128 bit Block Cipher Camellia Kazumaro Aoki Tetsuya
128 -bit Block Cipher Camellia Kazumaro Aoki* Tetsuya Ichikawa† Masayuki Kanda* Mitsuru Matsui† Shiho Moriai* Junko Nakajima† Toshio Tokita† * NTT † Mitsubishi Electric Corporation 3/12/2021 1

Outline ¦What’s Camellia? ¦Advantages over Rijndael ¦Performance Figures ¦Structure of Camellia ¦Security Consideration ¦Conclusion 2
What’s Camellia? ¦Jointly developed by NTT and Mitsubishi Electric Corporation § Designed by experts of research and development in cryptography § Inherited good characteristics from E 2 and MISTY ¦Same interface as AES § block size: 128 bits § key sizes: 128, 192, 256 bits 3

FAQ: Why “Camellia”? ¦Camellia is well known as “Camellia Japonica” botanically, and Japan is its origin. ¦Easy to pronounce : -) § unlike …. ¦Flower language: Good fortune, Perfect loveliness. 4
Users’ Demands on Block Ciphers Reliability Good Performer Interoperability AES coming soon! Royalty-Free (No IPR Problem) No More Ciphers! 5

Advantage over Rijndael ¦Efficiency in H/W Implementations § Smaller Hardware 9. 66 Kgates (0. 35 mm rule) § Better Throughput/Area 21. 9 Mbit/(s*Kgates) § Much more efficient in implementing both encryption and decryption ¦Excellent Key Agility § Shorter key setup time § On-the-fly subkey computation for both encryption and decryption 6
Advantage over Rijndael (Cont. ) ¦Symmetric Encryption and Decryption (Feistel cipher) § Very little additional area to implement both encryption and decryption in H/W § Little additional ROM is favorable in restrictedspace environments ¦Better performance in JAVA ¦Comparable speed on 8 -bit CPUs § e. g. Z 80 7
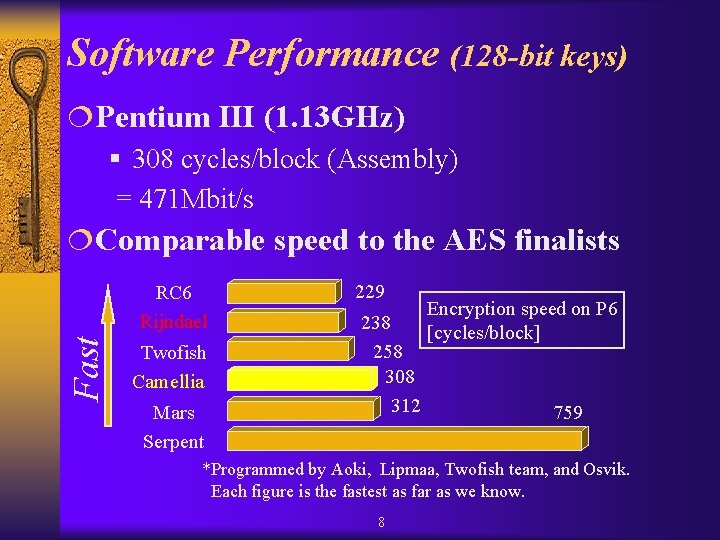
Software Performance (128 -bit keys) ¦Pentium III (1. 13 GHz) § 308 cycles/block (Assembly) = 471 Mbit/s ¦Comparable speed to the AES finalists Fast RC 6 Rijndael Twofish Camellia Mars Serpent 229 238 258 308 312 Encryption speed on P 6 [cycles/block] 759 *Programmed by Aoki, Lipmaa, Twofish team, and Osvik. Each figure is the fastest as far as we know. 8
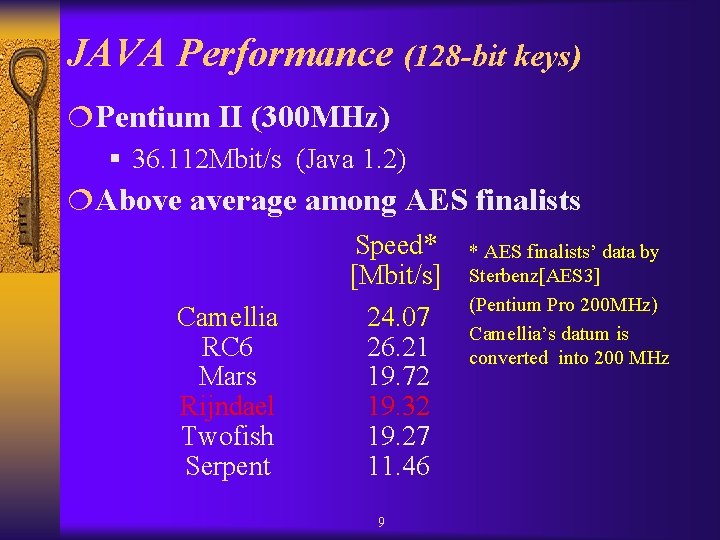
JAVA Performance (128 -bit keys) ¦Pentium II (300 MHz) § 36. 112 Mbit/s (Java 1. 2) ¦Above average among AES finalists Speed* * AES finalists’ data by [Mbit/s] Sterbenz[AES 3] (Pentium Pro 200 MHz) Camellia 24. 07 Camellia’s datum is RC 6 26. 21 converted into 200 MHz Mars 19. 72 Rijndael 19. 32 Twofish 19. 27 Serpent 11. 46 9

Hardware (128 -bit keys) ¦ASIC (0. 35 mm CMOS) § Type II: Top priority: Size • Less than 10 KGates (212 Mbit/s) • Among smallest 128 -bit block ciphers § Type I: Top priority: Speed Area [Kgates] Camellia 273 Rijndael 613 Serpent 504 Twofish 432 RC 6 1, 643 MARS 2, 936 Throughput [Mbit/s] 1, 171 1, 950 932 394 204 226 Thru/Area 4. 29 3. 18 1. 85 0. 91 0. 12 0. 08 The above data (except Camellia) by Ichikawa et al. are refered in NIST’s AES report. 10
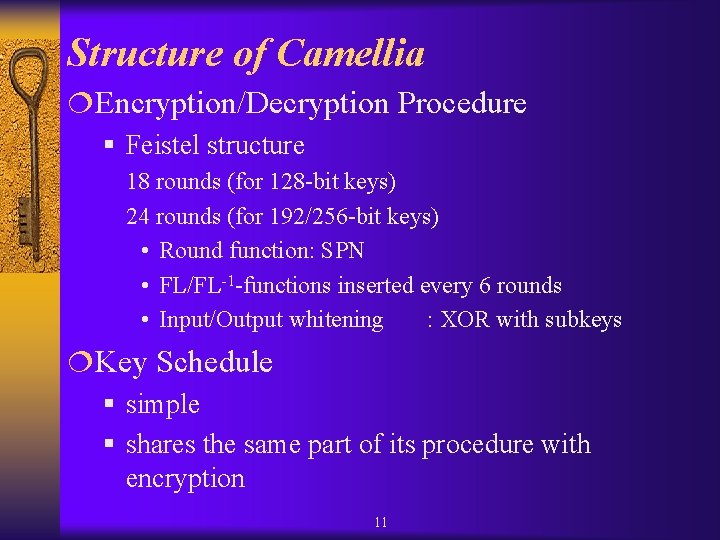
Structure of Camellia ¦Encryption/Decryption Procedure § Feistel structure 18 rounds (for 128 -bit keys) 24 rounds (for 192/256 -bit keys) • Round function: SPN • FL/FL-1 -functions inserted every 6 rounds • Input/Output whitening : XOR with subkeys ¦Key Schedule § simple § shares the same part of its procedure with encryption 11
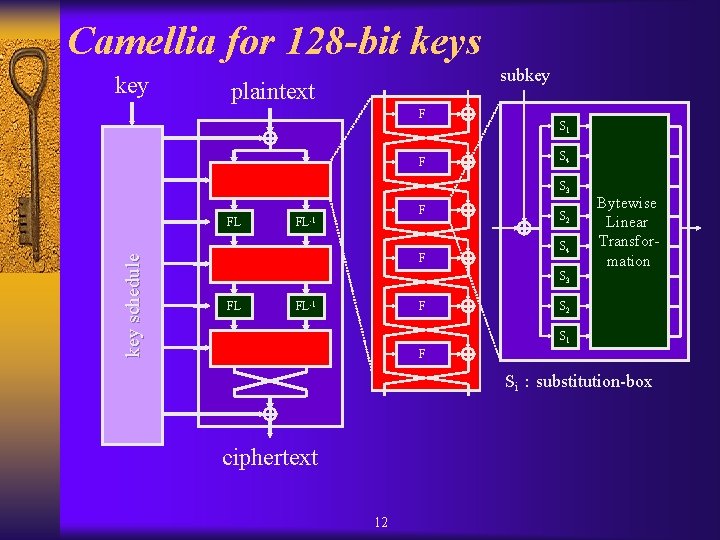
Camellia for 128 -bit keys key subkey plaintext F F S 1 S 4 S 3 key schedule FL F FL-1 F S 2 S 4 Bytewise Linear Transformation S 3 FL FL-1 F S 2 S 1 F Si:substitution-box ciphertext 12
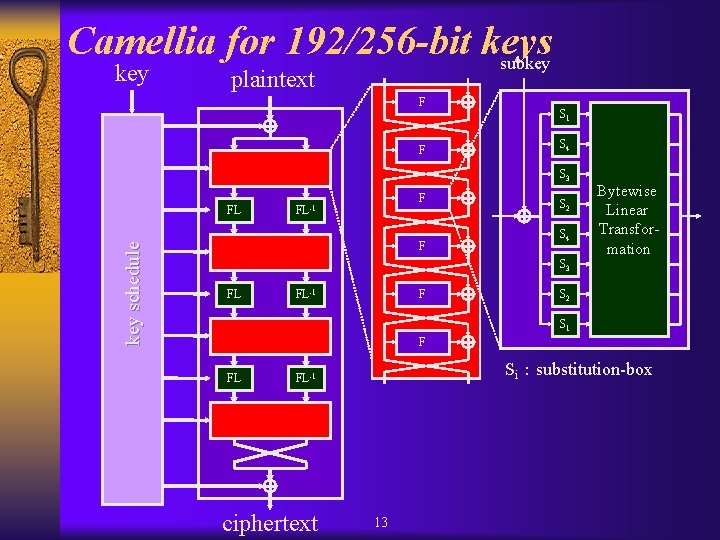
Camellia for 192/256 -bit keys subkey plaintext F F S 1 S 4 S 3 key schedule FL F FL-1 F S 2 S 4 Bytewise Linear Transformation S 3 FL FL-1 F S 2 S 1 F FL Si:substitution-box FL-1 ciphertext 13
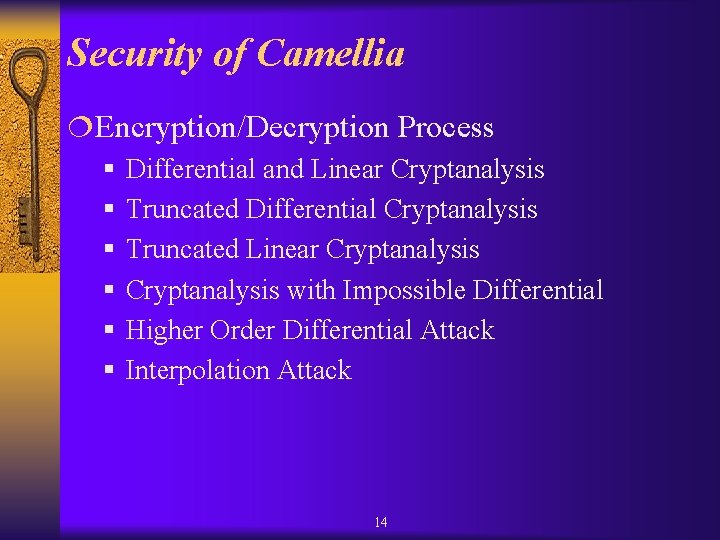
Security of Camellia ¦Encryption/Decryption Process § Differential and Linear Cryptanalysis § Truncated Differential Cryptanalysis § Truncated Linear Cryptanalysis § Cryptanalysis with Impossible Differential § Higher Order Differential Attack § Interpolation Attack 14

Security of Camellia (Cont. ) ¦Key Schedule § No Equivalent Keys § Slide Attack § Related-key Attack ¦Attacks on Implementations § Timing Attacks § Power Analysis 15
Conclusion ¦High level of Security § No known cryptanalytic attacks § A sufficiently large security margin ¦Efficiency on a wide range of platforms § Small and efficient H/W § High S/W performance § Performs well on low-cost platforms § JAVA 16

Standardization Activities ¦IETF § Submitted Internet-Drafts • A Description of the Camellia Encryption Algorithm – <draft-nakajima-camellia-00. txt> • Addition of the Camellia Encryption Algorithm to Transport Layer Security (TLS) – <draft-ietf-tls-camellia-00. txt> 18

Standardization Activities (Cont. ) ¦ISO/IEC JTC 1/SC 27 § Encryption Algorithms (N 2563) ¦CRYPTREC § Project to investigate and evaluate the cryptographic techniques proposed for the infrastructure of an electronic government of Japan ¦ WAP TLS ¦ Adopted in some Governmental Systems 19
- Slides: 18