3 DES and Block Cipher Modes of Operation

3 DES and Block Cipher Modes of Operation CSE 651: Introduction to Network Security
Abstract • We will discuss – 2 DES and 3 DES – AES (Advanced Encryption Standard) – How to use block ciphers? – RC 4: a widely used stream cipher – Problems with WEP’s use of RC 4 2

Multiple Encryption with DES • DES is not secure enough. • The once large key space, 256, is now too small. • In 2001, NIST published the Advanced Encryption Standard (AES) as an alternative. • But users in commerce and finance are not ready to give up on DES. • Solution: to use multiple DES with multiple keys 3

Double-DES • Consider 2 -DES with two keys: C = EK 2(EK 1(P)) • Decryption: P = DK 1(DK 2(C)) • Key length: 56 x 2 = 112 bits • This should have thwarted brute-force attacks? • Wrong! 4
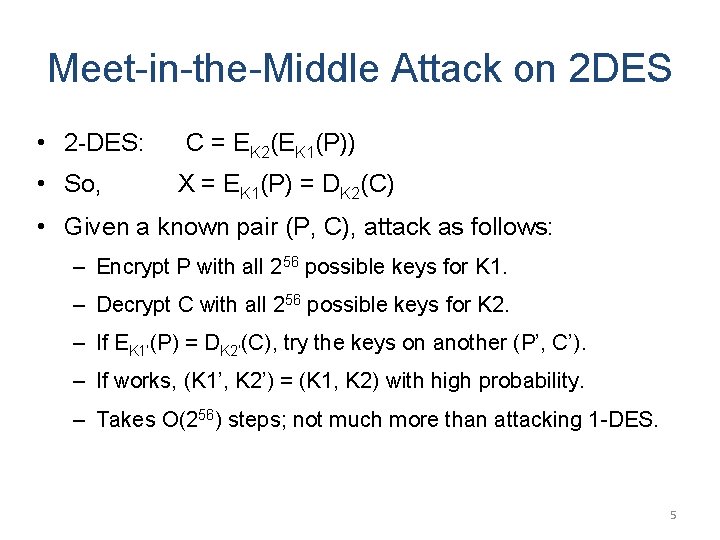
Meet-in-the-Middle Attack on 2 DES • 2 -DES: • So, C = EK 2(EK 1(P)) X = EK 1(P) = DK 2(C) • Given a known pair (P, C), attack as follows: – Encrypt P with all 256 possible keys for K 1. – Decrypt C with all 256 possible keys for K 2. – If EK 1’(P) = DK 2’(C), try the keys on another (P’, C’). – If works, (K 1’, K 2’) = (K 1, K 2) with high probability. – Takes O(256) steps; not much more than attacking 1 -DES. 5
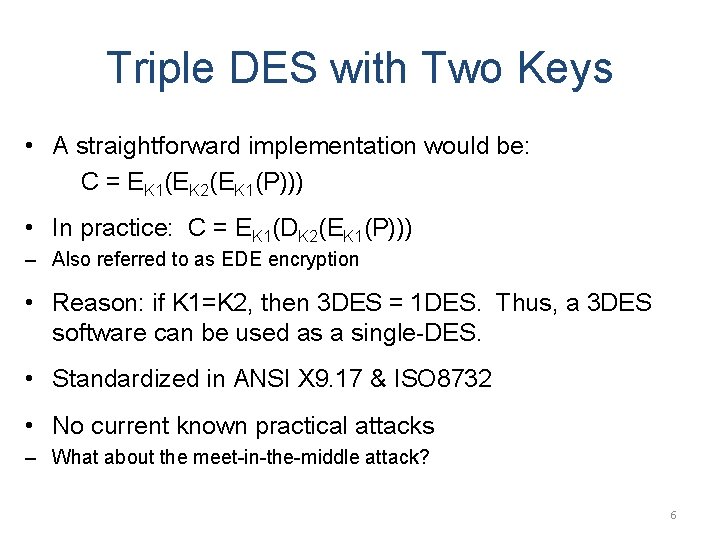
Triple DES with Two Keys • A straightforward implementation would be: C = EK 1(EK 2(EK 1(P))) • In practice: C = EK 1(DK 2(EK 1(P))) – Also referred to as EDE encryption • Reason: if K 1=K 2, then 3 DES = 1 DES. Thus, a 3 DES software can be used as a single-DES. • Standardized in ANSI X 9. 17 & ISO 8732 • No current known practical attacks – What about the meet-in-the-middle attack? 6
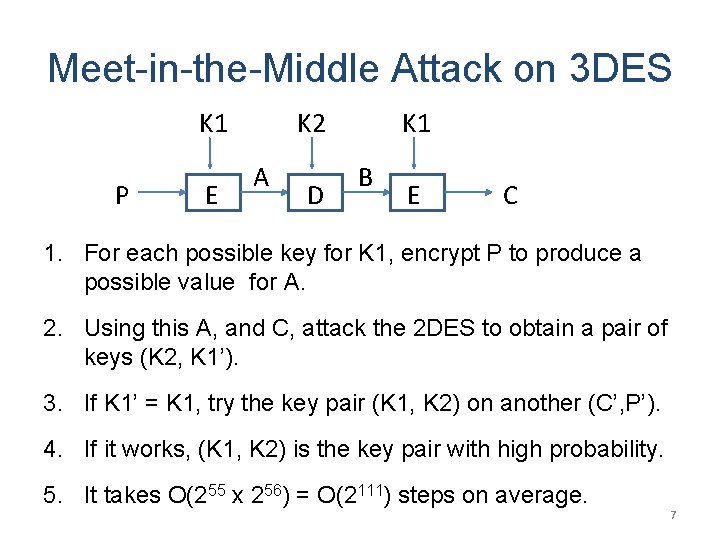
Meet-in-the-Middle Attack on 3 DES K 1 P E K 2 A D K 1 B E C 1. For each possible key for K 1, encrypt P to produce a possible value for A. 2. Using this A, and C, attack the 2 DES to obtain a pair of keys (K 2, K 1’). 3. If K 1’ = K 1, try the key pair (K 1, K 2) on another (C’, P’). 4. If it works, (K 1, K 2) is the key pair with high probability. 5. It takes O(255 x 256) = O(2111) steps on average. 7

Triple DES with Three Keys • Encryption: C = EK 3(DK 2(EK 1(P))). • If K 1 = K 3, we have 3 DES with 2 keys. • If K 1 = K 2 = K 3, we have the regular DES. • So, 3 DES w/ 3 keys is backward compatible with 3 DES w/ 2 keys and with the regular DES • Some internet applications have adopted 3 DES with three keys. – E. g. PGP and S/MIME. 8
Finite Fields Some mathematics used in AES



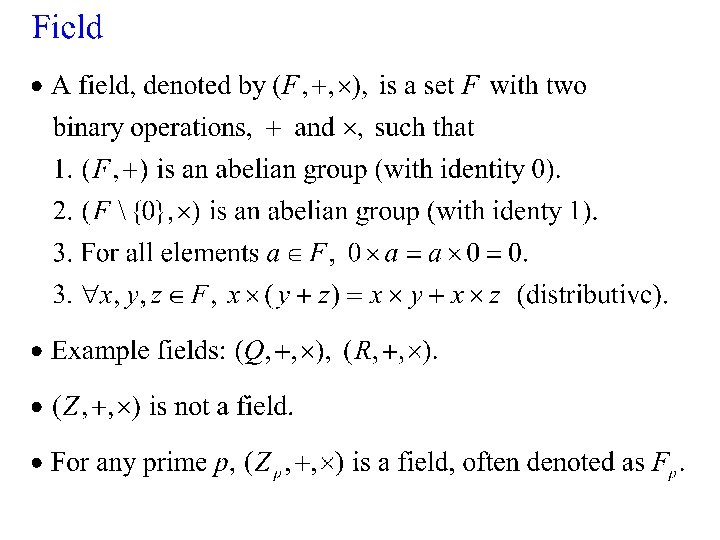


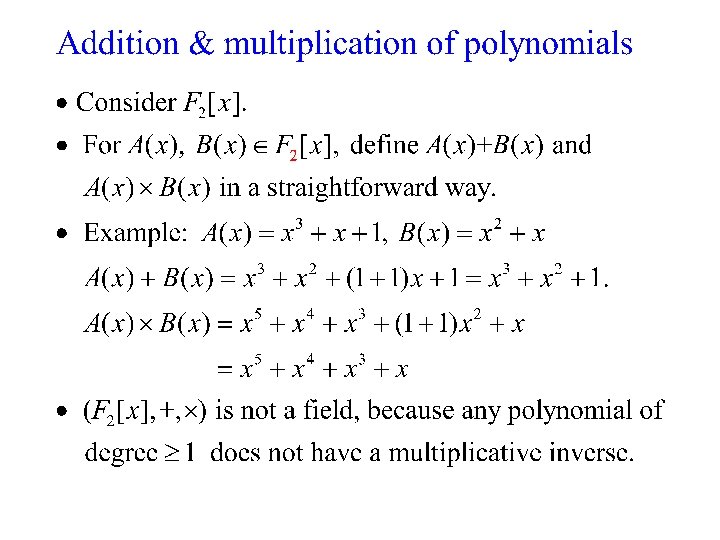

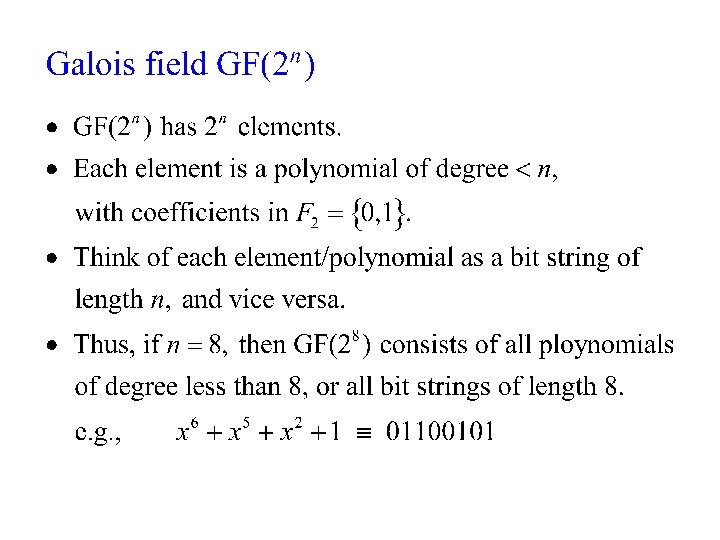

AES: Advanced Encryption Standard
AES: Advanced Encryption Standard • In 1997, NIST began the process of choosing a replacement for DES and called it the Advanced Encryption Standard. • Requirements: block length of 128 bits, key lengths of 128, 192, and 256 bits. • In 2000, Rijndael cipher (by Rijmen and Daemen) was selected. • An iterated cipher, with 10, 12, or 14 rounds. • Rijndael allows various block lengths. • But AES allows only one block size: 128 bits. 20

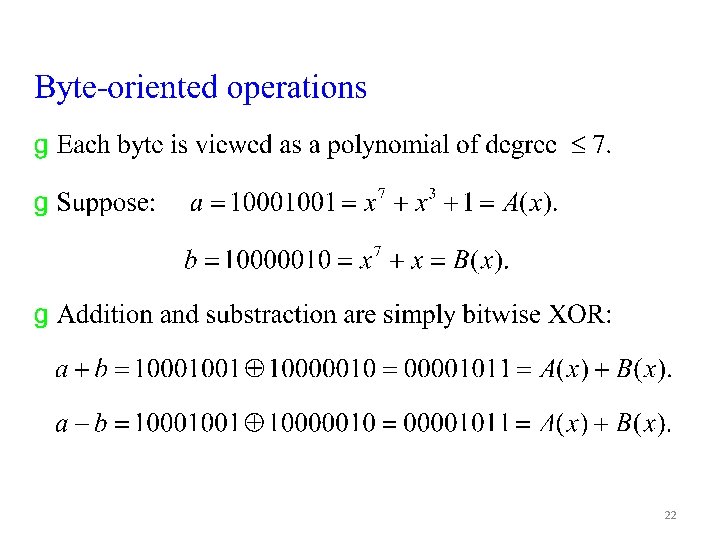
22
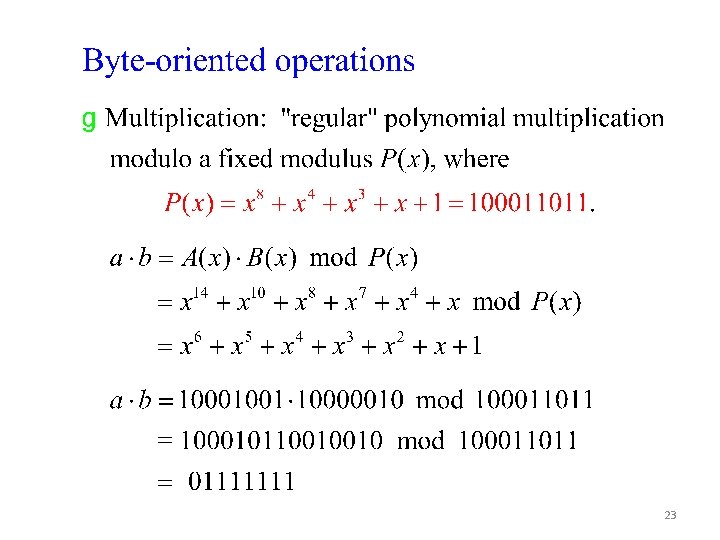
23

24
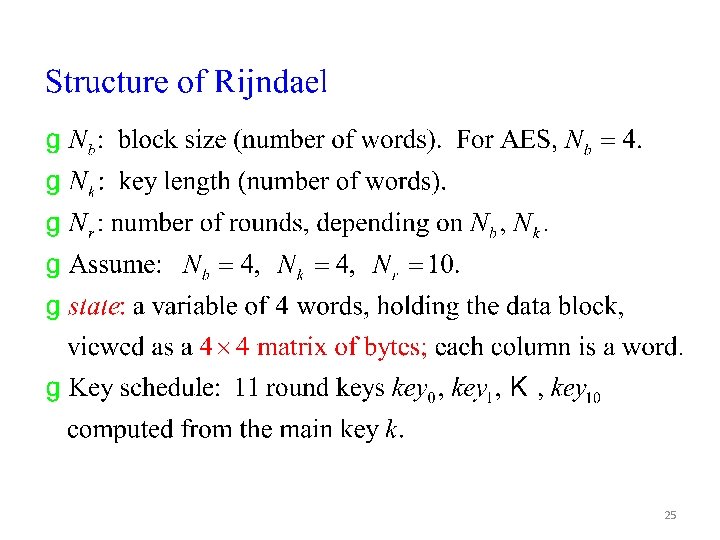
25

26

Figure 5. 1 AES Encryption and Decryption 27

28
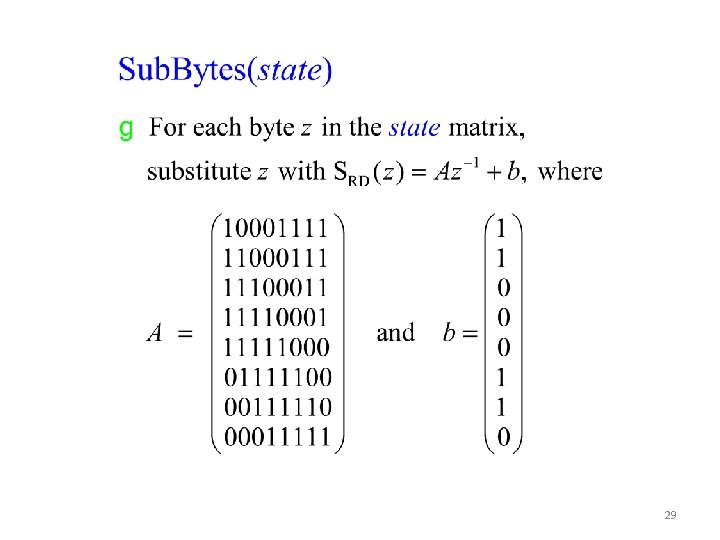
29

30

31
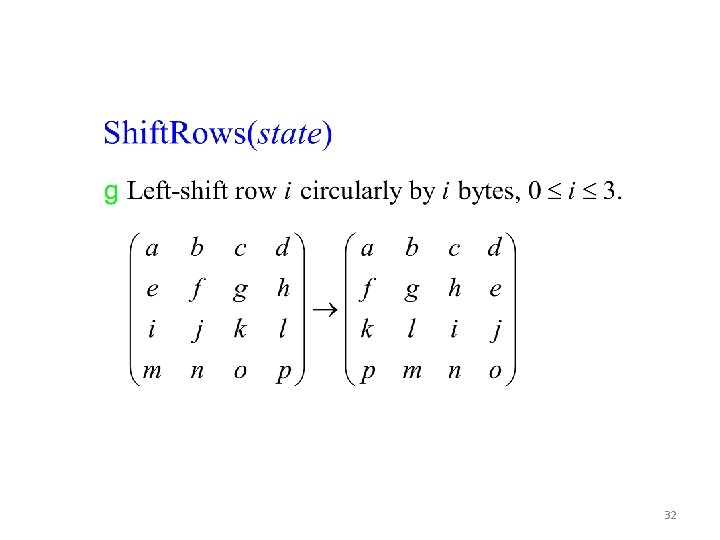
32
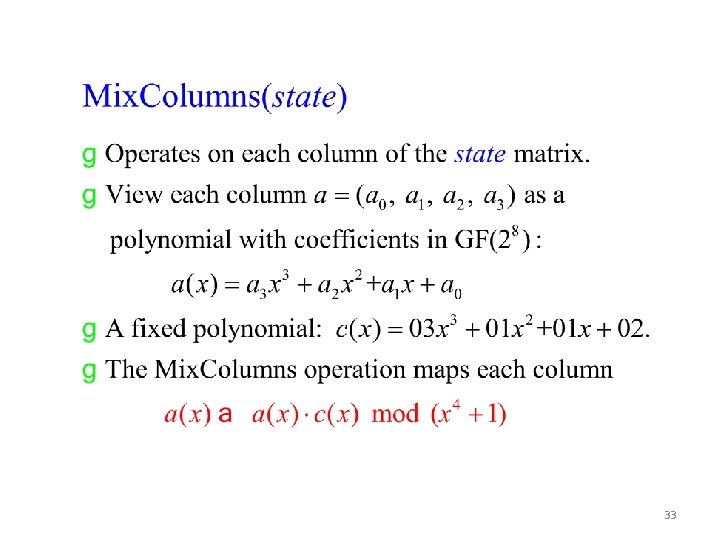
33

34
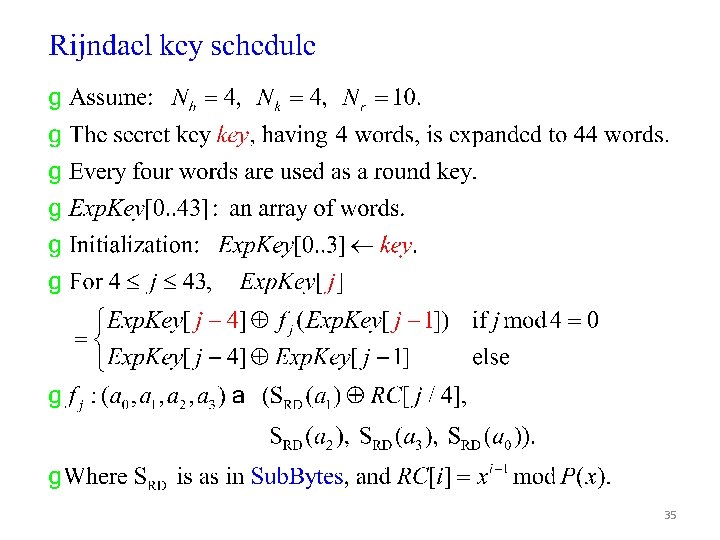
35

Modes of Operations

How to use a block cipher? • Block ciphers encrypt fixed size blocks – E. g. DES encrypts 64 -bit blocks • We need some way to encrypt arbitrary amounts of data – E. g. a message of 1000 bytes • NIST defines five ways to do it – Called modes of operations – Including block and stream modes 37

Five Modes of Operation – Electronic codebook mode (ECB) – Cipher block chaining mode (CBC) – most popular – Output feedback mode (OFB) – Cipher feedback mode (CFB) – Counter mode (CTR) 38

Electronic Code Book (ECB) • The plaintext is broken into blocks, P 1, P 2, P 3, . . . • Each block is encrypted independently of the other blocks Ci = EK(Pi) • For a given key, this mode behaves like we have a gigantic codebook, in which each plaintext block has an entry, hence the name Electronic Code Book 39

Remarks on ECB • Strength: it’s simple. • Weakness: – Repetitive information contained in the plaintext may show in the ciphertext, if aligned with blocks. – If the same message (e. g. , your SSN) is encrypted (with the same key) and sent twice, their ciphertexts are the same. • Typical application: secure transmission of short pieces of information (e. g. an encryption key) 40
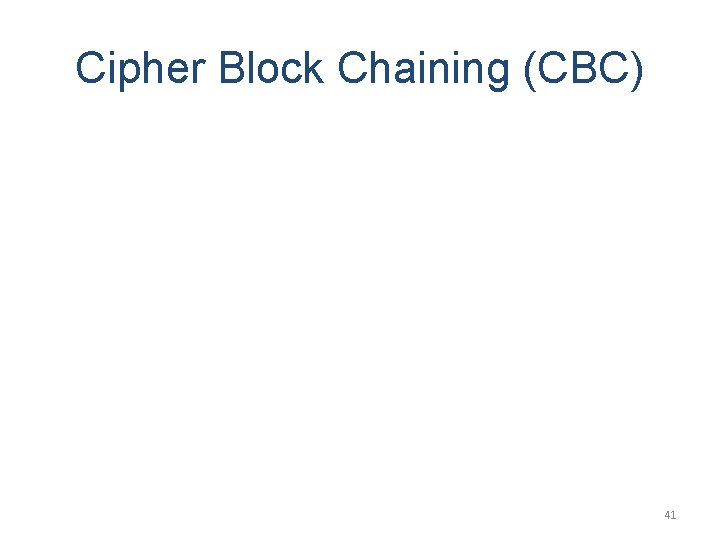
Cipher Block Chaining (CBC) 41
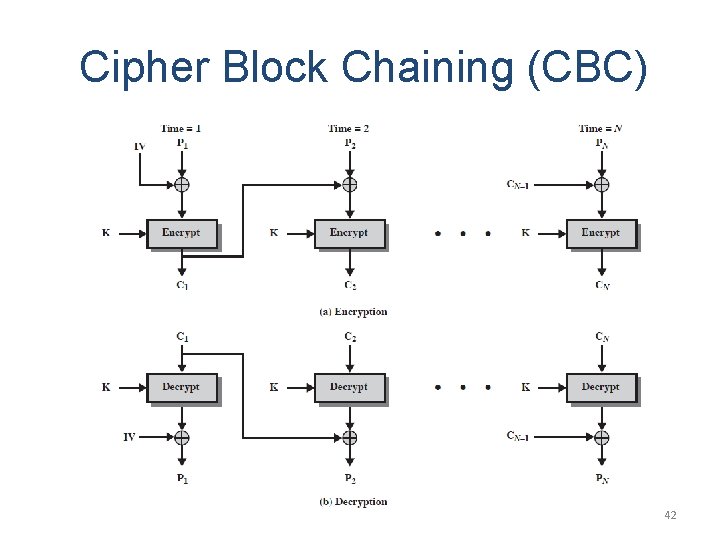
Cipher Block Chaining (CBC) 42
Remarks on CBC • The same key is used for all blocks. • A ciphertext block depends on all blocks before it. • So, repeated plaintext blocks are encrypted differently. • Initialization Vector (IV) – Must be known to both the sender & receiver – Typically, IV is either a fixed value – Or is sent encrypted in ECB mode before the rest of message. 43

Message Padding • The last plaintext block may be short of a whole block and needs padding: • Possible padding: – – Known non-data values (e. g. nulls) Or a number indicating the size of the pad Or a number indicating the size of the plaintext The last two schemes may require an extra block. 44
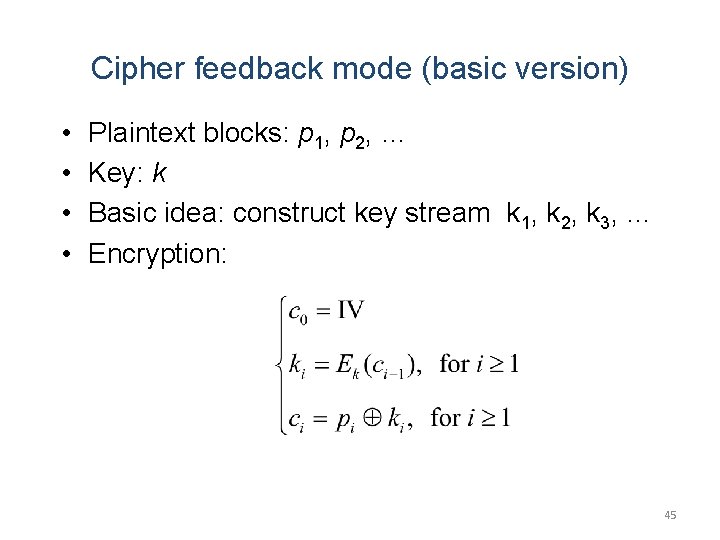
Cipher feedback mode (basic version) • • Plaintext blocks: p 1, p 2, … Key: k Basic idea: construct key stream k 1, k 2, k 3, … Encryption: 45
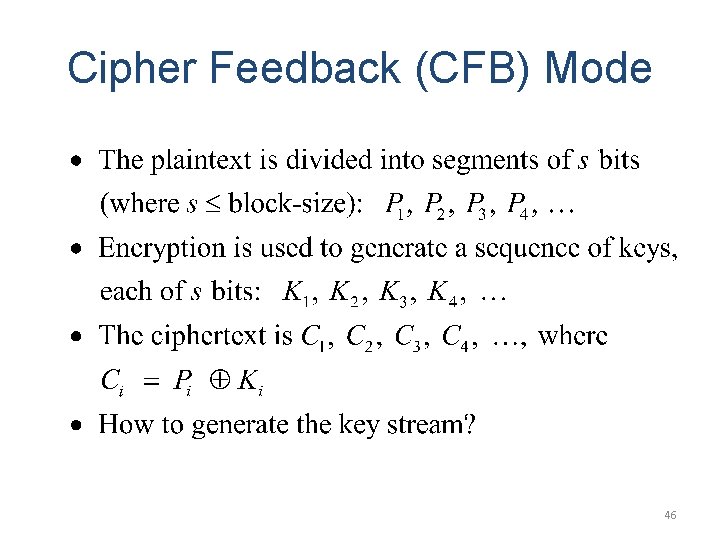
Cipher Feedback (CFB) Mode 46
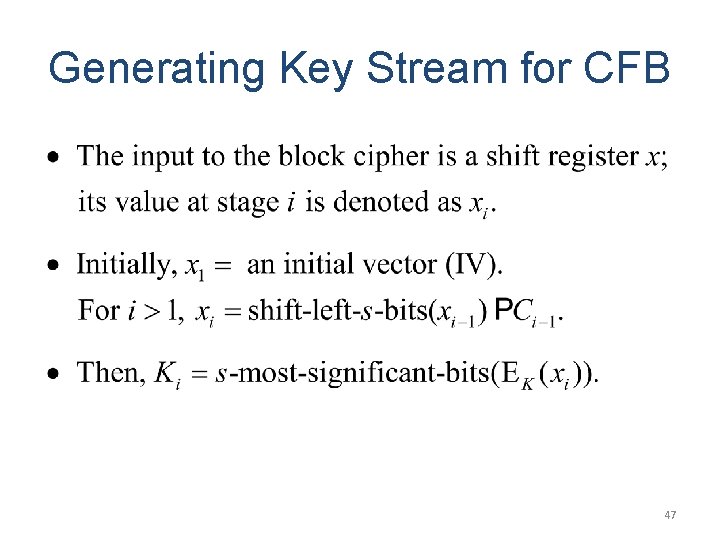
Generating Key Stream for CFB 47
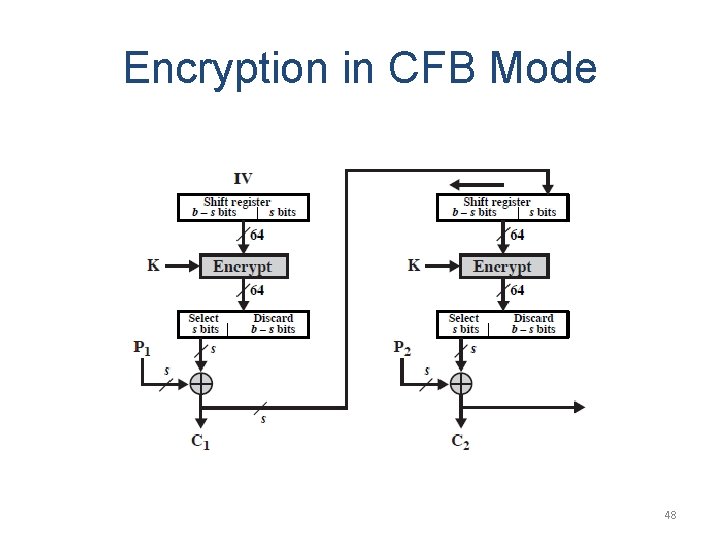
Encryption in CFB Mode 48
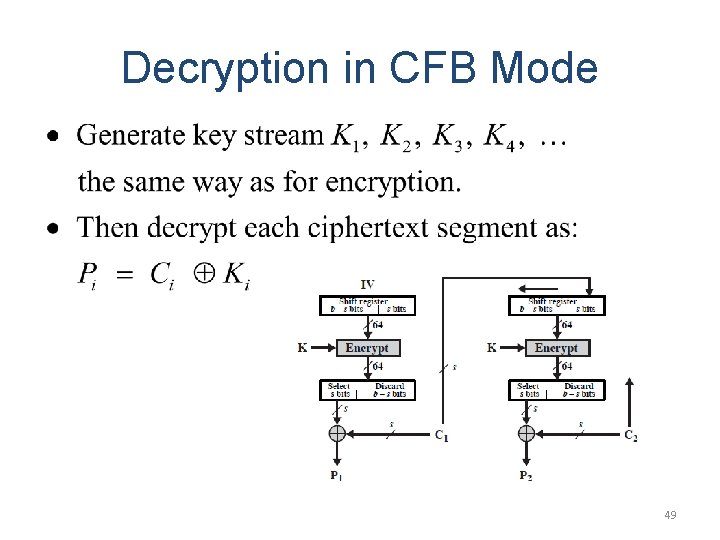
Decryption in CFB Mode 49
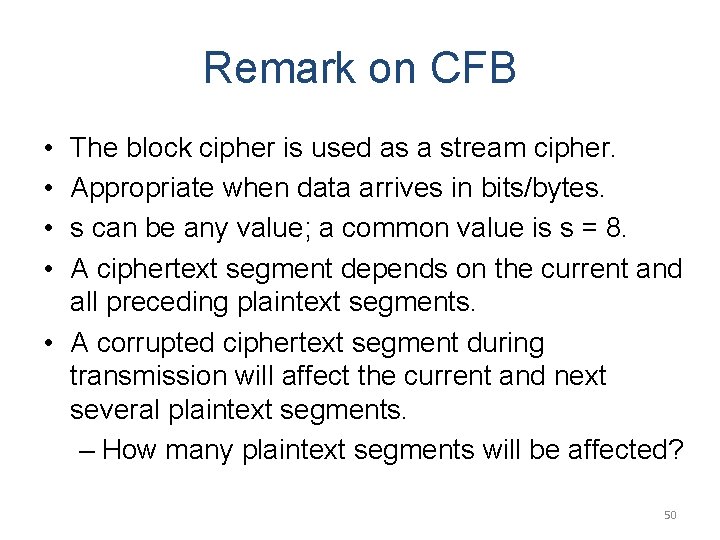
Remark on CFB • • The block cipher is used as a stream cipher. Appropriate when data arrives in bits/bytes. s can be any value; a common value is s = 8. A ciphertext segment depends on the current and all preceding plaintext segments. • A corrupted ciphertext segment during transmission will affect the current and next several plaintext segments. – How many plaintext segments will be affected? 50
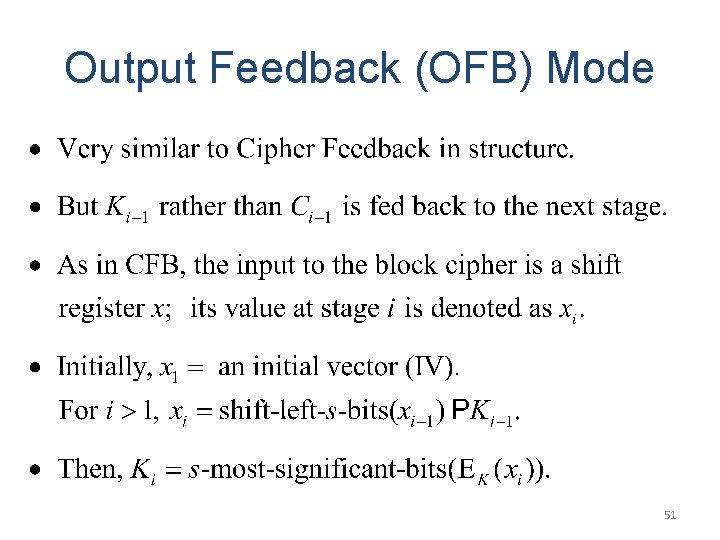
Output Feedback (OFB) Mode 51
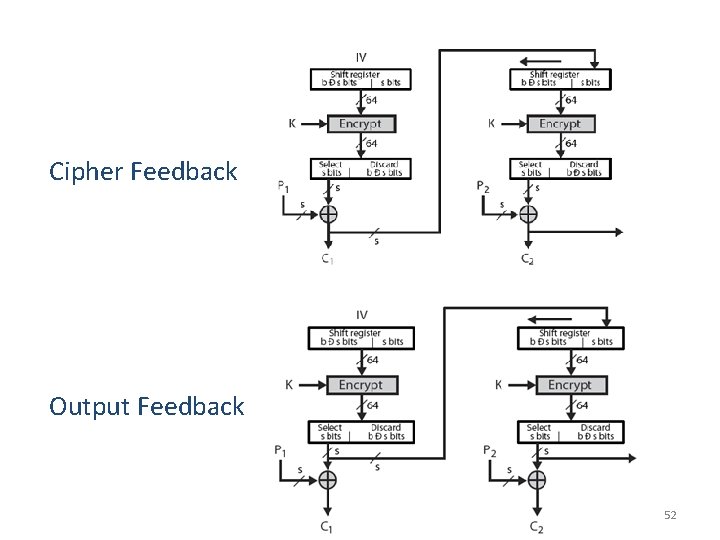
Cipher Feedback Output Feedback 52
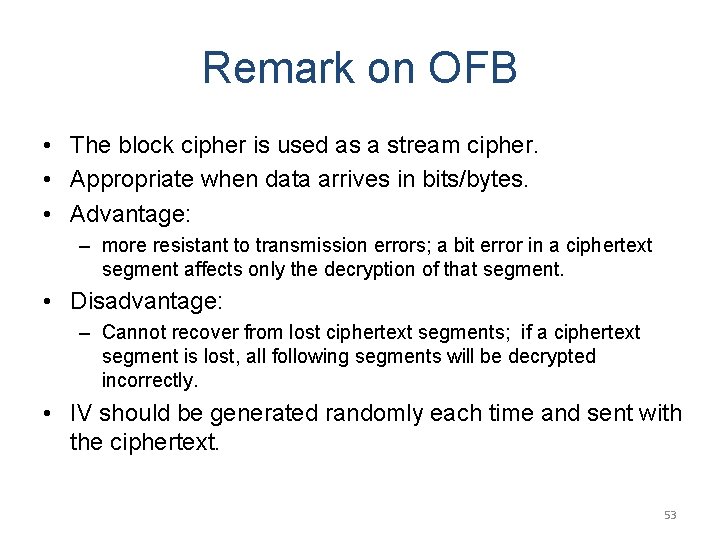
Remark on OFB • The block cipher is used as a stream cipher. • Appropriate when data arrives in bits/bytes. • Advantage: – more resistant to transmission errors; a bit error in a ciphertext segment affects only the decryption of that segment. • Disadvantage: – Cannot recover from lost ciphertext segments; if a ciphertext segment is lost, all following segments will be decrypted incorrectly. • IV should be generated randomly each time and sent with the ciphertext. 53
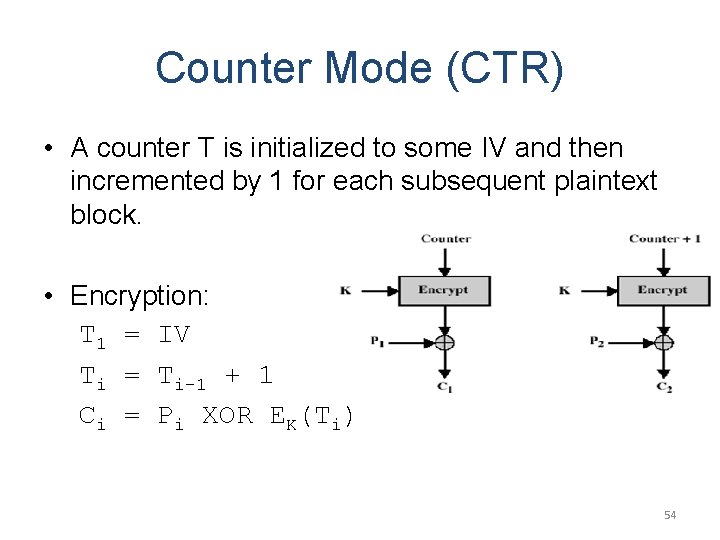
Counter Mode (CTR) • A counter T is initialized to some IV and then incremented by 1 for each subsequent plaintext block. • Encryption: T 1 = IV Ti = Ti-1 + 1 Ci = Pi XOR EK(Ti) 54
Remark on CTR • Strengthes: – Needs only the encryption algorithm (so do CFB and OFB) – Fast encryption/decryption; blocks can be processed (encrypted or decrypted) in parallel; good for high speed links – Random access to encrypted data blocks • As in OFB, IV should not be reused. 55

Stream Ciphers
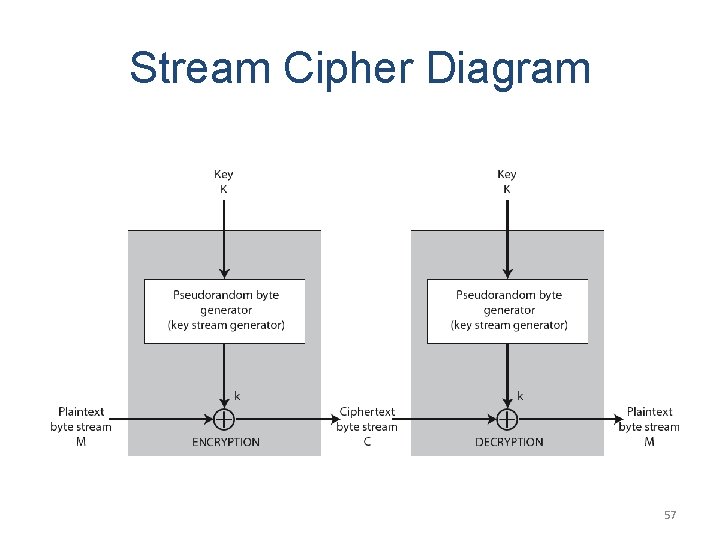
Stream Cipher Diagram 57
Stream Ciphers 58

Stream Ciphers 59

The RC 4 Stream Cipher • • • Designed by Ron Rivest in 1987 for RSA Security. Kept as a trade secret until leaked out in 1994. The most popular stream cipher. Simple and fast. With a 128 bits key, the period is > 10100. Used in the SSL/TLS standards (for secure Web communication), IEEE 802. 11 wireless LAN standard, Microsoft Point-to-Point Encryption, and many others. 60
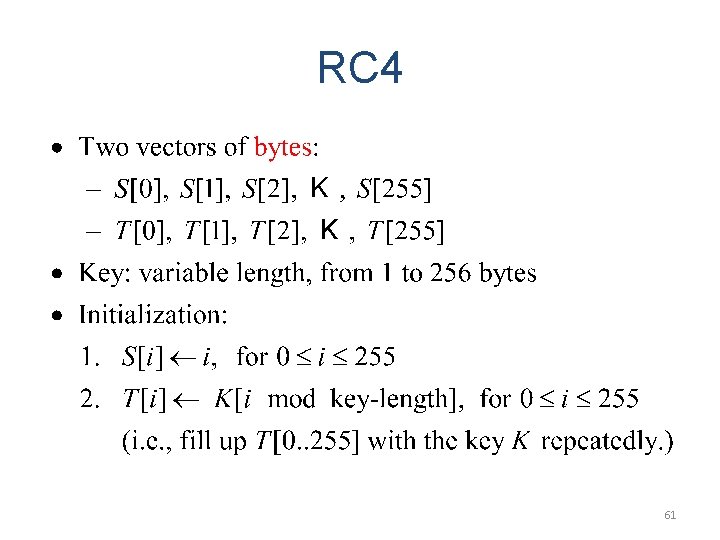
RC 4 61
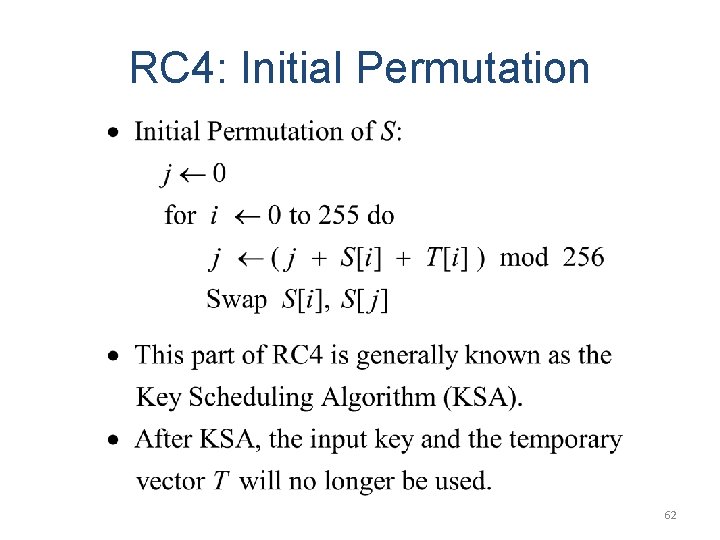
RC 4: Initial Permutation 62
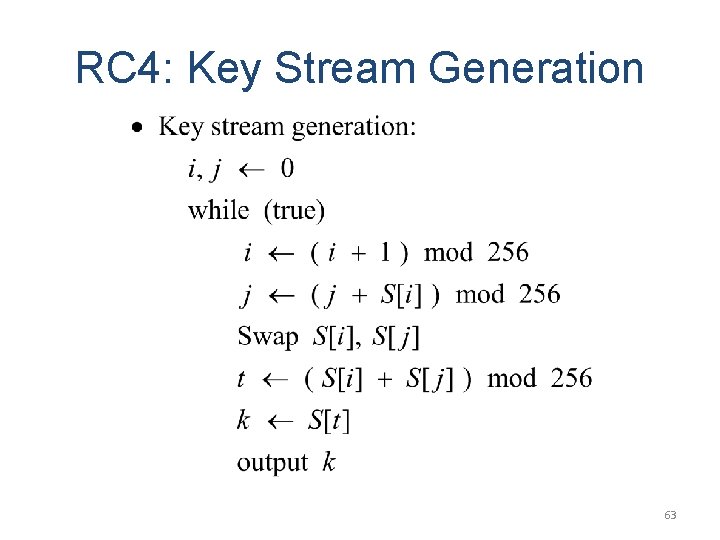
RC 4: Key Stream Generation 63
Security of RC 4 • The keystream generated by RC 4 is biased. – The second byte is biased toward zero with high probability. – The first few bytes are strongly non-random and leak information about the input key. • Defense: discard the initial n bytes of the keystream. – Called “RC 4 -drop[n-bytes]”. – Recommended values for n = 256, 768, or 3072 bytes. • Efforts are underway (e. g. the e. STREAM project) to develop more secure stream ciphers. 64
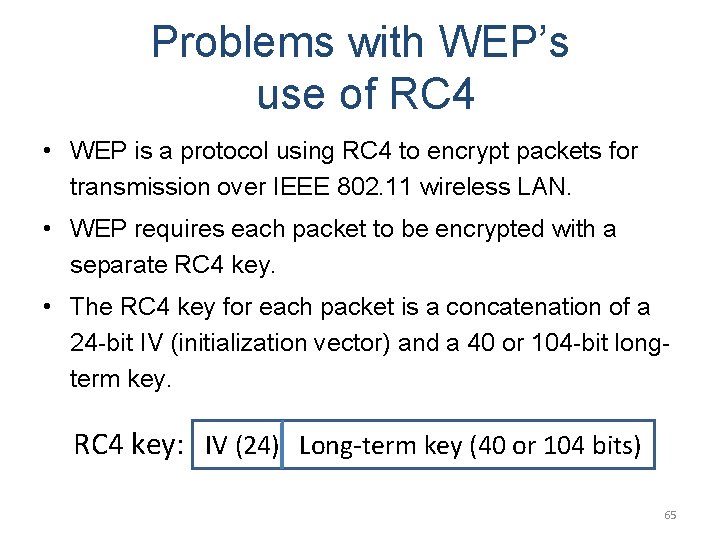
Problems with WEP’s use of RC 4 • WEP is a protocol using RC 4 to encrypt packets for transmission over IEEE 802. 11 wireless LAN. • WEP requires each packet to be encrypted with a separate RC 4 key. • The RC 4 key for each packet is a concatenation of a 24 -bit IV (initialization vector) and a 40 or 104 -bit longterm key. RC 4 key: IV (24) Long-term lkey (40 or 104 bits) 65
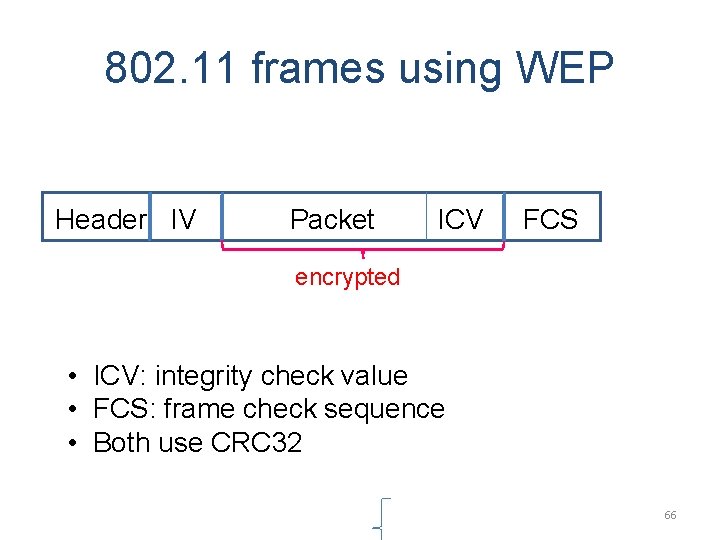
802. 11 frames using WEP Header IV l Packet ICV FCS encrypted • ICV: integrity check value • FCS: frame check sequence • Both use CRC 32 66

• Fluhrer, Mantin, and Shamir showed that: • If the same secret key is used with numerous IVs, and the attacker can obtain the first word of RC 4 output (keystream) corresponding to each IV, then he can construct the secret key with little effort. • The first word is known for many plaintext packets. • Recall: Ciphertext = plaintext XOR keystream • So, the first word of RC output (keystream) can be obtained. 67

• Tews, Weinmann, and Pyshkin wrote an article, “Breaking 104 bit WEP in less than 60 seconds, ” discussing how to discover the RC 4 key by analyzing the easily identified ARP packets. • ARP: Address Resolution Protocol. 68
- Slides: 68