2 Round MPC via MultiKey FHE Daniel Wichs

![Fully Homomorphic Encryption (FHE) [RAD 78, Gentry 09, …] Fully Homomorphic Encryption (FHE) [RAD 78, Gentry 09, …]](https://slidetodoc.com/presentation_image_h/3761cc8791277453b12088aa194e9d5f/image-2.jpg)
![Background on Multi-Key FHE • Proposed by [Lopez. Alt-Tromer-Vaikunatnathan ‘ 12] • construction based Background on Multi-Key FHE • Proposed by [Lopez. Alt-Tromer-Vaikunatnathan ‘ 12] • construction based](https://slidetodoc.com/presentation_image_h/3761cc8791277453b12088aa194e9d5f/image-5.jpg)
![Learning with Errors (LWE) [R 05] + = LWE assumption stat. far from uniform! Learning with Errors (LWE) [R 05] + = LWE assumption stat. far from uniform!](https://slidetodoc.com/presentation_image_h/3761cc8791277453b12088aa194e9d5f/image-9.jpg)
![Gadget Matrix G [Micciancio-Peikert ’ 12] Gadget Matrix G [Micciancio-Peikert ’ 12]](https://slidetodoc.com/presentation_image_h/3761cc8791277453b12088aa194e9d5f/image-14.jpg)



- Slides: 22

2 Round MPC via Multi-Key FHE Daniel Wichs (Northeastern University) with: Pratyay Mukherjee @ UC Berkeley
![Fully Homomorphic Encryption FHE RAD 78 Gentry 09 Fully Homomorphic Encryption (FHE) [RAD 78, Gentry 09, …]](https://slidetodoc.com/presentation_image_h/3761cc8791277453b12088aa194e9d5f/image-2.jpg)
Fully Homomorphic Encryption (FHE) [RAD 78, Gentry 09, …]

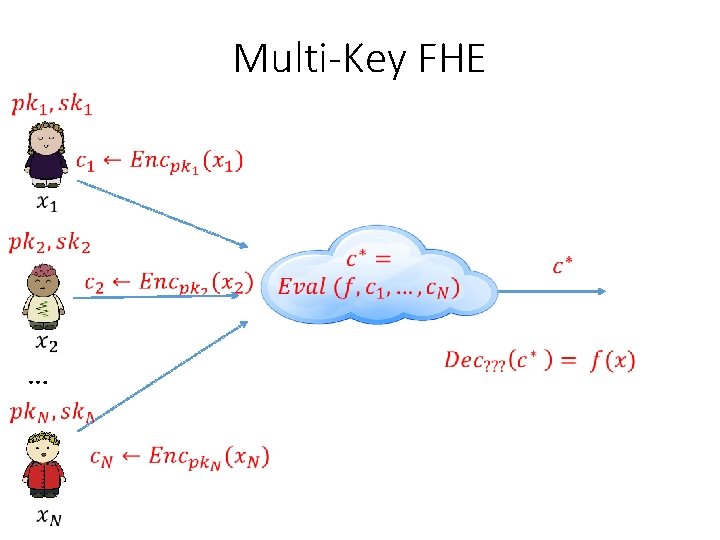
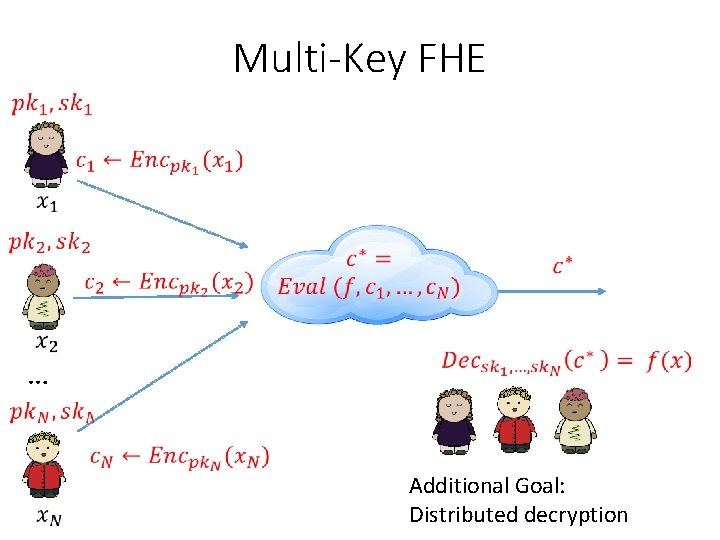
Multi-Key FHE …

Multi-Key FHE … Additional Goal: Distributed decryption
![Background on MultiKey FHE Proposed by Lopez AltTromerVaikunatnathan 12 construction based Background on Multi-Key FHE • Proposed by [Lopez. Alt-Tromer-Vaikunatnathan ‘ 12] • construction based](https://slidetodoc.com/presentation_image_h/3761cc8791277453b12088aa194e9d5f/image-5.jpg)
Background on Multi-Key FHE • Proposed by [Lopez. Alt-Tromer-Vaikunatnathan ‘ 12] • construction based on hard problems over ideal lattices • no distributed decryption • Construction from LWE [Clear-Mc. Goldrick ‘ 15] • complicated construction • no distributed decryption • Our Results: • simplified construction from LWE, adaptation of [GSW 13] FHE. • one round distributed decryption • application to multi-party computation

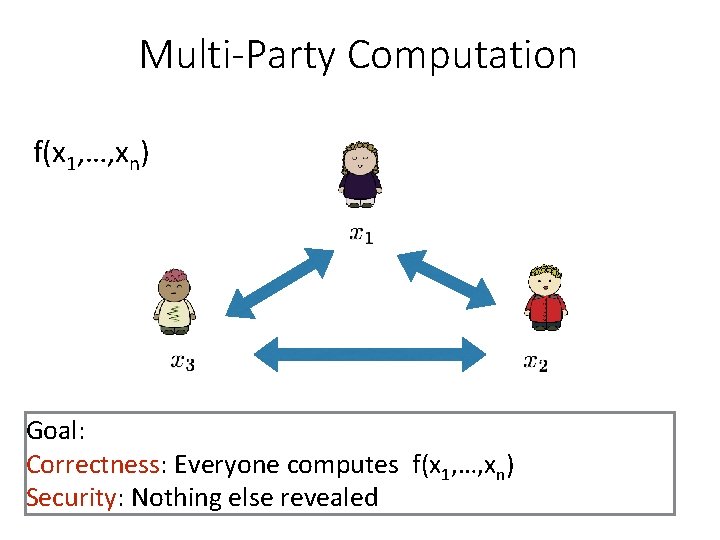
Multi-Party Computation f(x 1, …, xn) Goal: Correctness: Everyone computes f(x 1, …, xn) Security: Nothing else revealed

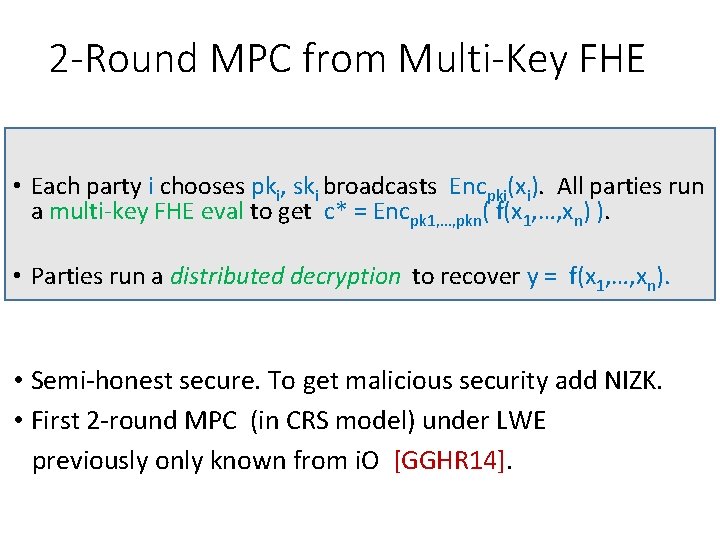
2 -Round MPC from Multi-Key FHE • Each party i chooses pki, ski broadcasts Encpki(xi). All parties run a multi-key FHE eval to get c* = Encpk 1, …, pkn( f(x 1, …, xn) ). • Parties run a distributed decryption to recover y = f(x 1, …, xn). • Semi-honest secure. To get malicious security add NIZK. • First 2 -round MPC (in CRS model) under LWE previously only known from i. O [GGHR 14].

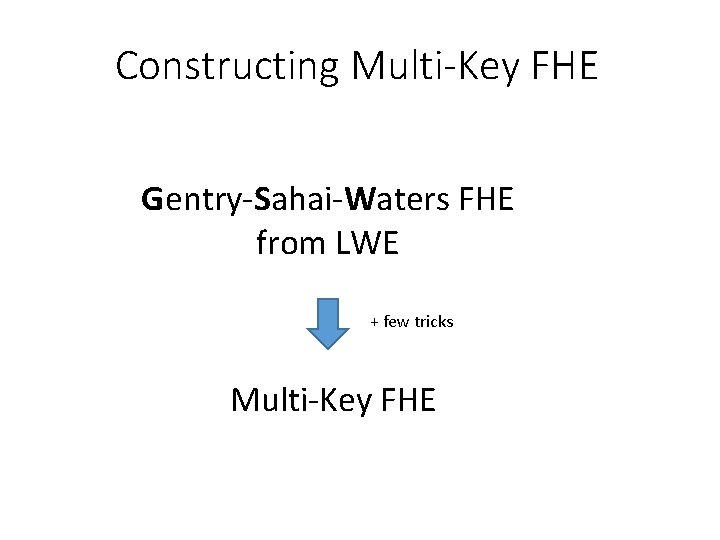
Constructing Multi-Key FHE Gentry-Sahai-Waters FHE from LWE + few tricks Multi-Key FHE
![Learning with Errors LWE R 05 LWE assumption stat far from uniform Learning with Errors (LWE) [R 05] + = LWE assumption stat. far from uniform!](https://slidetodoc.com/presentation_image_h/3761cc8791277453b12088aa194e9d5f/image-9.jpg)
Learning with Errors (LWE) [R 05] + = LWE assumption stat. far from uniform!

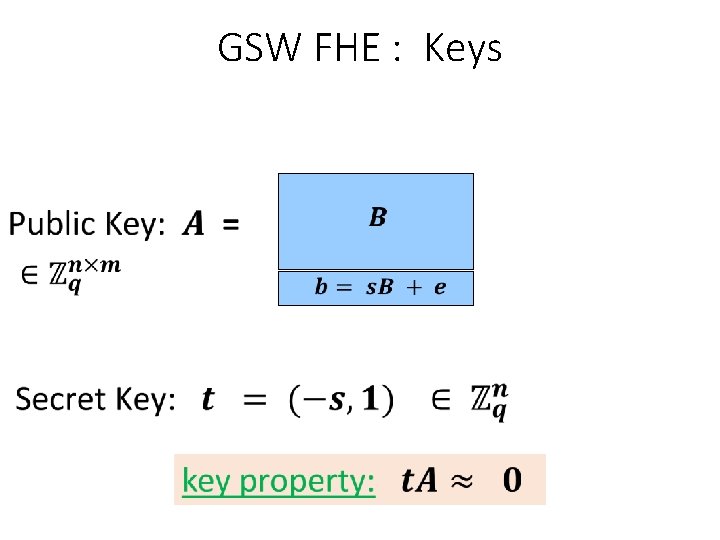
GSW FHE : Keys

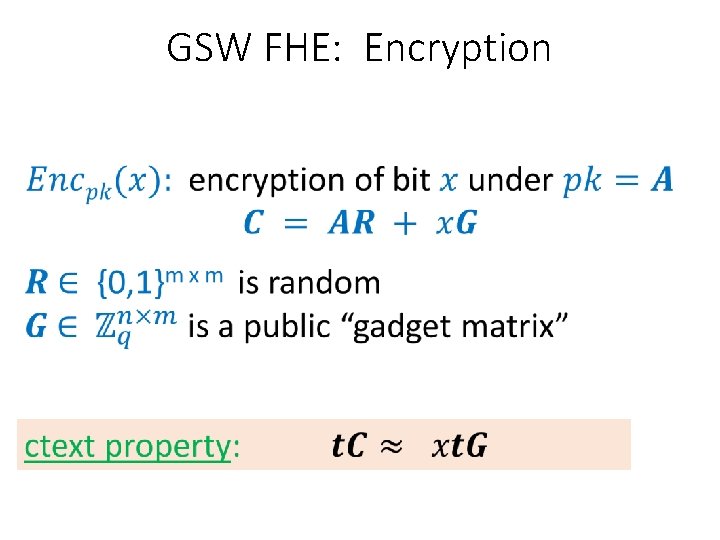
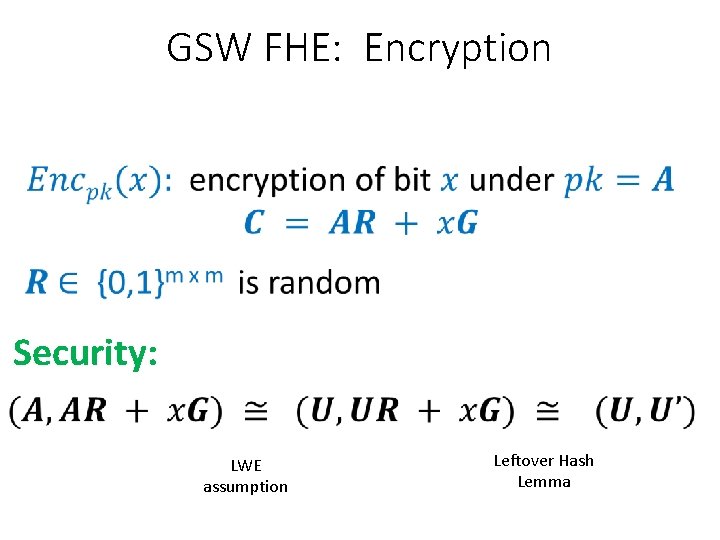
GSW FHE: Encryption

GSW FHE: Encryption Security: LWE assumption Leftover Hash Lemma

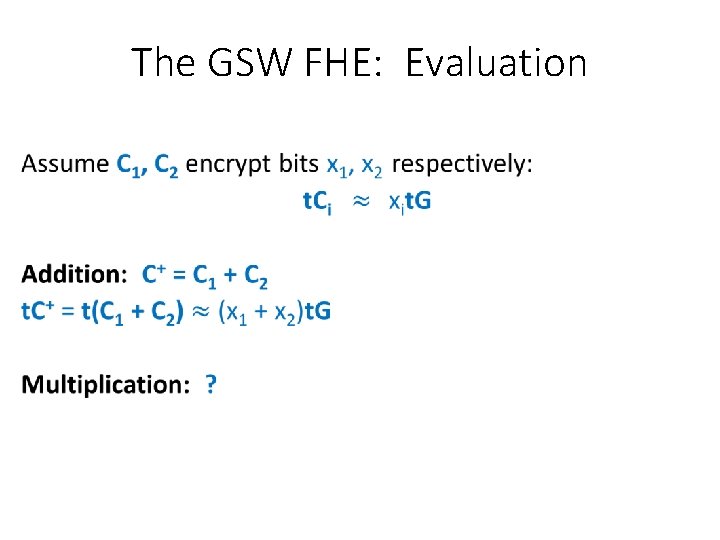
The GSW FHE: Evaluation •
![Gadget Matrix G MicciancioPeikert 12 Gadget Matrix G [Micciancio-Peikert ’ 12]](https://slidetodoc.com/presentation_image_h/3761cc8791277453b12088aa194e9d5f/image-14.jpg)
Gadget Matrix G [Micciancio-Peikert ’ 12]

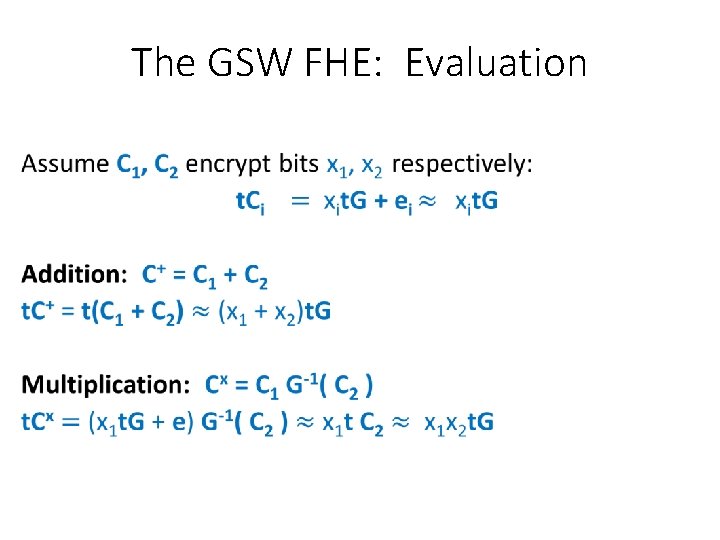
The GSW FHE: Evaluation •

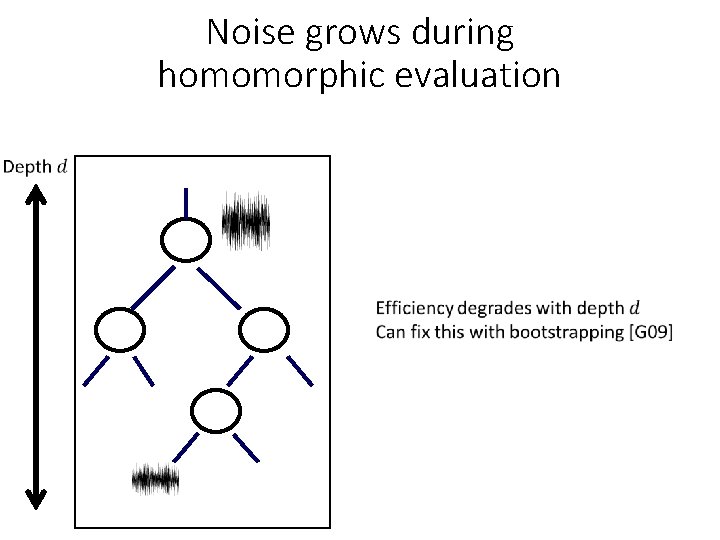
Noise grows during homomorphic evaluation

Extending GSW to Multi-Key Setting •

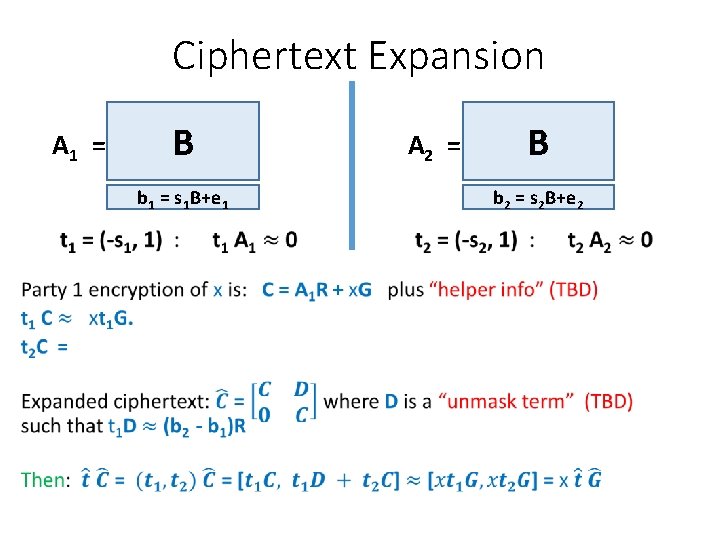
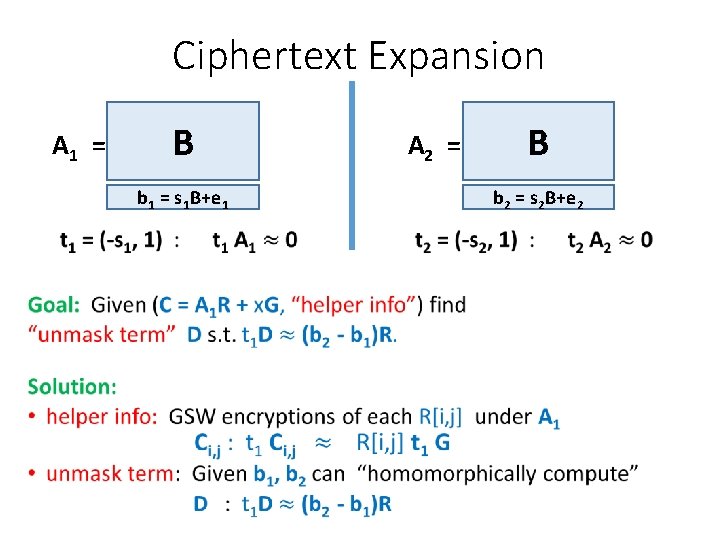
Ciphertext Expansion A 1 = B A 2 = b 1 = s 1 B+e 1 • B b 2 = s 2 B+e 2

Ciphertext Expansion A 1 = B A 2 = b 1 = s 1 B+e 1 • B b 2 = s 2 B+e 2

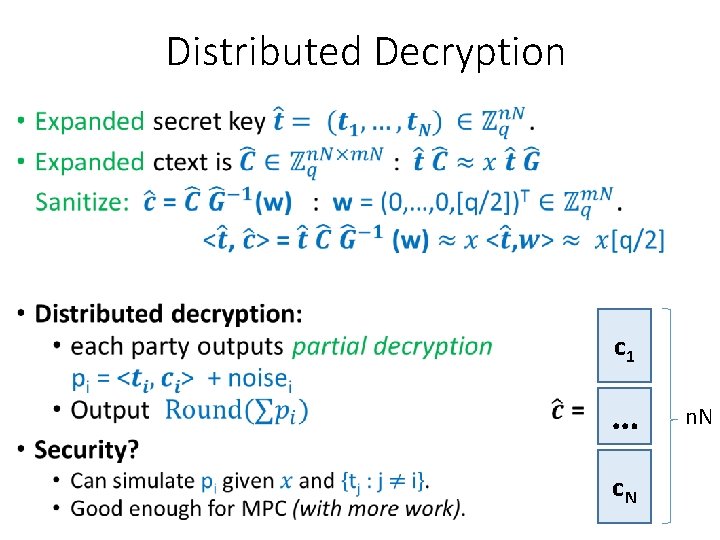
Distributed Decryption • c 1 … c. N n. N

Conclusions • Show: Multi-key FHE, 2 -round MPC from LWE Open questions: • Remove public parameters in Multi-Key FHE remove CRS in semi-honest 2 -round MPC • Improve efficiency (reduce expansion) • Non-compact multi-key FHE from other assumptions such as DDH? Good enough for 2 -round MPC.

Thank you