1 NET 431 ADVANCED NET SERVICES Networks and








- Slides: 13

1 NET 431: ADVANCED NET SERVICES Networks and Communication Department Tutorial 2

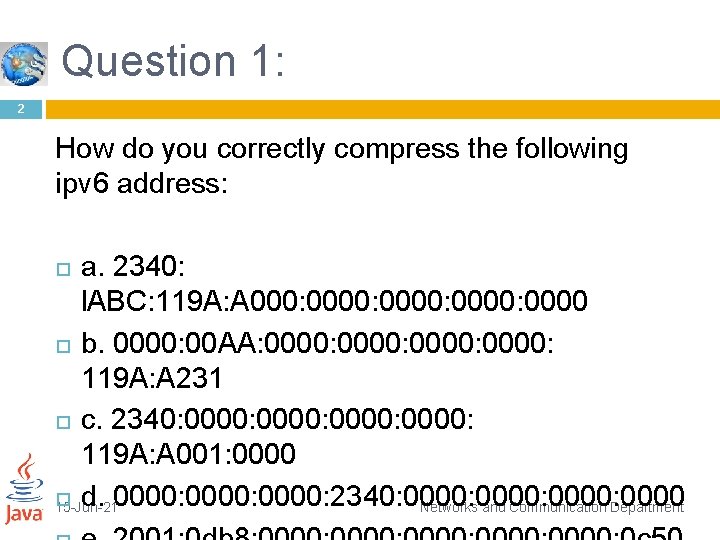
Question 1: 2 How do you correctly compress the following ipv 6 address: a. 2340: l. ABC: 119 A: A 000: 0000: 0000 b. 0000: 00 AA: 0000: 119 A: A 231 c. 2340: 0000: 119 A: A 001: 0000 d. 0000: 2340: 0000: 0000 15 -Jun-21 Networks and Communication Department

3 a. 2340: 1 ABC: 119 A: A 000: : 0 or 2340: 1 abc: 119 a: a 000: : b. 0: AA: : 119 A: A 231 c. 2340: : 119 A: A 001: 0 d. 0: 0: 0: 2340: : 0 or 0: 0: 0: 2340: : e. 15 -Jun-21 Networks and Communication Department

Question 2 4 Q 5: Show the expand (unabbreviated) form of the following ipv 6 addresses. a. 0: : 0 b. 0: AA: : 0 c. 0: 1234: : 3 d. 123: : 1: 2 15 -Jun-21 Networks and Communication Department

5 A- 0000: 0000: 0000 b. 0000: 00 AA: 0000: 0000 c. 0000: 1234: 0000: 0000: 0003 d. 0123: 0000: 0000: 0001: 0002 15 -Jun-21 Networks and Communication Department

Q 3: 6 What is the type of the following address? FE 80: : 12? Link local address 15 -Jun-21 Networks and Communication Department

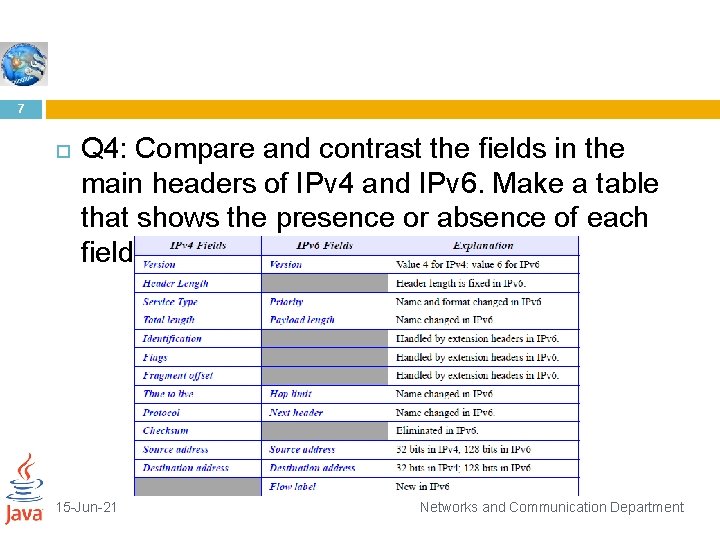
7 Q 4: Compare and contrast the fields in the main headers of IPv 4 and IPv 6. Make a table that shows the presence or absence of each field. 15 -Jun-21 Networks and Communication Department

8 Q 5: List three transition strategies to move from IPv 4 to IPv 6. Explain the difference between tunneling and dual stack strategies during the transition period. When is each strategy used? The three transition strategies are dual stack, tunneling, and header translation. In tunneling the IPv 6 packet is encapsulated in an IPv 4 packet when it enters the region, and it leaves its capsule when it exits the region. Tunneling is a strategy used when two computers using IPv 6 want to communicate with each other and the packet must pass through a region that uses IPv 4. In header translation, the header format must be totally changed from IPv 4 to IPv 6. Header translation is necessary when the majority of the Internet has moved to IPv 6 but some systems still use IPv 4. 15 -Jun-21 Networks and Communication Department

9 Q 6: What are the two protocols defined by IPSec? Are both AH and ESP needed for IP security? Why or why not? The two protocols defined by IPSec for exchanging datagrams are Authentication Header (AH) and Encapsulating Security Payload (ESP). Either AH or ESP is needed for IP security. ESP, with greater functionality than AH, was developed after AH was already in use. 15 -Jun-21 Networks and Communication Department

Q 7: What is a VPN and why is it needed? 10 A VPN is a technology that allows an organization to use the global Internet yet safely maintain private internal communication. 15 -Jun-21 Networks and Communication Department

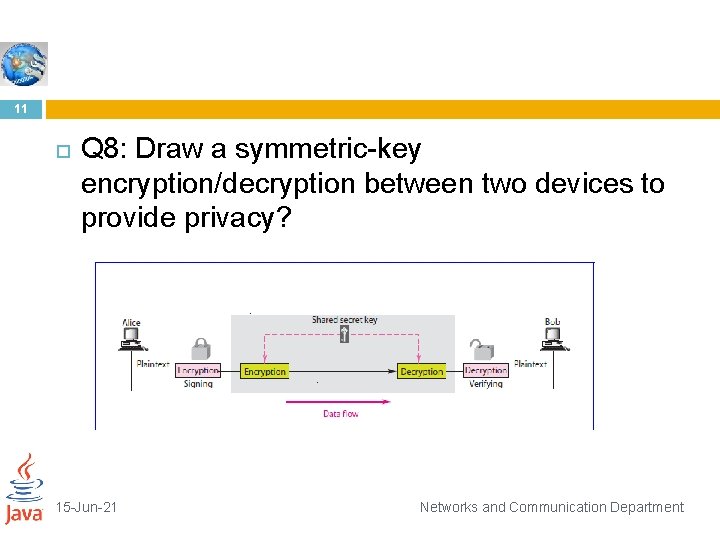
11 Q 8: Draw a symmetric-key encryption/decryption between two devices to provide privacy? 15 -Jun-21 Networks and Communication Department

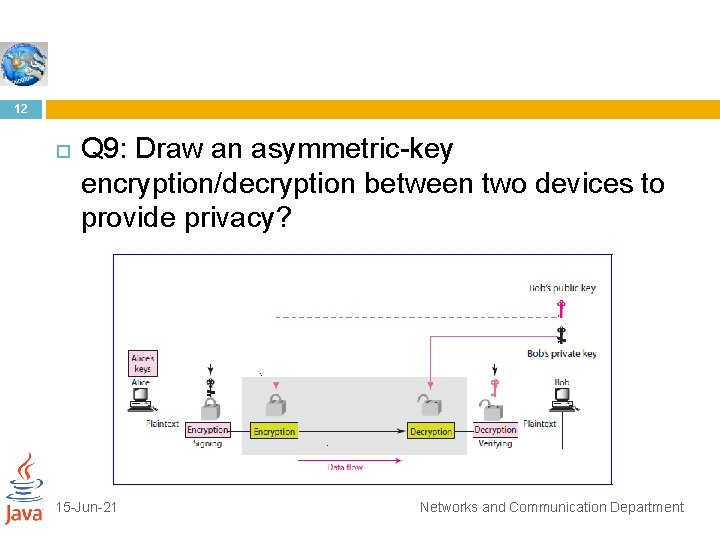
12 Q 9: Draw an asymmetric-key encryption/decryption between two devices to provide privacy? 15 -Jun-21 Networks and Communication Department

13 Q&A 15 -Jun-21 Networks and Communication Department