2016 RSM US LLP All Rights Reserved Cybersecurity

© 2016 RSM US LLP. All Rights Reserved.
Cybersecurity Readiness & Incident Response January 8, 2016 © 2016 RSM US LLP. All Rights Reserved.
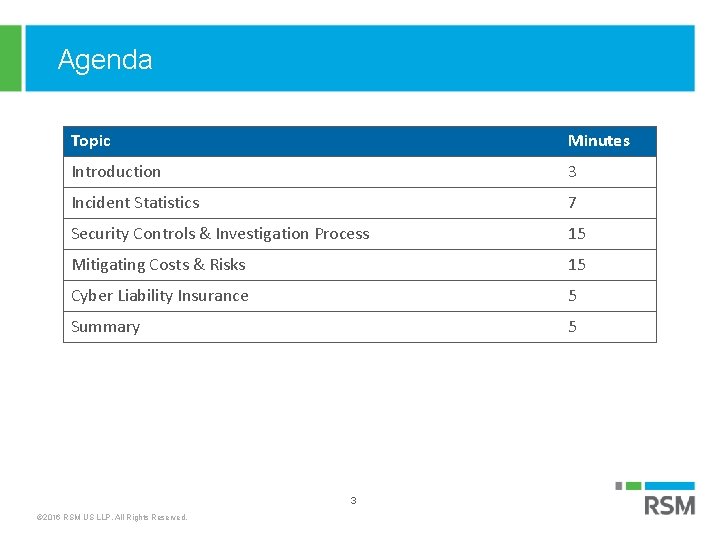
Agenda Topic Minutes Introduction 3 Incident Statistics 7 Security Controls & Investigation Process 15 Mitigating Costs & Risks 15 Cyber Liability Insurance 5 Summary 5 3 © 2016 RSM US LLP. All Rights Reserved.
With you today Director, Risk Advisory Services Atlanta Office Internal Audit / SOX / ERM (M) 404. 449. 4877 Ian. Burnett@rsmus. com EMPLOYMENT HISTORY • RSM – since 2014 • Crowe Horwath – 2012 -2014, Business Risk Consulting • Cumulus Media – 2009 -2012, Director of IA and Compliance • Deloitte – 2007 -2009, Enterprise Risk Services • KPMG – 1999 -2007, Advisory Services • Coca-Cola – 1995 -1999, Corporate Audit / Controller’s Group • Accenture – 1992 -1995, System Integration Consulting • Sun. Trust – 1988 -1992, Internal Audit / International Division 4 © 2016 RSM US LLP. All Rights Reserved.
With you today Director, Security and Privacy Services Boston Office National Leader – Digital Forensics, e. Discovery, and Data Privacy/Breach (M) 508. 922. 4770 Andy. Obuchowski@rsmus. co m EMPLOYMENT HISTORY • RSM – since 2013 • Navigant – National leader (Digital Forensics/Data Breach) • Kroll – Leader (Cyber Security, Data Breach, Forensics) • CIGNA – (e. Discovery, Investigations, Forensics, Cyber Security) • 13+ Years in Boston area law enforcement & Special US Marshall • Police Academy Instructor • Adjunct Professor (Current) • Masters in National Security • NSA Information Security Professional • Expert Testimony/Report Writing 5 © 2016 RSM US LLP. All Rights Reserved.

Experience the power of being understood On October 26, 2015 Mc. Gladrey LLP changed its name to RSM US LLP and united with fellow firms in its global network under the common brand – RSM. 6 © 2016 RSM US LLP. All Rights Reserved.

RSM overview Fifth largest audit, tax and consulting firm in the U. S. • Over $1. 6 billion in revenue • 80 cities and more than 8, 000 employees in the United States • Internationally § Presence in more than 110 countries § More than 37, 000 people in over 740 offices § $4. 4 billion (U. S. ) in worldwide revenues 7 © 2016 RSM US LLP. All Rights Reserved.

RSM US locations 8 © 2016 RSM US LLP. All Rights Reserved.
RSM International locations 9 © 2016 RSM US LLP. All Rights Reserved.

INCIDENT STATISTICS Data Breach vs Information Security Incident © 2016 RSM US LLP. All Rights Reserved.
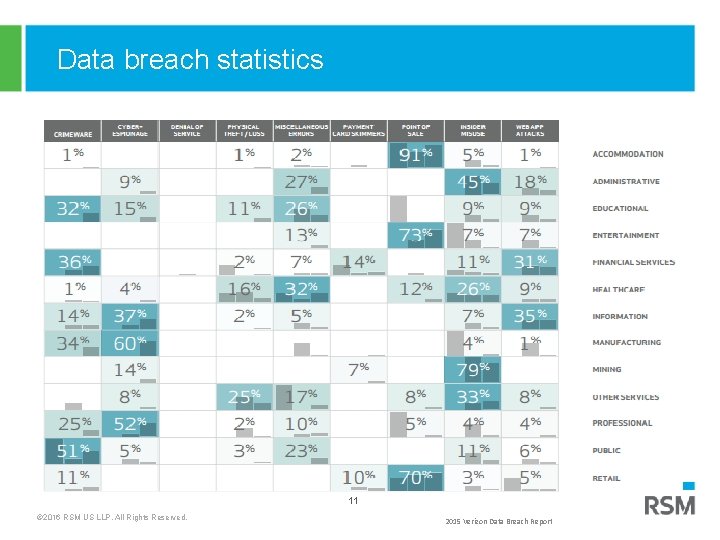
Data breach statistics 11 © 2016 RSM US LLP. All Rights Reserved. 2015 Verizon Data Breach Report
Security statistics Four most prevalent attack vectors 1. Hacking • “Traditional” hacking is used post-breach not as the original entry point • Current methods focus on web apps and browser plugins 2. Malware • Finding and purchasing non-detectable malware in the underground market is trivial • Modern anti-virus is an 80 -20 proposition at best 3. Social engineering • Why bother to do all the heavy lifting involved with “hacking” when you can just ask someone to do something for you? • While there is a technical component the attack is against human nature 4. Physical loss • Rare occurrence but significant impact 12 © 2016 RSM US LLP. All Rights Reserved.
Security statistics 13 © 2016 RSM US LLP. All Rights Reserved. 2014 Verizon Data Breach Report

SECURITY CONTROLS & INVESTIGATION PROCESS Prevention, Detection, & Correction © 2016 RSM US LLP. All Rights Reserved.
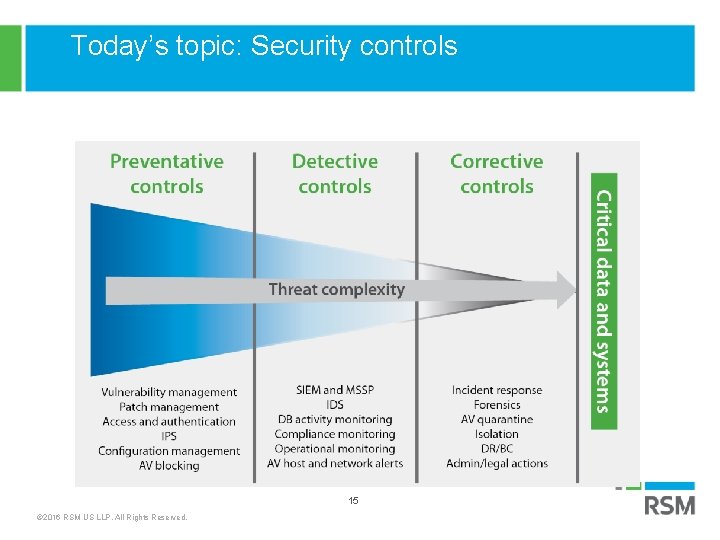
Today’s topic: Security controls can be preventive, detective or corrective by nature 15 © 2016 RSM US LLP. All Rights Reserved.
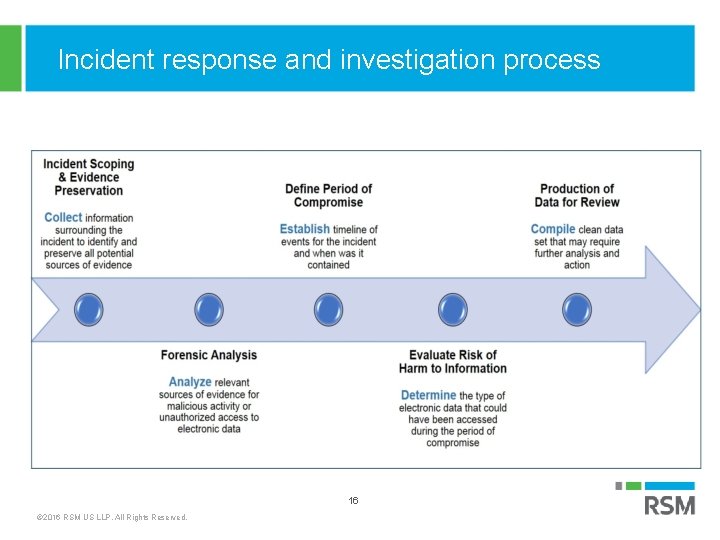
Incident response and investigation process 16 © 2016 RSM US LLP. All Rights Reserved.

Incident response § The initial objective is to learn about your organization and IT infrastructure and incident - What actions have been performed to date? What information did the attacker ask for and what did he receive? What known systems/information did the attacker access? Are there any remote tracking or wiping tools installed on the device? Does an employee have remote access to the network? Do logs show unusual network activity or failed login attempts? § Identifying potential evidence sources followed by the preservation/collection of data. 17 © 2016 RSM US LLP. All Rights Reserved.

Incident response § Evidence sources: § Network servers and applications § Computer system memory § Firewall, VPN, email, building access logs § Network and system backups § Information from third-party providers (cloud services) § Video surveillance 18 © 2016 RSM US LLP. All Rights Reserved.

Investigative hurdles § Investigating “unknowns” - Unable to identify appropriate resources - Third-party providers and custom applications § Evidence preservation – afterthought - Deleted digital evidence – expands scope/risk of harm - Lack of documentation, misconfigured applications, log retention § Data pooling - Human capital, accounting, user share data combined § Data quality § Non-standardized data formats § Manual review for protected information 19 © 2016 RSM US LLP. All Rights Reserved.

Incident response – Internal Audit questions § Is my organization’s IT staff appropriately trained to handle an information security incident? § Does my organization have the skill sets to conduct a forensic investigation? § Have we been through this type of incident before? § What was the result of previous incidents? § Does our organization know where our data is physically located? § Who within my organization is accountable for knowing where our data is physically stored? 20 © 2016 RSM US LLP. All Rights Reserved.

MITIGATING COSTS AND RISKS Avoid Financial and Reputational Risk of Harm © 2016 RSM US LLP. All Rights Reserved.
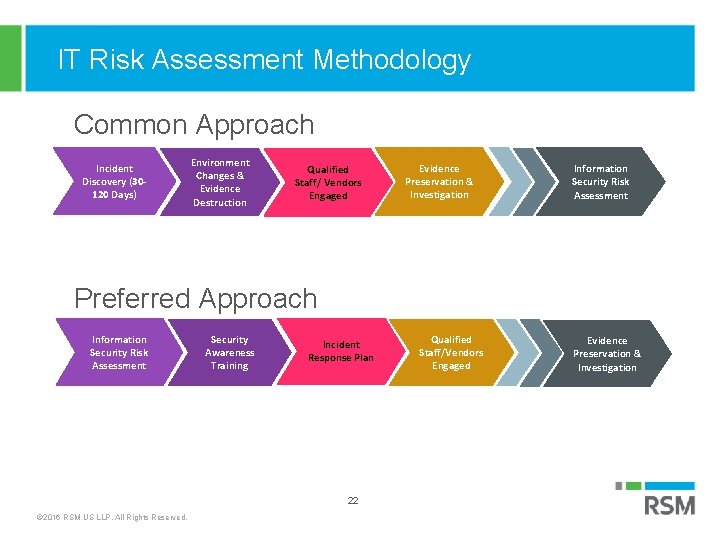
IT Risk Assessment Methodology Common Approach Low Demand Incident Discovery (30120 Days) Environment Changes & Evidence Destruction Qualified Staff/ Vendors Engaged Evidence Preservation & Investigation Information Security Risk Assessment Preferred Approach Low. Information Demand Security Risk Assessment Security Awareness Training Incident Response Plan Lessons Learned 22 © 2016 RSM US LLP. All Rights Reserved. Qualified Staff/Vendors Engaged Evidence Preservation & Investigation
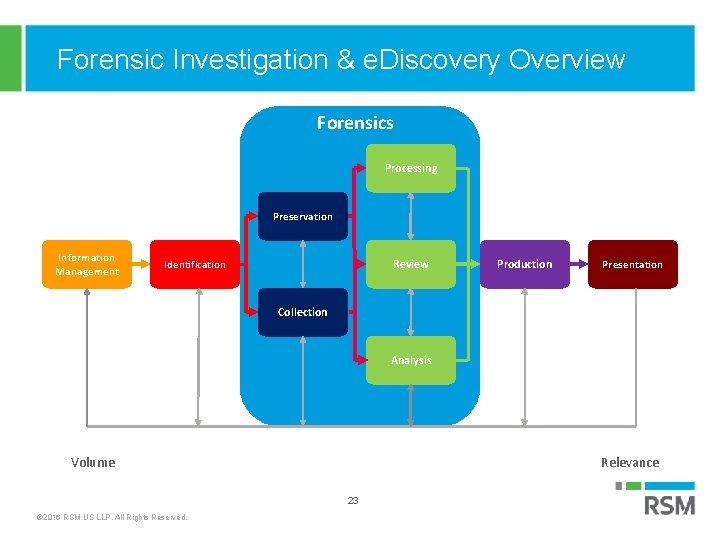
Forensic Investigation & e. Discovery Overview Forensics Processing Preservation Information Management Review Identification Production Presentation Collection Analysis Volume Electronic Discovery Reference Model (EDRM) 23 © 2016 RSM US LLP. All Rights Reserved. Relevance

Mitigating costs and risks - Administrative § Organizational Programs - Written Information Security Program (WISP) Vendor management Business continuity and disaster recovery plans § Specific Preparation Tasks - IT risk assessment Incident response plan Mock incident response drills Security awareness training § Response - Documentation • How was the incident discovered? Who performed what action? When did the change or event occur? What was the result? 24 © 2016 RSM US LLP. All Rights Reserved.
Mitigating costs and risks - Technical § Data segregation - Data classification/identification program § Network and application patch management § Backup and archiving solutions - Access to data backup and offsite facilities - Test archiving solutions (email, data vaults) - Speed of exports, change in file properties, search functionality § Network vulnerability testing § Enterprise monitoring solutions - Event logging (VPN, file audit, network access, building access) - Data Loss Prevention (DLP) solutions 25 © 2016 RSM US LLP. All Rights Reserved.

Mitigating costs and risks – Internal Audit questions § Has my organization’s IT staff tested the input and output of our email backup/archiving solution? § Does my organization have logs available to show who has accessed our network in the past week? § Who within my organization is accountable to review the logs? § Is there evidence that the logs are being reviewed? § What is my organization learning from reviewing the logs? § Is my organization doing enough to make us less vulnerable? 26 © 2016 RSM US LLP. All Rights Reserved.

CYBER LIABILITY INSURANCE Connected to Digital Foreniscs & Incident Response © 2016 RSM US LLP. All Rights Reserved.
Risk financing for data breach exposures § Not if, but when! § Data breach events may result in significant costs § More damage is caused by a poor response to a data breach than by the data breach itself § Insurance provides important balance sheet protection – and is ideal for difficult to predict events that create large losses § An insurance carrier can provide significant expertise in order to facilitate an effective and efficient response - Not the insurer’s first rodeo! 28 © 2016 RSM US LLP. All Rights Reserved.
Insurance overview § Security and privacy liability - Judgments, settlements and defense costs for a claim seeking damages from a loss, theft or unauthorized disclosure of information § Regulatory defense and penalties § Payment card industry (PCI) fines and penalties - Contractual fines and assessments for a failure to maintain PCI data security standards § Breach response costs - Expenses for: Computer forensics, notifications, credit monitoring, pre-claim legal, call center services and public relations § Other coverage options typically available - Media Liability - Business Interruption - Data Protection - Cyber Extortion 29 © 2016 RSM US LLP. All Rights Reserved.

RSM US LLP 1230 Peachtree St. , NE Suite 1700 Atlanta, GA 30309 +1 800. 274. 3978 www. rsmus. com This document contains general information, may be based on authorities that are subject to change, and is not a substitute for professional advice or services. This document does not constitute audit, tax, consulting, business, financial, investment, legal or other professional advice, and you should consult a qualified professional advisor before taking any action based on the information herein. RSM US LLP, its affiliates and related entities are not responsible for any loss resulting from or relating to reliance on this document by any person. RSM US LLP is a limited liability partnership and the U. S. member firm of RSM International, a global network of independent audit, tax and consulting firms. The member firms of RSM International collaborate to provide services to global clients, but are separate and distinct legal entities that cannot obligate each other. Each member firm is responsible only for its own acts and omissions, and not those of any other party. Visit rsmus. com/aboutus for more information regarding RSM US LLP and RSM International. RSM® and the RSM logo are registered trademarks of RSM International Association. The power of being understood® is a registered trademark of RSM US LLP. © 2016 RSM US LLP. All Rights Reserved.
- Slides: 30