5122005 doc IEEE 802 11 050392 Ripple A



- Slides: 16

5/12/2005 doc. : IEEE 802. 11 -05/0392 Ripple: A Distributed Medium Access Protocol for Wireless Mesh Network Presented at the IEEE 802. 11, 802. 15, 802. 18, 802. 19, 802. 20, 802. 21 & 802. 22 Interim Meeting, May 2004 by Ray-Guang Cheng (crg@mail. ntust. edu. tw), Cun-Yi Wang (M 9202226@mail. ntust. edu. tw), Jen-Shun Yang (jsyang@itri. org. tw) Submission

5/12/2005 doc. : IEEE 802. 11 -05/0392 Outline n n n Submission Motivation Lessons Learned from the Nature Our Solution Algorithm of Ripple Protocol An Example Appendix Slide 2 Ray-Guang Cheng, Cun-Yi Wang, and Jen-Shun Yang

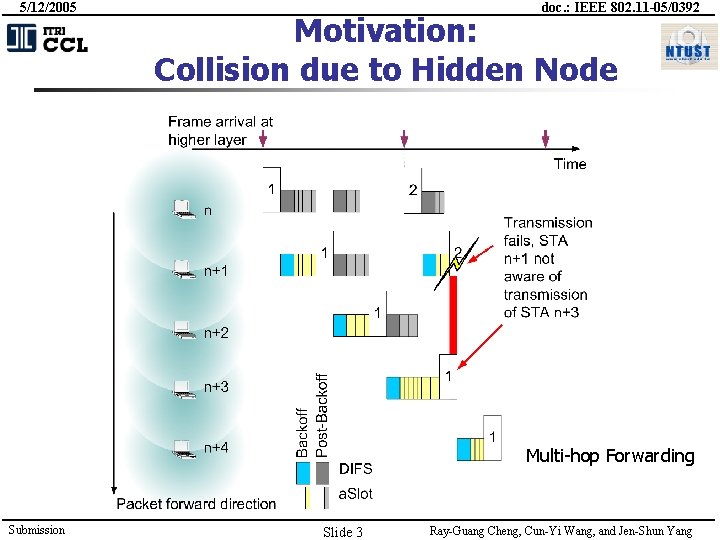
5/12/2005 doc. : IEEE 802. 11 -05/0392 Motivation: Collision due to Hidden Node Multi-hop Forwarding Submission Slide 3 Ray-Guang Cheng, Cun-Yi Wang, and Jen-Shun Yang

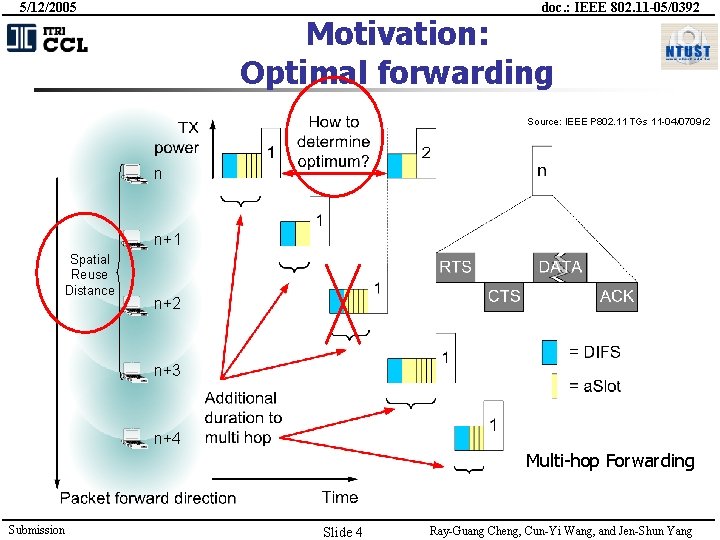
5/12/2005 doc. : IEEE 802. 11 -05/0392 Motivation: Optimal forwarding Source: IEEE P 802. 11 TGs 11 -04/0709 r 2 n n+1 Spatial Reuse Distance n+2 n+3 n+4 Multi-hop Forwarding Submission Slide 4 Ray-Guang Cheng, Cun-Yi Wang, and Jen-Shun Yang

5/12/2005 doc. : IEEE 802. 11 -05/0392 Observations n Existing MAC mechanisms n n Random access mechanism Performance degradation caused by n n Performance is severely degraded when the network is heavy loaded Could we have better solutions? n Prerequisites n Submission Hidden/exposed nodes exponential backoff Distributed protocol Slide 5 Ray-Guang Cheng, Cun-Yi Wang, and Jen-Shun Yang

5/12/2005 doc. : IEEE 802. 11 -05/0392 Lessons Learned from the Nature Optimum duration Spatial reuse distance Ripple Effect Submission Slide 6 Ray-Guang Cheng, Cun-Yi Wang, and Jen-Shun Yang

5/12/2005 doc. : IEEE 802. 11 -05/0392 Our Solution: Ripple Protocol n Approaches n Adopts controlled access mechanism n n Submission To prevent from unintentional frame collisions To eliminate exponential backoff Uses RTS/CTS to prevent from hidden node problem Utilizes spatial reuse to improve utilization Slide 7 Ray-Guang Cheng, Cun-Yi Wang, and Jen-Shun Yang

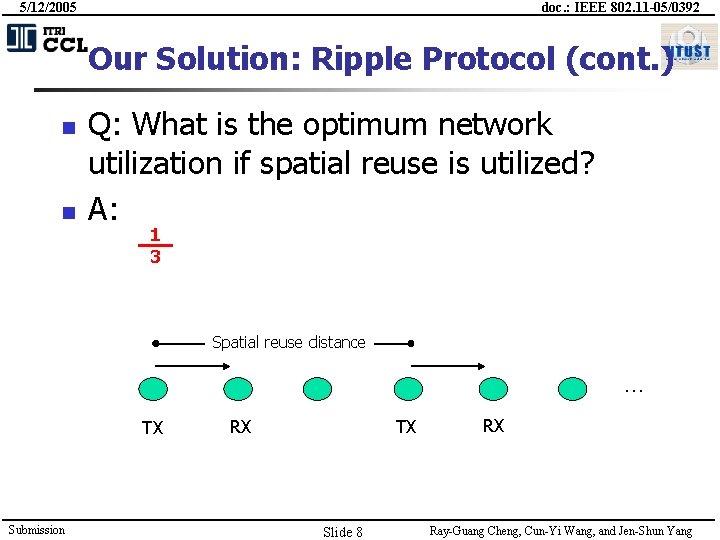
5/12/2005 doc. : IEEE 802. 11 -05/0392 Our Solution: Ripple Protocol (cont. ) n n Q: What is the optimum network utilization if spatial reuse is utilized? A: 1 3 Spatial reuse distance … TX Submission RX TX Slide 8 RX Ray-Guang Cheng, Cun-Yi Wang, and Jen-Shun Yang

5/12/2005 doc. : IEEE 802. 11 -05/0392 System Model n Targeted Application Environment n Wireless backbone (backhaul) system n n Basic assumption n n Tree Topology Non-mobile Mesh Points and Mesh AP n n n routing path has been determined One-hop radio coverage Separate channels are assigned for downlink and uplink paths n Submission high data rate is provided by mesh links Unidirectional data-frame delivery Slide 9 Ray-Guang Cheng, Cun-Yi Wang, and Jen-Shun Yang

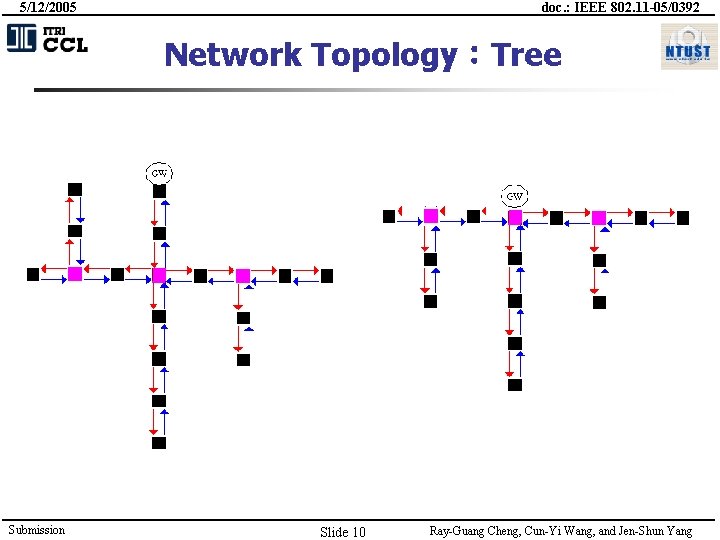
5/12/2005 doc. : IEEE 802. 11 -05/0392 Network Topology:Tree Submission Slide 10 Ray-Guang Cheng, Cun-Yi Wang, and Jen-Shun Yang

5/12/2005 doc. : IEEE 802. 11 -05/0392 Frame Formats n n n Submission DATA frame: DATA frame carries user information. The time required to transmit the DATA frame is a constant. NULL frame: NULL frame is a DATA frame but carries no information. RTS frame: a node, which has the right to send a DATA frame, will send an RTS frame. CTS frame: the target node that receives an RTS frame will responses a CTS frame. Ready-to-send (RTR) frame: a node, which has the right to receive a DATA frame, will send an RTR frame to the sender if the expected RTS frame is not received. ACK frame: a node receives a DATA frame correctly will response an ACK frame. Slide 11 Ray-Guang Cheng, Cun-Yi Wang, and Jen-Shun Yang

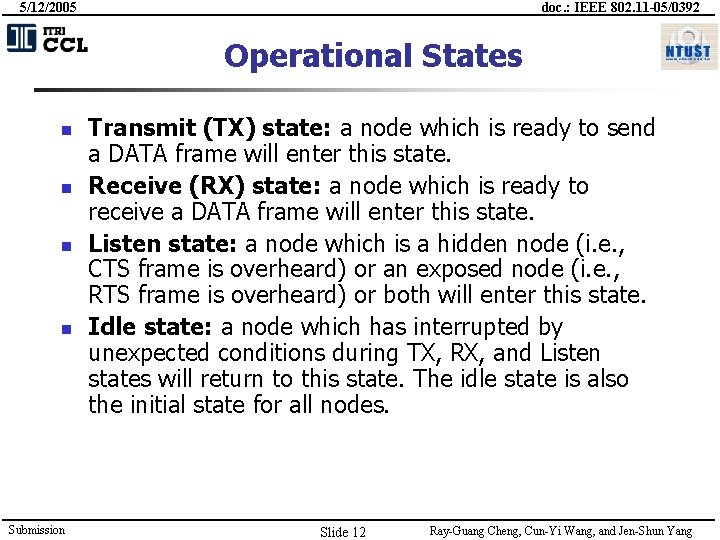
5/12/2005 doc. : IEEE 802. 11 -05/0392 Operational States n n Submission Transmit (TX) state: a node which is ready to send a DATA frame will enter this state. Receive (RX) state: a node which is ready to receive a DATA frame will enter this state. Listen state: a node which is a hidden node (i. e. , CTS frame is overheard) or an exposed node (i. e. , RTS frame is overheard) or both will enter this state. Idle state: a node which has interrupted by unexpected conditions during TX, RX, and Listen states will return to this state. The idle state is also the initial state for all nodes. Slide 12 Ray-Guang Cheng, Cun-Yi Wang, and Jen-Shun Yang

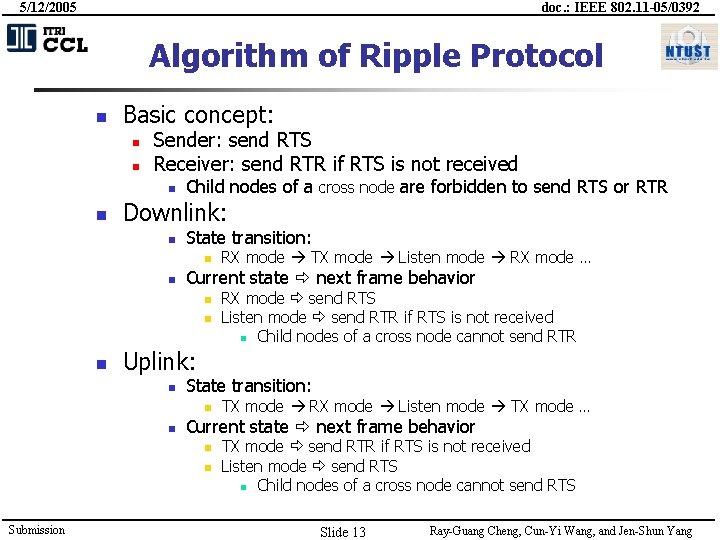
5/12/2005 doc. : IEEE 802. 11 -05/0392 Algorithm of Ripple Protocol n Basic concept: n n Sender: send RTS Receiver: send RTR if RTS is not received n n Child nodes of a cross node are forbidden to send RTS or RTR Downlink: n State transition: n n Current state next frame behavior n n n RX mode send RTS Listen mode send RTR if RTS is not received n Child nodes of a cross node cannot send RTR Uplink: n State transition: n n TX mode RX mode Listen mode TX mode … Current state next frame behavior n n Submission RX mode TX mode Listen mode RX mode … TX mode send RTR if RTS is not received Listen mode send RTS n Child nodes of a cross node cannot send RTS Slide 13 Ray-Guang Cheng, Cun-Yi Wang, and Jen-Shun Yang

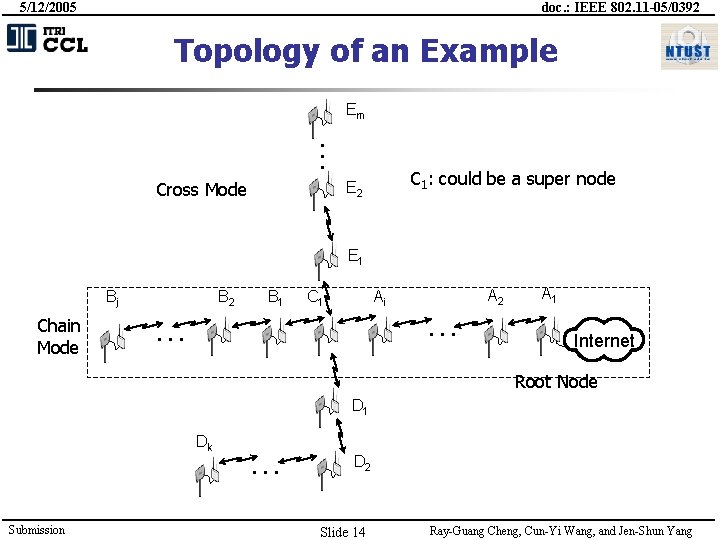
5/12/2005 doc. : IEEE 802. 11 -05/0392 Topology of an Example … Em Cross Mode C 1: could be a super node E 2 E 1 Bj Chain Mode B 2 B 1 C 1 Ai … … A 2 A 1 Internet Root Node D 1 Dk Submission … D 2 Slide 14 Ray-Guang Cheng, Cun-Yi Wang, and Jen-Shun Yang

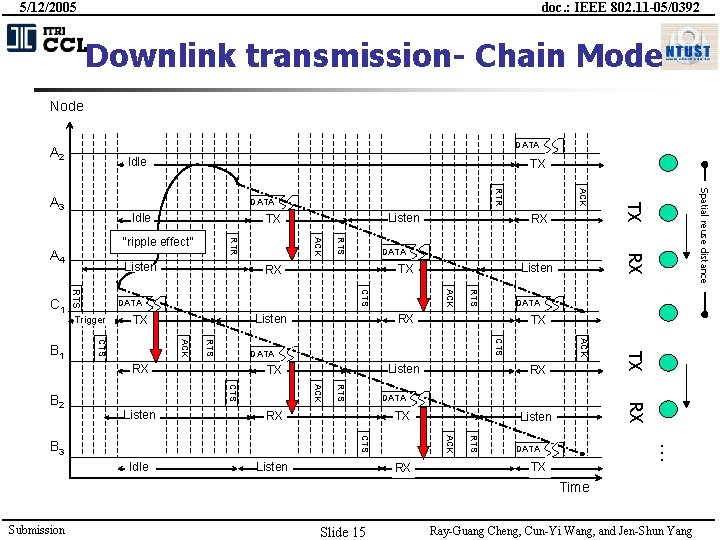
5/12/2005 doc. : IEEE 802. 11 -05/0392 Downlink transmission- Chain Mode Node DATA A 2 Idle RTS ACK CTS TX Listen … RX RTS ACK CTS Listen RX DATA RX Spatial reuse distance RX TX ACK CTS Listen TX RX TX DATA B 3 Idle RTS ACK CTS Listen DATA RX Listen TX DATA Trigger RX DATA RX RX B 2 RTS Listen ACK RTR “ripple effect” RTS B 1 Listen TX TX Idle ACK DATA A 4 C 1 RTR A 3 TX DATA TX Time Submission Slide 15 Ray-Guang Cheng, Cun-Yi Wang, and Jen-Shun Yang

5/12/2005 doc. : IEEE 802. 11 -05/0392 Thank you for you attention! crg@ieee. org Submission Slide 16 Ray-Guang Cheng, Cun-Yi Wang, and Jen-Shun Yang