10 Steps To Agile Development Without Compromising Enterprise








- Slides: 31

10 Steps To Agile Development Without Compromising Enterprise Security Author : Yair Rovek

Challenged by Agile “It is a well known and acknowledged fact that Agile processes are extremely difficult to combine with any existing security frameworks” -- Extract from a blog of a very popular software provider “The good news is that our retroactive security is very good…” -- Extract from the same blog as above

About Me Yair Rovek • 20+ years in the industry • 4 years Security Specialist @ • Leading the SDLC Program • Design security and new technologies within our products Contact Me! yairr@liveperson. com @lione_heart Hosted by OWASP & the NYC Chapter

Live. Person ID What we do? Saa. S platform for creation of meaningful connections through real-time engagement • • • 16 years in business Saa. S from day 1. NASDAQ & TASE (LPSN) ~8500 Customers ~800 employees How it works? Monitor web visitor’s behavior (Over 1. 5 B visits each month) Conduct behavioral ranking Provide the engagement platform (Over 10 M chats each month) Saa. S & Cloud only Hosted by OWASP & the NYC Chapter Security is NOT optional…

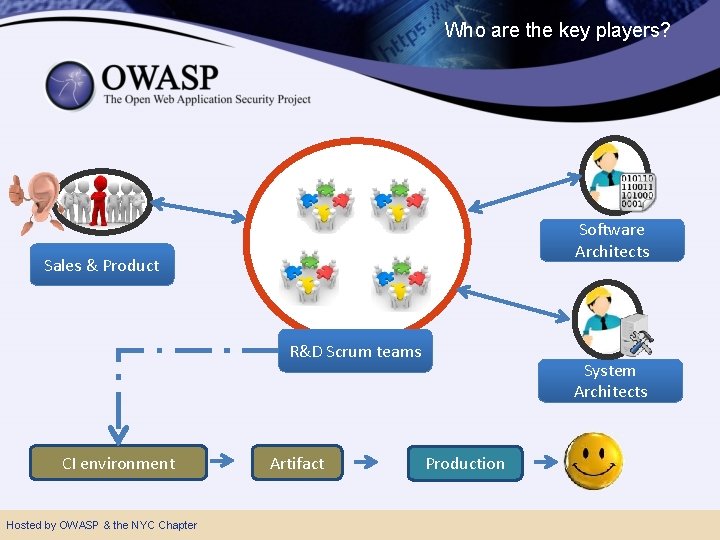
Who are the key players? Software Architects Sales & Product R&D Scrum teams CI environment Hosted by OWASP & the NYC Chapter Artifact System Architects Production

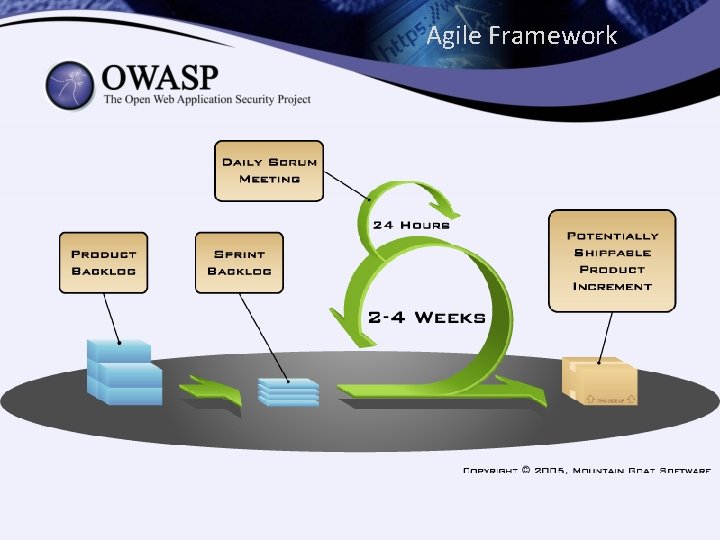
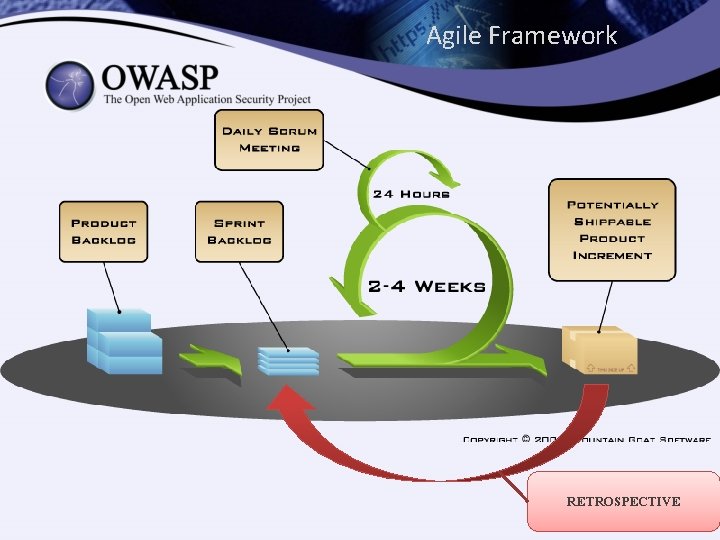
Agile Framework

Agile Framework RETROSPECTIVE

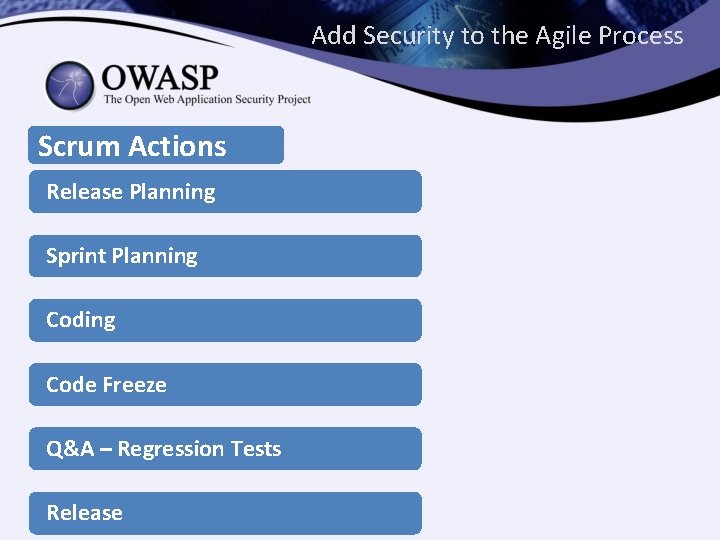
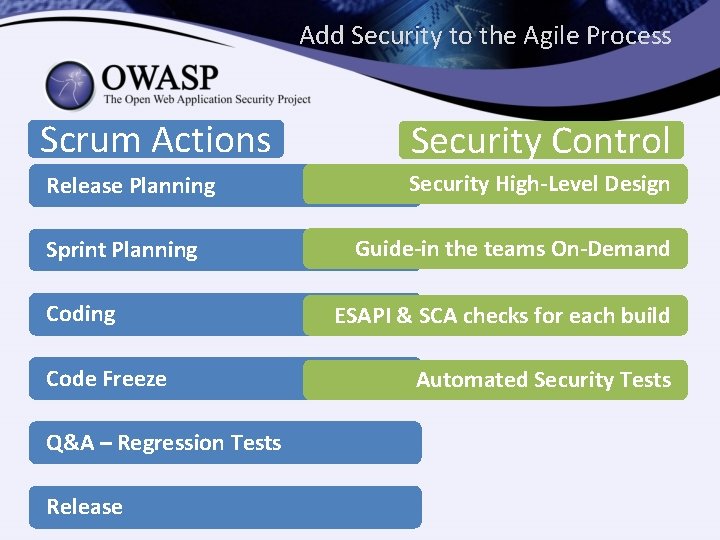
Add Security to the Agile Process Scrum Actions Release Planning Sprint Planning Code Freeze Q&A – Regression Tests Release

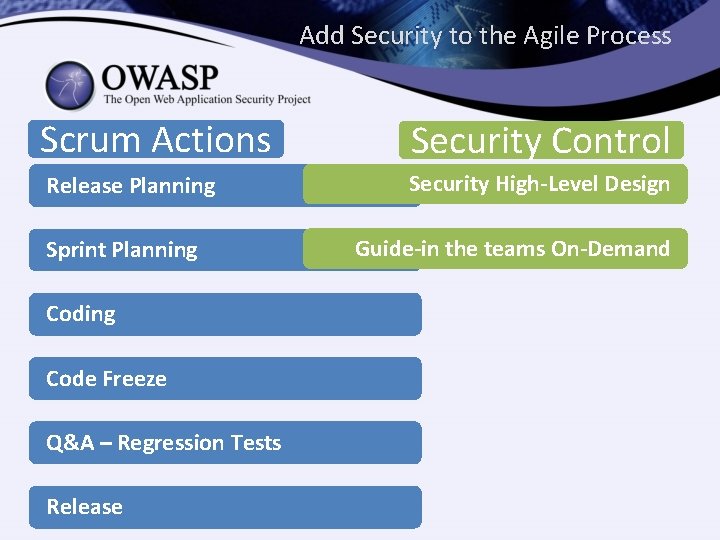
Add Security to the Agile Process Scrum Actions Security Control Release Planning Security High-Level Design Sprint Planning Code Freeze Q&A – Regression Tests Release

Add Security to the Agile Process Scrum Actions Security Control Release Planning Security High-Level Design Sprint Planning Code Freeze Q&A – Regression Tests Release Guide-in the teams On-Demand

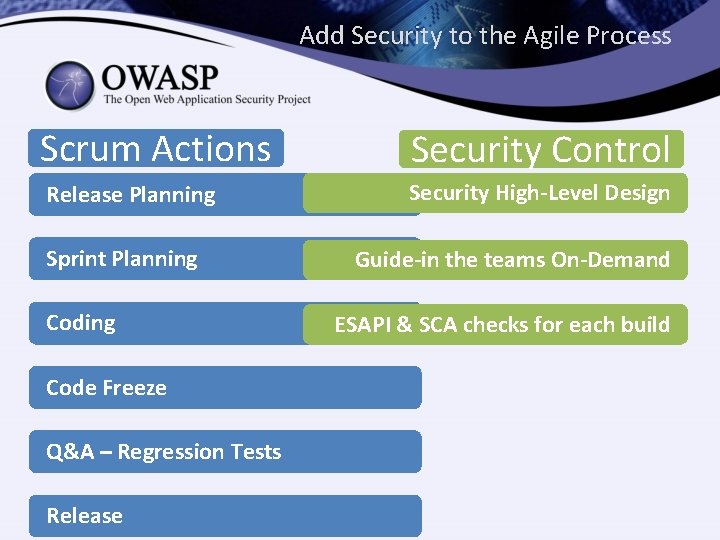
Add Security to the Agile Process Scrum Actions Security Control Release Planning Security High-Level Design Sprint Planning Code Freeze Q&A – Regression Tests Release Guide-in the teams On-Demand ESAPI & SCA checks for each build

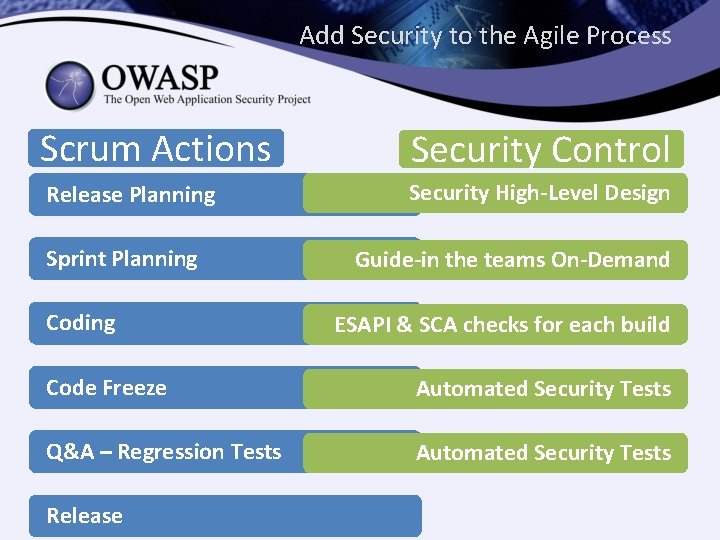
Add Security to the Agile Process Scrum Actions Security Control Release Planning Security High-Level Design Sprint Planning Code Freeze Q&A – Regression Tests Release Guide-in the teams On-Demand ESAPI & SCA checks for each build Automated Security Tests

Add Security to the Agile Process Scrum Actions Security Control Release Planning Security High-Level Design Sprint Planning Coding Guide-in the teams On-Demand ESAPI & SCA checks for each build Code Freeze Automated Security Tests Q&A – Regression Tests Automated Security Tests Release

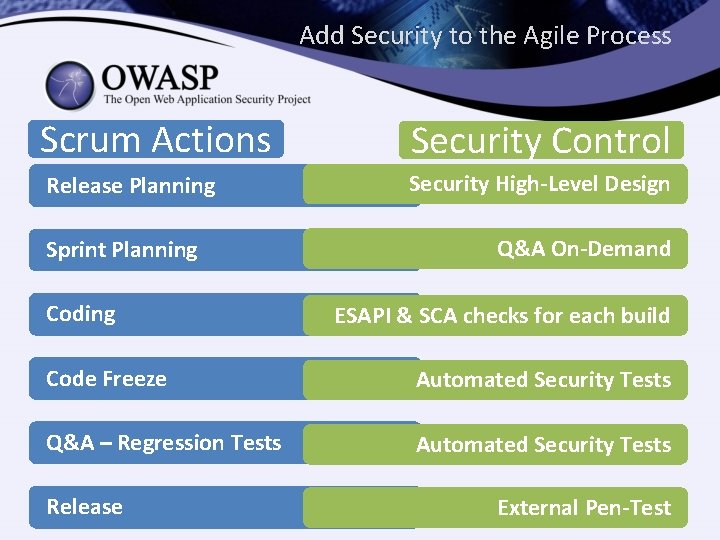
Add Security to the Agile Process Scrum Actions Security Control Release Planning Security High-Level Design Sprint Planning Coding Q&A On-Demand ESAPI & SCA checks for each build Code Freeze Automated Security Tests Q&A – Regression Tests Automated Security Tests Release External Pen-Test

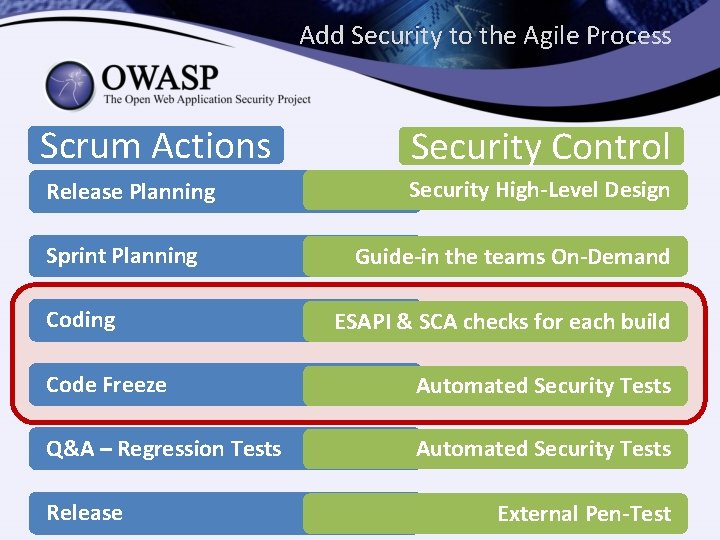
Add Security to the Agile Process Scrum Actions Security Control Release Planning Security High-Level Design Sprint Planning Coding Guide-in the teams On-Demand ESAPI & SCA checks for each build Code Freeze Automated Security Tests Q&A – Regression Tests Automated Security Tests Release External Pen-Test

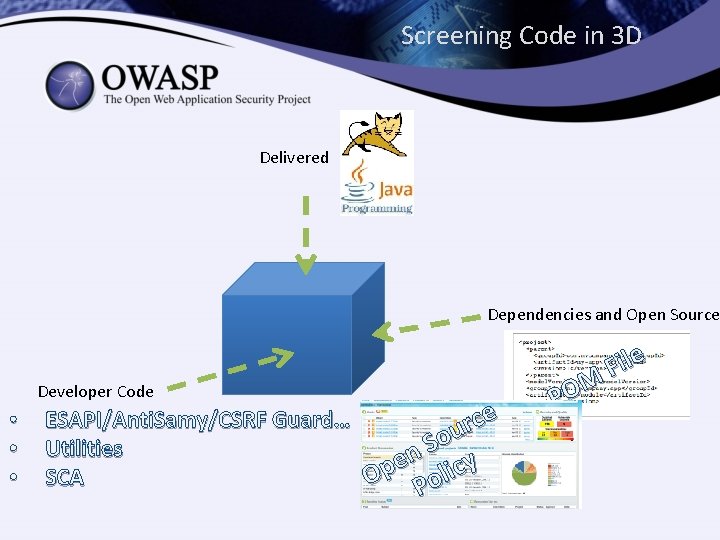
Screening Code in 3 D Delivered Dependencies and Open Source Developer Code • • • e ESAPI/Anti. Samy/CSRF Guard… c r u o S Utilities n e licy p SCA O Po File M O P

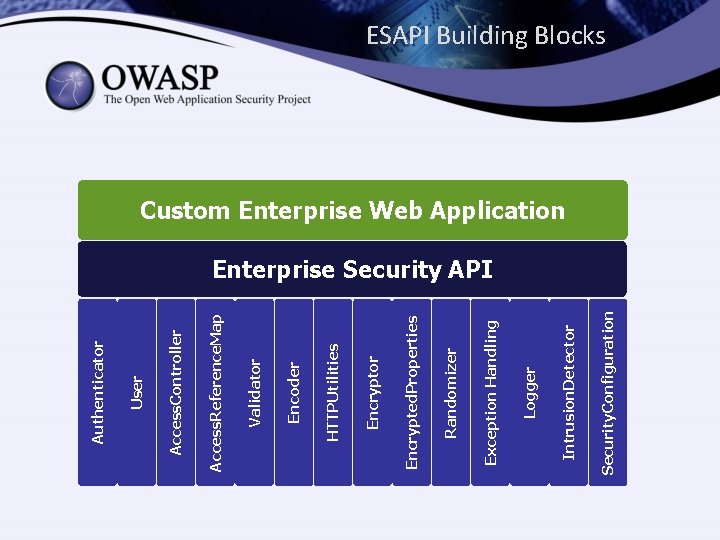
Security. Configuration Intrusion. Detector Logger Exception Handling Randomizer Encrypted. Properties Encryptor HTTPUtilities Encoder Validator Access. Reference. Map Access. Controller User Authenticator ESAPI Building Blocks Custom Enterprise Web Application Enterprise Security API

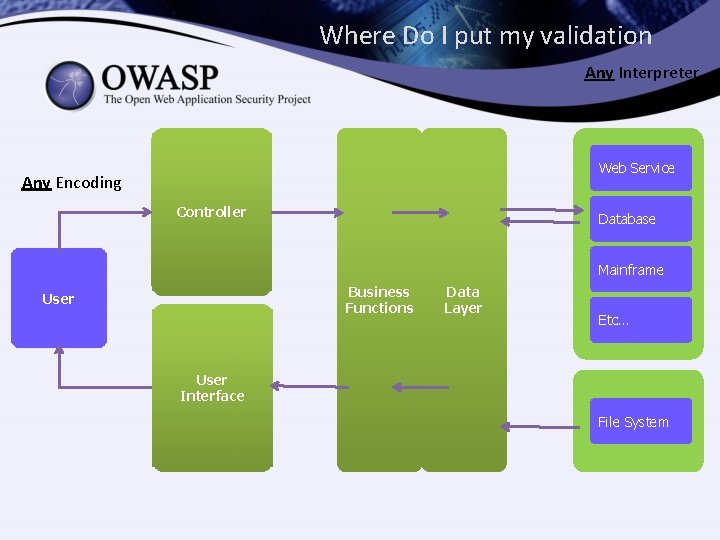
Where Do I put my validation Any Interpreter Web Service Any Encoding Controller Database Mainframe Business Functions User Data Layer Etc… User Interface File System

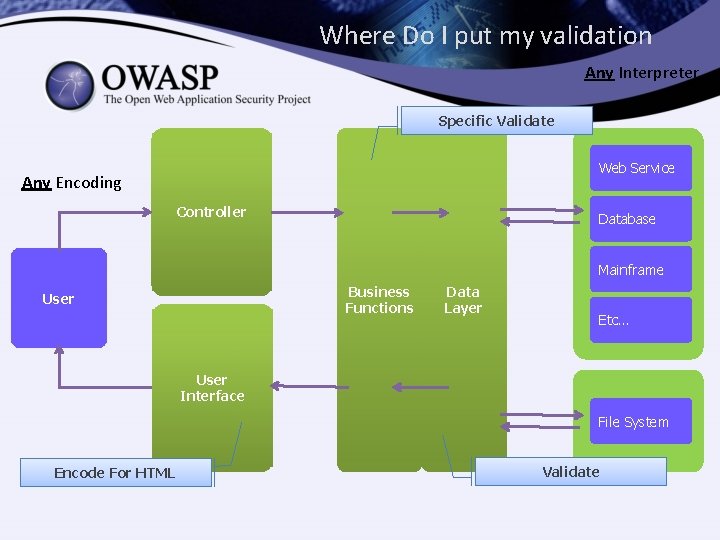
Where Do I put my validation Any Interpreter Specific Validate Web Service Any Encoding Controller Database Mainframe Business Functions User Data Layer Etc… User Interface File System Encode For HTML Validate

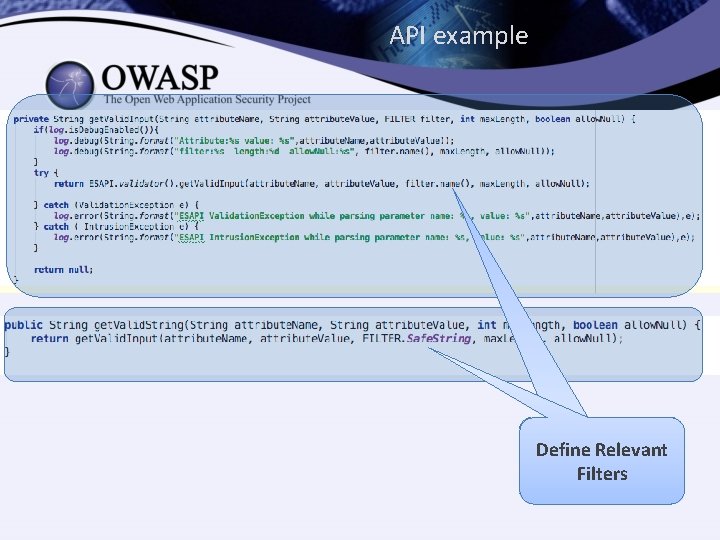
API example Define Relevant Filters

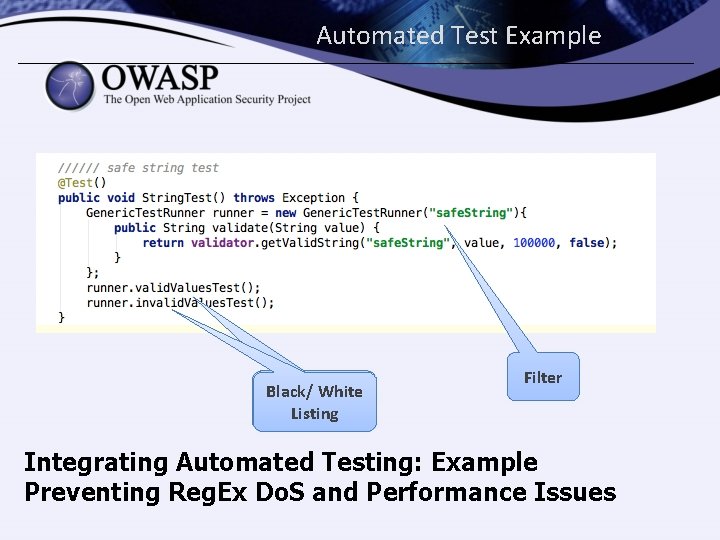
Automated Test Example Black/ White Listing Filter Integrating Automated Testing: Example Preventing Reg. Ex Do. S and Performance Issues

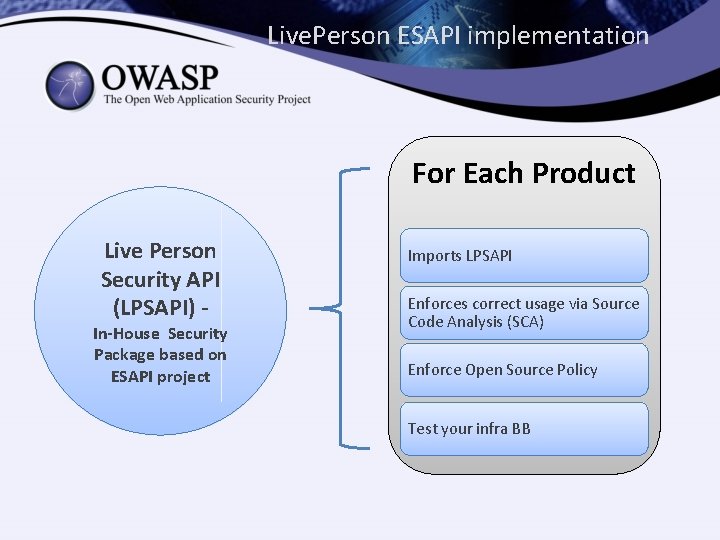
Live. Person ESAPI implementation For Each Product Live Person Security API (LPSAPI) - In-House Security Package based on ESAPI project Imports LPSAPI Enforces correct usage via Source Code Analysis (SCA) Enforce Open Source Policy Test your infra BB

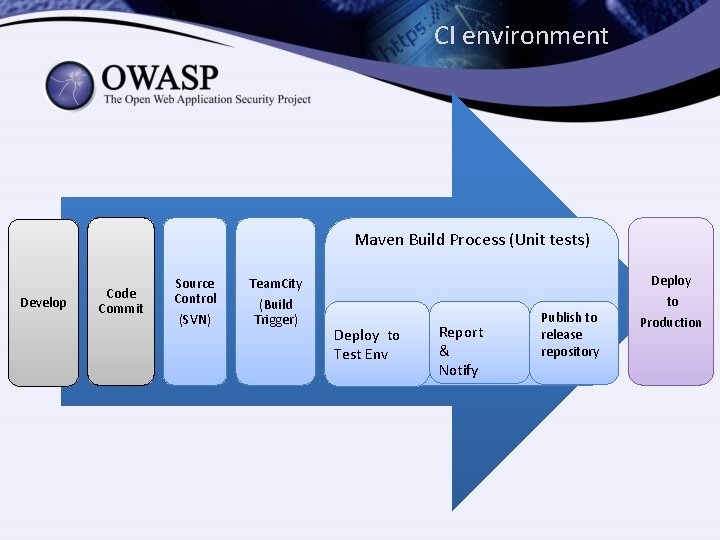
CI environment Maven Build Process (Unit tests) Develop Code Commit Source Control (SVN) Team. City (Build Trigger) Deploy to Test Env Report & Notify Publish to release repository Deploy to Production

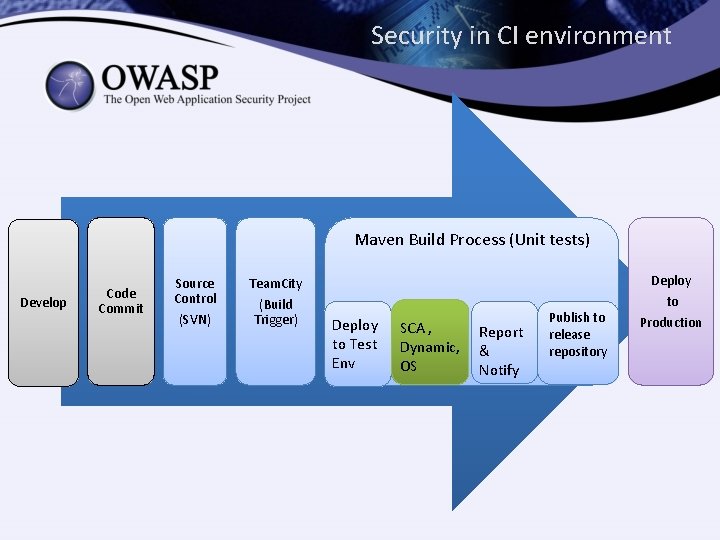
Security in CI environment Maven Build Process (Unit tests) Develop Code Commit Source Control (SVN) Team. City (Build Trigger) Deploy to Test Env SCA , Dynamic, OS Report & Notify Publish to release repository Deploy to Production

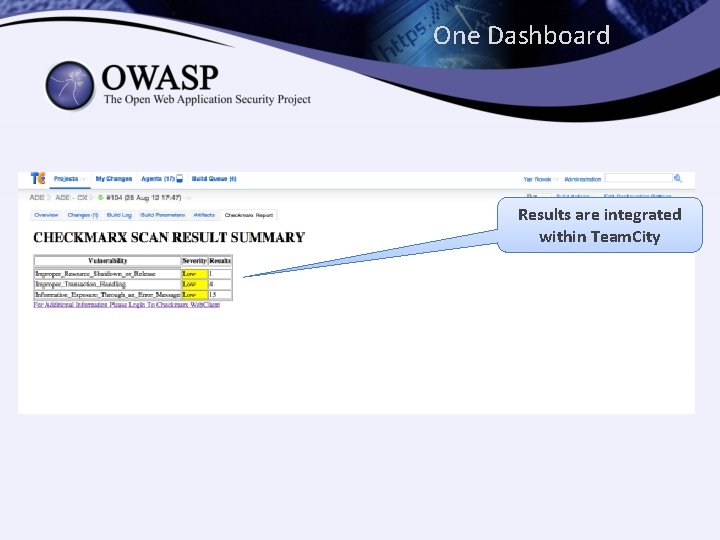
One Dashboard Results are integrated within Team. City

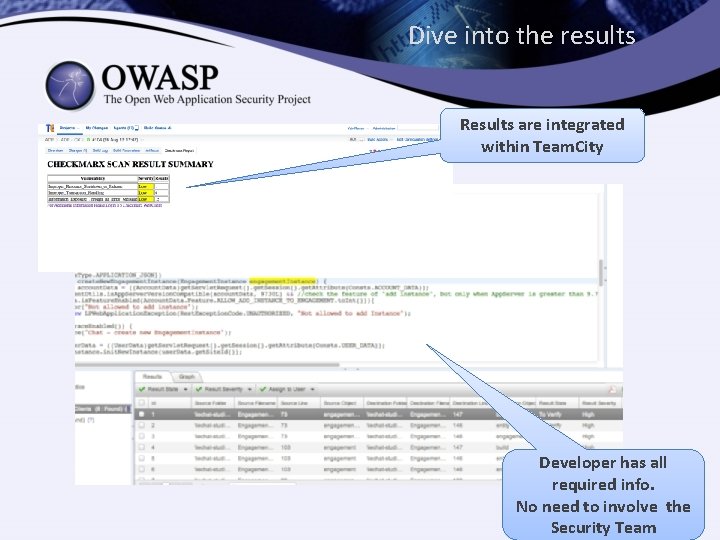
Dive into the results Results are integrated within Team. City Developer has all required info. No need to involve the Security Team

10 Best Practices Secure Agile Development

Key Success Factors Identify the process within R&D and set a plan to become part of it Security Package API to be consumed with each code (ESAPI Anti. Samy CSRF Guard) Screen and enforce your policy on your code Open Source and platform Use automation to collaborate with the security dynamic test Allow customer to run a pen test and work as a community to succeed

Key Success Factors Engage tech leaders as security champions by showing them the value Train developers on a regular basis Create a knowledge base and discussions around security Break the build for any “High” or “Medium” findings Start small but think big

Never ending story …

Contact Me! yairr@liveperson. com @lione_heart