15 441 Computer Networking Lecture 3 Physical Layer







- Slides: 51

15 -441 Computer Networking Lecture 3 – Physical Layer 1

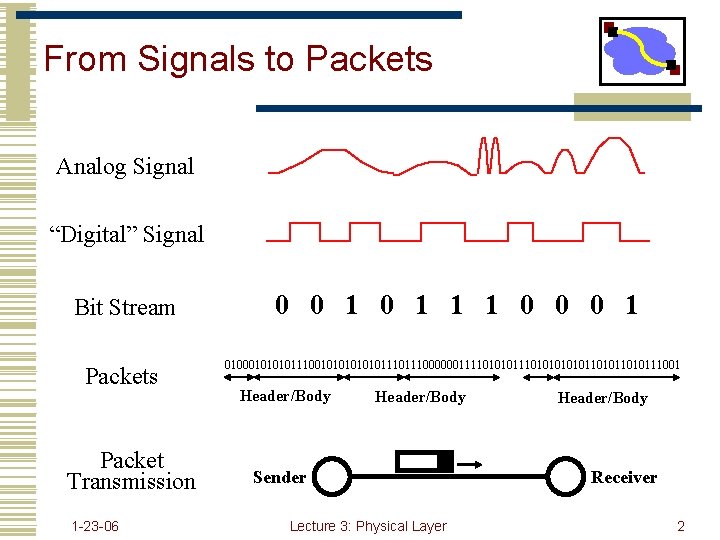
From Signals to Packets Analog Signal “Digital” Signal Bit Stream Packets Packet Transmission 1 -23 -06 0 0 1 1 1 0 0 0 1 01000101110010101110111000000111101010101011010111001 Header/Body Sender Lecture 3: Physical Layer Header/Body Receiver 2

Outline • • • RF introduction Modulation Antennas and signal propagation Equalization, diversity, channel coding Multiple access techniques Wireless systems and standards 1 -23 -06 Lecture 3: Physical Layer 3

Outline • • RF introduction Modulation Antennas and signal propagation Equalization, diversity, channel coding • • Dynamic equalization Diversity in space, frequency, and time • Multiple access techniques • Wireless systems and standards 1 -23 -06 Lecture 3: Physical Layer 4

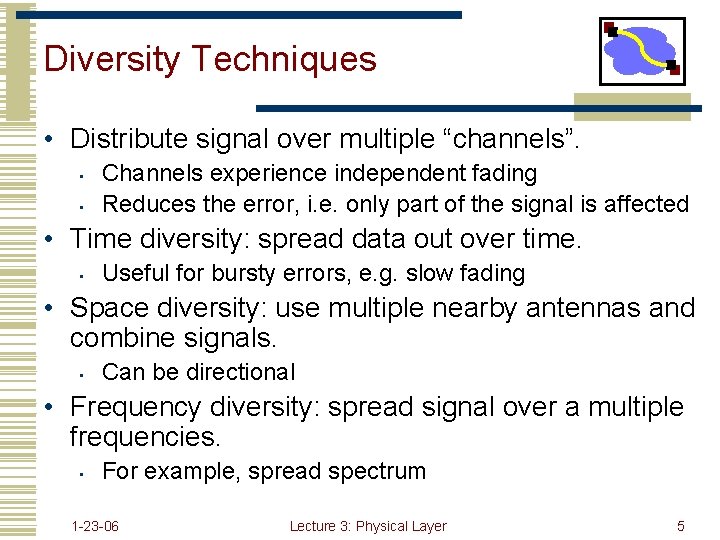
Diversity Techniques • Distribute signal over multiple “channels”. • • Channels experience independent fading Reduces the error, i. e. only part of the signal is affected • Time diversity: spread data out over time. • Useful for bursty errors, e. g. slow fading • Space diversity: use multiple nearby antennas and combine signals. • Can be directional • Frequency diversity: spread signal over a multiple frequencies. • For example, spread spectrum 1 -23 -06 Lecture 3: Physical Layer 5

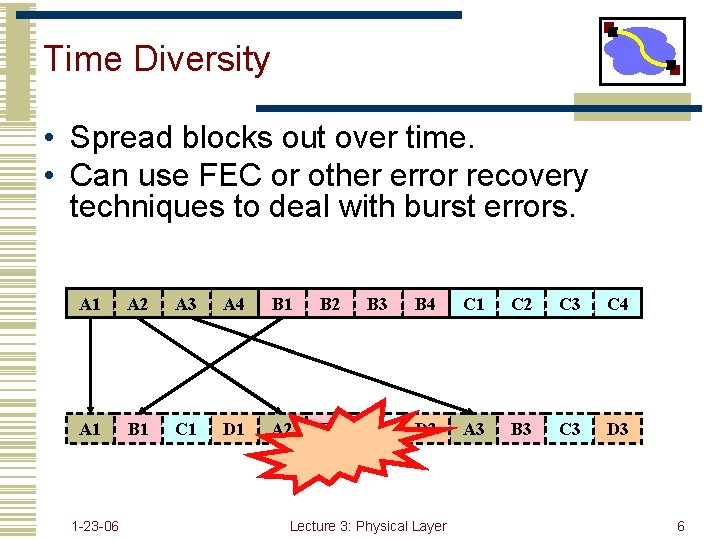
Time Diversity • Spread blocks out over time. • Can use FEC or other error recovery techniques to deal with burst errors. A 1 A 2 A 3 A 4 B 1 B 2 B 3 B 4 C 1 C 2 C 3 C 4 A 1 B 1 C 1 D 1 A 2 B 2 C 2 D 2 A 3 B 3 C 3 D 3 1 -23 -06 Lecture 3: Physical Layer 6

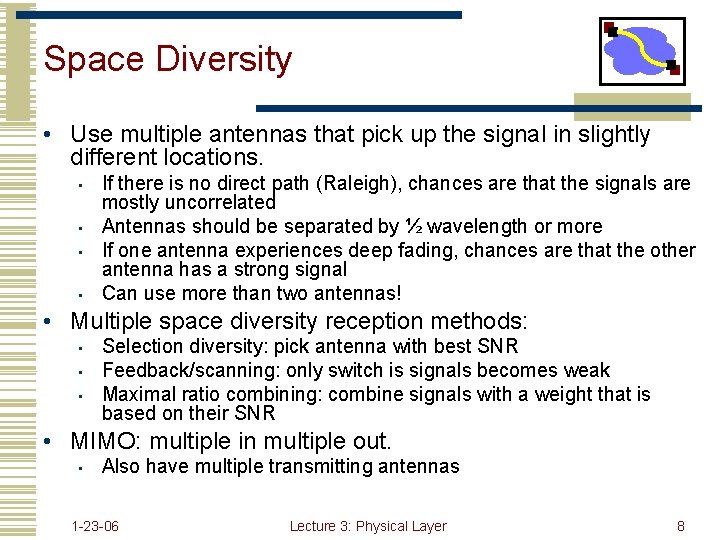
Space Diversity • Use multiple antennas that pick up the signal in slightly different locations. • • If there is no direct path (Raleigh), chances are that the signals are mostly uncorrelated Antennas should be separated by ½ wavelength or more If one antenna experiences deep fading, chances are that the other antenna has a strong signal Can use more than two antennas! • Multiple space diversity reception methods: • • • Selection diversity: pick antenna with best SNR Feedback/scanning: only switch is signals becomes weak Maximal ratio combining: combine signals with a weight that is based on their SNR • MIMO: multiple in multiple out. • Also have multiple transmitting antennas 1 -23 -06 Lecture 3: Physical Layer 8

Spread Spectrum and CDMA • Basic idea: Use a wider bandwidth than needed to transmit the signal. • Why? ? • • Don’t put all your eggs in one basket! Resistance to jamming and interference • • If one sub-channel is blocked, you still have the others Good for military Minimize impact of a “bad” frequency Pseudo-encryption • Have to know what frequencies it will use • Two techniques for spread spectrum… 1 -23 -06 Lecture 3: Physical Layer 9

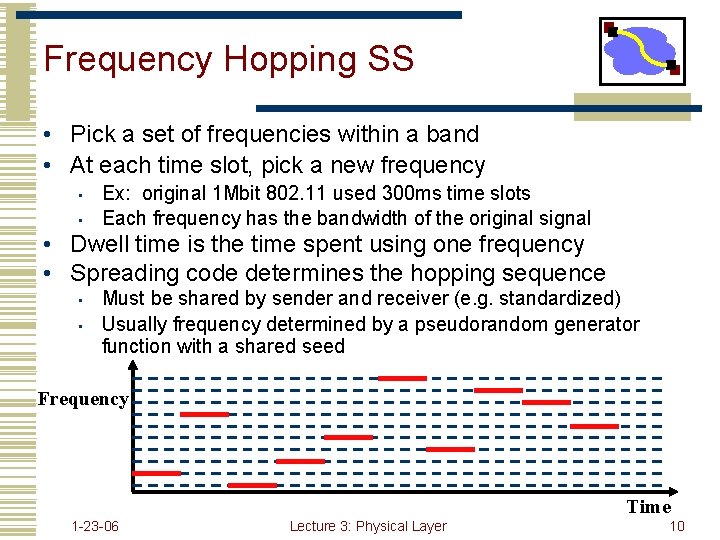
Frequency Hopping SS • Pick a set of frequencies within a band • At each time slot, pick a new frequency • • Ex: original 1 Mbit 802. 11 used 300 ms time slots Each frequency has the bandwidth of the original signal • Dwell time is the time spent using one frequency • Spreading code determines the hopping sequence • • Must be shared by sender and receiver (e. g. standardized) Usually frequency determined by a pseudorandom generator function with a shared seed Frequency Time 1 -23 -06 Lecture 3: Physical Layer 10

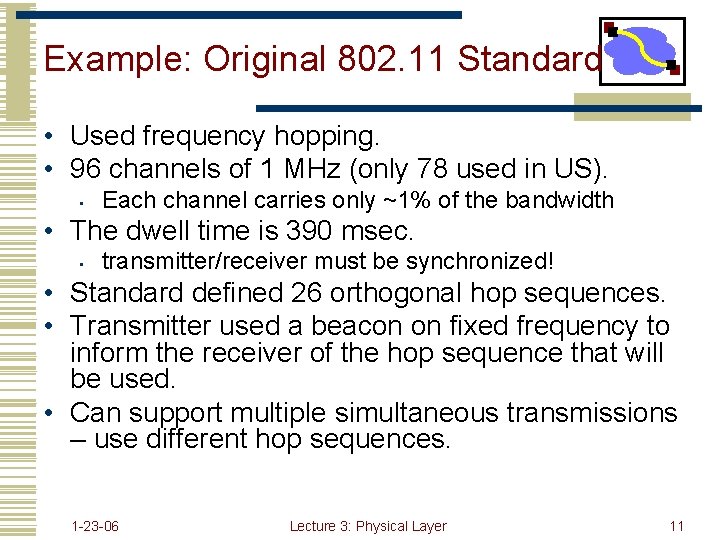
Example: Original 802. 11 Standard • Used frequency hopping. • 96 channels of 1 MHz (only 78 used in US). • Each channel carries only ~1% of the bandwidth • The dwell time is 390 msec. • transmitter/receiver must be synchronized! • Standard defined 26 orthogonal hop sequences. • Transmitter used a beacon on fixed frequency to inform the receiver of the hop sequence that will be used. • Can support multiple simultaneous transmissions – use different hop sequences. 1 -23 -06 Lecture 3: Physical Layer 11

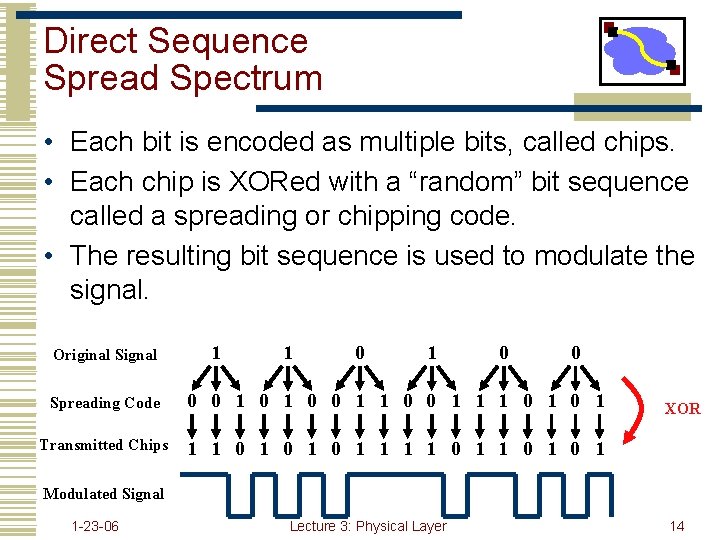
Direct Sequence Spread Spectrum • Each bit is encoded as multiple bits, called chips. • Each chip is XORed with a “random” bit sequence called a spreading or chipping code. • The resulting bit sequence is used to modulate the signal. Original Signal 1 1 0 0 Spreading Code 0 0 1 1 1 0 1 Transmitted Chips 1 1 0 1 0 1 1 0 1 XOR Modulated Signal 1 -23 -06 Lecture 3: Physical Layer 14

Properties • Since each bit it sent as multiple chips, you need more bps bandwidth to send the signal. • Number of chips per bit is called the spreading ratio • Given the Nyquist and Shannon results, you need more spectral bandwidth to do this. • Spreading the signal over the spectrum • Advantage is that is transmission is more resilient. • • DSSS signal will look like noise in a narrow band Can lose some chips in a word and recover easily • Multiple users can share bandwidth (easily). • • Follows directly from Shannon (capacity is there) Use a different chipping sequence 1 -23 -06 Lecture 3: Physical Layer 15

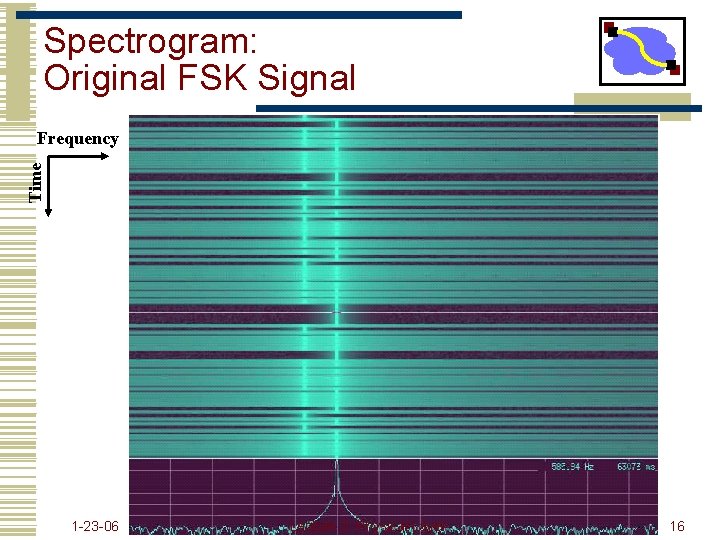
Spectrogram: Original FSK Signal Time Frequency 1 -23 -06 Lecture 3: Physical Layer 16

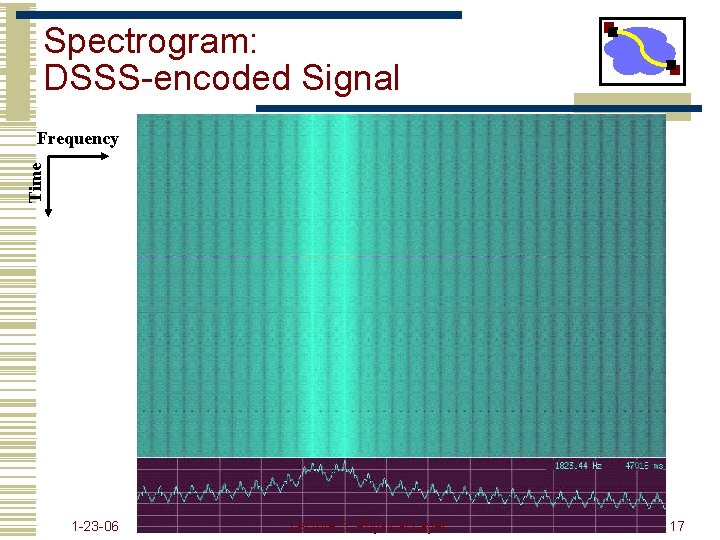
Spectrogram: DSSS-encoded Signal Time Frequency 1 -23 -06 Lecture 3: Physical Layer 17

Example: Original 802. 11 • The DS PHY used an 11 -to-1 spreading ratio and a Barker chipping sequence. • Barker sequence has low autocorrelation properties – why? • Receiver decodes by counting the number of “ 1” bits in each word • 6 “ 1” bits correspond to a 0 data bit • Chips were transmitted using B-PSK modulation. • • Data rate was 1 Mbps (i. e. 11 Mchips/sec) Extended to 2 Mbps by using a Q-PSK modulation • 1 -23 -06 Requires the detection of a ¼ phase shift Lecture 3: Physical Layer 18

Example: Current 802. 11 b • (Maximum) data rate is 11 Mbs. • Uses Complementary Code Keying (CCK). • Complementary means that the code has good autocorrelation properties • • Want nice properties to ease recovery in the presence of noise, multipath interference Each word is mapped onto an 8 bit chip sequence • The CCK chip stream is transmitted using Q-PSK modulation. • I. e. 4 values 1 -23 -06 Lecture 3: Physical Layer 19

Discussion • Spread spectrum is very widely used. • • Effective against noise and multipath Multiple transmitters can use the same frequency range • FCC requires the use of spread spectrum in ISM band. • If signal is above a certain power level • Is also used in higher speed 802. 11 versions. • No surprise! 1 -23 -06 Lecture 3: Physical Layer 20

Outline • • • RF introduction Modulation Antennas and signal propagation Equalization, diversity, channel coding Multiple access techniques • • • Dividing capacity: FDMA, TDMA, CDMA Bursty traffic: carrier sense techniques Capture effect and hidden terminal problem • Wireless systems and standards 1 -23 -06 Lecture 3: Physical Layer 22

MAC Layer • Coordinate access to a shared medium • Requirements • • • Efficiency Reliability Fairness Support priority Support group communication 1 -23 -06 Lecture 3: Physical Layer 23

MAC Layer (Cont. ) Base technologies • • • Frequency division multiple access (FDMA) Time division multiple access (TDMA) Code division multiple access (CDMA) Access schemes • Centralized • • • GSM IS-95 Distributed • • 1 -23 -06 CSMA/CD (Ethernet) CSMA/CA (wireless LAN) Lecture 3: Physical Layer 24

Supporting Multiple Channels • Multiple channels can coexist if they transmit at a different frequency, or at a different time, or in a different part of the space. • Three dimensional space: frequency, space, time • Space can be limited (using wires or) using transmit power of wireless transmitters. • Frequency multiplexing means that different users use a different part of the spectrum. • Again, similar to radio: 95. 5 versus 102. 5 station • Time division multiplexing means that users send at different times. • Static partitioning of time • Duplexing: splitting the time/frequencies between the up and down link. 1 -23 -06 Lecture 3: Physical Layer 25

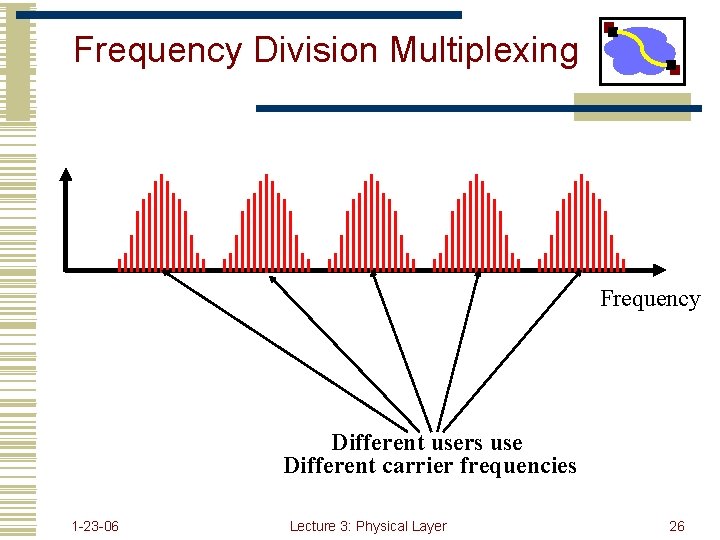
Frequency Division Multiplexing Frequency Different users use Different carrier frequencies 1 -23 -06 Lecture 3: Physical Layer 26

FDM Example: AMPS • US analog cellular system in early 80’s. • Each call uses an up and down link channel. • Channels are 30 KHz • About 12. 5 + 12. 5 MHz available for up and down link channels per operator. • • • Supports 416 channels in each direction 21 of the channels are used for data/control Total capacity (across operators) is double of this 1 -23 -06 Lecture 3: Physical Layer 27

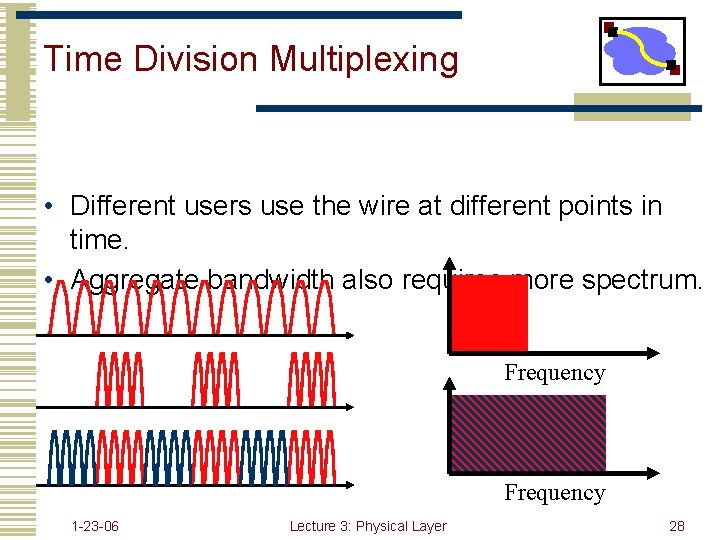
Time Division Multiplexing • Different users use the wire at different points in time. • Aggregate bandwidth also requires more spectrum. Frequency 1 -23 -06 Lecture 3: Physical Layer 28

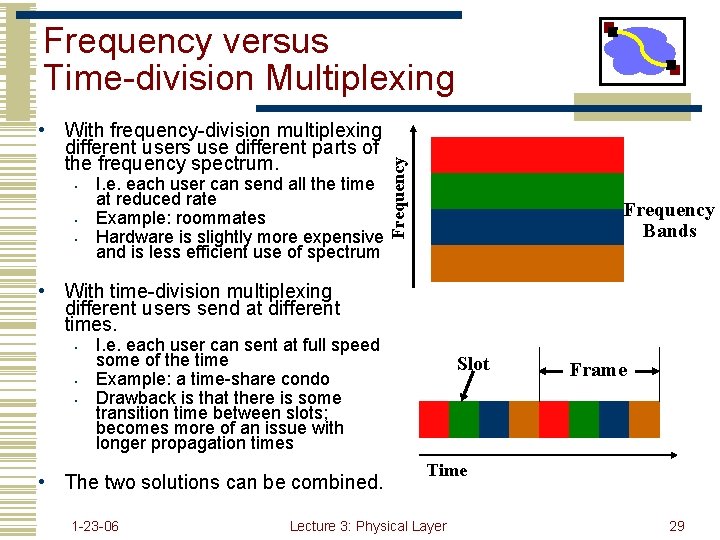
• With frequency-division multiplexing different users use different parts of the frequency spectrum. • • • I. e. each user can send all the time at reduced rate Example: roommates Hardware is slightly more expensive and is less efficient use of spectrum Frequency versus Time-division Multiplexing Frequency Bands • With time-division multiplexing different users send at different times. • • • I. e. each user can sent at full speed some of the time Example: a time-share condo Drawback is that there is some transition time between slots; becomes more of an issue with longer propagation times • The two solutions can be combined. 1 -23 -06 Slot Frame Time Lecture 3: Physical Layer 29

TDM Example: GSM • Global System for Mobile communication. • First introduced in Europe in early 90 s • Uses a combination of TDM and FDM. • 25 MHz each for up and down links. • Broken up in 200 KHz channels • • 125 channels in each direction Each channel can carry about 270 kbs • Each channel is broken up in 8 time slots • • Slots are 0. 577 msec long Results in 1000 channels, each with about 25 kbs of useful data; can be used for voice, data, control • General Packet Radio Service (GPRS). • Data service for GSM, e. g. 4 down and 1 up channel 1 -23 -06 Lecture 3: Physical Layer 30

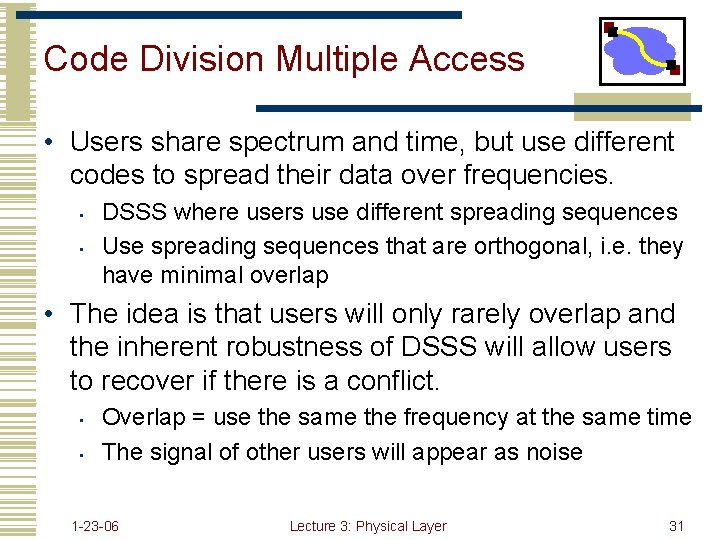
Code Division Multiple Access • Users share spectrum and time, but use different codes to spread their data over frequencies. • • DSSS where users use different spreading sequences Use spreading sequences that are orthogonal, i. e. they have minimal overlap • The idea is that users will only rarely overlap and the inherent robustness of DSSS will allow users to recover if there is a conflict. • • Overlap = use the same the frequency at the same time The signal of other users will appear as noise 1 -23 -06 Lecture 3: Physical Layer 31

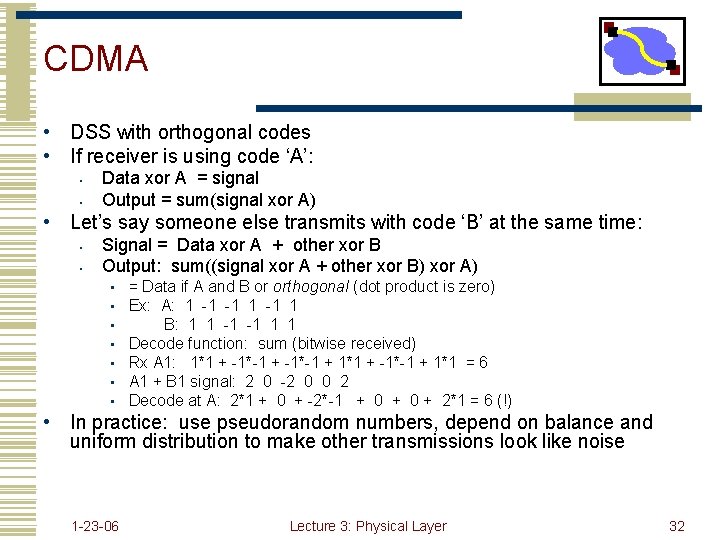
CDMA • DSS with orthogonal codes • If receiver is using code ‘A’: • • Data xor A = signal Output = sum(signal xor A) • Let’s say someone else transmits with code ‘B’ at the same time: • • Signal = Data xor A + other xor B Output: sum((signal xor A + other xor B) xor A) • • = Data if A and B or orthogonal (dot product is zero) Ex: A: 1 -1 -1 1 B: 1 1 -1 -1 1 1 Decode function: sum (bitwise received) Rx A 1: 1*1 + -1*-1 + 1*1 = 6 A 1 + B 1 signal: 2 0 -2 0 0 2 Decode at A: 2*1 + 0 + -2*-1 + 0 + 2*1 = 6 (!) • In practice: use pseudorandom numbers, depend on balance and uniform distribution to make other transmissions look like noise 1 -23 -06 Lecture 3: Physical Layer 32

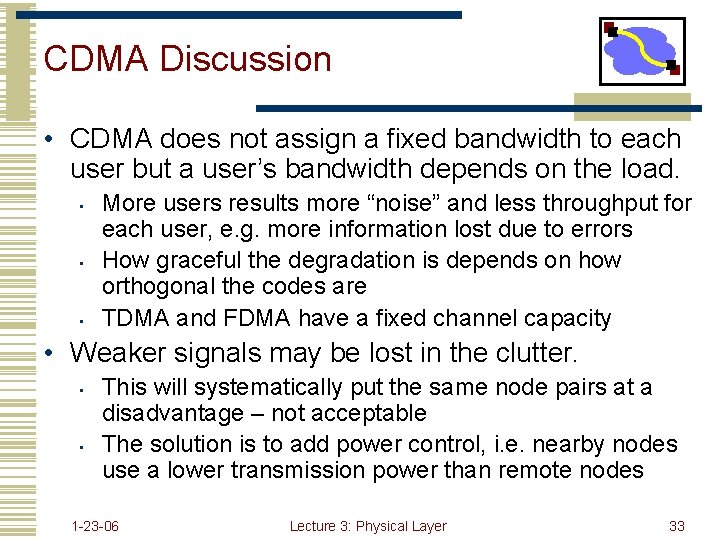
CDMA Discussion • CDMA does not assign a fixed bandwidth to each user but a user’s bandwidth depends on the load. • • • More users results more “noise” and less throughput for each user, e. g. more information lost due to errors How graceful the degradation is depends on how orthogonal the codes are TDMA and FDMA have a fixed channel capacity • Weaker signals may be lost in the clutter. • • This will systematically put the same node pairs at a disadvantage – not acceptable The solution is to add power control, i. e. nearby nodes use a lower transmission power than remote nodes 1 -23 -06 Lecture 3: Physical Layer 33

CDMA Example • CDMA cellular standard. • Used in the US, e. g. Spring • Allocates 1. 228 MHz for basestation to mobile communication. • • Shared by 64 “code channels” Used for voice (55), paging service (8), and control (1) • Provides a lot error coding to recover from errors. • • • Voice data is 8550 bps Coding and FEC increase this to 19. 2 kbps Then spread out over 1. 228 MHz using DSSS; uses QPSK 1 -23 -06 Lecture 3: Physical Layer 34

Supporting Bursty Data Traffic • FDMA, TDMA, and CDMA carve up bandwidth in fixedbandwidth channels – not efficient for bursty traffic. • Alternative is to do “dynamic time sharing” of a single channel, i. e. users send packets as they become available. • Called “multiple access” protocols • Challenge: users need contend for access to the channel. • • Class of “contention-based” MAC protocols When two users transmit at the same time, we have a collision, i. e. data is lost due to heavy interference 1 -23 -06 Lecture 3: Physical Layer 35

Medium Access Control • Think back to Ethernet MAC: • • • Wireless is a shared medium Transmitters interfere Need a way to ensure that (usually) only one person talks at a time. • Goals: Efficiency, possibly fairness • But wireless is harder! • Can’t really do collision detection: • • Carrier sense is a bit weaker: • • Can’t listen while you’re transmitting. You overwhelm your antenna… Takes a while to switch between Tx/Rx. Wireless is not perfectly broadcast 1 -23 -06 Lecture 3: Physical Layer 36

Example MAC Protocols • Pure ALOHA • • Transmit whenever a message is ready Retransmit when ACK is not received • Slotted ALOHA • • Time is divided into equal time slots Transmit only at the beginning of a time slot Avoid partial collisions Increase delay, and require synchronization • Carrier Sense Multiple Access (CSMA) • • Listen before transmit Transmit only when no carrier is detected 1 -23 -06 Lecture 3: Physical Layer 37

“Wireless Ethernet” • Collision detection is not practical. • • Signal power is too high at the transmitter So how do you detect collisions? • Signals attenuate significantly with distance. • • Strong signal from nearby node will overwhelm the weaker signal from a remote transmitter Capture effect: nearby node will always win in case of collision receiver may not even detect remote node • Hidden transmitter • Two transmitters may not hear each other, which can cause collisions at a common receiver. • • Hidden terminal problem RTS/CTS is designed to avoid this 1 -23 -06 Lecture 3: Physical Layer 38

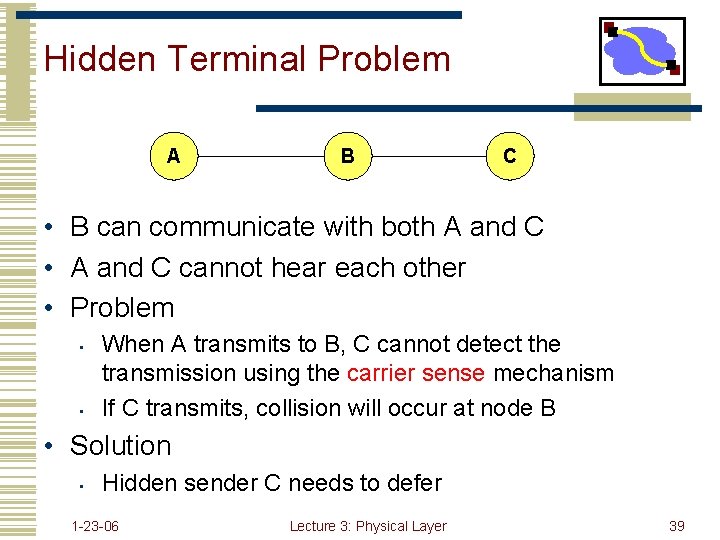
Hidden Terminal Problem A B C • B can communicate with both A and C • A and C cannot hear each other • Problem • • When A transmits to B, C cannot detect the transmission using the carrier sense mechanism If C transmits, collision will occur at node B • Solution • Hidden sender C needs to defer 1 -23 -06 Lecture 3: Physical Layer 39

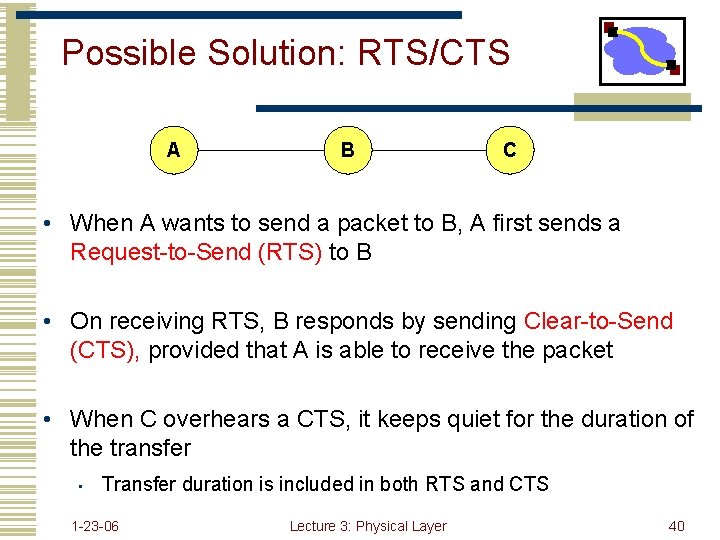
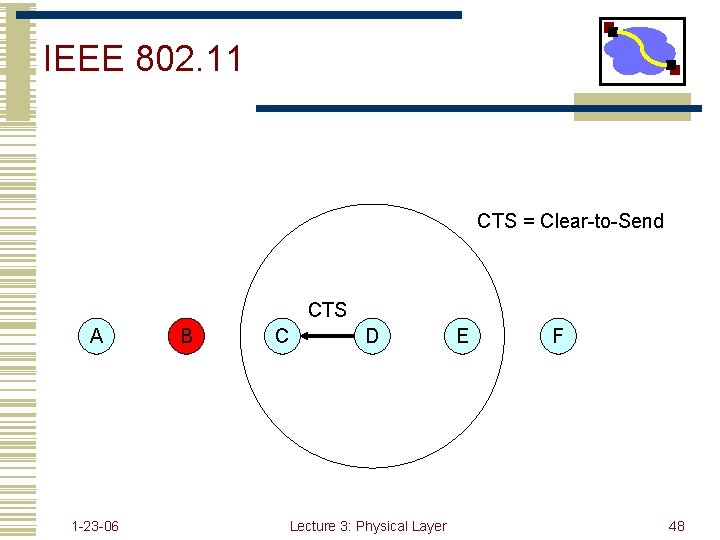
Possible Solution: RTS/CTS A B C • When A wants to send a packet to B, A first sends a Request-to-Send (RTS) to B • On receiving RTS, B responds by sending Clear-to-Send (CTS), provided that A is able to receive the packet • When C overhears a CTS, it keeps quiet for the duration of the transfer • Transfer duration is included in both RTS and CTS 1 -23 -06 Lecture 3: Physical Layer 40

Collision Detection & Reliability • Impossible to detect collision using halfduplex radios • Wireless links are prone to errors. High packet loss rate detrimental to transportlayer performance. • Mechanisms needed to reduce packet loss rate experienced by upper layers 1 -23 -06 Lecture 3: Physical Layer 41

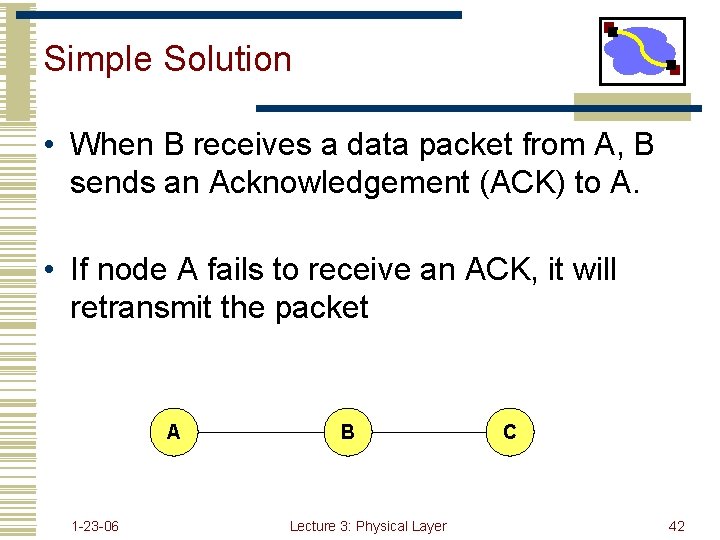
Simple Solution • When B receives a data packet from A, B sends an Acknowledgement (ACK) to A. • If node A fails to receive an ACK, it will retransmit the packet A 1 -23 -06 B Lecture 3: Physical Layer C 42

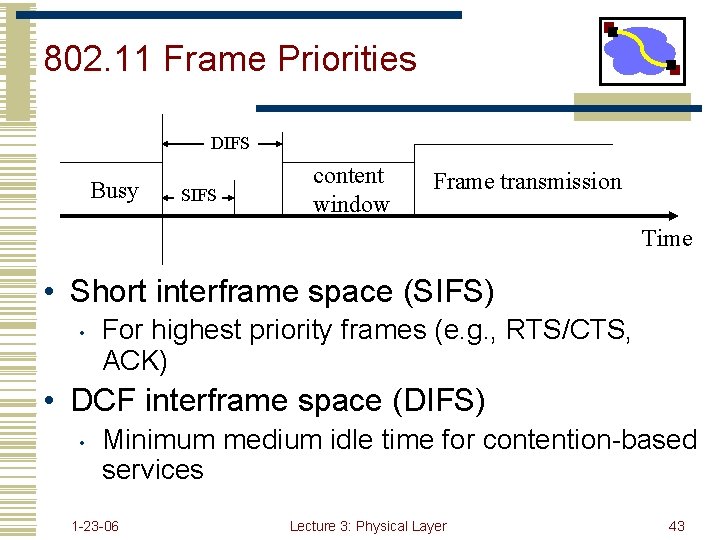
802. 11 Frame Priorities DIFS Busy SIFS content window Frame transmission Time • Short interframe space (SIFS) • For highest priority frames (e. g. , RTS/CTS, ACK) • DCF interframe space (DIFS) • Minimum medium idle time for contention-based services 1 -23 -06 Lecture 3: Physical Layer 43

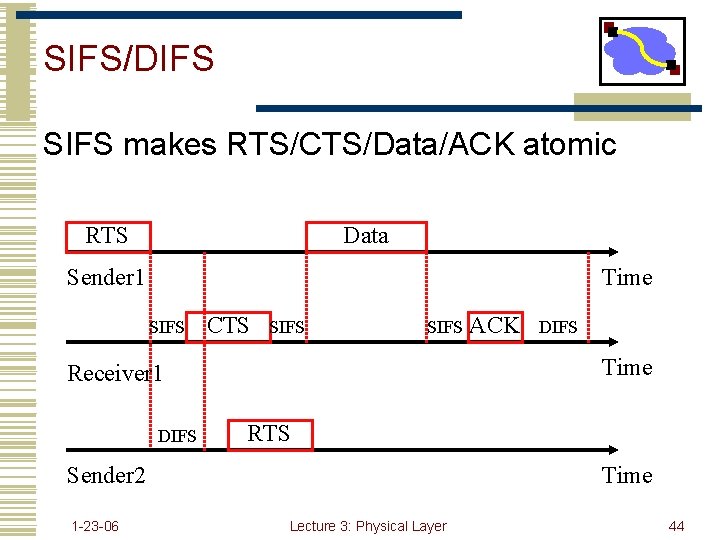
SIFS/DIFS SIFS makes RTS/CTS/Data/ACK atomic RTS Data Sender 1 Time SIFS CTS SIFS RTS Sender 2 1 -23 -06 DIFS Time Receiver 1 DIFS ACK Time Lecture 3: Physical Layer 44

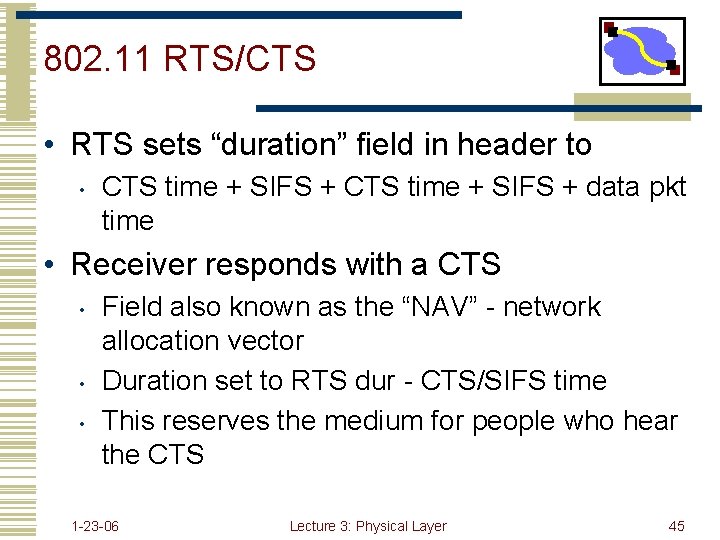
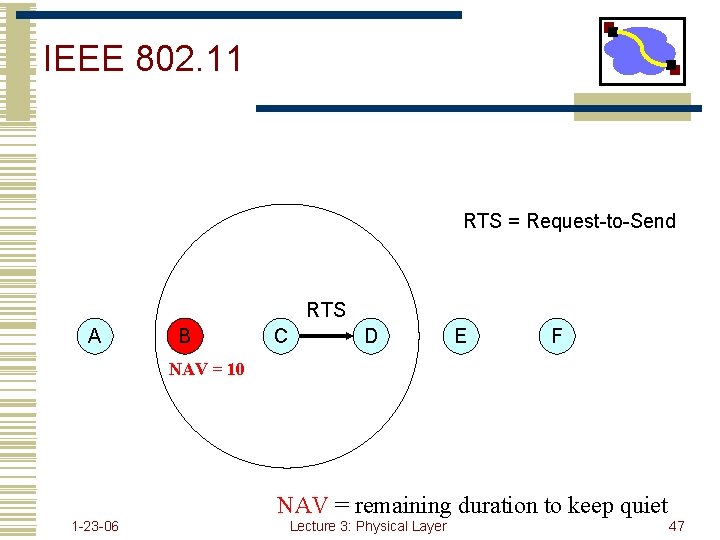
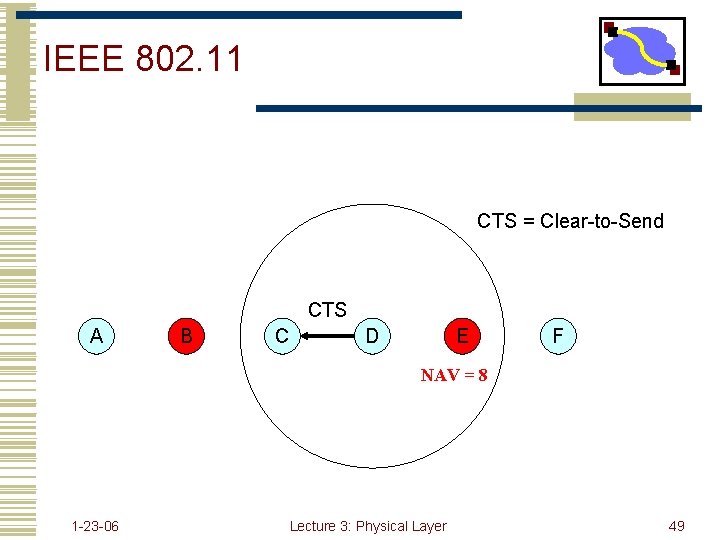
802. 11 RTS/CTS • RTS sets “duration” field in header to • CTS time + SIFS + data pkt time • Receiver responds with a CTS • • • Field also known as the “NAV” - network allocation vector Duration set to RTS dur - CTS/SIFS time This reserves the medium for people who hear the CTS 1 -23 -06 Lecture 3: Physical Layer 45

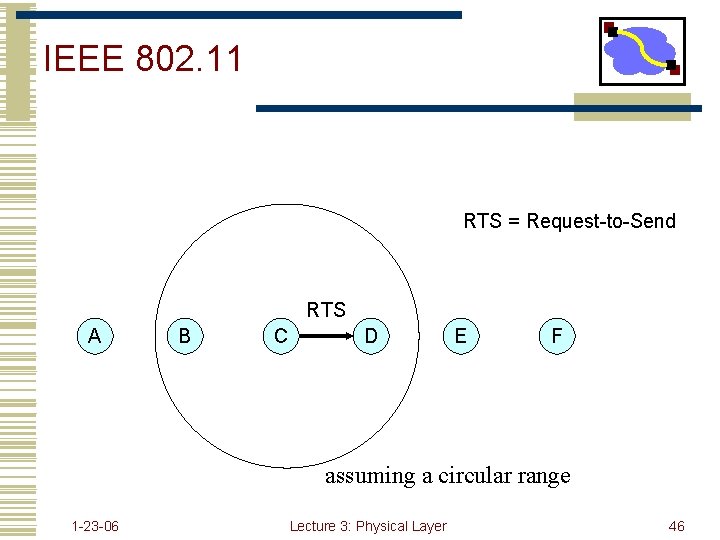
IEEE 802. 11 RTS = Request-to-Send RTS A B C D E F assuming a circular range 1 -23 -06 Lecture 3: Physical Layer 46

IEEE 802. 11 RTS = Request-to-Send RTS A B C D E F NAV = 10 NAV = remaining duration to keep quiet 1 -23 -06 Lecture 3: Physical Layer 47

IEEE 802. 11 CTS = Clear-to-Send CTS A 1 -23 -06 B C D Lecture 3: Physical Layer E F 48

IEEE 802. 11 CTS = Clear-to-Send CTS A B C D E F NAV = 8 1 -23 -06 Lecture 3: Physical Layer 49

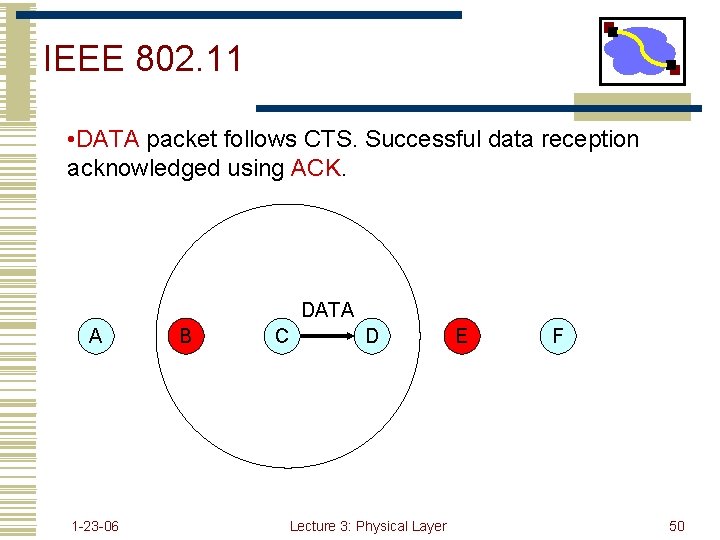
IEEE 802. 11 • DATA packet follows CTS. Successful data reception acknowledged using ACK. DATA A 1 -23 -06 B C D Lecture 3: Physical Layer E F 50

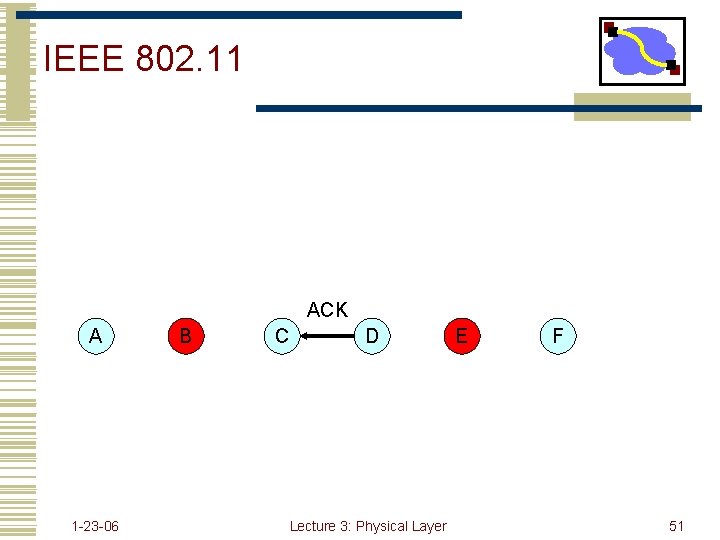
IEEE 802. 11 ACK A 1 -23 -06 B C D Lecture 3: Physical Layer E F 51

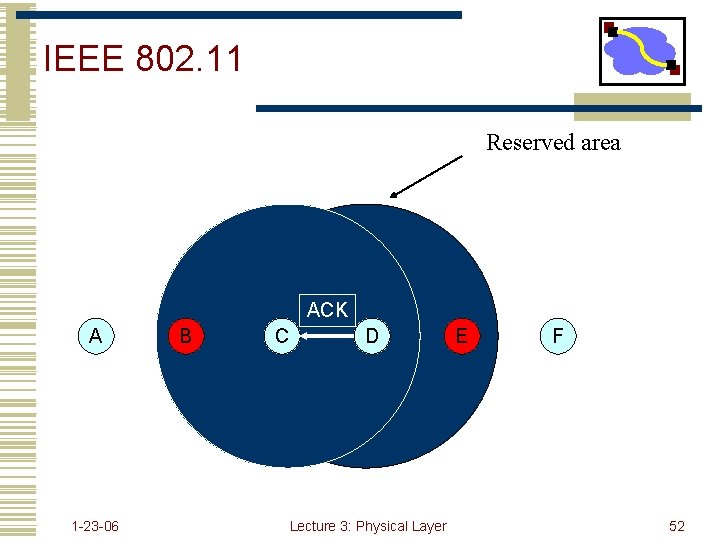
IEEE 802. 11 Reserved area ACK A 1 -23 -06 B C D Lecture 3: Physical Layer E F 52

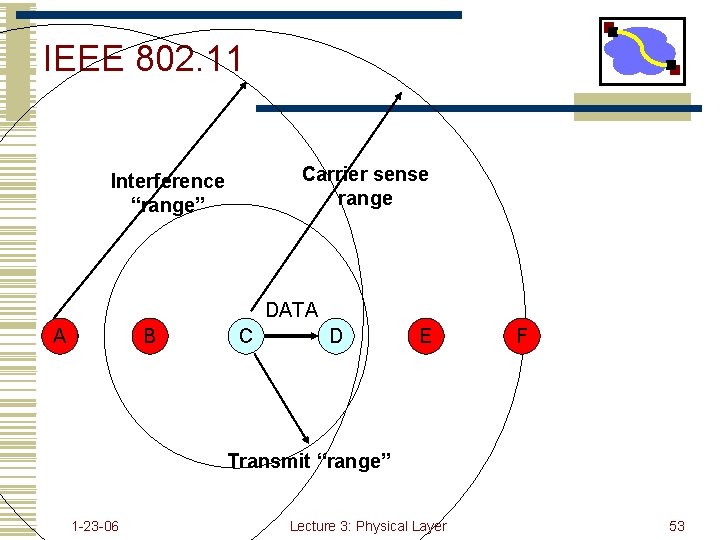
IEEE 802. 11 Carrier sense range Interference “range” DATA A B C D E F Transmit “range” 1 -23 -06 Lecture 3: Physical Layer 53

Outline • • • RF introduction Modulation Antennas and signal propagation Equalization, diversity, channel coding Multiple access techniques Wireless systems and standards • 802. 11 1 -23 -06 Lecture 3: Physical Layer 54

Readings • Performance analysis of the IEEE 802. 11 distributed coordination function, JSAC, Mar 2000 • Ultra-Wideband Technology for Short- and Medium-range Wireless Communication, Foerster, Green, Somayazulu, Leeper, Intel Technology Journal, Q 2 2001. • "The Bluetooth radio system, " J. C. Haartsen, IEEE Pers. Commun. Mag. , pp. 28 --36, Feb. 2000. 1 -23 -06 Lecture 3: Physical Layer 55