15 441 Computer Networking Introduction of Transport Protocols


- Slides: 30

15 -441 Computer Networking Introduction of Transport Protocols Hui Zhang, Fall 2012 1

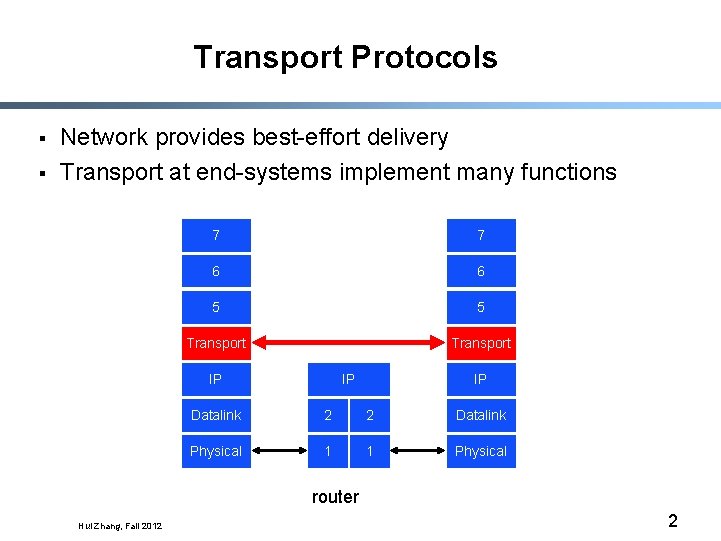
Transport Protocols § § Network provides best-effort delivery Transport at end-systems implement many functions 7 7 6 6 5 5 Transport IP IP IP Datalink 2 2 Datalink Physical 1 1 Physical router Hui Zhang, Fall 2012 2

Minimum Transport Protocol Function § § Multiplexing/de-multiplexing for multiple applications How does the protocol stack know what application should receive a packet? - Why not using process ID? Hui Zhang, Fall 2012 3

Multiplexing using Ports § Transport layer uses the port in the transport header to identify the application socket. - (Destination IP, destination port) identifies the destination - Port numbers 0 -1023 are well-known port numbers § § In UDP packets delivered at a socket can come from multiple sources (connectionless). Why do we need a source port number? - Needed to return a packet! - Flip source and destination (IP, port) pairs Hui Zhang, Fall 2012 4

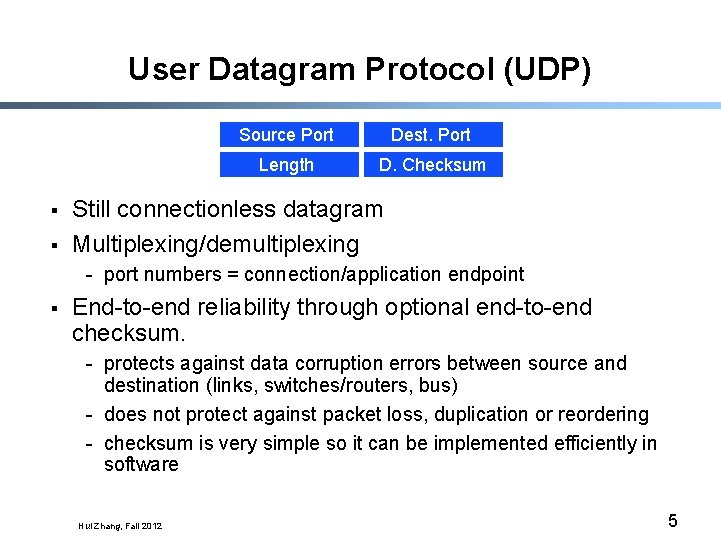
User Datagram Protocol (UDP) § § Source Port Dest. Port Length D. Checksum Still connectionless datagram Multiplexing/demultiplexing - port numbers = connection/application endpoint § End-to-end reliability through optional end-to-end checksum. - protects against data corruption errors between source and destination (links, switches/routers, bus) - does not protect against packet loss, duplication or reordering - checksum is very simple so it can be implemented efficiently in software Hui Zhang, Fall 2012 5

Using UDP § Examples: - remote procedure calls - multimedia - distributed computing communication libraries § § Use the port addressing provided by UDP implement their own reliability, flow control, ordering, congestion control Hui Zhang, Fall 2012 6

More Transport Protocol Functions § § Multiplexing/de-multiplexing for multiple applications Error control - Hide unreliability of the network layer from applications - Many types of errors: corruption, loss, duplication, reordering. § End-to-end flow control - Avoid flooding the receiver § Congestion control - Avoid flooding the network § Connection management - Logical end-to-end connection - Connection state to optimize performance Hui Zhang, Fall 2012 7

Problems to Be Solved by Error Control At Transport Layer § Best effort network layer - Packets can get corrupted - Packets can get lost - Packets can get re-ordered Hui Zhang, Fall 2012 8

Mechanisms used For Error Control § Packets can get corrupted - CRC or Checksum to detect, retransmission to recover - Error correction code to recover § Packets can get lost - Sequence number to detect - Acknowledgement + Timeout to detect, retransmission to recover § Packets can get re-ordered - Sequence number to detect, receiver buffer to re-order Hui Zhang, Fall 2012 9

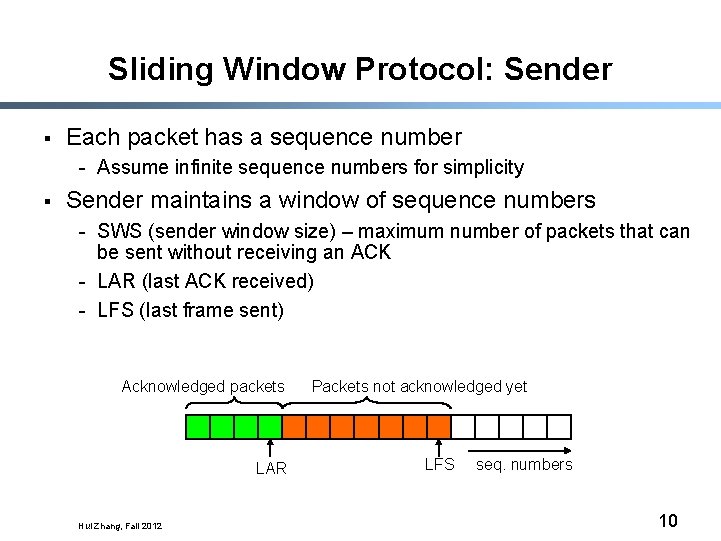
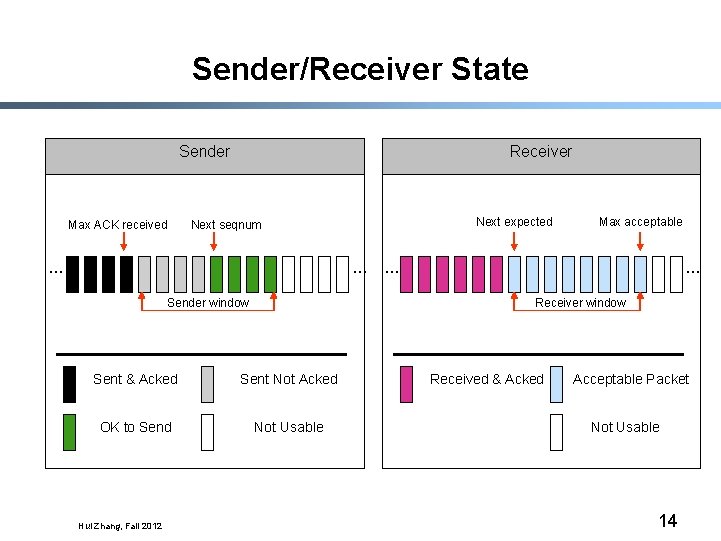
Sliding Window Protocol: Sender § Each packet has a sequence number - Assume infinite sequence numbers for simplicity § Sender maintains a window of sequence numbers - SWS (sender window size) – maximum number of packets that can be sent without receiving an ACK - LAR (last ACK received) - LFS (last frame sent) Acknowledged packets LAR Hui Zhang, Fall 2012 Packets not acknowledged yet LFS seq. numbers 10

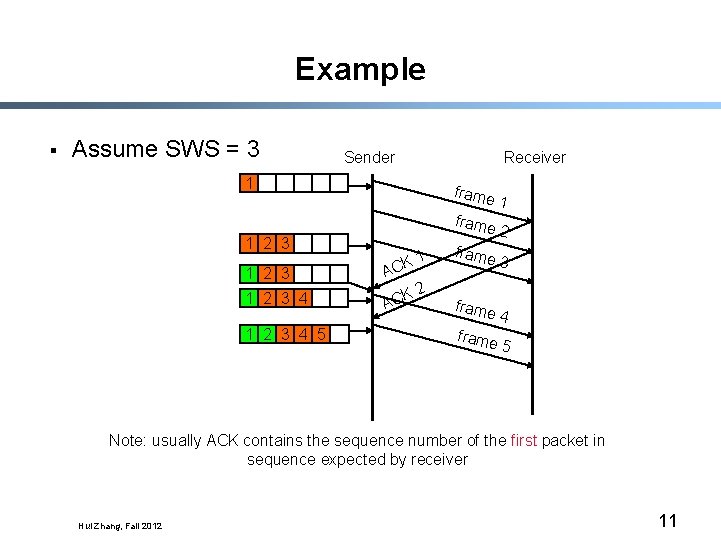
Example § Assume SWS = 3 Sender Receiver 1 1 2 3 1 CK 1 2 3 A 1 2 3 4 K AC 1 2 3 4 5 2 frame 1 frame 2 frame 3 frame 4 frame 5 Note: usually ACK contains the sequence number of the first packet in sequence expected by receiver Hui Zhang, Fall 2012 11

Sliding Window Protocol: Receiver § Receiver maintains a window of sequence numbers - RWS (receiver window size) – maximum number of outof-sequence packets that can received - LFR (last frame received) – last frame received in sequence - LAF (last acceptable frame) - LAF – LFR <= RWS Hui Zhang, Fall 2012 12

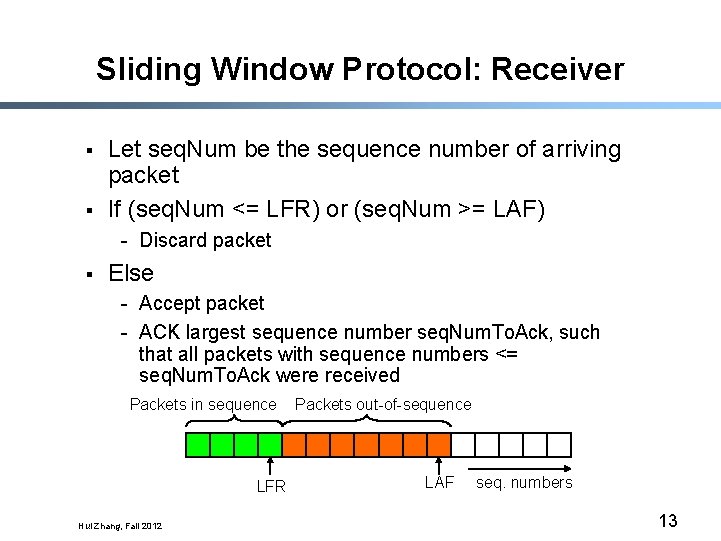
Sliding Window Protocol: Receiver § § Let seq. Num be the sequence number of arriving packet If (seq. Num <= LFR) or (seq. Num >= LAF) - Discard packet § Else - Accept packet - ACK largest sequence number seq. Num. To. Ack, such that all packets with sequence numbers <= seq. Num. To. Ack were received Packets in sequence LFR Hui Zhang, Fall 2012 Packets out-of-sequence LAF seq. numbers 13

Sender/Receiver State Sender Max ACK received Receiver Next expected Next seqnum … … Receiver window Sender window Sent & Acked Sent Not Acked OK to Send Not Usable Hui Zhang, Fall 2012 Max acceptable Received & Acked Acceptable Packet Not Usable 14

Sequence Numbers § How large do sequence numbers need to be? - Must be able to detect wrap-around - Depends on sender/receiver window size § E. g. - Max seq = 7, send win=recv win=7 - If pkts 0. . 6 are sent succesfully and all acks lost • Receiver expects 7, 0. . 5, sender retransmits old 0. . 6!!! § Max sequence must be send window + recv window Hui Zhang, Fall 2012 10 -24 -2006 Lecture 16: Transport Protocols 15 15

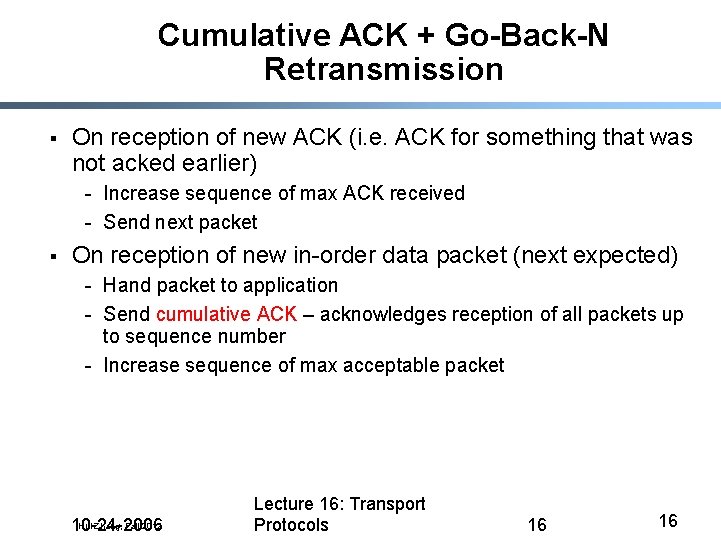
Cumulative ACK + Go-Back-N Retransmission § On reception of new ACK (i. e. ACK for something that was not acked earlier) - Increase sequence of max ACK received - Send next packet § On reception of new in-order data packet (next expected) - Hand packet to application - Send cumulative ACK – acknowledges reception of all packets up to sequence number - Increase sequence of max acceptable packet Hui Zhang, Fall 2012 10 -24 -2006 Lecture 16: Transport Protocols 16 16

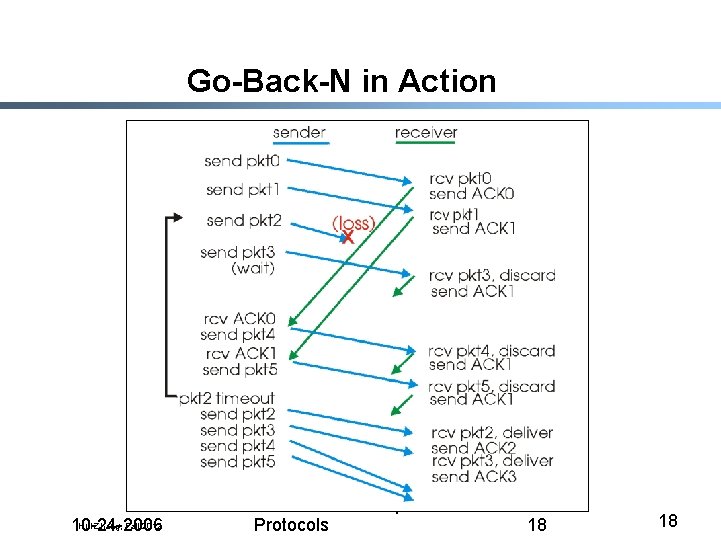
Loss Recovery § On reception of out-of-order packet - Send nothing (wait for source to timeout) - Cumulative ACK (helps source identify loss) § Timeout (Go-Back-N recovery) - Set timer upon transmission of packet - Retransmit all unacknowledged packets § Performance during loss recovery - No longer have an entire window in transit - Can have much more clever loss recovery Hui Zhang, Fall 2012 10 -24 -2006 Lecture 16: Transport Protocols 17 17

Go-Back-N in Action Hui Zhang, Fall 2012 10 -24 -2006 Lecture 16: Transport Protocols 18 18

Selective Ack + Selective Repeat § Receiver individually acknowledges all correctly received pkts - Buffers packets, as needed, for eventual in-order delivery to upper layer § Sender only resends packets for which ACK not received - Sender timer for each un. ACKed packet § Sender window - N consecutive seq #’s - Again limits seq #s of sent, un. ACKed packets Hui Zhang, Fall 2012 10 -24 -2006 Lecture 16: Transport Protocols 19 19

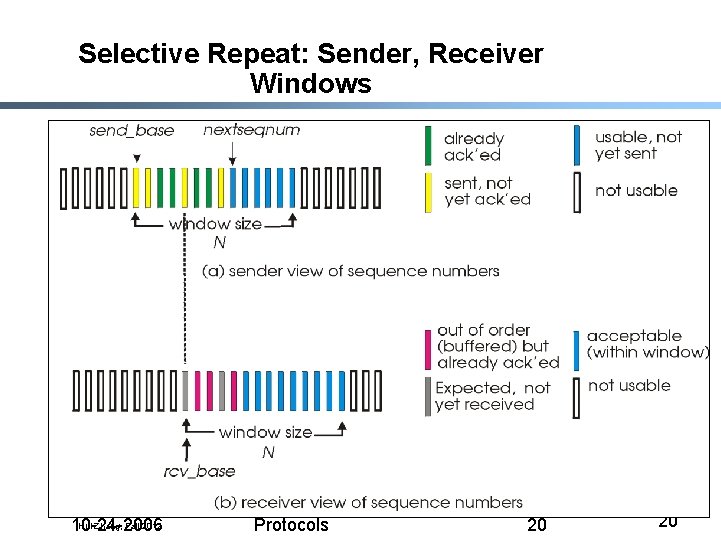
Selective Repeat: Sender, Receiver Windows Hui Zhang, Fall 2012 10 -24 -2006 Lecture 16: Transport Protocols 20 20

Summary of ARQ Protocols § Mechanisms: - Sequence number - Timeout - Acknowledgement § § Sender window: fill the pipe Receiver window: handle out-of-order delivery Hui Zhang, Fall 2012 10 -24 -2006 Lecture 16: Transport Protocols 21 21

Many Nuances § What type of acknowledgements? - Selective acknowledgement - Cumulative acknowledgement - Negative acknowledgement § How big should be the timeout value, SWS, RWS, sequence number field? § Reliability mechanism used to implement other functions: flow control, congestion control - Function overloading introduces ambiguity and complexity Hui Zhang, Fall 2012 22

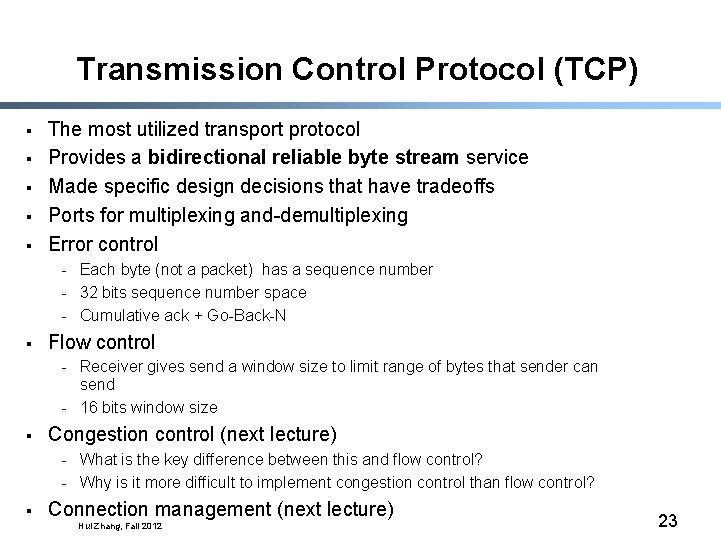
Transmission Control Protocol (TCP) § § § The most utilized transport protocol Provides a bidirectional reliable byte stream service Made specific design decisions that have tradeoffs Ports for multiplexing and-demultiplexing Error control - Each byte (not a packet) has a sequence number - 32 bits sequence number space - Cumulative ack + Go-Back-N § Flow control - Receiver gives send a window size to limit range of bytes that sender can send - 16 bits window size § Congestion control (next lecture) - What is the key difference between this and flow control? - Why is it more difficult to implement congestion control than flow control? § Connection management (next lecture) Hui Zhang, Fall 2012 23

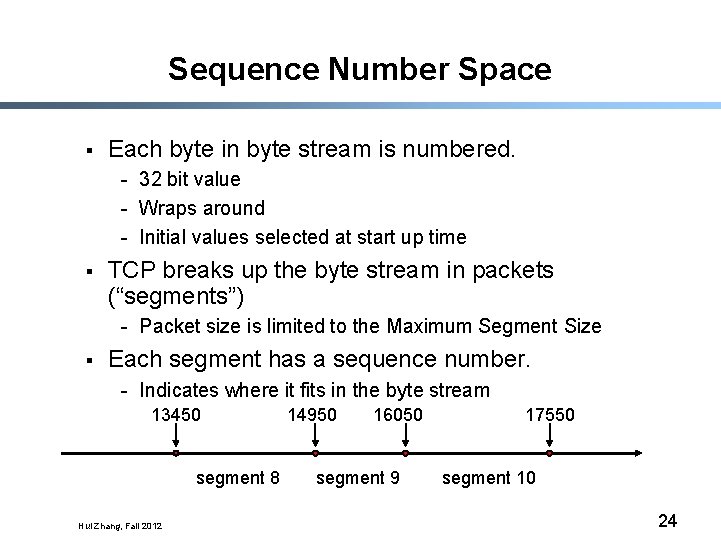
Sequence Number Space § Each byte in byte stream is numbered. - 32 bit value - Wraps around - Initial values selected at start up time § TCP breaks up the byte stream in packets (“segments”) - Packet size is limited to the Maximum Segment Size § Each segment has a sequence number. - Indicates where it fits in the byte stream 13450 segment 8 Hui Zhang, Fall 2012 14950 16050 segment 9 17550 segment 10 24

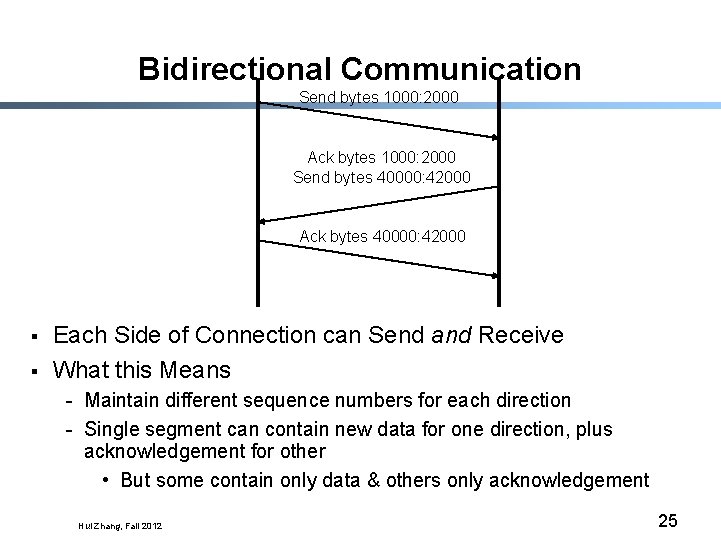
Bidirectional Communication Send bytes 1000: 2000 Ack bytes 1000: 2000 Send bytes 40000: 42000 Ack bytes 40000: 42000 § § Each Side of Connection can Send and Receive What this Means - Maintain different sequence numbers for each direction - Single segment can contain new data for one direction, plus acknowledgement for other • But some contain only data & others only acknowledgement Hui Zhang, Fall 2012 25

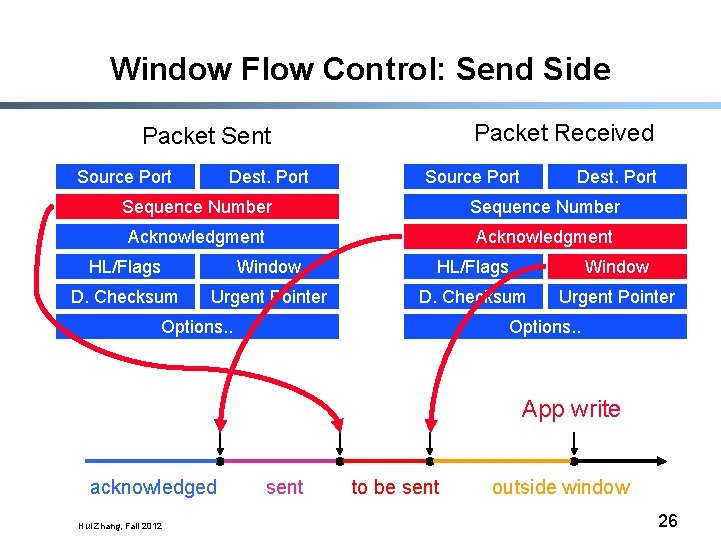
Window Flow Control: Send Side Packet Received Packet Sent Source Port Dest. Port Sequence Number Acknowledgment HL/Flags Window D. Checksum Urgent Pointer Options. . App write acknowledged Hui Zhang, Fall 2012 sent to be sent outside window 26

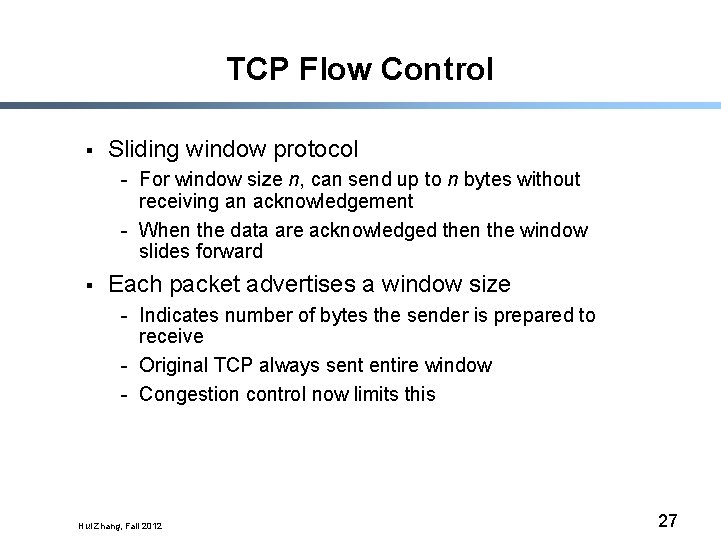
TCP Flow Control § Sliding window protocol - For window size n, can send up to n bytes without receiving an acknowledgement - When the data are acknowledged then the window slides forward § Each packet advertises a window size - Indicates number of bytes the sender is prepared to receive - Original TCP always sent entire window - Congestion control now limits this Hui Zhang, Fall 2012 27

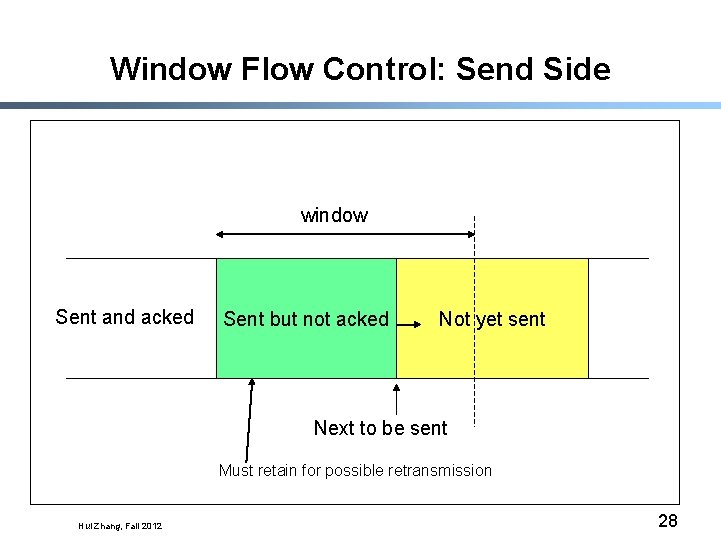
Window Flow Control: Send Side window Sent and acked Sent but not acked Not yet sent Next to be sent Must retain for possible retransmission Hui Zhang, Fall 2012 28

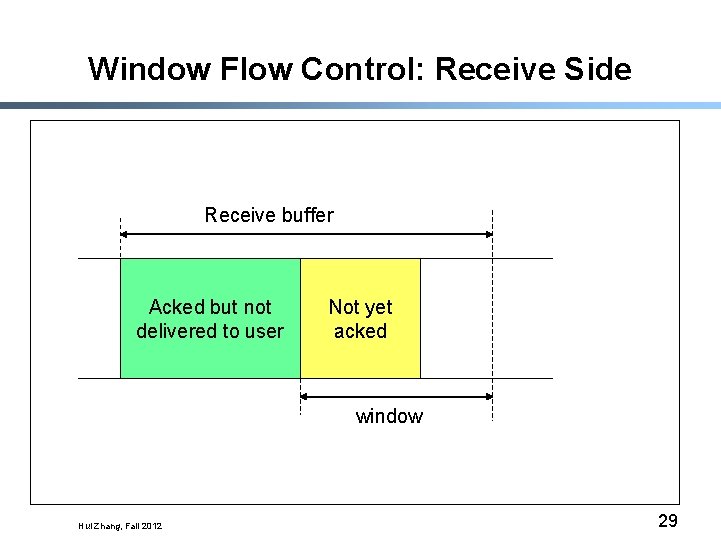
Window Flow Control: Receive Side Receive buffer Acked but not delivered to user Not yet acked window Hui Zhang, Fall 2012 29

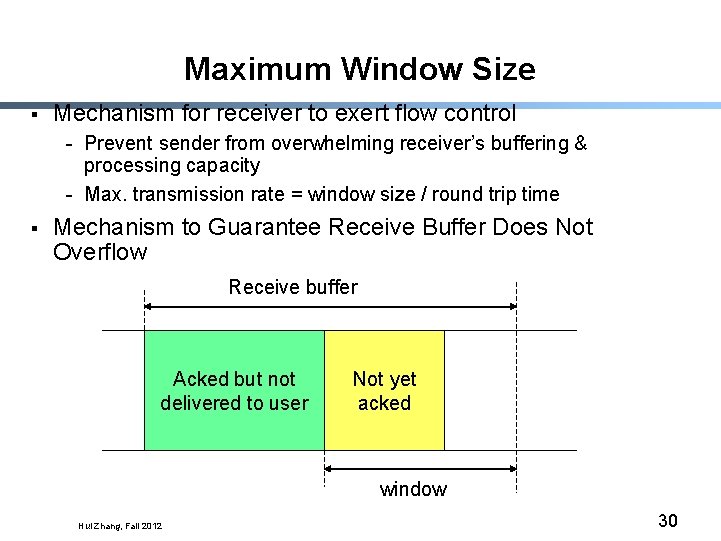
Maximum Window Size § Mechanism for receiver to exert flow control - Prevent sender from overwhelming receiver’s buffering & processing capacity - Max. transmission rate = window size / round trip time § Mechanism to Guarantee Receive Buffer Does Not Overflow Receive buffer Acked but not delivered to user Not yet acked window Hui Zhang, Fall 2012 30