12 th ICE 514 Concrete Mathematics Term project

- Slides: 9

12 th 구광현 김유미 ICE 514 Concrete Mathematics Term project presentation Network Protection Mechanism using Spanning Tree Algorithm 2003. 04. 02. Kwang Hyun, Koo Yu Mi, Kim

2 Contents q Background supporting the main idea Ø Spanning tree algorithm Ø The concept of protection in the network q Term project main idea q Expected result q Schedule

3 Spanning tree algorithm q Spanning tree for a graph G Ø Subgraph of G that contains every vertex of G and is a tree Ø DFS (depth first search) or BFS (breadth first search) to create a spanning tree q Minimum cost spanning tree Ø Spanning tree of least cost Ø Algorithms : greedy method • Kruskal • Prim • Sollin

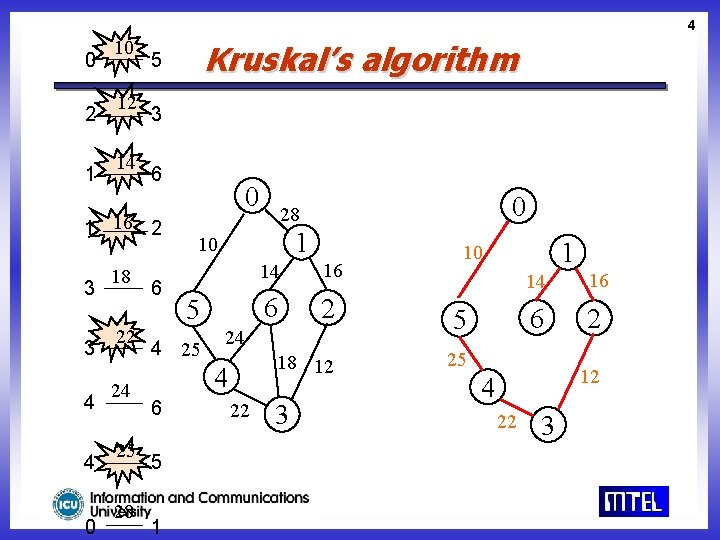
4 0 2 1 10 12 14 3 6 1 16 2 3 3 4 4 0 18 22 24 25 28 Kruskal’s algorithm 5 6 0 1 10 5 4 25 5 1 14 16 6 2 24 18 12 4 6 0 28 22 3 1 10 5 14 16 6 2 25 12 4 22 3

5 Concept of protection q Recovery framework Ø Ø Ø Failure detection Failure correction Failure localization & isolation Recovery Reversion

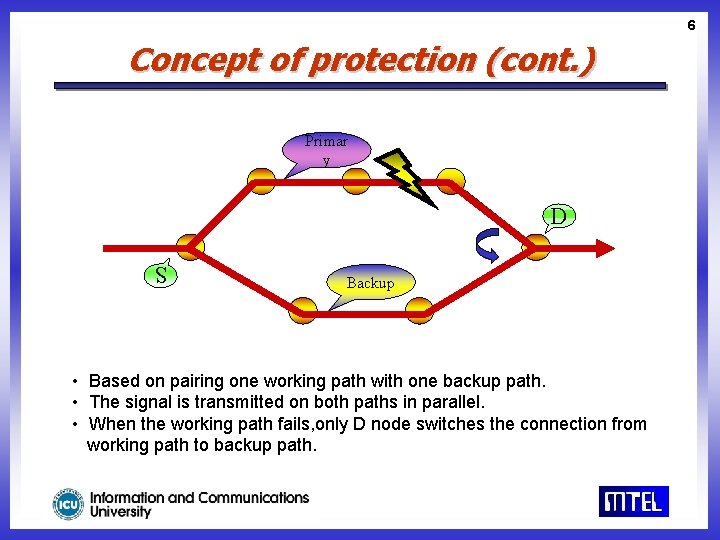
6 Concept of protection (cont. ) Primar y D Backup S • Based on pairing one working path with one backup path. • The signal is transmitted on both paths in parallel. • When the working path fails, only D node switches the connection from working path to backup path.

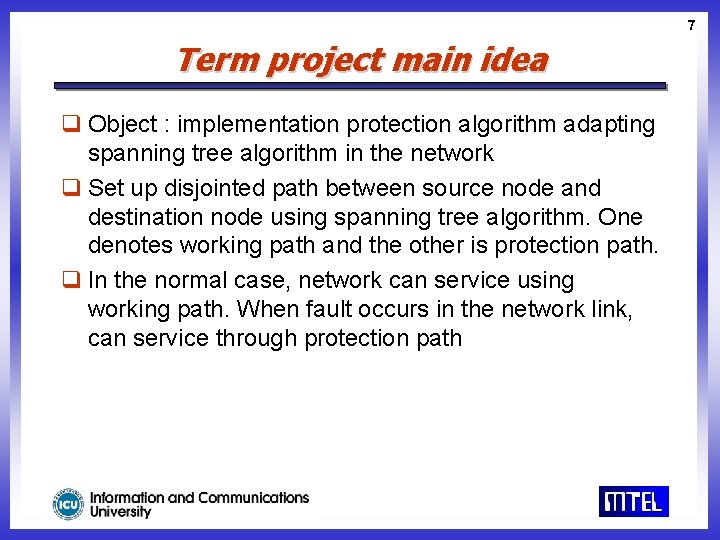
7 Term project main idea q Object : implementation protection algorithm adapting spanning tree algorithm in the network q Set up disjointed path between source node and destination node using spanning tree algorithm. One denotes working path and the other is protection path. q In the normal case, network can service using working path. When fault occurs in the network link, can service through protection path

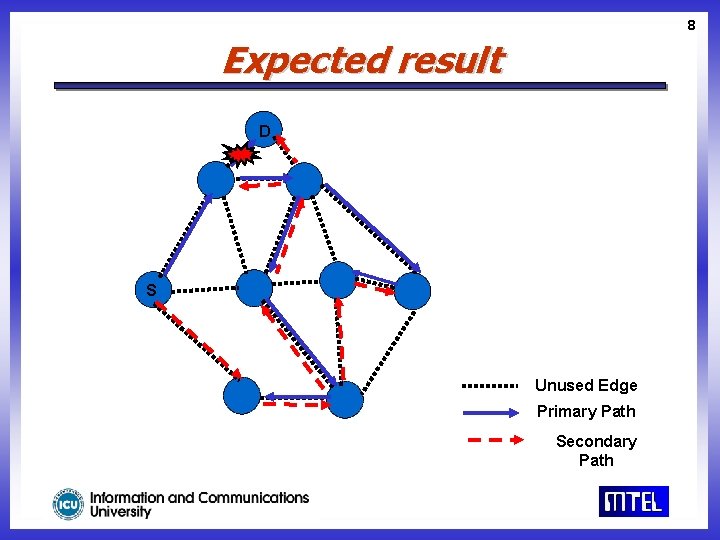
8 Expected result D S Unused Edge Primary Path Secondary Path

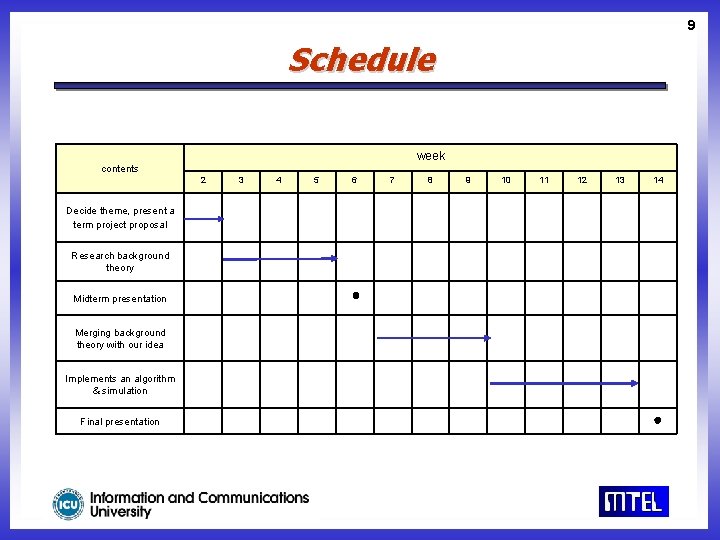
9 Schedule week contents 2 Decide theme, present a term project proposal Research background theory Midterm presentation Merging background theory with our idea Implements an algorithm & simulation Final presentation 3 4 5 6 7 8 9 10 11 12 13 14