2 Public Key Encryption Using Digital Signatures and

2. Public Key Encryption Using Digital Signatures and Hash Digests n Hash function: Mathematical algorithm that produces fixed-length number called message or hash digest v A HAS FUNCTION CEN BE SIMPLE, AND COUNT THE NUMBER OF DIGITAL 1 S IN A MESSAGE, OR It can be more complex, and produce a 128 bit number that reflects the number of 0 s and 1 s , the number 00 s , 11 s, and so on. v Example: MD 4, MD 5, SHA-1, SHA-2 n Hash digest of message sent to recipient along with message to verify integrity n (Hash digest and message) encrypted with recipient’s public key n Entire cipher text then encrypted with Sender private key—creating digital signature (e - signature)—for authenticity, nonrepudiation v Copyright © 2010 Pearson Education, Inc. Slide 5 -1

Public Key Encryption Using Digital Signatures and Hash Digests A digital signature or “signed” cipher text that can be sent over the Internet. n A digital signature is a close parallel to a handwritten signature. Like a handwritten signature, a digital signature is unique. n When used with a hash function, the digital signature is even more unique than a handwritten signature. And changes for every document. n Copyright © 2010 Pearson Education, Inc.
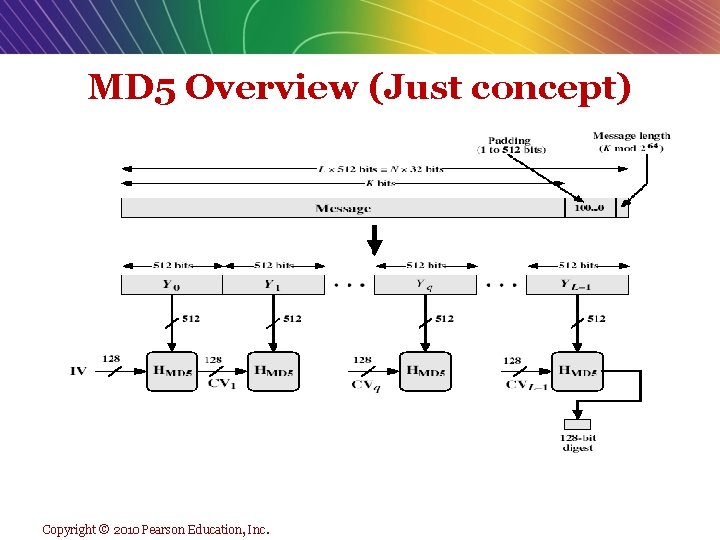
MD 5 Overview (Just concept) Copyright © 2010 Pearson Education, Inc.
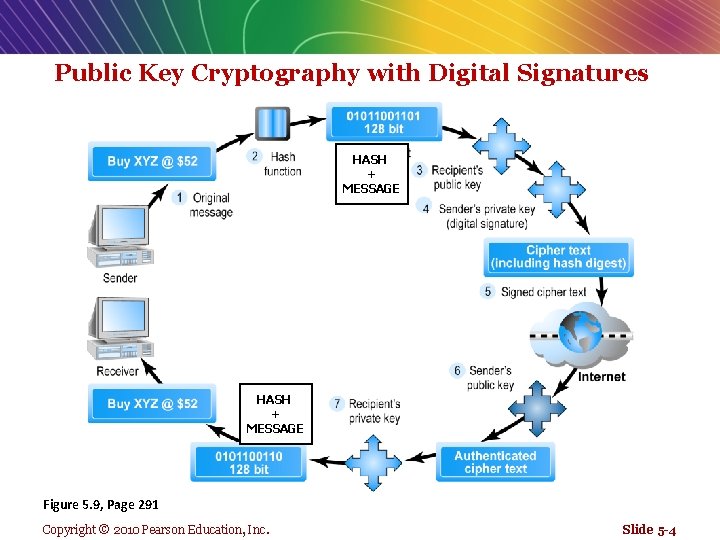
Public Key Cryptography with Digital Signatures HASH + MESSAGE Figure 5. 9, Page 291 Copyright © 2010 Pearson Education, Inc. Slide 5 -4

Public Key Encryption Using Digital Signatures and Hash Digests The receiver of this signed cipher( message + message digest) first uses the sender’s public key to authenticate the message. n Once Authenticate, the recipient uses his or her private key to obtain the hash result (message digest) and original message. n As a final step, the recipient applies the same hash function to the original text (original message) and compares the result with the result sent by the sender. n If the results are same (Send message digest = receiver message digest) the receiver now knows the message has not been changed during transmission The message has integrity. n Copyright © 2010 Pearson Education, Inc.
- Slides: 5