1 Contents MANET overview Properties of MANET applications

















![[Johnson-96] 44 [Johnson-96] 44](https://slidetodoc.com/presentation_image_h/2b05456c3d0a6b169b633ef9855863a2/image-44.jpg)

![Route Discovery in DSR Y Broadcast transmission [S] S Z E F B C Route Discovery in DSR Y Broadcast transmission [S] S Z E F B C](https://slidetodoc.com/presentation_image_h/2b05456c3d0a6b169b633ef9855863a2/image-47.jpg)
![Route Discovery in DSR S E Y Z [S, E] F B C A Route Discovery in DSR S E Y Z [S, E] F B C A](https://slidetodoc.com/presentation_image_h/2b05456c3d0a6b169b633ef9855863a2/image-48.jpg)
![Route Discovery in DSR Y Z S E F B [S, E, F] C Route Discovery in DSR Y Z S E F B [S, E, F] C](https://slidetodoc.com/presentation_image_h/2b05456c3d0a6b169b633ef9855863a2/image-49.jpg)
![Route Discovery in DSR Y Z S E [S, E, F, J] F B Route Discovery in DSR Y Z S E [S, E, F, J] F B](https://slidetodoc.com/presentation_image_h/2b05456c3d0a6b169b633ef9855863a2/image-50.jpg)
![Route Discovery in DSR Y Z S E [S, E, F, J, M] F Route Discovery in DSR Y Z S E [S, E, F, J, M] F](https://slidetodoc.com/presentation_image_h/2b05456c3d0a6b169b633ef9855863a2/image-51.jpg)

![Route Reply in DSR S E Y Z RREP [S, E, F, J, D] Route Reply in DSR S E Y Z RREP [S, E, F, J, D]](https://slidetodoc.com/presentation_image_h/2b05456c3d0a6b169b633ef9855863a2/image-53.jpg)
![Data Delivery in DSR Y Z DATA [S, E, F, J, D] S E Data Delivery in DSR Y Z DATA [S, E, F, J, D] S E](https://slidetodoc.com/presentation_image_h/2b05456c3d0a6b169b633ef9855863a2/image-55.jpg)

![[Ko 98 Mobicom] 59 [Ko 98 Mobicom] 59](https://slidetodoc.com/presentation_image_h/2b05456c3d0a6b169b633ef9855863a2/image-59.jpg)

![[Perkins-99] 63 [Perkins-99] 63](https://slidetodoc.com/presentation_image_h/2b05456c3d0a6b169b633ef9855863a2/image-63.jpg)









![[Haas 98] 81 [Haas 98] 81](https://slidetodoc.com/presentation_image_h/2b05456c3d0a6b169b633ef9855863a2/image-81.jpg)




- Slides: 94

1

Contents • • MANET overview Properties of MANET applications Routing and various routing algorithms – – Unicast routing protocols for MANET Broadcasting protocols for MANET Multicasting Protocols for MANET QOS Routing • Security in MANETS. Syllabus from chapter 15, 17 in handbook of wireless networks and mobile computing. By Ivan Stojmenovic 2

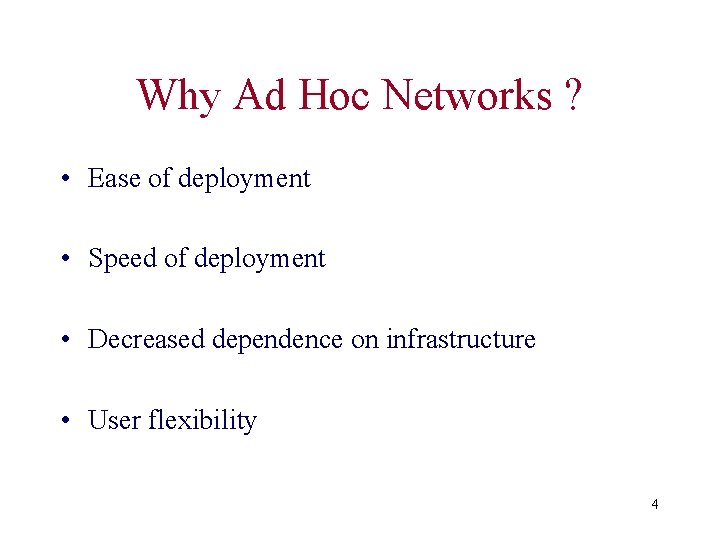
Mobile Ad Hoc Networks • Formed by wireless autonomous hosts • Without (necessarily) using a pre-existing infrastructure • Routes between hosts may potentially contain multiple hops • Host mobility cause route changes • Shared wireless channel 3

Why Ad Hoc Networks ? • Ease of deployment • Speed of deployment • Decreased dependence on infrastructure • User flexibility 4

Application areas • Military environments – Battle field: sensors, soldiers, vehicles • Emergency operations – search-and-rescue – policing and fire fighting • Civilian environments – conference halls – sports stadiums, Library, etc. • Personal area networking – laptop, PDA, cell phone, ear phone, wrist watch 5

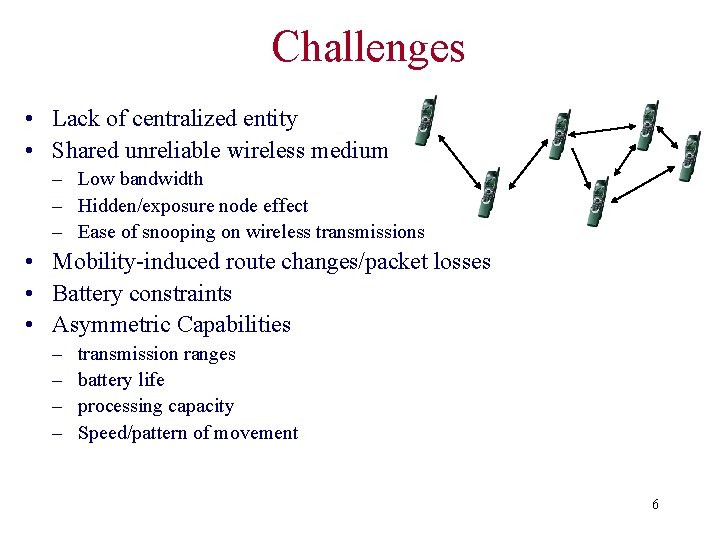
Challenges • Lack of centralized entity • Shared unreliable wireless medium – Low bandwidth – Hidden/exposure node effect – Ease of snooping on wireless transmissions • Mobility-induced route changes/packet losses • Battery constraints • Asymmetric Capabilities – – transmission ranges battery life processing capacity Speed/pattern of movement 6

Why is Routing in MANET Different? • Host mobility – link failure/repair due to mobility • different characteristics than those due to other causes – Rate of link failure/repair may be high when nodes move fast • Distributed Environment • New performance criteria may be used – Route stability despite mobility – Packet delivery ratio – Routing Overhead 7

8

Routing • Routing protocols in ad hoc networks need to deal with the mobility of nodes and constraints in power and bandwidth • Current transport protocols (e. g. TCP) are not designed for wireless ad hoc networks 9

• The properties of the ad-hoc network routing protocol – Simple – Less storage space – Loop free – Short control message (Low overhead) – Less power consumption – Multiple disjoint routes – Fast rerouting mechanism 10

Unicast Routing Protocols for Ad Hoc Networks • Many protocols have been proposed • Some specifically invented for MANET • Others adapted from protocols for wired networks • No single protocol works well in all environments – some attempts made to develop adaptive/hybrid protocols • Standardization efforts in IETF – MANET, Mobile. IP working groups – http: //www. ietf. org 11

AD-HOC MOBILE ROUTING PROTOCOLS FLAT ROUTING TABLE DRIVEN/ PROACTIVE DSDV ON-DEMAND-DRIVEN REACTIVE HYBRID DSR AODV WRP TORA ZRP 12

Ad Hoc Unicast Routing Protocols • Proactive protocols – Traditional distributed shortest-path protocols – Maintain routes between every host pair at all times – Based on periodic updates; High routing overhead – Example: DSDV (destination sequenced distance vector) • Reactive protocols – Determine route if and when needed – Source initiates route discovery – Example: DSR (dynamic source routing) • Hybrid protocols – Adaptive; Combination of proactive and reactive – Example : ZRP (zone routing protocol) 13

Proactive unicast routing protocols • • • Continuously makes routing decisions so routes are available when packets need to be transmitted Traditional distributed shortest-path protocols Maintain routes between every host pair at all times They consume a great deal of radio resources to exchange routing information – Based on periodic updates – High routing overhead – However, pre-determined routes may rapidly lose their validity in an ad hoc network • because its topology changes rapidly These attempt to maintain the network topology always updated by periodically exchanging control packets – Every node has a complete forwarding table • i. e. for any destination it knows the right next-hop, and optimal routing (e. g. shortest path) is possible Their problem is that the amount of control traffic is huge and often disproportionate 14 the – In highly dynamic networks, it is likely to happen that most of bandwidth is wasted in vain because nodes’ reaction to topological

DSDV Destination-Sequenced Distance-Vector Routing Protocol 15

Introduction • Routing Algorithm – Link-State algorithm: • Each node maintains a view of the network topology – Distance-Vector algorithm: • Every node maintains the distance of each destination 16

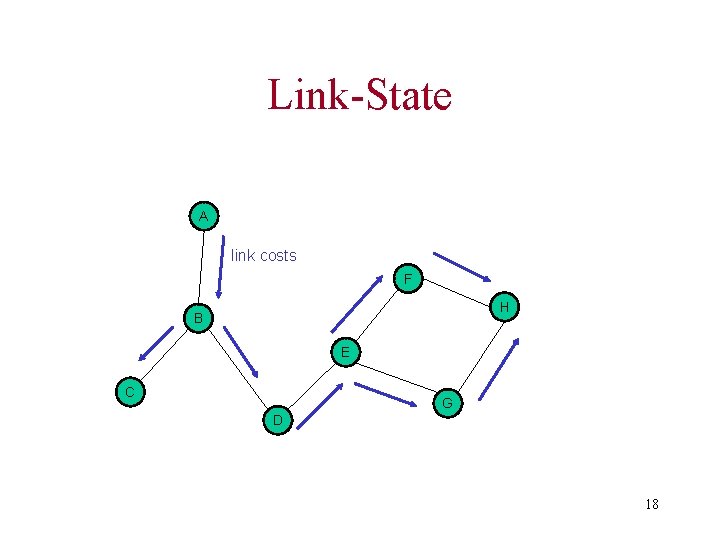
Link-State • Like the shortest-path computation method • Each node maintains a view of the network topology with a cost for each link • Periodically broadcast link costs to its outgoing links to all other nodes such as flooding 17

Link-State A link costs F H B E C G D 18

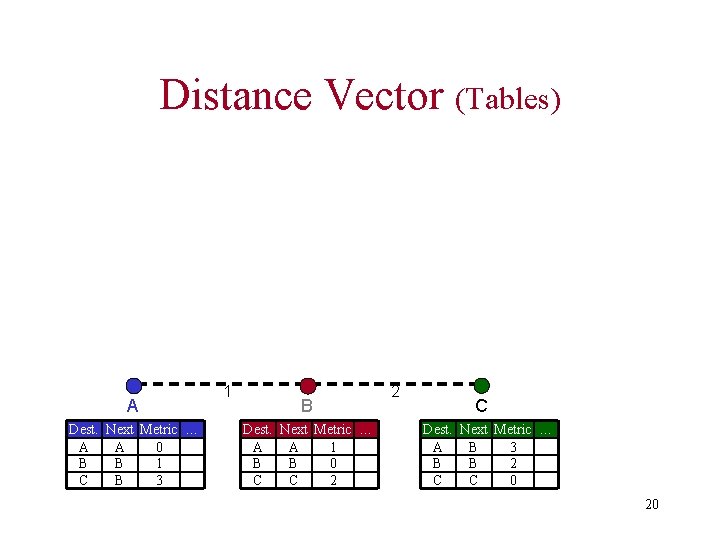
Distance-Vector • known also as Distributed Bellman-Ford or RIP (Routing Information Protocol) • Every node maintains a routing table – all available destinations – the next node to reach to destination – the number of hops to reach the destination • Periodically send table to all neighbors to maintain topology 19

Distance Vector (Tables) A Dest. Next Metric … A A 0 B B 1 C B 3 1 B Dest. Next Metric … A A 1 B B 0 C C 2 2 C Dest. Next Metric … A B 3 B B 2 C C 0 20

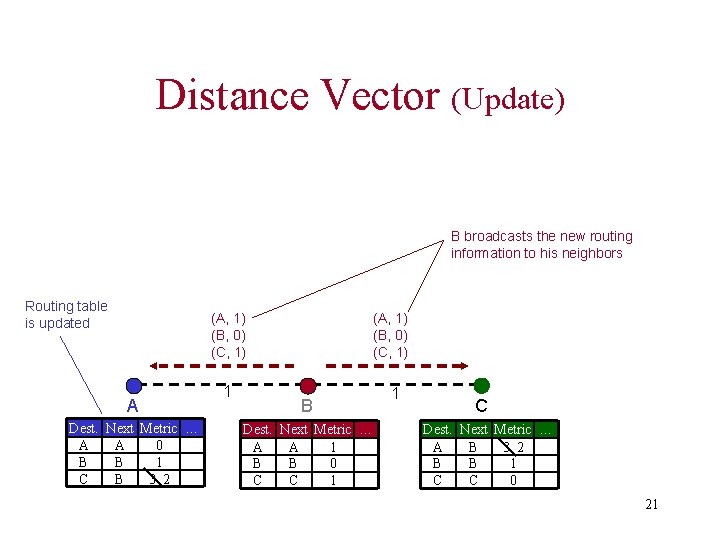
Distance Vector (Update) B broadcasts the new routing information to his neighbors Routing table is updated (A, 1) (B, 0) (C, 1) A Dest. Next Metric … A A 0 B B 1 C B 3 2 1 (A, 1) (B, 0) (C, 1) B Dest. Next Metric … A A 1 B B 0 C C 1 1 C Dest. Next Metric … A B 3 2 B B 1 C C 0 21

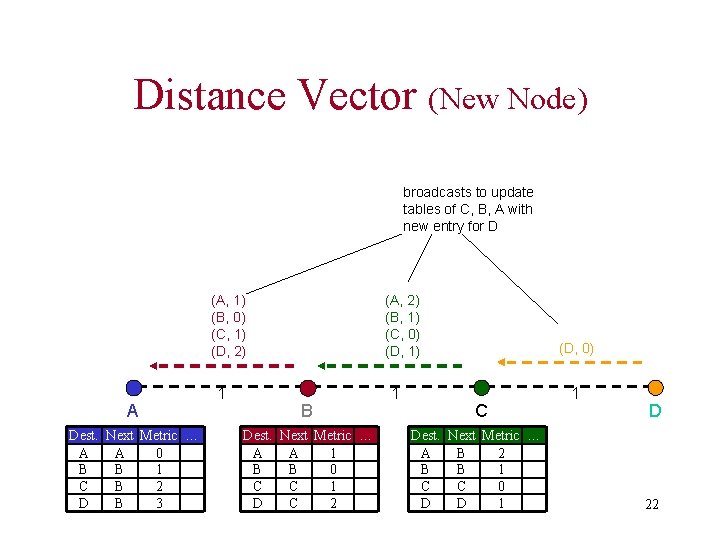
Distance Vector (New Node) broadcasts to update tables of C, B, A with new entry for D (A, 1) (B, 0) (C, 1) (D, 2) A Dest. Next Metric … A A 0 B B 1 C B 2 D B 3 1 (A, 2) (B, 1) (C, 0) (D, 1) B Dest. Next Metric … A A 1 B B 0 C C 1 D C 2 1 (D, 0) C Dest. Next Metric … A B 2 B B 1 C C 0 D D 1 1 D 22

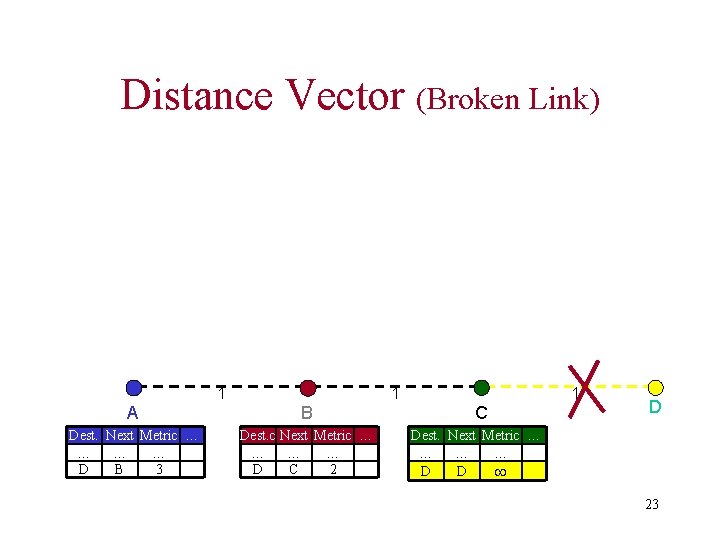
Distance Vector (Broken Link) 1 1 A B Dest. Next Metric … … D B 3 Dest. c Next Metric … … D C 2 1 C D Dest. Next Metric … … B 1 D D 23

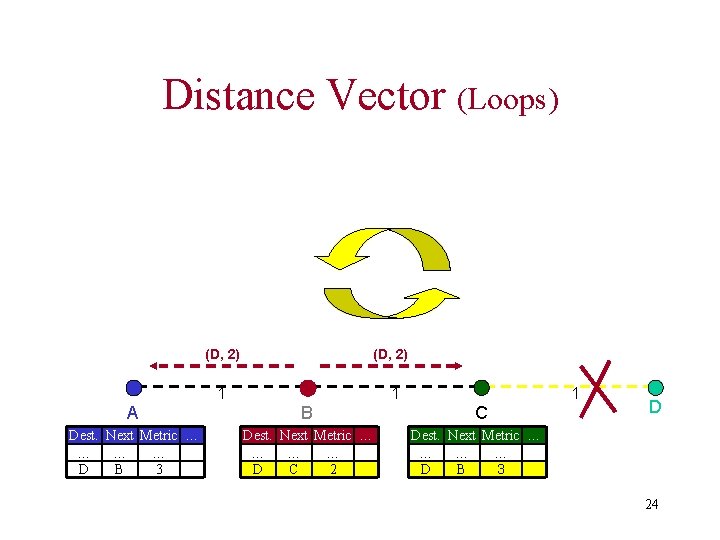
Distance Vector (Loops) (D, 2) 1 1 A B Dest. Next Metric … … D B 3 Dest. Next Metric … … D C 2 1 C D Dest. Next Metric … … D B 3 24

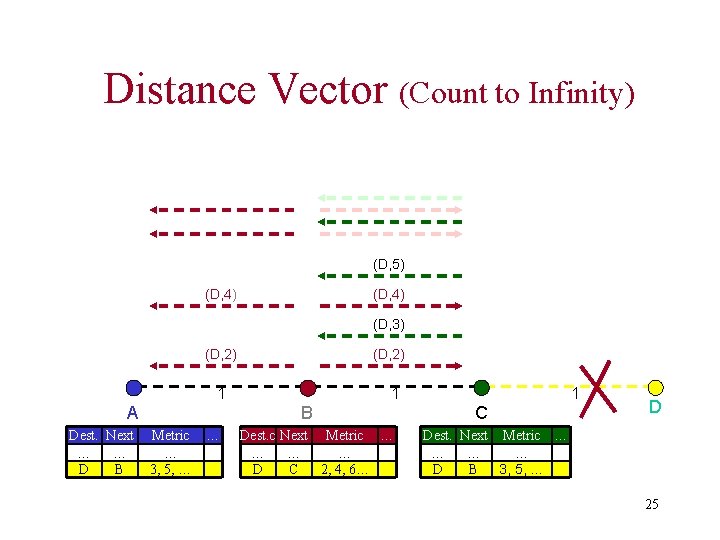
Distance Vector (Count to Infinity) (D, 5) (D, 4) (D, 3) (D, 2) 1 A Dest. Next … … D B 1 B Metric … … 3, 5, … Dest. c Next Metric … … D C 2, 4, 6… 1 C D Dest. Next Metric … … D B 3, 5, … 25

Distance Vector • DV not suited for ad-hoc networks! – Loops – Count to Infinity • New Solution -> DSDV Protocol 26

DSDV Protocol • DSDV is Destination Based • No global view of topology 27

DSDV Protocol • DSDV is Proactive (Table Driven) – Each node maintains routing information for all known destinations – Routing information must be updated periodically – Traffic overhead even if there is no change in network topology – Maintains routes which are never used 28

DSDV Protocol • Keep the simplicity of Distance Vector • Guarantee Loop Freeness – New Table Entry for Destination Sequence Number • Allow fast reaction to topology changes – Make immediate route advertisement on significant changes in routing table – but wait with advertising of unstable routes (damping fluctuations) 29

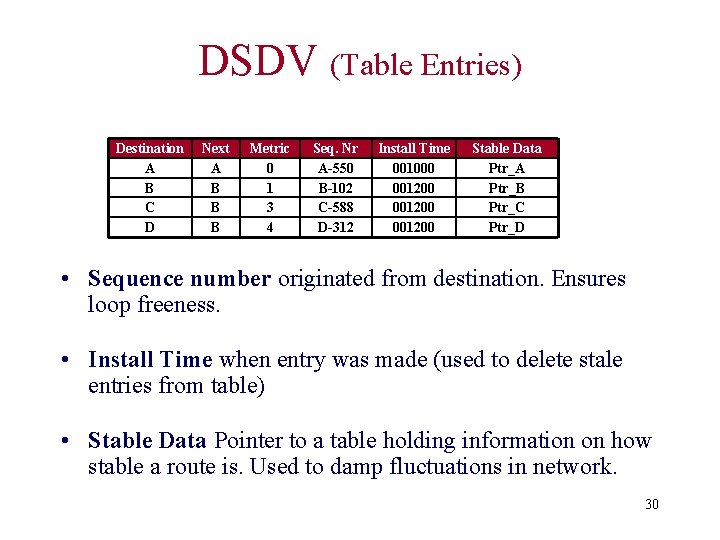
DSDV (Table Entries) Destination A B C D Next A B B B Metric 0 1 3 4 Seq. Nr A-550 B-102 C-588 D-312 Install Time 001000 001200 Stable Data Ptr_A Ptr_B Ptr_C Ptr_D • Sequence number originated from destination. Ensures loop freeness. • Install Time when entry was made (used to delete stale entries from table) • Stable Data Pointer to a table holding information on how stable a route is. Used to damp fluctuations in network. 30

DSDV (Route Advertisements) • Advertise to each neighbor own routing information – Destination Address – Metric = Number of Hops to Destination – Destination Sequence Number • Rules to set sequence number information – On each advertisement increase own destination sequence number (use only even numbers) – If a node is no more reachable (timeout) increase sequence number of this node by 1 (odd sequence number) and set metric = 31

DSDV (Route Selection) • Update information is compared to own routing table – 1. Select route with higher destination sequence number (This ensure to use always newest information from destination) – 2. Select the route with better metric when sequence numbers are equal. 32

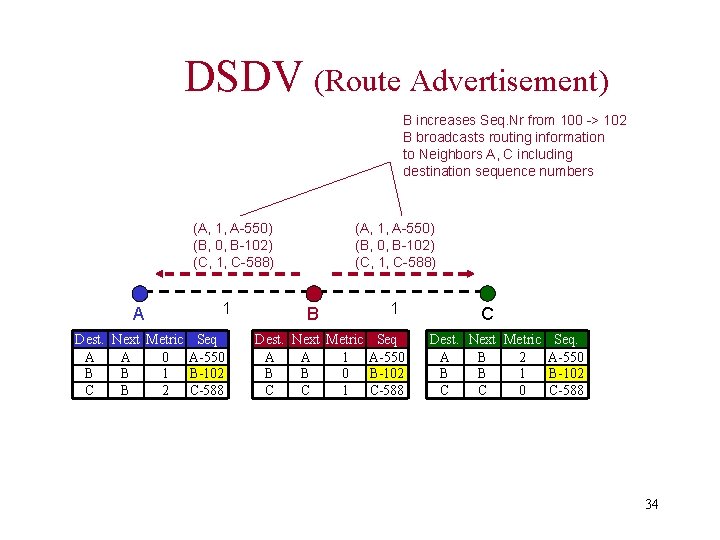
DSDV (Tables) A 1 Dest. Next Metric Seq A A 0 A-550 B B 1 B-100 C B 3 C-586 B 2 Dest. Next Metric Seq A A 1 A-550 B B 0 B-100 C C 2 C-588 C Dest. Next Metric Seq. A B 1 A-550 B B 2 B-100 C C 0 C-588 33

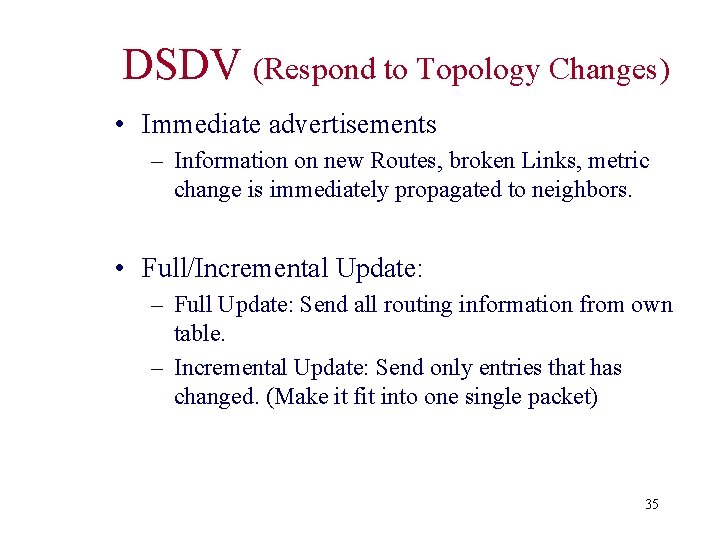
DSDV (Route Advertisement) B increases Seq. Nr from 100 -> 102 B broadcasts routing information to Neighbors A, C including destination sequence numbers (A, 1, A-550) (B, 0, B-102) (C, 1, C-588) A 1 Dest. Next Metric Seq A A 0 A-550 B B 1 B-102 C B 2 C-588 (A, 1, A-550) (B, 0, B-102) (C, 1, C-588) B 1 Dest. Next Metric Seq A A 1 A-550 B B 0 B-102 C C 1 C-588 C Dest. Next Metric Seq. A B 2 A-550 B B 1 B-102 C C 0 C-588 34

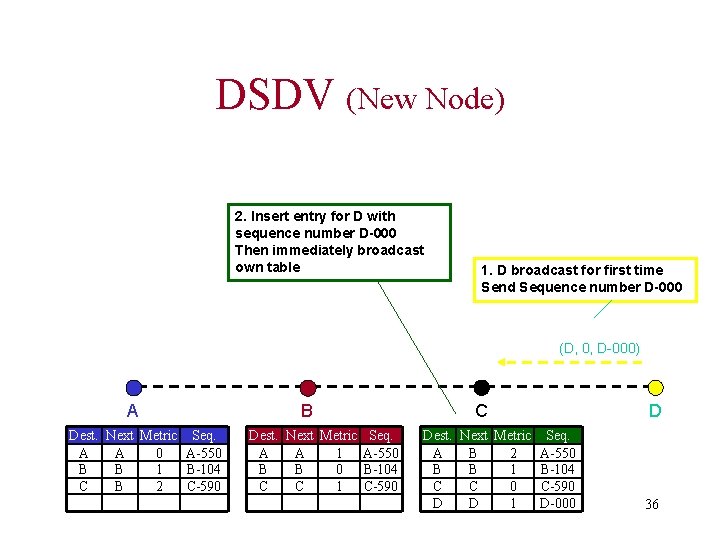
DSDV (Respond to Topology Changes) • Immediate advertisements – Information on new Routes, broken Links, metric change is immediately propagated to neighbors. • Full/Incremental Update: – Full Update: Send all routing information from own table. – Incremental Update: Send only entries that has changed. (Make it fit into one single packet) 35

DSDV (New Node) 2. Insert entry for D with sequence number D-000 Then immediately broadcast own table 1. D broadcast for first time Send Sequence number D-000 (D, 0, D-000) A Dest. Next Metric Seq. A A 0 A-550 B B 1 B-104 C B 2 C-590 B Dest. Next Metric Seq. A A 1 A-550 B B 0 B-104 C C 1 C-590 C Dest. Next Metric Seq. A B 2 A-550 B B 1 B-104 C C 0 C-590 D D 1 D-000 D 36

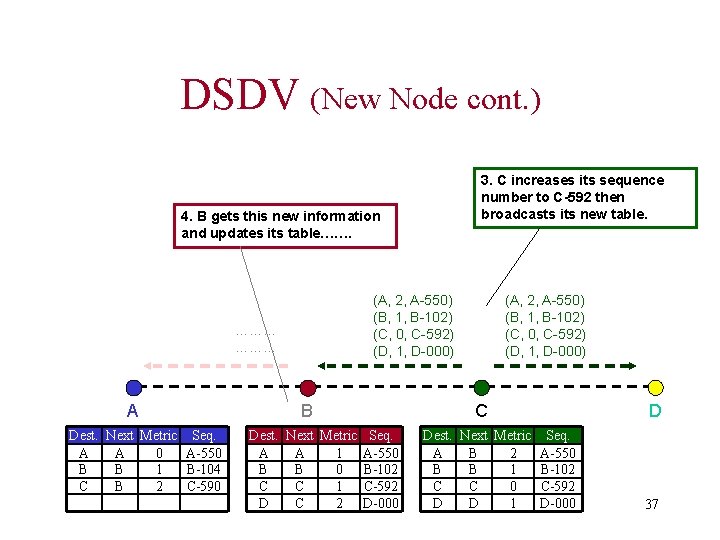
DSDV (New Node cont. ) 3. C increases its sequence number to C-592 then broadcasts its new table. 4. B gets this new information and updates its table……. (A, 2, A-550) (B, 1, B-102) (C, 0, C-592) (D, 1, D-000) ……… A Dest. Next Metric Seq. A A 0 A-550 B B 1 B-104 C B 2 C-590 B Dest. Next Metric Seq. A A 1 A-550 B B 0 B-102 C C 1 C-592 D C 2 D-000 (A, 2, A-550) (B, 1, B-102) (C, 0, C-592) (D, 1, D-000) C Dest. Next Metric Seq. A B 2 A-550 B B 1 B-102 C C 0 C-592 D D 1 D-000 D 37

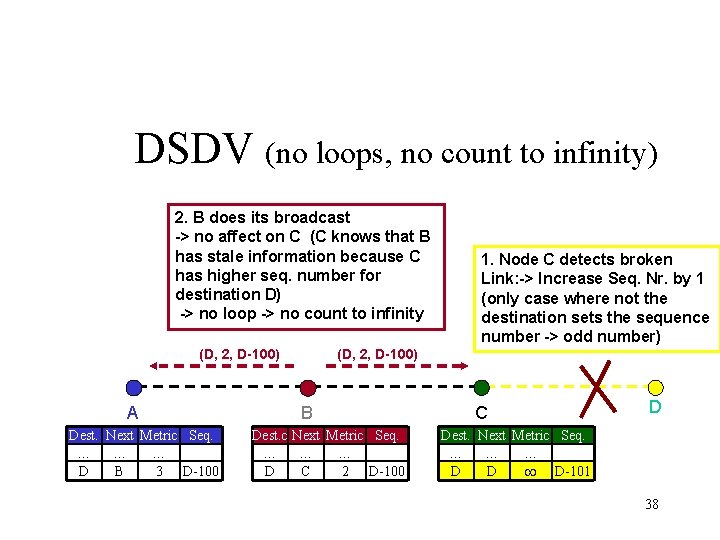
DSDV (no loops, no count to infinity) 2. B does its broadcast -> no affect on C (C knows that B has stale information because C has higher seq. number for destination D) -> no loop -> no count to infinity (D, 2, D-100) A Dest. Next Metric Seq. … … … D B 3 D-100 1. Node C detects broken Link: -> Increase Seq. Nr. by 1 (only case where not the destination sets the sequence number -> odd number) (D, 2, D-100) B Dest. c Next Metric Seq. … … … D C 2 D-100 C D Dest. Next Metric Seq. … … … D D D-101 38

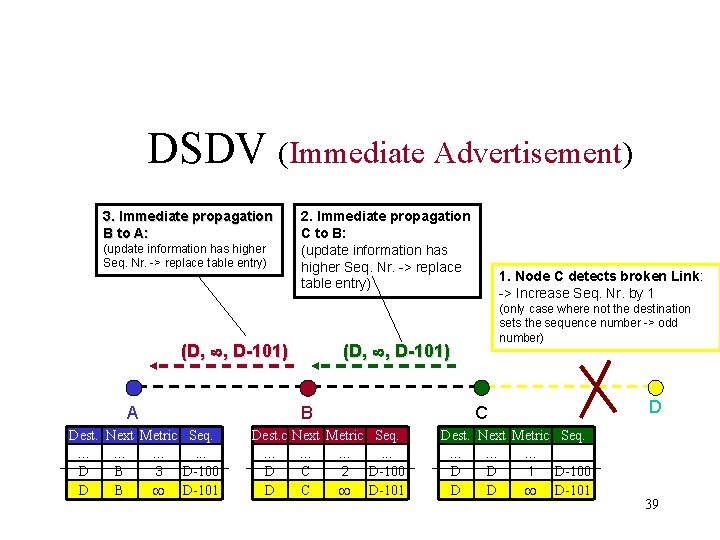
DSDV (Immediate Advertisement) 3. Immediate propagation B to A: (update information has higher Seq. Nr. -> replace table entry) 2. Immediate propagation C to B: (update information has higher Seq. Nr. -> replace table entry) (D, , D-101) A Dest. Next Metric Seq. … … …. . . 4 D-100 D B 3 D B D-101 (only case where not the destination sets the sequence number -> odd number) (D, , D-101) B Dest. c … D D 1. Node C detects broken Link: -> Increase Seq. Nr. by 1 Next Metric Seq. … …. . . C 3 D-100 2 C D-101 C Dest. Next Metric Seq. … … … B D D 1 D-100 D D D-101 D 39

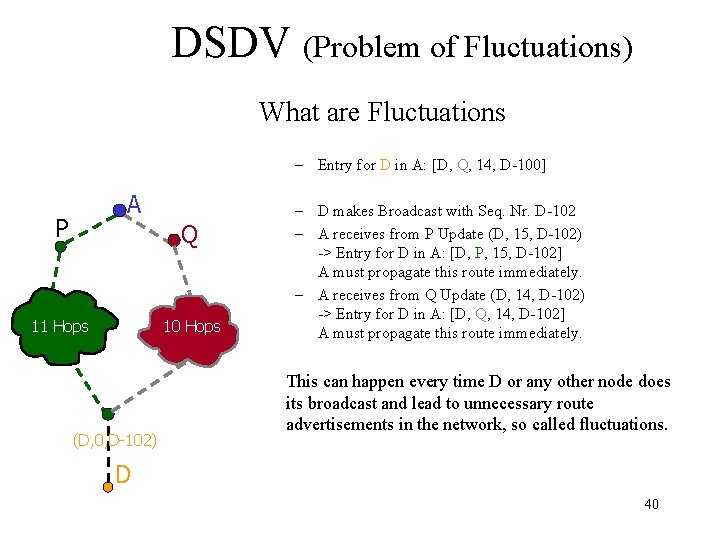
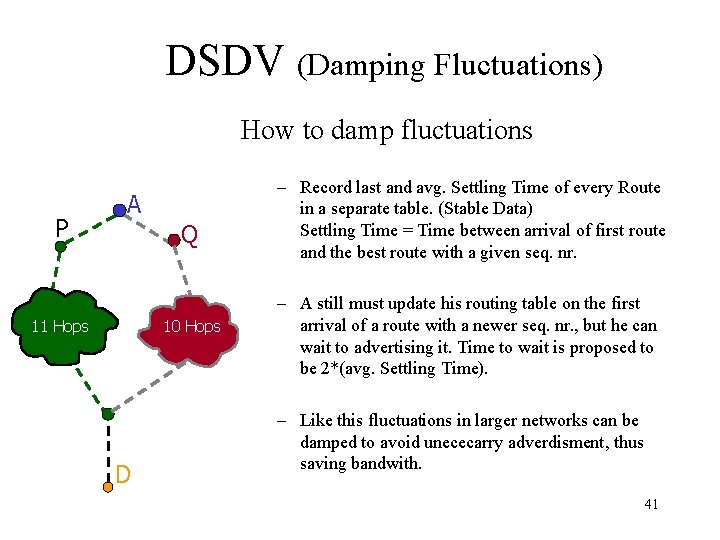
DSDV (Problem of Fluctuations) What are Fluctuations – Entry for D in A: [D, Q, 14, D-100] A P Q 11 Hops 10 Hops (D, 0, D-102) – D makes Broadcast with Seq. Nr. D-102 – A receives from P Update (D, 15, D-102) -> Entry for D in A: [D, P, 15, D-102] A must propagate this route immediately. – A receives from Q Update (D, 14, D-102) -> Entry for D in A: [D, Q, 14, D-102] A must propagate this route immediately. This can happen every time D or any other node does its broadcast and lead to unnecessary route advertisements in the network, so called fluctuations. D 40

DSDV (Damping Fluctuations) How to damp fluctuations P A Q 11 Hops 10 Hops D – Record last and avg. Settling Time of every Route in a separate table. (Stable Data) Settling Time = Time between arrival of first route and the best route with a given seq. nr. – A still must update his routing table on the first arrival of a route with a newer seq. nr. , but he can wait to advertising it. Time to wait is proposed to be 2*(avg. Settling Time). – Like this fluctuations in larger networks can be damped to avoid unececarry adverdisment, thus saving bandwith. 41

Summery of DSDV • Advantages – Simple (almost like Distance Vector) – Loop free through destination seq. numbers – No latency caused by route discovery • Disadvantages – No sleeping nodes – Overhead: most routing information never used 42

Reactive unicast routing protocols • Determine routes on an as-needed basis: – when a node has a packet to transmit, it queries the network for a route • Source initiates route discovery • They performed better than proactive protocols • Reactive protocols are on-demand protocols: routes are discovered only if needed – i. e. when the source does not know a route to the destination. • Nodes do not make any effort to keep routing table updated • Most of the routing protocols are reactive • Examples: – AODV – DSR (dynamic source routing) – TORA etc… 43
![Johnson96 44 [Johnson-96] 44](https://slidetodoc.com/presentation_image_h/2b05456c3d0a6b169b633ef9855863a2/image-44.jpg)
[Johnson-96] 44

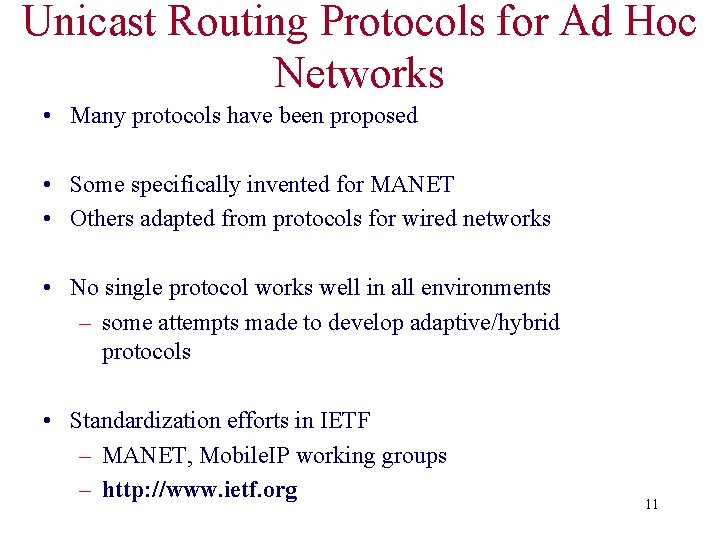
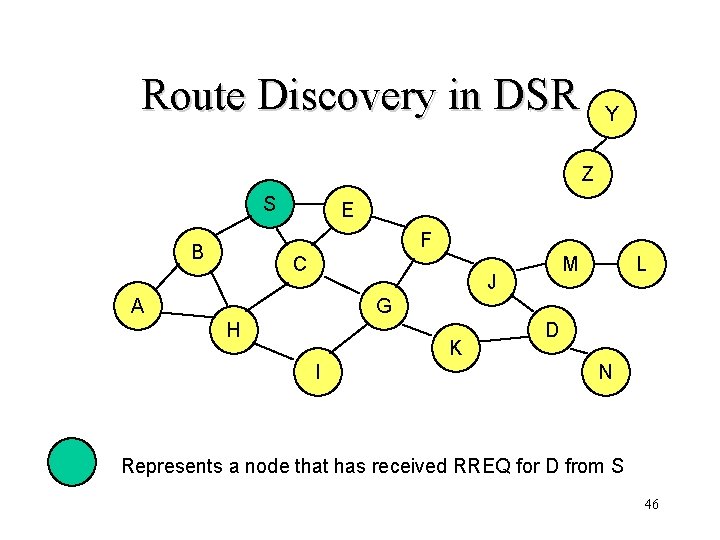
• When node S wants to send a packet to node D, but does not know a route to D, node S initiates a route discovery • Source node S floods Route Request (RREQ) • Each node appends own identifier when forwarding RREQ 45

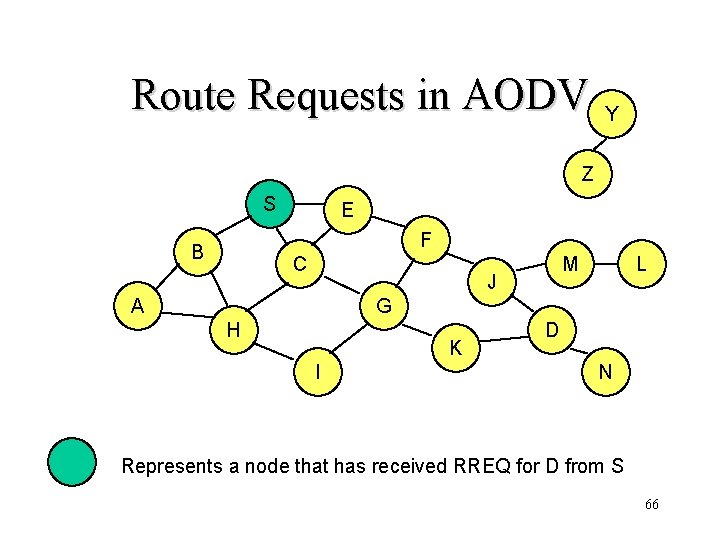
Route Discovery in DSR Y Z S E F B C M J A L G H K I D N Represents a node that has received RREQ for D from S 46
![Route Discovery in DSR Y Broadcast transmission S S Z E F B C Route Discovery in DSR Y Broadcast transmission [S] S Z E F B C](https://slidetodoc.com/presentation_image_h/2b05456c3d0a6b169b633ef9855863a2/image-47.jpg)
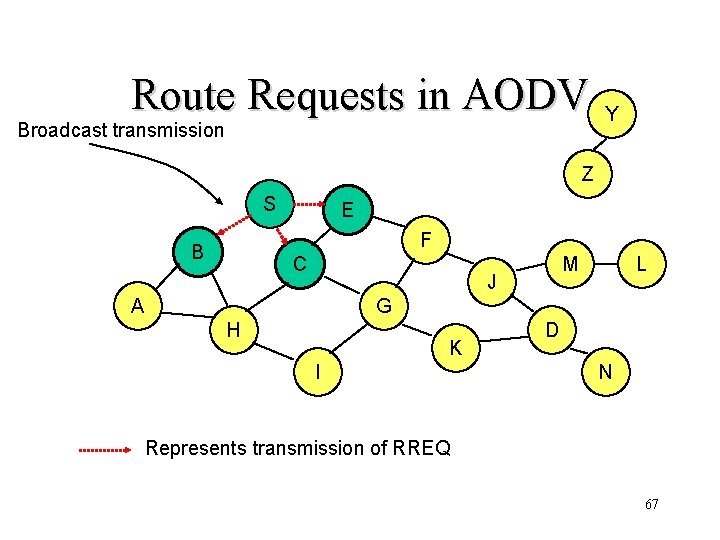
Route Discovery in DSR Y Broadcast transmission [S] S Z E F B C M J A L G H K D I N Represents transmission of RREQ [X, Y] Represents list of identifiers appended to RREQ 47
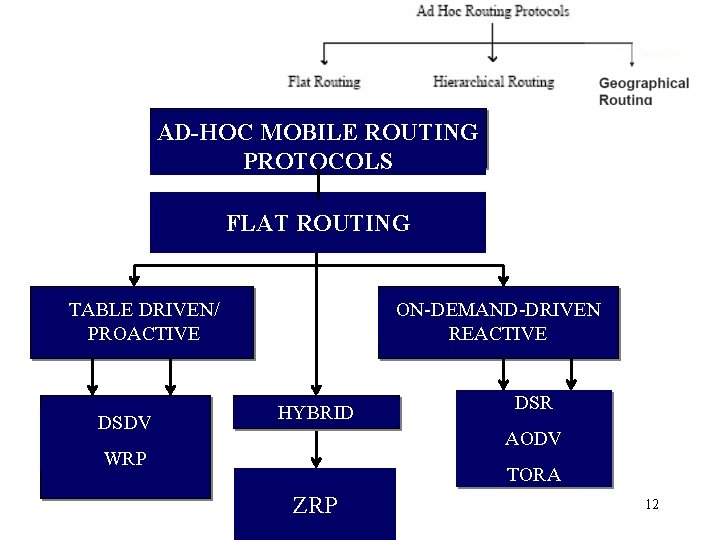
![Route Discovery in DSR S E Y Z S E F B C A Route Discovery in DSR S E Y Z [S, E] F B C A](https://slidetodoc.com/presentation_image_h/2b05456c3d0a6b169b633ef9855863a2/image-48.jpg)
Route Discovery in DSR S E Y Z [S, E] F B C A M J [S, C] H L G K D I N • Node H receives packet RREQ from two neighbors: potential for collision 48
![Route Discovery in DSR Y Z S E F B S E F C Route Discovery in DSR Y Z S E F B [S, E, F] C](https://slidetodoc.com/presentation_image_h/2b05456c3d0a6b169b633ef9855863a2/image-49.jpg)
Route Discovery in DSR Y Z S E F B [S, E, F] C M J A L G H I [S, C, G] K D N • Node C receives RREQ from G and H, but does not forward it again, because node C has already forwarded RREQ once 49
![Route Discovery in DSR Y Z S E S E F J F B Route Discovery in DSR Y Z S E [S, E, F, J] F B](https://slidetodoc.com/presentation_image_h/2b05456c3d0a6b169b633ef9855863a2/image-50.jpg)
Route Discovery in DSR Y Z S E [S, E, F, J] F B C J A L M G H K I D [S, C, G, K] • Nodes J and K both broadcast RREQ to node D • Since nodes J and K are hidden from each other, their transmissions may collide N 50
![Route Discovery in DSR Y Z S E S E F J M F Route Discovery in DSR Y Z S E [S, E, F, J, M] F](https://slidetodoc.com/presentation_image_h/2b05456c3d0a6b169b633ef9855863a2/image-51.jpg)
Route Discovery in DSR Y Z S E [S, E, F, J, M] F B C M J A L G H K D I • Node D does not forward RREQ, because node D is the intended target of the route discovery N 51

Route Discovery in DSR • Destination D on receiving the first RREQ, sends a Route Reply (RREP) • RREP is sent on a route obtained by reversing the route appended to received RREQ 52
![Route Reply in DSR S E Y Z RREP S E F J D Route Reply in DSR S E Y Z RREP [S, E, F, J, D]](https://slidetodoc.com/presentation_image_h/2b05456c3d0a6b169b633ef9855863a2/image-53.jpg)
Route Reply in DSR S E Y Z RREP [S, E, F, J, D] F B C J A L M G H K I Represents RREP control message D N 53

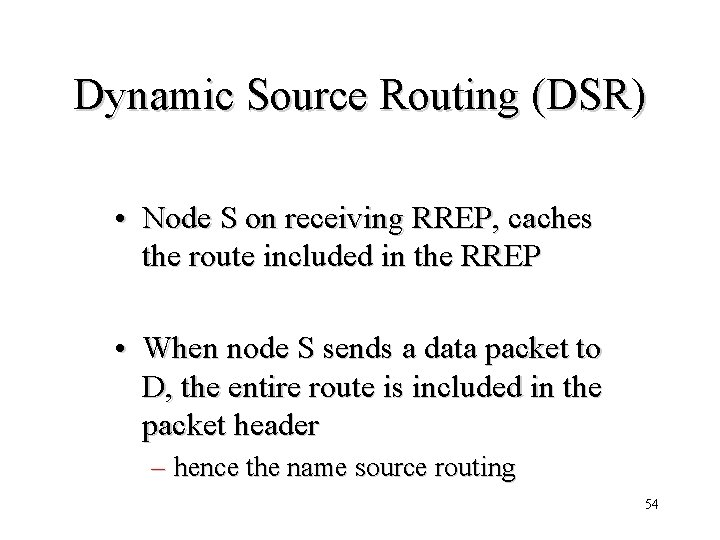
Dynamic Source Routing (DSR) • Node S on receiving RREP, caches the route included in the RREP • When node S sends a data packet to D, the entire route is included in the packet header – hence the name source routing 54
![Data Delivery in DSR Y Z DATA S E F J D S E Data Delivery in DSR Y Z DATA [S, E, F, J, D] S E](https://slidetodoc.com/presentation_image_h/2b05456c3d0a6b169b633ef9855863a2/image-55.jpg)
Data Delivery in DSR Y Z DATA [S, E, F, J, D] S E F B C J A L M G H K I D N Packet header size grows with route length 55

DSR Optimization: Route Caching • Each node caches a new route it learns by any means • When node S finds route [S, E, F, J, D] to node D, node S also learns route [S, E, F] to node F • When node K receives Route Request [S, C, G] destined for node, node K learns route [K, G, C, S] to node S • When node F forwards Route Reply RREP [S, E, F, J, D], node F learns route [F, J, D] to node 56 D

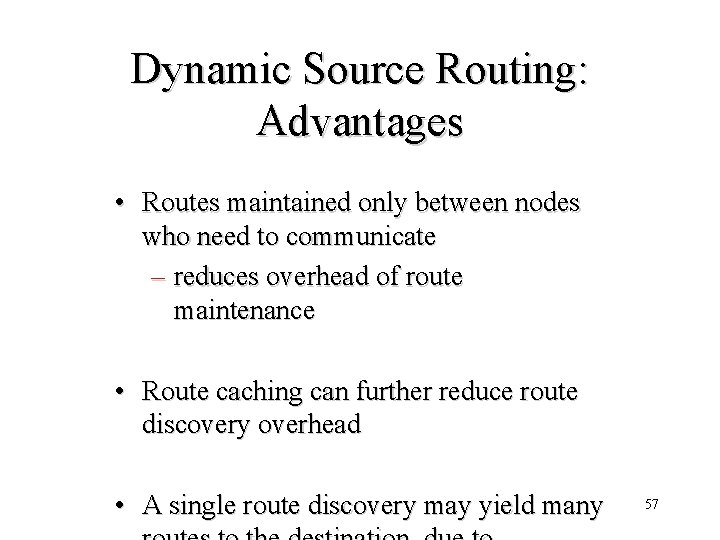
Dynamic Source Routing: Advantages • Routes maintained only between nodes who need to communicate – reduces overhead of route maintenance • Route caching can further reduce route discovery overhead • A single route discovery may yield many 57

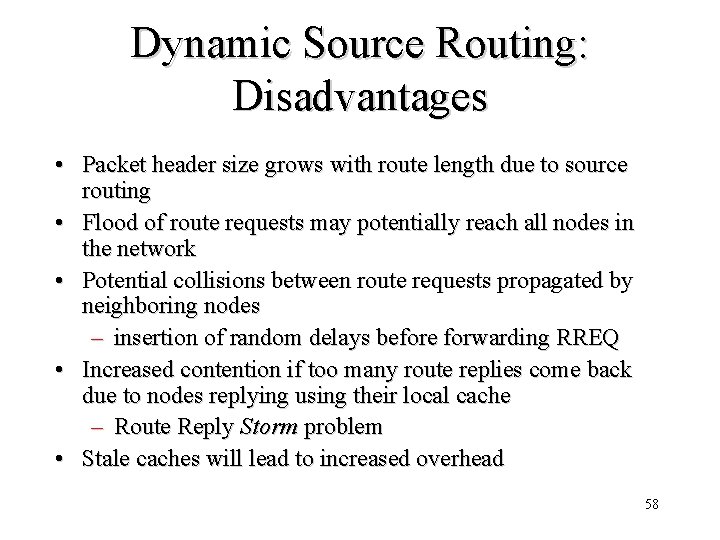
Dynamic Source Routing: Disadvantages • Packet header size grows with route length due to source routing • Flood of route requests may potentially reach all nodes in the network • Potential collisions between route requests propagated by neighboring nodes – insertion of random delays before forwarding RREQ • Increased contention if too many route replies come back due to nodes replying using their local cache – Route Reply Storm problem • Stale caches will lead to increased overhead 58
![Ko 98 Mobicom 59 [Ko 98 Mobicom] 59](https://slidetodoc.com/presentation_image_h/2b05456c3d0a6b169b633ef9855863a2/image-59.jpg)
[Ko 98 Mobicom] 59

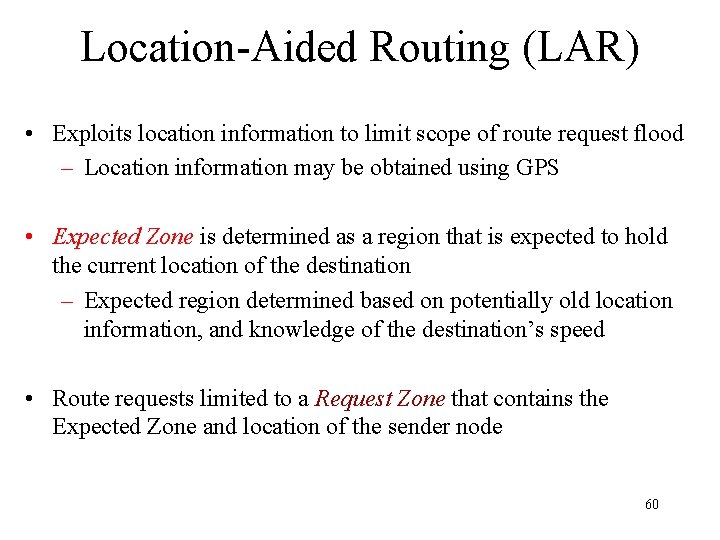
Location-Aided Routing (LAR) • Exploits location information to limit scope of route request flood – Location information may be obtained using GPS • Expected Zone is determined as a region that is expected to hold the current location of the destination – Expected region determined based on potentially old location information, and knowledge of the destination’s speed • Route requests limited to a Request Zone that contains the Expected Zone and location of the sender node 60

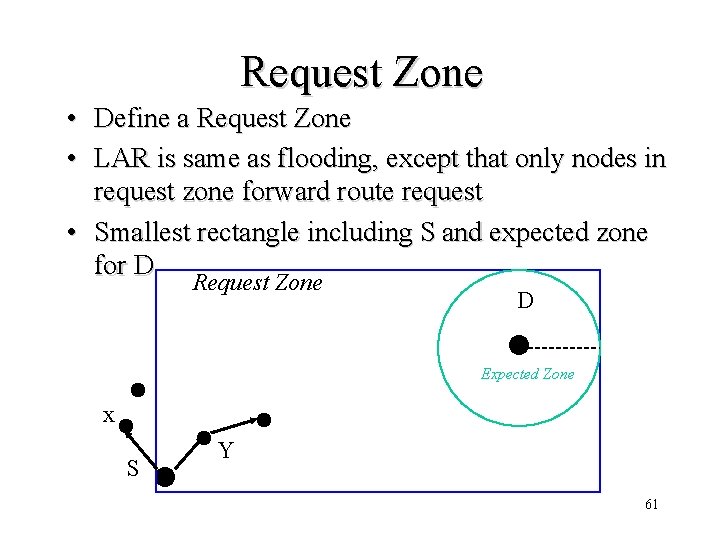
Request Zone • Define a Request Zone • LAR is same as flooding, except that only nodes in request zone forward route request • Smallest rectangle including S and expected zone for D Request Zone D Expected Zone x S Y 61

Location Aided Routing (LAR) • Advantages – reduces the scope of route request flood – reduces overhead of route discovery • Disadvantages – Nodes need to know their physical locations – Does not take into account possible existence of 62 obstructions for radio transmissions
![Perkins99 63 [Perkins-99] 63](https://slidetodoc.com/presentation_image_h/2b05456c3d0a6b169b633ef9855863a2/image-63.jpg)
[Perkins-99] 63

• DSR includes source routes in packet headers • Resulting large headers can sometimes degrade performance – particularly when data contents of a packet are small • AODV attempts to improve on DSR by maintaining routing tables at the nodes, so that data packets do not have to contain routes 64

AODV • Route Requests (RREQ) are forwarded in a manner similar to DSR • When a node re-broadcasts a Route Request, it sets up a reverse path pointing towards the source – AODV assumes directional) links symmetric (bi- • When the intended destination receives a Route Request, it replies 65

Route Requests in AODV Y Z S E F B C M J A L G H K I D N Represents a node that has received RREQ for D from S 66

Route Requests in AODV Broadcast transmission Y Z S E F B C M J A L G H K I D N Represents transmission of RREQ 67

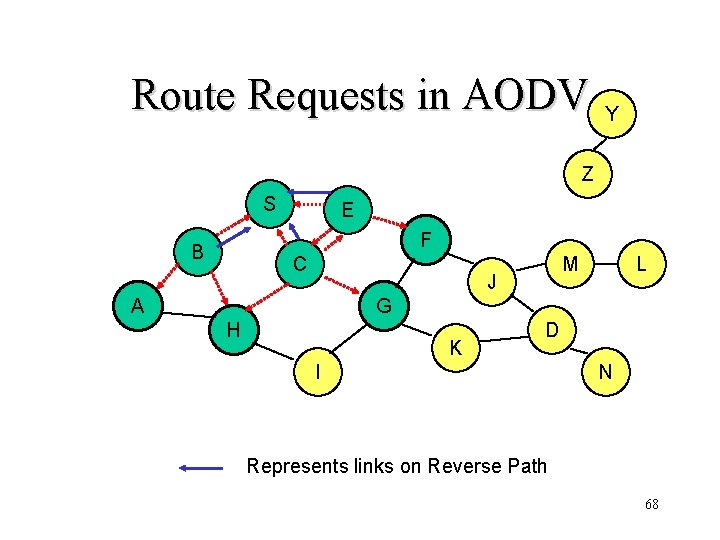
Route Requests in AODV Y Z S E F B C M J A L G H K D I N Represents links on Reverse Path 68

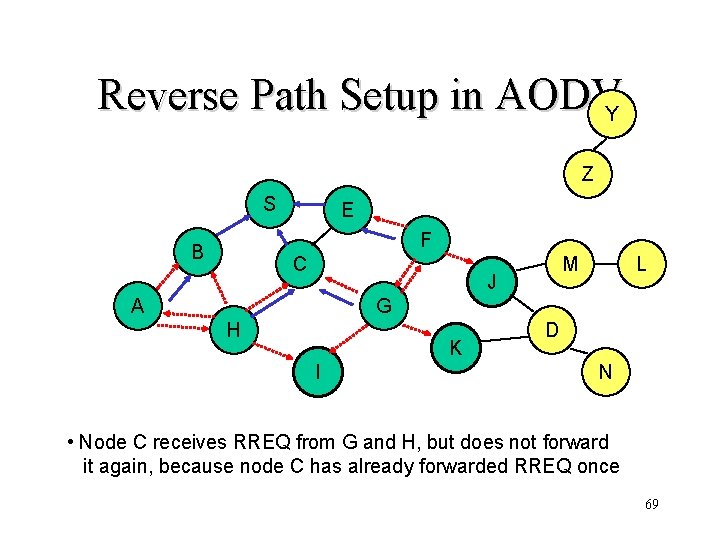
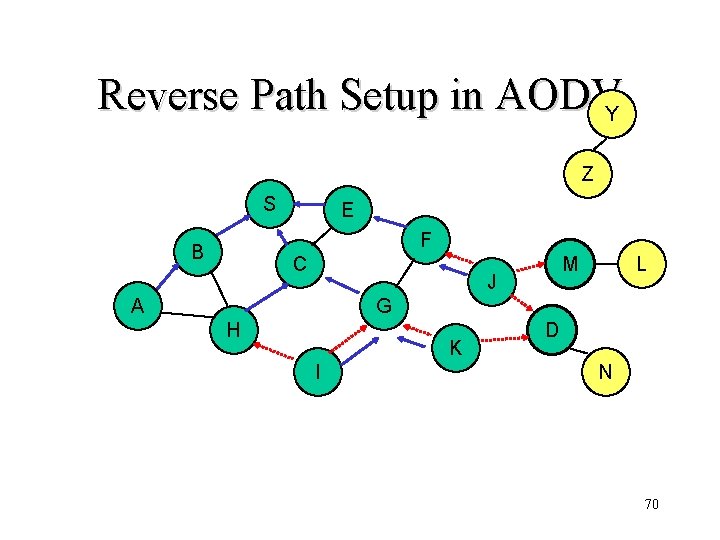
Reverse Path Setup in AODVY Z S E F B C M J A L G H K I D N • Node C receives RREQ from G and H, but does not forward it again, because node C has already forwarded RREQ once 69

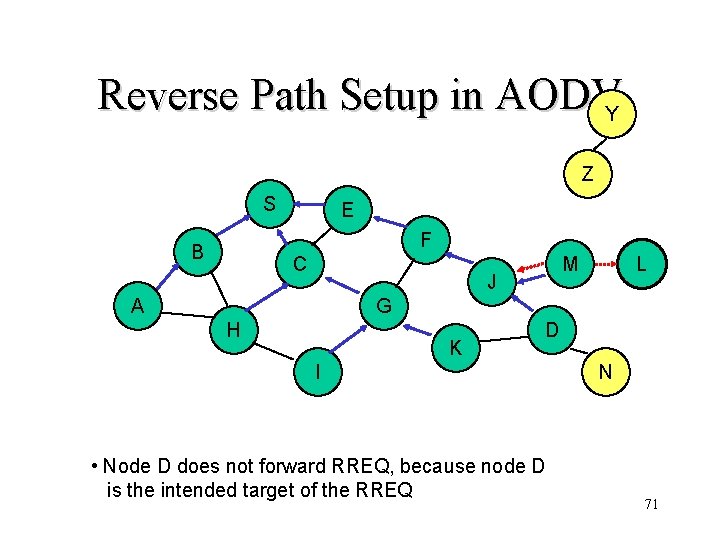
Reverse Path Setup in AODVY Z S E F B C J A L M G H K I D N 70

Reverse Path Setup in AODVY Z S E F B C M J A L G H K D I • Node D does not forward RREQ, because node D is the intended target of the RREQ N 71

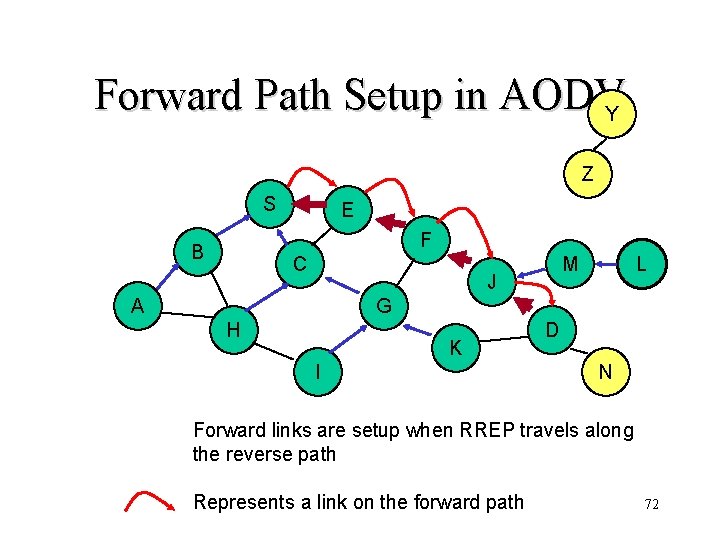
Forward Path Setup in AODVY Z S E F B C M J A L G H K I D N Forward links are setup when RREP travels along the reverse path Represents a link on the forward path 72

Route Request and Route Reply • Route Request (RREQ) includes the last known sequence number for the destination • An intermediate node may also send a Route Reply (RREP) provided that it knows a more recent path than the one previously known to sender • Intermediate nodes that forward the RREP, also record the next hop to destination 73

Link Failure • A neighbor of node X is considered active for a routing table entry if the neighbor sent a packet within active_route_timeout interval which was forwarded using that entry • Neighboring nodes periodically exchange hello message • When the next hop link in a routing table entry breaks, all active neighbors are informed 74

Route Error • When node X is unable to forward packet P (from node S to node D) on link (X, Y), it generates a RERR message • Node X increments the destination sequence number for D cached at node X • The incremented sequence number N is included in the RERR • When node S receives the RERR, it initiates a new route discovery for D using destination sequence number at least as 75 large as

AODV: Summary • Routes are not needed to be included in packet headers • Nodes maintain routing tables containing entries only for routes that are in active use • At most one next-hop per destination maintained at each node – DSR may maintain several routes for a single destination • Sequence numbers are used to avoid 76

77

• Route optimality is considered of secondary importance; longer routes may be used • At each node, a logically separate copy of TORA is run for each destination, that computes the height of the node with respect to the destination • Height captures number of hops and next hop 78

Other Protocols • Many variations of using control packet flooding for route discovery • Power-Aware Routing [Singh 98 Mobicom] – Assign a weight to each link: function of energy consumed when transmitting a packet on that link, as well as the residual energy level – Modify DSR to incorporate weights and prefer a route with the smallest aggregate weight • Associativity-Based Routing (ABR) [Toh 97] – Only links that have been stable for some minimum duration are utilized – Nodes increment the associativity ticks of neighbors by using periodic beacons • Signal Stability Based Adaptive Routing (SSA) [Dube 97] – A node X re-broadcasts a Route Request received from Y only if the (X, Y) link has a strong signal stability – Signal stability is evaluated as a moving average of the signal 79 strength of packets received on the link in recent past

Hybrid Routing Protocols 80
![Haas 98 81 [Haas 98] 81](https://slidetodoc.com/presentation_image_h/2b05456c3d0a6b169b633ef9855863a2/image-81.jpg)
[Haas 98] 81

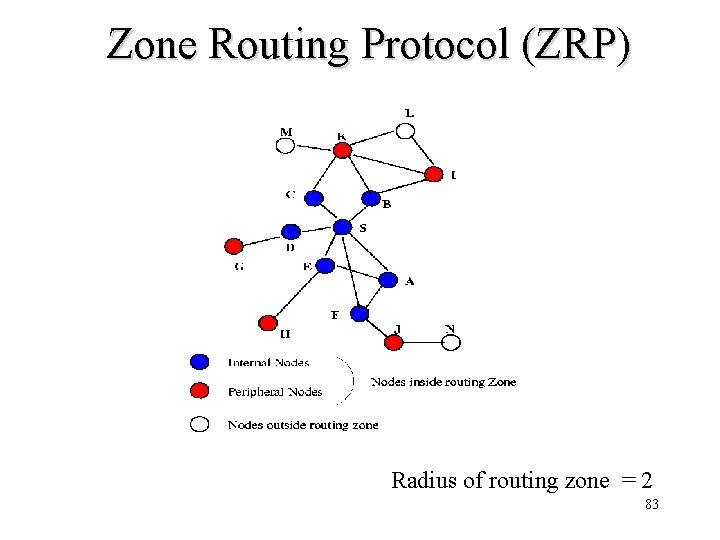
• ZRP combines proactive and reactive approaches • All nodes within hop distance at most d from a node X are said to be in the routing zone of node X • All nodes at hop distance exactly d are said to be peripheral nodes of node X’s routing zone 82 • Intra-zone routing: Proactively

Zone Routing Protocol (ZRP) Radius of routing zone = 2 83

Ad Hoc Unicast Routing Summary • Protocols – Typically divided into proactive, reactive and hybrid – Plenty of routing protocols. Discussion here is far from exhaustive • Performance Studies – Typically studied by simulations using NS, discrete event simulator – Nodes (10 -30) remains stationary for pause time seconds (0 -900 s) and then move to a random destination (1500 m X 300 m space) at a uniform speed (0 -20 m/s). CBR traffic sources (4 -30 packets/sec, 64 -1024 bytes/packet) – Attempt to estimate latency of route discovery, routing overhead … • Actual trade-off depends a lot on traffic and mobility patterns – Higher traffic diversity (more source-destination pairs) increases overhead in on-demand protocols – Higher mobility will always increase overhead in all protocols 84

85

Recap • Multicasting – Group communication – One-to-many • In Battle field – Many-to-many • Rescue team communication • Why not using existing multicast protocol – Resource constraints – Frequent tree reorganization • signaling overhead • loss of datagram – Protocol design • robustness vs. efficiency 86

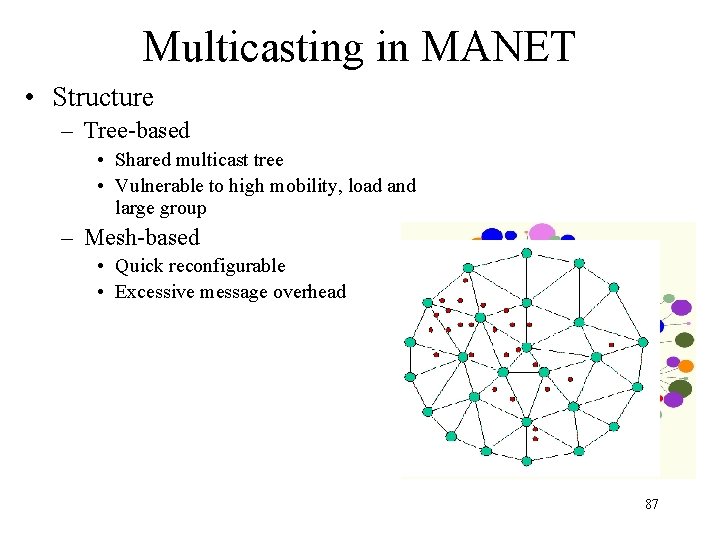
Multicasting in MANET • Structure – Tree-based • Shared multicast tree • Vulnerable to high mobility, load and large group – Mesh-based • Quick reconfigurable • Excessive message overhead 87

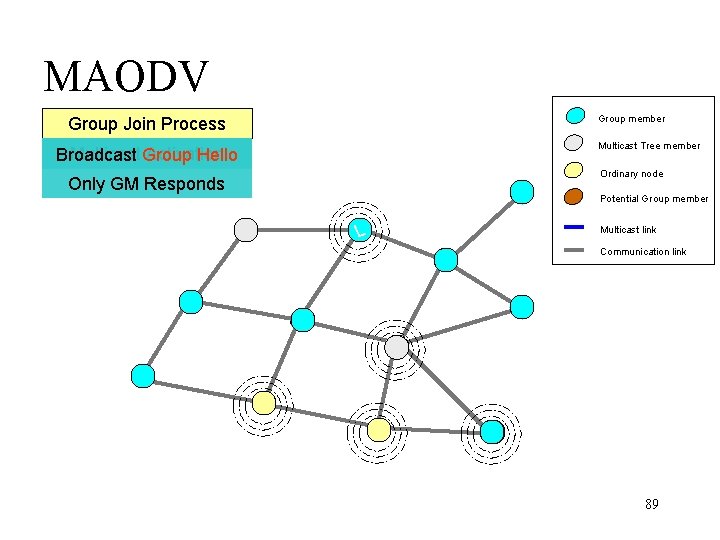
MAODV (Royer and Perkins, 1999) • Each multicast group has a group leader – 1 st node joining a group becomes Group Leader – Responsible for maintaining group SN (sequence number) – SN ensures freshness of routing information • A node on becoming a group leader – Broadcasts a Group Hello message 88

MAODV Group member Group Join Process Multicast Tree member Multicast Broadcast Activation - RREQ Broadcast Group Hello Ordinary node Only GM Responds Potential Group member L Multicast link Communication link 89

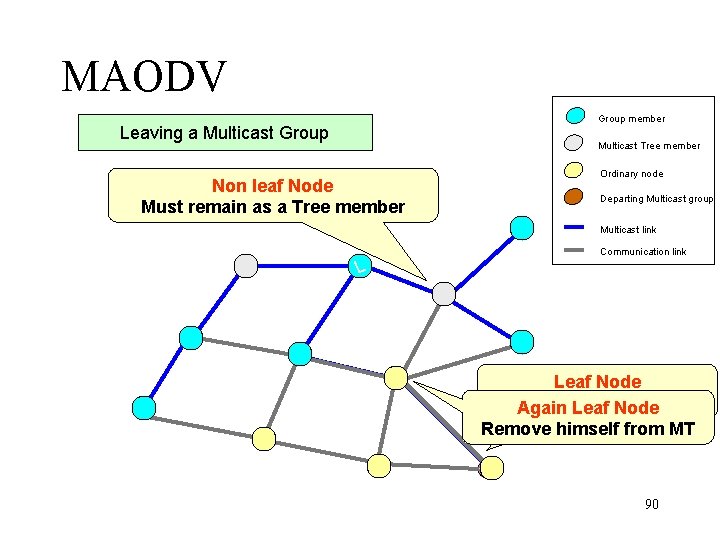
MAODV Group member Leaving a Multicast Group Multicast Tree member Non leaf Node Must remain as a Tree member Ordinary node Departing Multicast group Multicast link Communication link L Leaf Node Send a Prune Again Leaf Node Remove himself from MT 90

MAODV • Observation – Similar to unicast AODV – Leader helps in tree maintenance – No alternate path as it forms a tree – Excessive use of RREQ • lead to multicast tree instability 91

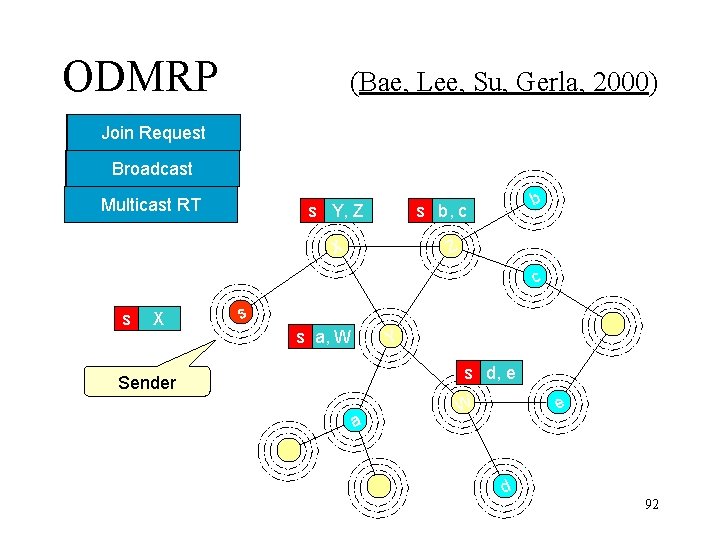
ODMRP (Bae, Lee, Su, Gerla, 2000) Join. Request Reply Forwarding Broadcast Group Multicast RT s Y, Z b s b, c Z X c s X s s a, W Y s d, e Sender a e W d 92

ODMRP Robustness 93

ODMRP • Observation – Sender Forms and Maintains the multicast group – Don’t need to be built on top of a unicast routing protocol – Richer connectivity q. May have multiple routes for one particular destination q. Helps in case of topology changes and node failures – soft state • Member nodes are refreshed as needed by source • Do not send explicit leave message – Periodic Broadcast of Join Request – Control overhead of route refreshes => Scalability issue. 94