128 bit Block Cipher Camellia Kazumaro Aoki Tetsuya

128 -bit Block Cipher Camellia Kazumaro Aoki* Tetsuya Ichikawa† Masayuki Kanda* Mitsuru Matsui† Shiho Moriai* Junko Nakajima† Toshio Tokita† * NTT † Mitsubishi Electric Corporation 2001. 10. 09. CRYPTREC Workshop Copyright (C) NTT & Mitsubishi Electric Corp. 2001 1

Outline What’s Camellia? r Structure of Camellia r Security Evaluation r Performance Figures r Intellectual Property Rights r Standardization Activities r Conclusion r <Appendix> r Comments on Security r Design Rationale 2001. 10. 09. CRYPTREC Workshop Copyright (C) NTT & Mitsubishi Electric Corp. 2001 2
What’s Camellia? r Jointly developed by NTT and Mitsubishi, 2000 l r Combining strength on cipher design technologies u NTT: High-speed SW implementation u Mitsubishi: Compact & high-speed HW implementation u Both: State-of-the-art security evaluation Same interface as AES l l Block size: Key size: 2001. 10. 09. CRYPTREC Workshop 128 bits 128, 192, 256 bits Copyright (C) NTT & Mitsubishi Electric Corp. 2001 3

What’s Camellia? r High level of security l l r Withstanding all known cryptanalytic attacks High security margin for use of the next several decades Efficiency on multiple platforms l l l Software: u High-speed on 32 -/64 -bit processors u Compact and high-performance on smart cards (8/32 -bit processors with restricted-space) Hardware: compact and high-performance u Smallest-class of area size among existing 128 -bit block ciphers Excellent key agility: short key setup time 2001. 10. 09. CRYPTREC Workshop Copyright (C) NTT & Mitsubishi Electric Corp. 2001 4
Structure of Camellia r Encryption/Decryption Procedure: l l r 18 -round Feistel structure (for 128 -bit keys) 24 -round Feistel structure (for 192 -/256 -bit keys) u Round function: SPN -1 u FL/FL -functions inserted every 6 rounds u Input/Output whitening : XOR with subkeys Key Schedule: l l Simple Shares the same 2 -round Feistel structure 2001. 10. 09. CRYPTREC Workshop Copyright (C) NTT & Mitsubishi Electric Corp. 2001 5
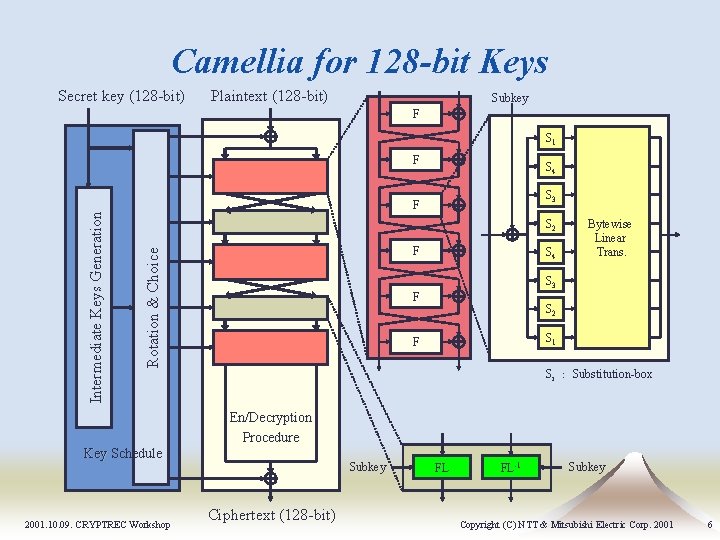
Camellia for 128 -bit Keys Secret key (128 -bit) Plaintext (128 -bit) Subkey F S 1 S 4 S 3 F S 2 F Rotation & Choice Intermediate Keys Generation F Key Schedule 2001. 10. 09. CRYPTREC Workshop S 4 Bytewise Linear Trans. S 3 F S 2 S 1 F Si : Substitution-box En/Decryption Procedure Subkey Ciphertext (128 -bit) FL FL-1 Subkey Copyright (C) NTT & Mitsubishi Electric Corp. 2001 6
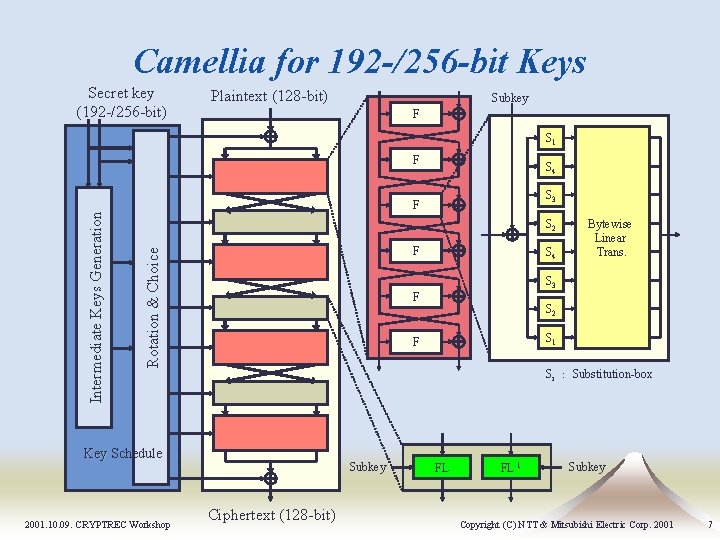
Camellia for 192 -/256 -bit Keys Secret key (192 -/256 -bit) Plaintext (128 -bit) Subkey F S 1 S 4 S 3 F S 2 F Rotation & Choice Intermediate Keys Generation F S 3 F S 2 S 1 F Si : Substitution-box Key Schedule 2001. 10. 09. CRYPTREC Workshop S 4 Bytewise Linear Trans. Subkey Ciphertext (128 -bit) FL FL-1 Subkey Copyright (C) NTT & Mitsubishi Electric Corp. 2001 7

Design Rationale (Digest) r Round function l l l r FL/FL-1 -functions l l r to provide high security against differential and linear cryptanalysis to achieve high performance on multiple platform to design small hardware to provide non-regularity across rounds without significantly impacting its performance Key schedule l l to provide excellent key agility to design small hardware 2001. 10. 09. CRYPTREC Workshop Copyright (C) NTT & Mitsubishi Electric Corp. 2001 8

Security Consideration r Camellia was designed to provide strong security against: l l l l l Differential and Linear Cryptanalysis Truncated Differential and Linear Cryptanalysis with Impossible Differential Boomerang Attack Higher Order Differential Attack & Square Attack Interpolation Attack & Linear Sum Attack No Equivalent Keys Slide Attack Related-key Attack Implementation Attacks, … 2001. 10. 09. CRYPTREC Workshop Copyright (C) NTT & Mitsubishi Electric Corp. 2001 9
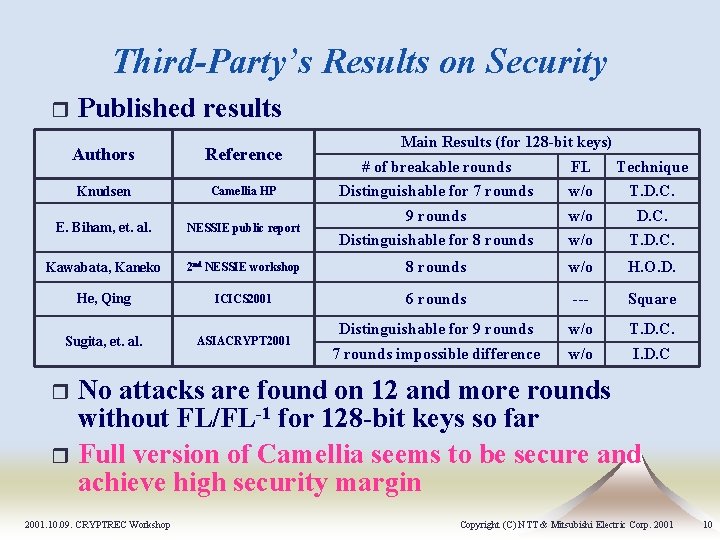
Third-Party’s Results on Security r Published results Authors Reference Knudsen Camellia HP E. Biham, et. al. NESSIE public report Kawabata, Kaneko Main Results (for 128 -bit keys) # of breakable rounds FL Technique Distinguishable for 7 rounds w/o T. D. C. 9 rounds w/o D. C. Distinguishable for 8 rounds w/o T. D. C. 2 nd NESSIE workshop 8 rounds w/o H. O. D. He, Qing ICICS 2001 6 rounds --- Square Sugita, et. al. ASIACRYPT 2001 Distinguishable for 9 rounds w/o T. D. C. 7 rounds impossible difference w/o I. D. C No attacks are found on 12 and more rounds without FL/FL-1 for 128 -bit keys so far r Full version of Camellia seems to be secure and achieve high security margin r 2001. 10. 09. CRYPTREC Workshop Copyright (C) NTT & Mitsubishi Electric Corp. 2001 10
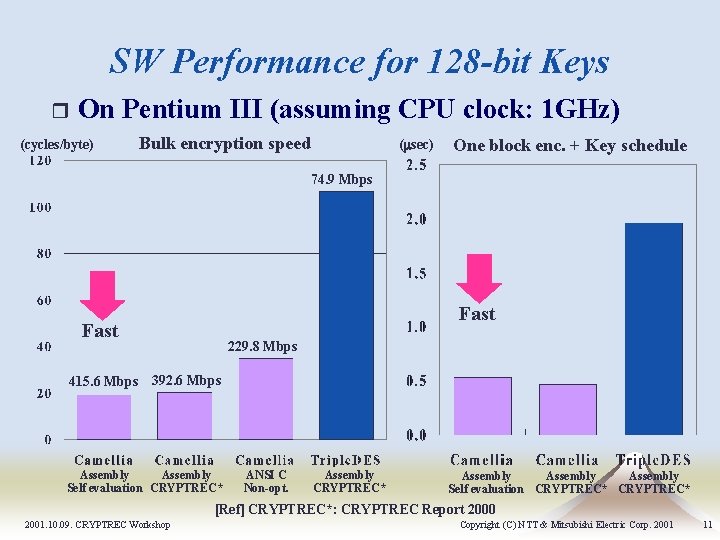
SW Performance for 128 -bit Keys r On Pentium III (assuming CPU clock: 1 GHz) (cycles/byte) Bulk encryption speed (msec) One block enc. + Key schedule 74. 9 Mbps Fast 229. 8 Mbps 415. 6 Mbps 392. 6 Mbps Assembly Self evaluation CRYPTREC* ANSI C Non-opt. Assembly CRYPTREC* Assembly Self evaluation CRYPTREC* [Ref] CRYPTREC*: CRYPTREC Report 2000 2001. 10. 09. CRYPTREC Workshop Copyright (C) NTT & Mitsubishi Electric Corp. 2001 11
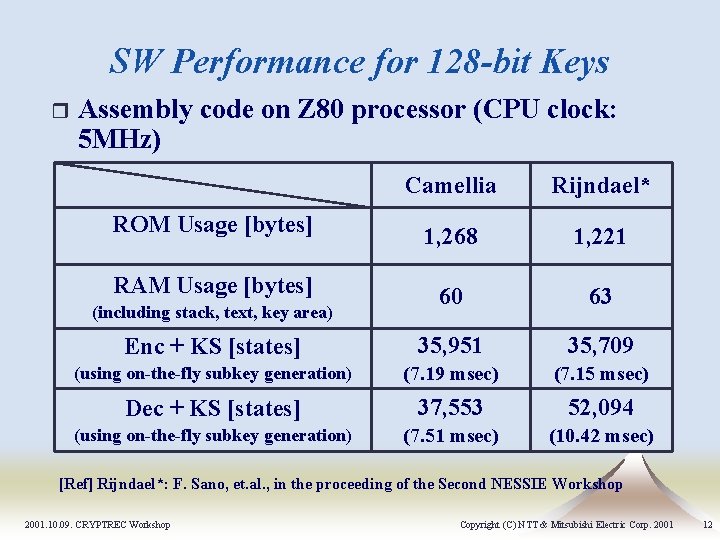
SW Performance for 128 -bit Keys r Assembly code on Z 80 processor (CPU clock: 5 MHz) Camellia Rijndael* ROM Usage [bytes] 1, 268 1, 221 RAM Usage [bytes] 60 63 Enc + KS [states] 35, 951 35, 709 (using on-the-fly subkey generation) (7. 19 msec) (7. 15 msec) Dec + KS [states] 37, 553 52, 094 (using on-the-fly subkey generation) (7. 51 msec) (10. 42 msec) (including stack, text, key area) [Ref] Rijndael*: F. Sano, et. al. , in the proceeding of the Second NESSIE Workshop 2001. 10. 09. CRYPTREC Workshop Copyright (C) NTT & Mitsubishi Electric Corp. 2001 12
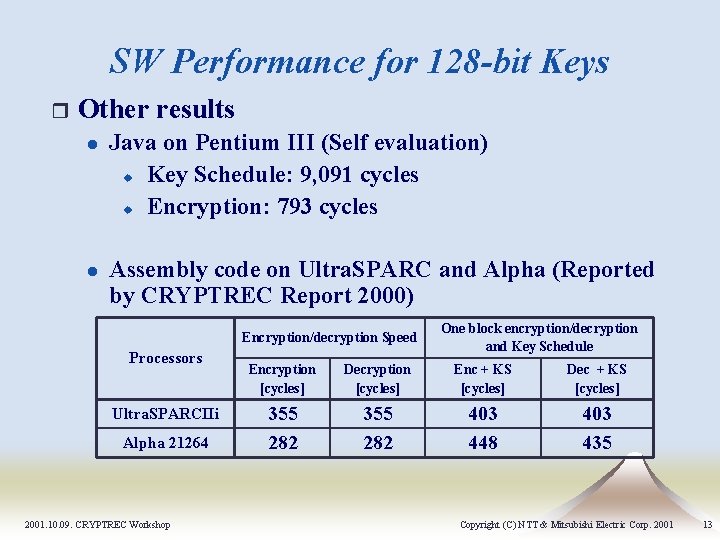
SW Performance for 128 -bit Keys r Other results l l Java on Pentium III (Self evaluation) u Key Schedule: 9, 091 cycles u Encryption: 793 cycles Assembly code on Ultra. SPARC and Alpha (Reported by CRYPTREC Report 2000) Encryption/decryption Speed Processors Ultra. SPARCIIi Alpha 21264 2001. 10. 09. CRYPTREC Workshop One block encryption/decryption and Key Schedule Encryption [cycles] Decryption [cycles] Enc + KS [cycles] Dec + KS [cycles] 355 282 403 448 403 435 Copyright (C) NTT & Mitsubishi Electric Corp. 2001 13
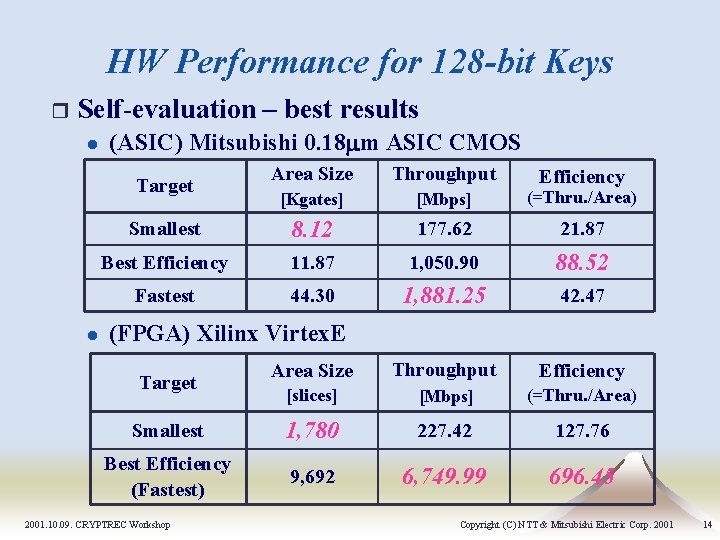
HW Performance for 128 -bit Keys r Self-evaluation – best results l (ASIC) Mitsubishi 0. 18 mm ASIC CMOS Area Size Throughput [Kgates] [Mbps] (=Thru. /Area) Smallest 8. 12 177. 62 21. 87 Best Efficiency 11. 87 1, 050. 90 88. 52 Fastest 44. 30 1, 881. 25 42. 47 Area Size Throughput Efficiency [slices] [Mbps] (=Thru. /Area) Smallest 1, 780 227. 42 127. 76 Best Efficiency (Fastest) 9, 692 6, 749. 99 696. 45 Target l Efficiency (FPGA) Xilinx Virtex. E Target 2001. 10. 09. CRYPTREC Workshop Copyright (C) NTT & Mitsubishi Electric Corp. 2001 14

Intellectual Property Rights r We declare that there is no responsibility for evaluation purpose of CRYPTREC on Camellia r We are prepared to grant, on the basis of reciprocity and non-discriminatory, a royaltyfree license under the essential patent of Camellia to an unrestricted number of applicants to manufacture, use and/or sell implementations of Camellia 2001. 10. 09. CRYPTREC Workshop Copyright (C) NTT & Mitsubishi Electric Corp. 2001 15
Standardization Activities r NESSIE (New European Schemes for Signature, Integrity, and Encryption) project l r IETF l r Advanced to Phase II evaluation Submitted Internet-Drafts u Addition of the Camellia Encryption Algorithm to Transport Layer Security (TLS) u A Description of the Camellia Encryption Algorithm ISO/IEC JTC 1/SC 27 l Submitted to Japan NB u Encryption Algorithms (18033) 2001. 10. 09. CRYPTREC Workshop Copyright (C) NTT & Mitsubishi Electric Corp. 2001 16

For More Information… r Camellia Home Page http: //info. isl. ntt. co. jp/camellia/ l l r Specification & Sample code Technical papers on design rationale, performance, software implementation techniques, hardware evaluation, and details of cryptanalysis. E-mail camellia@isl. ntt. co. jp MISTY@isl. melco. jp 2001. 10. 09. CRYPTREC Workshop Copyright (C) NTT & Mitsubishi Electric Corp. 2001 17
Conclusion r Camellia is a 128 -bit block cipher with 128 -/192/256 -bit keys l l l r Based on precise design rationales High level of security u No known cryptanalytic attacks u High security margin Efficiency on a wide range of platforms u High performance on SW u Small and high performance on HW u Performs well on smart cards (low-cost platforms with restricted space) Camellia is a ROYALTY-FREE algorithm 2001. 10. 09. CRYPTREC Workshop Copyright (C) NTT & Mitsubishi Electric Corp. 2001 18

Question? 2001. 10. 09. CRYPTREC Workshop Copyright (C) NTT & Mitsubishi Electric Corp. 2001 19

Appendix 2001. 10. 09. CRYPTREC Workshop Copyright (C) NTT & Mitsubishi Electric Corp. 2001 20
Comments on Security of Camellia r Differential and Linear Cryptanalysis l r Truncated Differential and Linear Cryptanalysis l r Camellia with more than 10 rounds is indistinguishable from a random permutation Cryptanalysis with Impossible Differential l r 12 -round Camellia with FL/FL-1 -function layers has no differential/linear characteristic with probability higher than 2 -128 FL/FL-1 -function changes differential paths depending on key values Boomerang Attack l Best boomerang probability of 8 -round Camellia without FL/FL-1 -function layers is bounded by 2 -66 2001. 10. 09. CRYPTREC Workshop Copyright (C) NTT & Mitsubishi Electric Corp. 2001 21
Comments on Security of Camellia r Higher Order Differential Attack & Square Attack l r Interpolation Attack & Linear Sum Attack l r Degree of Boolean polynomial of Camellia is expected to become high enough Smallest number of unknown coefficients of Camellia is expected to become maximum Implementation Attacks l l One of “Favorable” algorithms Easiest to defend against the attacks u Some defense can be provided against such attacks without significantly impacting its performance 2001. 10. 09. CRYPTREC Workshop Copyright (C) NTT & Mitsubishi Electric Corp. 2001 22
Comments on Security of Camellia r No Equivalent Keys l r Slide Attack l r Set of subkeys generated by the key schedule contains the original secret key FL/FL-1 -function layers are inserted between every 6 rounds of Feistel network to provide non-regularity across rounds Related-key Attack l Subkey relations is hard to control and predict 2001. 10. 09. CRYPTREC Workshop Copyright (C) NTT & Mitsubishi Electric Corp. 2001 23
Design Rationale – Round Function r P-function l l r Can be represented by only bytewise XORs u For efficiency in a wide range of environments Branch number is optimal u For security against differential and linear cryptanalyses S-box l Functions affine equivalent to the inversion function in GF(28) u For security against v v v u differential and linear cryptanalysis higher order differential attacks interpolation attacks For small hardware design 2001. 10. 09. CRYPTREC Workshop Copyright (C) NTT & Mitsubishi Electric Corp. 2001 24
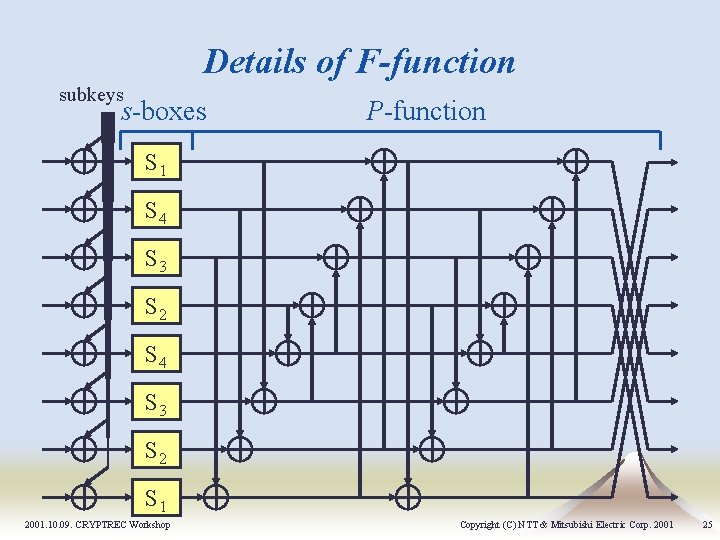
Details of F-function subkeys s-boxes P-function S 1 S 4 S 3 S 2 S 1 2001. 10. 09. CRYPTREC Workshop Copyright (C) NTT & Mitsubishi Electric Corp. 2001 25
Design Rationale – FL/FL-1 -functions r Provides non-regularity across rounds l l r A merit of regular Feistel structure is still preserved l r To be secure against slide attacks To thwart future unknown attacks Encryption and decryption procedures are the same except the order of subkeys Design criteria are similar to FL-function of MISTY l l To be linear for any fixed key, and to have variable forms depending on key values Constructed by logical operations for efficiency in both software and hardware 2001. 10. 09. CRYPTREC Workshop Copyright (C) NTT & Mitsubishi Electric Corp. 2001 26
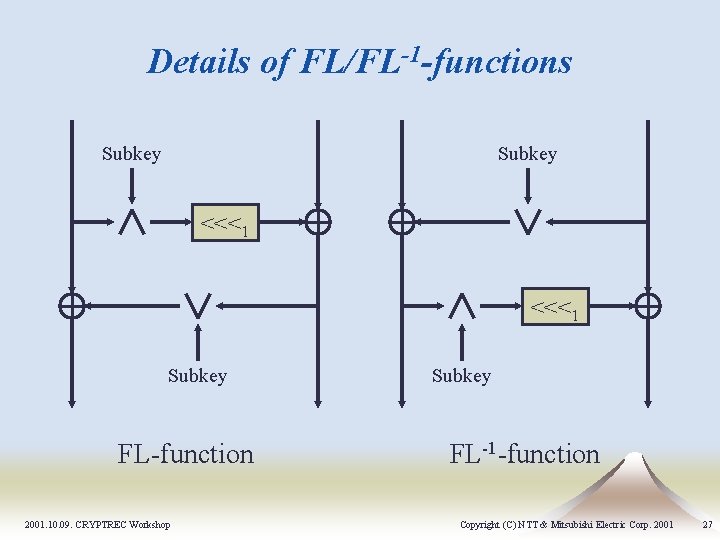
Details of FL/FL-1 -functions Subkey <<<1 Subkey FL-function 2001. 10. 09. CRYPTREC Workshop Subkey FL-1 -function Copyright (C) NTT & Mitsubishi Electric Corp. 2001 27
Design Rationale – Key Schedule r From HW aspect l l r For efficiency in a wide range of environments l l l r Simple and share part of its procedure with encryption/decryption Key schedule for 128 -bit keys can be performed by using a part of that for all keys Key setup time should be shorter than encryption time Support on-the-fly subkey generation On-the-fly subkey generation should be computable in the same way in both encryption and decryption From security aspect l l No equivalent keys No related-key attack 2001. 10. 09. CRYPTREC Workshop Copyright (C) NTT & Mitsubishi Electric Corp. 2001 28
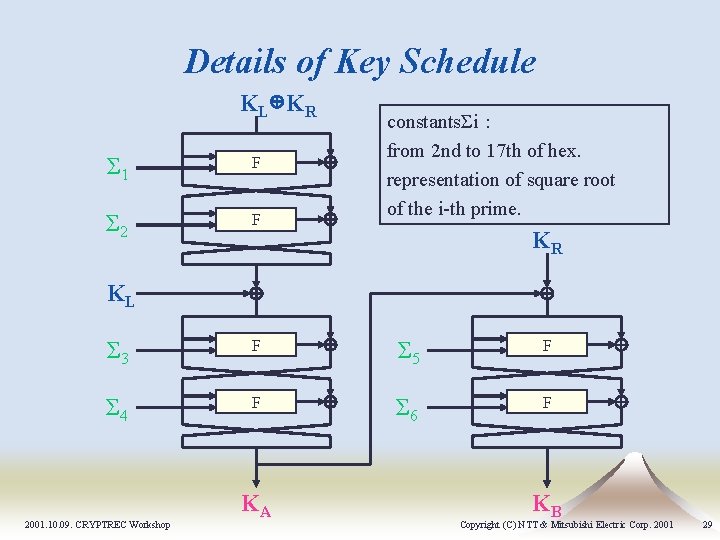
Details of Key Schedule KL KR Σ 1 F Σ 2 F constantsΣi: from 2 nd to 17 th of hex. representation of square root of the i-th prime. KR KL Σ 3 F Σ 5 F Σ 4 F Σ 6 F 2001. 10. 09. CRYPTREC Workshop KA KB Copyright (C) NTT & Mitsubishi Electric Corp. 2001 29
- Slides: 29