4 Securing Secure the hardware Lock the server





- Slides: 24

4 Securing • Secure the hardware – Lock the server room and other ways to get access to the hardware. – Password protect the BIOS-setup • Secure the NOS

Windows EFS • NTFS can be encrypted (EFS) with File Encryption Key (FEK) • Encrypting File Recovery Agents (Selected Users) are able to recover FEKs. [Additional users are added by editing EFS recovery policy]

Windows-Authentication Two functions: – Verify a user’s credentials (Username and password). – Provide access to resources. • GINA (Graphical Identification and Authentication) • Basic Authentication • External Authentication – Biometrics/Smartcard/Tokenbased • Kerberos

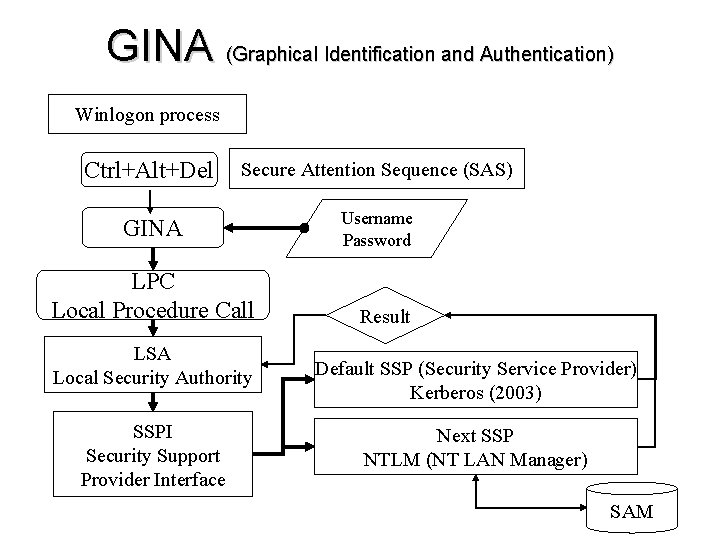
GINA (Graphical Identification and Authentication) Winlogon process Ctrl+Alt+Del Secure Attention Sequence (SAS) GINA Username Password LPC Local Procedure Call LSA Local Security Authority SSPI Security Support Provider Interface Result Default SSP (Security Service Provider) Kerberos (2003) Next SSP NTLM (NT LAN Manager) SAM

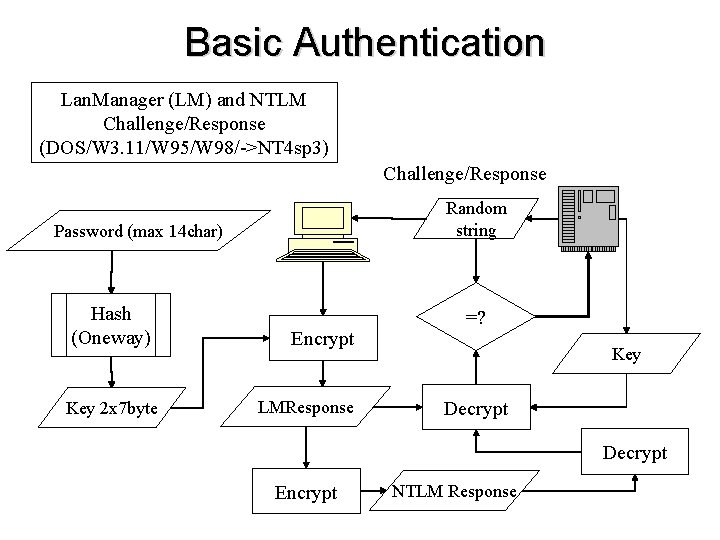
Basic Authentication Lan. Manager (LM) and NTLM Challenge/Response (DOS/W 3. 11/W 95/W 98/->NT 4 sp 3) Challenge/Response Random string Password (max 14 char) Hash (Oneway) Key 2 x 7 byte Encrypt LMResponse =? Key Decrypt Encrypt NTLM Response

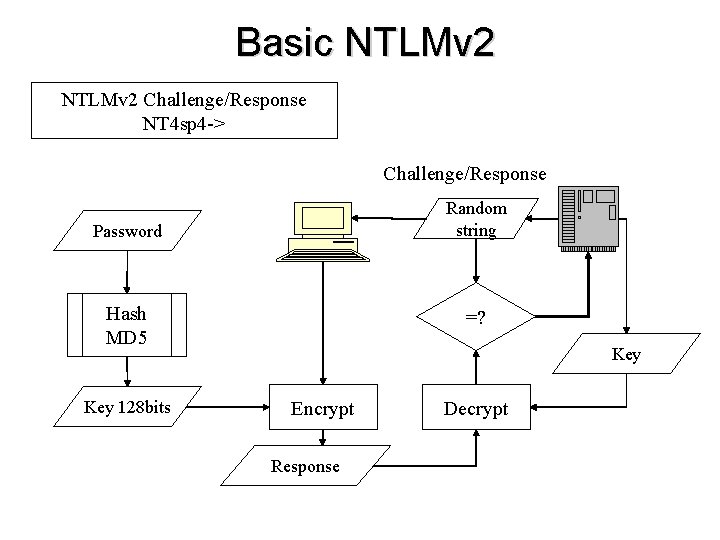
Basic NTLMv 2 Challenge/Response NT 4 sp 4 -> Challenge/Response Random string Password Hash MD 5 Key 128 bits =? Key Encrypt Response Decrypt

External: • Biometrics (Fingerprint, eye) • Smartcard (Reader for smartcard) • RSA Secure. ID Tokens (Internetpayment)

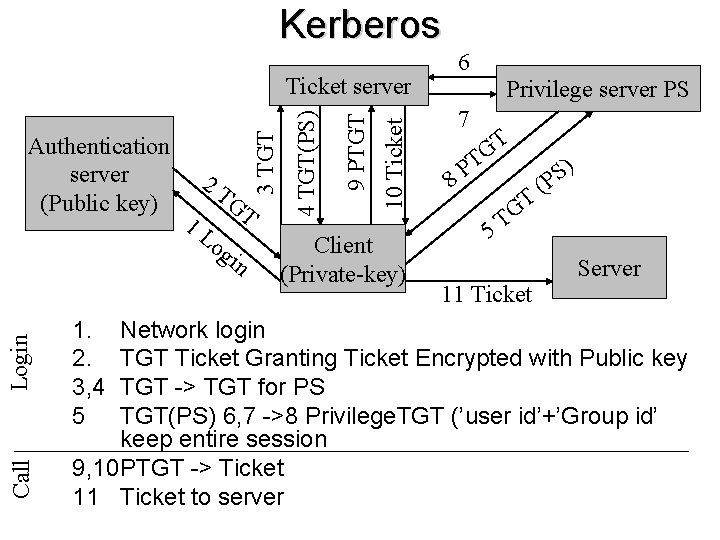
Kerberos Developed at MIT ~1980 (Massachusetts Institute of Technology) • Secure authentication protocol – Uses Public key encryption • • Ticket Granting (Only one authentication needed) Kerberos supports proxy and forwarding of credentials. Uses NTP (Network Time Protocol) for synchronization. Used in: – – – W 2 K 3 -server W 2000 environment Active Directory Windows XP Stored in AD and generate keys automatically. Compatible with MIT Kerberos implementation for Unix

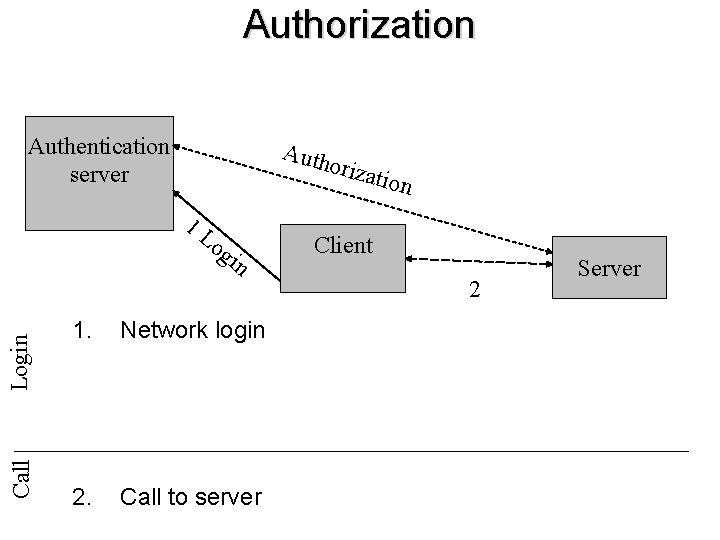
Authorization Authentication server Auth oriza 1 L og in tion Client Call Login 2 1. Network login 2. Call to server Server

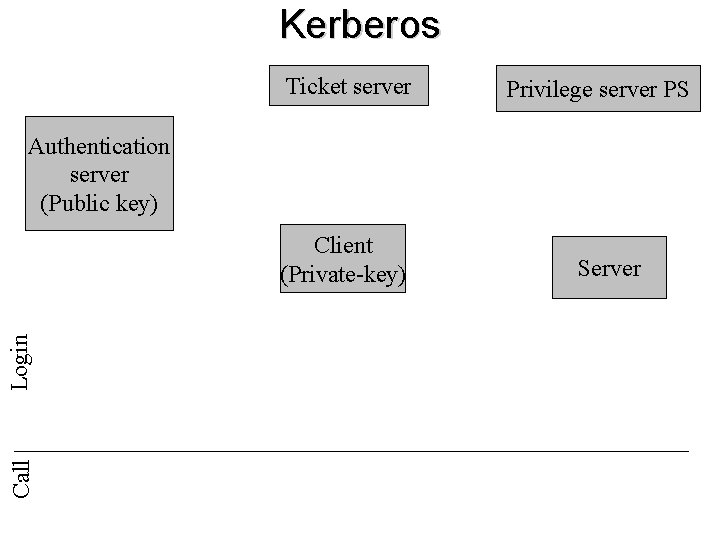
Kerberos Ticket server Privilege server PS Authentication server (Public key) Call Login Client (Private-key) Server

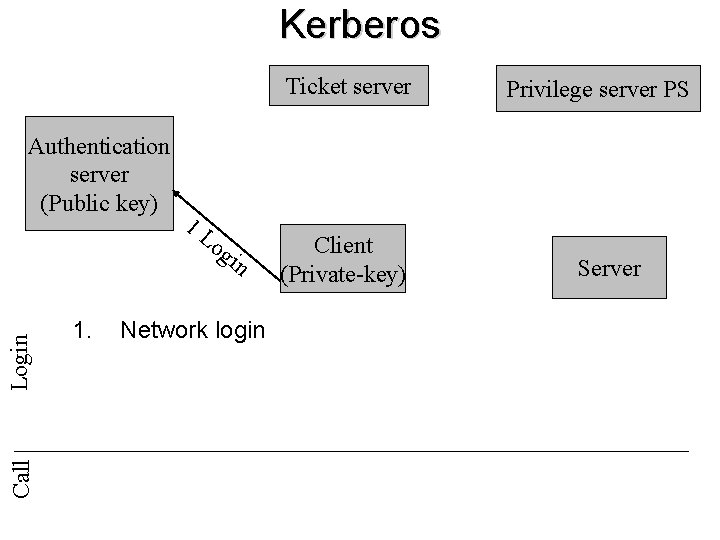
Kerberos Ticket server Call Login Authentication server (Public key) 1. 1 L og in Network login Client (Private-key) Privilege server PS Server

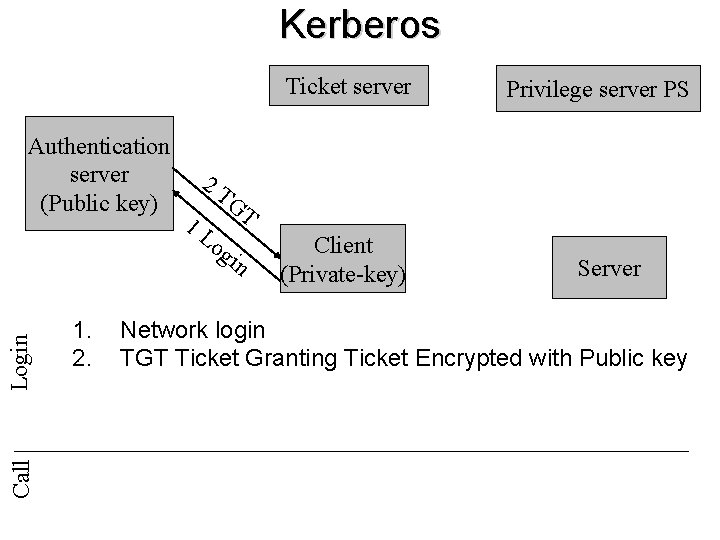
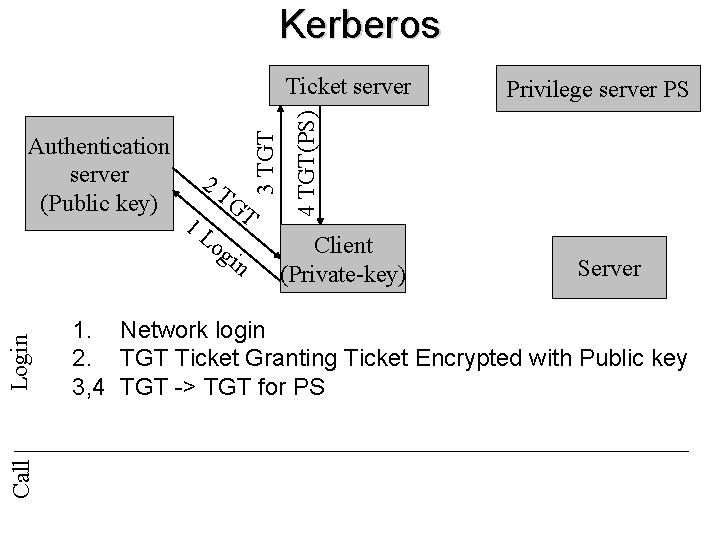
Kerberos Ticket server Call Login Authentication server (Public key) 1. 2. 2 T 1 L Privilege server PS GT og in Client (Private-key) Server Network login TGT Ticket Granting Ticket Encrypted with Public key

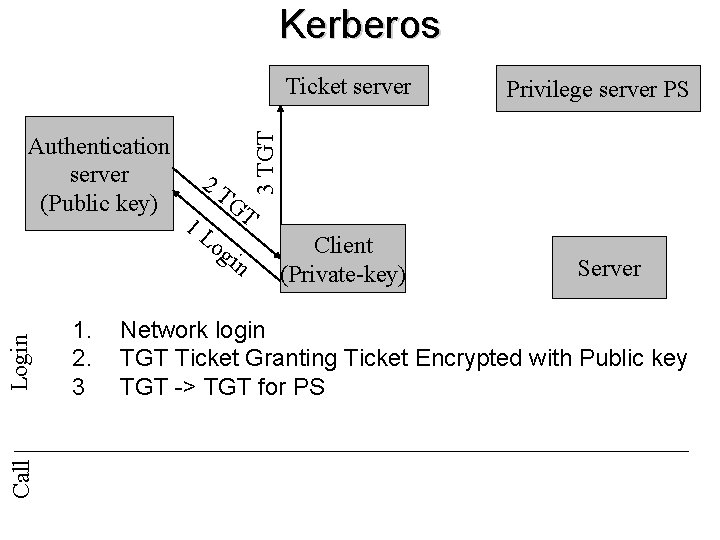
Kerberos Call Login Authentication server (Public key) 1. 2. 3 2 T 1 L GT og in Privilege server PS 3 TGT Ticket server Client (Private-key) Server Network login TGT Ticket Granting Ticket Encrypted with Public key TGT -> TGT for PS

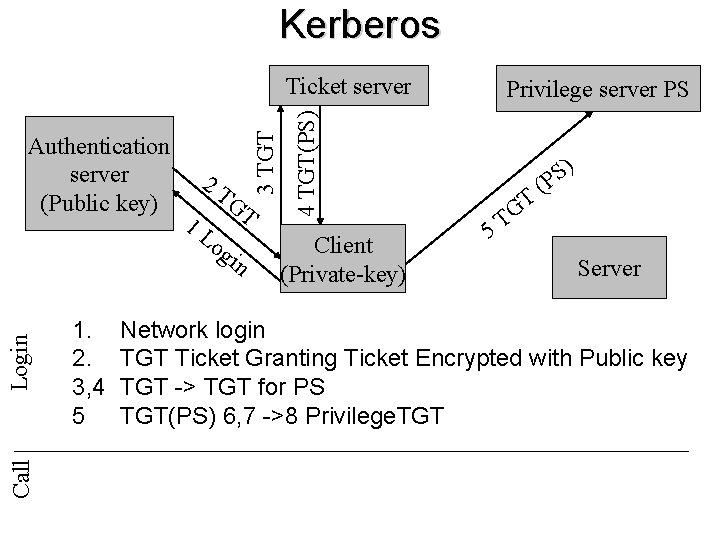
Kerberos Call Login 2 T 1 L GT og in Privilege server PS 4 TGT(PS) Authentication server (Public key) 3 TGT Ticket server Client (Private-key) Server 1. Network login 2. TGT Ticket Granting Ticket Encrypted with Public key 3, 4 TGT -> TGT for PS

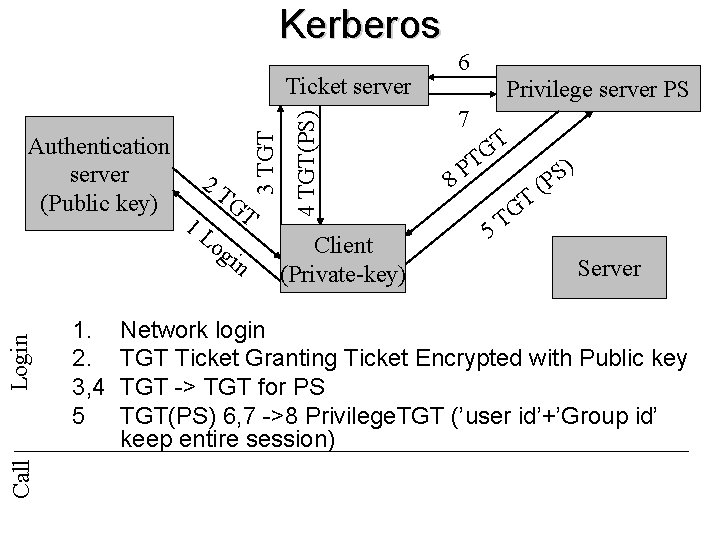
Kerberos Call Login 1. 2. 3, 4 5 2 T 1 L GT og in Privilege server PS 4 TGT(PS) Authentication server (Public key) 3 TGT Ticket server Client (Private-key) 5 T G T ) S P ( Server Network login TGT Ticket Granting Ticket Encrypted with Public key TGT -> TGT for PS TGT(PS) 6, 7 ->8 Privilege. TGT

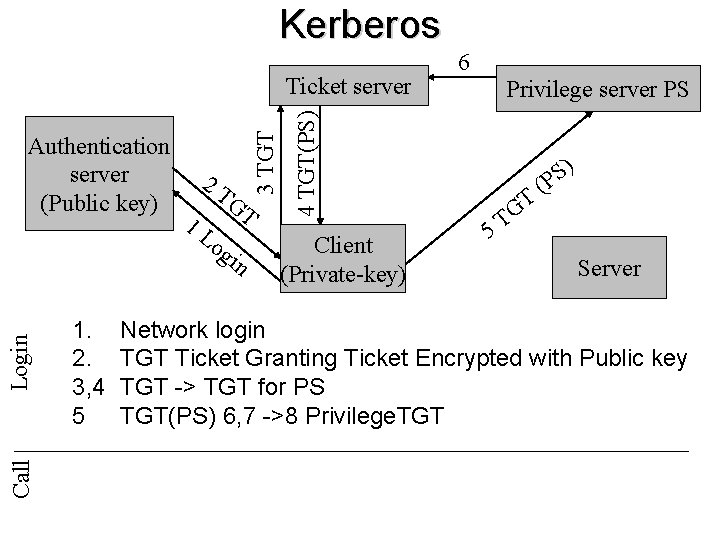
Kerberos Call Login 1. 2. 3, 4 5 2 T 1 L GT og in Privilege server PS 4 TGT(PS) Authentication server (Public key) 3 TGT Ticket server 6 Client (Private-key) 5 T G T ) S P ( Server Network login TGT Ticket Granting Ticket Encrypted with Public key TGT -> TGT for PS TGT(PS) 6, 7 ->8 Privilege. TGT

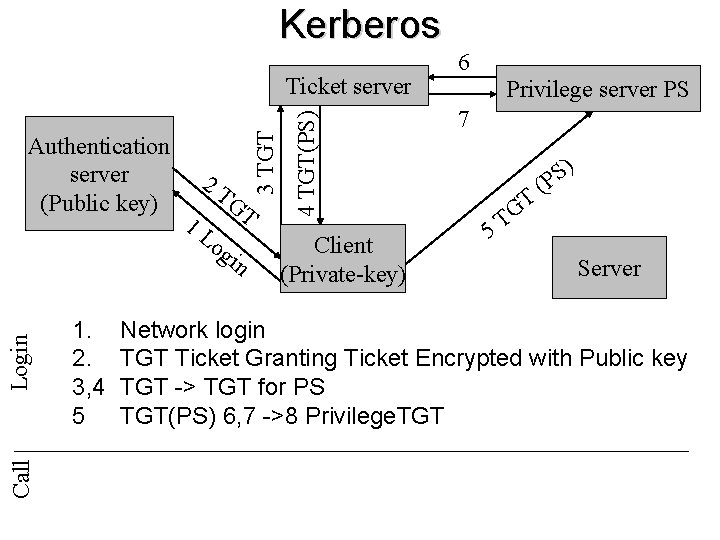
Kerberos Call Login 1. 2. 3, 4 5 2 T 1 L GT og in 4 TGT(PS) Authentication server (Public key) 3 TGT Ticket server Client (Private-key) 6 Privilege server PS 7 5 T G T ) S P ( Server Network login TGT Ticket Granting Ticket Encrypted with Public key TGT -> TGT for PS TGT(PS) 6, 7 ->8 Privilege. TGT

Kerberos Call Login 1. 2. 3, 4 5 2 T 1 L GT og in 4 TGT(PS) Authentication server (Public key) 3 TGT Ticket server Client (Private-key) 6 Privilege server PS 7 T G T 8 P 5 T G T ) S P ( Server Network login TGT Ticket Granting Ticket Encrypted with Public key TGT -> TGT for PS TGT(PS) 6, 7 ->8 Privilege. TGT (’user id’+’Group id’ keep entire session)

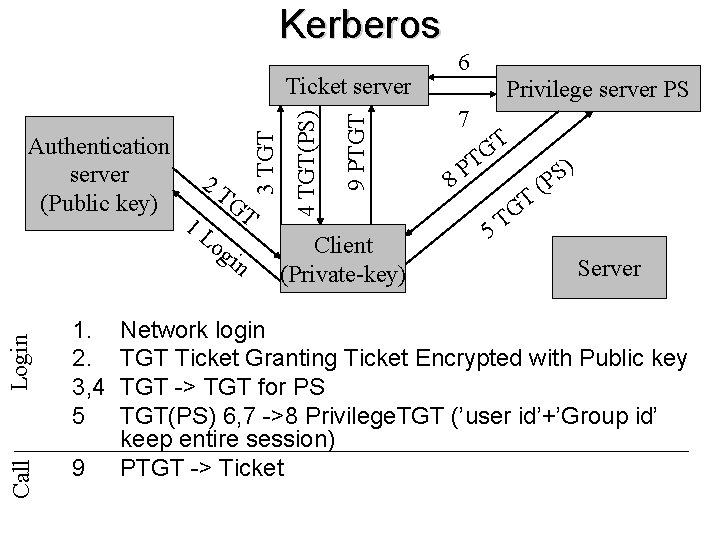
Kerberos Login 1. 2. 3, 4 5 Call 9 1 L GT og in 9 PTGT 2 T 4 TGT(PS) Authentication server (Public key) 3 TGT Ticket server Client (Private-key) 6 Privilege server PS 7 T G T 8 P 5 T G T ) S P ( Server Network login TGT Ticket Granting Ticket Encrypted with Public key TGT -> TGT for PS TGT(PS) 6, 7 ->8 Privilege. TGT (’user id’+’Group id’ keep entire session) PTGT -> Ticket

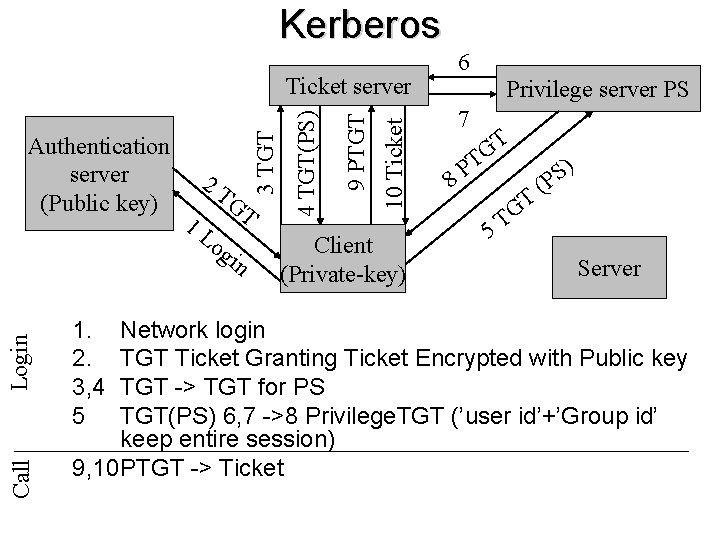
Kerberos Call Login 1. 2. 3, 4 5 og in 10 Ticket 1 L GT 9 PTGT 2 T 4 TGT(PS) Authentication server (Public key) 3 TGT Ticket server Client (Private-key) 6 Privilege server PS 7 T G T 8 P 5 T G T ) S P ( Server Network login TGT Ticket Granting Ticket Encrypted with Public key TGT -> TGT for PS TGT(PS) 6, 7 ->8 Privilege. TGT (’user id’+’Group id’ keep entire session) 9, 10 PTGT -> Ticket

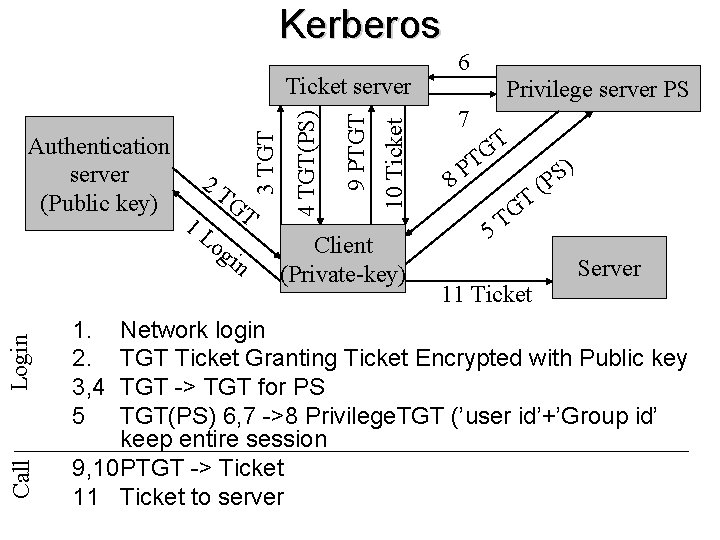
Kerberos Call Login 1. 2. 3, 4 5 og in 10 Ticket 1 L GT 9 PTGT 2 T 4 TGT(PS) Authentication server (Public key) 3 TGT Ticket server Client (Private-key) 6 Privilege server PS 7 T G T 8 P 5 T G T 11 Ticket ) S P ( Server Network login TGT Ticket Granting Ticket Encrypted with Public key TGT -> TGT for PS TGT(PS) 6, 7 ->8 Privilege. TGT (’user id’+’Group id’ keep entire session 9, 10 PTGT -> Ticket 11 Ticket to server

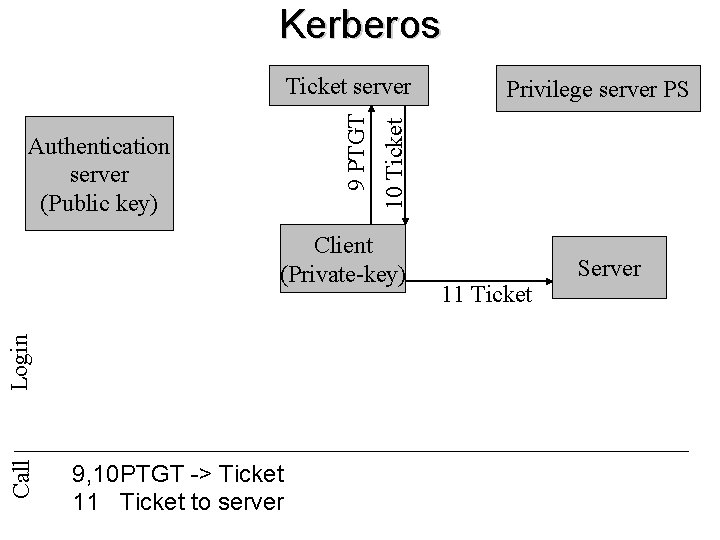
Kerberos Authentication server (Public key) Call Login Client (Private-key) 9, 10 PTGT -> Ticket 11 Ticket to server Privilege server PS 10 Ticket 9 PTGT Ticket server 11 Ticket Server

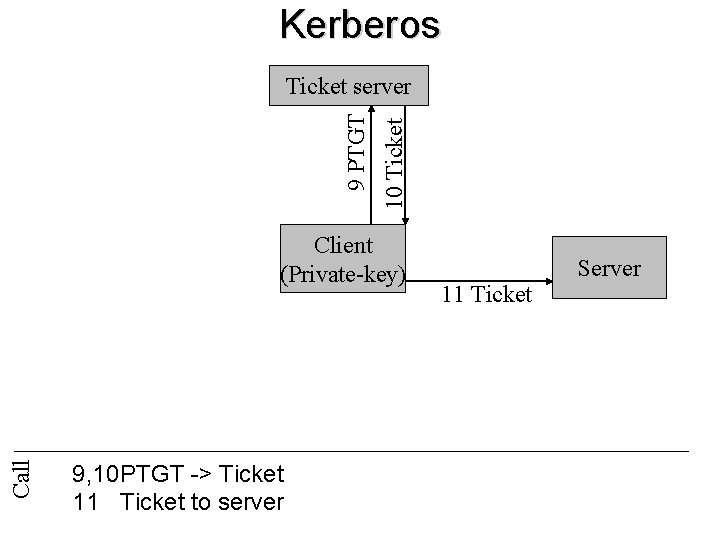
Kerberos 10 Ticket 9 PTGT Ticket server Call Client (Private-key) 9, 10 PTGT -> Ticket 11 Ticket to server 11 Ticket Server

Kerberos Call Login 1. 2. 3, 4 5 og in 10 Ticket 1 L GT 9 PTGT 2 T 4 TGT(PS) Authentication server (Public key) 3 TGT Ticket server Client (Private-key) 6 Privilege server PS 7 T G T 8 P 5 T G T 11 Ticket ) S P ( Server Network login TGT Ticket Granting Ticket Encrypted with Public key TGT -> TGT for PS TGT(PS) 6, 7 ->8 Privilege. TGT (’user id’+’Group id’ keep entire session 9, 10 PTGT -> Ticket 11 Ticket to server