1 Current Network Firewall Architecture Internet 3750 Switch
- Slides: 2

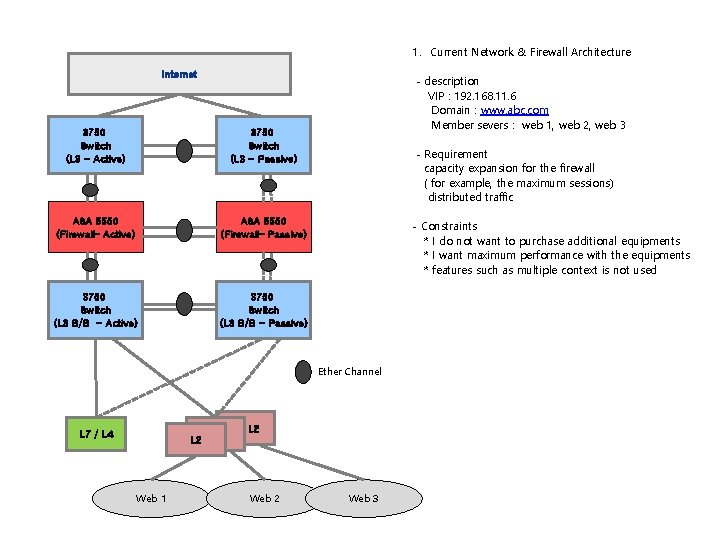
1. Current Network & Firewall Architecture Internet 3750 Switch (L 3 - Active) 3750 Switch (L 3 - Passive) ASA 5550 (Firewall– Active) ASA 5550 (Firewall– Passive) 3750 Switch (L 3 B/B - Active) 3750 Switch (L 3 B/B - Passive) - description VIP : 192. 168. 11. 6 Domain : www. abc. com Member severs : web 1, web 2, web 3 - Requirement capacity expansion for the firewall ( for example, the maximum sessions) distributed traffic - Constraints * I do not want to purchase additional equipments * I want maximum performance with the equipments * features such as multiple context is not used Ether Channel L 7 / L 4 L 2 Web 1 L 2 Web 3

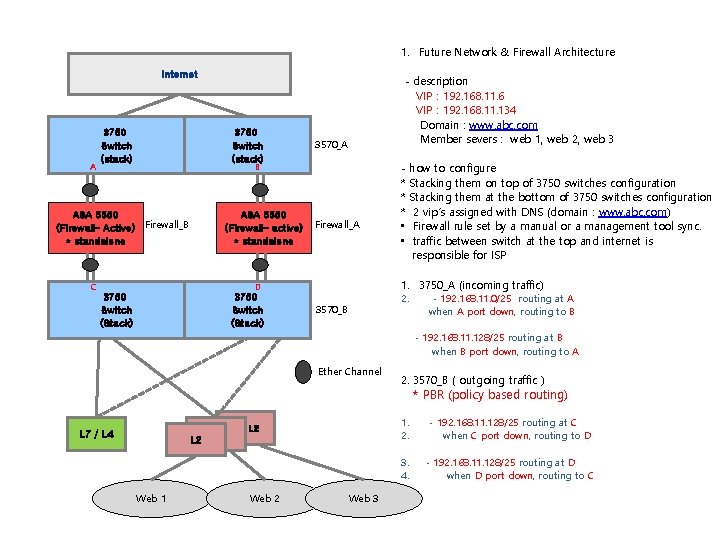
1. Future Network & Firewall Architecture Internet A 3750 Switch (stack) - description VIP : 192. 168. 11. 6 VIP : 192. 168. 11. 134 Domain : www. abc. com Member severs : web 1, web 2, web 3 3570_A B ASA 5550 (Firewall– Active) Firewall_B * standalone ASA 5550 (Firewall– active) * standalone C Firewall_A 3750 Switch (Stack) how to configure Stacking them on top of 3750 switches configuration Stacking them at the bottom of 3750 switches configuration 2 vip’s assigned with DNS (domain : www. abc. com) Firewall rule set by a manual or a management tool sync. traffic between switch at the top and internet is responsible for ISP 1. 3750_A (incoming traffic) D 3750 Switch (Stack) * * * • • 2. 3570_B - 192. 168. 11. 0/25 routing at A when A port down, routing to B - 192. 168. 11. 128/25 routing at B when B port down, routing to A Ether Channel 2. 3570_B ( outgoing traffic ) * PBR (policy based routing) L 7 / L 4 L 2 Web 1 L 2 Web 3 1. 2. - 192. 168. 11. 128/25 routing at C when C port down, routing to D 3. 4. - 192. 168. 11. 128/25 routing at D when D port down, routing to C 5.