2018 2019 Term 1 INTRODUCTION TO COMPUTER NETWORKS












- Slides: 24

2018 -2019 Term 1 INTRODUCTION TO COMPUTER NETWORKS

How two friends can communicate with each other nowadays?

Network

Lesson 1 Objectives: • • Describe how networks are used in real life (home, school, work) Explain cyber security Describe the different types of hackers Discuss advantages and disadvantages of computer networks. Use real life scenarios. Explain LANs and WANs. Discuss network topologies 4

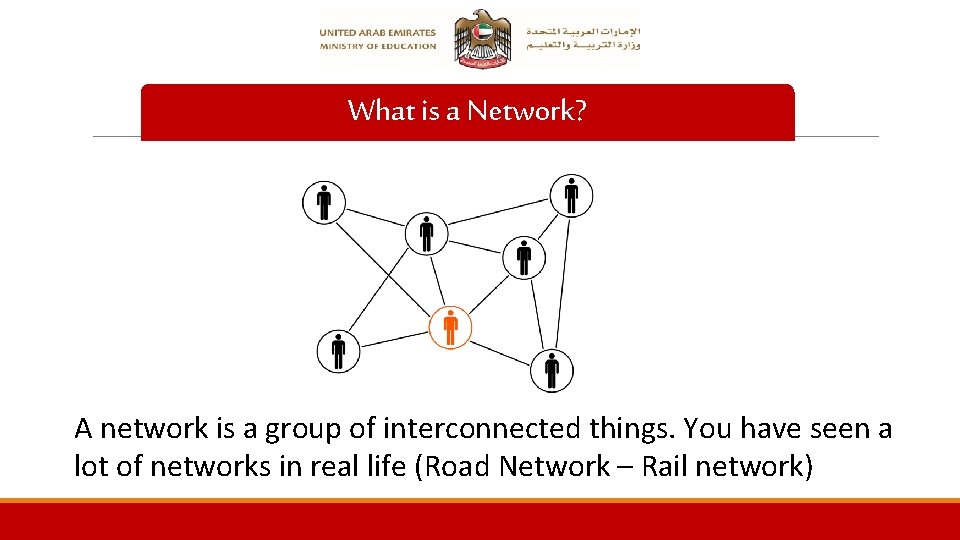
What is a Network? A network is a group of interconnected things. You have seen a lot of networks in real life (Road Network – Rail network)

Activity 1 – Page 12

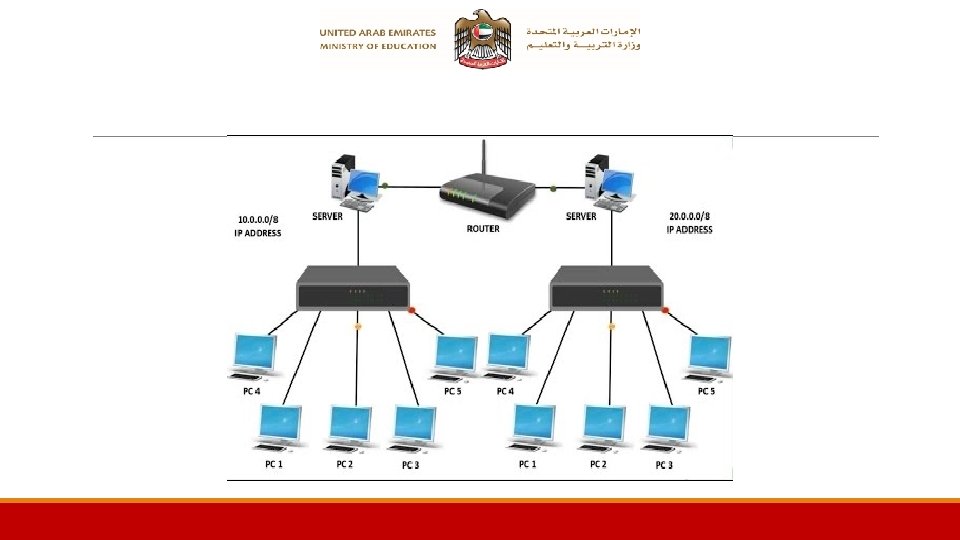
What is a Computer Network? A computer network is a group of computers and other devices that are connected using cables or radio signals.


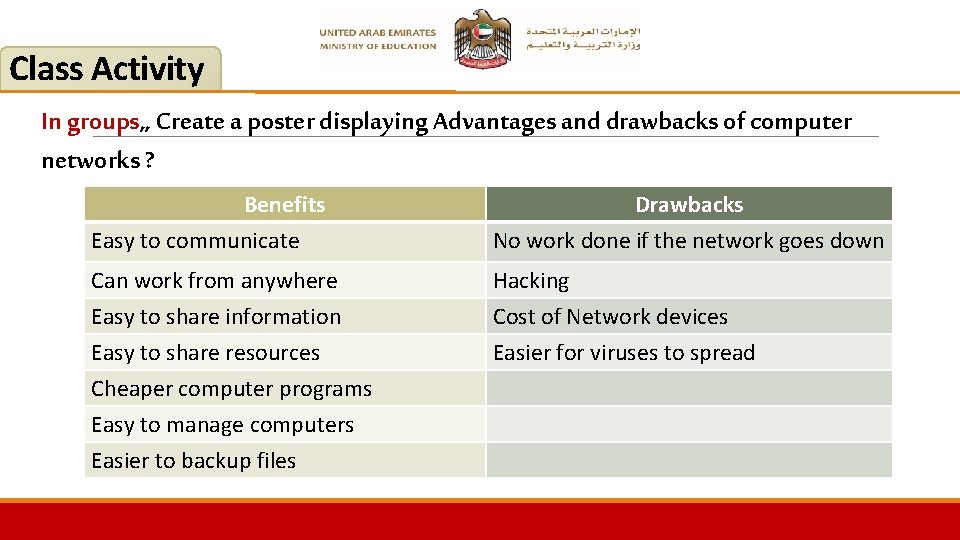
Class Activity In groups, , Create a poster displaying Advantages and drawbacks of computer networks ? Benefits Easy to communicate Drawbacks No work done if the network goes down Can work from anywhere Easy to share information Easy to share resources Cheaper computer programs Easy to manage computers Easier to backup files Hacking Cost of Network devices Easier for viruses to spread

Activity 2 – Page 16 Case Study • • One person can view Slower in delivery Can be affected by virus Data can be lost • Can be shared by all followers • Fast to upload and share

Cyber Security - Hackers Black Hat Hackers illegally access computers to steal information , cause damage to computer system or can be involved in espionage. White Hat Hackers used by companies to hack their systems to find out the weaknesses in their systems

Cyber Security Cyber security – Ethical Hacking is designed to protect computer systems theft, damage and disruption.

Cyber Security – UAE law The UAE has clear and strict laws against cybercrimes, with various penalties that can include lengthy prison terms and fines of up to Dh 3 million. UAE Cybercrime Law No. 5 of 2012, which was issued by the President, His Highness Shaikh Khalifa bin Zayed Al Nahyan, includes a range of violations and penalties, with fines ranging between Dh 50, 000 and Dh 3 million depending on the type and severity of offence.

Activity 3 – Page 18 Identify type of hackers?

Types of Computer Networks Study the three types of the computer in your group and present the different types in a poster ? You will be supplied by A 3 paper – Marker –wool -glue?

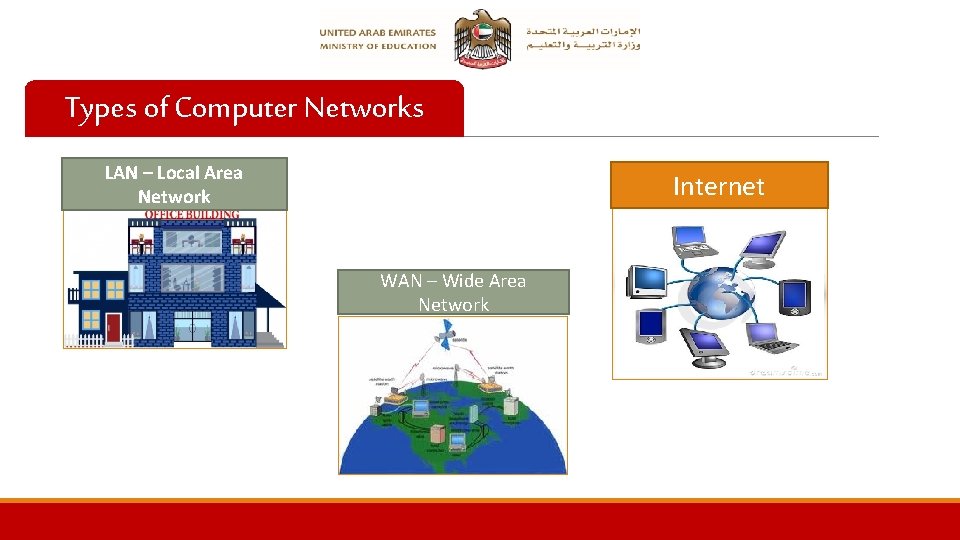
Types of Computer Networks LAN – Local Area Network Internet WAN – Wide Area Network

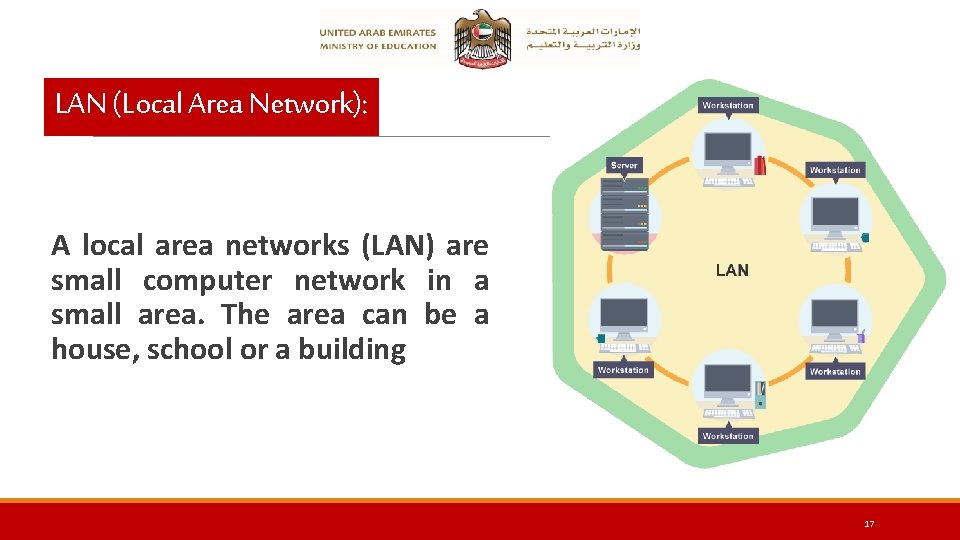
LAN (Local Area Network): A local area networks (LAN) are small computer network in a small area. The area can be a house, school or a building 17

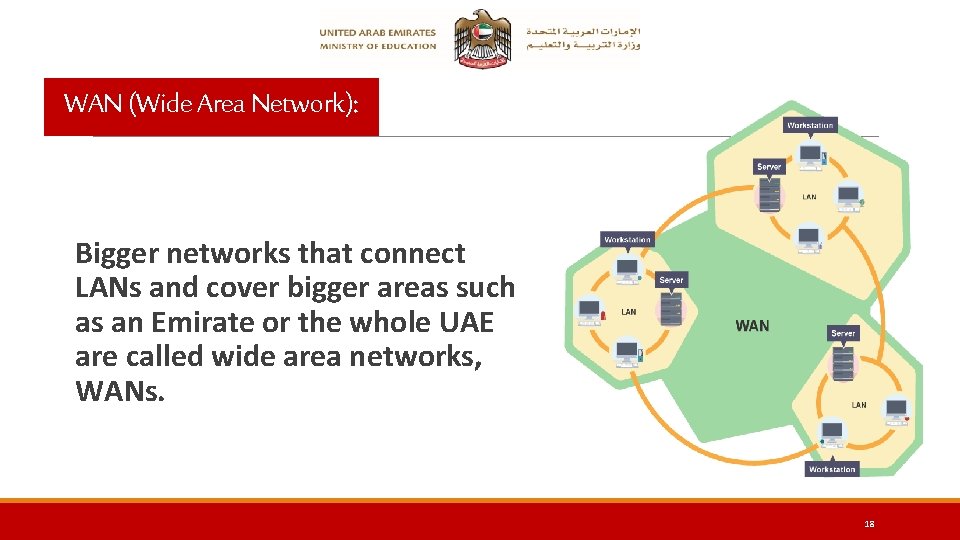
WAN (Wide Area Network): Bigger networks that connect LANs and cover bigger areas such as an Emirate or the whole UAE are called wide area networks, WANs. 18

Internet The Internet is a global network connecting computers around the world. Used for : ü Searching ü Massaging ü Playing games ü Watching videos 19

Activity 4 & 5– Pages 22 -23 Identify type of networks?

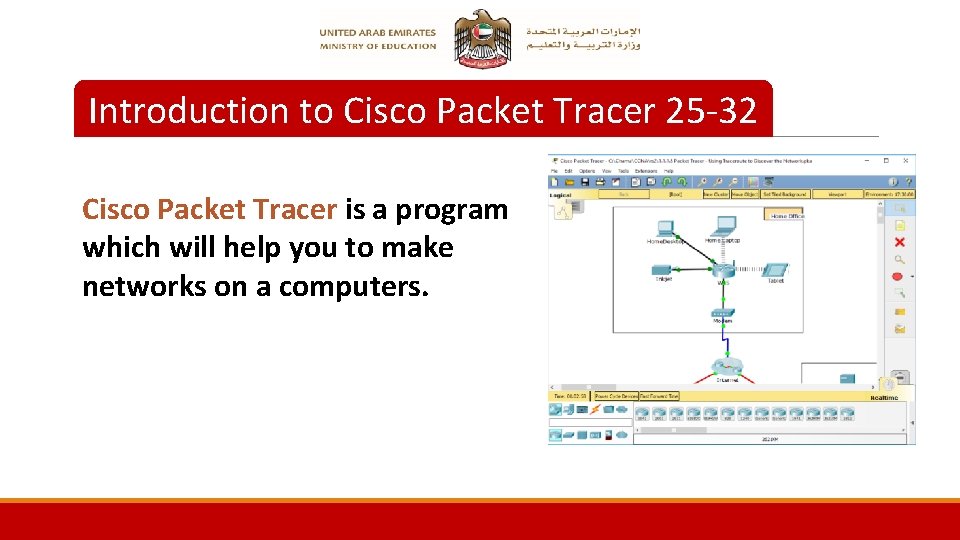
Introduction to Cisco Packet Tracer 25 -32 Cisco Packet Tracer is a program which will help you to make networks on a computers.

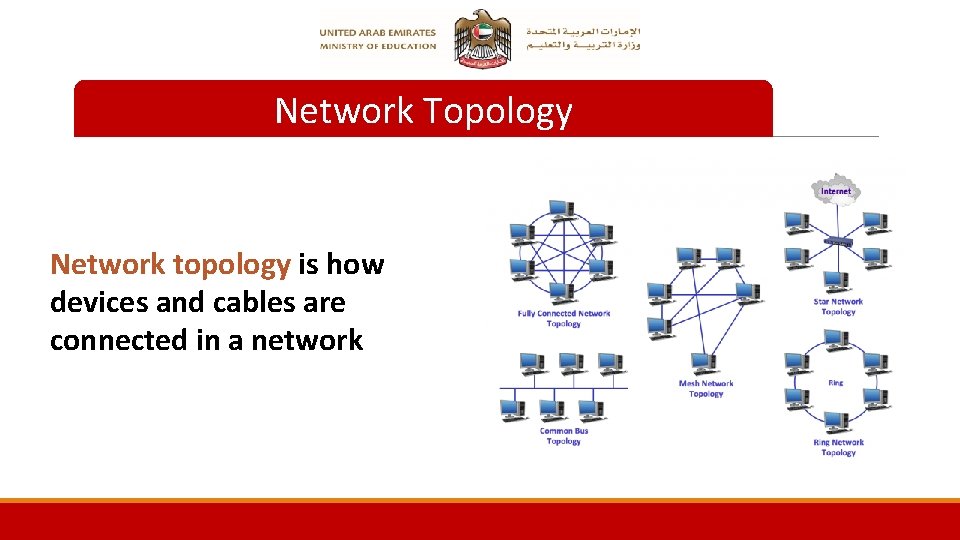
Network Topology Network topology is how devices and cables are connected in a network

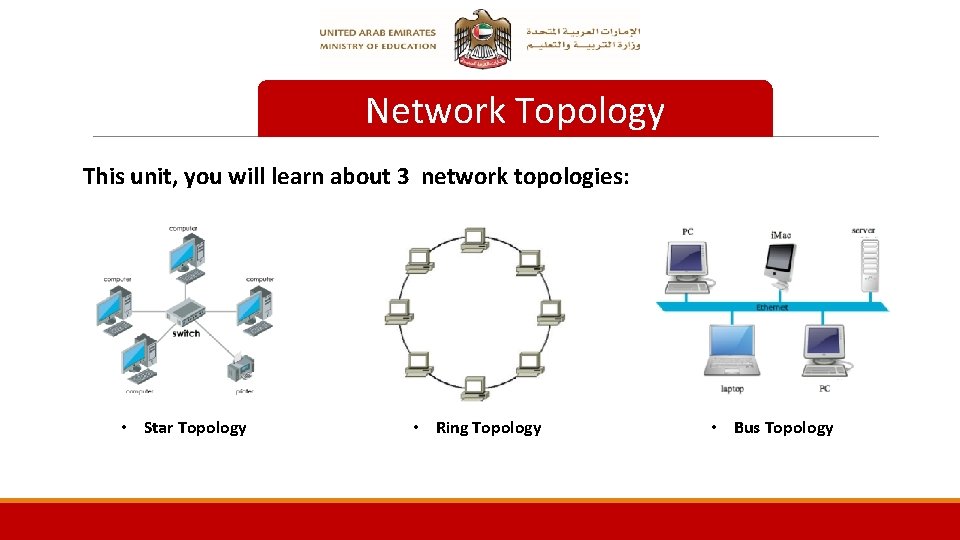
Network Topology This unit, you will learn about 3 network topologies: • Star Topology • Ring Topology • Bus Topology

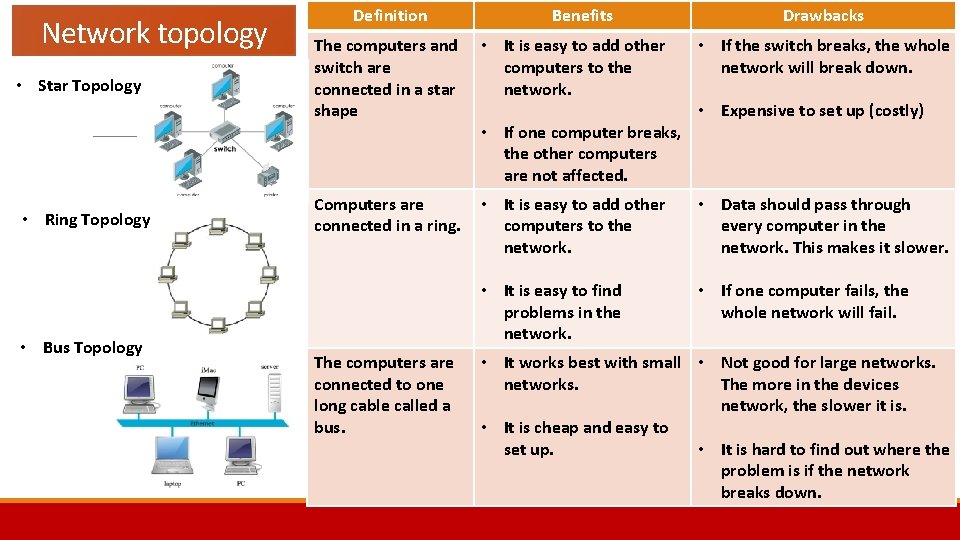
Network topology • Star Topology • Ring Topology • Bus Topology Definition Benefits Drawbacks The computers and switch are connected in a star shape • It is easy to add other computers to the network. Computers are connected in a ring. • It is easy to add other computers to the network. • Data should pass through every computer in the network. This makes it slower. • It is easy to find problems in the network. • If one computer fails, the whole network will fail. The computers are connected to one long cable called a bus. • If one computer breaks, the other computers are not affected. • If the switch breaks, the whole network will break down. • Expensive to set up (costly) • It works best with small • Not good for large networks. The more in the devices network, the slower it is. • It is cheap and easy to set up. • It is hard to find out where the problem is if the network breaks down.