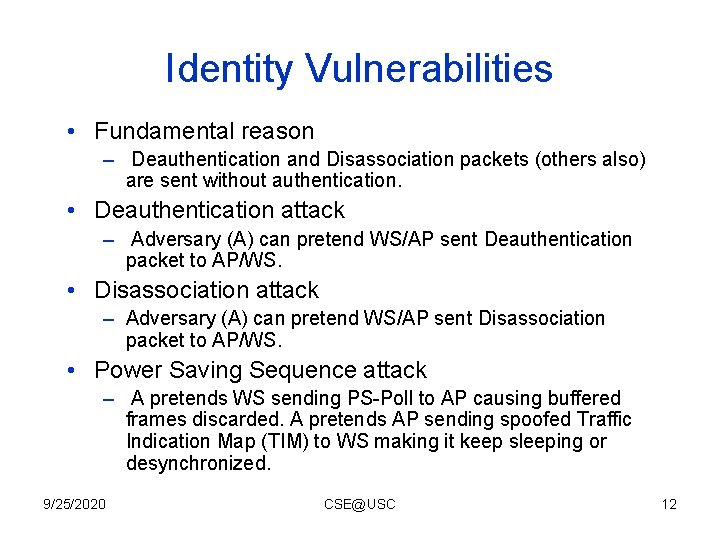
Identity Vulnerabilities • Fundamental reason – Deauthentication and Disassociation packets (others also) are sent without authentication. • Deauthentication attack – Adversary (A) can pretend WS/AP sent Deauthentication packet to AP/WS. • Disassociation attack – Adversary (A) can pretend WS/AP sent Disassociation packet to AP/WS. • Power Saving Sequence attack – A pretends WS sending PS-Poll to AP causing buffered frames discarded. A pretends AP sending spoofed Traffic Indication Map (TIM) to WS making it keep sleeping or desynchronized. 9/25/2020 CSE@USC 12
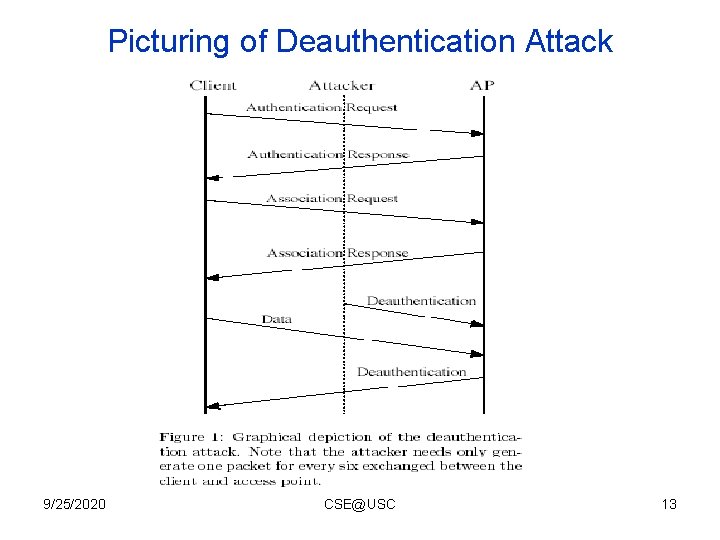
Picturing of Deauthentication Attack 9/25/2020 CSE@USC 13

Media Access Vulnerabilities • Fundamental reason – Still because packet sending to the media is not authenticated in 802. 11. • One possible attack – Sending packet within each SIFS to compete the media; may require sending 50, 000 packets/second. • Virtual Carrier-Sense attack – Sending out packets with large NAV. (30 p/s) 9/25/2020 CSE@USC 14
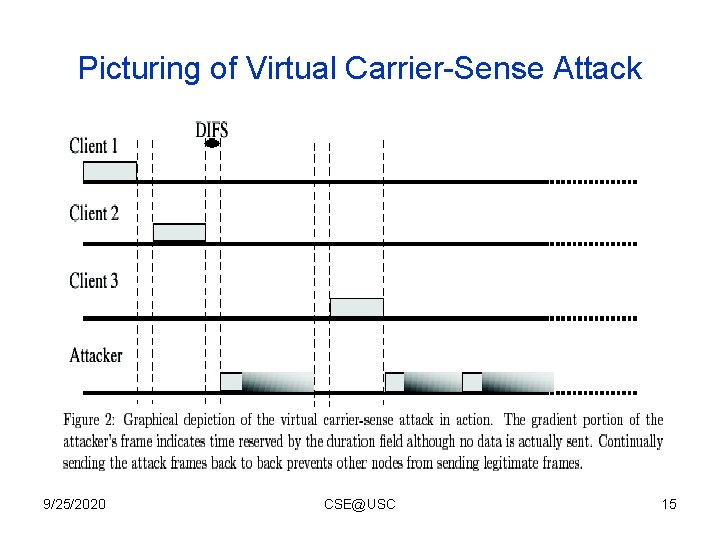
Picturing of Virtual Carrier-Sense Attack 9/25/2020 CSE@USC 15

Practical 802. 11 attack infrastructure • What A need to implement the attack? • General structure of current Network Interface Cards (NIC) • Practical Problem • Solution to the Practical Problem 9/25/2020 CSE@USC 16

What A need to implement the attack? • It’s possible that A can design and make new NIC which can send out different packets as A wants, but it’s more likely improbable. • Hopefully A can use current available NIC to implement attacks. 9/25/2020 CSE@USC 17
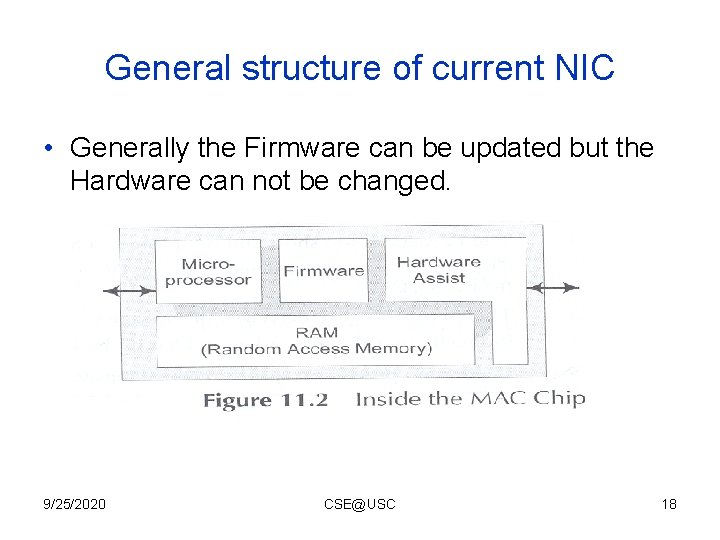
General structure of current NIC • Generally the Firmware can be updated but the Hardware can not be changed. 9/25/2020 CSE@USC 18

Practical Problem • A wide variety of 802. 11 NIC tested by the authors do not typically allow the generation of any control frames, permit other key fields (such as NAV) to specified by the host, or allow reserved or illegal field values to be transmitted. 9/25/2020 CSE@USC 19
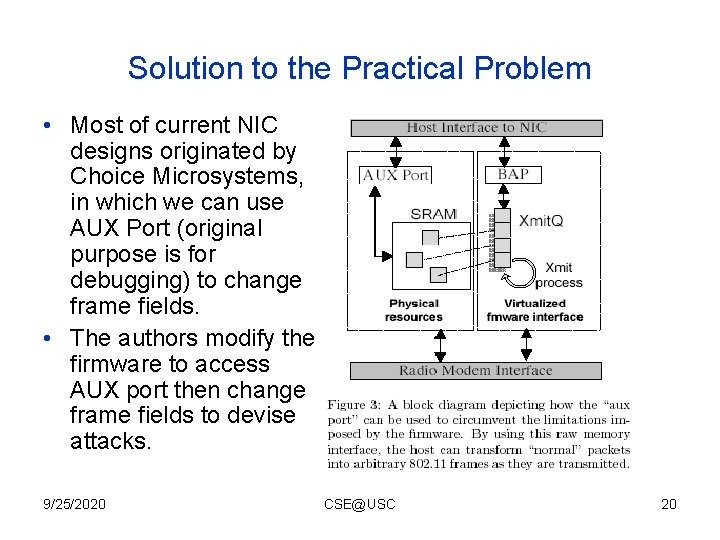
Solution to the Practical Problem • Most of current NIC designs originated by Choice Microsystems, in which we can use AUX Port (original purpose is for debugging) to change frame fields. • The authors modify the firmware to access AUX port then change frame fields to devise attacks. 9/25/2020 CSE@USC 20

Deauthentication attack and defense • Experimental settings • Deauthentication Attack • Defense to Deauthentication Attacks 9/25/2020 CSE@USC 21

Experimental Settings • Small 802. 11 network with 7 machines: – 1 attacker, 1 access point, 1 monitoring station and 4 legitimate clients. • In-kernel software-based access point with Linux Host. AP driver. • Clients attempted to ftp a large file through the access point machine – a transfer exceeding the testing period 9/25/2020 CSE@USC 22
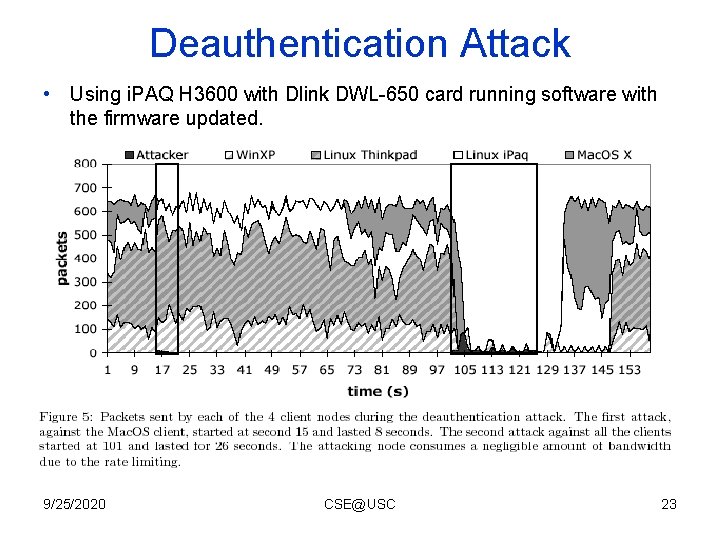
Deauthentication Attack • Using i. PAQ H 3600 with Dlink DWL-650 card running software with the firmware updated. 9/25/2020 CSE@USC 23
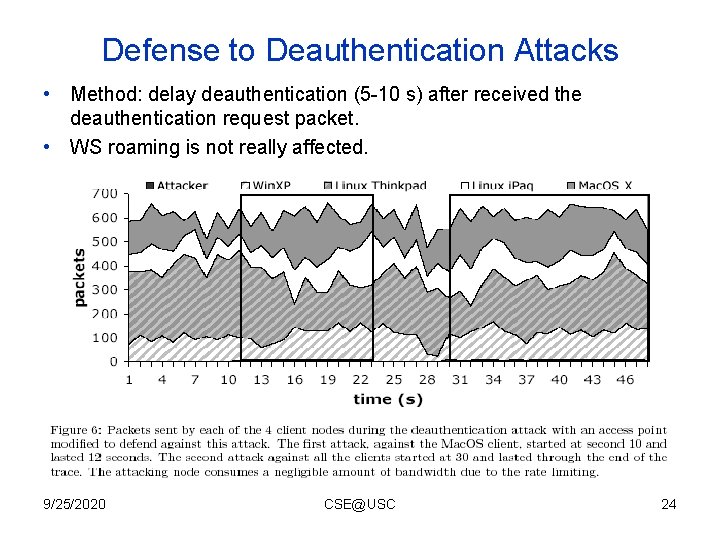
Defense to Deauthentication Attacks • Method: delay deauthentication (5 -10 s) after received the deauthentication request packet. • WS roaming is not really affected. 9/25/2020 CSE@USC 24

Virtual carrier-sense attack and defense • Virtual Carrier-Sense Attack Using A Real NIC • Virtual Carrier-Sense Attack Using ns simulator • Defense to Virtual Carrier-Sense Attack 9/25/2020 CSE@USC 25

Virtual Carrier-Sense Attack Using A Real NIC • It does not work • Conclusion: most of the devices available do not properly implement 802. 11, i. e. NAV reserve period is not fully executed. 9/25/2020 CSE@USC 26
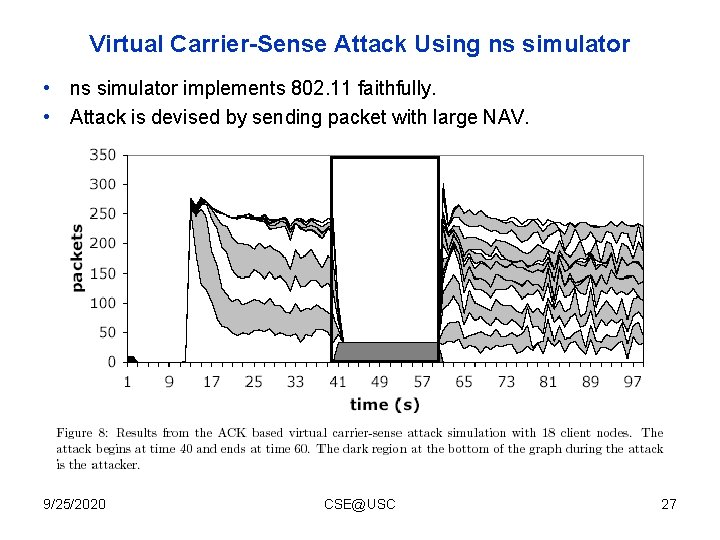
Virtual Carrier-Sense Attack Using ns simulator • ns simulator implements 802. 11 faithfully. • Attack is devised by sending packet with large NAV. 9/25/2020 CSE@USC 27
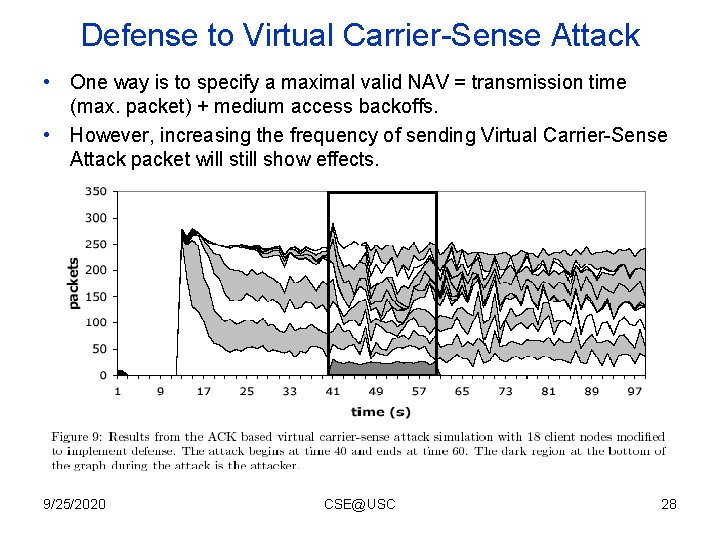
Defense to Virtual Carrier-Sense Attack • One way is to specify a maximal valid NAV = transmission time (max. packet) + medium access backoffs. • However, increasing the frequency of sending Virtual Carrier-Sense Attack packet will still show effects. 9/25/2020 CSE@USC 28

Defense to Virtual Carrier-Sense Attack • Another way specified by the authors needs to modify 802. 11: • No fragmentation, since the default fragmentation thresholds in wireless media is significantly exceed the Ethernet MTU. • For four key frame types contains NAV: – ACK and Data frame: ignore NAV since there is no fragmentation. – RTS frame NAV: respected until such time as a data frame should be sent. – CTS frame NAV: specify some threshold (30%) if such time is used by CTS frame then ignore NAV. • This way is not tested by the authors of the paper. 9/25/2020 CSE@USC 29

Conclusions • Vulnerabilities in the 802. 11 management and media access services are identified. • Theoretical attacks are analyzed. • Implementing of deauthenticaiton and virtual carrier-sense attacks are provided with testing results. • Low-overhead, non-cryptographic countermeasures are specified, some test results with the suggested improvement are also provided. 9/25/2020 CSE@USC 30

References • 1. 802. 11 Denial-of-Service Attacks: Real Vulnerabilities and Practical Solutions, John Bellardo and Stefan Savage, Dept of CSE @ UC San Diego. • 2. 802. 11 Wireless Networks – The Definitive Guide, Matthew S. Gast, O’Reilly 2002. • 3. Real 802. 11 Security – WI-Fi Protected Access and 802. 11 i, Jon Edney and William A. Arbaugh, Addison-Wesley 2003. 9/25/2020 CSE@USC 31
- Slides: 31